Robust Iterative Distributed Minimum Total MSE Algorithm for Secure Communications in the Internet of Things Using Relays
Abstract
1. Introduction
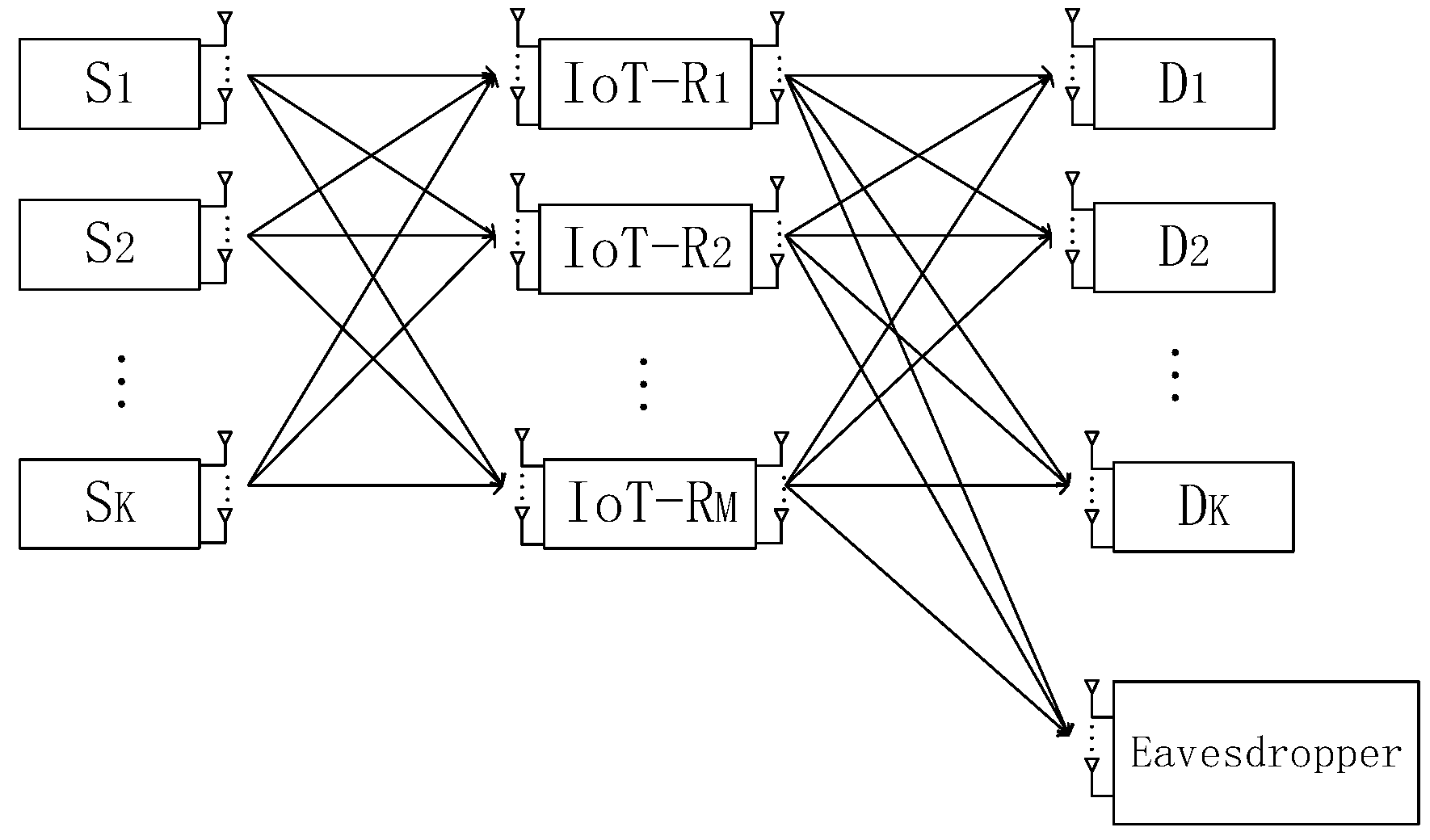
2. System Model and Methods
3. The Iterative Distributed Algorithm of Solving Source, Relay, Destination and Eavesdropper Matrices
3.1. Solution of Destination Matrices
3.2. Solution of Source Matrices
3.3. Solution of Relay Matrices
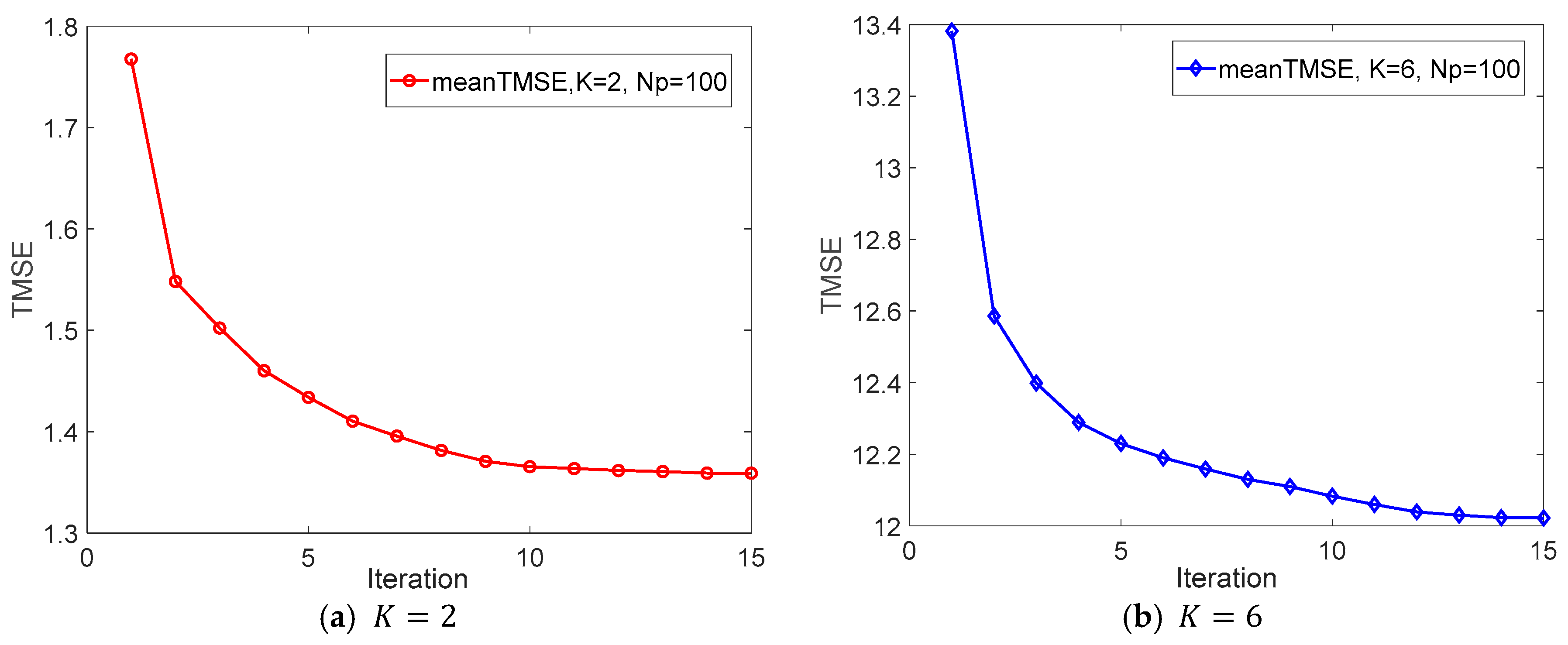
4. The Convergence of the Proposed Algorithm
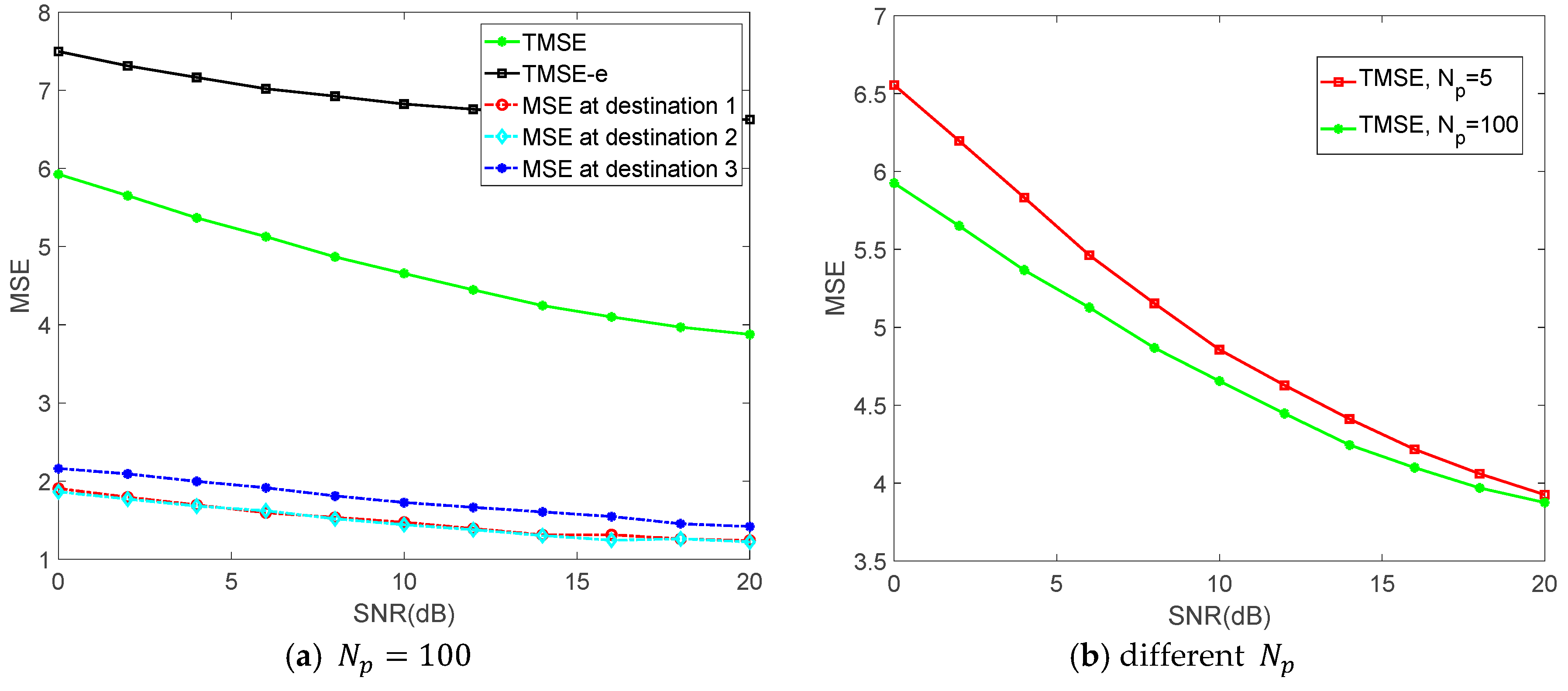
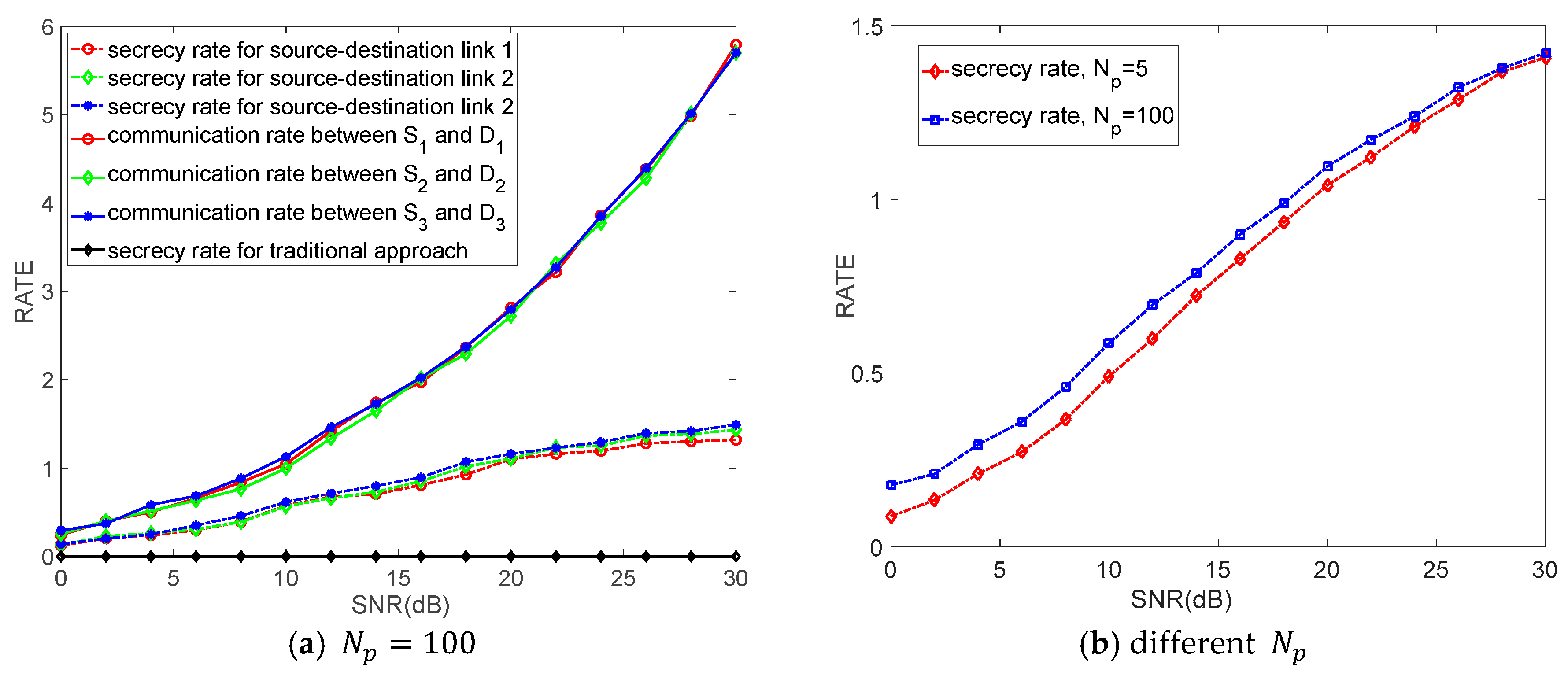
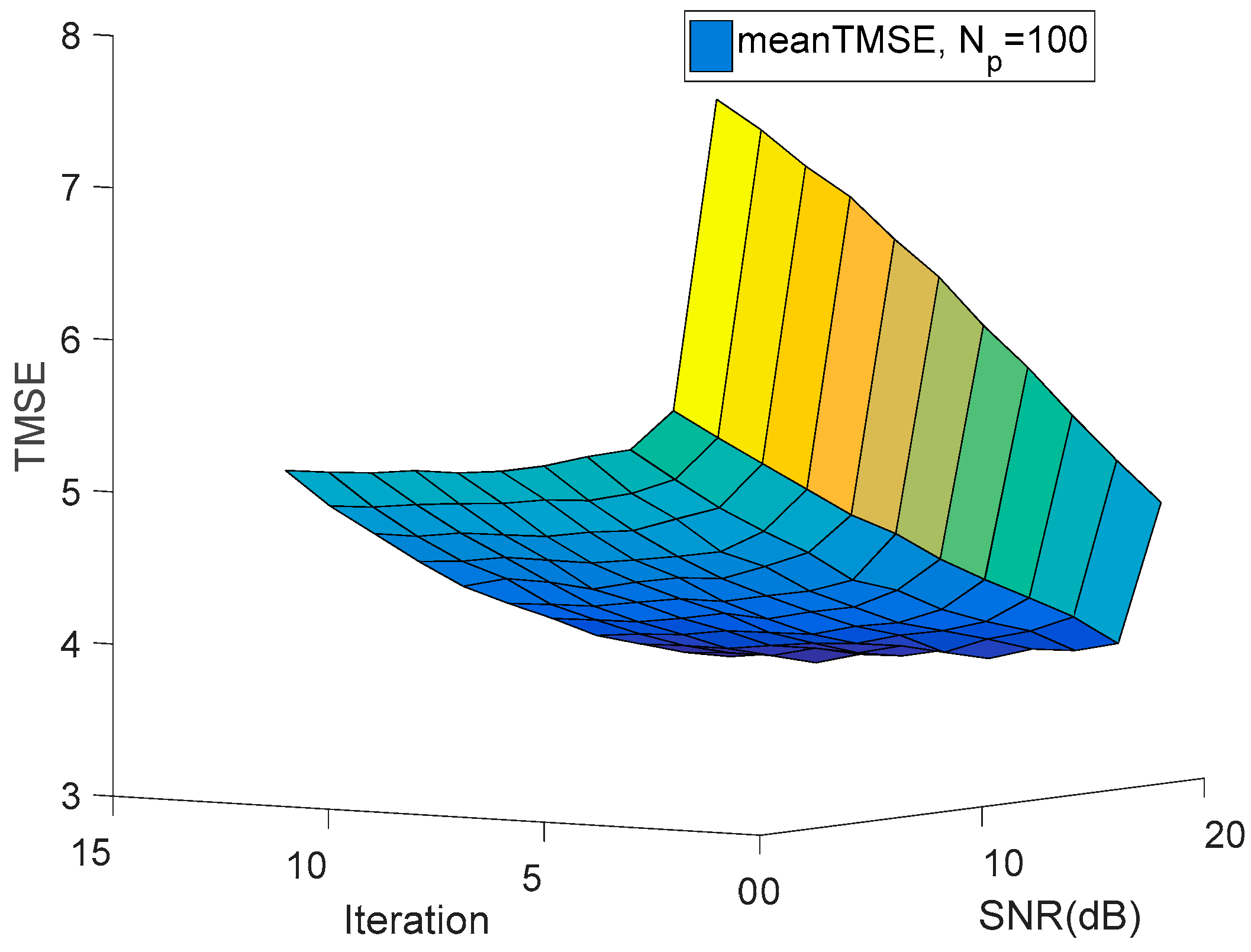
5. Numerical Results
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Zhu, C.; Wang, H.; Liu, X.; Shu, L.; Yang, L.T.; Leung, V.C.M. A novel sensory data processing framework to integrate sensor networks with mobile cloud. IEEE Syst. J. 2016, 10, 1125–1136. [Google Scholar] [CrossRef]
- Liu, H.; Ning, H.; Zhang, Y.; Xiong, Q.; Yang, L.T. Role-dependent privacy preservation for secure V2G networks in the smart grid. IEEE Trans. Inf. Forensics Secur. 2014, 9, 208–220. [Google Scholar] [CrossRef]
- Jiang, P.; Winkley, J.; Zhao, C.; Munnoch, R.; Min, G.; Yang, L.T. An intelligent information forwarder for healthcare big data systems with distributed wearable sensors. IEEE Syst. J. 2016, 10, 1147–1159. [Google Scholar] [CrossRef]
- Liu, H.; Ning, H.; Zhang, Y.; Yang, L.T. Aggregated-proofs based privacy-preserving authentication for V2G networks in the smart grid. IEEE Trans. Smart Grid 2012, 3, 1722–1733. [Google Scholar] [CrossRef]
- Xiong, W.; Hu, H.; Xiong, N.; Yang, L.T.; Peng, W.-C.; Wang, X.; Qu, Y. Anomaly secure detection methods by analyzing dynamic characteristics of the network traffic in cloud communications. Inf. Sci. 2014, 258, 403–415. [Google Scholar] [CrossRef]
- Naik, V.K.; Liu, C.; Yang, L.T.; Wagner, J. Online resource matching for heterogeneous grid environments. In Proceedings of the IEEE International Symposium on Cluster Computing and the Grid, Cardiff, UK, 9–12 May 2005; pp. 607–614. [Google Scholar] [CrossRef]
- Deng, X.J.; Tang, Z.J.; Yang, L.T.; Lin, M.; Wang, B. Confident Information Coverage Hole Healing in Hybrid Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2018, 14, 2220–2229. [Google Scholar] [CrossRef]
- Deng, X.J.; Tang, Z.J.; Yi, L.Z.; Yang, L.T. Healing Multimodal Confident Information Coverage Holes in NB-IoT-Enabled Networks. IEEE Internet Things J. 2018, 5, 1463–1473. [Google Scholar] [CrossRef]
- Deng, X.J.; Yang, L.T.; Yi, L.Z.; Wang, M.; Zhu, Z. Detecting Confident Information Coverage Hole in Industrial Internet of Things: An Energy-Efficient Perspective. IEEE Commun. Mag. 2018, 56, 68–73. [Google Scholar] [CrossRef]
- Yi, L.Z.; Deng, X.J.; Wang, M.H.; Ding, D.; Wang, Y. Localized Confident Information Coverage Hole Detection in Internet of Things for Radioactive Pollution Monitoring. IEEE Access 2017, 5, 18665–18674. [Google Scholar] [CrossRef]
- Zou, Z.H.; Deng, X.J.; Yi, L.Z.; Tang, Z.; Wang, M.; Gong, X. A Novel Confident Information Coverage Hole Detection Algorithm in Sensor Networks. In Proceedings of the 2016 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data, Chengdu, China, 15–18 December 2016; pp. 199–204. [Google Scholar]
- Li, J.L.; Chang, S.; Fu, X.M.; Zhang, L.; Su, Y.; Jin, Z. A Coalitional Formation Game for Physical Layer Security of Cooperative Compressive Sensing Multi-Relay Networks. Sensors 2018, 18, 2942. [Google Scholar] [CrossRef] [PubMed]
- Mukherjee, A. Physical-Layer Security in the Internet of Things: Sensing and Communication Confidentiality under Resource Constraints. Proc. IEEE 2015, 103, 1747–1761. [Google Scholar] [CrossRef]
- Albashier, M.A.M.; Abdaziz, A.; Ghani, H.A. Performance analysis of physical layer security over different error correcting codes in wireless sensor networks. In Proceedings of the 2017 20th International Symposium on Wireless Personal Multimedia Communications (WPMC), Bali, Indonesia, 17–20 December 2017; pp. 191–195. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J. Physical-Layer Security: From Information Theory to Security Engineering; Cambridge University Press: Cambridge, UK, 2011; ISBN 9780521516501. [Google Scholar]
- Mukherjee, A.; Fakoorian, S.A.A.; Huang, J. Principles of Physical Layer Security in Multiuser Wireless Networks: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 1550–1573. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J.; Rodrigues, M.R.D. Wireless Information-Theoretic Security. IEEE Trans. Inf. Theory 2008, 54, 2515–2534. [Google Scholar] [CrossRef]
- Zou, Y.L.; Wang, X.B.; Shen, W.M. Optimal relay selection for physical-layer security in cooperative wireless networks. IEEE J. Sel. Areas Commun. 2013, 31, 2099–2111. [Google Scholar] [CrossRef]
- Park, K.H.; Wang, T.; Alouini, M.S. On the Jamming Power Allocation for Secure Amplify-and-Forward Relaying via Cooperative Jamming. IEEE J. Sel. Areas Commun. 2013, 31, 1741–1750. [Google Scholar] [CrossRef]
- Krikidis, I.; Thompson, J.; Mclaughlin, S. Relay selection for secure cooperative networks with jamming. IEEE Trans. Wirel. Commun. 2009, 8, 5003–5011. [Google Scholar] [CrossRef]
- Chen, J.; Zhang, R.; Song, L. Joint relay and jammer selection for secure two-way relay networks. Proc. IEEE Trans. Inf. Forensics Secur. 2012, 7, 310–320. [Google Scholar] [CrossRef]
- Zhang, H.J.; Xing, H.; Cheng, J.L. Secure Resource Allocation for OFDMA Two-Way Relay Wireless Sensor Networks without and with Cooperative Jamming. IEEE Trans. Ind. Inform. 2016, 12, 1714–1725. [Google Scholar] [CrossRef]
- Xu, Q.; Ren, P.Y.; Song, H.B. Security Enhancement for IoT Communications Exposed to Eavesdroppers with Uncertain Locations. IEEE Access 2016, 4, 2840–2853. [Google Scholar] [CrossRef]
- Zhang, Y.Y.; Shen, Y.L.; Wang, H. On Secure Wireless Communications for IoT under Eavesdropper Collusion. IEEE Trans. Autom. Sci. Eng. 2016, 13, 1281–1293. [Google Scholar] [CrossRef]
- Islam, S.N.; Mahmud, M.A. Secured Communication among IoT Devices in the Presence of Cellular Interference. In Proceedings of the 2017 IEEE 85th Vehicular Technology Conference (VTC Spring), Sydney, Australia, 4–7 June 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Ying, L.; Liang, L.; Alexandropoulos, G.C. Securing Relay Networks with Artificial Noise: An Error Performance Based Approach. Entropy 2017, 19, 384. [Google Scholar]
- Jeong, C.; Kim, I.; Kim, D.I. Joint Secure Beamforming Design at the Source and the Relay for an Amplify-and-Forward MIMO Untrusted Relay System. IEEE Trans. Signal Process. 2012, 60, 310–325. [Google Scholar] [CrossRef]
- Khandaker, M.R.A.; Rong, Y. Interference MIMO Relay Channel: Joint Power Control and Transceiver-Relay Beamforming. IEEE Trans. Signal Process. 2012, 60, 6509–6518. [Google Scholar] [CrossRef]
- Kong, Z.M.; Yang, S.S.; Wu, F.L. Iterative Distributed Minimum Total MSE Approach for Secure Communications in MIMO Interference Channels. IEEE Trans. Inf. Forensics Secur. 2016, 11, 594–608. [Google Scholar] [CrossRef]
- Badra, N.; Yang, J.X.; Psaromiligkos, I.; Champagne, B. Robust and secure beamformer design for MIMO relaying with imperfect eavesdropper CSI. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), Philadelphia, PA, USA, 17–19 October 2016; pp. 442–449. [Google Scholar] [CrossRef]
- Alexandropoulos, G.C.; Peppas, K.P. Secrecy Outage Analysis Over Correlated Composite Nakagami-m/Gamma Fading Channels. IEEE Commun. Lett. 2018, 22, 77–80. [Google Scholar] [CrossRef]
- Alexandropoulos, G.C.; Papadias, C.B. A reconfigurable distributed algorithm for K-user MIMO interference networks. In Proceedings of the 2013 IEEE International Conference on Communications (ICC), Budapest, Hungary, 9–13 June 2013; pp. 3063–3067. [Google Scholar] [CrossRef]
- Shi, Q.; Razaviyayn, M.; Luo, Z. An Iteratively Weighted MMSE Approach to Distributed Sum-Utility Maximization for a MIMO Interfering Broadcast Channel. IEEE Trans. Signal Process. 2011, 59, 4331–4340. [Google Scholar] [CrossRef]
- Alexandropoulos, G.C.; Ferrand, P.; Papadias, C.B. On the Robustness of Coordinated Beamforming to Uncoordinated Interference and CSI Uncertainty. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Alexandropoulos, G.C.; Barousis, V.I.; Papadias, C.B. Precoding for multiuser MIMO systems with single-fed parasitic antenna arrays. In Proceedings of the 2014 IEEE Global Communications Conference (GLOBECOM), Austin, TX, USA, 8–12 December 2014; pp. 3897–3902. [Google Scholar] [CrossRef]
- Xu, D.; Ren, P.; Ritcey, J.A. Optimal Grassmann Manifold Eavesdropping: A Huge Security Disaster for M-1-2 Wiretap Channels. In Proceedings of the 2017 IEEE Global Communications Conference (GLOBECOM), Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Xu, Z.Y.; Zhong, J.; Chen, G.J. Novel joint secure resource allocation optimization for full-duplex relay networks with cooperative jamming. In Proceedings of the 2016 IEEE 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Valencia, Spain, 4–8 September 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Yang, S.S.; Hanzo, L. Fifty Years of MIMO Detection: The Road to Large-Scale MIMOs. IEEE Commun. Surv. Tutor. 2015, 17, 1941–1988. [Google Scholar] [CrossRef]
- Horn, R.A.; Johnson, C.R. Topics in Matrix Analysis, 1st ed.; Cambridge University Press: Cambridge, UK, 1994. [Google Scholar]
- Boyd, S.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]
- Grant, M.; Boyd, S. Cvx: MATLAB Software for Disciplined Convex Programming (Webpage and Software). Available online: http://cvxr.com/cvx (accessed on 1 April 2010).
- Fang, H.; Xu, L. Coordinated Multiple-Relays Based Physical-Layer Security Improvement: A Single-Leader Multiple-Followers Stackelberg Game Scheme. IEEE Trans. Inf. Forensics Secur. 2018, 13, 197–209. [Google Scholar] [CrossRef]
- Al-jamali, M.; Al-nahari, A.; AlKhawlani, M.M. Relay selection scheme for improving the physical layer security in cognitive radio networks. In Proceedings of the 2015 23nd Signal Processing and Communications Applications Conference (SIU), Malatya, Turkey, 16–19 May 2015; pp. 495–498. [Google Scholar] [CrossRef]
- Shen, H.; Li, B.; Tao, M. MSE-Based Transceiver Designs for the MIMO Interference Channel. IEEE Trans. Wirel. Commun. 2010, 9, 3480–3489. [Google Scholar] [CrossRef]
- Zheng, C.; Kanapathippillai, C.; Ding, Z.G. Robust outage secrecy rate optimizations for a MIMO secrecy channel. IEEE Wirel. Commun. Lett. 2015, 4, 86–89. [Google Scholar] [CrossRef]
| Steps | Specific Progress |
|---|---|
| Step 1 | Set , and initialize the and satisfying power constrains (11) and (12). |
| Step 2 | Calculate and with and obtained from previous iteration. |
| Step 3 | Update by solving the problem (25) with , and . |
| Step 4 | Update by solving the problem (31) with , and then calculate . |
| Step 5 | If , then end; otherwise set , then go to step 2. |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kong, Z.; Wang, D.; Li, Y.; Wang, C. Robust Iterative Distributed Minimum Total MSE Algorithm for Secure Communications in the Internet of Things Using Relays. Sensors 2018, 18, 3914. https://doi.org/10.3390/s18113914
Kong Z, Wang D, Li Y, Wang C. Robust Iterative Distributed Minimum Total MSE Algorithm for Secure Communications in the Internet of Things Using Relays. Sensors. 2018; 18(11):3914. https://doi.org/10.3390/s18113914
Chicago/Turabian StyleKong, Zhengmin, Die Wang, Yunjuan Li, and Chao Wang. 2018. "Robust Iterative Distributed Minimum Total MSE Algorithm for Secure Communications in the Internet of Things Using Relays" Sensors 18, no. 11: 3914. https://doi.org/10.3390/s18113914
APA StyleKong, Z., Wang, D., Li, Y., & Wang, C. (2018). Robust Iterative Distributed Minimum Total MSE Algorithm for Secure Communications in the Internet of Things Using Relays. Sensors, 18(11), 3914. https://doi.org/10.3390/s18113914






