PSPS: A Step toward Tamper Resistance against Physical Computer Intrusion
Abstract
:1. Introduction
1.1. Problem Statement
1.2. Research Contribution
1.3. Organization
2. Background
2.1. Computer Security
2.2. Vulnerabilities
2.3. Computer Protection
2.4. Hardware Protection Mechanisms
2.5. Intrusion Detection System
- (1)
- Network intrusion detection systems (NIDS);
- (2)
- Host-based intrusion detection systems (HIDS),
2.6. Network-Based Intrusion Detection System
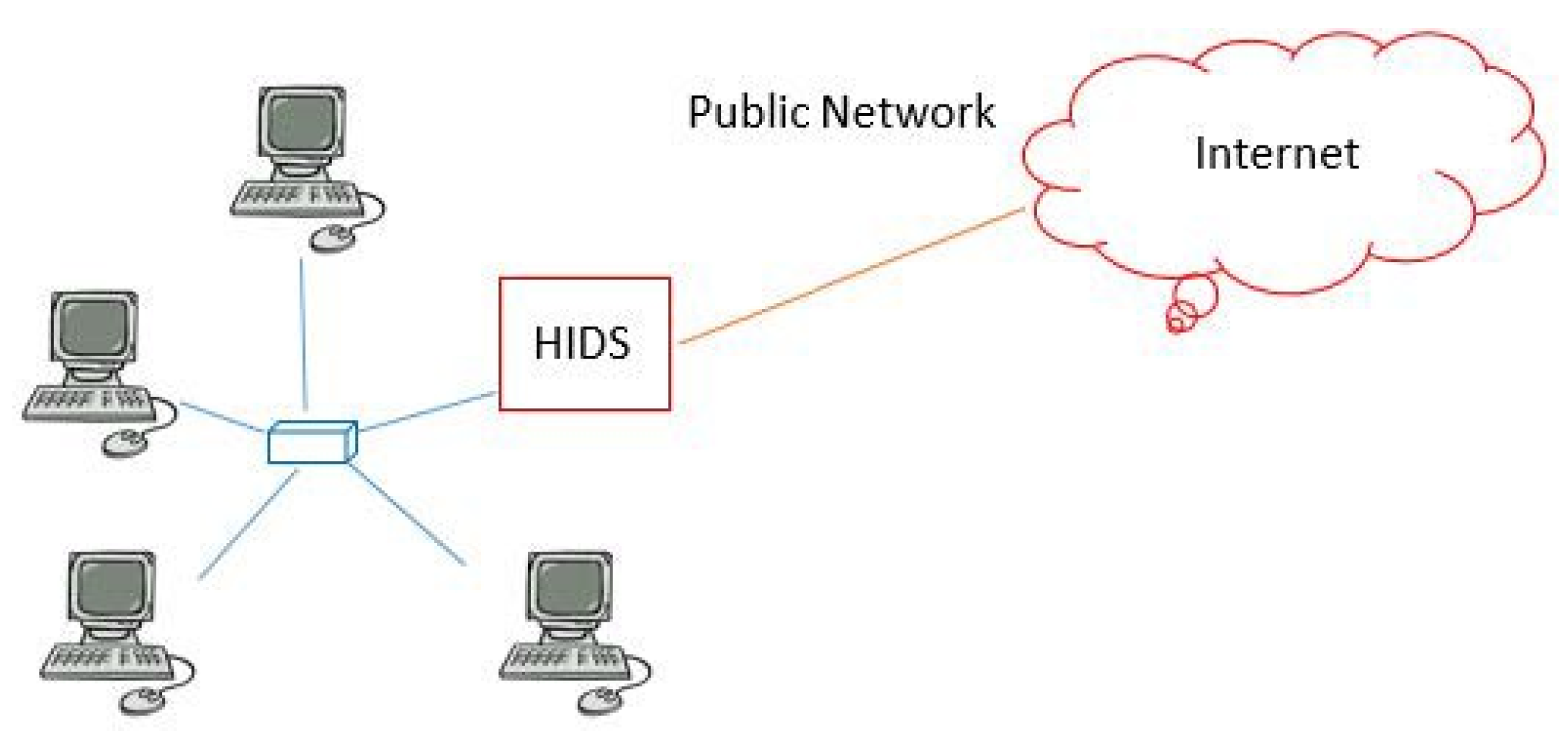
2.7. Host-Based Intrusion Detection System
- (1)
- Confirms whether the hacker has successfully intruded;
- (2)
- Monitors the activity of a specific host system;
- (3)
- Detects malicious activity in real time;
- (4)
- Does not require additional hardware equipment.
- (1)
- Low flexibility: All hosts may be installed with different operating platforms, and each operating system has different audit log files, so various HIDS must be installed for different hosts.
- (2)
- Restricted monitoring and scanning: HIDS can only see the network packet information received through the host.
- (3)
- Additional system resources: System resources of the monitored host are consumed during monitoring, which restricts performance of the host itself.
2.8. Intrusion Prevention System
2.9. Physical Security
3. Related Work
3.1. Snort
3.2. OSSEC
3.3. Intrusion Prevention System Design
4. Methodology
4.1. Goal of the System
4.2. State Diagram
4.2.1. Initial State
4.2.2. Operating State
4.2.3. Locked State
4.2.4. Maintenance State
5. Implementation
5.1. Development Environment
- (1)
- Visual C++ 2019;
- (2)
- Java 1.8.0;
- (3)
- HTML, CSS, JavaScript.
- (1)
- Microsoft Visual Studio Community 2019;
- (2)
- Eclipse IDE for Enterprise Java Developers 2020-03;
- (3)
- MySQL Server 8.0;
- (4)
- Connector ODBC 8.0;
- (5)
- Apache Tomcat 8.5;
- (6)
- Hei-diSQL 11.0;
- (7)
- FileZilla Server;
- (8)
- SyncBack.
5.2. Important Basic Functions
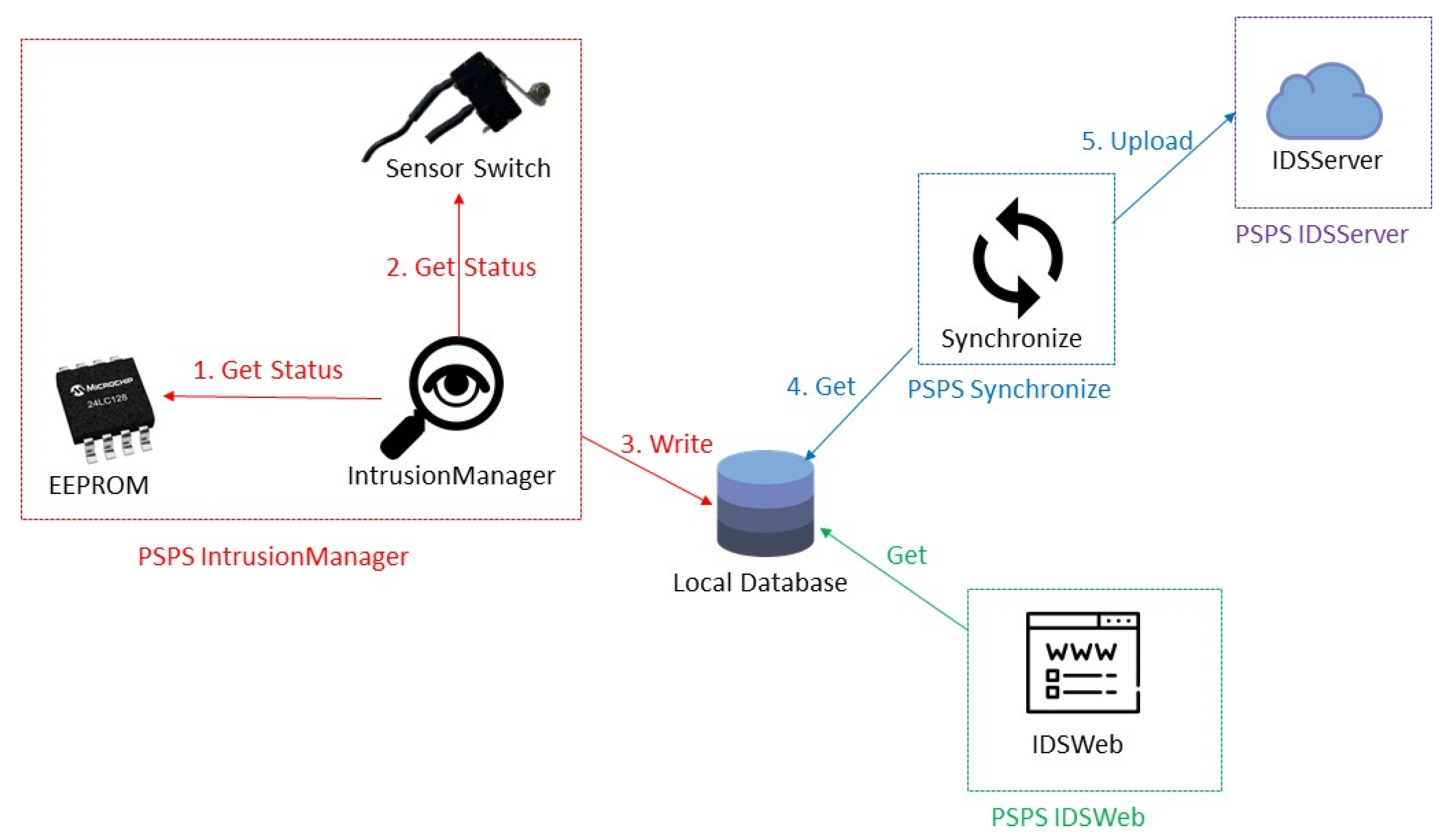
5.3. PSPS IntrusionManager
5.4. PSPS Defense
5.5. PSPS Synchronize
5.6. PSPS RecoveryManager
5.7. PSPS IDSWeb
5.8. PSPS IDSServer
6. Experimental Results
6.1. Purpose
6.2. Test Case 1
6.3. Test Case 2
6.4. BitLocker Protection
6.5. Unlock Process
6.6. PSPS IDSWeb Process
6.7. Intrusion Alert
6.8. Comparison
7. Conclusions
7.1. Discussion
7.2. Future Work
- (1)
- Build a website for PSPS IDSServer to monitor several systems;
- (2)
- Encrypt the Ini file to enhance security;
- (3)
- Use a smart card to encrypt and decrypt the password in PSPS RecoveryManager;
- (4)
- Apply this system to IoT devices;
- (5)
- Provide more protection for the EEPROM and sensor switches.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
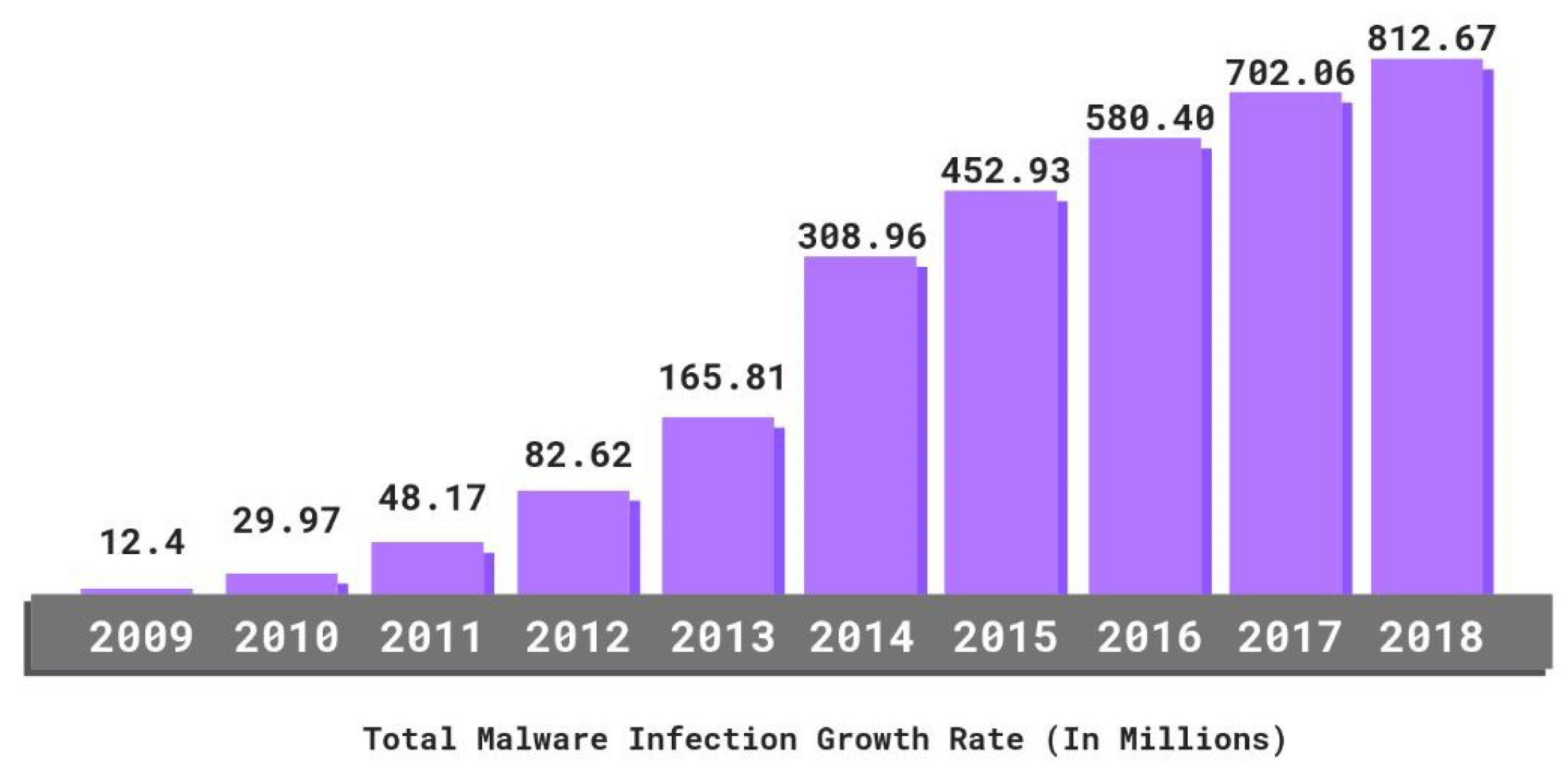
- The Ultimate List of Cyber Security Statistics for 2019. Available online: https://purplesec.us/resources/cyber-security-statistics/ (accessed on 21 December 2021).
- Security Onion. Available online: https://securityonion.net/ (accessed on 21 December 2021).
- Suricata. Available online: https://suricata-ids.org/ (accessed on 21 December 2021).
- Snort. Available online: https://www.snort.org/ (accessed on 21 December 2021).
- Ossec. Available online: https://www.ossec.net/ (accessed on 21 December 2021).
- Sabir, U.; Azam, F.; Haq, S.U.; Anwar, M.W.; Butt, W.H.; Amjad, A. A Model Driven Reverse Engineering Framework for Generating High Level UML Models From Java Source Code. IEEE Access 2019, 7, 158931–158950. [Google Scholar] [CrossRef]
- Reznik, L. Computer Security with Artificial Intelligence, Machine Learning, and Data Science Combination. In Intelligent Security Systems: How Artificial Intelligence, Machine Learning and Data Science Work For and Against Computer Security; IEEE: Piscataway, NJ, USA, 2022; pp. 1–56. [Google Scholar] [CrossRef]
- Common Vulnerabilities and Exposures. Available online: https://cve.mitre.org/ (accessed on 21 December 2021).
- Top 5 Computer Security Vulnerabilities. Available online: https://www.compuquip.com/blog/computer-security-vulnerabilities (accessed on 21 December 2021).
- Edgar, W. Internet of Things Security: Fundamentals, Techniques and Applications; River Publishers: Aalborg, Denmark, 2018; pp. 129–139. [Google Scholar]
- Borkar, A.; Donode, A.; Kumari, A. A survey on Intrusion Detection System (IDS) and Internal Intrusion Detection and protection system (IIDPS). In Proceedings of the 2017 International Conference on Inventive Computing and Informatics (ICICI), Coimbatore, India, 23–24 November 2017; pp. 949–953. [Google Scholar] [CrossRef]
- Xu, Y.; Ren, J.; Wang, G.; Zhang, C.; Yang, J.; Zhang, Y. A Blockchain-Based Nonrepudiation Network Computing Service Scheme for Industrial IoT. IEEE Trans. Ind. Inform. 2019, 15, 3632–3641. [Google Scholar] [CrossRef]
- Ahmed, M.; Pal, R.; Hossain, M.M.; Bikas, M.A.N.; Hasan, M.K. NIDS: A Network Based Approach to Intrusion Detection and Prevention. In Proceedings of the 2009 International Association of Computer Science and Information Technology—Spring Conference, Singapore, 17–20 April 2009; pp. 141–144. [Google Scholar] [CrossRef]
- Maske, S.A.; Parvat, T.J. Advanced anomaly intrusion detection technique for host based system using system call patterns. In Proceedings of the 2016 International Conference on Inventive Computation Technologies (ICICT), Coimbatore, India, 26–27 August 2016; pp. 1–4. [Google Scholar] [CrossRef]
- Al-Hamami, A.H.; Al-Saadoon, G.M.W. Development of a network-based: Intrusion Prevention System using a Data Mining approach. In Proceedings of the 2013 Science and Information Conference, London, UK, 7–9 October 2013; pp. 641–644. [Google Scholar]
- Gaddam, R.; Nandhini, M. An analysis of various snort based techniques to detect and prevent intrusions in networks proposal with code refactoring snort tool in Kali Linux envi- ronment. In Proceedings of the 2017 International Conference on Inventive Communication and Computational Technologies (ICICCT), Coimbatore, India, 10–11 March 2017; pp. 10–15. [Google Scholar] [CrossRef]
- Ajay Kumara, M.A.; Jaidhar, C.D. Hypervisor and virtual machine dependent Intrusion Detection and Prevention System for virtualized cloud environment. In Proceedings of the 2015 1st International Conference on Telematics and Future Generation Networks (TAFGEN), Kuala Lumpur, Malaysia, 26–28 May 2015; pp. 28–33. [Google Scholar] [CrossRef]
- Zhang, W.; Dong, M.; Ota, K.; Li, J.; Yang, W.; Wu, J. A Big Data Management Architecture for Standardized IoT Based on Smart Scalable SNMP. In Proceedings of the ICC 2020–2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–7. [Google Scholar] [CrossRef]
- Advantech DPX-S1435 High Performance Intel® Multi-Screen Gaming Platform. Available online: https://bkaii.com.vn/san-pham/advantech/dpx-s1435-high-performance-intel-multi-screen-gaming-platform (accessed on 21 December 2021).
- Meng, X.; Yang, S.; Chen, Z.; Lu, W.; Zhang, Y.; Huang, J.; Li, H.; Su, W.; Li, S. Low power eeprom designed for sensor interface circuit. In Proceedings of the 2011 IEEE International Conference of Electron Devices and Solid-State Circuits, Tianjin, China, 17–18 November 2011; pp. 1–2. [Google Scholar] [CrossRef]
- Smsto Api. Available online: https://sms.to/sms-api (accessed on 21 December 2021).
- Javamail Api. Available online: https://javaee.github.io/javamail/ (accessed on 21 December 2021).
- Syncback-Free. Available online: https://www.2brightsparks.com/download-syncbackfree.html (accessed on 21 December 2021).


























| Rank | Vulnerabilities |
|---|---|
| 1 | Hidden Backdoor Programs |
| 2 | Superuser or Administration Account Privileges |
| 3 | Automated Running of Scripts without Malware/Virus Checks |
| 4 | Unknown Security Bugs in Software or Programming Interfaces |
| 5 | Unencrypted Data on the Network |
| IDS | PSPS | OSSEC | SNORT |
|---|---|---|---|
| Placement | Host | Host | Network |
| Monitoring | Computer chassis | System logs | Network packets |
| Alerts | Web/SMS/Email/Logs | Email/Logs | Logs |
| IPS | V | X | V |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lu, M.-C.; Huang, Q.-X.; Chiu, M.-Y.; Tsai, Y.-C.; Sun, H.-M. PSPS: A Step toward Tamper Resistance against Physical Computer Intrusion. Sensors 2022, 22, 1882. https://doi.org/10.3390/s22051882
Lu M-C, Huang Q-X, Chiu M-Y, Tsai Y-C, Sun H-M. PSPS: A Step toward Tamper Resistance against Physical Computer Intrusion. Sensors. 2022; 22(5):1882. https://doi.org/10.3390/s22051882
Chicago/Turabian StyleLu, Ming-Chang, Qi-Xian Huang, Min-Yi Chiu, Yuan-Chia Tsai, and Hung-Min Sun. 2022. "PSPS: A Step toward Tamper Resistance against Physical Computer Intrusion" Sensors 22, no. 5: 1882. https://doi.org/10.3390/s22051882






