A Systematic Review on Machine Learning and Deep Learning Models for Electronic Information Security in Mobile Networks
Abstract
:1. Introduction
1.1. Contribution of This Survey
- We provide a comprehensive study on the various machine learning and deep learning models used for electronic information security in mobile networks. A brief explanation of several machine learning and deep learning methodologies is included.
- A concise review of cyberattacks as well as an application-oriented analysis of their datasets is given.
- We highlight the current open challenges and future research possibilities in the fields of mobile networks, electronic data security, and cyber threats for aspiring researchers and enthusiasts to investigate.
1.2. Survey Methodology
1.2.1. Search Strategy and Literature Sources
1.2.2. Inclusion Criteria
1.2.3. Elimination Criteria
1.2.4. Results
1.3. Structure of this Survey
2. Machine Learning and Deep Learning Models Used in Electronic Information Security Applications
2.1. The Evolution and Overview of Machine Learning and Deep Learning Models
2.2. Machine Learning Techniques
2.2.1. Artificial Neural Network
2.2.2. Naïve Bayes
2.2.3. Decision Tree
2.2.4. K-Nearest Neighbour
- It does not require any assumptions about the shape or distribution of input data.
- It does not require any pre-processing or transformation of input data before assigning them to clusters, making it computationally effective.
- It does not require any parameter tuning and can be used for both dense and sparse sets of data.
2.2.5. K-Means Clustering
2.2.6. Random Forest
2.2.7. Support Vector Machine
2.2.8. Ensemble Models
2.2.9. Machine Learning Models for Electronic Information Security
2.3. Deep Learning Models
2.3.1. Recurrent Neural Networks
2.3.2. Deep Autoencoder
2.3.3. Long Short-Term Memory
2.3.4. Deep Neural Network
2.3.5. Deep Belief Network
2.3.6. Deep Convolutional Neural Network
2.3.7. Deep Generative Models
2.3.8. Deep Boltzmann Machine
2.3.9. Deep Reinforcement Learning
2.3.10. Extreme Learning Machine
2.3.11. Deep Learning Models for Electronic Information Security
| Reference | Security-Category | Deep Learning Models Used | Key Contribution | Limitations |
|---|---|---|---|---|
| [95] | Malware Detection | Deep Convolutional Neural Network (DCNN) |
|
|
| [96] | Intrusion Detection System (IDS) | Artificial Neural Network (ANN), Stacked Auto Encoder (SAE) |
|
|
| [97] | Network Traffic Identification | Stacked autoencoder and one-dimensional convolution neural network (CNN) |
|
|
| [98] | Spam Email Detection | Bidirectional Encoder Representations from Transformers (BERT) |
|
|
| [78] | Intrusion Detection (5G) | RBM; RNN |
|
|
| [99] | False Data Injection | RBM |
|
|
| [100] | Keystroke Verification | RNN |
|
|
| [101] | Border Gateway Protocol Anomaly Detection | RNN |
|
|
| [102] | DGA | CNN RNN |
|
|
| [103] | Insider Threat | DFNN RNN CNN GNN |
|
|
3. Electronic Information Security, Cyber-Attacks and Their Defences
3.1. Cyber-Attacks
3.2. Cyber-Attack Defences
3.3. Cyber-Attack Datasets
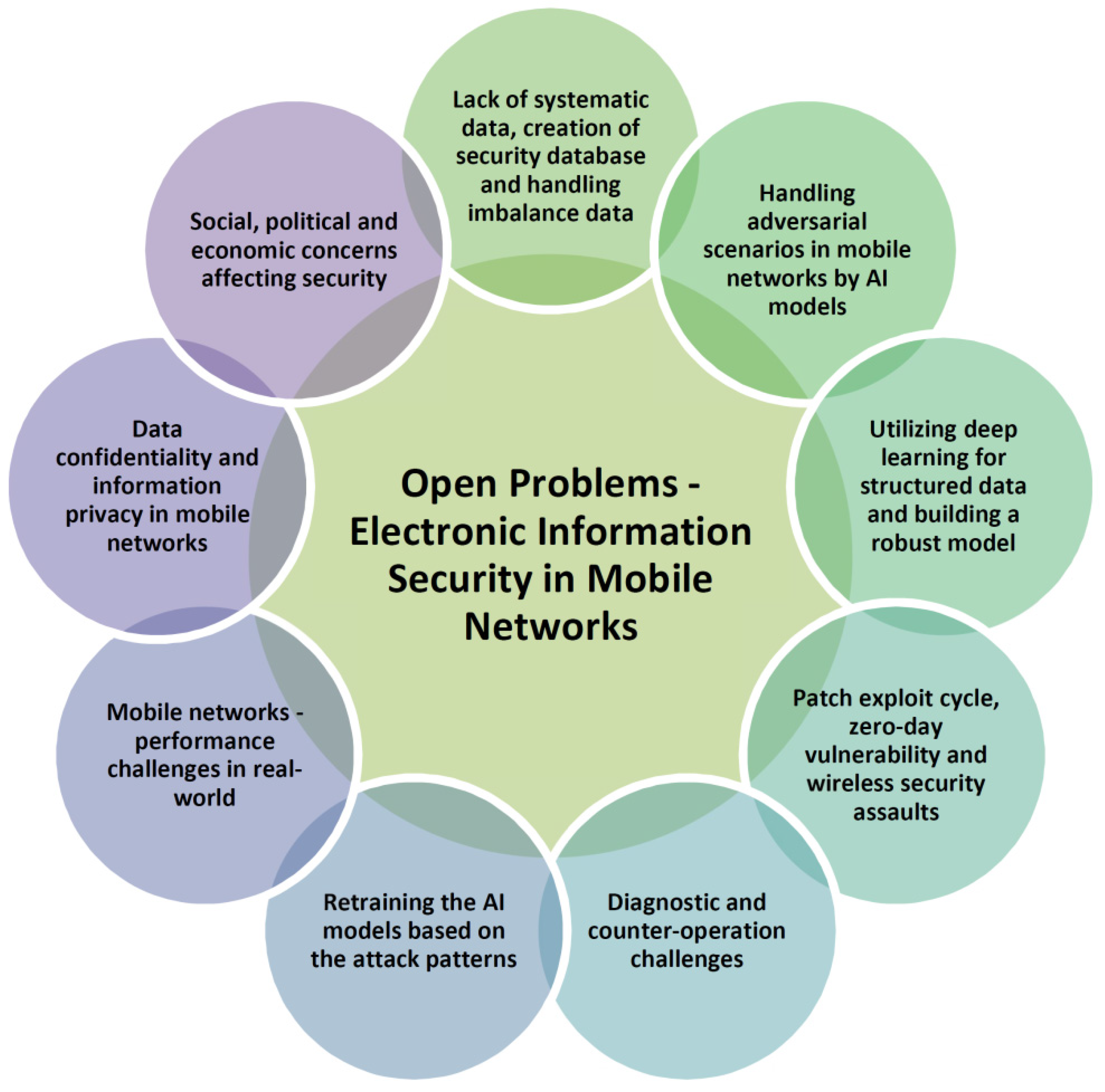
4. Open Problems-Electronic Information Security in Mobile Networks
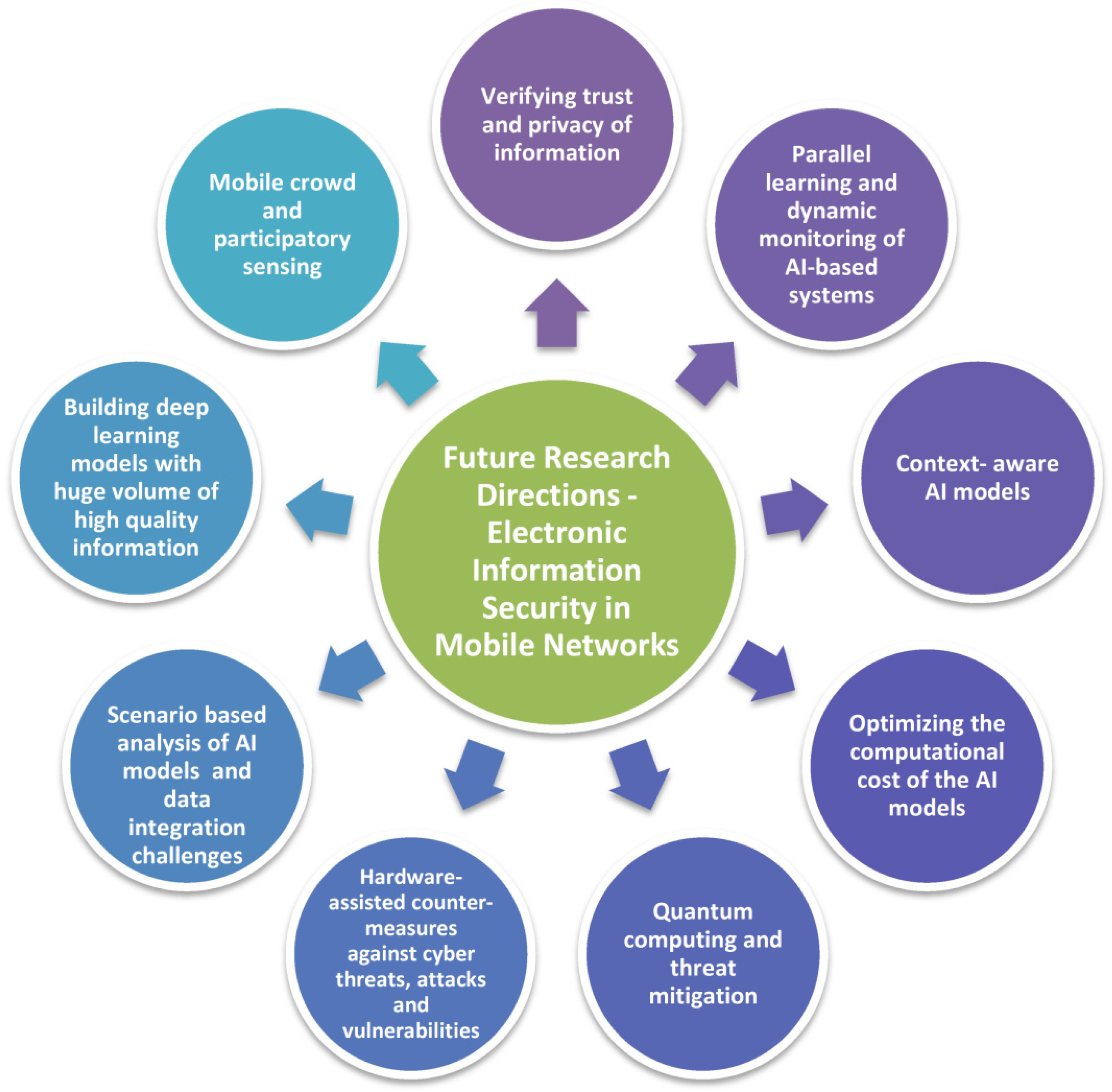
5. Future Directions—Electronic Information Security in Mobile Networks
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| Acronym | Definition |
|---|---|
| 5G | 5th Generation |
| AE | Autoencoder |
| AI | Artificial Intelligence |
| ANN | Artificial Neural Network |
| BLSTM-RNN | Bidirectional LSTM RNN |
| BM | Boltzmann Machine |
| BP | Back-Propagation |
| CNN | Convolutional Neural Network |
| CPPS DBM | Cyber-Physical Power System Deep Boltzmann machine |
| DBN | Deep Belief Network |
| DCNN | Deep Convolutional Neural Network |
| DDoS | Distributed Denial of Service |
| DFNN | Deep Feedforward Neural Network |
| DL | Deep Learning |
| DOS | Denial of Service |
| DRL | Deep Reinforcement Learning |
| DT | Decision Tree |
| ELM | Extreme Learning Machine |
| GA | Genetic Algorithm |
| GNN | Graph Neural Network |
| GRA | Grey Relational Analysis |
| GRU | Gated Recurrent Unit |
| ICMP | Internet Control Message Protocol |
| IEEE | Institute of Electrical and Electronics Engineers |
| IET | Institution of Engineering and Technology |
| IDS | Intrusion Detection System |
| IoT | Internet of Things |
| IP | Internet Protocol |
| IS | Information Security |
| IT | Information Technology |
| KNN | K-nearest Neighbour |
| LR | Logistic Regression |
| LSTM | Long Short-Term Memory |
| LTE | Long Term Evolution |
| MIB | Management Information Base |
| ML | Machine Learning |
| MLP | Multilayer Perceptron |
| NB | Naive Bayesian |
| NIDS | Network Intrusion Detection System |
| NLP | Natural Language Processing |
| NN | Neural Networks |
| NoC | Network-on-Chip |
| OCSVM | One Class Support Vector Machine |
| PCA | Principal Component Analysis |
| PHP | Hypertext Pre-processor |
| PLS | Partial Least Squares |
| PRISMA | Preferred Reporting Items for Systematic Reviews and Meta-Analyses |
| PSO | Particle Swarm Optimization |
| RBF | Radial Basis Function |
| RBM | Restricted Boltzmann Machine |
| RF | Reinforcement Learning |
| RL | Reinforcement Learning |
| RNN | Recurrent Neural Network |
| SDN | Software Defined Networking |
| SE | Social Engineering |
| SGD | Stochastic Gradient Descent |
| SLFN | Single Hidden Layer Feedforward Neural Network |
| SMS | Short Message Service |
| SNMP | Simple Network Management Protocol |
| SQL | Structured Query Language |
| SVM | Support Vector Machines |
| TAN | Transaction Authentication Numbers |
| TCP | Transmission Control Protocol |
| TFIDF | Term Frequency Inverse Document Frequency |
| TPR | True Positive Rate |
| UAV | Unmanned Aerial Vehicle |
| UDP | User Datagram Protocol |
| WiNoC | Wireless Network-on-Chip |
| WSN | Wireless Sensor Network |
References
- Zeadally, S.; Adi, E.; Baig, Z.; Khan, I.A. Harnessing Artificial Intelligence Capabilities to Improve Cybersecurity. IEEE Access 2020, 8, 23817–23837. [Google Scholar] [CrossRef]
- Kong, L.-J. An improved information-security risk assessment algorithm for a hybrid model. Int. J. Adv. Comput. Technol. 2013, 5, 2. [Google Scholar]
- Suo, H.; Liu, Z.; Wan, J.; Zhou, K. Security and privacy in mobile cloud computing. In Proceedings of the 9th International Wireless Communications and Mobile Computing Conference (IWCMC), Sardinia, Italy, 1–5 July 2013; pp. 655–659. [Google Scholar] [CrossRef]
- Chamola, V.; Jolfaei, A.; Chanana, V.; Parashari, P.; Hassija, V. Information security in the post quantum era for 5G and beyond networks: Threats to existing cryptography, and post-quantum cryptography. Comput. Commun. 2021, 176, 99–118. [Google Scholar] [CrossRef]
- Gan, X.-S.; Duanmu, J.-S.; Wang, J.-F.; Cong, W. Anomaly intrusion detection based on PLS feature extraction and core vector machine. Knowl.-Based Syst. 2013, 40, 1–6. [Google Scholar] [CrossRef]
- Narudin, F.A.; Feizollah, A.; Anuar, N.B.; Gani, A. Evaluation of machine learning classifiers for mobile malware detection. Soft Comput. 2014, 20, 343–357. [Google Scholar] [CrossRef]
- Zhang, B.-Y.; Yin, J.-P.; Wang, S.-L.; Yan, X.-A. Research on virus detection technique based on ensemble neural network and SVM. Neurocomputing 2014, 137, 24–33. [Google Scholar] [CrossRef]
- Yang, K.; Zhang, K.; Ren, J.; Shen, X. Security and privacy in mobile crowdsourcing networks: Challenges and opportunities. IEEE Commun. Mag. 2015, 53, 75–81. [Google Scholar] [CrossRef]
- Deng, S.; Yue, N.; Fu, X.; Zhou, A. Security risk assessment of cyber physical power system based on rough set and gene expression programming. IEEE/CAA J. Autom. Sin. 2015, 2, 431–439. [Google Scholar] [CrossRef]
- Liu, X.; Lu, R.; Ma, J.; Chen, L.; Qin, B. Privacy-Preserving Patient-Centric Clinical Decision Support System on Naïve Bayesian Classification. IEEE J. Biomed. Health Inform. 2015, 20, 655–668. [Google Scholar] [CrossRef]
- Liyanage, M.; Abro, A.B.; Ylianttila, M.; Gurtov, A. Opportunities and Challenges of Software-Defined Mobile Networks in Network Security. IEEE Secur. Priv. 2016, 14, 34–44. [Google Scholar] [CrossRef]
- Aburomman, A.; Reaz, M.B.I. A novel SVM-kNN-PSO ensemble method for intrusion detection system. Appl. Soft Comput. 2016, 38, 360–372. [Google Scholar] [CrossRef]
- Chen, J.; Ma, H.; Zhao, D.; Liu, L. Correlated Differential Privacy Protection for Mobile Crowdsensing. IEEE Trans. Big Data 2021, 7, 784–795. [Google Scholar] [CrossRef]
- Jiang, C.; Zhang, H.; Ren, Y.; Han, Z.; Chen, K.-C.; Hanzo, L. Machine Learning Paradigms for Next-Generation Wireless Networks. IEEE Wirel. Commun. 2016, 24, 98–105. [Google Scholar] [CrossRef] [Green Version]
- Wang, W.; Zhu, M.; Zeng, X.; Ye, X.; Sheng, Y. Malware traffic classification using convolutional neural network for representation learning. In Proceedings of the International Conference on Information Networking (ICOIN), Da Nang, Vietnam, 11–13 January 2017; pp. 712–717. [Google Scholar] [CrossRef]
- Fadlullah, Z.M.; Tang, F.; Mao, B.; Kato, N.; Akashi, O.; Inoue, T.; Mizutani, K. State-of-the-Art Deep Learning: Evolving Machine Intelligence Toward Tomorrow’s Intelligent Network Traffic Control Systems. IEEE Commun. Surv. Tutor. 2017, 19, 2432–2455. [Google Scholar] [CrossRef]
- Shah, S.K.; Tariq, Z.; Lee, J.; Lee, Y. Event-Driven Deep Learning for Edge Intelligence (EDL-EI). Sensors 2021, 21, 6023. [Google Scholar] [CrossRef]
- Xiong, J.; Ma, R.; Chen, L.; Tian, Y.; Lin, L.; Jin, B. Achieving Incentive, Security, and Scalable Privacy Protection in Mobile Crowdsensing Services. Wirel. Commun. Mob. Comput. 2018, 2018, 1–12. [Google Scholar] [CrossRef] [Green Version]
- Zhang, Q.; Mozaffari, M.; Saad, W.; Bennis, M.; Debbah, M. Machine Learning for Predictive On-Demand Deployment of Uavs for Wireless Communications. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 10–12 December 2018; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Lin, X.; Li, J.; Wu, J.; Liang, H.; Yang, W. Making Knowledge Tradable in Edge-AI Enabled IoT: A Consortium Blockchain-Based Efficient and Incentive Approach. IEEE Trans. Ind. Inform. 2019, 15, 6367–6378. [Google Scholar] [CrossRef]
- Yasin, A.; Fatima, R.; Liu, L.; Yasin, A.; Wang, J. Contemplating social engineering studies and attack scenarios: A review study. Secur. Priv. 2019, 2, e73. [Google Scholar] [CrossRef] [Green Version]
- Chen, Z.; He, Q.; Liu, L.; Lan, D.; Chung, H.-M.; Mao, Z. An Artificial Intelligence Perspective on Mobile Edge Computing. In Proceedings of the IEEE International Conference on Smart Internet of Things (SmartIoT), Tianjin, China, 9–11 August 2019; pp. 100–106. [Google Scholar] [CrossRef]
- Li, B.; Fei, Z.; Zhang, Y. UAV Communications for 5G and Beyond: Recent Advances and Future Trends. IEEE Internet Things J. 2018, 6, 2241–2263. [Google Scholar] [CrossRef] [Green Version]
- Zhang, C.; Patras, P.; Haddadi, H. Deep Learning in Mobile and Wireless Networking: A Survey. IEEE Commun. Surv. Tutor. 2019, 21, 2224–2287. [Google Scholar] [CrossRef] [Green Version]
- Arivudainambi, D.; KA, V.K.; Visu, P. Malware traffic classification using principal component analysis and artificial neural network for extreme surveillance. Comput. Commun. 2019, 147, 50–57. [Google Scholar] [CrossRef]
- Serey, J.; Quezada, L.; Alfaro, M.; Fuertes, G.; Vargas, M.; Ternero, R.; Sabattin, J.; Duran, C.; Gutierrez, S. Artificial Intelligence Methodologies for Data Management. Symmetry 2021, 13, 2040. [Google Scholar] [CrossRef]
- Zhang, Y.; Kantarci, B. Invited Paper: AI-Based Security Design of Mobile Crowdsensing Systems: Review, Challenges and Case Studies. In Proceedings of the 2019 IEEE International Conference on Service-Oriented System Engineering (SOSE), San Francisco, CA, USA, 4–9 April 2019; pp. 17–1709. [Google Scholar] [CrossRef]
- Kulin, M.; Kazaz, T.; De Poorter, E.; Moerman, I. A Survey on Machine Learning-Based Performance Improvement of Wireless Networks: PHY, MAC and Network Layer. Electronics 2021, 10, 318. [Google Scholar] [CrossRef]
- Berman, D.S.; Buczak, A.L.; Chavis, J.S.; Corbett, C.L. A Survey of Deep Learning Methods for Cyber Security. Information 2019, 10, 122. [Google Scholar] [CrossRef] [Green Version]
- Ali, M.; Hu, Y.-F.; Luong, D.K.; Oguntala, G.; Li, J.-P.; Abdo, K. Adversarial Attacks on AI based Intrusion Detection System for Heterogeneous Wireless Communications Networks. In Proceedings of the 2020 AIAA/IEEE 39th Digital Avionics Systems Conference (DASC), San Antonio, TX, USA, 11–15 October 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Qiu, J.; Du, L.; Chen, Y.; Tian, Z.; Du, X.; Guizani, M. Artificial Intelligence Security in 5G Networks: Adversarial Examples for Estimating a Travel Time Task. IEEE Veh. Technol. Mag. 2020, 15, 95–100. [Google Scholar] [CrossRef]
- Kuzlu, M.; Fair, C.; Guler, O. Role of Artificial Intelligence in the Internet of Things (IoT) cybersecurity. Discov. Internet Things 2021, 1, 1–14. [Google Scholar] [CrossRef]
- Basit, A.; Zafar, M.; Liu, X.; Javed, A.R.; Jalil, Z.; Kifayat, K. A comprehensive survey of AI-enabled phishing attacks detection techniques. Telecommun. Syst. 2020, 76, 139–154. [Google Scholar] [CrossRef]
- Song, H.; Bai, J.; Yi, Y.; Wu, J.; Liu, L. Artificial Intelligence Enabled Internet of Things: Network Architecture and Spectrum Access. IEEE Comput. Intell. Mag. 2020, 15, 44–51. [Google Scholar] [CrossRef]
- Pan, Q.; Wu, J.; Li, J.; Yang, W.; Guan, Z. Blockchain and AI Empowered Trust-Information-Centric Network for Beyond 5G. IEEE Netw. 2020, 34, 38–45. [Google Scholar] [CrossRef]
- Tang, F.; Kawamoto, Y.; Kato, N.; Liu, J. Future Intelligent and Secure Vehicular Network Toward 6G: Machine-Learning Approaches. Proc. IEEE 2019, 108, 292–307. [Google Scholar] [CrossRef]
- Radanliev, P.; De Roure, D.; Walton, R.; Van Kleek, M.; Montalvo, R.M.; Maddox, L.; Santos, O.; Burnap, P.; Anthi, E. Artificial intelligence and machine learning in dynamic cyber risk analytics at the edge. SN Appl. Sci. 2020, 2, 1–8. [Google Scholar] [CrossRef]
- Tom, E.; Keane, P.A.; Blazes, M.; Pasquale, L.R.; Chiang, M.F.; Lee, A.Y.; Lee, C.S.; Force, A.A.A.I.T. Protecting Data Privacy in the Age of AI-Enabled Ophthalmology. Transl. Vis. Sci. Technol. 2020, 9, 36. [Google Scholar] [CrossRef] [PubMed]
- Dasgupta, D.; Akhtar, Z.; Sen, S. Machine learning in cybersecurity: A comprehensive survey. J. Déf. Model. Simul. Appl. Methodol. Technol. 2020, 19, 57–106. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Xu, M. A Survey on Machine Learning Techniques for Cyber Security in the Last Decade. IEEE Access 2020, 8, 222310–222354. [Google Scholar] [CrossRef]
- Drewek-Ossowicka, A.; Pietrołaj, M.; Rumiński, J. A survey of neural networks usage for intrusion detection systems. J. Ambient Intell. Humaniz. Comput. 2020, 12, 497–514. [Google Scholar] [CrossRef]
- Ahmad, Z.; Khan, A.S.; Shiang, C.W.; Abdullah, J.; Ahmad, F. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Trans. Emerg. Telecommun. Technol. 2020, 32, e4150. [Google Scholar] [CrossRef]
- Jaffry, S.; Hussain, R.; Gui, X.; Hasan, S.F. A Comprehensive Survey on Moving Networks. IEEE Commun. Surv. Tutor. 2020, 23, 110–136. [Google Scholar] [CrossRef]
- Sarker, I.H.; Kayes, A.S.M.; Badsha, S.; Alqahtani, H.; Watters, P.; Ng, A. Cybersecurity data science: An overview from machine learning perspective. J. Big Data 2020, 7, 1–29. [Google Scholar] [CrossRef]
- Zhang, Z.; Zhou, S. A decentralized strongly secure attribute-based encryption and authentication scheme for distributed Internet of Mobile Things. Comput. Netw. 2021, 201, 108553. [Google Scholar] [CrossRef]
- Trnka, M.; Abdelfattah, A.S.; Shrestha, A.; Coffey, M.; Cerny, T. Systematic Review of Authentication and Authorization Advancements for the Internet of Things. Sensors 2022, 22, 1361. [Google Scholar] [CrossRef]
- Yan, X.; Ma, M. A lightweight and secure handover authentication scheme for 5G network using neighbour base stations. J. Netw. Comput. Appl. 2021, 193, 103204. [Google Scholar] [CrossRef]
- Xiong, J.; Zhao, M.; Alam Bhuiyan, Z.; Chen, L.; Tian, Y. An AI-Enabled Three-Party Game Framework for Guaranteed Data Privacy in Mobile Edge Crowdsensing of IoT. IEEE Trans. Ind. Inform. 2019, 17, 922–933. [Google Scholar] [CrossRef]
- Otoum, S.; Al Ridhawi, I.; Mouftah, H.T. Preventing and Controlling Epidemics Through Blockchain-Assisted AI-Enabled Networks. IEEE Netw. 2021, 35, 34–41. [Google Scholar] [CrossRef]
- Bochie, K.; Gilbert, M.S.; Gantert, L.; Barbosa, M.S.; Medeiros, D.S.; Campista, M.E.M. A survey on deep learning for challenged networks: Applications and trends. J. Netw. Comput. Appl. 2021, 194, 103213. [Google Scholar] [CrossRef]
- Rabbani, M.; Wang, Y.; Khoshkangini, R.; Jelodar, H.; Zhao, R.; Ahmadi, S.B.B.; Ayobi, S. A Review on Machine Learning Approaches for Network Malicious Behavior Detection in Emerging Technologies. Entropy 2021, 23, 529. [Google Scholar] [CrossRef]
- Yavanoglu, O.; Aydos, M. A review on cyber security datasets for machine learning algorithms. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; pp. 2186–2193. [Google Scholar] [CrossRef]
- Apruzzese, G.; Colajanni, M.; Ferretti, L.; Guido, A.; Marchetti, M. On the Effectiveness of Machine and Deep Learning for Cyber Security. In Proceedings of the 2018 10th International Conference on Cyber Conflict (CyCon), Tallinn, Estonia, 29 May–1 June 2018. [Google Scholar] [CrossRef]
- Bhamare, D.; Salman, T.; Samaka, M.; Erbad, A.; Jain, R. Feasibility of Supervised Machine Learning for Cloud Security. In Proceedings of the 2016 International Conference on Information Science and Security (ICISS), Pattaya, Thailand, 19 December 2016; pp. 1–5. [Google Scholar] [CrossRef] [Green Version]
- Damopoulos, D.; Menesidou, S.A.; Kambourakis, G.; Papadaki, M.; Clarke, N.; Gritzalis, S. Evaluation of anomaly-based IDS for mobile devices using machine learning classifiers. Secur. Commun. Netw. 2011, 5, 3–14. [Google Scholar] [CrossRef]
- Saied, A.; Overill, R.E.; Radzik, T. Detection of known and unknown DDoS attacks using Artificial Neural Networks. Neurocomputing 2016, 172, 385–393. [Google Scholar] [CrossRef]
- Sinclair, C.; Pierce, L.; Matzner, S. An application of machine learning to network intrusion detection. In Proceedings of the 15th Annual Computer Security Applications Conference (ACSAC’99), Phoenix, AZ, USA, 6–10 December 1999. [Google Scholar] [CrossRef] [Green Version]
- Wu, Y.C.; Tseng, H.R.; Yang, W.; Jan, R.H. DDoS detection and traceback with decision tree and grey relational analysis. Int. J. Ad Hoc Ubiquitous Comput. 2011, 7, 121. [Google Scholar] [CrossRef] [Green Version]
- Do, V.T.; Engelstad, P.; Feng, B.; van Do, T. Detection of DNS Tunneling in Mobile Networks Using Machine Learning. In Proceedings of the International Conference on Information Science and Applications, Wuhan, China, 8–9 July 2017; pp. 221–230. [Google Scholar] [CrossRef] [Green Version]
- Belavagi, M.C.; Muniyal, B. Performance Evaluation of Supervised Machine Learning Algorithms for Intrusion Detection. Procedia Comput. Sci. 2016, 89, 117–123. [Google Scholar] [CrossRef] [Green Version]
- Rajagopal, S.; Kundapur, P.P.; Hareesha, K.S. A Stacking Ensemble for Network Intrusion Detection Using Heterogeneous Datasets. Secur. Commun. Netw. 2020, 2020, 4586875. [Google Scholar] [CrossRef] [Green Version]
- Abdullahi, M.; Baashar, Y.; Alhussian, H.; Alwadain, A.; Aziz, N.; Capretz, L.F.; Abdulkadir, S.J. Detecting Cybersecurity Attacks in Internet of Things Using Artificial Intelligence Methods: A Systematic Literature Review. Electronics 2022, 11, 198. [Google Scholar] [CrossRef]
- Nanda, S.; Zafari, F.; DeCusatis, C.; Wedaa, E.; Yang, B. Predicting network attack patterns in SDN using machine learning approach. In Proceedings of the 2016 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Palo Alto, CA, USA, 7–9 November 2016; pp. 167–172. [Google Scholar] [CrossRef]
- Shon, T.; Kim, Y.; Lee, C.; Moon, J. A machine learning framework for network anomaly detection using SVM and GA. In Proceedings of the Sixth Annual IEEE SMC Information Assurance Workshop, West Point, NY, USA, 15–17 June 2005. [Google Scholar] [CrossRef]
- Wang, P.; Lin, S.-C.; Luo, M. A Framework for QoS-aware Traffic Classification Using Semi-supervised Machine Learning in SDNs. In Proceedings of the 2016 IEEE International Conference on Services Computing (SCC), San Francisco, CA, USA, 27 June–2 July 2016; pp. 760–765. [Google Scholar] [CrossRef]
- Wang, J.; Hong, X.; Ren, R.R.; Li, T.H. A real-time intrusion detection system based on PSO-SVM. International Workshop on Information Security and Application. In Proceedings of the 2009 International Workshop on Information Security and Application (IWISA 2009), Wuhan, China, 23–24 May 2009. [Google Scholar]
- Bensalem, M.; Singh, S.K.; Jukan, A. On Detecting and Preventing Jamming Attacks with Machine Learning in Optical Networks. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Big Island, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Singhal, P. Malware Detection Module using Machine Learning Algorithms to Assist in Centralized Security in Enterprise Networks. Int. J. Netw. Secur. Its Appl. 2012, 4, 61–67. [Google Scholar] [CrossRef]
- Al Naymat, G.; Al Kasassbeh, M.; Al Harwari, E. Using machine learning methods for detecting network anomalies within SNMP-MIB dataset. Int. J. Wirel. Mob. Comput. 2018, 15, 67. [Google Scholar] [CrossRef]
- Yong, B.; Wei, W.; Li, K.; Shen, J.; Zhou, Q.; Wozniak, M.; Połap, D.; Damaševičius, R. Ensemble machine learning approaches for webshell detection in Internet of things environments. Trans. Emerg. Telecommun. Technol. 2020. [Google Scholar] [CrossRef]
- Vashist, A.; Keats, A.; Dinakarrao, S.M.P.; Ganguly, A. Securing a Wireless Network-on-Chip Against Jamming-Based Denial-of-Service and Eavesdropping Attacks. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2019, 27, 2781–2791. [Google Scholar] [CrossRef]
- Kang, J.; Xiong, Z.; Niyato, D.; Zou, Y.; Zhang, Y.; Guizani, M. Reliable Federated Learning for Mobile Networks. IEEE Wirel. Commun. 2020, 27, 72–80. [Google Scholar] [CrossRef] [Green Version]
- Luong, N.C.; Hoang, D.T.; Gong, S.; Niyato, D.; Wang, P.; Liang, Y.-C.; Kim, D.I. Applications of Deep Reinforcement Learning in Communications and Networking: A Survey. IEEE Commun. Surv. Tutor. 2019, 21, 3133–3174. [Google Scholar] [CrossRef] [Green Version]
- Rodriguez, E.; Otero, B.; Gutierrez, N.; Canal, R. A Survey of Deep Learning Techniques for Cybersecurity in Mobile Networks. IEEE Commun. Surv. Tutor. 2021, 23, 1920–1955. [Google Scholar] [CrossRef]
- Xiao, A.; Liu, J.; Li, Y.; Song, Q.; Ge, N. Two-phase rate adaptation strategy for improving real-time video QoE in mobile networks. China Commun. 2018, 15, 12–24. [Google Scholar] [CrossRef]
- Rahim, N.; Ahmad, J.; Muhammad, K.; Sangaiah, A.K.; Baik, S.W. Privacy-preserving image retrieval for mobile devices with deep features on the cloud. Comput. Commun. 2018, 127, 75–85. [Google Scholar] [CrossRef]
- Zhong, Y.; Yuan, Z.; Zhao, S.; Luo, X. A Wifi Positioning Method Based on Stack Auto Encoder. In Proceedings of the 2018 7th International Conference on Digital Home (ICDH), Guilin, China, 30 November–1 December 2018; pp. 286–293. [Google Scholar] [CrossRef]
- Maimo, L.F.; Gomez, A.L.P.; Clemente, F.J.G.; Gil Pérez, M.; Perez, G.M. A Self-Adaptive Deep Learning-Based System for Anomaly Detection in 5G Networks. IEEE Access 2018, 6, 7700–7712. [Google Scholar] [CrossRef]
- Wang, Q.; Yang, H.; Wang, Q.; Huang, W.; Deng, B. A deep learning based data forwarding algorithm in mobile social networks. Peer-to-Peer Netw. Appl. 2019, 12, 1638–1650. [Google Scholar] [CrossRef]
- Guo, L.; Wang, S.; Yin, J.; Wang, Y.; Yang, J.; Gui, G. Federated user activity analysis via network traffic and deep neural network in mobile wireless networks. Phys. Commun. 2021, 48, 101438. [Google Scholar] [CrossRef]
- Arya, G.; Bagwari, A.; Chauhan, D.S. Performance Analysis of Deep Learning-Based Routing Protocol for an Efficient Data Transmission in 5G WSN Communication. IEEE Access 2022, 10, 9340–9356. [Google Scholar] [CrossRef]
- Kasongo, S.M.; Sun, Y. A deep learning method with wrapper based feature extraction for wireless intrusion detection system. Comput. Secur. 2020, 92, 101752. [Google Scholar] [CrossRef]
- Ullah, F.; Naeem, H.; Jabbar, S.; Khalid, S.; Latif, M.A.; Al-Turjman, F.; Mostarda, L. Cyber Security Threats Detection in Internet of Things Using Deep Learning Approach. IEEE Access 2019, 7, 124379–124389. [Google Scholar] [CrossRef]
- Chandy, S.E.; Rasekh, A.; Barker, Z.A.; Shafiee, M.E. Cyberattack Detection Using Deep Generative Models with Variational Inference. J. Water Resour. Plan. Manag. 2019, 145, 04018093. [Google Scholar] [CrossRef] [Green Version]
- Kos, J.; Fischer, I.; Song, D. Adversarial Examples for Generative Models. In Proceedings of the 2018 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 21–23 May 2018; pp. 36–42. [Google Scholar] [CrossRef] [Green Version]
- Kim, D.; Ko, M.; Kim, S.; Moon, S.; Cheon, K.-Y.; Park, S.; Kim, Y.; Yoon, H.; Choi, Y.-H. Design and Implementation of Traffic Generation Model and Spectrum Requirement Calculator for Private 5G Network. IEEE Access 2022, 10, 15978–15993. [Google Scholar] [CrossRef]
- Alam, M.R.; Bennamoun, M.; Togneri, R.; Sohel, F. A Joint Deep Boltzmann Machine (jDBM) Model for Person Identification Using Mobile Phone Data. IEEE Trans. Multimed. 2016, 19, 317–326. [Google Scholar] [CrossRef]
- Wang, J.; Lu, S.; Wang, S.-H.; Zhang, Y.-D. A review on extreme learning machine. Multimed. Tools Appl. 2021, 1–50. [Google Scholar] [CrossRef]
- Huang, G.B.; Zhu, Q.Y.; Siew, C.K. Extreme learning machine: Theory and applications. Neurocomputing 2016, 70, 489–501. [Google Scholar]
- Leung, H.C.; Leung, C.S.; Wong, E.W.M. Fault and Noise Tolerance in the Incremental Extreme Learning Machine. IEEE Access 2019, 7, 155171–155183. [Google Scholar] [CrossRef]
- She, Q.; Hu, B.; Gan, H.; Fan, Y.; Nguyen, T.; Potter, T.; Zhang, Y. Safe Semi-Supervised Extreme Learning Machine for EEG Signal Classification. IEEE Access 2018, 6, 49399–49407. [Google Scholar] [CrossRef]
- Rathore, S.; Park, J.H. Semi-supervised learning based distributed attack detection framework for IoT. Appl. Soft Comput. 2018, 72, 79–89. [Google Scholar] [CrossRef]
- Alimi, O.A.; Ouahada, K.; Abu-Mahfouz, A.M.; Rimer, S.; Alimi, K.O.A. A Review of Research Works on Supervised Learning Algorithms for SCADA Intrusion Detection and Classification. Sustainability 2021, 13, 9597. [Google Scholar] [CrossRef]
- Ahmad, W.; Rasool, A.; Javed, A.R.; Baker, T.; Jalil, Z. Cyber Security in IoT-Based Cloud Computing: A Comprehensive Survey. Electronics 2022, 11, 16. [Google Scholar] [CrossRef]
- McLaughlin, N.; del Rincon, J.M.; Kang, B.; Yerima, S.; Miller, P.; Sezer, S.; Safaei, Y.; Trickel, E.; Zhao, Z.; Doupe, A.; et al. Deep android malware detection. In Proceedings of the 7th ACM on Conference on Data and Application Security and Privacy, Scottsdale, AZ, USA, 22–24 March 2017; pp. 301–308. [Google Scholar]
- Aminanto, M.E.; Kwangjo, K. Deep Learning-based Feature Selection for Intrusion Detection System in Transport Layer 1). In Proceedings of the Korea Institutes of Information Security and Cryptology Conference, Seoul, Korea, 30 November–2 December 2016. [Google Scholar]
- Lotfollahi, M.; Siavoshani, M.J.; Zade, R.S.H.; Saberian, M. Deep packet: A novel approach for encrypted traffic classification using deep learning. Soft Comput. 2019, 24, 1999–2012. [Google Scholar] [CrossRef] [Green Version]
- AbdulNabi, I.; Yaseen, Q. Spam Email Detection Using Deep Learning Techniques. Procedia Comput. Sci. 2021, 184, 853–858. [Google Scholar] [CrossRef]
- He, Y.; Mendis, G.J.; Wei, J. Real-Time Detection of False Data Injection Attacks in Smart Grid: A Deep Learning-Based Intelligent Mechanism. IEEE Trans. Smart Grid 2017, 8, 2505–2516. [Google Scholar] [CrossRef]
- Kobojek, P.; Saeed, K. Application of recurrent neural networks for user verification based on keystroke dynamics. J. Telecommun. Inf. Technol. 2016, 3, 80–90. [Google Scholar]
- Cheng, M.; Xu, Q.; Lv, J.; Liu, W.; Li, Q.; Wang, J. MS-LSTM: A multi-scale LSTM model for BGP anomaly detection. In Proceedings of the IEEE 24th International Conference Network Protocols (ICNP), Singapore, 8–11 November 2016; pp. 1–6. [Google Scholar]
- Mac, H.; Tran, D.; Tong, V.; Nguyen, L.G.; Tran, H.A. DGA Botnet Detection Using Supervised Learning Methods. In Proceedings of the 8th International Symposium on Information and Communication Technology, Nhatrang, Vietnam, 7–8 December 2017; pp. 211–218. [Google Scholar]
- Yuan, S.; Wu, X. Deep learning for insider threat detection: Review, challenges and opportunities. Comput. Secur. 2021, 104, 102221. [Google Scholar] [CrossRef]
- Hoque, N.; Bhattacharyya, D.K.; Kalita, J.K. FFSc: A novel measure for low-rate and high-rate DDoS attack detection using multivariate data analysis. Secur. Commun. Networks 2016, 9, 2032–2041. [Google Scholar] [CrossRef] [Green Version]
- Malik, R.; Alankar, B. Botnet and Botnet Detection Techniques. Int. J. Comput. Appl. 2019, 178, 8–11. [Google Scholar] [CrossRef]
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the Second IEEE Symposium on Computational Intelligence for Security and Defence Applications, Ottawa, ON, Canada, 8–10 July 2009; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Barthakur, P.; Dahal, M.; Ghose, M.K. An Efficient Machine Learning Based Classification Scheme for Detecting Distributed Command & Control Traffic of P2P Botnets. Int. J. Mod. Educ. Comput. Sci. 2013, 5, 9–18. [Google Scholar] [CrossRef] [Green Version]
- Turcotte, M.J.M.; Kent, A.D.; Hash, C. Unified Host and Network Data Set. In Data Science for Cyber-Security; World Scientific: Singapore, 2018; pp. 1–22. [Google Scholar] [CrossRef] [Green Version]
- Joseph, B. Yahoo Password Frequency Corpus. Figshare. Available online: https://figshare.com/articles/dataset/Yahoo_Password_Frequency_Corpus/2057937 (accessed on 24 December 2015).
- Tyson, G.; Huang, S.; Cuadrado, F.; Castro, I.; Perta, V.C.; Sathiaseelan, A.; Uhlig, S. Exploring HTTP Header Manipulation In-The-Wild. In Proceedings of the 26th International Conference on World Wide Web, Perth, Australia, 3–7 April 2017; pp. 451–458. [Google Scholar] [CrossRef]
- Luo, S.Q.; Ni, B.; Jiang, P.; Tian, S.W.; Yu, L.; Wang, R.J. Deep Learning in Drebin: Android malware Image Texture Median Filter Analysis and Detection. KSII Trans. Internet Inf. Syst. 2019, 13, 3654–3670. [Google Scholar] [CrossRef] [Green Version]
- Roziewski, S.; Kozłowski, M. LanguageCrawl: A generic tool for building language models upon common Crawl. Comput. Humanit. 2021, 55, 1047–1075. [Google Scholar] [CrossRef]
- Onwubiko, C.; Lenaghan, A.P. Challenges and complexities of managing information security. Int. J. Electron. Secur. Digit. Forensics 2009, 2, 306–321. [Google Scholar] [CrossRef]
- Choobineh, J.; Dhillon, G.; Grimaila, M.R.; Rees, J. Management of Information Security: Challenges and Research Directions. Commun. Assoc. Inf. Syst. 2007, 20, 57. [Google Scholar] [CrossRef]
- Anand, A.; Gokhale, A.A. 1 Impact of available resources on software patch management. Syst. Perform. Modeling 2020, 4, 1–12. [Google Scholar] [CrossRef]
- Appling, D.S.; Briscoe, E.J.; Hutto, C.J. Discriminative Models for Predicting Deception Strategies. In Proceedings of the 24th International Conference on World Wide Web, Florence, Italy, 18–22 May 2015; pp. 947–952. [Google Scholar] [CrossRef]
- Ashenden, D. Information Security management: A human challenge? Inf. Secur. Tech. Rep. 2008, 13, 195–201. [Google Scholar] [CrossRef] [Green Version]
- Laszka, A.; Felegyhazi, M.; Buttyan, L. A Survey of Interdependent Information Security Games. ACM Comput. Surv. 2015, 47, 1–38. [Google Scholar] [CrossRef] [Green Version]
- Kumaar, M.A.; Samiayya, D.; Vincent, P.M.D.R.; Srinivasan, K.; Chang, C.-Y.; Ganesh, H. A Hybrid Framework for Intrusion Detection in Healthcare Systems Using Deep Learning. Front. Public Health 2022, 9, 824898. [Google Scholar] [CrossRef] [PubMed]
- Angel, N.A.; Ravindran, D.; Vincent, P.M.D.R.; Srinivasan, K.; Hu, Y.-C. Recent Advances in Evolving Computing Paradigms: Cloud, Edge, and Fog Technologies. Sensors 2021, 22, 196. [Google Scholar] [CrossRef] [PubMed]
- Mamdiwar, S.D.; Shakruwala, Z.; Chadha, U.; Srinivasan, K.; Chang, C.-Y. Recent Advances on IoT-Assisted Wearable Sensor Systems for Healthcare Monitoring. Biosensors 2021, 11, 372. [Google Scholar] [CrossRef]
- Patel, D.; Srinivasan, K.; Chang, C.-Y.; Gupta, T.; Kataria, A. Network Anomaly Detection inside Consumer Networks—A Hybrid Approach. Electronics 2020, 9, 923. [Google Scholar] [CrossRef]
- Oliveira, N.; Praça, I.; Maia, E.; Sousa, O. Intelligent Cyber Attack Detection and Classification for Network-Based Intrusion Detection Systems. Appl. Sci. 2021, 11, 1674. [Google Scholar] [CrossRef]
- Nisa, M.; Shah, J.H.; Kanwal, S.; Raza, M.; Khan, M.A.; Damaševičius, R.; Blažauskas, T. Hybrid Malware Classification Method Using Segmentation-Based Fractal Texture Analysis and Deep Convolution Neural Network Features. Appl. Sci. 2020, 10, 4966. [Google Scholar] [CrossRef]
- Nasralla, M.M.; Garcia-Magarino, I.; Lloret, J. Defenses Against Perception-Layer Attacks on IoT Smart Furniture for Impaired People. IEEE Access 2020, 8, 119795–119805. [Google Scholar] [CrossRef]
- Guo, J.; Nazir, S. Internet of Things Based Intelligent Techniques in Workable Computing: An Overview. Sci. Program. 2021, 2021, 1–15. [Google Scholar] [CrossRef]
- Khan, M.A.; Nasralla, M.M.; Umar, M.M.; Rehman, G.U.; Khan, S.; Choudhury, N. An Efficient Multilevel Probabilistic Model for Abnormal Traffic Detection in Wireless Sensor Networks. Sensors 2022, 22, 410. [Google Scholar] [CrossRef]
- Chabaa, S.; Zeroual, A.; Antari, J. Identification and Prediction of Internet Traffic Using Artificial Neural Networks. J. Intell. Learn. Syst. Appl. 2010, 2, 147–155. [Google Scholar] [CrossRef] [Green Version]
- Shuai, Y.; Xu, C.; Zhi, Z.; Xiaowen, G.; Di, W. When Deep Reinforcement Learning Meets Federated Learning: Intelligent Multi-Timescale Resource Management for Multi-access Edge Computing in 5G Ultra Dense Network. IEEE Internet Things J. 2020, 8, 2238–2251. [Google Scholar]
- Li, J.-H. Cyber security meets artificial intelligence: A survey. Front. Inf. Technol. Electron. Eng. 2018, 19, 1462–1474. [Google Scholar] [CrossRef]
- Hughes-Lartey, K.; Li, M.; Botchey, F.E.; Qin, Z. Human factor, a critical weak point in the information security of an organization’s Internet of things. Heliyon 2021, 7, e06522. [Google Scholar] [CrossRef] [PubMed]
- Cram, W.A.; University of Waterloo; Proudfoot, J.G.; D’Arcy, J.; Bentley University; University of Delaware. Maximizing Employee Compliance with Cybersecurity Policies. MIS Q. Exec. 2020, 183–198. [Google Scholar] [CrossRef]
- Bal, P.K.; Mohapatra, S.K.; Das, T.K.; Srinivasan, K.; Hu, Y.-C. A Joint Resource Allocation, Security with Efficient Task Scheduling in Cloud Computing Using Hybrid Machine Learning Techniques. Sensors 2022, 22, 1242. [Google Scholar] [CrossRef]
- Chadwick, D.W.; Fan, W.; Costantino, G.; de Lemos, R.; Di Cerbo, F.; Herwono, I.; Manea, M.; Mori, P.; Sajjad, A.; Wang, X.-S. A cloud-edge based data security architecture for sharing and analysing cyber threat information. Future Gener. Comput. Syst. 2020, 102, 710–722. [Google Scholar] [CrossRef]
- Gupta, A.; Srinivasan, K. Quantum Computing: A Brief Study. In Proceedings of the 2019 IEEE International Conference on Consumer Electronics—Taiwan (ICCE-TW), Yilan, Taiwan, 20–22 May 2019; pp. 1–2. [Google Scholar] [CrossRef]
- Badsha, S.; Vakilinia, I.; Sengupta, S. Privacy Preserving Cyber Threat Information Sharing and Learning for Cyber Defense. In Proceedings of the 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 7–9 January 2019; pp. 0708–0714. [Google Scholar] [CrossRef]
- Mavroeidis, V.; Bromander, S. Cyber Threat Intelligence Model: An Evaluation of Taxonomies, Sharing Standards, and Ontologies within Cyber Threat Intelligence. In Proceedings of the 2017 European Intelligence and Security Informatics Conference (EISIC), Athens, Greece, 11–13 September 2017; pp. 91–98. [Google Scholar] [CrossRef] [Green Version]
- Hrri, J.; Bonnet, C. Security in Mobile Telecommunication Networks. In Wireless and Mobile Network Security; John Wiley and Sons: Hoboken, NJ, USA, 2009; pp. 315–360. [Google Scholar] [CrossRef]
- Xie, J.; Jiang, S.; Xie, W.; Gao, X. An Efficient Global K-means Clustering Algorithm. J. Comput. 2011, 6, 271–279. [Google Scholar] [CrossRef]
- Datta, D.; Garg, L.; Srinivasan, K.; Inoue, A.G.; Thippa, G.R.; Praveen, M.K.R.; Ramesh, K.; Nasser, N. An Efficient Sound and Data Steganography Based Secure Authentication System. Comput. Mater. Contin. 2021, 67, 723–751. [Google Scholar] [CrossRef]
- Ahmad, I.; Basheri, M.; Iqbal, M.J.; Rahim, A. Performance Comparison of Support Vector Machine, Random Forest, and Extreme Learning Machine for Intrusion Detection. IEEE Access 2018, 6, 33789–33795. [Google Scholar] [CrossRef]
- Liu, H.; Lang, B. Machine Learning and Deep Learning Methods for Intrusion Detection Systems: A Survey. Appl. Sci. 2019, 9, 4396. [Google Scholar] [CrossRef] [Green Version]
- Sharma, V.; Srinivasan, K. QoS-Aware Routing in Wireless Networks Using Aerial Vehicles. J. Internet Technol. 2018, 19, 73–89. [Google Scholar] [CrossRef]
- Ogino, T. Evaluation of Machine Learning Method for Intrusion Detection System on Jubatus. Int. J. Mach. Learn. Comput. 2015, 5, 137–141. [Google Scholar] [CrossRef]
- Kumar, N.S.; Vincent, P.M.D.R.; Srinivasan, K.; Rajagopal, S.; Angayarkanni, S.A.; Alhadidi, B. Role of M-CORD Computing Architecture for Over the Top (OTT) Services and Applications. In Proceedings of the International Conference on Innovative Computing and Cuttingedge Technologies, Istanbul, Turkey, 30–31 October 2021; pp. 75–86. [Google Scholar] [CrossRef]
- Ma, X.; Zhang, X.; Dong, C.; Chen, X. A Survey on Secure Outsourced Deep Learning. In Cyber Security Meets Machine Learning; Springer: Berlin/Heidelberg, Germany, 2021; pp. 129–163. [Google Scholar] [CrossRef]
- Letaief, K.B.; Chen, W.; Shi, Y.; Zhang, J.; Zhang, Y.-J.A. The Roadmap to 6G: AI Empowered Wireless Networks. IEEE Commun. Mag. 2019, 57, 84–90. [Google Scholar] [CrossRef] [Green Version]
- Sesto-Castilla, D.; Garcia-Villegas, E.; Lyberopoulos, G.; Theodoropoulou, E. Use of Machine Learning for energy efficiency in present and future mobile networks. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019. [Google Scholar]
- Ding, X. Discussion and Research on Information Security Attack and Defense Platform Construction in Universities Based on Cloud Computing and Virtualization. J. Inf. Secur. 2016, 07, 297–303. [Google Scholar] [CrossRef] [Green Version]
- Sriram, P.P.; Wang, H.-C.; Jami, H.G.; Srinivasan, K. 5G Security: Concepts and Challenges; Springer International Publishing: Berlin/Heidelberg, Germany, 2019; pp. 1–43. [Google Scholar] [CrossRef]
- Kotenko, I.; Izrailov, K.; Buinevich, M. Static Analysis of Information Systems for IoT Cyber Security: A Survey of Machine Learning Approaches. Sensors 2022, 22, 1335. [Google Scholar] [CrossRef]
- Dai, H.-N.; Wong, R.C.-W.; Wang, H.; Zheng, Z.; Vasilakos, A.V. Big Data Analytics for Large-scale Wireless Networks. ACM Comput. Surv. 2020, 52, 1–36. [Google Scholar] [CrossRef] [Green Version]
- Srinivasan, K.; Garg, L.; Chen, B.-Y.; Alaboudi, A.A.; Jhanjhi, N.Z.; Chang, C.-T.; Prabadevi, B.; Deepa, N. Expert System for Stable Power Generation Prediction in Microbial Fuel Cell. Intell. Autom. Soft Comput. 2021, 29, 17–30. [Google Scholar] [CrossRef]
- Zwilling, M. Trends and Challenges Regarding Cyber Risk Mitigation by CISOs—A Systematic Literature and Experts’ Opinion Review Based on Text Analytics. Sustainability 2022, 14, 1311. [Google Scholar] [CrossRef]
- Schlatt, V.; Guggenberger, T.; Schmid, J.; Urbach, N. Attacking the trust machine: Developing an information systems research agenda for blockchain cybersecurity. Int. J. Inf. Manag. 2022, 102470. [Google Scholar] [CrossRef]
- Yang, B.; Guo, H.; Cao, E. Design of cyber-physical-social systems with forensic-awareness based on deep learning. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 2020; pp. 39–79. [Google Scholar] [CrossRef]
- Luo, G. Extension clustering-based extreme learning machine neural network. J. Comput. Appl. 2013, 33, 1942–1945. [Google Scholar] [CrossRef]
- Srinivasan, K.; Garg, L.; Datta, D.; Alaboudi, A.A.; Jhanjhi, N.Z.; Agarwal, R.; Thomas, A.G. Performance Comparison of Deep CNN Models for Detecting Driver’s Distraction. Comput. Mater. Contin. 2021, 68, 4109–4124. [Google Scholar] [CrossRef]
- Geetha, R.; Thilagam, T. A Review on the Effectiveness of Machine Learning and Deep Learning Algorithms for Cyber Security. Arch. Comput. Methods Eng. 2020, 28, 2861–2879. [Google Scholar] [CrossRef]
- Duan, Y.; Edwards, J.S.; Dwivedi, Y.K. Artificial intelligence for decision making in the era of Big Data—Evolution, challenges and research agenda. Int. J. Inf. Manag. 2019, 48, 63–71. [Google Scholar] [CrossRef]
- Arel, I.; Rose, D.C.; Karnowski, T.P. Deep Machine Learning—A New Frontier in Artificial Intelligence Research [Research Frontier]. IEEE Comput. Intell. Mag. 2010, 5, 13–18. [Google Scholar] [CrossRef]
- Xiao, G.; Li, J.; Chen, Y.; Li, K. MalFCS: An effective malware classification framework with automated feature extraction based on deep convolutional neural networks. J. Parallel Distrib. Comput. 2020, 141, 49–58. [Google Scholar] [CrossRef]
- Srinivasan, K.; Agrawal, N.K. A study on M-CORD based architecture in traffic offloading for 5G-enabled multiaccess edge computing networks. In Proceedings of the 2018 IEEE International Conference on Applied System Invention (ICASI), Chiba, Japan, 13–17 April 2018; pp. 303–307. [Google Scholar] [CrossRef]
- Oppliger, R. Intrusion Detection; Network Security Beyond the Firewall. Comput. Commun. 2000, 23, 429. [Google Scholar] [CrossRef]
- Buschkes, R.; Kesdogan, D.; Reichl, P. How to increase security in mobile networks by anomaly detection. In Proceedings of the 14th Annual Computer Security Applications Conference (Cat. No. 98EX217), Phoenix, AZ, USA, 7–11 December 1998; pp. 3–12. [Google Scholar] [CrossRef]
- Looi, M. Enhanced authentication services for Internet systems using mobile networks. In Proceedings of the GLOBECOM’01. IEEE Global Telecommunications Conference (Cat. No. 01CH37270), San Antonio, TX, USA, 21–29 November 2001; pp. 3468–3472. [Google Scholar] [CrossRef]
- Srinivasan, K.; Cherukuri, A.K.; Das, T.K. Realizing a Ultra-Low Latency M-CORD Model for Real-Time Traffic Settings in Smart Cities. In Innovations in the Industrial Internet of Things (IIoT) and Smart Factory; IGI Global: Hershey, PA, USA, 2021; pp. 93–105. [Google Scholar] [CrossRef]
- Taherdoost, H. A Review on Risk Management in Information Systems: Risk Policy, Control and Fraud Detection. Electronics 2021, 10, 3065. [Google Scholar] [CrossRef]
- Chellappa, R.K.; Pavlou, P.A. Perceived information security, financial liability and consumer trust in electronic commerce transactions. Logist. Inf. Manag. 2002, 15, 358–368. [Google Scholar] [CrossRef]
- Srinivasan, K.; Agrawal, N.K.; Cherukuri, A.K.; Pounjeba, J. An M-CORD Architecture for Multi-Access Edge Computing: A Review. In Proceedings of the 2018 IEEE International Conference on Consumer Electronics-Taiwan (ICCE-TW), Taichung, Taiwan, 19–21 May 2018; pp. 1–2. [Google Scholar] [CrossRef]
- Höne, K.; Eloff, J. Information security policy—What do international information security standards say? Comput. Secur. 2002, 21, 402–409. [Google Scholar] [CrossRef]
- Baskerville, R.; Siponen, M. An information security meta-policy for emergent organizations. Logist. Inf. Manag. 2002, 15, 337–346. [Google Scholar] [CrossRef] [Green Version]
- Srinivasan, K.; Mahendran, N.; Vincent, D.R.; Chang, C.-Y.; Syed-Abdul, S. Realizing an Integrated Multistage Support Vector Machine Model for Augmented Recognition of Unipolar Depression. Electronics 2020, 9, 647. [Google Scholar] [CrossRef] [Green Version]
- Afifi, M.A. Assessing Information Security Vulnerabilities and Threats to Implementing Security Mechanism and Security Policy Audit. J. Comput. Sci. 2020, 16, 321–329. [Google Scholar] [CrossRef] [Green Version]
- Shang, W.; Gong, T.; Chen, C.; Hou, J.; Zeng, P. Information Security Risk Assessment Method for Ship Control System Based on Fuzzy Sets and Attack Trees. Secur. Commun. Networks 2019, 2019, 3574675. [Google Scholar] [CrossRef]
- Kumar, R.; Goel, S.; Sharma, V.; Garg, L.; Srinivasan, K.; Julka, N. A Multifaceted Vigilare System for Intelligent Transportation Services in Smart Cities. IEEE Internet Things Mag. 2020, 3, 76–80. [Google Scholar] [CrossRef]
- Al-Karaki, J.N.; Kamal, A.E. End-to-end support for statistical quality of service in heterogeneous mobile ad hoc networks. Comput. Commun. 2005, 28, 2119–2132. [Google Scholar] [CrossRef]
- Fichtner, L. What kind of cyber security? Theorising cyber security and mapping approaches. Internet Policy Rev. 2018, 7. [Google Scholar] [CrossRef] [Green Version]








| Reference | Year | Number of Articles | Time Span | One-Sentence Summary | ML | DL |
|---|---|---|---|---|---|---|
| [16] | 2017 | 260 | 1986–2017 | Intelligent network traffic control systems analysis and future study directions. | ✓ | ✓ |
| [23] | 2019 | 145 | 2011–2019 | UAV communications for 5G networks and upcoming future networks. | × | × |
| [24] | 2019 | 574 | 1986–2019 | Deep learning techniques in mobile and wireless networks. | ✓ | ✓ |
| [29] | 2019 | 174 | 1958–2019 | Survey on DL methods for cyber security. | × | ✓ |
| [33] | 2020 | 65 | 2004–2020 | An examination of AI-enabled phishing attack detection techniques. | ✓ | ✓ |
| [36] | 2020 | 139 | 1990–2019 | Description of several ML approaches used in vehicular networks for communication, networking, and security. | ✓ | × |
| [39] | 2020 | 262 | 2009–2020 | ML techniques used for cyber security. | ✓ | × |
| [40] | 2020 | 668 | 1988–2020 | ML techniques description and comparison for cyber security. | ✓ | × |
| [41] | 2020 | 88 | 1958–2020 | Report on neural networks usage for intrusion detection systems. | ✓ | ✓ |
| [42] | 2020 | 142 | 1993–2020 | Network intrusion detection system. | ✓ | ✓ |
| [43] | 2020 | 175 | 2002–2020 | Survey on moving networks. | × | × |
| [44] | 2020 | 181 | 1991–2019 | Cyber security data science using machine learning. | ✓ | × |
| [50] | 2021 | 189 | 1989–2021 | DL for challenged networks. | × | ✓ |
| [51] | 2021 | 138 | 1999–2020 | ML approaches for mobile network and malicious behaviour detection. | ✓ | × |
| Our Review | 2022 | 177 | 1998–2022 | This review offers a widespread investigation on the various machine learning and deep learning models for electronic information security in mobile networks. | ✓ | ✓ |
| Reference | Security-Category | Machine Learning Approaches Used | Key Contribution | Limitations |
|---|---|---|---|---|
| [63] | Network Attack Patterns | C4.5 Decision Tree; Bayesian Network; Naive-Bayes; Decision Table |
| The approach generates variable results for different datasets. A higher variance in data would lead to higher chances of false prediction. |
| [64] | Network Anomaly Detection | GA; SVM |
| A more realistic profiling method would be required to apply the framework in a real TCP/IP traffic environment. |
| [65] | Traffic Classification | Laplacian SVM |
| Labelling to be performed explicitly for the datasets in semi-supervised algorithms as unsupervised ML-based algorithms cannot be directly applied in SDN. |
| [66] | Real-time Intrusion Detection | PSO; SVM |
| Requires improvement in feature selection algorithm on search strategy and evaluation criterion. |
| [67] | Jamming Attacks | ANN; SVM; LR; KNN; DT; NB |
| The studied localization is limited to the jammed channel. |
| [68] | Malware Detection | DT; NB; RF |
| The proposed solution is not viable for home users, being very processor heavy for a general-purpose machine. |
| [69] | Network Anomalies (DoS Flooding) | AdaboostM1; RF; MLP |
| None of the classifiers managed to detect the brute force attack in the TCP dataset.F-Measure results performance is less effective for AdaboostM1 classifiers in the TCP-SYN and UDP flood attacks compared to other attacks. |
| [70] | Webshell Detection | K-means; MLP; NB; DT; SVM; KNN |
| Tests carried out on machine learning models for webshell detection on PHP scripts only. Higher accuracy results require IoT servers with reliable computing power. |
| [71] | Jamming-Based Denial-of-Service and Eavesdropping Attacks | MLP; SVM; KNN; DT; Thresh |
| In the presence of an internal DoS attack, the performance is not as adequate and only slightly better than a wired NoC. |
| [72] | Poisoning Attacks (Unreliable Model Updates) | Stochastic Gradient Descent (SGD) Algorithm |
| Each local worker model trained needs to send regular updates to the central server at regular periods. Insufficient reliable method to monitor worker metrics. |
| Reference | Year | Dataset Used | Dataset Size | Format | Details about the Dataset/Brief Description |
|---|---|---|---|---|---|
| [104] | 2016 | CAIDA DDoS 2007 and MIT DARPA dataset | 5.3 GB | pcap (tcpdump) format |
|
| [105] | 2015 | Botnet [Zeus (Snort), Zeus (NETRESEC), Zeus-2 (NIMS), Conficker (CAIDA) and ISOT-Uvic] | 14 GB packets | packet |
|
| [106] | 2009 | NSL-KDD | 4 GB of compressed (approx.)/150k points | tcpdump data |
|
| [107] | 2011 | ISOT | 11 GB packets | packet |
|
| [54] | 2016 | UNSW-NB-15 | 100 GB | CSV files |
|
| [108] | 2017 | Unified Host and Network | 150 GB flows (compressed) | bi. flows, logs |
|
| [109] | 2011 | Yahoo Password Frequency Corpus | 130.64 kB (compressed) | txt files |
|
| [110] | 2014 | 500K HTTP Headers | 75 MB | CSV files |
|
| [111] | 2014 | The Drebin Dataset | 6 MB (approx.) | txt log, CSV and XML files |
|
| [112] | 2008 | Common Crawl | 320 TiB | WARC and ARC format |
|
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gupta, C.; Johri, I.; Srinivasan, K.; Hu, Y.-C.; Qaisar, S.M.; Huang, K.-Y. A Systematic Review on Machine Learning and Deep Learning Models for Electronic Information Security in Mobile Networks. Sensors 2022, 22, 2017. https://doi.org/10.3390/s22052017
Gupta C, Johri I, Srinivasan K, Hu Y-C, Qaisar SM, Huang K-Y. A Systematic Review on Machine Learning and Deep Learning Models for Electronic Information Security in Mobile Networks. Sensors. 2022; 22(5):2017. https://doi.org/10.3390/s22052017
Chicago/Turabian StyleGupta, Chaitanya, Ishita Johri, Kathiravan Srinivasan, Yuh-Chung Hu, Saeed Mian Qaisar, and Kuo-Yi Huang. 2022. "A Systematic Review on Machine Learning and Deep Learning Models for Electronic Information Security in Mobile Networks" Sensors 22, no. 5: 2017. https://doi.org/10.3390/s22052017







