A Survey on Quantitative Risk Estimation Approaches for Secure and Usable User Authentication on Smartphones
Abstract
:1. Introduction
- Before selecting references, we determined the scope of the survey paper, which is to investigate existing quantitative risk estimation approaches that could be possibly adopted in risk-based continuous user authentication solutions for smartphones.
- Afterwards, we identified the most relevant databases and search engines, namely Google Scholar, IEEE Xplore, ACM Digital Library, and ScienceDirect.
- Then, we used appropriate keywords to find relevant references (i.e., quantitative risk estimation, risk-based user authentication, continuous user authentication, behavioral biometrics), also utilizing Boolean operators (AND, OR, NOT) to refine our search. We also used advanced search options to further refine our search.
- After that, we evaluated the quality of the references by: (i) looking for references that were published in reputable peer-reviewed journals or conference proceedings; (ii) checking the authors’ credentials and their affiliations; and (iii) looking for references that were recent and relevant to our topic.
- Finally, we organized the references by creating a spreadsheet to keep track of all the references. Then, we analyzed each reference and identified the key findings and themes. Afterwards, we created a table (which is presented in the end of our manuscript), where we extracted from every reference the technique used, as well as our main observations.
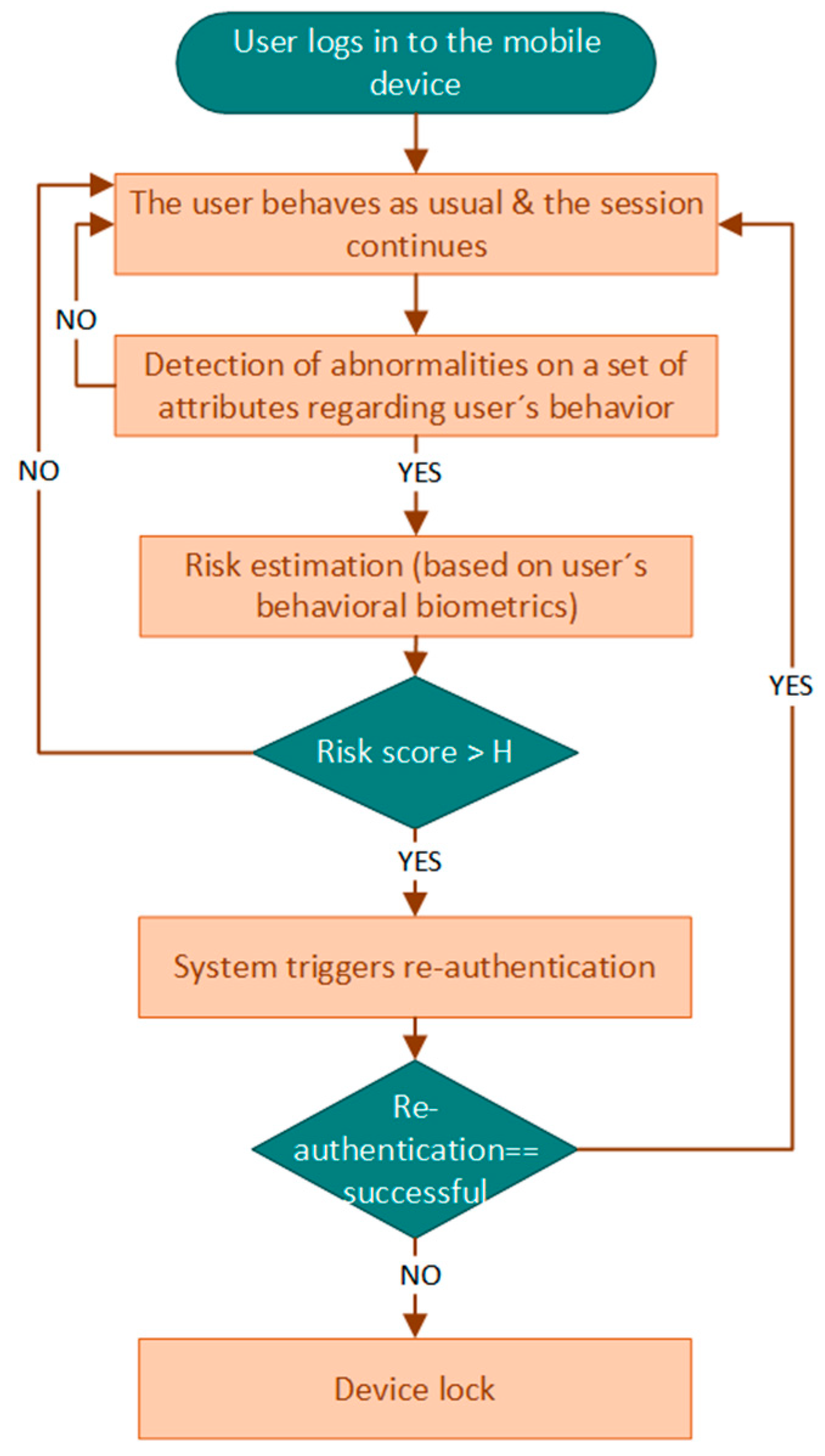
2. Fundamentals of Risk-Based Continuous User Authentication Relying on Behavioral Biometrics for Mobile Devices
- (i)
- to overcome the limitations of the conventional one-time authentication, in which user authentication only occurs at the start of the session, and afterwards, any future changes and/or abnormalities in user identity/behavior remain undetected;
- (ii)
- to increase the efficiency of user authentication by triggering the verification process for user re-authentication only when it is actually required (i.e., real-time risk score above predefined threshold), minimizing the consumed resources;
- (iii)
- to adapt the user re-authentication levels (i.e., uni-modal or multimodal authentication) autonomously in an on-the-fly approach based on the apparent risks (i.e., real-time risk score);
- (iv)
- to re-authenticate users unobtrusively, based on their interactions with the device (i.e., beharioural biometrics), and thus address the security versus usability challenge in mobile user authentication.
3. Quantitative Risk Estimation Approaches (QREAs)
3.1. Probabilistic QREA Approaches
3.1.1. Freeman et al. Approach
3.1.2. Hidden Markov Model
Arnes et al.
Chen et al.
3.1.3. D–S Evidence Theory
- Ability to handle uncertainty: The D–S theory can handle uncertain and incomplete information, making it useful in situations where traditional probability theory may not be suitable.
- Incorporation of multiple sources of evidence: The D–S theory allows for the integration of evidence from multiple sources, even when they may be conflicting or inconsistent, making it well-suited for situations where there are multiple sources of information.
- Flexibility in representation: The D–S theory provides a flexible framework for representing uncertainty and making decisions based on evidence, making it adaptable to a wide range of applications.
- Transparent reasoning process: The D–S theory provides a transparent reasoning process that allows users to trace the origins of their beliefs and decisions.
- Robustness to outliers: The D–S theory is robust to outliers or noise in the data, making it well-suited for applications where there may be inaccuracies or errors in the data.
Mu et al.
3.2. ML-Based RBA Models
3.2.1. Siamese Neural Networks
Acien et al.
3.2.2. Classification Algorithms
Misbahuddin et al.
3.2.3. Novelty Detection Algorithms
Papaioannou et al.
- True Positive (TP) refers to the number of positive instances (malicious users) that are correctly classified.
- True Negative (TN) refers to the number of negative instances (legitimate users) that are correctly classified.
- False Positive (FP) refers to the number of negative instances (legitimate users) that are mistakenly classified as positive (malicious users).
- False Negative (FN) refers to the number of positive instances (malicious users) that are mistakenly classified as negative (legitimate users).
3.2.4. Bayesian Networks
Luo et al.
3.3. Fuzzy Logic
3.3.1. Haslum et al.
3.3.2. Gusmão et al.
3.4. Non-Graph-Based
Gehani et al.
3.5. Monte Carlo Simulation
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Bubukayr, M.A.S.; Almaiah, M.A. Cybersecurity Concerns in Smart-phones and applications: A survey. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14–15 July 2021; pp. 725–731. [Google Scholar]
- Almaiah, M.A.; Al-Zahrani, A.; Almomani, O.; Alhwaitat, A.K. Classification of Cyber Security Threats on Mobile Devices and Applications. In Artificial Intelligence and Blockchain for Future Cybersecurity Applications; Springer: Cham, Switzerland, 2021; Volume 90, pp. 107–123. [Google Scholar] [CrossRef]
- Beier, G.; Hoffman, P.; Shorter, S. Information System Security Best Practices for UOCAVA-Supporting Systems (NISTIR 7682). Natl. Inst. Stand. Technol. (NIST), NIST Special Publication, Report NISTIR 7682. 2011. Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/IR/nistir7682.pdf (accessed on 7 January 2023).
- Papaioannou, M.; Karageorgou, M.; Mantas, G.; Sucasas, V.; Essop, I.; Rodriguez, J.; Lymberopoulos, D. A survey on security threats and countermeasures in Internet of Medical Things (IoMT). Trans. Emerg. Telecommun. Technol. 2020, 33, e4049. [Google Scholar] [CrossRef]
- Pelekoudas-Oikonomou, F.; Zachos, G.; Papaioannou, M.; de Ree, M.; Ribeiro, J.C.; Mantas, G.; Rodriguez, J. Blockchain-Based Security Mechanisms for IoMT Edge Networks in IoMT-Based Healthcare Monitoring Systems. Sensors 2022, 22, 2449. [Google Scholar] [CrossRef]
- Papaioannou, M.; Ribeiro, J.C.; Monteiro, V.; Sucasas, V.; Mantas, G.; Rodriguez, J. A privacy-preserving user authentication mechanism for smart city mobile apps. In Proceedings of the IEEE International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (IEEE CAMAD), Porto, Portugal, 25–27 October 2021; pp. 1–5. [Google Scholar]
- Ribeiro, J.; Saghezchi, F.B.; Mantas, G.; Rodriguez, J.; Abd-Alhameed, R.A. HIDROID: Prototyping a behavioral host-based intrusion detection and prevention system for android. IEEE Access 2020, 8, 23154–23168. [Google Scholar] [CrossRef]
- Zhu, L.; Li, M.; Zhang, Z.; Xu, C.; Zhang, R.; Du, X.; Guizani, N. Privacy-Preserving Authentication and Data Aggregation for Fog-Based Smart Grid. IEEE Commun. Mag. 2019, 57, 80–85. [Google Scholar] [CrossRef]
- Grassi, P.A.; Garcia, M.E.; Fenton, J.L. NIST 800-63-3: Digital Identity Guidelines. NIST Spec. Publ. 2017, 75. [Google Scholar] [CrossRef]
- Harbach, M.; von Zezschwitz, E.; Fichtner, A.; De Luca, A.; Smith, M. It’s a Hard Lock Life: A Field Study of Smartphone (Un)Locking Behavior and Risk Perception. In Proceedings of the Symposium on Usable Privacy and Security (SOUPS 2014), Menlo Park, CA, USA, 9–11 July 2014; pp. 213–230. [Google Scholar]
- Stylios, I.; Kokolakis, S.; Thanou, O.; Chatzis, S. Behavioral biometrics & continuous user authentication on mobile devices: A survey. Inf. Fusion 2021, 66, 76–99. [Google Scholar] [CrossRef]
- Gupta, S.; Buriro, A.; Crispo, B. Demystifying authentication concepts in smartphones: Ways and types to secure access. Hindawi Mob. Inf. Syst. 2018, 2018, 2649598. [Google Scholar] [CrossRef] [Green Version]
- Zhang, J.; Luo, X.; Akkaladevi, S.; Ziegelmayer, J. Improving multiple-password recall: An empirical study. Eur. J. Inf. Syst. 2009, 18, 165–176. [Google Scholar] [CrossRef]
- Abuhamad, M.; Abusnaina, A.; Member, G.S.; Nyang, D.; Mohaisen, D.; Member, S. Sensor-Based Continuous Authentication of Smartphones’ Users Using Behavioral Biometrics: A Contemporary Survey. IEEE Internet Things J. 2021, 8, 65–84. [Google Scholar] [CrossRef]
- Theofanos, M.; Stanton, B.; Wolfson, C. Usability and Biometrics: Ensuring Successful Biometric Systems, International Workshop on Usability and Biometrics. 2008. Available online: https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=152184 (accessed on 7 January 2023).
- Schneier, B. Applied Cryptography; Wiley: New York, NY, USA, 1996; Volume 1, ISBN 978-0471117094. [Google Scholar]
- Titcomb, J. Hackers Claim to Beat iPhone X’s Face id in One Week with 115 Mask. 2017. Available online: http://www.telegraph.co.uk/technology/2017/11/13/hackers-beat-iphone-xs-face-oneweek-115-mask/ (accessed on 7 January 2023).
- Kovach, S. Business Insider-Samsung’s Galaxy S8 Facial Recognition Feature Can be Fooled with a Photo. 2017. Available online: http://www.businessinsider.com/samsung-galaxy-s8-facial-recognitiontricked-with-a-photo-2017-3?IR=T (accessed on 7 January 2023).
- Charles, A. The Guardian-iPhone 5S Fingerprint Sensor Hacked by Germany’s Chaos Computer Club. 2013. Available online: https://www.theguardian.com/technology/2013/sep/22/apple-iphonefingerprint-scanner-hacked (accessed on 10 January 2023).
- McGoogan, C.; Demetriou, D. Peace Sign Selfies could Let Hackers Copy Your Fingerprints. 2017. Available online: http://www.telegraph.co.uk/technology/2017/01/12/peace-signselfies-could-let-hackers-copy-fingerprints (accessed on 10 January 2023).
- Wiefling, S.; Dürmuth, M.; Iacono, L. Lo Verify It’s You: How Users Perceive Risk-Based Authentication. IEEE Secur. Priv. 2021, 19, 47–57. [Google Scholar] [CrossRef]
- Wiefling, S.; Lo Iacono, L.; Dürmuth, M. Is this really you? An empirical study on risk-based authentication applied in the wild. In Proceedings of the IFIP International Conference on ICT Systems Security and Privacy Protection, Lisbon, Portugal, 25–27 June 2019; Springer: Cham, Switzerland; pp. 134–148. [Google Scholar]
- Patel, V.M.; Chellappa, R.; Chandra, D.; Barbello, B. Continuous user authentication on mobile devices: Recent progress and remaining challenges. IEEE Signal Process. Mag. 2016, 33, 49–61. [Google Scholar] [CrossRef]
- Stylios, I.; Kokolakis, S.; Thanou, O.; Chatzis, S. Key factors driving the adoption of behavioral biometrics and continuous authentication technology: An empirical research. Inf. Comput. Secur. 2022, 30, 562–582. [Google Scholar] [CrossRef]
- Jeong, J.J.; Zolotavkin, Y.; Doss, R. Examining the Current Status and Emerging Trends in Continuous Authentication Technologies through Citation Network Analysis. ACM Comput. Surv. 2022, 55, 1–31. [Google Scholar] [CrossRef]
- ClearLogin Risk-Based Authentication. 2017. Available online: http://www.clearlogin.com/glossary/risk-based-authentication/ (accessed on 10 January 2023).
- Wiefling, S.; Jørgensen, P.R.; Thunem, S.; Iacono, L. Lo Pump Up Password Security! Evaluating and Enhancing Risk-Based Authentication on a Real-World Large-Scale Online Service. ACM Trans. Priv. Secur. 2022, 1, 1–36. [Google Scholar] [CrossRef]
- Wiefling, S.; Dürmuth, M.; Lo Iacono, L. What’s in Score for Website Users: A Data-Driven Long-Term Study on Risk-Based Authentication Characteristics. Lect. Notes Comput. Sci. Incl. Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinform. 2021, 12675, 361–381. [Google Scholar] [CrossRef]
- Jansen, W.A.; Winograd, T.; Scarfone, K. Guidelines on Active Content and Mobile Code; NIST: Gaithersburg, MD, USA, 2001. Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-28ver2.pdf (accessed on 25 January 2023).
- Hubbard, D.W.; Seiersen, R. How to Measure Anything in Cybersecurity Risk; Wiley: New York, NY, USA, 2016; ISBN 978-1-119-22460-0. [Google Scholar]
- Ghazouani, M.; Faris, S.; Medromi, H.; Sayouti, A. Information Security Risk Assessment A Practical Approach with a Mathematical Formulation of Risk. Int. J. Comput. Appl. 2014, 103, 36–42. [Google Scholar] [CrossRef]
- Quinn, S.; Ivy, N.; Barrett, M.; Witte, G.; Gardner, R.K. Identifying and Estimating Cybersecurity Risk for Enterprise Risk Management. Natl. Inst. Stand. Technol. NIST Special Publication. 2021; pp. 1–52. Available online: https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=933223 (accessed on 25 January 2023).
- Freeman, D.; Jain, S.; Duermuth, M.; Biggio, B.; Giacinto, G. Who Are You? A Statistical Approach to Measuring User Authenticity. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 21–24 February 2016. [Google Scholar] [CrossRef]
- Chen, G.; Wang, K.; Tan, J.; Li, X. A risk assessment method based on software behavior. In Proceedings of the 2019 IEEE International Conference on Intelligence and Security Informatics (ISI), Shenzhen, China, 1–3 July 2019; pp. 47–52. [Google Scholar] [CrossRef]
- Arnes, A.; Sallhammar, K.; Haslum, K.; Brekne, T.; Gaup Moe, M.E.; Knapskog, S.J. Real-Time Risk Assessment with Network Sensors and Intrusion Detection Systems. In Proceedings of the Computational Intelligence and Security: International Conference, CIS 2005, Xi’an, China, 15–19 December 2005; Volume 3808, pp. 388–397, ISBN 3540307370. [Google Scholar]
- Mor, B.; Garhwal, S.; Kumar, A. A Systematic Review of Hidden Markov Models and Their Applications. Arch. Comput. Methods Eng. 2021, 28, 1429–1448. [Google Scholar] [CrossRef]
- AS/NZS 4360: 2004; Risk Management. Standards Australia International: Sydney, Australia, Standards New Zealand: Wellington, New Zealand. 2004.
- Mu, C.P.; Li, X.J.; Huang, H.K.; Tian, S.F. Online Risk Assessment of Intrusion Scenarios Using D-S Evidence Theory. In Proceedings of the Computer Security—ESORICS 2008, 13th European Symposium on Research in Computer Security Proceedings, Malaga, Spain, 6–8 October 2008; Volume 3523, pp. 35–48, ISBN 9783540883128. [Google Scholar]
- Rivera, E.; Tengana, L.; Solano, J.; Castelblanco, A.; López, C.; Ochoa, M. Risk-based Authentication Based on Network Latency Profiling. In Proceedings of the 13th ACM Workshop on Artificial Intelligence and Security, Virtual, 13 November 2020; pp. 105–115. [Google Scholar] [CrossRef]
- Acien, A.; Morales, A.; Vera-Rodriguez, R.; Fierrez, J.; Monaco, J.V. TypeNet: Scaling up keystroke biometrics. In Proceedings of the 2020 IEEE International Joint Conference on Biometrics (IJCB), Houston, TX, USA, 28 September–1 October 2020. [Google Scholar] [CrossRef]
- Deb, D.; Ross, A.; Jain, A.K.; Prakah-Asante, K.; Prasad, K.V. Actions Speak Louder Than (Pass)words: Passive Authentication of Smartphone Users via Deep Temporal Features. In Proceedings of the 2019 International Conference on Biometrics (ICB), Crete, Greece, 4–7 June 2019. [Google Scholar] [CrossRef] [Green Version]
- Singh, P. Introduction To Siamese Networks. Available online: https://medium.com/analytics-vidhya/a-friendly-introduction-to-siamese-networks-283f31bf38cd (accessed on 25 January 2023).
- Taigman, Y.; Ranzato, M.A.; Aviv, T.; Park, M. DeepFace: Closing the Gap to Human-Level Performance in Face Verification. In Proceedings of the 2014 IEEE Conference on Computer Vision and Pattern Recognition, Columbus, OH, USA, 23–28 June 2014; pp. 1701–1708. [Google Scholar] [CrossRef]
- Identity Automation Risk-Based Authentication. Available online: https://blog.identityautomation.com/what-is-risk-based-authentication-types-of-authentication-methods (accessed on 25 January 2023).
- Atlam, H.F.; Alenezi, A.; Walters, R.J.; Wills, G.B. An overview of risk estimation techniques in risk-based access control for the internet of things. In Proceedings of the 2nd International Conference on Internet of Things, Big Data and Security, Porto, Portugal, 24–26 April 2017; pp. 254–260. [Google Scholar] [CrossRef]
- Hintze, D.; Scholz, S.; Koch, E.; Mayrhofer, R. Location-based risk assessment for mobile authentication. In Proceedings of the 2016 ACM International Joint Conference on Pervasive and Ubiquitous Computing: Adjunct, Heidelberg, Germany, 12–16 September 2016; pp. 85–88. [Google Scholar] [CrossRef]
- Gebrie, M.T.; Abie, H. Risk-based adaptive authentication for internet of things in smart home eHealth. In Proceedings of the 11th European Conference on Software Architecture: Companion Proceedings, Canterbury, UK, 11–15 September 2017; Part F1305. pp. 102–108. [Google Scholar] [CrossRef]
- Papaioannou, M.; Zachos, G.; Essop, I.; Mantas, G.; Rodriguez, J. Towards a Secure and Usable User Authentication for Mobile Passenger ID Devices for Land/Sea Border Control. IEEE Access 2022, 10, 38832–38849. [Google Scholar] [CrossRef]
- Misbahuddin, M.; Bindhumadhava, B.S.; Dheeptha, B. Design of a risk based authentication system using machine learning techniques. In Proceedings of the 2017 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computed, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), San Francisco, CA, USA, 4–8 August 2017; pp. 1–6. [Google Scholar]
- Acien, A.; Morales, A.; Fierrez, J.; Vera-Rodriguez, R.; Delgado-Mohatar, O. BeCAPTCHA: Bot detection in smartphone interaction using touchscreen biometrics and mobile sensors. arXiv 2020, arXiv:2005.13655. [Google Scholar]
- Acien, A.; Morales, A.; Fierrez, J.; Vera-Rodriguez, R.; Bartolome, I. BeCAPTCHA: Detecting human behavior in smartphone interaction using multiple inbuilt sensors. arXiv 2020, arXiv:2002.00918. [Google Scholar]
- Papaioannou, M.; Zachos, G.; Mantas, G.; Rodriguez, J. Novelty Detection for Risk-based User Authentication on Mobile Devices. In Proceedings of the IEEE Global Communications Conference, Rio de Janeiro, Brazil, 4–8 December 2022. [Google Scholar]
- Scikit-Learn Developers Novelty and Outlier Detection. Available online: https://scikit-learn.org/stable/modules/outlier_detection.html (accessed on 25 January 2023).
- Gupta, S.; Kumar, R.; Kacimi, M.; Crispo, B. IDeAuth: A novel behavioral biometric-based implicit deauthentication scheme for smartphones. Pattern Recognit. Lett. 2022, 157, 8–15. [Google Scholar] [CrossRef]
- Kim, J.; Kim, H.; Kang, P. Keystroke dynamics-based user authentication using freely typed text based on user-adaptive feature extraction and novelty detection. Appl. Soft Comput. J. 2018, 62, 1077–1087. [Google Scholar] [CrossRef]
- Kumar, R.; Kundu, P.P.; Phoha, V.V. Continuous authentication using one-class classifiers and their fusion. In Proceedings of the 2018 IEEE 4th International Conference on Identity, Security, and Behavior Analysis (ISBA), Singapore, 11–12 January 2018; pp. 1–8. [Google Scholar] [CrossRef] [Green Version]
- Antal, M.; Szabo, L.Z. An evaluation of one-class and two-class classification algorithms for keystroke dynamics authentication on mobile devices. In Proceedings of the 2015 20th International Conference on Control Systems and Computer Science, Bucharest, Romania, 27–29 May 2015; pp. 343–350. [Google Scholar] [CrossRef]
- Shen, C.; Cai, Z.; Guan, X.; Du, Y.; Maxion, R.A. User authentication through mouse dynamics. IEEE Trans. Inf. Forensics Secur. 2013, 8, 16–30. [Google Scholar] [CrossRef]
- Antal, M.; Szabó, L.Z. Biometric Authentication Based on Touchscreen Swipe Patterns. Procedia Technol. 2016, 22, 862–869. [Google Scholar] [CrossRef] [Green Version]
- Papaioannou, M.; Mantas, G.; Essop, A.; Sucasas, V.; Aaraj, N.; Rodriguez, J. Risk Estimation for a Secure & Usable User Authentication Mechanism for Mobile Passenger ID Devices. In Proceedings of the 2022 IEEE 27th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Paris, France, 2–3 November 2022; pp. 173–178. [Google Scholar]
- Forsblom, N. Were you Aware of All These Sensors in Your Smartphone? Available online: https://blog.adtile.me/2015/11/12/wereyou-%0Aaware-of-all-these-sensors-in-your-smartphone/ (accessed on 25 January 2023).
- Ribeiro, J.; Saghezchi, F.B.; Mantas, G.; Rodriguez, J.; Shepherd, S.J.; Abd-Alhameed, R.A. An Autonomous Host-Based Intrusion Detection System for Android Mobile Devices. Mob. Netw. Appl. 2020, 25, 164–172. [Google Scholar] [CrossRef]
- Borges, P.; Sousa, B.; Ferreira, L.; Saghezchi, F.; Mantas, G.; Ribeiro, J.; Rodriguez, J.; Cordeiro, L.; Simoes, P. Towards a Hybrid Intrusion Detection System for Android-based PPDR Terminals. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM): Workshop on Security for Emerging Distributed Network Technologies (DISSECT 2017), Lisbon, Portugal, 8–12 May 2017; pp. 1034–1039. [Google Scholar]
- Behbehani, D.; Komninos, N.; Behbehani, D.; Komninos, N.; Al-begain, K.; Rajarajan, M. Cloud Enterprise Dynamic Risk Assessment (CEDRA ): A Dynamic Risk Assessment Using Dynamic Bayesian Networks for Cloud Environment, 3 May 2022. PREPRINT (Version 2). Available online: https://doi.org/10.21203/rs.3.rs-1512376/v2 (accessed on 25 January 2023).
- Luo, Z.; Xu, R.; Wang, J.; Zhu, W. A Dynamic Risk Assessment Method Based on Bayesian Attack Graph. Int. J. Netw. Secur. 2022, 24, 787–796. [Google Scholar] [CrossRef]
- Friedman, M.; Kandel, A. On the design of a fuzzy intelligent differential equation solver. In Fuzzy Expert Systems; CRC Press: Boca Raton, FL, USA, 1992; pp. 203–212. [Google Scholar]
- Zadeh, L.A. On fuzzy algorithms. In Fuzzy Sets, Fuzzy Logic, and Fuzzy Systems: Selected Papers By Lotfi A Zadeh; World Scientific: Singapore, 1996; pp. 127–147. [Google Scholar]
- Kecman, V. Learning and Soft Computing: Support Vector Machines, Neural Networks, and Fuzzy Logic Models; MIT Press: Cambridge, MA, USA, 2001. [Google Scholar]
- Iliadis, L.S. A decision support system applying an integrated fuzzy model for long-term forest fire risk estimation. Environ. Model. Softw. 2005, 20, 613–621. [Google Scholar] [CrossRef]
- Xiao, Z.; Xia, S.; Gong, K.; Li, D. The trapezoidal fuzzy soft set and its application in Multiple Criterion Decision-Making (MCDM). Appl. Math. Model. 2012, 36, 5844–5855. [Google Scholar] [CrossRef]
- Wierman, M.J. An Introduction to the Mathematics of Uncertainty: Including Set Theory, Logic, Probability, Fuzzy Sets, Rough Sets, and Evidence Theory; Center for the Mathematics of Uncertainty, Creighton University College of Arts and Sciences: Omaha, NE, USA, 2010. [Google Scholar]
- Shang, K.; Hossen, Z. Applying Fuzzy Logic to Risk Assessment and Decision-Making. Available online: https://www.soa.org/globalassets/assets/Files/Research/Projects/research-2013-fuzzy-logic.pdf (accessed on 25 January 2023).
- Papaioannou, M.; Mantas, G.; Rodriguez, J. Risk-based user authentication for mobile passenger ID devices for land and sea border control. In Proceedings of the 2021 IEEE International Mediterranean Conference on Communications and Networking (MeditCom), Athens, Greece, 7–10 September 2021; pp. 180–185. [Google Scholar]
- Haslum, K.; Abraham, A.; Knapskog, S. Fuzzy online risk assessment for distributed intrusion prediction and prevention systems. In Proceedings of the Tenth International Conference on Computer Modeling and Simulation (uksim 2008), Cambridge, UK, 1–3 April 2008; pp. 216–223. [Google Scholar] [CrossRef] [Green Version]
- Henriques de Gusmão, A.P.; Mendonça Silva, M.; Poleto, T.; Camara e Silva, L.; Cabral Seixas Costa, A.P. Cybersecurity risk analysis model using fault tree analysis and fuzzy decision theory. Int. J. Inf. Manag. 2018, 43, 248–260. [Google Scholar] [CrossRef]
- Gehani, A.; Kedem, G. RheoStat: Real-Time Risk Management. In Recent Advances in Intrusion Detection, Proceedings of the7th International Symposium, RAID 2004, Sophia Antipolis, France, 15–17 September 2004; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3523, pp. 296–314. ISBN 3540231234. [Google Scholar]
- Lederm, T.; Clarke, N.L. Risk assessment for mobile devices. In Trust, Privacy and Security in Digital Business, Proceedings of the 8th International Conference, TrustBus 2011, Toulouse, France, August 29 September 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 210–221. [Google Scholar]
- Locke, G.; Gallagher, P.D. Managing Information Security Risk Organization, Mission, and Information System View; National Institute of Standards & Technology: Gaithersburg, MD, USA, 2011. Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-39.pdf (accessed on 25 January 2023).
- Nieles, M.; Dempsey, K.; Yan Pillitteri, V. NIST Special Publication 800-12 Revision 1—An Introduction to Information Security. NIST Spec. Publ. 2017, 800, 101. [Google Scholar] [CrossRef]
- Goerdin, S.A.; Smit, J.J.; Mehairjan, R.P. Monte Carlo simulation applied to support risk-based decision making in electricity distribution networks. In Proceedings of the 2015 IEEE Eindhoven PowerTech, Eindhoven, The Netherlands, 29 June–2 July 2015; pp. 1–5. [Google Scholar]
- Sui, T.; Marelli, D.; Sun, X.; Fu, M. Multi-sensor state estimation over lossy channels using coded measurements. Automatica 2020, 111, 108561. [Google Scholar] [CrossRef]














| User Parameter | User Parameter Weight |
|---|---|
| Browser version | 1 |
| OS version | 2 |
| Login time | 3 |
| IP address | 4 |
| Device type | 5 |
| No. of failed attempts | 6 |
| Geolocation | 7 |
| Time zone | 8 |
| SVM and NB Classifiers Output (i.e., Probabilities P) | One-Class SVM Output (i.e., Risk Score S) | Risk Level | Action Required (i.e., Authentication Method) |
|---|---|---|---|
| 1 | Security questions | ||
| 2 | OTP token | ||
| 3 | Graphical password | ||
| 4 | Digital signature |
| Indexes | Measurements | Score |
|---|---|---|
| AV | Network (N) | 0.85 |
| Adjacent (A) | 0.62 | |
| Local (L) | 0.55 | |
| Physical (P) | 0.20 | |
| AC | Low (L) | 0.77 |
| High (H) | 0.44 | |
| PR | None (N) | 0.85 |
| Low (L) | 0.62 | |
| High (H) | 0.07 | |
| UI | None (N) | 0.85 |
| Required (R) | 0.62 |
| Cost | Measurements | Score |
|---|---|---|
| SI | Complete/Function/Null | 0.1/0.3/0.7 |
| SP | Common/Special/Particular | 0.15/0.35/0.6 |
| OR | Tool/Script/Manual/Corporation | 0.1/0.25/0.45/0.7 |
| IR | Null/Regular/Configuration/Critical | 0/0.2/0.55/0.8 |
| Measurements | Score |
|---|---|
| Information leakage | 0.3–0.55 |
| Remote register | 0.55–0.7 |
| Authentication bypass | 0.7–0.8 |
| Limited access | 0.85–0.95 |
| Root access | 1.0 |
| Step | Definition |
|---|---|
| Step 1 | Define the system of interest, regarding the cyberattacks and other events as initial conditional causes of failure in the security system. |
| Step 2 | Define the top event for the analysis and specify the problem of interest that the analysis will address. |
| Step 3 | Define the treetop structure. Determine the events and conditions (i.e., intermediate events) that lead most directly to the top event, which in this case can be faulty network and fault IS. |
| Step 4 | Explore each branch in successive levels of detail. Determine the events and conditions that lead most directly to each intermediate event. |
| Reference | Used Technique | Observations | Platform | |
|---|---|---|---|---|
| Smartphone | Other | |||
| Freeman et al. [33] | Probabilistic | Proposed to estimate a risk score for a login attempt in a web service to classify the login attempt into normal or suspicious, strengthening this way password-based authentication. Freeman et al. approach showed to be the most suitable for categorical data (i.e., IP address and useragent) for scalable and practical RBA solutions that can be used in large-scale online services. | x | |
| Arnes et al. [35] | Probabilistic; Hidden Markov Model | Proposed to estimate a real-time risk score approach for intrusion detection systems based on observations from network sensors, showing promising results. It can be the basis for automated response IDSs | x | |
| Chen et al. [34] | Probabilistic; Hidden Markov Model | Proposed to evaluate system risk based on software behavior using HMMs. The approach has demonstrated credible results for risk assessment in a quantitative manner and can be utilized in the actual risk assessment process for various applications. | x | |
| Mu et al. [38] | Probabilistic; D–S Evidence | Proposed for online risk assessment of intrusion scenarios. The deployment of the proposed risk assessment model enables IDAM&IRS to tolerate IDS false positive alerts setting the foundation for effective intrusion response decision-making. | x | |
| Acien et al. [40] | ML-based; Siamese Neural Networks | Proposed for keystroke dynamics behavioral biometric to effectively authenticate 100 K users typing free-text, when the amount of data per user is very limited: a common scenario in free-text keystroke authentication. Demonstrated efficient performance in terms of EER and computational time. Demonstrated potential use of SNN in risk-based user authentication based on behavioral biometrics. | x | |
| Misbahuddin et al. [49] | ML-based; Classification Algorithms | Proposed to determine the risk score every time the user sings-in in a web application. Demonstrated promising results in terms of effectively classifying the user as genuine or suspicious while ensuring usability. The authors deployed 3 classifiers, namely SVM, one-class SVM, and NB, and suggested that one-class SVM classifier is more efficient in real-world applications where there is not enough data for both classes (i.e., genuine and suspicious). | x | |
| Papaioannou et al. [48] | ML-based; Novelty Detection Algorithms | Proposed to estimate a real-time risk score in risk-based user authentication for smartphone devices. The deployed novelty detection algorithms demonstrated high-performance evaluation results. However, performance evaluation results of the whole REA component were not provided. | x | |
| Luo, Z. [65] | ML-based; Dynamic Bayesian Attach Graph | Efficient results compared to similar works of research in the literature. The used data were derived from CVSS standard. In addition to the value of the vulnerability, it also considered the cost and benefit of the attack to obtain a more accurate vulnerability assessment probability, which is more precise given an actual network attack. Ideal for handling time-dependent risk assessments, for instance when they are used in risk-based user authentication, they are able to present changes over time and relationships between a smartphone device’s current, past or future states. | x | |
| Iliadis L.S. [69] | Fuzzy Logic | Proposed for forest fire prediction. Suggested that the triangular and semi-triangular membership functions performed better than the trapezoidal and semi-trapezoidal membership functions. | x | |
| Shang et al. [72] | Fuzzy Logic | Suggested that fuzzy logic models can serve as a complementary approach to probability models, particularly in cases where data are limited and knowledge is incomplete. Fuzzy logic models provide a framework that allows human reasoning and imprecise data to contribute to efficient risk analysis in various applications, including risk-based user authentication. | x | |
| Haslum et al. [74] | Fuzzy Logic | Proposed for distributed intrusion prediction and prevention systems. Demonstrated to be very practical and highly effective in practice when it comes to protect assets which are highly at risk of misuse and/or attacks. | x | |
| Gehani et al. [76] | Non-Graph-based; Addition, Multiplication & Division | Proposed for achieving a systematic, fine-grained response by dynamically managing a host’s exposure to perceived threats. The approach has been shown to be highly effective in a series of attack scenarios, where risk is managed in real-time, leading to the containment of attacks. | x | |
| Goerdin et al. [80] | Monte Carlo Simulation | Capable of handling intricate and substantial systems. Able to regulate the uncertain behavior of multiple inputs to the system, which are considered constant values in analytical methods. | x | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Papaioannou, M.; Pelekoudas-Oikonomou, F.; Mantas, G.; Serrelis, E.; Rodriguez, J.; Fengou, M.-A. A Survey on Quantitative Risk Estimation Approaches for Secure and Usable User Authentication on Smartphones. Sensors 2023, 23, 2979. https://doi.org/10.3390/s23062979
Papaioannou M, Pelekoudas-Oikonomou F, Mantas G, Serrelis E, Rodriguez J, Fengou M-A. A Survey on Quantitative Risk Estimation Approaches for Secure and Usable User Authentication on Smartphones. Sensors. 2023; 23(6):2979. https://doi.org/10.3390/s23062979
Chicago/Turabian StylePapaioannou, Maria, Filippos Pelekoudas-Oikonomou, Georgios Mantas, Emmanouil Serrelis, Jonathan Rodriguez, and Maria-Anna Fengou. 2023. "A Survey on Quantitative Risk Estimation Approaches for Secure and Usable User Authentication on Smartphones" Sensors 23, no. 6: 2979. https://doi.org/10.3390/s23062979







