A Review of IoT Firmware Vulnerabilities and Auditing Techniques
Abstract
:1. Introduction
- Deliver an overview of the related work in multiple areas of firmware security including reverse engineering, tool development, auditing mechanisms, and preliminary yet relevant work in machine learning. The paper couples the inherent limitations of IoT environments with existing tools and auditing mechanisms.
- Present and analyze IoT firmware vulnerabilities across eight broad axes, their respective susceptibility triggers, and domain limitations based on prior literature. Although a number of prior studies do focus on particular aspects of the vulnerability spectrum, here the paper aims not only to define and categorize in terms of vulnerabilities, challenges, and corresponding mitigation measures, but also to map each of them with the exploitation vector and with the auditing tool that could help in identifying the vulnerability.
- Undertake a detailed software vulnerability analysis, discussing reverse engineering methods and the latest solutions and frameworks available in the static and dynamic vulnerability analysis domain. Hybrid vulnerability auditing approaches are presented, along with the limitations of state-of-the-art auditing techniques and recommendations for improving scalability, coverage, support, and automation. This is an area that has been traditionally overlooked as past approaches delivered solutions aimed at open systems with no resource limitations, while existing reverse-engineering tools focused on eliciting system behavior rather than identifying vulnerabilities.
- Summarize the state-of-the-art research in the area of IoT firmware security, including framework unification, multi-platform and multi-architecture support, tool management, machine learning and blockchain technology, all in the context of improving firmware security challenges, increasing vulnerability coverage, and providing potential recommendations for future research.
2. Related Works
- Interface security: Vulnerable interface identification in hardware, software, network, and application domains of IoT-ware represented the focality of studies in [29,31]. Some of the work in this area focuses on interface security and vulnerability solutions of consumer devices, detailing mechanisms for remote hijacking and control of IoT-ware, including surveillance nodes and general threats posed by IoT-specific malware [28,29,30,80]. Additionally, [31] provided a classification of existing solutions to detect IoT firmware threats, albeit without discussing corresponding solutions.
- Auditing techniques: Solutions describing the challenges in static [45,69,81,82] and dynamic auditing methods [33,38,83,84,85,86,87,88] have been proposed for IoT firmware vulnerability detection. Furthermore, to describing these fundamental vulnerability auditing techniques, some studies also highlighted the use of fuzzing technology and symbolic system execution to identify susceptibility in IoT-ware [84,89,90,91,92,93]. The primary efforts have been focused on assessing the effectiveness of different existing auditing methods and recommendations for developers/testers.
- Reverse engineering: Reverse engineering evaluation has been carried out on several commodity IoT devices to understand firmware vulnerabilities [94,95]. Employing fault injection, researchers have sought to identify the shortcomings of several vulnerabilities including weak authentication (password, PIN, etc.), device capability, and backdoors in IoT-ware [96,97]. System emulation schemes have also been the subject of research with a view to understand common challenges faced by developers and testers [38,87,98]. The tools and techniques employed for reverse engineering have been discussed in [19,25,94,95,96,99,100], providing basic discussion of pre-processing, de-compiling, unpacking, and evaluation techniques.
- Emerging applications: Ongoing advances in blockchain technology and machine learning technologies have also been topical areas of research in IoT-ware. Firmware data transmitted to IoT devices connected to a blockchain network is cryptographically proofed and signed by the true sender holding a unique public key, ensuring authentication and integrity of firmware [57,58,59,60,101,102]. When an IoT device needs to be updated, a smart contract [61] sends the hash or metadata file to that IoT device to obtain a copy of the update through peer-to-peer exchange with other nodes [58,59], or it is directly downloaded from the manufacturer’s server [62]. Bitcoin technology can also be employed to verify a firmware version before the update begins and to acknowledge a transaction before the IoT device can download and install it [57,101]. The studies [63,64] proposed direct and indirect firmware update distribution based on Ethereum blockchain. Similarly, Skipchain blockchain technology has also been proposed for secure trusted firmware updates using smart contracts [103].
- Commercial developments: In the commercial realm, TrustZone [73] by ARM has provided users a hardware-based security extension establishing a root of trust (RoT) and cryptographic services to securely store critical (firmware) data, which is an improvement over conventional trusted platform modules (TPM). TrustZone allows a wider set of hosted sensitive services driven by (hardware-based) isolation; however, an ever-expanding set of threats from secure-mode operation is not uncommon [74]. Similarly, Intel Turstlite [75], a generic security architecture suited to low-power embedded devices, allows remote management, authentication, and over the air (OTA) updating as well as remote attestation [76]. Among low-cost solutions, IoT-ware memory access control can also be implemented using SMART [79], using a ROM measurement routine with a secret key to provide remote attestation. However, SMART does not specifically deal with memory access violations or provide provisions for updating the attestation code [77] and, as discussed in [42,78], the verifier can also be malicious while the prover is benign, a significant limitation of remote attestation.
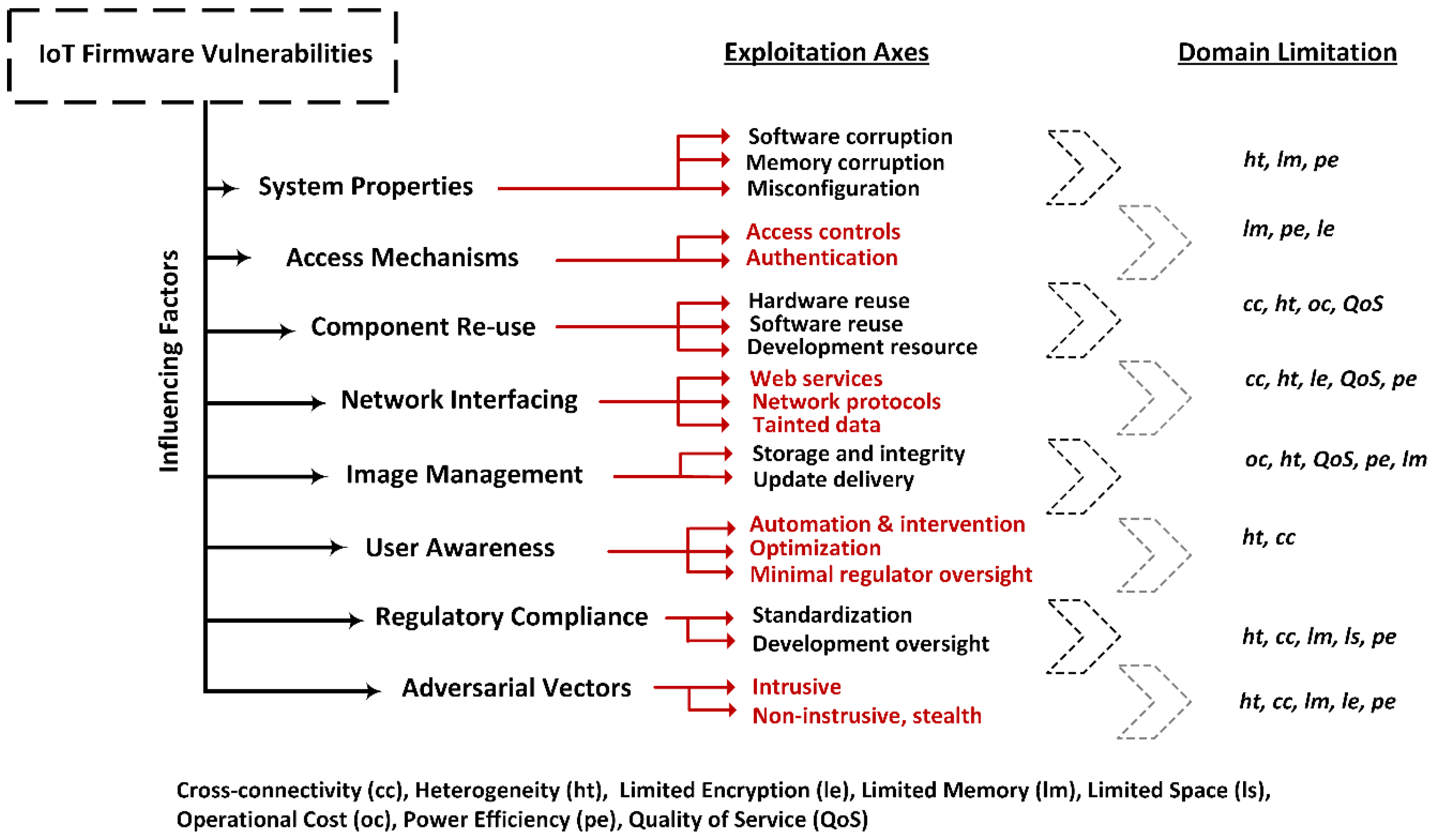
3. Firmware Vulnerability: Influences and Challenges
3.1. System Properties
- Software corruption: IoT firmware is inherently susceptible to software corruption, such as coding bugs introduced at service initiation or operation or during upgrades [29]. Coding bugs may introduce pointer violations, and type/format confusion, while programming related issues can also lead to malicious code injections, running of privileged commands and system failures. Tainted data and unexpected input can alter device behavior and further expose it to firmware threats.
- Memory management: Inefficient or corrupt coding can also lead to integer and buffer overflow, a common cause of security vulnerabilities further exacerbated by memory constraints inherent in IoT-ware [105]. Application requirements also may dictate implementing safety critical services in separate hardware chips [93,106]. While hardware-based trust management (HTM) is considered an optimal solution, the spatial and financial cost again might render it unfeasible for IoT-ware. Adopting HTM is also limited by the typical absence of dedicated Memory Management Units (MMU) in IoT systems, leading to frequent memory violations. Service isolation can also be offered solely in software, utilizing virtual memory and enabling monitoring of device sub-systems, allowing wider cryptographic support despite code-sharing on a single processor [79,106]. Additionally, dynamically establishing a root of trust by modifying the existing microcontroller units (MCU) using a hardware-software co-design approach is being used to allow greater flexibility and lesser spatial, as well as memory consumption for secure code execution. Using remote attestation techniques [76,78,107], detection and disabling of malicious code can be actioned before compromised execution.
- Misconfiguration: Domain limitations including limited memory, power efficiency and device heterogeneity need to be recognized during system configuration to mitigate some of the system vulnerability exploits discussed earlier. Misconfiguration of the system may lead to a successful exploitation.
3.2. Access Mechanisms
- Access control: IoT firmware access requires well-defined policies and suitable encryption to mitigate against password, certificate, or encryption key threats. The device manifest, containing author information and firmware update policy, if left un-encrypted, can lead to accessing, altering, or deleting vital metadata required for future authentication and upgrades to device firmware. Similarly, public certificate servers utilizing SSL (Secure Sockets Layer) certificates for provision of IoT-ware security may lead to man-in-the-middle attacks if repeatedly reused for a range of devices [81]. While vendors may also incorporate backdoor channels or push mechanisms to access devices for regular updates, such channels, if not protected by adequate credential management, may result in compromising device firmware or device data [85,108].
- Authentication: IoT-ware attacks due to weak authentication mechanisms are rather common [31]. Misconfigured and erroneous authentication routes allow control and jeopardizing of normal operation [108]. Weak authentication is usually due to resource constraints, allowing limited authentication schemes to conserve memory and processing power.
3.3. Component Re-Use
- Hardware and Software Re-use: Hardware and software components re-use, including off-the-shelf boards, circuitry, sensors, bootloaders, or software libraries, is prevalent among vendors to reduce development time and associated costs in the IoT domain [88], while inadvertently overlooking vulnerabilities arising due to heterogeneous cross-connectivity. In multi-controller systems, firmware from different manufacturers requires comprehensive security analysis and testing of each individual component. Firmware vulnerabilities in one controller or in exploitable software can lead to cascaded threats disrupting the entire operation and to the mass production of a range of insecure IoT devices [18].
- Development Resource: An ever-evolving set of IoT applications has also generally led to vendors frequently employing developers with limited expertise in developing high-quality firmware [16,34]. In addition, vendors also tend to overlook firmware vulnerabilities in favor of overall device usability and performance.
3.4. Network Interfacing
- Web Services: IoT devices communicate with cloud, fog, edge computing and monitoring systems over a range of web APIs. Insecure, poorly designed web services remain one of the leading causes of device exploitation, allowing service interruption via application-level and firmware-based attacks [33,35,100]. Prominent malware such as IoTReaper have successfully exploited IoT web interfacing to launch wide variety of attacks on device-ware [109]. Limited resources again hamper the adoption of multi-factor authentication incorporation in IoT-web interactions [46].
- Network Protocols: Vendors use a wide range of standardized and proprietary network protocols that, when combined with reusable hardware and software components, may lead to propagation of existing security issues in IoT-ware. Poor management of device network configuration, such as leaving open unused ports, may lead to security issues. The security firm Kaspersky reported that, in the first half of 2023, honeypots recorded that nearly 98% of the network-related attacks on IoT-ware occurred on the unsecure Telnet interface [43]. Over-the-air updates need to employ standardized and tested protocols that offer greater protection against man-in-the-middle and spoofing attacks while patching firmware.
- Tainted Data: The sensor and actuation services process incoming data that may require acquisition, perusal, validation, processing, and sanitization through associated fog and cloud nodes. Data acquired from sensory or actuator portals, if tainted or malformed, can overwhelm device operability and expose the device firmware to security risks [110].
3.5. Image Management
- Storage Integrity: IoT device firmware requires image storage integrity as well as secure distribution and updating to mitigate the threat exposure. Despite improvements in OTA mechanisms, device developers are generally reluctant to provide security patching as a continual maintenance service [47]. Given the significant lifespan of IoT operations, devices may be running obsolete firmware several years old that has several discovered, widely acknowledged flaws. Where OTA updates and encryption mechanisms are available, the network protocols also need to be tested for security compliance and suitable encryption. As an example, investigations by the security community identified that the update protocol for the popular FitBit devices is prone to hacking despite using end-to-end encryption [111]. Firmware image integrity is a strict requirement to avoid attempts at flashing or modifying existing images from unwarranted sources, protecting image confidentiality from adversaries recovering plain text binaries.
- Update Delivery: The process of firmware update, where available, can be used as an attack delivery option, as it can be initiated by the customer, pushed from a server, or follow a hybrid approach; in addition, vendors may introduce provisions for backdoor updating of device firmware [64,103,112]. While not an intrinsic vulnerability, having firmware downloads available publicly may also offer an insight into the libraries, settings, and functionality to launch sophisticated attacks. Lack of coordination between the operating parties, server and network downtime, and device outages can also lead to inconsistencies in update tracking, causing unnecessary delays to firmware updating.
3.6. User Awareness
- Automation and Intervention: An efficient device update process requires a balance between automation and human intervention, whereby large-scale updates should be performed using minimal manual intervention. To optimize decision making, necessary provisions for manual intervention can be kept, while maximizing de-facto upgrade policies using dynamic updates to be applied as released. Users can also be incentivized to update by flagging the risks that they expose themselves to in case of non-compliance.
- Optimization: Incorrect operational settings such as disabling or reducing event logging to conserve energy makes post-incident analysis difficult and prone to errors. A significant number of IoT vendors provide devices without any user guidelines for updating configuration parameters based on usage. Opting for default settings, ranging from generic authentication passwords, switched off update notifications, or outdated web applications, vendors pass the responsibility and burden of device firmware updates to the end-user. However, as widely acknowledged in the literature, firmware adjustments are rarely considered or applied by everyday users [23,28,112]. A general improvement in the set of guidelines to provide the user with sufficient information to secure their devices is nonetheless vital and consortiums such as IoT Alliance Australia issued specific user guidelines on the maintenance and operation of IoT firmware updating and help in identifying firmware hijacking [113].
3.7. Regulatory Compliance
- Standardization: Existing IoT-ware regulations have been introduced by commercial and governmental organizations including OWASP (Open Web Application Security Project), IoT Security Foundation, and NIST (National Institute of Standards and Technology). Standardization bodies have provided operational guidelines as well as best-practice mechanisms to provide secure IoT systems; however, these have not been widely adopted due to limited regulation. On a similar note, inadequate and inefficient compliance resulted in insecure booting, minimal or no encryption, and outdated firmware. Enforcing security compliance as part of IoT-related products engineering, development frameworks, and business policies requires greater regulatory oversight by governmental and non-governmental bodies which are usually beyond the scope of standardization organizations.
- Development Oversight: Vendors with inadequate experience in the IoT domain have been mass producing devices without adequate security inclusion [94,114,115]. A separate category of oversight challenges is linked to the design and manufacturing process. Hardware device manufacturing and software provision tend to be rather independent processes and coordination issues between original device manufacturers (ODM) and original equipment manufacturers (OEM) may result in overlooking firmware flaws. Code developed and supplied by ODMs may contain security loopholes that, when used and implemented by OEMs, may result in replication across thousands of commercial devices [16,35].
3.8. Adversarial Vector
- Local and Remote Vectors: Remote or over the network adversarial factors can infect systems via malware, while local adversaries can eavesdrop and interfere with device communication [107]. Stealth-based adversaries can attack either from closer physical proximity or remotely, masquerading as an authentic entity and gain unwarranted access to the IoT ecosystem [79].
- Side-channeling: Similarly, side-channel attacks can be carried out by a physical non-intrusive entity, while an intrusive adversary can completely overtake an authentication mechanism to prove its identity to an IoT device aiming to solicit information or exploit device behavior through hardware-software modification [79].
- Hybrid Designs: Dedicated hardware and software security have associated cost implications; the inherent spatial, financial, and power efficiency compromises for IoT-ware require careful trading off. A combinatorial approach using a mix of hardware and software-based controls to address adversarial threats is often considered to be a more viable option compared to purely hardware-based security or an entirely software-oriented security primitive [107].
3.9. Domain Limitations and Associated Impact
4. Vulnerability Auditing
4.1. Reverse Engineering
4.1.1. Firmware Acquisition
4.1.2. Firmware Unpacking
4.1.3. Decompiling
4.1.4. Challenges
- Packing logic: packers do not modify the code functionality, making presentation of the code sequential and not readily human-legible for security analysis. Therefore, use of automated dynamic analysis as opposed to manual perusal can yield better results, providing auditing scalability for a multitude of firmware solutions [104]. Testing frameworks, including FAT [49] and QEMU [125], simplify the analysis by incorporating several vulnerability assessments tools and emulation.
- Mitigation techniques: In addition to cryptic packing, vendors may resort to de-compilation mitigation, adding to firmware source inspection obstacles.
- Metadata unavailability: Masquerading device meta-data to avoid hardware-based hacking can inadvertently complicate the security auditing process [94,129] by limiting information on product release, update log and version number, and hardware architecture for de-compiler selection [132]. Intuitively assuming protocols, OS and libraries and other data inputs are used to analyze the device for security vulnerabilities is therefore common, as is brute-force fuzzing using genetic algorithms such as the American Fuzzy Lop (AFL) fuzzer [126] that aids when randomizing input testing. The scope, applicability, and operational capability of auditing techniques remains vital to firmware vulnerability assessment and device protection.
4.2. Auditing Techniques
4.2.1. Static Analysis
4.2.2. Dynamic Analysis
| Tool | Year | Analysis Method | Target Vulnerab. | SC. | UV. | PV. | Architecture |
|---|---|---|---|---|---|---|---|
| FIE [92] | 2013 | Symbolic execution | Memory bugs | Partly | Yes | Yes | MSP430 |
| Avatar [85] | 2014 | Emulation | Any | Partly | Yes | Yes | Multiple |
| Firmadyne [141] | 2016 | Emulation | Multi-domain | Yes | Yes | Yes | ARM MIPS |
| Dynamic auto. [33] | 2016 | Emulation | Web vulnerability | Yes | Partly | Partly | Multiple |
| Multi-stager [99] | 2016 | Binary analysis, virtualization | Industrial IoT systems | Yes | Yes | Yes | Multiple |
| FIoT [142] | 2016 | Symbolic execution | Memory corruption | Yes | Partly | No | Multiple |
| P2IM [86] | 2017 | Abstraction model | Any | Partly | Yes | Yes | Multiple |
| DICE [38] | 2021 | Abstraction model | Any | Yes | Yes | Yes | Multiple |
| HALucinator [87] | 2020 | HAL, Emulation | Any | Yes | Yes | Yes | Multiple |
| PRETENDER [88] | 2018 | Emulation | Any | Yes | Yes | Partly | Multiple |
| Laelaps [98] | 2020 | Symbolic execution | Any | Yes | Yes | Yes | Multiple |
| µEmu [140] | 2021 | Symbolic execution | Any | Yes | Yes | Partly | Multiple |
| Gerbil [88] | 2019 | Symbolic execution | Any | Partly | Yes | Yes | Multiple |
4.2.3. Hybrid Proposals
4.3. Discussion of Auditing Techniques
5. Contemporary Research and Open Challenges
5.1. Standardization
5.1.1. Unification
5.1.2. Firmware Stack and Instruction Set
5.2. Technical Redressal
5.2.1. Analysis Methodologies
5.2.2. Secure Ecosystem
5.2.3. Tool Management and Data Collection
5.3. Design Innovations
5.3.1. Operating Systems and Platforms
5.3.2. Emulation Support
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Trasvi-Moreno, C.A.; Blasco, R.; Casas, R.; Marco, A. Autonomous WiFi Sensor for Heating Systems in the Internet of Things. J. Sensors 2016, 2016, 7235984. [Google Scholar] [CrossRef]
- AlLifah, N.M.; Zualkernan, I. Ranking Security of IoT-based Smart Home Consumer Devices. IEEE Access 2022, 10, 18352–18369. [Google Scholar] [CrossRef]
- Das, A.; Sharma, S.C.M.; Ratha, B.K. The new era of smart cities, from the perspective of the internet of things. In Smart Cities Cybersecurity and Privacy; Elsevier: Amsterdam, The Netherlands, 2018; pp. 1–9. [Google Scholar] [CrossRef]
- Jeyaraj, P.R.; Nadar, E.R.S. Smart-Monitor: Patient Monitoring System for IoT-Based Healthcare System Using Deep Learning. IETE J. Res. 2022, 68, 1435–1442. [Google Scholar] [CrossRef]
- TajDini, M.; Sokolov, V.; Kuzminykh, I.; Shiaeles, S.; Ghita, B. Wireless Sensors for Brain Activity-A Survey. Electronics 2020, 9, 2092. [Google Scholar] [CrossRef]
- Pradha, S.E.; Moshika, A.; Natarajan, B.; Andal, K.; Sambasivam, G.; Shanmugam, M. Scheduled Access Strategy for Improving Sensor Node Battery Lifetime and Delay Analysis of Wireless Body Area Network. IEEE Access 2022, 10, 3459–3468. [Google Scholar] [CrossRef]
- Ni, Y.; Cai, L.; He, J.; Vinel, A.; Li, Y.; Mosavat-Jahromi, H.; Pan, J. Toward Reliable and Scalable Internet of Vehicles: Performance Analysis and Resource Management. Proc. IEEE 2020, 108, 324–340. [Google Scholar] [CrossRef]
- Kuzminykh, I. Development of traffic light control algorithm in smart municipal network. In Proceedings of the 2016 13th International Conference on Modern Problems of Radio Engineering, Telecommunications and Computer Science (TCSET), Lviv, Ukraine, 23–26 February 2016; pp. 896–898. [Google Scholar] [CrossRef]
- Hunzinger, R. Scada fundamentals and applications in the IoT. In Internet of Things and Data Analytics Handbook; Wiley: Hoboken, NJ, USA, 2017; pp. 283–293. [Google Scholar] [CrossRef]
- Liberg, O.; Wang, Y.P.E.; Sachs, J.; Sundberg, M.; Bergman, J. Cellular Internet of Things—Technologies, Standards and Performance; Academic Press: Cambridge, MA, USA, 2017; Chapter 9; pp. 327–360. [Google Scholar] [CrossRef]
- Chaudhari, B.S.; Zennaro, M. LPWAN Technologies for IoT and M2M Applications; Academic Press: Cambridge, MA, USA, 2020. [Google Scholar] [CrossRef]
- Kshetri, N. The evolution of the internet of things industry and market in China: An interplay of institutions, demands and supply. Telecommun. Policy 2017, 41, 49–67. [Google Scholar] [CrossRef]
- Kuzminykh, I.; Ghita, B.; Such, J.M. The Challenges with Internet of Things Security for Business. In Internet of Things, Smart Spaces, and Next Generation Networks and Systems; Koucheryavy, Y., Balandin, S., Andreev, S., Eds.; Springer: Cham, Switzerland, 2022; LNCS; Volume 13158, pp. 46–58. [Google Scholar] [CrossRef]
- Sørensen, A.; Wang, H.; Remy, M.J.; Kjettrup, N.; Sørensen, R.B.; Nielsen, J.J.; Popovski, P.; Madueño, G.C. Modelling and Experimental Validation for Battery Lifetime Estimation in NB-IoT and LTE-M. IEEE Internet Things J. 2022, 9, 9804–9819. [Google Scholar] [CrossRef]
- Kuzminykh, I.; Yevdokymenko, M.; Sokolov, V. Encryption Algorithms in IoT: Security vs. Lifetime. Available online: https://ssrn.com/abstract=4636161 (accessed on 29 November 2023).
- Gupta, A.; Guzman, A. IoT Penetration Testing Cookbook: Identify Vulnerabilities and Secure Your Smart Devices; Packt Publishing: Birmingham, UK, 2017; ISBN 9781787280571. [Google Scholar]
- Abdul-Ghani, H.A.; Konstantas, D.; Mahyoub, M. A comprehensive IoT attacks survey based on a building-blocked reference model. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 355–373. [Google Scholar] [CrossRef]
- Adat, V.; Gupta, B.B. Security in Internet of Things: Issues, challenges, taxonomy, and architecture. Telecommun. Syst. 2018, 67, 423–441. [Google Scholar] [CrossRef]
- Ammar, M.; Russello, G.; Crispo, B. Internet of Things: A survey on the security of IoT frameworks. J. Inf. Secur. Appl. 2018, 38, 8–27. [Google Scholar] [CrossRef]
- Kuzminykh, I.; Carlsson, A.; Yevdokymenko, M.; Sokolov, V. Investigation of the IoT Device Lifetime with Secure Data Transmission. In Internet of Things, Smart Spaces, and Next Generation Networks and Systems (NEW2AN/ruSMART 2019); Galinina, O., Andreev, S., Balandin, S., Koucheryavy, Y., Eds.; Springer: Cham, Switzerland, 2019; LNCS; Volume 11660, pp. 16–27. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Ling, Z.; Liu, K.; Xu, Y.; Jin, Y.; Fu, X. An End-to-End View of IoT Security and Privacy. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Microsoft. Security Signals March 2021. Available online: https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RWPStZ (accessed on 29 November 2023).
- Rothman, M.; Zimmer, V. Understanding UEFI Firmware Update and Its Vital Role in Keeping Computing Systems Secure. Available online: https://embeddedcomputing.com/technology/security/software-security/understanding-uefi-firmware-update-and-its-vital-role-in-keeping-computing-systems-secure (accessed on 15 October 2023).
- Vasile, S.; Oswald, D.; Chothia, T. Breaking All the Things-A Systematic Survey of Firmware Extraction Techniques for IoT Devices. In Smart Card Research and Advanced Applications; Springer: Cham, Switzerland, 2019; pp. 171–185. [Google Scholar] [CrossRef]
- Quantum IoT Protect Firmwar—Security Risk Assessment. Available online: https://pages.checkpoint.com/iot-firmware-risk-assessment.html (accessed on 29 November 2023).
- Arias, O.; Wurm, J.; Hoang, K.; Jin, Y. Privacy and security in internet of things and wearable devices. IEEE Trans. Multi-Scale Comput. Syst. 2015, 1, 99–109. [Google Scholar] [CrossRef]
- Costin, A.; Zaddach, J. IoT Malware: Comprehensive Survey, Analysis Framework and Case Studies. In Proceedings of the Black Hat USA 2018, Las Vegas, NV, USA, 4–9 August 2018; pp. 1–7. Available online: http://firmware.re/malw/bh18us_costin.pdf (accessed on 29 November 2023).
- Yu, M.; Zhuge, J.; Cao, M.; Shi, Z.; Jiang, L. A Survey of Security Vulnerability Analysis, Discovery, Detection, and Mitigation on IoT Devices. Future Internet 2020, 12, 27. [Google Scholar] [CrossRef]
- Mohanty, A.; Obaidat, I.; Yilmaz, F.; Sridhar, M. Control-hijacking vulnerabilities in IoT firmware: A brief survey. In Proceedings of the 1st International Workshop on Security and Privacy for the Internet-of-Things, Orlando, FL, USA, 17–20 April 2020; pp. 1–42018. [Google Scholar]
- Xie, W.; Jiang, Y.; Tang, Y.; Ding, N.; Gao, Y. Vulnerability Detection in IoT Firmware: A Survey. In Proceedings of the 2017 IEEE 23rd International Conference on Parallel and Distributed Systems (ICPADS), Shenzhen, China, 15–17 December 2017; pp. 769–772. [Google Scholar] [CrossRef]
- Wright, C.; Moeglein, W.A.; Bagchi, S.; Kulkarni, M.; Clements, A.A. Challenges in Firmware Re-Hosting, Emulation, and Analysis. ACM Comput. Surv. 2021, 54, 5. [Google Scholar] [CrossRef]
- Costin, A.; Zarras, A.; Francillon, A. Automated dynamic firmware analysis at scale: A case study on embedded web interfaces. In Proceedings of the 11th ACM Asia Conference on Computer and Communications Security (ASIA CCS), Xi’an, China, 30 May–3 June 2016; pp. 437–448. [Google Scholar] [CrossRef]
- Gupta, A. The IoT Hacker’s Handbook—A Practical Guide to Hacking the Internet of Things; Apress: Berkeley, CA, USA, 2019. [Google Scholar] [CrossRef]
- Hamada, R.; Kuzminykh, I. Exploitation Techniques of IoST Vulnerabilities in Air-Gapped Networks and Security Measures—A Systematic Review. Signals 2023, 4, 687–707. [Google Scholar] [CrossRef]
- Hicken, A. How Does Static Analysis Prevent Defects & Accelerate Delivery? Available online: https://www.parasoft.com/blog/how-does-static-analysis-prevent-defects-and-accelerate-delivery/ (accessed on 1 December 2023).
- Sockut, G.H. Firmware/hardware support for operating systems. ACM SIGMICRO Newsl. 1975, 6, 17–26. [Google Scholar] [CrossRef]
- Mera, A.; Feng, B.; Lu, L.; Kirda, E. DICE: Automatic Emulation of DMA Input Channels for Dynamic Firmware Analysis. In Proceedings of the 2021 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 24–27 May 2021; pp. 1938–1954. [Google Scholar] [CrossRef]
- gdb(1)—Linux Man Page. Available online: https://linux.die.net/man/1/gdb (accessed on 1 December 2023).
- Xu, X.; Liu, C.; Feng, Q.; Yin, H.; Song, L.; Song, D. Neural Network-based Graph Embedding for Cross-Platform Binary Code Similarity Detection. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 363–376. [Google Scholar] [CrossRef]
- Wang, Y.; Shen, J.; Lin, J.; Lou, R. Staged Method of Code Similarity Analysis for Firmware Vulnerability Detection. IEEE Access 2019, 7, 14171–14185. [Google Scholar] [CrossRef]
- Hristozov, S.; Heyszl, J.; Wagner, S.; Sigl, G. Practical Runtime Attestation for Tiny IoT Devices. In Proceedings of the NDSS Workshop on Decentralized IoT Security and Standards (DISS), San Diego, CA, USA, 18 February 2018. [Google Scholar] [CrossRef]
- Kaspersky Unveils an Overview of IoT-Related Threats in 2023. Available online: https://www.kaspersky.com/about/press-releases/2023_kaspersky-unveils-an-overview-of-iot-related-threats-in-2023 (accessed on 15 October 2023).
- Egele, M.; Scholte, T.; Kirda, E.; Kruegel, C. A survey on automated dynamic malware-analysis techniques and tools. ACM Comput. Surv. 2012, 44, 6. [Google Scholar] [CrossRef]
- Thomas, S.L.; Garcia, F.D.; Chothia, T. HumIDIFy: A Tool for Hidden Functionality Detection in Firmware. In Detection of Intrusions and Malware, and Vulnerability Assessment (DIMVA 2017); Polychronakis, M., Meier, M., Eds.; Springer: Cham, Switzerland, 2017; Volume 10327, pp. 279–300. [Google Scholar] [CrossRef]
- Barcena, M.; Wueest, C. Insecurity in the Internet of Things, Symantec Report. Available online: https://docs.broadcom.com/doc/insecurity-in-the-internet-of-things-en (accessed on 1 December 2023).
- Lezzi, M.; Lazoi, M.; Corallo, A. Cybersecurity for Industry 4.0 in the current literature: A reference framework. Comput. Ind. 2018, 103, 97–110. [Google Scholar] [CrossRef]
- Cadar, C.; Dunbar, D.; Engler, D. KLEE: Unassisted and Automatic Generation of High-Coverage Tests for Complex Systems Programs. In Proceedings of the 8th USENIX Symposium on Operating Systems Design and Implementation (OSDI), San Diego, CA, USA, 8–10 December 2008; pp. 209–224. [Google Scholar]
- FAT: Firmware Analysis Toolkit. Available online: https://github.com/attify/firmware-analysis-toolkit (accessed on 1 December 2023).
- Zheng, M.; Sun, M.; Lui, J.C.S. DroidRay: A security evaluation system for customized android firmwares. In Proceedings of the 9th ACM Symposium on Information, Computer and Communications Security (ASIA CCS), Kyoto, Japan, 4–6 June 2014; pp. 471–482. [Google Scholar]
- Zheng, Y.; Davanian, A.; Yin, H.; Song, C.; Zhu, H.; Sun, L. FIRM-AFL: High-throughput greybox fuzzing of IoT firmware via augmented process emulation. In Proceedings of the 28th USENIX Conference on Security Symposium, Santa Clara, CA, USA, 14–16 August 2019; pp. 1099–1114. [Google Scholar]
- Cheng, K.; Li, Q.; Wang, L.; Chen, Q.; Zheng, Y.; Sun, L.; Liang, Z. DTaint: Detecting the Taint-Style Vulnerability in Embedded Device Firmware. In Proceedings of the 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Luxembourg, 25–28 June 2018; pp. 430–441. [Google Scholar] [CrossRef]
- Celik, Z.B.; Babun, L.; Sikder, A.K.; Aksu, H.; Tan, G.; McDaniel, P.; Uluagac, A.S. Sensitive Information Tracking in Commodity IoT. In Proceedings of the 27th USENIX Conference on Security Symposium, Baltimore, MD, USA, 15–17 August 2018; pp. 1687–1704. [Google Scholar]
- IoT Inspector. Security Analysis for IoT Devices. Completely Automated. Available online: https://level5tech.com/iot-inspector/ (accessed on 1 December 2023).
- FIRMALYZER. Discover IoT/Connected Devices, Their CVEs and Their Firmware Risks. Available online: https://firmalyzer.com/ (accessed on 1 December 2023).
- Smith, C. Firmwalker: Script for Searching the Extracted Firmware File System for Goodies! Available online: https://github.com/craigz28/firmwalker (accessed on 1 December 2023).
- Boudguiga, A.; Bouzerna, N.; Granboulan, L.; Olivereau, A.; Quesnel, A.; Roger, A.; Sirdey, R. Towards Better Availability and Accountability for IoT Updates by Means of a Blockchain. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Paris, France, 26–28 April 2017; pp. 50–58. [Google Scholar] [CrossRef]
- Choi, S.; Lee, J.H. Blockchain-Based Distributed Firmware Update Architecture for IoT Devices. IEEE Access 2020, 8, 37518–37525. [Google Scholar] [CrossRef]
- Fukuda, T.; Omote, K. Efficient Blockchain-based IoT Firmware Update Considering Distribution Incentives. In Proceedings of the 2021 IEEE Conference on Dependable and Secure Computing (DSC), Aizuwakamatsu, Japan, 30 January–2 February 2021; pp. 1–8. [Google Scholar] [CrossRef]
- Cao, B.; Liu, W.; Peng, M. Blockchain Driven Internet of Things. In Wireless Blockchain: Principles, Technologies and Applications; Imran, M.A., Cao, B., Zhang, L., Peng, M., Eds.; John Wiley & Sons, Ltd.: Hoboken, NJ, USA, 2021; pp. 93–115. [Google Scholar] [CrossRef]
- Ream, J.; Chu, Y.; Schatsky, D. Upgrading Blockchains: Smart Contract Use Cases in Industry; Deloitte University Press: Westlake, TX, USA, 2016; Available online: https://www2.deloitte.com/us/en/insights/focus/signals-for-strategists/using-blockchain-for-smart-contracts.html (accessed on 1 December 2023).
- Witanto, E.N.; Oktian, Y.E.; Lee, S.-G.; Lee, J.-H. A Blockchain-Based OCF Firmware Update for IoT Devices. Appl. Sci. 2020, 10, 6744. [Google Scholar] [CrossRef]
- Yohan, A.; Lo, N.-W. An Over-the-Blockchain Firmware Update Framework for IoT Devices. In Proceedings of the 2018 IEEE Conference on Dependable and Secure Computing (DSC), Kaohsiung, Taiwan, 10–13 December 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Yohan, A.; Lo, N.-W. FOTB: A secure blockchain-based firmware update framework for IoT environment. Int. J. Inf. Secur. 2020, 19, 257–278. [Google Scholar] [CrossRef]
- Sutherland, I.; Kalb, G.E.; Blyth, A.; Mulley, G. An empirical examination of the reverse engineering process for binary files. Comput. Secur. 2006, 25, 221–228. [Google Scholar] [CrossRef]
- Chess, B.; Mcgraw, G. Static analysis for security. IEEE Secur. Priv. 2004, 2, 76–79. [Google Scholar] [CrossRef]
- Chen, H.; Dean, D.; Wagner, D. Model Checking One Million Lines of C Code. In Proceedings of the NDSS Symposium 2004, San Diego, CA, USA, 5 February 2004; pp. 171–185. [Google Scholar]
- Fagbuyiro, D. Benefits of Using Static Code Analysis Tools for Software Testing. Available online: https://www.stickyminds.com/article/benefits-using-static-code-analysis-tools-software-testing (accessed on 1 December 2023).
- Cojocar, L.; Zaddach, J.; Verdult, R.; Bos, H.; Francillon, A.; Balzarotti, D. PIE: Parser Identification in Embedded Systems. In Proceedings of the 31st Annual Computer Security Applications Conference, New York, NY, USA, 7–11 December 2015; pp. 251–260. [Google Scholar] [CrossRef]
- Miettinen, M.; Marchal, S.; Hafeez, I.; Frassetto, T.; Asokan, N.; Sadeghi, A.-R.; Tarkoma, S. IoT Sentinel Demo: Automated Device-Type Identification for Security Enforcement in IoT. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 2511–2514. [Google Scholar] [CrossRef]
- Costin, A.; Zarras, A.; Francillon, A. Towards Automated Classification of Firmware Images and Identification of Embedded Devices. In ICT Systems Security and Privacy Protection (SEC 2017); De Capitani di Vimercati, S., Martinelli, F., Eds.; Springer: Cham, Switzerland, 2017; IFIP AICT; Volume 502, pp. 233–247. [Google Scholar] [CrossRef]
- Lee, S.; Paik, J.-Y.; Jin, R.; Cho, E.-S. Toward Machine Learning Based Analyses on Compressed Firmware. In Proceedings of the 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019; pp. 586–591. [Google Scholar] [CrossRef]
- Pinto, S.; Santos, N. Demystifying Arm TrustZone: A Comprehensive Survey. ACM Comput. Surv. 2019, 51, 130. [Google Scholar] [CrossRef]
- Koutroumpouchos, N.; Ntantogian, C.; Xenakis, C. Building Trust for Smart Connected Devices: The Challenges and Pitfalls of TrustZone. Sensors 2021, 21, 520. [Google Scholar] [CrossRef] [PubMed]
- Koeberl, P.; Schulz, S.; Sadeghi, A.-R.; Varadharajan, V. TrustLite: A security architecture for tiny embedded devices. In Proceedings of the 9th European Conference on Computer Systems, Amsterdam, The Netherlands, 14–16 April 2014; pp. 1–14. [Google Scholar] [CrossRef]
- Dushku, E.; Østergaard, J.H.; Dragoni, N. Memory Offloading for Remote Attestation of Multi-Service IoT Devices. Sensors 2022, 22, 4340. [Google Scholar] [CrossRef] [PubMed]
- Brasser, F.; Rasmussen, K.B.; Sadeghi, A.-R.; Tsudik, G. Remote attestation for low-end embedded devices: The prover’s perspective. In Proceedings of the 53rd Annual Design Automation Conference, Austin, TX, USA, 5–9 June 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Conti, M.; Dushku, E.; Mancini, L.V.; Rabbani, M.; Ranise, S. Remote Attestation as a Service for IoT. In Proceedings of the 2019 Sixth International Conference on Internet of Things: Systems, Management and Security (IOTSMS), Granada, Spain, 22–25 October 2019; pp. 320–325. [Google Scholar] [CrossRef]
- Eldefrawy, K.; Tsudik, G.; Francillon, A.; Perito, D. SMART: Secure and Minimal Architecture for (Establishing Dynamic) Root of Trust. In Proceedings of the NDSS Symposium 2019, San Diego, CA, USA, 24–27 February 2019. [Google Scholar]
- Costin, A. Security of CCTV and Video Surveillance Systems: Threats, Vulnerabilities, Attacks, and Mitigations. In Proceedings of the 6th International Workshop on Trustworthy Embedded Devices, Vienna, Austria, 28 October 2016; pp. 45–54. [Google Scholar] [CrossRef]
- Costin, A.; Zaddach, J.; Francillon, A.; Balzarotti, D. Large Scale Security Analysis of Embedded Devices’ Firmware. In Proceedings of the 23rd USENIX Conference on Security Symposium, San Diego, CA, USA, 20–22 August 2014; pp. 95–110. [Google Scholar]
- David, Y.; Partush, N.; Yahav, E. FirmUp: Precise Static Detection of Common Vulnerabilities in Firmware. ACM SIGPLAN Not. 2018, 53, 392–404. [Google Scholar] [CrossRef]
- Chen, D.D.; Woo, M.; Brumley, D.; Egele, M. Towards Automated Dynamic Analysis for Linux-based Embedded Firmware. In Proceedings of the NDSS Symposium 2016, San Diego, CA, USA, 21–24 February 2016. [Google Scholar]
- Gui, Z.; Shu, H.; Kang, F.; Xiong, X. FIRMCORN: Vulnerability-Oriented Fuzzing of IoT Firmware via Optimized Virtual Execution. IEEE Access 2020, 8, 29826–29841. [Google Scholar] [CrossRef]
- Zaddach, J.; Bruno, L.; Francillon, A.; Balzarotti, D. AVATAR: A Framework to Support Dynamic Security Analysis of Embedded Systems’ Firmwares. In Proceedings of the NDSS Symposium 2014, San Diego, CA, USA, 23–24 February 2014. [Google Scholar]
- Feng, B.; Mera, A.; Lu, L. P2IM: Scalable and Hardware-independent Firmware Testing via Automatic Peripheral Interface Modeling. In Proceedings of the 29th USENIX Conference on Security Symposium, Boston, MA, USA, 12–14 August 2020; pp. 1237–1254. [Google Scholar]
- Clements, A.A.; Gustafson, E.; Scharnowski, T.; Grosen, P.; Fritz, D.; Kruegel, C.; Vigna, G.; Bagchi, S.; Payer, M. HALucinator: Firmware Re-hosting Through Abstraction Layer Emulation. In Proceedings of the 29th USENIX Conference on Security Symposium, Boston, MA, USA, 12–14 August 2020; pp. 1201–1218. [Google Scholar]
- Gustafson, E.; Muench, M.; Spensky, C.; Redini, N.; Machiry, A.; Fratantonio, Y.; Balzarotti, D.; Francillon, A.; Choe, Y.R.; Kruegel, C.; et al. Toward the Analysis of Embedded Firmware through Automated Re-hosting. In Proceedings of the 22nd International Symposium on Research in Attacks, Intrusions and Defenses (RAID), Beijing, China, 23–25 September 2019; pp. 135–150. [Google Scholar]
- Liu, X.; Cui, B.; Fu, J.; Ma, J. HFuzz: Towards automatic fuzzing testing of NB-IoT core network protocols implementations. Future Gener. Comput. Syst. 2020, 108, 390–400. [Google Scholar] [CrossRef]
- Maier, D.; Radtke, B.; Harren, B. Unicorefuzz: On the viability of emulation for kernel space fuzzing. In Proceedings of the 13th USENIX Workshop on Offensive Technologies, Santa Clara, CA, USA, 12–13 August 2019; p. 8. [Google Scholar]
- Wang, D.; Zhang, X.; Chen, T.; Li, J. Discovering Vulnerabilities in COTS IoT Devices through Blackbox Fuzzing Web Management Interface. Secur. Commun. Netw. 2019, 2019, 5076324. [Google Scholar] [CrossRef]
- Davidson, D.; Moench, B.; Jha, S.; Ristenpart, T. FIE on firmware: Finding vulnerabilities in embedded systems using symbolic execution. In Proceedings of the 22nd USENIX Conference on Security Symposium, Washington, DC, USA, 14–16 August 2013; pp. 463–478. [Google Scholar]
- Yao, Y.; Zhou, W.; Jia, Y.; Zhu, L.; Liu, P.; Zhang, Y. Identifying Privilege Separation Vulnerabilities in IoT Firmware with Symbolic Execution. In Computer Security—ESORICS 2019; Sako, K., Schneider, S., Ryan, P., Eds.; Springer: Cham, Switzerland, 2019; Volume 11735, pp. 638–657. [Google Scholar] [CrossRef]
- Shwartz, O.; Mathov, Y.; Bohadana, M.; Elovici, Y.; Oren, Y. Reverse Engineering IoT Devices: Effective Techniques and Methods. IEEE Internet Things J. 2018, 5, 4965–4976. [Google Scholar] [CrossRef]
- Zaddach, J.; Costin, A. Embedded Devices Security and Firmware Reverse Engineering. In Proceedings of the Black Hat USA 2013, Las Vegas, NV, USA, 31 July–1 August 2013. [Google Scholar]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT Security: An Exhaustive Survey on IoT Vulnerabilities and a First Empirical Look on Internet-Scale IoT Exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Makhdoom, I.; Abolhasan, M.; Lipman, J.; Liu, R.P.; Ni, W. Anatomy of Threats to the Internet of Things. IEEE Commun. Surv. Tutor. 2019, 21, 1636–1675. [Google Scholar] [CrossRef]
- Cao, C.; Guan, L.; Ming, J.; Liu, P. Device-agnostic Firmware Execution is Possible: A Concolic Execution Approach for Peripheral Emulation. In Proceedings of the 36th Annual Computer Security Applications Conference, Austin, TX, USA, 7–11 December 2020; pp. 746–759. [Google Scholar] [CrossRef]
- Palavicini, G., Jr.; Bryan, J.; Sheets, E.; Kline, M.; San Miguel, J. Towards Firmware Analysis of Industrial Internet of Things (IIoT)–Applying Symbolic Analysis to IIoT Firmware Vetting. In Proceedings of the 2nd International Conference on Internet of Things, Big Data and Security (IoTBDS 2017), Porto, Portugal, 24–26 April 2017; pp. 470–477. [Google Scholar]
- Wang, Z.; Zhang, Y.; Tian, Z.; Ruan, Q.; Liu, T.; Wang, H.; Liu, Z.; Lin, J.; Fang, B.; Shi, W. Automated Vulnerability Discovery and Exploitation in the Internet of Things. Sensors 2019, 19, 3362. [Google Scholar] [CrossRef] [PubMed]
- Lee, B.; Lee, J.H. Blockchain-based secure firmware update for embedded devices in an Internet of Things environment. J. Supercomput. 2017, 73, 1152–1167. [Google Scholar] [CrossRef]
- Lee, B.; Malik, S.; Wi, S.; Lee, J.H. Firmware Verification of Embedded Devices Based on a Blockchain. In Quality, Reliability, Security and Robustness in Heterogeneous Networks; Lee, J.H., Pack, S., Eds.; Springer: Cham, Switzerland, 2017; LNICSSITE; Volume 199, pp. 52–61. [Google Scholar] [CrossRef]
- Yohan, A.; Lo, N.-W.; Santoso, L.P. Secure and Lightweight Firmware Update Framework for IoT Environment. In Proceedings of the 2019 IEEE 8th Global Conference on Consumer Electronics (GCCE), Osaka, Japan, 5–18 October 2019; pp. 684–685. [Google Scholar] [CrossRef]
- Yu, D.; Zhang, L.; Chen, Y.; Ma, Y.; Chen, J. Large-Scale IoT Devices Firmware Identification Based on Weak Password. IEEE Access 2020, 8, 7981–7992. [Google Scholar] [CrossRef]
- Tsoutsos, N.G.; Maniatakos, M. Anatomy of Memory Corruption Attacks and Mitigations in Embedded Systems. IEEE Embed. Syst. Lett. 2018, 10, 95–98. [Google Scholar] [CrossRef]
- Strackx, R.; Piessens, F.; Preneel, B. Efficient Isolation of Trusted Subsystems in Embedded Systems. In Security and Privacy in Communication Networks; Jajodia, S., Zhou, J., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; LNICSSITE; Volume 50, pp. 344–361. [Google Scholar] [CrossRef]
- Abera, T.; Asokan, N.; Davi, L.; Koushanfar, F.; Paverd, A.; Sadeghi, A.-R.; Tsudik, G. Invited: Things, trouble, trust: On building trust in IoT systems. In Proceedings of the 53rd Annual Design Automation Conference, Austin, TX, USA, 5–9 June 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Shoshitaishvili, Y.; Wang, R.; Hauser, C.; Kruegel, C.; Vigna, G. Firmalice–Automatic Detection of Authentication Bypass Vulnerabilities in Binary Firmware. In Proceedings of the NDSS Symposium 2015, San Diego, CA, USA, 8–11 February 2015. [Google Scholar]
- Greenberg, A. The Reaper IoT Botnet Has Already Infected a Million Networks. Available online: https://www.wired.com/story/reaper-iot-botnet-infected-million-networks/ (accessed on 4 December 2023).
- Mandal, A.; Ferrara, P.; Khlyebnikov, Y.; Cortesi, A.; Spoto, F. Cross-program taint analysis for IoT systems. In Proceedings of the 35th Annual ACM Symposium on Applied Computing, Brno, Czech Republic, 30 March–3 April 2020; pp. 1944–1952. [Google Scholar] [CrossRef]
- Bertino, E.; Islam, N. Botnets and Internet of Things Security. Computer 2017, 50, 76–79. [Google Scholar] [CrossRef]
- Wazzan, M.; Algazzawi, D.; Bamasaq, O.; Albeshri, A.; Cheng, L. Internet of Things Botnet Detection Approaches: Analysis and Recommendations for Future Research. Appl. Sci. 2021, 11, 5713. [Google Scholar] [CrossRef]
- IoT Alliance Australia. Available online: https://iot.org.au/ (accessed on 4 December 2023).
- Fagan, M.; Megas, K.; Scarfone, K.; Smith, M. NIST IR 8259; Foundational Cybersecurity Activities for IoT Device Manufacturers. NIST: Gaithersburg, MD, USA, 2020. [CrossRef]
- Regenscheid, A. NIST SP 800-193; Platform Firmware Resiliency Guidelines. NIST: Gaithersburg, MD, USA, 2018. [CrossRef]
- Binwalk: Firmware Analysis Tool. Available online: https://github.com/ReFirmLabs/binwalk (accessed on 4 December 2023).
- Hemel, A. binaryanalysis-ng: Binary Analysis Next Generation (BANG). Available online: https://github.com/armijnhemel/binaryanalysis-ng (accessed on 4 December 2023).
- FMK: Firmware Mod Kit. Available online: https://github.com/rampageX/firmware-mod-kit/ (accessed on 4 December 2023).
- The Firmware Analysis and Comparison Tool (FACT). Available online: https://github.com/fkie-cad/FACT_core (accessed on 4 December 2023).
- Angr: Platform-Agnostic Binary Analysis Framework. Available online: https://github.com/angr/angr (accessed on 4 December 2023).
- Vector 35, Binary Ninja. Available online: https://binary.ninja/features/ (accessed on 4 December 2023).
- Radare2: Libre Reversing Framework for Unix Geeks. Available online: https://github.com/radareorg/radare2 (accessed on 4 December 2023).
- Ghidra Firmware Utilities. Available online: https://github.com/al3xtjames/ghidra-firmware-utils (accessed on 4 December 2023).
- IDA Pro: A Powerful Disassembler and a Versatile Debugger. Available online: https://hex-rays.com/ida-pro/ (accessed on 4 December 2023).
- Bellard, F. QEMU, a Fast and Portable Dynamic Translator. In Proceedings of the USENIX Annual Technical Conference, Anaheim, CA, USA, 10–15 April 2005; pp. 41–46. [Google Scholar]
- Zalewski, M. AFL: American Fuzzy Lop. Available online: https://github.com/google/AFL (accessed on 4 December 2023).
- Manske, A. Conducting a Vulnerability Assessment of an IP Camera. Master’s Thesis, KTH Royal Institute of Technology, Stockholm, Sweden, 2019. [Google Scholar]
- Mansfield-Devine, S. Ransomware: Taking businesses hostage. Netw. Secur. 2016, 2016, 8–17. [Google Scholar] [CrossRef]
- Chen, J.; Diao, W.; Zhao, Q.; Zuo, C.; Lin, Z.; Wang, X.F.; Lau, W.C.; Sun, M.; Yang, R.; Zhang, K. IoTFuzzer: Discovering Memory Corruptions in IoT Through App-based Fuzzing. In Proceedings of the NDSS Symposium 2018, San Diego, CA, USA, 18–21 February 2018; pp. 1–15. [Google Scholar] [CrossRef]
- Popa, M. Binary Code Disassembly for Reverse Engineering. J. Mob. Embed. Distrib. Syst. 2012, IV, 233–248. [Google Scholar]
- Serrano, M. Lecture Notes on Decompilation; Lecture 20; Carnegie Mellon School of Computer Science: Pittsburgh, PA, USA, 2013. [Google Scholar]
- Zandberg, K.; Schleiser, K.; Acosta, F.; Tschofenig, H.; Baccelli, E. Secure Firmware Updates for Constrained IoT Devices Using Open Standards: A Reality Check. IEEE Access 2019, 7, 71907–71920. [Google Scholar] [CrossRef]
- Johnson, S.C. Lint, a C Program Checker. Comp Sci Tech. Rep. 1978, 65, 1–11. [Google Scholar]
- Thomas, S.L.; Chothia, T.; Garcia, F.D. Stringer: Measuring the Importance of Static Data Comparisons to Detect Backdoors and Undocumented Functionality. In Computer Security—ESORICS 2017; Foley, S., Gollmann, D., Snekkenes, E., Eds.; Springer: Cham, Switzerland, 2017; LNCS; Volume 10493, pp. 513–531. [Google Scholar] [CrossRef]
- Grace, M.; Zhou, Y.; Wang, Z.; Jiang, X.; Drive, O. Systematic Detection of Capability Leaks in Stock Android Smartphones. In Proceedings of the NDSS Symposium 2012, San Diego, CA, USA, 5–8 February 2012; pp. 1–15. [Google Scholar]
- Feng, Q.; Zhou, R.; Xu, C.; Cheng, Y.; Testa, B.; Yin, H. Scalable graph-based bug search for firmware images. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 480–491. [Google Scholar] [CrossRef]
- Tien, C.W.; Tsai, T.T.; Chen, I.Y.; Kuo, S.Y. UFO–Hidden Backdoor Discovery and Security Verification in IoT Device Firmware. In Proceedings of the 2018 IEEE International Symposium on Software Reliability Engineering Workshops (ISSREW), Memphis, TN, USA, 15–18 October 2018; pp. 18–23. [Google Scholar] [CrossRef]
- UL 2900-1; Software Cybersecurity for Network-Connectable Products, Part 1: General Requirements. UL Standards and Engagement: Bensenville, IL, USA, 2023. Available online: https://standardscatalog.ul.com/standards/en/standard_2900-1_1 (accessed on 4 December 2023).
- ETSI EN 303 645 V2.1.1; CYBER; Cyber Security for Consumer Internet of Things: Baseline Requirements. ETSI: Sophia Antipolis, France, 2020; 34 p.
- Zhou, W.; Guan, L.; Liu, P.; Zhang, Y. Automatic Firmware Emulation through Invalidity-guided Knowledge Inference. In Proceedings of the 30th USENIX Conference on Security Symposium, Virtual, 11–13 August 2021; pp. 2007–2024. [Google Scholar]
- Firmadyne: Platform for Emulation and Dynamic Analysis of Linux-Based Firmware. Available online: https://github.com/firmadyne/firmadyne (accessed on 4 December 2023).
- Zhu, L.; Fu, X.; Yao, Y.; Zhang, Y.; Wang, H. FIoT: Detecting the Memory Corruption in Lightweight IoT Device Firmware. In Proceedings of the 2019 18th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/13th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), Rotorua, New Zealand, 5–8 August 2019; pp. 248–255. [Google Scholar] [CrossRef]
- Shoshitaishvili, Y.; Bianchi, A.; Borgolte, K.; Cama, A.; Corbetta, J.; Disperati, F.; Dutcher, A.; Grosen, J.; Grosen, P.; Machiry, A.; et al. Mechanical Phish: Resilient Autonomous Hacking. IEEE Secur. Priv. 2018, 16, 12–22. [Google Scholar] [CrossRef]
- Lally, G.; Sgandurra, D. Towards a Framework for Testing the Security of IoT Devices Consistently. In Emerging Technologies for Authorization and Authentication (ETAA 2018); Saracino, A., Mori, P., Eds.; Springer: Cham, Switzerland, 2018; LNCS; Volume 11263, pp. 88–102. [Google Scholar] [CrossRef]
- Muzaffar, S.; Elfadel, I.M. An Instruction Set Architecture for Secure, Low-Power, Dynamic IoT Communication. In VLSI-SoC: Design and Engineering of Electronics Systems Based on New Computing Paradigms (VLSI-SoC 2018); Bombieri, N., Pravadelli, G., Fujita, M., Austin, T., Reis, R., Eds.; Springer: Cham, Switzerland, 2018; IFIP AICT; Volume 561, pp. 14–31. [Google Scholar] [CrossRef]
- UEFI. Getting a Handle on Firmware Security. Available online: https://uefi.org/sites/default/files/resources/Getting%20a%20Handle%20on%20Firmware%20Security%2011.11.17%20Final.pdf (accessed on 5 December 2023).
- Wilkins, D. Firmware Security for IoT Devices. Available online: https://www.embedded-computing.com/articles/firmware-security-for-iot-devices (accessed on 5 December 2023).
- Khan, L.U.; Saad, W.; Han, Z.; Hossain, E.; Hong, C.S. Federated Learning for Internet of Things: Recent Advances, Taxonomy, and Open Challenges. IEEE Comm. Surv. Tut. 2012, 23, 1759–1799. [Google Scholar] [CrossRef]
- Sun, P.; Garcia, L.; Salles-Loustau, G.; Zonouz, S. Hybrid Firmware Analysis for Known Mobile and IoT Security Vulnerabilities. In Proceedings of the 2020 50th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Valencia, Spain, 29 June–2 July 2020; pp. 373–384. [Google Scholar] [CrossRef]
- Chua, Z.L.; Shen, S.; Saxena, P.; Liang, Z. Neural Nets Can Learn Function Type Signatures from Binaries. In Proceedings of the 26th USENIX Conference on Security Symposium, Vancouver, BC, Canada, 16–18 August 2017; pp. 99–116. [Google Scholar]
- Krau, M.; Wei, D. Clarifying the Ten Most Common Misconceptions about UEFI, UEFI Forum White Paper. Available online: https://uefi.org/sites/default/files/resources/UEFI_Clarifying_Common_Misconceptions_White_Paper_April%202014_Final.pdf (accessed on 5 December 2023).

| Domain | Incorporation | References | |||
|---|---|---|---|---|---|
| Monolithic | Cross-domain | Standards and reg. | Security survey | ||
| Interface security | ✓ | ✓ | ✓ | ƥ | [33,34,35,36] |
| Firmware auditing | ✓ | ƥ | ƥ | ƥ | [17,24,29,37,38,39,40,41] |
| Reverse engineering | ✓ | ✓ | X | ƥ | [33,36] |
| Threat analysis | ✓ | ✓ | ƥ | ✓ | [36,42,43,44] |
| Tools and testbeds | ƥ | ƥ | ✓ | ƥ | [2,4,44,45,46,47,48,49,50,51,52,53,54,55,56] |
| Distributed ledgers | ✓ | ✓ | ✓ | ✓ | [45,57,58,59,60,61,62,63,64,65,66,67,68] |
| Machine learning | ƥ | ✓ | X | X | [31,45,69,70,71,72] |
| Commercial developments | ✓ | ƥ | ✓ | ƥ | [73,74,75] |
| Remote attestation | ✓ | X | X | ƥ | [42,76,77,78,79] |
| Tool | Operational Domain | Features | Limitations |
|---|---|---|---|
| Binwalk [116] | FU | Firmware analysis, extraction, file system identification, entropy comparison | Limited firmware extraction, recursive unpacking |
| BANG [117] | FU | Recursive unpacking for approximately 130 file types | Inconsistent support |
| FMK [118] | FU | Firmware unpacking and extraction and repacking specific to Linux. | Insufficient support, supports only Linux platforms |
| FACT [119] | MRE, FU | Automatic, extensible basic firmware analysis and comparison to | Limited to static analysis, and to certain Linux distributions, resource heavy |
| ANGR [120] | MRE, FU | Framework for binary analysis using CFG | Complex usability, limited Windows binary support |
| Binary Ninja [121] | MRE, FD | Binary analysis with intermediate language supporting multiple platforms, with GUI | Closed source. Limited support for dynamic analysis |
| Radare2 [122] | FD | Binary analysis, disassembling and debugging | Difficult to learn, and analyze complex code |
| Ghidra [123] | FD | Open-source analysis and de-compilation tool, supporting multiple platforms | Supports limited architectures and de-buggers, slow performance |
| KLEE [48] | MRE, FD | Symbolic VM based on LLVM compiler support | Resource heavy |
| FAT [49] | MRE | Built atop multiple analysis and reverse engineering tools | Compatibility issues of base-tools with Linux |
| IDA Pro [124] | MRE | Powerful interactive disassembler, debugger, support for multiple architectures | High cost, closed source, basic GUI |
| QEMU [125] | MRE | Efficient open-source emulator, and virtualization for Linux platforms | Limited GUI, only Linux support |
| AFL [126] | MRE | Security oriented brute-force fuzzer employing generic algorithms | Requires target input to learn and improve |
| Auditing Feature | Static | Dynamic |
|---|---|---|
| Methodology | Code scanning (manual, semi-automated) | Execution-based behavior analysis |
| De-compilation | Limited applicability as de-compiler may not be available or produce false output | No requirement for code de-compilation |
| False Positives/Errors | High rate of false positives | N/A |
| Firmware Acquisition | Acquiring device firmware is necessary | There is no need to acquire firmware if the device is locally or remotely available |
| Manifest | Desired but not necessary | Necessary for virtualization |
| Non-exploitable code | Non-exploitable code cannot be analyzed | Cannot find unexploited code |
| Physical device access | Physical access to devices is not needed | IoT device or firmware emulation required |
| Run-time Insights | No real-time code execution information; problems due to run-time vulnerabilities. | Can provide additional insights on input data/execution during run-time |
| Scalability | Possible to automate if a large repository of device firmware is available | Can be achieved with greater virtualization |
| Unused Code | Unused code can be inspected | Not feasible to identify vulnerabilities in unused code of program |
| Virtualization | Virtualization is not needed | Virtualization needed for manifest/meta-data |
| Vulnerability Focus | Buffer overflows, memory corruption, segmentation errors, uninitialized variables | Any type of vulnerability can be inspected by running relevant code |
| Tool | Year | Analysis Method | Target Vulnerability | SC. | UV. | PV. | Architecture |
|---|---|---|---|---|---|---|---|
| Woodpecker [135] | 2012 | Code analysis | Permission leaks | N/A | N/A | Yes | Android |
| Correlation engine [81] | 2014 | Vulnerability correlations | Any | Yes | Yes | Yes | Multiple |
| Firmalice [108] | 2015 | Symbolic execution | Authentication | Yes | Yes | No | Multiple |
| PIE [69] | 2015 | Parsing identification | Bugs, protocol specs, commands | No | Yes | No | Multiple |
| ANGR [120] | 2016 | Binary control flow graphs | Any | Yes | Partly | Yes | Limited |
| Genius [136] | 2016 | Control flow graphs | Any | Yes | Yes | No | Multiple |
| Gemini [40] | 2017 | Neural network | Any | Yes | Partly | Yes | Multiple |
| HumIDIfy [45] | 2017 | Machine learning | Finding hidden functionality | No | Partly | Yes | Multiple |
| Stringer [134] | 2017 | Automated analysis | Finding backdoors | Yes | No | No | Multiple |
| FirmUp [82] | 2018 | Program slicing | Multi-domain | Yes | Yes | Partly | Multiple |
| UFO [137] | 2018 | Shell script dependency | Multi-domain | Yes | Yes | Yes | Multiple |
| Two-stager [41] | 2019 | Code similarity | Any | Yes | Yes | No | Multiple |
| Vulnerab. Influence | Exploitation Axes | Auditing Technique | Supported Platform | Architecture Compatibility | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Static | Dynamic | Linux | Windows | RTOS | Other | ARM | MIPS | X86 | Other | ||
| System Property | Memory corruption | [52,69,82] | [41,51,129,142] | [37,41,51,52,69,82,129,142] | [41,69,82,129,142] | [37,41,56,69,82,129] | [51,69,82,129,142] | [41,51,69,82,129,142] | [53,69,82,129,142] | [14,41,83,86,95] | [82,129,142] |
| Taint vulnerability | [52,53] | - | [52,53] | [53] | [53] | [53] | [52,53] | [52,53] | [53] | [53] | |
| Access Mechanisms | Authentic./Backdoor | [39,45,81,108,122,137] | [99] | [45,81,99,108,137] | [108] | [108] | [108] | [45,81,99,108,137] | [45,81,99,108,137] | [99,108] | [99,108] |
| Weak password | - | [45,81,122,137] | - | [81] | - | [45,81] | |||||
| Comp. Re-use | Obsolete components | [54,55] | [104] | [50,54,55,104] | [104] | [104] | [104] | [50,54,55,104] | [50,54,55,104] | [50,54,55,104] | [50,54,55,104] |
| Network Interface | Insecure interfaces | [137] | [69] | [69,137] | - | - | [69] | [69,137] | [69,137] | [69,137] | [69,137] |
| Weak firewall | [45] | - | [45] | - | - | - | [45] | [45] | - | - | |
| Image Mgmt. | Web Services, Storage | [81] | [81] | [81] | - | [81] | - | [81] | [81] | [81] | [81] |
| Regulatory Compliance, User awareness | Hard-coded credentials | [39,45,56,81,143] | - | [45,56,81] | - | - | - | [45,81] | [45,81] | [81] | [81] |
| Information leakage | - | [99] | [99] | - | - | - | [99] | [99] | [99] | [99] | |
| Adversary Vectors | Side-channeling | [7,33,38,85] | [142] | [3,38,85,94] | [108] | [108] | [108] | [3,7,38,94] | [3,7,38,94] | [99,108] | [99,108] |
| Technology | Application Area | Adaptations and Recommendations |
|---|---|---|
| ML and DL | Automated reverse engineering [148] | Reverse engineering tasks require greater automation using intelligent code analysis and ML/federated learning models. |
| ML and DL | Improved emulation [31,57,66] | Improvement in emulation systems can help to extend dynamic analysis to architectures where static analysis is the only primitive available. Self-evolving emulators based on prediction DL models with automated selection of architecture-dependent parameters can also be helpful. |
| ML and DL | Identifying vulnerability patterns [149,150] Auditing framework [57] | ML and DL technologies can aid in pattern/signature recognition while federated learning platforms can ensure low-latency local model generation for global classifiers. FL can ensure greater data privacy and anonymity while the framework can utilize blockchain peers for verifiability and immutability. |
| Blockchain | Secure firmware update [62,63,64,101] | OTA updates need to have sufficient security guarantees; blockchain technology can be employed as a promising alternative to deliver OTA updates. |
| Blockchain | Image storage and verification [57,58,59,102] | Blockchain technology can be used for storage and delivery of firmware images offering verifiability and accountability for regulatory bodies. |
| Blockchain | Metadata collection | Metadata and manifest information should be available in a central repository and verifiable for authenticity. Blockchain can be leveraged for this purpose. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bakhshi, T.; Ghita, B.; Kuzminykh, I. A Review of IoT Firmware Vulnerabilities and Auditing Techniques. Sensors 2024, 24, 708. https://doi.org/10.3390/s24020708
Bakhshi T, Ghita B, Kuzminykh I. A Review of IoT Firmware Vulnerabilities and Auditing Techniques. Sensors. 2024; 24(2):708. https://doi.org/10.3390/s24020708
Chicago/Turabian StyleBakhshi, Taimur, Bogdan Ghita, and Ievgeniia Kuzminykh. 2024. "A Review of IoT Firmware Vulnerabilities and Auditing Techniques" Sensors 24, no. 2: 708. https://doi.org/10.3390/s24020708
APA StyleBakhshi, T., Ghita, B., & Kuzminykh, I. (2024). A Review of IoT Firmware Vulnerabilities and Auditing Techniques. Sensors, 24(2), 708. https://doi.org/10.3390/s24020708








