5.3. Simulation Results and Discussions
Two experiment scenarios, experiment scenarios (a) and experiment scenarios (b), were done for performance analysis of safety period, energy consumption, packet delivery ratio, and end-to-end delay. In the scenarios (a), the performance was observed under fixed source packet rate of 1 packet/second against varied source-sink distance. The source-sink distance was varied between 10 and 70 hops. In scenarios (b), performance was observed under fixed source-sink distance against varied source packet generation rate. The source packet generation rate was varied from 1 to 7 packet/second. For the analysis of attack success rate, three experiment scenarios were done. In scenario (a), the attack success rate was observed against varied number of sensor nodes in the network. In scenario (b), the attack success rate was observed at varied network size. In scenario (c), the attack success rate was observed against varied adversary detection range.
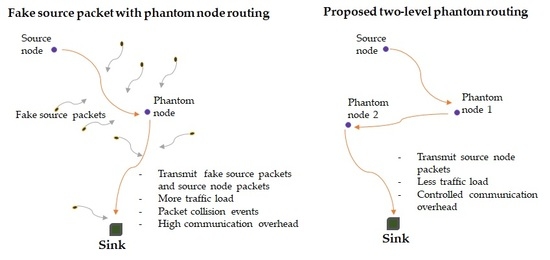
Figure 5 shows the privacy performance of the protocols. The figure shows that the TreeR protocol achieves very strong SLP protection. The TreeR achieves longer safety period by integrating many routing techniques. It employs phantom nodes located far away from the source node. It also employs significantly long backbone routes with many diversionary routes. At the end of each diversionary route, fake packets are emitted periodically. As a result, the eavesdropping adversary is effectively obfuscated and long safety period is guaranteed. However, the use of long backbone routes, diversionary routing paths which diverge to the network border regions, and the distribution of fake packet traffic at the end of each diversionary route introduce very high communication overhead as shown in the next paragraphs. The figure also shows that the proposed PhaT protocol achieves relatively short safety period compared to the TreeR protocol. However, compared to the traditional Pha protocol, the PhaT protocol offers significantly longer safety period. For example, at 60 hops from the sink node, the safety period of the PhaT is approximately 4 times higher than Pha protocol. Since PhaT can achieve approximately 4 times higher safety period than the Pha protocol, we consider the level of SLP protection for PhaT to be effectively strong. Also shown in the
Figure 5a, the proposed PhaP protocol achieves significantly longer safety period than the existing ProbR protocol. The ProbR protocol achieves a relatively short safety period because the fake packet source is located away from the real source node, on the opposite side of the real source node. Also, the real packet routes and fake packet routes are not exactly homogeneous due to the location of the fake packet sources being in the near-sink region. The fake packet routes are relatively short. As a result, it has a small effect on the privacy protection. After sometime of traffic analysis attack, adversary can predict the real packet routes and perform a more focused back tracing attack to improve its attack success rate. Furthermore, the ProbR protocol distributes only one fake packet at a time. As a result, the adversary is not effectively distracted from the real packet routes and short safety period is achieved by the ProbR protocol. The safety period of Pha protocol is significantly lower because the protocol employs a simple routing algorithm with short and fixed routes. The adversary is capable of successfully back tracing the routing paths of the Pha within a short time. For all the protocols, the privacy performance improves with the increase in source-sink distance because the adversary back tracing attack becomes more complicated with longer routing paths.
Figure 5b shows the privacy performance of the protocols at a source-sink distance of 40 hops against varied source packet generation rate. The protocols offer lower safety period as the source packet rate increases. The main reason for the reduced safety period is that, as more packets are sent in the network, the probability that the cautious adversary will capture successive packets within the specified waiting timer is increased. At higher data rates, the cautious adversary is capable of capturing enough number of successive packets to allow it to make a successful back tracing attack and capture the asset. Therefore, the level of SLP protection is reduced.
Figure 6 shows the attack success rate (ASR) of the adversary against the analyzed protocols. In the analysis, the source packet generation rate was 1 packet/second, the adversary trace time was 900 source packets, and the source-sink distance was fixed at 50 hops. For the results in
Figure 6a, the ASR was observed against varied number of sensor nodes in the network. The number of sensor nodes was varied between 2500 and 4000 nodes. The figure shows that the ASR of all the protocols tend to decrease with the increase in the number of sensor nodes in the network. However, for the proposed protocols, the ASR decreases at a slightly higher rate. This means that, the SLP protection in the proposed protocols increases at a higher rate that in the other protocols. The main reason for the increased SLP protection with the increase in node density is that, when the number of nodes in the network increases, the number of neighboring nodes and candidate phantom nodes also increase. As an example, in PhaP protocol, when the node density increases it also increases the probability of a greater number of nodes in the
Pring. Therefore, the number of candidate
PNsec for each successive packet also increases. As a result, there is a higher probability that a different
PNsec is selected for each successive packet and the routing paths becomes less predictable to the eavesdropping adversary. Also, the number of random routing paths increases with the increase in number of neighboring nodes of the
PNfst and
PNsec. As an example, if a source node has
w neighboring nodes with shorter hop distance to
PNfst, the probability of the source node selecting a particular neighboring node as the next-hop node during the directed random-walk is 1/
w. If
PNfst has
k neighboring nodes with shorter hop distance to
PNsec, the probability of
PNfst selecting a particular neighboring node as the next-hop node during the directed random-walk is 1/
k. If
PNsec has
v neighboring nodes with shorter hop distance to sink, the probability of
PNsec selecting a particular neighboring node as the next-hop node during the directed random-walk is 1/
v. Overall, there can be up to
random routes between the source node and the sink node. That is,
. It is therefore evident that the SLP protection will increase with the increase in node density. As a result, ASR decreases with the increase in node density. This effect is similar in the PhaT protocol. The ProbR protocol employs only one phantom node and one fake packet source in the near-sink region. As a result, the increase in node density has a small effect on limiting the ASR. The TreeR depends highly on the fake packet routes to obfuscate the adversary. Since the number of diversionary routes remained the same, obfuscation of the adversary on the backbone route does not improve very much with the increase in node density. As a result, ASR decreases at a slow rate. The Pha protocol selects the shortest paths which may become fixed, as a result, the increase in node density has little effect on the ability of the protocol to limit the ASR.
Figure 6b shows the ASR of the adversary against varied network size. The network has a square structure. For analysis, we use the term “Length” which means the length or width of the network. In the experiments, the length was varied between 2000 and 3500 m. In the figure, it shows that the ASR against the Pha, ProbR, and PhaP protocols has insignificant change as the length increases. The main reason for the insignificant change is that the routing paths of the protocols are directed towards the sink node. Since the source-sink distance remained the same and the phantom node selection criteria did not change, the change in the network size had no significant impact on the performance of protocols. In the PhaT protocol, the ASR decreases significantly with the increase in length. The main reason for the improved privacy performance as length increases is that, since the location of the sink node is constant at the center of the network, then the distance between the sink node and phantom nodes increases with the increase in length. This is mainly because the phantom nodes are located in the near network border regions. Also, since the source-sink distance was fixed at 50 hops, the distance between the source node and phantom nodes increase with the increase in length. As a result, the routing paths become longer and the directed random-walk routing strategy becomes more obfuscating to the adversary. Consequently, the adversary takes longer time to back trace the packet routes, makes insignificant progress towards the source node, and the ASR is limited. However, for the proposed PhaT protocol, it is important to control the length. If the length is too long, it may lead to excessively long routing paths which incur high communication overhead. In the TreeR protocol, when the intermediate node is kept at a fixed location, it is possible to increase the length of the diversionary routes as the network size increase. As a result, the obfuscation ability of the protocol is increased. When the adversary is misled into back tracing the diversionary routes which become longer with the increase in length, the adversary may be misled into regions further away from the source node. Hence, the ASR is reduced.
Figure 6c shows the ASR of the adversary against adversary detection range. The adversary detection range was varied between 30 and 90 m. The sensor node sensing range was fixed at 30 m. The figure shows that the ASR increases with the increase in adversary detection range. This is mainly due to the fact that adversary becomes more powerful when it has a longer detection range. The traffic analysis attacks become less complex when the adversary can detect a packet sent from a sensor node which is more than 1 hop away. The figure shows that, when a source node is 50 hops away from the sink node, at a trace time of 900 source packets, an adversary with 60 m detection range can achieve up to 100% ASR against the Pha protocol. An adversary with 90 m detection range can achieve up to 90% ASR against the ProbR protocol and up to 65% ASR against the PhaP protocol. For PhaT and TreeR protocols, an adversary with 90 m detection range can achieve less than 55% ASR. These results establish that, amongst all the analyzed protocols, the PhaT and TreeR protocols have the strongest SLP protection and when the adversary has 30 m detection range, the protocols are capable of limiting the adversary ASR to less than 25%.
Figure 7 shows the energy consumption performance of the protocols. In the energy consumption analysis, 15 experiment scenarios were assumed, each scenario with a different source node location. Each scenario involved a transmission of 1000 packets from a source node to the sink node. After all the packets were received at the destination sink node, for each scenario, the average energy consumption per sensor node was computed according to Equations (1) and (2). For both TreeR and ProbR protocols, real packets and fake packets were transmitted simultaneously.
Figure 7a shows the average total energy consumption per sensor node for sensor nodes at different locations. The figure shows the energy consumption of TreeR protocol is significantly high. The high energy consumption is due to the integration of many routing techniques. The backbone routes which divert to the network border cause the protocol to generate long routing paths. Also the multiple diversionary routes which act as branches for the backbone routes distribute a large amount of fake packets. Fake packets are also distributed along the phantom route. As a result, the sensor nodes incur exhaustive energy consumption. Furthermore, multiple fake packets are transmitted for each real packet transmission. As shown in Equations (1) and (2), each hop involves consumption of transmit and receive energy. As a result, more energy is consumed for each real packet transmission. Moreover, the distribution of fake packets in the network increases the probability of packet collision events which result in packet retransmission incidents. Hence, higher energy consumption is incurred by the TreeR protocol. The proposed PhaT has significantly lower energy consumption than the TreeR protocol mainly because while the PhaT protocol employs a single route for each packet transmission, the TreeR protocol employs multiple routes which include a route for real packet transmission and multiple diversionary routes for fake packets transmission. Both TreeR and PhaT protocols employ backbone route near the sink region to minimize the energy consumption in the region. The energy consumption of PhaT is higher than in the ProbR, PhaP, and Pha protocols. The main reason for the high energy consumption is that, PhaT locates the phantom nodes in the network border regions which results in longer and highly diversified routing paths.
In the near-sink region, ProbR protocol incurs higher energy consumption than the proposed PhaP because ProbR transmits multiple packets for each event packet. A fake source packet is transmitted with every real packet transmission. Sensor nodes in the near-sink region experience exhaustive energy consumption due to the big load of packet forwarding. The sensor nodes not only transmit their own packets to the sink node, they also forward packets originating from the sensor nodes in the away from sink regions. The PhaP protocol ensures the energy consumption of the sensor nodes in the near-sink region is minimized. In the away from the sink regions, PhaP and
Prob incur same amount of energy consumption because the protocols employ a similar phantom node routing strategy in the away from the sink regions. The energy consumption of the Pha protocol is significantly lower because the protocol employs a simple routing algorithm with short and fixed routes.
Figure 7b shows the energy consumption of sensor nodes at 600 m from the sink node, against varied source packet generation rate. The energy consumption of the sensor nodes increases with the increase in source packet generation rate. At higher packet rates, more packet traffic is generated in the network. Consequently, the sensor nodes consume more energy to transmit the packets. The energy consumption of TreeR protocol increases at a faster rate because more packet collision events occur due to the transmission of both, real packet and fake packets. More packet collision events result in packet loss and packet retransmission events. As a result, the energy consumption of the sensor nodes is increased.
Figure 8 shows the packet delivery ratio (PDR) performance of the protocols.
Figure 8a shows the PDR performance of the protocols at a fixed source packet rate. The analysis included source nodes at different source-sink distances. 100 packets were transmitted from each source node to the sink node with a fixed source packet generation rate of 1 packet/second. Average values for PDR were found according to Equation (4). The figure shows that PDR of all the protocols decreases with the increase in source-sink distance. This is due to the fact that as the distance between the source node and sink node increases, more hops are included in the transmission and the probability of packet loss increases. Therefore, the PDR performance is affected. The figure shows that the TreeR protocol incurs low PDR. The low PDR performance of TreeR is due to the integration of many routing strategies. The use of phantom nodes, backbone routes, and diversionary routes result in routing paths which have high probability of packet loss events and low PDR. Furthermore, the distribution of fake packets in the network results in high probability of packet collision events and low PDR is achieved. The proposed PhaT protocol achieves higher PDR than the TreeR protocol because it incurs few packet collision and packet loss events due to the absence of fake packet distribution. The ProbR protocol achieves higher PDR than the TreeR protocol because it employs shorter routing paths with only one fake packet source at a time period. The ProbR and PhaP protocols have comparable PDR performance because they both employ phantom node routing with routing paths which are directed towards the sink node. The fake packet sources in the ProbR are located far away from the real sources. Consequently, the fake packets incur less significant effect on the PDR of the protocol. The PDR of the Pha protocol is significantly high because the protocol employs a simple routing algorithm with short and fixed routing paths. The short and fixed routing paths incur few events of packet loss and packet collision.
Figure 8b shows the PDR performance of the protocols at a fixed source-sink distance of 40 hops. The experiment scenarios included multiple source nodes. 100 packets were sent from each source node to the sink node at varied source packet rate from 1 to 7 packet/second. The figure shows that PDR of all the protocols decreases with the increase in source packet rate. When more packets are generated per second, the probability of packet collision and packet loss is increased and PDR is affected. The TreeR protocol incurs the worst PDR performance at high source packet rates due to the increasing number of packet collision events between the real and fake packets.
Figure 9 shows the end-to-end (EED) performance of the protocols.
Figure 9a shows the EED performance of the protocols at different source-sink distances. Investigations were done for multiple source nodes at different source-sink distances. 100 packets were sent from each source node to the sink node with a fixed source packet generation rate of 1 packet/second. Average values for EED were found according to Equation (5). The figure shows that the EED of the protocols tend to increase with the increase in the source-sink distance. This is due to the fact that as the distance between the source node and sink node increases, the number of packet forwarding events (hops) also increases. Each hop incurs some EED. Hence, the overall EDD is increased. Furthermore, longer routing paths have a higher probability of packet loss and packet retransmission events which have negative effect on the EED performance. The TreeR and PhaT protocols employ long routing paths. Consequently, the EED for the TreeR and PhaT protocols is long. The location of phantom nodes in the ProbR and PhaP protocols guarantee relatively short routing paths with better EED performance than the TreeR and PhaT protocols. The fake source packets in ProbR are located far away from the real source node. As a result, the fake packets have less significant effect on the EED performance of the protocol. The Pha protocol has significantly low EED because the protocol employs a simple routing algorithm with short and fixed routing paths.
Figure 9a also shows the impact of adding a second level phantom node routing on the EED of the PhaP and PhaT protocols. The PhaP has a slightly longer EED than ProbR. The increase in EED is controlled by the strategic location of the
Pring which guarantees that the directed random-walk routing is directed towards the sink node. The PhaT has considerably lower EED than the TreeR. However, the EED of PhaT is significantly high. The EED of PhaT can be up to 3 times the EED of the traditional Pha protocol which employs only one level of phantom node routing. The long EED is mainly due to the designated location of the phantom nodes which results in elongated routing paths. Packets are first routed to the near network border regions before they are routed to the sink node. These results demonstrate that the PhaP and PhaT protocols incur some tradeoffs between privacy protection and the EED performance.
Figure 9b shows the EED performance of the protocols at a fixed source-sink distance of 40 hops. The experiment scenarios included multiple source nodes. 100 packets were sent from each source node to the sink node at varied source packet rate from 1 to 7 packet/second. The figure shows that EED of all the protocols increases with the increase in source packet rate. This is due to the fact that as more packets are generated per second, the probability of packet collision, packet loss, and packet retransmission events is increased. When packet retransmission events occur, the EED is significantly increased. The EED for the TreeR protocol increases at a higher rate due to the presence of a considerable amount of fake packets which increase the probability of packet collision events. The EED of ProbR protocol increases at a slower rate because the protocol distributes only one fake source packet at a time period. There is no fake source packet distribution in the PhaT and PhaP protocols. Consequently, the EED of the protocols increases at a slower rate.
In summary, the analysis results have demonstrated that factors such as the location of fake packet sources, location of phantom nodes, source packet generation rate, source-sink distance, and the amount of distributed fake packets can present significant impact on the SLP protection, energy consumption, PDR, and EED performance of the protocols. The TreeR protocol which positions the fake packet sources near the network border guarantees more obfuscating routing paths with strong SLP protection than the ProbR protocol which locates the fake packet sources near the sink node. The proposed PhaT protocol positions the phantom nodes in the near network border regions. Subsequently, it guarantees strong SLP protection than the PhaP protocol which positions the phantom nodes in the phantom ring located at some distance from the sink node. However, the TreeR and PhaT protocols incur relatively high energy consumption, low PDR and long EED. The TreeR protocol distributes a considerable amount of fake packets in the network. As a result, it achieves significantly higher SLP protection than the ProbR protocol which distributes only one fake packet at a time. All the analyzed protocols offer lower SLP protection when the source packet generation rate is increased. Longer source-sink distance increases the complexity of the adversary tracing back attack which results in higher degree of SLP protection for all the protocols. By eliminating the fake packet traffic in the network, the proposed PhaT and PhaP protocols achieve strong SLP protection with controlled energy consumption, PDR, and EED. The PhaT protocol preserves effective SLP protection with better communication overhead than its contender TreeR protocol. Similarly, the PhaP protocol preserves stronger SLP protection than its contender ProbR protocol with controlled communication overhead. An additional superior feature of the PhaP protocol is that, it achieves minimized energy consumption in the near-sink region where the sensor nodes experience exhaustive energy consumption. High energy consumption for the sensor nodes in the near-sink region greatly affects the network lifetime [
3,
4]. Thus, PhaP may be considered as a better candidate than ProbR when network lifetime maximization is an important requirement.