Risk-Limiting Scheduling of Optimal Non-Renewable Power Generation for Systems with Uncertain Power Generation and Load Demand
Abstract
:1. Introduction
2. Method
2.1. Statement and Computational Challenges of Risk-Limiting Schedule of Optimal Non-Renewable Power-Generation Problem
2.1.1. Conventional Optimal Power Flow Problem
2.1.2. Statement of Risk-Limiting Schedule of Optimal Non-Renewable Power-Generation Problem
2.1.3. Monte Carlo Simulation Procedures for Evaluating Exact Conditional Probability of Satisfying Security Constraints
2.1.4. Computational Challenges of Risk-Limiting Schedule of Optimal Non-Renewable Power-Generation Problem
2.2. Risk-Limiting Schedule of Optimal Non-Renewable Power-Generation Algorithm
2.2.1. Method for Solving Risk-Limiting Schedule of Optimal Non-Renewable Power-Generation Problem
2.2.2. Evaluating η-Upper and η-Lower Bounds of
- Step Co1: Randomly select a sample of , α, β, and .
- Step Co2: For use the MCS that is described in Section 2.1.3 to obtain 10,000 samples of to compute and , and determine the and based on Equation (14); the obtained and form a pair of input and output data of .
- Step Co3: Repeat Steps Co1-Co2 M times, where M = 16,512. Then, for , M pairs of input output data that are and , , can be obtained as the training data set, where and represent the and of , respectively, obtained based on the th randomly selected sample of , (α, β) and .
2.2.3. Risk-Limiting Schedule of Optimal Non-Renewable Power-Generation Algorithm
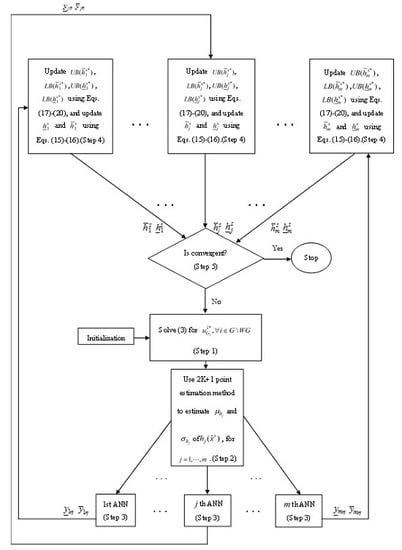
2.2.4. Flow Chart of the Risk-Limiting Schedule of Optimal Non-Renewable Power-Generation Algorithm
3. Results and Discussion
3.1. Setup of Tests
3.2. Test Results, Comparison and Discussions of Case A
3.3. Test Results, Comparisons and Discussions of Case B
4. Conclusions and Further Research
Acknowledgments
Author Contributions
Conflicts of Interest
Nomenclature
| OPF | Optimal power flow |
| RSONP | Risk-limiting schedule of optimal non-renewable power-generation |
| MCS | Monte Carlo simulation |
| OPFPRB | OPF problem with restrictive bounds, Equation (3) |
| SONP | Scheduled Optimal Non-renewable Power-generation |
| COPF | Conventional OPF |
| OSONP | Optimal SONP |
| NPAR | Non-renewable Power-generation After Re-dispatching |
| RSAR | Random State-vector After Re-dispatching |
| STAR | Security Term after Re-dispatching |
| CSONP | Conventional Schedule of Optimal Non-renewable Power-generation |
| NRSAR | Normal-bound-based Random State-vector After Re-dispatching |
| NSTAR | Normal-bound-based Security Term after re-dispatching |
| NNPAR | Normal-bound-based Non-renewable Power-generation after Re-dispatching |
| Voltage magnitude/phase angle of bus | |
| Normal upper/lower bound of | |
| state variable of bus | |
| Total number of busses/the set of all transmission lines of the system | |
| state vector of all busses | |
| Set of all/wind power/non-renewable power generation busses | |
| Real/reactive power generation at bus | |
| the power generation at bus | |
| Upper/lower bound of | |
| Random wind speed of wind power generation bus | |
| Probability density function (pdf) of random wind speed | |
| Predicted wind power generation at bus | |
| Random wind power generation at bus | |
| Vector of predicted large load-demand | |
| Vector of predicted small load-demand | |
| random large load demand at bus | |
| random large load demand at bus | |
| random vector of large load demand | |
| Probability density function (pdf) of random large real load demand at bus | |
| Real power flow over transmission line | |
| Normal upper/lower bound of | |
| Real and reactive power flow balance equation | |
| Total non-renewable power generation cost, where , and are cost coefficients | |
| Function of the th security term such as voltage magnitude at bus or real power flow over transmission line | |
| Normal upper/lower bound of the th security constraint | |
| Restrictive upper/lower bound of the th security constraint; and | |
| Optimal restrictive upper/lower bound | |
| =/ | for any superscript , where denotes the total number of security constraints |
| η | Required probability level of satisfying the security constraints in Equation (2), and 0 < η < 1 |
| Non-renewable power generation bus ’s re-dispatching percentage share of real/reactive power generation | |
| CSONP, which is the solution of COPF Problem (1) | |
| SONP for the given restrictive bounds , which is the solution of OPFPRB (3) | |
| OSONP, which is the solution of OPFPRB (3) when | |
| NNPAR | |
| NPAR for the given restrictive bounds | |
| for any heading (&), subscript or superscript ($), where and are real and reactive parts of , respectively | |
| NRSAR | |
| The th NSTAR | |
| The RSAR resulted from the scheduling and re-dispatching stages | |
| The th STAR for the given restrictive bounds | |
| η-upper bound/η-lower bound of | |
| mean/variance of |
References
- Niayifar, A.; Porte-Agel, F. Analytical modeling of wind farms: A new approach for power prediction. Energies 2016, 9, 741. [Google Scholar] [CrossRef]
- Cho, Y.; Lee, C.; Hur, K.; Kang, Y.C.; Muljadi, E.; Park, S.-H.; Choy, Y.-D.; Yoon, G.-G. A framework to analyze the stochastic harmonics and resonance of wind energy grid interconnection. Energies 2016, 9, 700. [Google Scholar] [CrossRef]
- Curreli, A.; Serra-Coch, G.; Isalgue, A.; Crespo, I.; Coch, H. Solar energy as a form giver for future cities. Energies 2016, 9, 544. [Google Scholar] [CrossRef]
- Buonomano, A.; Calise, F.; Vicidomini, M. Design, simulation and experimental investigation of a solar system based on PV and PVT collectors. Energies 2016, 9, 496. [Google Scholar] [CrossRef]
- Luo, Z.; Hong, S.-H.; Kim, J.-B. A price-based demand response scheme for discrete manufacturing in smart grids. Energies 2016, 9, 650. [Google Scholar] [CrossRef]
- Kim, Y.-S.; Hwang, C.-S.; Kim, E.-S.; Cho, C. State of charge-based active power sharing method in a standalone microgrid with high penetration level of renewable energy sources. Energies 2016, 9, 480. [Google Scholar] [CrossRef]
- Li, Y.; Li, W.; Yan, W.; Yu, J.; Zhao, X. Probabilistic optimal power flow considering correlations of wind speeds following different distributions. IEEE Trans. Power Syst. 2014, 29, 1847–1854. [Google Scholar] [CrossRef]
- Zou, B.; Xiao, Q. Solving probabilistic optimal power flow problem using quasi Monte Carlo method and ninth-order polynomial normal transformation. IEEE Trans. Power Syst. 2014, 29, 300–306. [Google Scholar] [CrossRef]
- Dvorkin, Y.; Pandzic, H.; Ortega-Vazquez, M.A.; Kirschen, D.S. A hybrid stochastic/interval approach to transmission-constrained unit commitment. IEEE Trans. Power Syst. 2015, 30, 621–631. [Google Scholar] [CrossRef]
- Wu, H.; Shahidehpour, M.; Li, Z.; Tian, W. Chance-constrained day-ahead scheduling in stochastic power system operation. IEEE Trans. Power Syst. 2014, 29, 1583–1591. [Google Scholar] [CrossRef]
- Ahmadi-Khatir, A.; Conejo, A.J.; Cherkaoui, R. Multi-area unit scheduling and reserve allocation under wind power uncertainty. IEEE Trans. Power Syst. 2014, 29, 1701–1710. [Google Scholar] [CrossRef]
- Kusiak, A.; Verma, A.; Wei, X. Wind turbine capacity frontier from SCADA. Wind Syst. Mag. 2012, 3, 36–39. [Google Scholar]
- Sttt, B.; Marinho, J.L. Linear programming for power system network security applications. IEEE Trans. Power Appl. Syst. 1979, 98, 837–848. [Google Scholar] [CrossRef]
- Burchett, R.C.; Happ, H.H.; Vierth, D.R. Quadratically convergent optimal power flow by Newton approach. IEEE Trans. Power Appl. Syst. 1985, 103, 3267–3275. [Google Scholar]
- Sun, D.I.; Ashly, B.; Brewer, B.; Hughes, A.; Tinney, W.F. Optimal power flow by Newton approach. IEEE Trans. Power Appl. Syst. 1984, 103, 2864–2880. [Google Scholar] [CrossRef]
- Wu, Y.; Debs, A.S.; Marsten, R.E. A direct nonlinear predictor-corrector primal-dual interior point algorithm for optimal power flow. IEEE Trans. Power Syst. 1994, 9, 876–882. [Google Scholar]
- Lin, C.-H.; Lin, S.-Y. A new dual-type method used in solving optimal power flow problems. IEEE Trans. Power Syst. 1997, 12, 1667–1675. [Google Scholar]
- Salgado, R.S.; Ranger, E.L., Jr. Optimal power flow solutions through multi-objective programming. Energy 2012, 42, 35–45. [Google Scholar] [CrossRef]
- Narimani, M.R.; Azizipanah-Abarghooee, R.; Zoghdar-Moghadam-Shahrekohne, B.; Gholami, K. A novel approach to multi-objective optimal power flow by a new hybrid optimization algorithm considering generator constraints and multi-fuel type. Energy 2013, 49, 119–136. [Google Scholar] [CrossRef]
- Niknam, T.; Narimani, M.R.; Jabbari, M.; Malekpour, A.R. A modified shuffle frog leaping algorithm for multi-objective optimal power flow. Energy 2011, 36, 6420–6432. [Google Scholar] [CrossRef]
- Niknam, T.; Azizipanah-Abarghooee, R.; Narimani, R. Reserve constrained dynamic optimal power flow subject to valve-point effects, prohibited zones and multi-fuel constraints. Energy 2012, 47, 451–464. [Google Scholar] [CrossRef]
- Varaiya, P.; Wu, F.F.; Bialek, J.W. Smart operation of smart grid: Risk-limiting dispatch. Proc. IEEE 2011, 99, 40–57. [Google Scholar] [CrossRef]
- Zhang, H.; Li, P. Chance constrained programming for optimal power flow under uncertainty. IEEE Trans. Power Syst. 2011, 26, 2417–2424. [Google Scholar] [CrossRef]
- Lin, S.-Y.; Lin, A.-C. RLOPF (risk-limiting optimal power flow) for systems with high penetration of wind power. Energy 2014, 71, 49–61. [Google Scholar] [CrossRef]
- Danaraj, R.M.S. Economic Dispatch by Quadratic Programming. Available online: http://www.mathworks.com/matlabcentral/fileexchange/19538-economic-dispatch-by-quadratic-programming (accessed on 4 April 2015).
- Svozil, D.; Kvasnicka, V.; Pospichal, J. Introduction to multi-layer feed-forward neural networks. Chemom. Intell. Lab. Syst. 1997, 39, 43–62. [Google Scholar] [CrossRef]
- Wei, X.; Kusiak, A.; Sadat, H.R. Prediction of influent flow rate: Data-mining approach. J. Energy Eng. 2012, 139, 118–123. [Google Scholar] [CrossRef]
- Wilamowski, B.M.; Yu, H. Improved computation for Levenberg-Marquardt training. IEEE Trans. Neural Netw. 2010, 21, 930–937. [Google Scholar] [CrossRef] [PubMed]
- Morales, J.M.; Perez-Ruiz, J. Point estimate schemes to solve the probabilistic power flow. IEEE Trans. Power Syst. 2007, 22, 1594–1601. [Google Scholar] [CrossRef]
- Zimmerman, R.; Murillo-Sanchez, C.; Gan, D. MATPOWER: A MATLAB Power System Simulation Package; PSERC, Cornell University: Ithaca, NY, USA, 2005. [Google Scholar]
- IIT Power Group. One-Line Diagram of IEEE 118-Bus System. Illinois Institute of Technology, 2003. Available online: http://motor.ece.iit.edu/data/IEEE118bus_inf/IEEE118bus_figure.pdf (accessed on 25 May 2015).


| Term | Content |
|---|---|
| (a) | Number of iterations executed in the RSONP algorithm |
| (b) | Corresponding CPU time of (a) |
| (c) | |
| (d) | |
| (e) |
| (a) * | (b) * | (c) * | (d) * | (e) * |
|---|---|---|---|---|
| 6 | 48.6 | 18.292 | 129,711.75 | 95.89 |
| 7 | 56.8 | 10.871 | 129,699.91 | 95.74 |
| 8 | 64.5 | 4.355 | 129,688.83 | 95.43 |
| 9 | 72.1 | 2.871 | 129,673.23 | 95.29 |
| 10 | 83.4 | 0.709 | 129,661.69 | 95.21 |
| (a) * | (b) * | (c) * | (d) * | (e) * |
|---|---|---|---|---|
| 6 | 47.5 | 18.278 | 129,709.06 | 95.86 |
| 7 | 56.4 | 10.843 | 129,696.38 | 95.65 |
| 8 | 65.3 | 4.326 | 129,681.13 | 95.38 |
| 9 | 71.5 | 2.858 | 129,670.84 | 95.26 |
| 10 | 82.6 | 0.722 | 129,659.72 | 95.17 |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lin, S.-Y.; Lin, A.-C. Risk-Limiting Scheduling of Optimal Non-Renewable Power Generation for Systems with Uncertain Power Generation and Load Demand. Energies 2016, 9, 868. https://doi.org/10.3390/en9110868
Lin S-Y, Lin A-C. Risk-Limiting Scheduling of Optimal Non-Renewable Power Generation for Systems with Uncertain Power Generation and Load Demand. Energies. 2016; 9(11):868. https://doi.org/10.3390/en9110868
Chicago/Turabian StyleLin, Shin-Yeu, and Ai-Chih Lin. 2016. "Risk-Limiting Scheduling of Optimal Non-Renewable Power Generation for Systems with Uncertain Power Generation and Load Demand" Energies 9, no. 11: 868. https://doi.org/10.3390/en9110868
APA StyleLin, S.-Y., & Lin, A.-C. (2016). Risk-Limiting Scheduling of Optimal Non-Renewable Power Generation for Systems with Uncertain Power Generation and Load Demand. Energies, 9(11), 868. https://doi.org/10.3390/en9110868