Security Risk Analysis of LoRaWAN and Future Directions
Abstract
:1. Introduction
- Smart Gas and Water Metering: This field is expected to witness the biggest growth rate. The traditional power grid started to be replaced by its smarter counterpart (smart-grid) and therefore smart-metering is one of the most important components, and which lets us understand energy consumption at all the levels of the power grid. The adoption of LPWAN technology by this sector would promote rapid standardization among various smart-meter manufacturers and vendors.
- Oil and gas operations: LPWAN connected devices and systems can provide more efficient oil and gas operations, by requiring minimum human-intervention, and constitute a higher value than legacy technologies.
- Smart streetlights: According to [4], a special application of LPWAN called LoRaWAN (this technology will be described thoroughly in the remaining part of this manuscript) has been already selected as an enabling technology to monitor not only light illumination levels, but also traffic intensity and air pollution levels of a city in smart city application.
- Livestock monitoring: It has been reported that, in another project (Cattle Traxx), yet again LoRaWAN has been used to track cows of a farm. End-devices are attached to the ear tags of the cows and gateways around the farm provide the position of the cows with the command center (attached to the application server) [4]. No GPS sensor is attached to the cattle, which leads to less power consumption, eventually less battery usage and less equipment installation on the animal. Hence, traditional triangulation methods are used to calculate the relative positions of the cows from the gateways. Therefore, three or more gateways are deployed in the field. The positions of the gateways are tracked with GPS sensor.
- High community support: LoRa users (the implementers and researchers) constitute a big community and they support each other. For example “The Things Network” is a crowd-sourced community from 85 countries building a global, public LoRa-based IoT data network [15].
- Installation cost: LoRa end-devices are cheap when compared to its rivals and this is important for large deployments.
2. Related Work
3. Introduction to LoRaWAN v1.1
3.1. Session Keys
3.2. Lifetime Join Session Keys
- JSIntKey (new): Used for the MIC of the Rejoin-Request type-1 messages and related Join-Accept answers.
- JSEncKey (new): Used for the encryption of the Join-Accept messages in response to Rejoin-Request messages.
3.3. Parameters
- A device address (DevAddr—new): Allocated by the NS of the end-device.
- Triplet of network session keys: FNwkSIntKey, SNwkSIntKey and NwkSEncKey
- Application session key: AppSKey
3.4. Frame Counters
- Network Session: FCntUp, NFCntDwn (new)
- Application Session: FCntUp, AFCntDwn (new)
3.5. New Requirements
4. Security Challenges of LoRaWAN v1.1
4.1. Network Entities Related
- These several network entities complicate network management. Orchestration of all these NS’s and Join Server, along with the Application Server (see Figure 2 for the architecture of LoRaWAN v1.1) is non-trivial for the service provider.
- Hence all the keys are embedded (installed) upfront to the end-devices; ABP of LoRaWAN v1.1 does not support re-keying of the session keys. In LoRaWAN v1.1, re-keying of the session keys are only possible with Join-initiation and Re-Join commands during OTAA session. However, there is no apparent mechanism to perform re-keying of the root keys on demand or periodically. A solution needs to be devised so that re-keying would be possible for the root keys as well. A candidate solution can be implementing a mechanism to acquire usage of smart-phones or Bluetooth enabled platforms such as tablets to initiate and perform re-keying of the root keys on-site by using explicit certificates.
- There is a lack of the definition on the session (e.g., an OTAA session) durations of LoRaWAN v1.1: It is ambiguous that how long a session lasts. The dwell time of the signals on air is very well defined in Physical Layer specification, however the session times for the higher protocol layers are not indicated in the specification document.
4.2. Key Distribution Related
- For the OTAA activation procedure, the root keys are needed for generating the session keys. These NwkKey and AppKey are AES-128 root keys specific to the end-device that are assigned to the end-device during fabrication. These keys need to be securely stored.
- During fabrication NwkKey/AppKey key-pair will be generated for each end-device (all related session keys are generated later on by using these specific root keys); but it brings the challenge about keeping the track and taking care of these key pairs.
- PKI can be used for distributing the keys to the end-devices, instead of embedding them during the fabrication process. This would introduce more flexibility and security to the LoRaWAN. Hence, by this way, it would be possible to update the root keys (NwkKey/AppKey pair) periodically as well. This remedy is further discussed in Section 6.1 with more details.
4.3. Implementation Related
4.4. Trust Related
- In the specification of LoRaWAN v1.1, following is stated: “Application payloads are end-to-end encrypted between the end-device and the application server, but they are integrity protected only in a hop-by-hop fashion: one hop between the end-device and the NS, and the other hop between the NS and the application server” [16]. As mentioned in [24], this means that, a malicious NS may be able to alter the content of the data messages in transit, which may even help the NS to infer some information about the data by observing the reaction of the application end-points to the altered data. As a conclusion to this statement, it can be stated that end-to-end confidentiality and integrity protection between the servers is not warranted or supported by LoRaWAN v1.1.
- While the specification implements a “federated NS infrastructure in which network operators are not able to eavesdrop on application data”, there is some trust put on the NS in that it will not perform selective forwarding attack or act as a sinkhole.
4.5. Roaming-Related
- Both versions of LoRaWAN are susceptible to bit-flipping attacks (please refer to next section for details of this attack type) happening in between servers. The inclusion of handover-roaming in v1.1 makes the situation worse.
- As also stressed in [34], handover-roaming enables more possibilities for a MITM attack.
- Handover-roaming can cause a fall-back when the back-end () that serves the roaming runs an older version of LoRaWAN, i.e., v1.0 [34].
4.6. Compatibility-Related
5. Security Threat and Risk Assessment of LoRaWAN v1.1
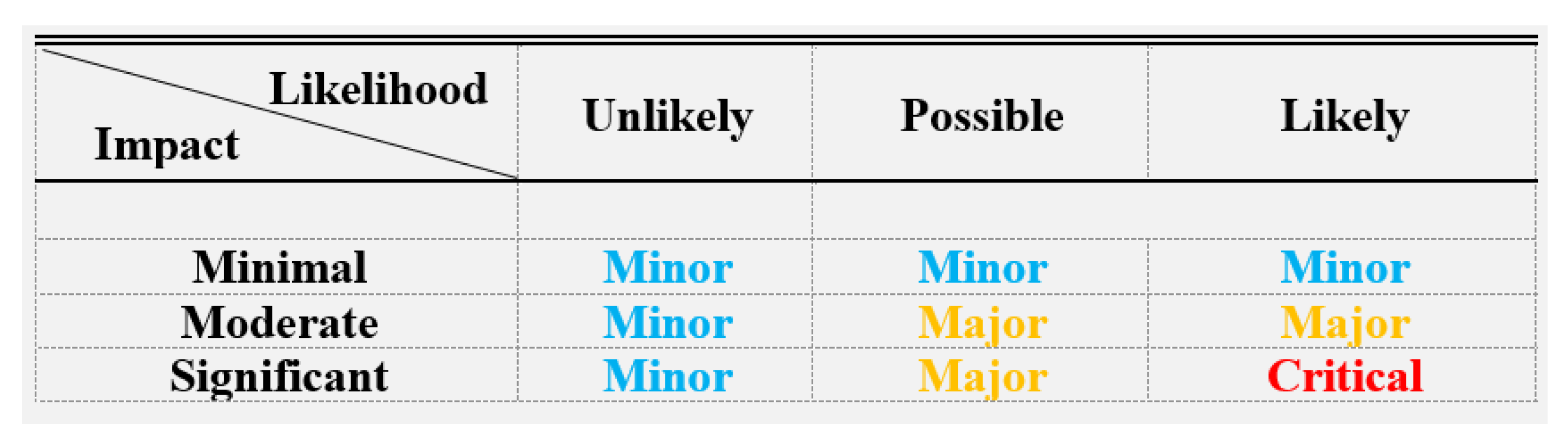
5.1. Risk Assessment Methodology
5.1.1. Likelihood Assessment
5.1.2. Impact Assessment
5.1.3. Risk Assessment
5.2. LoRaWAN v1.1 Threat Catalog
5.2.1. False Join Packets
5.2.2. MITM Attacks
- Bit-flipping or Message Forgery Attack: As also mentioned earlier in Section 2, several security vulnerabilities of LoRaWAN v1.0 are presented in [29]. Especially, a specific version of MITM attack called “bit-flipping attack”, in which an adversary (or a rogue ) changes the content of the messages in between and . Bit-flipping attack still constitutes a threat for v1.1 as also declared in the specification document [16].
- Frame Payload Attack:Section 4.5 described that handover-roaming enables more possibilities for a MITM attack, as the unprotected FRMPayload’s are first transported from the (serving-NS) to the (homing-NS), and from there to the .
5.2.3. Network Flooding Attack
5.2.4. Network Traffic Analysis
5.2.5. Physical Attacks
- Destroy, Remove, or Steal End-device: In both versions of LoRaWAN, root keys (from which session keys are generated) are uniquely generated for each device during fabrication or before deployment. Therefore, revealing of a single root key will not compromise any information in the network other than the data stored at that specific device.
- Security Parameter Extraction: The LoRaWAN specification [16] requires protection of the relevant key material against reuse, but nodes need to be adequately protected against firmware change that might indirectly lead to key material reuse.
- Device Cloning or Firmware Replacement: An attacker with physical access to the device and can replace firmware or steal/reuse key material. While [16] specifically mentions protection of the relevant key material against reuse, but nodes need to be adequately protected against firmware change that might indirectly lead to key material reuse.
5.2.6. Plaintext Key Capture
5.2.7. RF Jamming Attack
5.2.8. Rogue End-Device Attack
5.2.9. Rogue Gateway Attack
- Beacon Synchronization DoS Attack: Class B sessions might be vulnerable to Rogue-Gateway attack, which is in line with Session Hijacking Attacks. In LoRaWAN, Class B beacons are not secured by any means, indicating that an attacker can set up a Rogue-GW to send fake beacons. This could result in class B end-devices to receive messages in windows out-of-sync with the Rogue-GW and also increased collisions on packets being transmitted. Addressing this threat would require issuing a key that ’s could use to authenticate beacon transmissions.
- Impersonation Attack: Gateways (GWs) can also be impersonated to set-up attacks against end-devices (EDs). EDs can be listened to and their network addresses can be determined. More importantly, a triangulation method (minimum 3 GWs are needed in this case to perform the intended capturing attack towards the ED) can be used to determine the physical location of the EDs.
5.2.10. Routing Attacks
- Selective Forwarding Attack: In this attack type, an attacker can selectively forward packets and can cause one or several nodes in the network to be totally blocked, or totally overwhelmed.
- Sinkhole or Blackhole Attack: In these attacks, an attacker attracts the traffic through itself by falsely advertising modified routing information. As a result, whole network traffic might collapse.
5.2.11. Self-Replay Attack
5.3. Security Risk Analysis of LoRaWAN v1.1
- Bit-flipping or Message Forgery Attack
- Destroy, Remove, or Steal End-device
- False Join Packets
- Frame Payload Attack
- Network Flooding Attack
- Network Traffic Analysis
- RF Jamming Attack
- Selective Forwarding Attack
- Sinkhole or Blackhole Attack
- Beacon Synchronization DoS Attack (major risk for availability and minor risk for the rest)
- Impersonation Attack (major risk for availability and minor risk for the rest)
- Plaintext Key Capture (minor risk for availability and major risk for the rest)
- Security Parameter Extraction (minor risk for integrity and availability and major risk for the rest)
- Device Cloning or Firmware Replacement (critical risk for authentication and access control, major risk for confidentiality and integrity and minor risk for availability)
- Self-Replay Attack (critical risk for availability and minor risk for the rest)
- Rogue End-Device Attack (critical risk for authentication and access control availability and minor risk for the rest)
6. Security Suggestions for the Improvement of LoRaWAN
6.1. Usage of Public Certificates for Generation of Root Keys at the End-Devices
6.2. Nonce Related Improvement
6.3. Introduction of End-to-End Encryption between Servers
6.4. Inclusion of Padding
6.5. Packet Count Limitation
6.6. Time Synchronization
6.7. Gateway Related Improvement
6.8. Server Trust Related Suggestion
6.9. End-Device Related Improvement
7. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| ABP | Activation by Personalization |
| ADHE | Authenticated Diffie-Hellman key Exchange algorithm |
| ADR | Adaptive Data Rate |
| AFCntDwn | Application Frame Counter Down |
| AppKey | Application Key, root key for AppSKey |
| AS | Application Server |
| CSS | Chirp Spread Spectrum |
| DER | Data Extraction Rate |
| DevAddr | Device Address of end-device |
| DevNonce | Device Nonce of end-device |
| DoS | Denial of Service |
| ED | End Device |
| ETSI | European Telecommunications Standards Institute |
| FCntUp | Frame Counter Up |
| fNs | forwarding Network server |
| FNwkSIntKey | Forwarding Network Session Integrity Key |
| GW | Gateway |
| HSM | Hardware Security Module |
| IoT | Internet of things |
| JoinNonce | Nonce of Joining server |
| JS | Joining Server |
| JSEncKey | Joining Session Encryption Key |
| JSIntKey | Joining Session Initiation Key |
| LoRa | Long-Range LPWAN technology |
| LoRaWAN | An application of LoRa |
| LPWAN | Low Power Wide Area Network |
| MIC | Message Integrity Check |
| MITM | Man-In-The-Middle attack |
| NFCntDwn | Network Frame Counter Down |
| NS | Network Server |
| NwkKey | Network Key, root key for session keys: FNwkSIntKey, NwkSEncKey, SNwkSIntKey |
| NwkSEncKey | Network Session Encryption Key |
| OTAA | Over the Air Activation |
| PKI | Public Key Infrastructure |
| RD | Rogue Device |
| RF | Radio Frequency |
| SE | Secure Elements |
| SNwkSIntKey | Serving Network Session Integrity Key |
| SWOT | Strength, Weakness, Opportunity and Threat analysis |
References
- Friedman, V. On the Edge: Solving the Challenges of Edge Computing in the Era of IoT. Data-Economy.com. Available online: https://data-economy.com/on-the-edge-solving-the-challenges-of-edge-computing-in-the-era-of-iot/ (accessed on 13 September 2018).
- Rohan, M. Low Power Wide Area Network Market Worth 24.46 Billion USD by 2021. Biz Journals. Available online: https://www.bizjournals.com/prnewswire/press_releases (accessed on 22 August 2018).
- Kocakulak, M.; Butun, I. An overview of Wireless Sensor Networks towards internet of things. In Proceedings of the 2017 IEEE 7th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 9–11 January 2017; pp. 1–6. [Google Scholar]
- De Carvalho Silva, J.; Rodrigues, J.J.; Alberti, A.M.; Solic, P.; Aquino, A.L. LoRaWAN—A low power WAN protocol for Internet of Things: A review and opportunities. In Proceedings of the 2017 2nd International Multidisciplinary Conference on Computer and Energy Science (SpliTech), Split, Croatia, 12–14 July 2017; pp. 1–6. [Google Scholar]
- LoRa Technology. Semtech Inc. Available online: http://www.semtech.com/wireless-rf/internet-of-things/what-is-lora/ (accessed on 22 August 2018).
- Sigfox Inc. Available online: https://sigfox.com (accessed on 22 August 2018).
- Home Standardization of NB-IoT Completed. Available online: http://www.3gpp.org/news-events/3gpp-news/1785-nb_iot_complete (accessed on 22 October 2018).
- Weightless SIG. Available online: http://weightless.org/ (accessed on 22 August 2018).
- Waviot Inc. Available online: http://waviot.com/ (accessed on 22 August 2018).
- Nwave Technologies Inc. Available online: http://nwave.io (accessed on 22 August 2018).
- Ingenu Inc. Available online: http://ingenu.com/technology/rpma/ (accessed on 22 August 2018).
- Telensa Inc. Available online: https://telensa.com/unb-wireless/ (accessed on 22 August 2018).
- Qowisio Inc. Available online: http://qowisio.com (accessed on 22 August 2018).
- Vangelista, L.; Zanella, A.; Zorzi, M. Long-range IoT technologies: The dawn of LoRa™. In Future Access Enablers of Ubiquitous and Intelligent Infrastructures; Springer: Cham, Switzerland, 2015; pp. 51–58. [Google Scholar]
- The Things Network. Available online: http://thethingsnetwork.org/ (accessed on 22 August 2018).
- LoRaWAN 1.1 Specification. Lora Alliance. 2017. Available online: http://lora-alliance.org/lorawan-for-developers (accessed on 22 August 2018).
- The New Gumstix Conduit Dev Boards. Available online: https://gumstix.com/lorawan-family/ (accessed on 22 August 2018).
- Kolias, C.; Kambourakis, G.; Gritzalis, S. Attacks and countermeasures on 802.16: Analysis and assessment. IEEE Commun. Surv. Tutor. 2013, 15, 487–514. [Google Scholar] [CrossRef]
- Antipolis, S.; Girard, P. Low Power Wide Area Networks Security; White Paper; Gemalto Inc.: Amsterdam, The Netherlands, 2015. [Google Scholar]
- Tomasin, S.; Zulian, S.; Vangelista, L. Security Analysis of LoRaWAN Join Procedure for Internet of Things Networks. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), San Francisco, CA, USA, 19–22 March 2017; pp. 1–6. [Google Scholar]
- Zulian, S. Security Threat Analysis and Countermeasures for Lorawan Join Procedure. Master’s Thesis, Universit’a degli Studi di Padova, Padova, Italy, 2016. [Google Scholar]
- Naoui, S.; Elhdhili, M.E.; Saidane, L.A. Enhancing the security of the IoT LoraWAN architecture. In Proceedings of the 2016 International Conference on Performance Evaluation and Modeling in Wired and Wireless Networks (PEMWN), Paris, France, 22–25 November 2016; pp. 1–7. [Google Scholar]
- Miller, R. Lora Security: Building a Secure Lora Solution. In Proceedings of the 2017 SyScan360 Information Security Conference, Seattle, WA, USA, 31 May 2017. [Google Scholar]
- Kim, J.; Song, J. A Dual Key-Based Activation Scheme for Secure LoRaWAN. Wirel. Commun. Mob. Comput. 2017, 2017. [Google Scholar] [CrossRef]
- Na, S.; Hwang, D.; Shin, W.; Kim, K.H. Scenario and countermeasure for replay attack using join request messages in LoRaWAN. In Proceedings of the 2017 International Conference on Information Networking (ICOIN), Da Nang, Vietnam, 11–13 January 2017; pp. 718–720. [Google Scholar]
- Mahmood, A.; Sisinni, E.; Guntupalli, L.; Rondon, R.; Hassan, S.A.; Gidlund, M. Scalability Analysis of a LoRa Network under Imperfect Orthogonality. IEEE Trans. Ind. Inform. 2018. [Google Scholar] [CrossRef]
- Aras, E.; Ramachandran, G.S.; Lawrence, P.; Hughes, D. Exploring The Security Vulnerabilities of LoRa. In Proceedings of the 2017 3rd IEEE International Conference on Cybernetics (CYBCONF), Exeter, UK, 21–23 June 2017; pp. 1–6. [Google Scholar]
- Voigt, T.; Bor, M.; Roedig, U.; Alonso, J. Mitigating Inter-network Interference in LoRa Networks. In Proceedings of the 2017 International Conference on Embedded Wireless Systems and Networks, Uppsala, Sweden, 20–22 February 2017; pp. 323–328. [Google Scholar]
- Yang, X. LoRaWAN: Vulnerability Analysis and Practical Exploitation. M.Sc. Thesis, Delft University of Technology, Delft, The Netherlands, 2017. [Google Scholar]
- Lin, J.; Shen, Z.; Miao, C. Using Blockchain Technology to Build Trust in Sharing LoRaWAN IoT. In Proceedings of the 2nd International Conference on Crowd Science and Engineering, Beijing, China, 6–9 July 2017; pp. 38–43. [Google Scholar]
- Sanchez-Iborra, R.; Sánchez-Gómez, J.; Pérez, S.; Fernández, P.J.; Santa, J.; Hernández-Ramos, J.L.; Skarmeta, A.F. Enhancing LoRaWAN Security through a Lightweight and Authenticated Key Management Approach. Sensors 2018, 18, 1833. [Google Scholar] [CrossRef] [PubMed]
- You, I.; Kwon, S.; Choudhary, G.; Sharma, V.; Seo, J.T. An Enhanced LoRaWAN Security Protocol for Privacy Preservation in IoT with a Case Study on a Smart Factory-Enabled Parking System. Sensors 2018, 18. [Google Scholar] [CrossRef] [PubMed]
- Haxhibeqiri, J.; De Poorter, E.; Moerman, I.; Hoebeke, J. A Survey of LoRaWAN for IoT: From Technology to Application. Sensors 2018, 18, 3995. [Google Scholar] [CrossRef] [PubMed]
- Dönmez, T.C.; Nigussie, E. Security of LoRaWAN v1.1 in Backward Compatibility Scenarios. Procedia Comput. Sci. 2018, 134, 51–58. [Google Scholar] [CrossRef]
- Butun, I.; Pereira, N.; Gidlund, M. Analysis of LoRaWAN V1.1 Security: Research Paper. In Proceedings of the 4th ACM MobiHoc Workshop on Experiences with the Design and Implementation of Smart Objects, Los Angeles, CA, USA, 25 June 2018; ACM: New York, NY, USA, 2018; pp. 5:1–5:6. [Google Scholar] [CrossRef]
- Plósz, S.; Farshad, A.; Tauber, M.; Lesjak, C.; Ruprechter, T.; Pereira, N. Security vulnerabilities and risks in industrial usage of wireless communication. In Proceedings of the 2014 IEEE Emerging Technology and Factory Automation (ETFA), Barcelona, Spain, 16–19 September 2014; pp. 1–8. [Google Scholar]
- ETSI, TS. Telecommunications and Internet Protocol Harmonization over Networks (TIPHON) Release 4; Protocol Framework Definition; Methods and Protocols for Security; Part 1: Threat Analysis; Technical Specification; ETSI TS: S. Antipolis, France, 2003; Volume 102, p. 165-1. [Google Scholar]
- Adelantado, F.; Vilajosana, X.; Tuset-Peiro, P.; Martinez, B.; Melia-Segui, J.; Watteyne, T. Understanding the limits of LoRaWAN. IEEE Commun. Mag. 2017, 55, 34–40. [Google Scholar] [CrossRef]
- Boyko, V.; MacKenzie, P.; Patel, S. Provably secure password-authenticated key exchange using Diffie-Hellman. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Bruges, Belgium, 14–18 May 2000; pp. 156–171. [Google Scholar]
- Meier, S.; Schmidt, B.; Cremers, C.; Basin, D. The TAMARIN prover for the symbolic analysis of security protocols. In Proceedings of the International Conference on Computer Aided Verification, Saint Petersburg, Russia, 13–19 July 2013; pp. 696–701. [Google Scholar]
- Cremers, C.J.F. Scyther: Semantics and Verification of Security Protocols. Ph.D. Thesis, Eindhoven University of Technology, Eindhoven, The Netherlands, 2006. [Google Scholar]





© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Butun, I.; Pereira, N.; Gidlund, M. Security Risk Analysis of LoRaWAN and Future Directions. Future Internet 2019, 11, 3. https://doi.org/10.3390/fi11010003
Butun I, Pereira N, Gidlund M. Security Risk Analysis of LoRaWAN and Future Directions. Future Internet. 2019; 11(1):3. https://doi.org/10.3390/fi11010003
Chicago/Turabian StyleButun, Ismail, Nuno Pereira, and Mikael Gidlund. 2019. "Security Risk Analysis of LoRaWAN and Future Directions" Future Internet 11, no. 1: 3. https://doi.org/10.3390/fi11010003
APA StyleButun, I., Pereira, N., & Gidlund, M. (2019). Security Risk Analysis of LoRaWAN and Future Directions. Future Internet, 11(1), 3. https://doi.org/10.3390/fi11010003






