Analysis of Dynamic Complexity of the Cyber Security Ecosystem of Colombia
Abstract
:1. Introduction
2. Conceptualization
2.1. Ecosystem
- In a natural ecosystem, every living organism is inter-dependent and need one another. Likewise, in a technology ecosystem every component is inter-dependent on one another. If one component is entirely independent, then; it is not part of the ecosystem.
- Diversity in ecosystems is the main constituent of stability. The more diverse an ecosystem, the more likely it is to offer possibilities and opportunities under the premises of harmony, unity, security, and coherence.
- The growth of a system is expected to occur in a controlled manner as raw materials are limited. That is why, the technology ecosystem must evolve under the guidance of a clear and specific objective. Otherwise, it would become unsustainable and therefore the objective for which it was created might not be achieved.
2.2. The Influence Language of System Dynamics
2.3. Domain Model from Software Engineering
2.4. Cyber Security
3. Cyber Security Ecosystem of Colombia
3.1. Legislation and Political Guidelines of Cyber Security in Colombia
3.2. Definition of the Components of the Cyber Security Ecosystem of Colombia
3.3. Entities of the Cyber Security Ecosystem of Colombia
3.4. Cyber Security as a Strategic Component of National Security
4. Complexity of the Cyber Security Ecosystem of Colombia Visualized from an Influence Diagram of System Dynamics and the Domain Model of Software Engineering
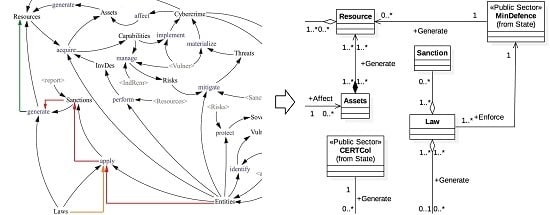
4.1. Influence Diagrams in the Cyber Security Ecosystem of Colombia
4.2. Domain Model of the Cyber Security Ecosystem of Colombia from Software Engineering
- <<Meta>>Public Sector.
- <<Meta>>Private Sector.
- <<Meta>>Citizen.
- <<Meta>>Research Center.
- <<Meta>>Attacker.
- <<Meta>>Critical Infrastructure.
- 1.
- State (Figure 15): composed by the organisms or institutions that have a direct relationship with anything related to cyber security in the public sector:
- <<Public Sector>> President.<<Public Sector>> Congress.<<Public Sector>> Chancellor´s Office.<<Public Sector>> NIA.<<Public Sector>> MinDefence.
- <<Public Sector>> CPC.
- <<Public Sector>> CCG.
- <<Public Sector>> CERTCol.
<<Public Sector>> NPD.<<Public Sector>> MinICT.- <<Public Sector>> CRC.
<<Public Sector>> MinJustice.<<Public Sector>> MinCIT.- <<Public Sector>> SIC.
<<Public Sector>> MinFinance.- <<Public Sector>> FSC.
<<Public Sector>> Judicial Branch.<<Public Sector>> Attorney General Office – TBI<<Public Sector>> Public Administration.<<Critical Infrastructure>> Critical Infrastructure.
- 2.
- Attackers (Figure 16): entities capable of affecting other entities or their assets. Any entity found in the model can be included in this group if their actions lead to the commitment of a cybercrime.
- <<Attackers>> Hacktivist.<<Attackers>> Hacker.<<Attackers>> Contractor.<<Attackers>> Criminal organization.<<Attackers>> Terrorist group.<<Attackers>> Competing businesses.<<Attackers>> Sabotaging employee
- 3.
- Sectors (Figure 17) (Private sector, citizens, research centers):
- <<Private Sector>> Big business.<<Private Sector>> Small and medium business.<<Private Sector>> Independent.<<Private Sector>> Contracted labor.<<Private Sector>> Financing.<<Private Sector>> ICT.<<Critical Infrastructure>> Critical Infrastructure.<<Citizen>> Internet user.<<Citizen>> Telecommunications user.<<Citizen>> Citizens Organizations.<<Citizen>> Underage citizens.<<Citizen>> Residents.<<Research center>> Colciencias.<<Research center>> Academic institutions.<<Research center>> Excellency center.<<Research center>> Think thank.<<Research center>> Research and innovation center.
- Protect the Sovereignty (critical infrastructure).Protect Sovereignty (Risks).Reduce Threats (Risks, Sanctions).
- Enforce Sanctions (Laws): Resources.Make Laws (Regulation): Laws.Make Laws (Indicators and Recommendations): Laws.Make Regulation (Strategies): Regulation.Generate Resources (Sanctions, Laws): Resources.Generate Strategies (Cybercrimes): Strategies.
- Acquire Capability (Investigation and Development): Capabilities.Acquire Assets (Resources, Investigation and Development): Assets.Report (Cybercrimes): Sanctions.Manage Risks (Capabilities, Indicators and Recommendations, Vulnerabilities): Indicators and Recommendations.Generate Resources (Assets): Resources.Generate Indicators and Recommendations (Strategies): Indicators and Recommendations.Generate Strategies (Cybercrimes): Strategies.Generate Regulation (Strategies): Regulation.Identify Vulnerabilities (Indicators and Recommendations): Vulnerabilities.Promote Regulation (Strategies): Regulation.Realize Investigation and Development (Resources): Investigation and Development.
- Affect Entities (Cybercrimes).Affect Assets (Cybercrimes).
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Organización de los Estados Americanos. Misión de Asistencia Técnica en Seguridad Cibernética: Conclusiones y Recomendaciones. Available online: http://www.oas.org/documents/spa/press/Recomendaciones_COLOMBIA_SPA.pdf (accessed on 10 March 2015).
- Schaffernicht, M. Indagación de Situaciones Complejas Mediante la Dinámica de Sistemas; Editorial Universidad de Talca: Santiago de Chile, Chile, 2009. [Google Scholar]
- Oropeza Cortés, M.G.; Urciaga García, J.I.; Ponce Díaz, G. Importancia Económica y Social de los Servicios de los Ecosistemas: Una revisión de la Agenda de Investigación. Rev. Glob. Negoc. 2015, 3, 103–113. [Google Scholar]
- García-Holgado, A.; García-Penalvo, F.J. Análisis de integración de soluciones basadas en software como servicio para la implantación de ecosistemas tecnológicos corporativos. Repos. Doc. Univ. Salamanca 2013. Available online: http://gredos.usal.es/jspui/handle/10366/122472 (accessed on 4 July 2016). [Google Scholar]
- Andrade, H.; Dyner, I.; Espinosa, A.; López, H.; Sotaquirá, R. Pensamiento Sistémico: Diversidad en Búsqueda de Unidad; Universidad Industrial de Santander: Santander, Colombia, 2001. [Google Scholar]
- Gómez, U.E.; Andrade, H.H.; Vásquez, C.A. Lineamientos Metodológicos para construir Ambientes de Aprendizaje en Sistemas Productivos Agropecuarios soportados en Dinámica de Sistemas. Inf. Tecnol. 2015, 26, 125–136. [Google Scholar] [CrossRef]
- ISO/IEC. International Standard ISO/IEC 27032: Information Technology—Security techniques—Guidelines for Cybersecurity; ISO/IEC: Geneva, Switzerland, 2012. [Google Scholar]
- Larman, C. UML y Patrones, 2nd ed.; Pearson Prentice Hall: Madrid, Spain, 2005; pp. 121–165. [Google Scholar]
- Consejo Nacional de Política Económica y Social. República de Colombia. Departamento Nacional de Planeación. Documento CONPES 3701. Available online: http://www.mintic.gov.co/portal/604/articles-3510_documento.pdf (accessed on 12 June 2015).
- República de Colombia. Constitución Política de Colombia. Available online: http://www.secretariasenado.gov.co/senado/basedoc/constitucion_politica_1991.html (accessed on 10 June 2015).
- El Congreso de Colombia. Ley No. 1341. Available online: http://www.mintic.gov.co/portal/604/articles-3707_documento.pdf (accessed on 12 June 2015).
- Ministerio de Defensa Nacional. Decreto 1512 de 2000. Available online: http://www.mindefensa.gov.co/irj/go/km/docs/Mindefensa/Documentos/descargas/Sobre_el_Ministerio/fondelibertad/Dec_1512_2000.pdf (accessed on 12 June 2015).
- Ministerio de Defensa Nacional. Resolución 127 de 2012. Available online: http://www.icbf.gov.co/cargues/avance/docs/resolucion_mindefensa_0127_2012.htm (accessed on 10 June 2015).
- Ministerio de Defensa Nacional. Resolución 3933 de 2013. Available online: http://www.icbf.gov.co/cargues/avance/docs/resolucion_mindefensa_3933_2013.htm (accessed on 12 June 2015).
- Presidente de la República de Colombia. Decreto 3355 de 2009. Available online: https://www.cancilleria.gov.co/sites/default/files/Normograma/docs/decreto_3355_2009.htm (accessed on 5 June 2015).
- Departamento Nacional de Planeación. Subdirección de Seguridad y Defensa: Gobierno de Colombia. Available online: https://www.dnp.gov.co/programas/justicia-seguridad-y-gobierno/Paginas/subdireccion-de-seguridad-y-defensa.aspx (accessed on 12 June 2015).
- Departamento Administrativo de la Función Pública. Decreto Número 2897 de 2011. Available online: http://wsp.presidencia.gov.co/Normativa/Decretos/2011/Documents/Agosto/11/dec289711082011.pdf (accessed on 5 June 2015).
- Ministerio de Hacienda y Crédito Público. Ministerio de Hacienda y Crédito Público: ¿Conoces el Ministerio? Available online: http://www.minhacienda.gov.co/HomeMinhacienda/elministerio (accessed on 10 June 2015).
- Ministerio de Comercio, Industrial y Turismo. Misión, Visión, Objetivos, Normas y Principios Éticos. Available online: http://www.mincit.gov.co/publicaciones.php?id=13 (accessed on 5 June 2015).
- Superintendencia Financiera de Colombia. Acerca de la Superintentencia Finanaciera de Colombia. Available online: https://www.superfinanciera.gov.co/jsp/loader.jsf?lServicio=Publicaciones&lTipo=publicaciones&lFuncion=loadContenidoPublicacion&id=60607#funciones2 (accessed on 7 June 2015).
- Superintendencia Financiera de Colombia. Circular Externa 052 de 2007. Available online: https://www.superfinanciera.gov.co/SFCant/ConsumidorFinanciero/ce05207.docx (accessed on 12 June 2015).
- El Congreso de Colombia. Ley Estatutaria No. 1581. Available online: http://www.sic.gov.co/drupal/sites/default/files/normatividad/Ley_1581_2012.pdf (accessed on 4 June 2015).
- Departamento de Seguridad Nacional de España. Estrategia de Seguridad Nacional: Un Proyecto Compartido. Available online: http://www.lamoncloa.gob.es/documents/seguridad_1406connavegacionfinalaccesiblebpdf.pdf (accessed on 9 May 2015).
- Booch, G.; Rumbaugh, J.; Jacoboson, I. El Lenguaje Unificado de Modelado; Pearson: Madrid, Spain, 2004. [Google Scholar]





















© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Flórez, A.; Serrano, L.; Gómez, U.; Suárez, L.; Villarraga, A.; Rodríguez, H. Analysis of Dynamic Complexity of the Cyber Security Ecosystem of Colombia. Future Internet 2016, 8, 33. https://doi.org/10.3390/fi8030033
Flórez A, Serrano L, Gómez U, Suárez L, Villarraga A, Rodríguez H. Analysis of Dynamic Complexity of the Cyber Security Ecosystem of Colombia. Future Internet. 2016; 8(3):33. https://doi.org/10.3390/fi8030033
Chicago/Turabian StyleFlórez, Angélica, Lenin Serrano, Urbano Gómez, Luis Suárez, Alejandro Villarraga, and Hugo Rodríguez. 2016. "Analysis of Dynamic Complexity of the Cyber Security Ecosystem of Colombia" Future Internet 8, no. 3: 33. https://doi.org/10.3390/fi8030033