Sustainable Information Security Behavior Management: An Empirical Approach for the Causes of Employees’ Voice Behavior
Abstract
:1. Introduction
2. Literature Review
2.1. Information Security-Related Voice Behavior
2.2. Information Security-Related Work Impediment
2.3. Organizational Identification
2.4. Information Security-Related Organization Justice
2.5. Justice Sensitivity
3. Research Model and Hypotheses
3.1. Research Model
3.2. Hypotheses Development
3.2.1. Information Security-Related Organization Justice
3.2.2. Intention Information Security-Related Work Impediment
3.2.3. Organizational Identification
3.2.4. Justice Sensitivity
4. Research Methodology
4.1. Participants and Data Collection
4.2. Measurement Development
5. Analysis Results
5.1. Validity and Reliability
5.2. Structural Model Assessment
5.3. Assessment of Moderation Effects
6. Conclusions
6.1. Summary
6.2. Implications
6.3. Limitations and Future Research
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Grand View Research. Cyber Security Market Size, Share & Trends Analysis Report by Component, by Security Type, by Solution, by Service, by Deployment, by Organization, by Application, and Segment Forecasts, 2019–2025. 2019. Available online: https://www.globenewswire.com (accessed on 30 April 2021).
- Verizon. 2020 Data Breach Investigations Report. 2020. Available online: https://enterprise.verizon.com (accessed on 30 July 2020).
- Loch, K.D.; Carr, H.H.; Warkentin, M.E. Threats to information systems: Today’s reality, yesterday’s understanding. MIS Q. 1992, 16, 173–186. [Google Scholar] [CrossRef] [Green Version]
- Bulgurcu, B.; Cavusoglu, H.; Benbasat, I. Information security policy compliance: An empirical study of rationality-based beliefs and information security awareness. MIS Q. 2010, 34, 523–548. [Google Scholar] [CrossRef] [Green Version]
- Kajtazi, M.; Cavusoglu, H.; Benbasat, I.; Haftor, D. Escalation of commitment as an antecedent to noncompliance with information security policy. Inf. Comput. Secur. 2018, 26, 171–193. [Google Scholar] [CrossRef] [Green Version]
- Guo, K.H.; Yuan, Y.; Archer, N.P.; Connelly, C.E. Understanding nonmalicious security violations in the workplace: A composite behavior model. J. Manag. Inf. Syst. 2011, 28, 203–236. [Google Scholar] [CrossRef] [Green Version]
- Jaeger, L.; Eckhardt, A.; Kroenung, J. The role of deterrability for the effect of multi-level sanctions on information security policy compliance: Results of a multigroup analysis. Inf. Manag. 2021, 58, 103318. [Google Scholar] [CrossRef]
- Posey, C.; Roberts, T.L.; Lowry, P.B. The impact of organizational commitment on insiders’ motivation to protect organizational information assets. J. Manag. Inf. Syst. 2015, 32, 179–214. [Google Scholar] [CrossRef]
- Wu, D. Empirical study of knowledge withholding in cyberspace: Integrating protection motivation theory and theory of reasoned behavior. Comput. Hum. Behav. 2020, 105, 106229. [Google Scholar] [CrossRef]
- Tsai, M.-T.; Cheng, N.-C. Understanding knowledge sharing between IT professionals an integration of social cognitive and social exchange theory. Behav. Inf. Technol. 2012, 31, 1069–1080. [Google Scholar] [CrossRef]
- Alam, M.A. Techno-stress and productivity: Survey evidence from the aviation industry. J. Air Transp. Manag. 2016, 50, 62–70. [Google Scholar] [CrossRef]
- Judge, T.A.; Colquitt, J.A. Organizational justice and stress: The mediating role of work-family conflict. J. Appl. Psychol. 2004, 89, 395–404. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Colquitt, J.A. On the dimensionality of organizational justice: A construct validation of a measure. J. Appl. Psychol. 2001, 86, 386–400. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Yoon, C. Theory of planned behavior and ethics theory in digital piracy: An integrated model. J. Bus. Ethic. 2010, 100, 405–417. [Google Scholar] [CrossRef]
- Gori, A.; Topino, E.; Palazzeschi, L.; Di Fabio, A. How can organizational justice contribute to job satisfaction? A chained mediation model. Sustainability 2020, 12, 7902. [Google Scholar] [CrossRef]
- Zhang, Y.; LePine, J.A.; Buckman, B.R.; Wei, F. It’s not fair or is it? The role of justice and leadership in explaining work stressor–job performance relationships. Acad. Manag. J. 2014, 57, 675–697. [Google Scholar] [CrossRef]
- Adams, J.S. Inequity in social exchange. In Advances in Experimental Social Psychology; Elsevier BV: Amsterdam, The Netherlands, 1965; Volume 2, pp. 267–299. [Google Scholar]
- Ding, M.C.; Lii, Y.S. Handling online service recovery: Effects of perceived justice on online games. Telemat. Inform. 2016, 33, 881–895. [Google Scholar] [CrossRef]
- Schmitt, M.; Gollwitzer, M.; Maes, J.; Arbach, D. Justice sensitivity. Eur. J. Psychol. Assess. 2005, 21, 202–211. [Google Scholar] [CrossRef]
- Xue, Y.; Liang, H.; Wu, L. Punishment, justice, and compliance in mandatory IT settings. Inf. Syst. Res. 2011, 22, 400–414. [Google Scholar] [CrossRef]
- Li, H.; Sarathy, R.; Zhang, J.; Luo, X. Exploring the effects of organizational justice, personal ethics and sanction on internet use policy compliance. Inf. Syst. J. 2014, 24, 479–502. [Google Scholar] [CrossRef]
- Safa, N.S.; Maple, C.; Furnell, S.; Azad, M.A.; Perera, C.; Dabbagh, M.; Sookhak, M. Deterrence and prevention-based model to mitigate information security insider threats in organisations. Future Gener. Comput. Syst. 2019, 97, 587–597. [Google Scholar] [CrossRef]
- West, R. The psychology of security. Commun. ACM 2008, 51, 34–40. [Google Scholar] [CrossRef]
- Dong, K.; Ali, R.; Dominic, P.; Ali, S. The effect of organizational information security climate on information security policy compliance: The mediating effect of social bonding towards healthcare nurses. Sustainability 2021, 13, 2800. [Google Scholar] [CrossRef]
- Hwang, I.; Kim, D.; Kim, T.; Kim, S. Why not comply with information security? An empirical approach for the causes of non-compliance. Online Inf. Rev. 2017, 41, 2–18. [Google Scholar] [CrossRef]
- Van Dyne, L.; LePine, J.A. Helping and voice extra-role behaviors: Evidence of construct and predictive validity. Acad. Manag. J. 1998, 41, 108–119. [Google Scholar]
- Song, J.; Wu, J.; Gu, J. Voice behavior and creative performance moderated by stressors. J. Manag. Psychol. 2017, 32, 177–192. [Google Scholar] [CrossRef]
- Svendsen, M.; Joensson, T.S. Transformational leadership and change related voice behavior. Leadersh. Organ. Dev. J. 2016, 37, 357–368. [Google Scholar] [CrossRef]
- Tarafdar, M.; Tu, Q.; Ragu-Nathan, B.S.; Ragu-Nathan, T.S. The impact of technostress on role stress and productivity. J. Manag. Inf. Syst. 2007, 24, 301–328. [Google Scholar] [CrossRef]
- Ragu-Nathan, T.S.; Tarafdar, M.; Ragu-Nathan, B.S.; Tu, Q. The consequences of technostress for end users in organizations: Conceptual development and empirical validation. Inf. Syst. Res. 2008, 19, 417–433. [Google Scholar] [CrossRef] [Green Version]
- Huang, Y.-H.; Sung, C.-Y.; Chen, W.; Liu, S.-S. Relationships between social support, social status perception, social identity, work stress, and safety behavior of construction site management personnel. Sustainability 2021, 13, 3184. [Google Scholar] [CrossRef]
- Tarafdar, M.; Bolman Pullins, E.; Ragu-Nathan, T.S. Examining impacts of technostress on the professional salesperson’s behavioural performance. Leadersh. Organ. Dev. J. 2014, 34, 51–69. [Google Scholar] [CrossRef]
- D’Arcy, J.; Teh, P.L. Predicting employee information security policy compliance on a daily basis: The interplay of security-related stress, emotions, and neutralization. Inf. Manag. 2019, 56, 103151. [Google Scholar] [CrossRef]
- Hwang, I.; Cha, O. Examining technostress creators and role stress as potential threats to employees’ information security compliance. Comput. Hum. Behav. 2018, 81, 282–293. [Google Scholar] [CrossRef]
- Graham, K.A.; Resick, C.J.; Margolis, J.A.; Shao, P.; Hargis, M.B.; Kiker, J.D. Egoistic norms, organizational identification, and the perceived ethicality of unethical pro-organizational behavior: A moral maturation perspective. Hum. Relat. 2020, 73, 1249–1277. [Google Scholar] [CrossRef]
- Li, H.; Zhang, J.; Sarathy, R. Understanding compliance with internet use policy from the perspective of rational choice theory. Decis. Support. Syst. 2010, 48, 635–645. [Google Scholar] [CrossRef]
- Zhao, H.; Peng, Z.; Chen, H.K. Compulsory citizenship behavior and organizational citizenship behavior: The role of organizational identification and perceived interactional justice. J. Psychol. 2014, 148, 177–196. [Google Scholar] [CrossRef]
- Smidts, A.; Pruyn, A.; van Riel, C. The impact of employee communication and perceived external prestige on organization identification. Acad. Manag. J. 2001, 44, 1051–1062. [Google Scholar]
- Liu, Y.; Berry, C.M. Identity, moral, and equity perspectives on the relationship between experienced injustice and time theft. J. Bus. Ethic. 2013, 118, 73–83. [Google Scholar] [CrossRef]
- Greenberg, J. Organizational justice: Yesterday, today, and tomorrow. J. Manag. 1990, 16, 399–432. [Google Scholar] [CrossRef]
- Ceylan, A.; Sulu, S. Work alienation as a mediator of the relationship of procedural injustice to job stress. South. East. Eur. J. Econ. Bus. 2010, 5, 65–74. [Google Scholar] [CrossRef] [Green Version]
- Chou, T.-Y.; Chou, S.-C.T.; Jiang, J.J.; Klein, G. The organizational citizenship behavior of IS personnel: Does organizational justice matter? Inf. Manag. 2013, 50, 105–111. [Google Scholar] [CrossRef]
- Muchinsky, P.M. Psychology Applied to Work: An Introduction to Industrial and Organizational Osychology; Wadsworth/Thomson Learning: Belmont, CA, USA, 2012. [Google Scholar]
- Kim, M.; Beehr, T.A. Making the case for procedural justice: Employees thrive and work hard. J. Manag. Psychol. 2020, 35, 100–114. [Google Scholar] [CrossRef] [Green Version]
- Zhang, H.; Agarwal, N.C. The mediating roles of organizational justice on the relationships between HR practices and workplace outcomes: An investigation in China. Int. J. Hum. Resour. Manag. 2009, 20, 676–693. [Google Scholar] [CrossRef]
- Lee, C.; Ha, B.C. Interactional justice, informational quality, and sustainable supply chain management: A comparison of domestic and multinational pharmaceutical companies. Sustainability 2021, 13, 998. [Google Scholar] [CrossRef]
- Greenberg, J. Using socially fair treatment to promote acceptance of a worksite smoking ban. J. Appl. Psychol. 1994, 79, 288–297. [Google Scholar] [CrossRef] [PubMed]
- Cropanzano, R.; Paddock, E.L.; Rupp, D.E.; Bagger, J.; Baldwin, A. How regulatory focus impacts the process-by-outcome interaction for perceived fairness and emotions. Organ. Behav. Hum. Decis. Process. 2008, 105, 36–51. [Google Scholar] [CrossRef]
- Van Lange, P.A. The Pursuit of joint outcomes and equality in outcomes: An integrative model of social value orientation. J. Pers. Soc. Psychol. 1999, 77, 337–349. [Google Scholar] [CrossRef]
- Gollwitzer, M.; Rothmund, T.; Pfeiffer, A.; Ensenbach, C. Why and when justice sensitivity leads to pro-and antisocial behavior. J. Res. Pers. 2009, 43, 999–1005. [Google Scholar] [CrossRef]
- Schmitt, M.; Dörfel, M. Procedural injustice at work, justice sensitivity, job satisfaction and psychosomatic well-being. Eur. J. Soc. Psychol. 1999, 29, 443–453. [Google Scholar] [CrossRef]
- Tziner, A.; Sharoni, G. Organizational citizenship behavior, organizational justice, job stress, and work-family conflict: Examination of their interrelationships with respondents from a non-western culture. J. Work. Organ. Psychol. 2014, 30, 35–42. [Google Scholar]
- Wood, S.; Braeken, J.; Niven, K. Discrimination and well-being in organizations: Testing the differential power and organizational justice theories of workplace aggression. J. Bus. Ethics. 2013, 115, 617–634. [Google Scholar] [CrossRef]
- Hwang, I.; Ahn, S. The Effect of organizational justice on information security-related role stress and negative behaviors. J. Kor. Soc. Comp. Inf. 2019, 24, 87–98. [Google Scholar]
- Fallatah, F.; Laschinger, H.K.; Read, E.A. The effects of authentic leadership, organizational identification, and occupational coping self-efficacy on new graduate nurses’ job turnover intentions in Canada. Nurs. Outlook 2017, 65, 172–183. [Google Scholar] [CrossRef]
- Nunnally, J.C. Psychometric theory, 2nd ed.; McGraw-Hill: New York, NY, USA, 1994; ISBN 007047849X. [Google Scholar]
- Bentler, P.M. Comparative fit indexes in structural models. Psychol. Bull. 1990, 107, 238–246. [Google Scholar] [CrossRef] [PubMed]
- Wixom, B.H.; Watson, H.J. An empirical investigation of the factors affecting data warehousing success. MIS Q. 2001, 25, 17. [Google Scholar] [CrossRef]
- Fornell, C.; Larcker, D.F. Evaluating structural equation models with unobservable variables and measurement Error. J. Mark. Res. 1981, 18, 39–50. [Google Scholar] [CrossRef]
- Podsakoff, P.M.; MacKenzie, S.B.; Lee, J.Y.; Podsakoff, N.P. Common method biases in behavioral research: A critical review of the literature and recommended remedies. J. Appl. Psychol. 2003, 88, 879–903. [Google Scholar] [CrossRef] [PubMed]
- Lin, G.C.; Wen, Z.; Marsh, H.W.; Lin, H.S. Structural equation models of latent interactions: Clarification of orthogonalizing and double-mean-centering strategies. Struct. Equ. Model. A Multidiscip. J. 2010, 17, 374–391. [Google Scholar] [CrossRef]
- Dawson, J.F. Moderation in management research: What, why, when, and how. J. Bus. Psychol. 2014, 29, 1–19. [Google Scholar] [CrossRef]
- Taghva, M. The effect of security awareness on compliance with security regulations by teleworkers in the period of COVID-19 epidemic. Manag. Res. 2021, 13, 179–204. [Google Scholar]
- Tang, Z.; Miller, A.S.; Zhou, Z.; Warkentin, M. Does government social media promote users’ information security behavior towards COVID-19 scams? Cultivation effects and protective motivations. Gov. Inf. Q. 2021, 38, 101572. [Google Scholar] [CrossRef]
- Prasetyo, Y.T.; Castillo, A.M.; Salonga, L.J.; Sia, J.A.; Seneta, J.A. Factors affecting perceived effectiveness of COVID-19 prevention measures among Filipinos during enhanced community quarantine in Luzon, Philippines: Integrating protection motivation theory and extended theory of planned behavior. Int. J. Infect. Dis. 2020, 99, 312–323. [Google Scholar] [CrossRef]
- Ali, R.; Dominic, P.; Ali, S.; Rehman, M.; Sohail, A. Information security behavior and information security policy compliance: A systematic literature review for identifying the transformation process from noncompliance to compliance. Appl. Sci. 2021, 11, 3383. [Google Scholar] [CrossRef]
- Merchan-Lima, J.; Astudillo-Salinas, F.; Tello-Oquendo, L.; Sanchez, F.; Lopez-Fonseca, G.; Quiroz, D. Information security management frameworks and strategies in higher education institutions: A systematic review. Ann. Telecommun. 2021, 76, 255–270. [Google Scholar] [CrossRef]
- Huseman, C.R.; Hatfield, D.J.; Miles, E.W. A new perspective on equity theory: The equity sensitivity construct. Acad. Manag. Rev. 1987, 12, 222–234. [Google Scholar] [CrossRef] [Green Version]
- Vance, A.; Siponen, M.T.; Straub, D.W. Effects of sanctions, moral beliefs, and neutralization on information security policy violations across cultures. Inf. Manag. 2020, 57, 103212. [Google Scholar] [CrossRef]


| Demographic Categories | Frequency | Percentage (%) | |
|---|---|---|---|
| Type | Manufacturer | 57 | 17.5 |
| Service | 268 | 82.5 | |
| Gender | Male | 205 | 63.1 |
| Female | 120 | 36.9 | |
| Job Position | Staff | 105 | 32.3 |
| Assistant Manager | 92 | 28.3 | |
| Manager | 95 | 29.2 | |
| General Manager | 33 | 10.2 | |
| Department | Management Support | 66 | 20.3 |
| Marketing and Sales | 187 | 57.5 | |
| Research and Development | 13 | 4.0 | |
| Production | 16 | 4.9 | |
| Technical Support | 14 | 4.3 | |
| Other | 29 | 8.9 | |
| Total | 325 | 100.0 | |
| Constructs | Items # | Items | References |
|---|---|---|---|
| IS-related procedural justice | PJ1 PJ2 PJ3 | Organization’s IS process influences the result of my IS behavior. Organization’s IS process is applied consistently. Organization’s IS process is applied without prejudice. | [13] |
| IS-related information justice | IJ1 IJ2 IJ3 | Organization communicates about IS. Organization clearly explains the IS process. Organization provides details about IS compliance. | [13] |
| IS-related work impediment | WI1 WI2 WI3 | Complying with the requirements of the security policy slows down my response time to my peers, customers, managers, etc. Complying with the requirements of the security policy hinders my productivity at work. Complying with the requirements of the security policy impedes my efficiency at work. | [4] |
| Organization identification | OI1 OI2 OI3 | I am proud to be an employee of my organization. I am glad I chose to work for my organization rather than another company. I am willing to put in a great deal of effort beyond that normally expected to help my organization be successful. | [36] |
| IS-related voice behavior | VB1 VB2 VB3 | I provide and recommend opinions for our organization’s IS. I encourage my colleagues to participate in issues affecting our organization’s IS. I give an idea of a change to our organization’s IS policy. | [28] |
| Justice sensitivity | JS1 JS2 JS3 JS4 JS5 | I cannot stand it for long when I have to fix the consequences of others’ carelessness. I feel disappointed when I have fewer opportunities to develop my skills than others. It pisses me off when others get better than me. I rebel for a long time when others are being treated better than me (dropped). | [19] |
| Construct | Item | Mean | Std. Dev. | Factor Loading | Cronbach’s Alpha | CR | AVE |
|---|---|---|---|---|---|---|---|
| IS-related procedural justice | PJ1 PJ2 PJ3 | 5.357 5.277 5.477 | 1.260 1.231 1.190 | 0.802 0.781 0.820 | 0.861 | 0.973 | 0.924 |
| IS-related information justice | IJ1 IJ2 IJ3 | 5.326 5.246 5.335 | 1.273 1.296 1.277 | 0.844 0.803 0.823 | 0.889 | 0.977 | 0.934 |
| IS-related work impediment | WI1 WI2 WI3 | 2.748 2.791 2.818 | 1.138 1.227 1.083 | 0.801 0.819 0.805 | 0.889 | 0.980 | 0.943 |
| Organization identification | OI1 OI2 OI3 | 5.111 5.108 5.166 | 1.165 1.138 1.126 | 0.841 0.881 0.865 | 0.915 | 0.986 | 0.958 |
| IS-related voice behavior | VB1 VB2 VB3 | 4.905 4.954 4.908 | 1.165 1.109 1.154 | 0.856 0.851 0.878 | 0.922 | 0.987 | 0.962 |
| Justice sensitivity | JS1 JS2 JS3 | 5.206 4.858 5.138 | 1.246 1.295 1.330 | 0.779 0.795 0.811 | 0.839 | 0.975 | 0.906 |
| Construct | 1 | 2 | 3 | 4 | 5 | 6 |
|---|---|---|---|---|---|---|
| IS-related procedural justice | 0.961 | |||||
| IS-related information justice | 0.518 ** | 0.966 | ||||
| IS-related work impediment | −0.521 ** | −0.487 ** | 0.971 | |||
| Organization identification | 0.532 ** | 0.461 ** | −0.397 ** | 0.979 | ||
| IS-related voice behavior | 0.412 ** | 0.461 ** | −0.460 ** | 0.349 ** | 0.981 | |
| Justice sensitivity | 0.467 ** | 0.489 ** | −0.517 ** | 0.425 ** | 0.503 ** | 0.952 |
| Hypothesis | Path | Path Coefficient | t-Value | Result |
|---|---|---|---|---|
| H1 | Procedural Justice → Work Impediment | −0.391 | −5.542 ** | Supported |
| H2 | Information Justice → Work Impediment | −0.317 | −4.661 ** | Supported |
| H3 | Procedural Justice → Organizational Identification | 0.417 | 6.041 ** | Supported |
| H4 | Information Justice → Organizational Identification | 0.257 | 3.882 ** | Supported |
| H5 | Work Impediment → Voice Behavior | −0.431 | −7.102 ** | Supported |
| H6 | Organizational Identification → Voice Behavior | 0.235 | 4.149 ** | Supported |
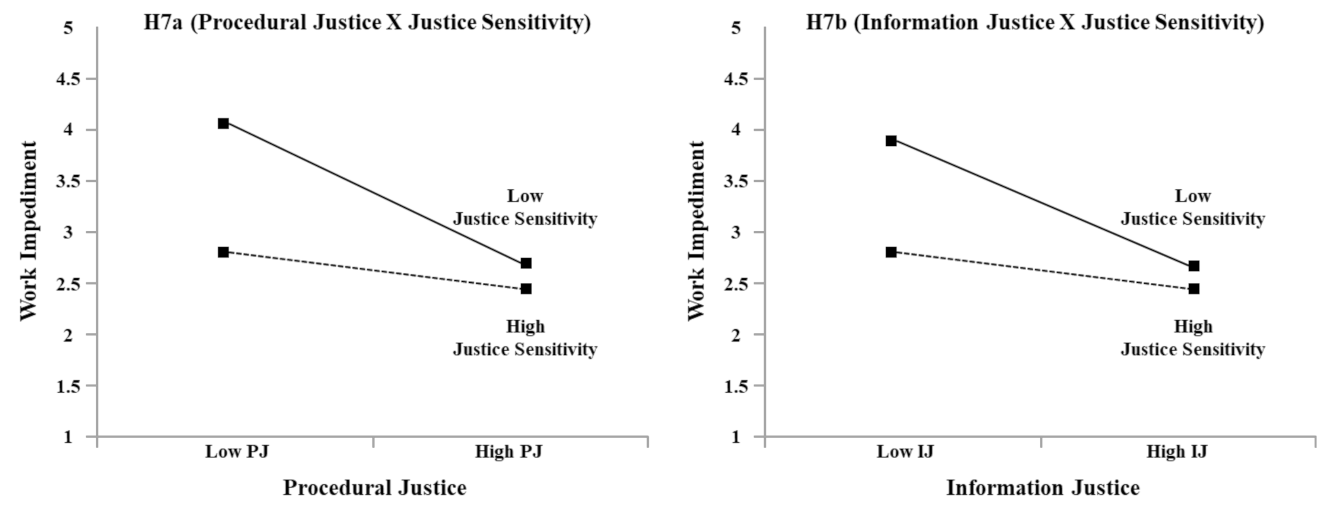
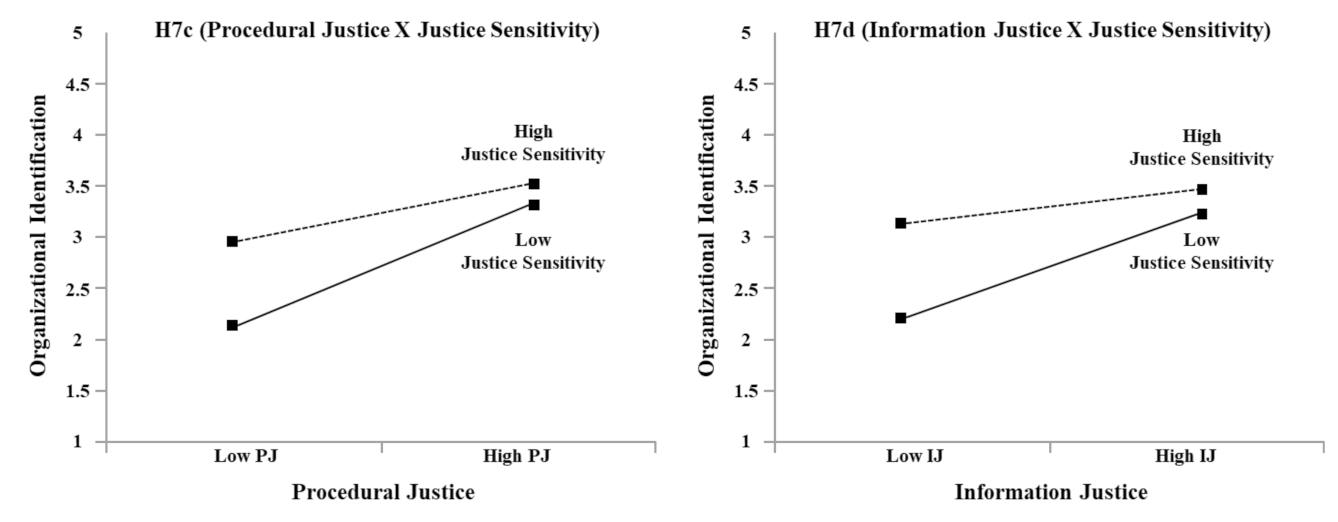
| Hypothesis | Path | Path Coefficient | t-Value | Result |
|---|---|---|---|---|
| H7a | Procedural Justice → Work Impediment | −0.383 | −5.830 ** | Supported |
| Justice Sensitivity → Work Impediment | −0.341 | −5.116 ** | ||
| Procedural Justice X Justice Sensitivity → Work Impediment | 0.263 | 4.791 ** | ||
| H7b | Information Justice → Work Impediment | −0.33 | −5.035 ** | Supported |
| Justice Sensitivity → Work Impediment | −0.361 | −5.196 ** | ||
| Information Justice X Justice Sensitivity → Work Impediment | 0.204 | 3.908 ** | ||
| H7c | Procedural Justice → Organizational Identification | 0.431 | 6.420 ** | Supported |
| Justice Sensitivity → Organizational Identification | 0.246 | 3.745 ** | ||
| Procedural Justice X Justice Sensitivity → Organizational Identification | −0.165 | −3.089 ** | ||
| H7d | Information Justice → Organizational Identification | 0.331 | 4.968 ** | Supported |
| Justice Sensitivity → Organizational Identification | 0.293 | 4.240 ** | ||
| Information Justice X Justice Sensitivity → Organizational Identification | −0.163 | −3.091 ** |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, W.J.; Hwang, I. Sustainable Information Security Behavior Management: An Empirical Approach for the Causes of Employees’ Voice Behavior. Sustainability 2021, 13, 6077. https://doi.org/10.3390/su13116077
Lee WJ, Hwang I. Sustainable Information Security Behavior Management: An Empirical Approach for the Causes of Employees’ Voice Behavior. Sustainability. 2021; 13(11):6077. https://doi.org/10.3390/su13116077
Chicago/Turabian StyleLee, Woo Jin, and Inho Hwang. 2021. "Sustainable Information Security Behavior Management: An Empirical Approach for the Causes of Employees’ Voice Behavior" Sustainability 13, no. 11: 6077. https://doi.org/10.3390/su13116077






