Critical Infrastructures Overview: Past, Present and Future
Abstract
:1. Introduction
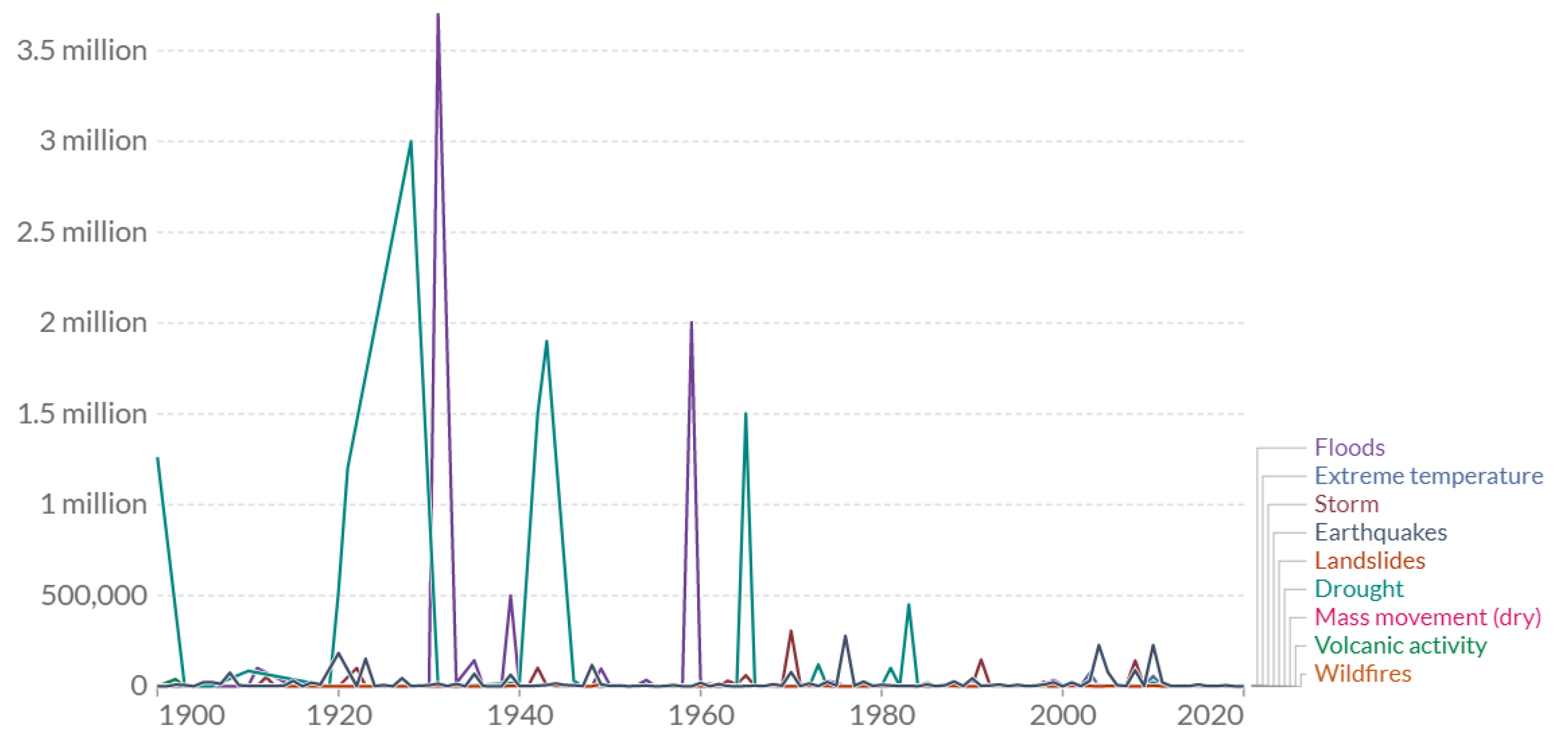
1.1. Critical Infrastructures, Definitions and Terms
1.2. Motivation of the Research
1.3. Structure of the Research
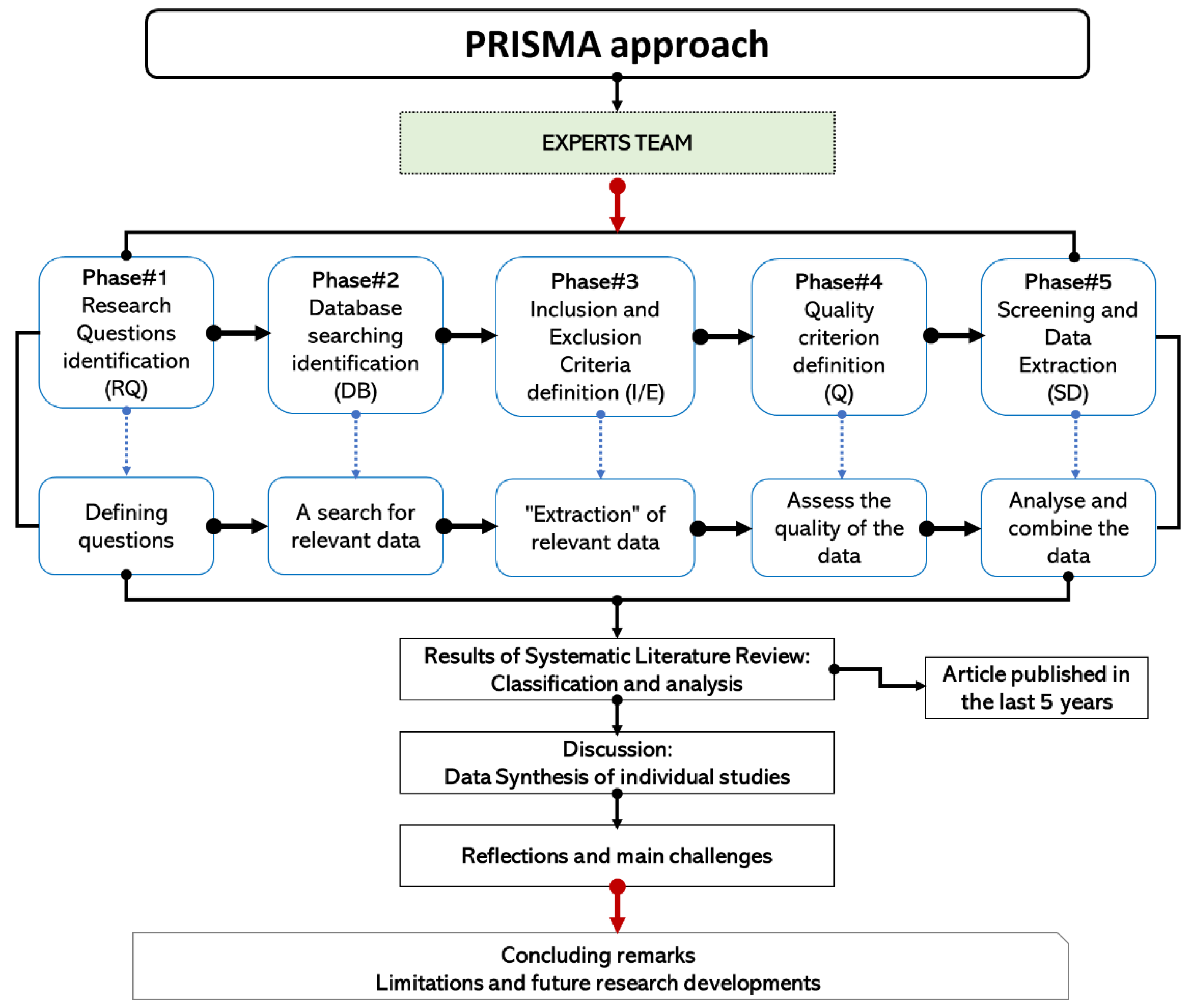
2. Materials and Methods
2.1. Search Strategy
- RQ1. What types of risk assessment method are used to manage CIs?
- RQ2. What are the environmental risk mitigation strategies for CIs?
- RQ3. What is the role of the human factor in the prevention of risks for CIs?
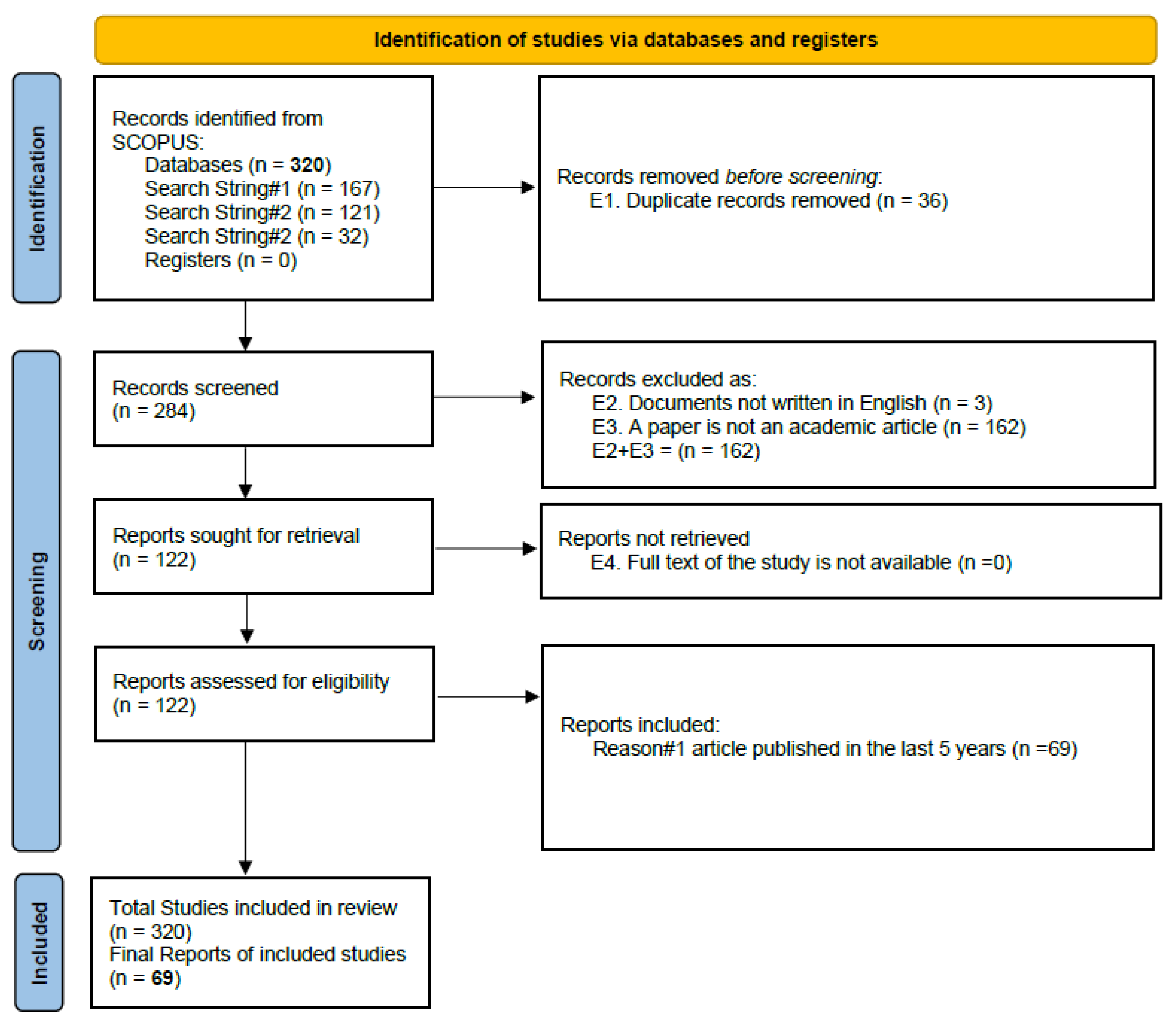
2.2. Database Searching Identification
2.3. Inclusion and Exclusion Criteria
2.4. Quality Criteria
- Q1: Documents in the context of CIs using different methodologies and approaches.
- Q2: Documents with impact factor, SJR or CiteScore.
2.5. Screening and Data Extraction
- 1st investigation: critical infrastructures AND risk assessment (name CLUSTER#1);
- 2nd investigation: critical infrastructures AND risk environment (name CLUSTER#2);
- 3rd investigation: critical infrastructures AND human factors (name CLUSTER#3).
3. Results
- Publication by years.
- Documents by type.
- Country analysis.
- Subject area.
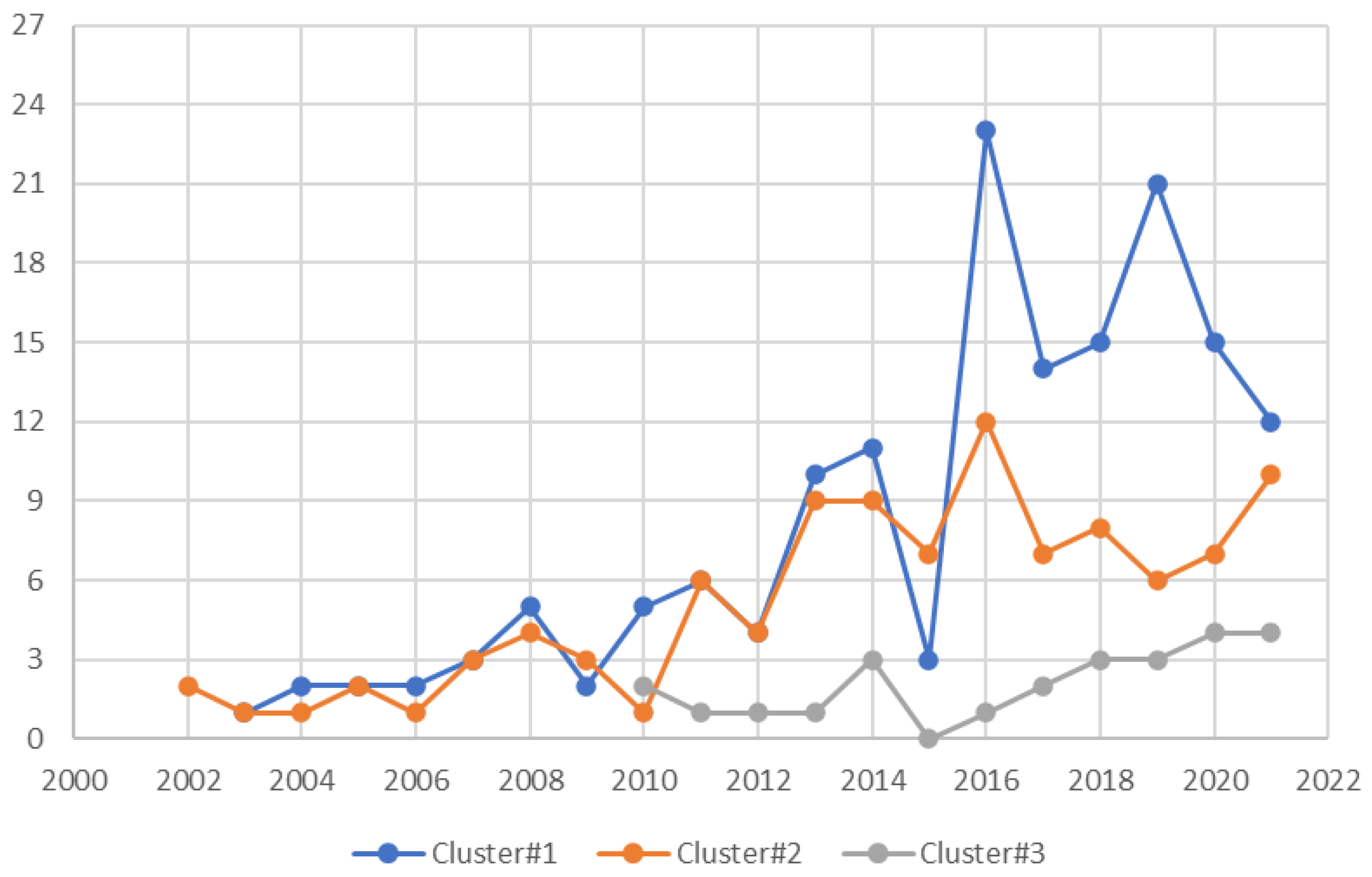
3.1. Publication by Years
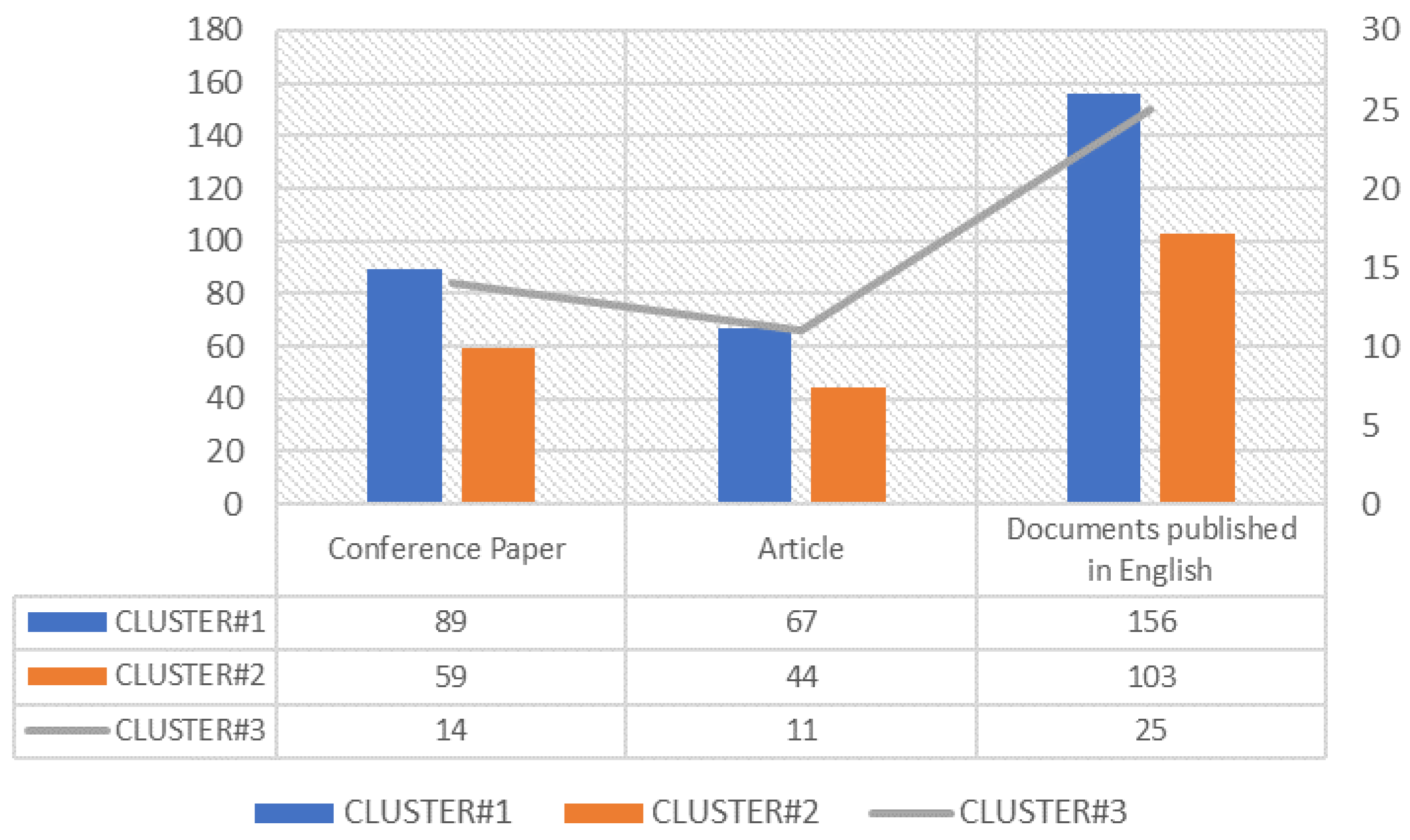
3.2. Documents by Types
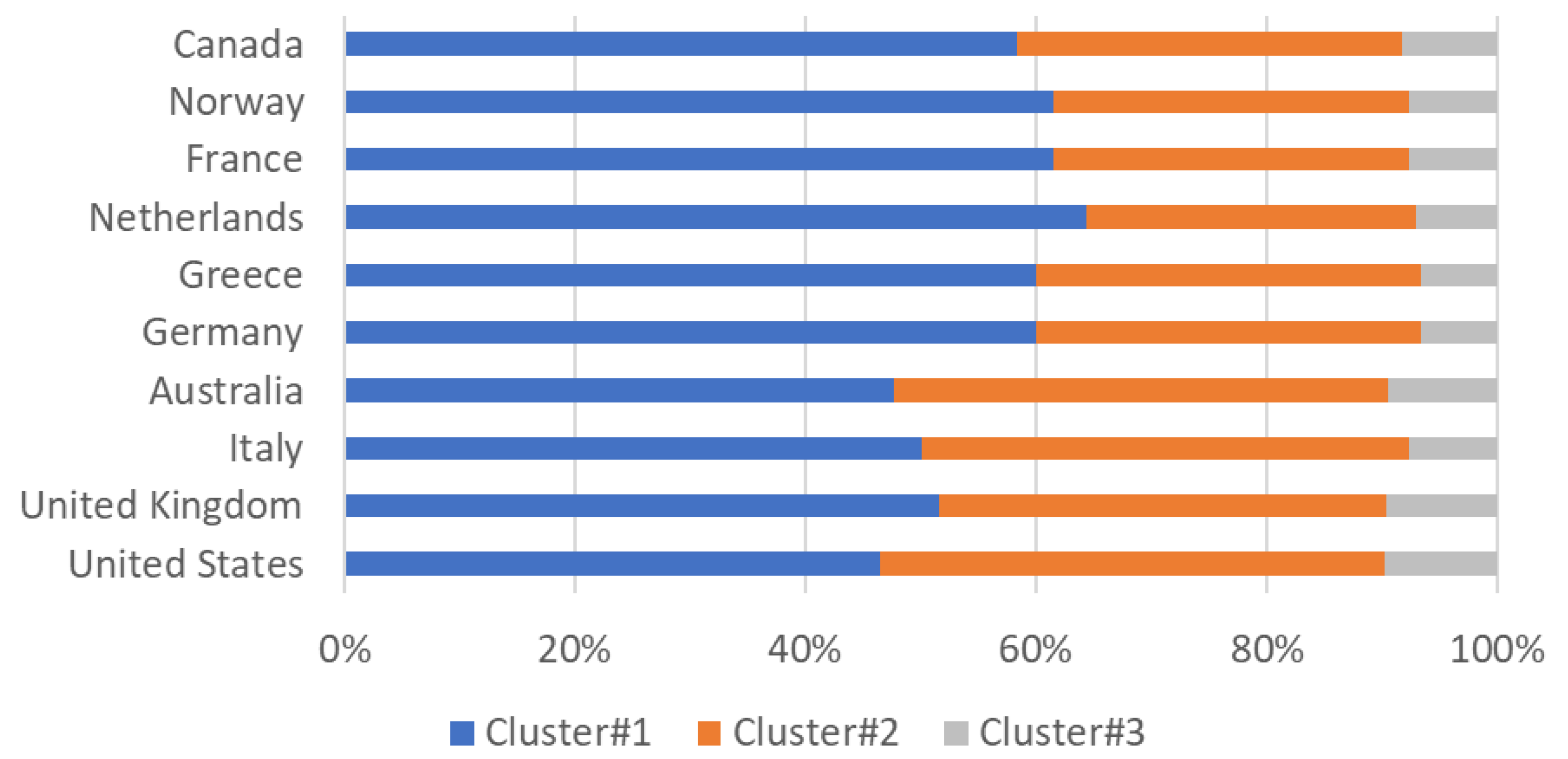
3.3. Country Analysis
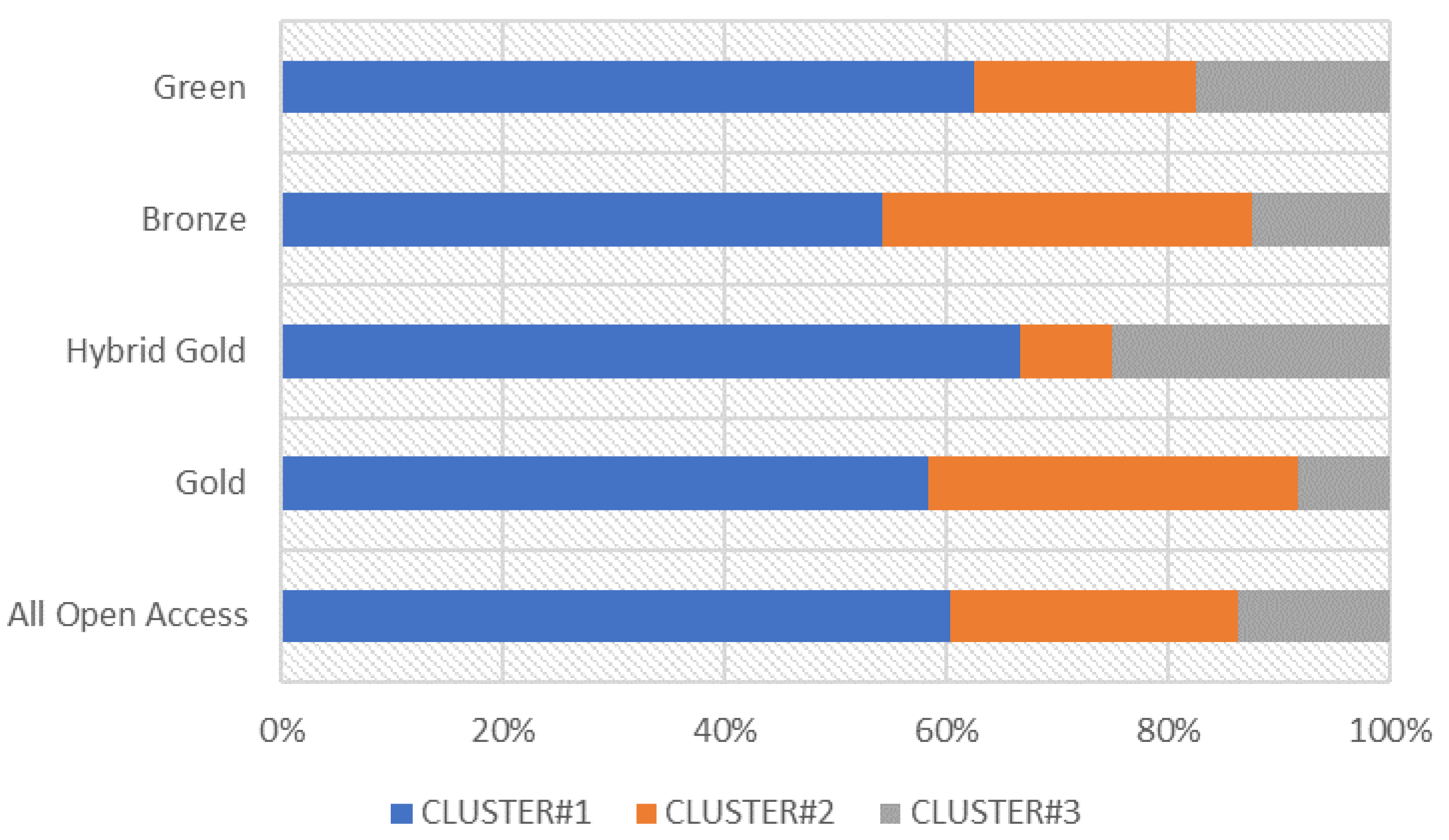
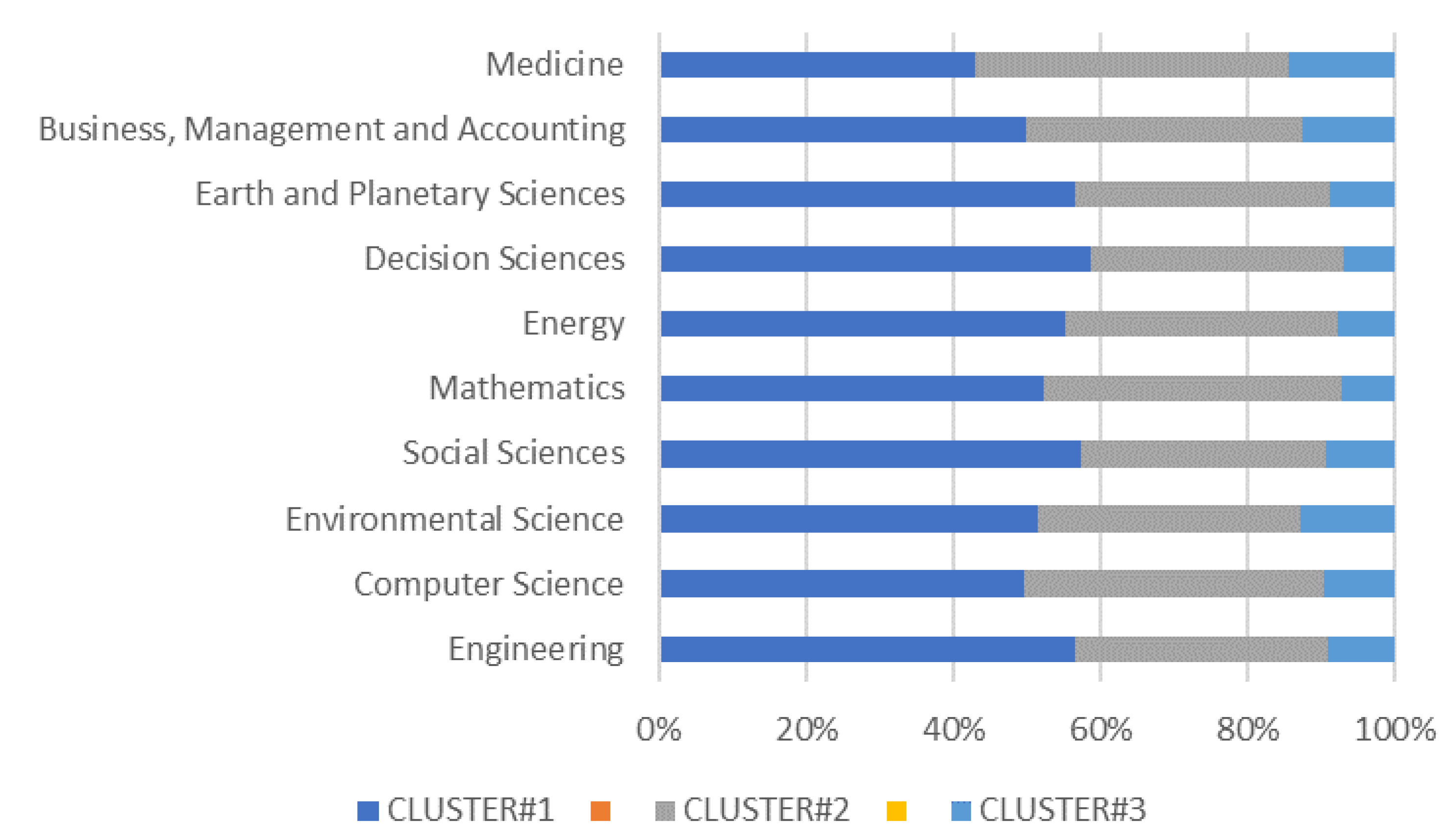
3.4. Subject Area
4. Discussion
4.1. Data Synthesis of Individual Studies
4.2. CLUSTER#1 “Risk Assessment” (39 Documents)
4.3. CLUSTER#2 “Risk Environment” (21 Documents)
4.4. CLUSTER#3 “Human Factors” (9 Documents)
5. Reflections and Main Challenges
6. Conclusions
6.1. Concluding Remarks
6.2. Limitations and Future Research Developments
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Berger, C.; Eichhammer, P.; Reiser, H.P.; Domaschka, J.; Hauck, F.J.; Habiger, G. A Survey on Resilience in the IoT: Taxonomy, Classification, and Discussion of Resilience Mechanisms. ACM Comput. Surv. 2022, 54, 147. [Google Scholar] [CrossRef]
- Balani, H. Assessing the introduction of anti-money laundering regulations on bank stock valuation: An empirical analysis. J. Money Laund. Control. 2019, 22, 76–88. [Google Scholar] [CrossRef]
- The Council of the European Union. COUNCIL DIRECTIVE 2008/114/EC of 8 December 2008 on the Identification and Designation of European Critical Infrastructures and the Assessment of the Need to Improve Their Protection; The Council of the European Union: Brussels, Belgium, 2008. [Google Scholar]
- Coppolino, L.; D’Antonio, S.; Giuliano, V.; Mazzeo, G.; Romano, L. A framework for Seveso-compliant cyber-physical security testing in sensitive industrial plants. Comput. Ind. 2022, 136, 103589. [Google Scholar] [CrossRef]
- Di Pasquale, V.; Miranda, S.; Neumann, W.P. Ageing and human-system errors in manufacturing: A scoping review. Int. J. Prod. Res. 2020, 58, 4716–4740. [Google Scholar] [CrossRef]
- Zhang, N.; Alipour, A. Flood risk assessment and application of risk curves for design of mitigation strategies. Int. J. Crit. Infrastruct. Prot. 2022, 36, 100490. [Google Scholar] [CrossRef]
- Yu, Y.-C.; Gardoni, P. Predicting road blockage due to building damage following earthquakes. Reliab. Eng. Syst. Saf. 2022, 219, 108220. [Google Scholar] [CrossRef]
- Bona, G.D.; Falcone, D.; Forcina, A.; Silvestri, L. Systematic Human Reliability Analysis (SHRA): A New Approach to Evaluate Human Error Probability (HEP) in a Nuclear Plant. Int. J. Math. Eng. Manag. Sci. 2021, 6, 345–362. [Google Scholar]
- Babar, A.H.K.; Ali, Y. Framework construction for augmentation of resilience in critical infrastructure: Developing countries a case in point. Technol. Soc. 2022, 68, 101809. [Google Scholar] [CrossRef]
- Petrillo, A.; de Felice, F.; Longo, F.; Bruzzone, A. Factors affecting the human error: Representations of mental models for emergency management. Int. J. Simul. Process Model. 2017, 12287–12299. [Google Scholar] [CrossRef] [Green Version]
- Gurevitch, J.; Koricheva, J.; Nakagawa, S.; Stewart, G. Meta-analysis and the science of research synthesis. Nature 2018, 555, 175–182. [Google Scholar] [CrossRef]
- Sonesson, T.R.; Johansson, J.; Cedergren, A. Governance and interdependencies of critical infrastructures: Exploring mechanisms for cross-sector resilience. Saf. Sci. 2021, 142, 105383. [Google Scholar] [CrossRef]
- Michalis, P.; Sentenac, P. Subsurface condition assessment of critical dam infrastructure with non-invasive geophysical sensing. Environ. Earth Sci. 2021, 80, 556. [Google Scholar] [CrossRef]
- Johnson, C.A.; Flage, R.; Guikema, S.D. Feasibility study of PRA for critical infrastructure risk analysis. Reliab. Eng. Syst. Saf. 2021, 212, 107643. [Google Scholar] [CrossRef]
- Meslem, A.; Iversen, H.; Iranpour, K.; Lang, D. A computational platform to assess liquefaction-induced loss at critical infrastructures scale. Bull. Earthq. Eng. 2021, 19, 4083–4114. [Google Scholar] [CrossRef]
- Veeraraghavan, S.; Bolisetti, C.; Slaughter, A.; Coleman, J.; Dhulipala, S.; Hoffman, W.; Kim, K.; Kurt, E.; Spears, R.; Munday, L. MASTODON: An open-source software for seismic analysis and risk assessment of critical infrastructure. Nucl. Technol. 2021, 207, 1073–1095. [Google Scholar] [CrossRef]
- Donratanapat, N.; Samadi, S.; Vidal, J.M.; Tabas, S.S. A national scale big data analytics pipeline to assess the potential impacts of flooding on critical infrastructures and communities. Environ. Model. Softw. 2020, 133, 104828. [Google Scholar] [CrossRef]
- Chou, J.-S.; Ongkowijoyo, C.S. Hybrid decision-making method for assessing interdependency and priority of critical infrastructure. Int. J. Disaster Risk Reduct. 2019, 39, 101134. [Google Scholar] [CrossRef]
- Vamvakeridou-Lyroudia, L.S.; Chen, A.S.; Khoury, M.; Gibson, M.J.; Kostaridis, A.; Stewart, D.; Wood, M.; Djordjevic, S.; Savic, D.A. Assessing and visualising hazard impacts to enhance the resilience of critical infrastructures to urban flooding. Sci. Total Environ. 2020, 707, 136078. [Google Scholar] [CrossRef]
- Turskis, Z.; Goranin, N.; Nurusheva, A.; Boranbayev, S. Information security risk assessment in critical infrastructure: A hybrid MCDM approach. Informatica 2019, 30, 187–211. [Google Scholar] [CrossRef]
- Přibyl, P.; Přibyl, O.; Czech, J.M. Computer modelling of fire consequences on road critical infrastructure-tunnels. Struct. Monit. Maint. 2018, 5, 363–377. [Google Scholar]
- Greiving, S.; Fleischhauer, M.; León, C.D.; Schödl, L.; Miralles, I.K.Q.; Larraín, B.P. Participatory assessment of multi risks in urban regions—The case of critical infrastructures in metropolitan lima. Sustainability 2021, 13, 2813. [Google Scholar] [CrossRef]
- Kasmi, O.; Baina, A.; Bellafkih, M. Fuzzy logic based clustering algorithm for management in critical infrastructure. Clust. Comput. 2021, 4, 433–458. [Google Scholar] [CrossRef]
- Di Bona, G.; Forcina, A.; Falcone, D.; Silvestri, L. Critical risks method (CRM): A new safety allocation approach for a critical infrastructure. Sustainability 2020, 12, 4949. [Google Scholar] [CrossRef]
- Boothroyd, R.J.; Williams, R.D.; Hoey, T.B.; Tolentino, P.L.M.; Yang, X. National-scale assessment of decadal river migration at critical bridge infrastructure in the Philippines. Sci. Total Environ. 2021, 768, 144460. [Google Scholar] [CrossRef] [PubMed]
- Fekete, A. Critical infrastructure cascading effects. Disaster resilience assessment for floods affecting city of cologne and rhein-erft-kreis. J. Flood Risk Manag. 2020, 13, e312600. [Google Scholar] [CrossRef]
- Rehak, D.; Senovsky, P.; Hromada, M.; Lovecek, T.; Novotny, P. Cascading impact assessment in a critical infrastructure system. Int. J. Crit. Infrastruct. Prot. 2018, 22, 125–138. [Google Scholar] [CrossRef]
- Esposito, S.; Stojadinović, B.; Babič, A.; Dolšek, M.; Iqbal, S.; Selva, J.; Broccardo, M.; Mignan, A.; Giardini, D. Risk-based multilevel methodology to stress test critical infrastructure systems. J. Infrastruct. Syst. 2020, 26, 04019035. [Google Scholar] [CrossRef]
- Argyroudis, S.A.; Fotopoulou, S.; Karafagka, S.; Pitilakis, K.; Selva, J.; Salzano, E.; Basco, A.; Crowley, H.; Rodrigues, D.; Matos, J.P.; et al. A risk-based multi-level stress test methodology: Application to six critical non-nuclear infrastructures in Europe. Nat. Hazards 2020, 100, 595–633. [Google Scholar] [CrossRef]
- Huff, J.; Leonard, W.B.; Smith, B.K.; Griendling, K.; Medal, H. NATO human view executable architectures for critical infrastructure analysis. EMJ Eng. Manag. J. 2019, 31, 224–245. [Google Scholar] [CrossRef]
- Mokhor, V.; Gonchar, S.; Dybach, O. Methods for the total risk assessment of cybersecurity of critical infrastructure facilities. Nucl. Radiat. Saf. 2019, 2, 4–8. [Google Scholar] [CrossRef]
- De Bruijn, K.M.; Maran, C.; Zygnerski, M.; Jurado, J.; Burzel, A.; Jeuken, C.; Obeysekera, J. Flood resilience of critical infrastructure: Approach and method applied to Fort Lauderdale, Florida. Water 2019, 11, 517. [Google Scholar] [CrossRef] [Green Version]
- Karbowski, A.; Malinowski, K.; Szwaczyk, S.; Jaskóła, P. Critical infrastructure risk assessment using markov chain model. J. Telecommun. Inf. Technol. 2019, 2, 15–20. [Google Scholar] [CrossRef]
- Murdock, H.J.; de Bruijn, K.M.; Gersonius, B. Assessment of critical infrastructure resilience to flooding using a response curve approach. Sustainability 2018, 10, 3470. [Google Scholar] [CrossRef]
- Pearson, J.; Punzo, G.; Mayfield, M.; Brighty, G.; Parsons, A.; Collins, P.; Jeavons, S.; Tagg, A. Flood resilience: Consolidating knowledge between and within critical infrastructure sectors. Enviro. Sys. Decis. 2018, 38, 318–329. [Google Scholar] [CrossRef] [Green Version]
- Tweneboah-Koduah, S.; Buchanan, W.J. Security risk assessment of critical infrastructure systems: A comparative study. Comput. J. 2018, 61, 1389–1406. [Google Scholar] [CrossRef]
- Zimmermann, M.; Winker, M.; Schramm, E. Vulnerability analysis of critical infrastructures in the case of a semi-centralised water reuse system in Qingdao, China. Int. J. Crit. Infrastruct. Prot. 2018, 22, 4–15. [Google Scholar] [CrossRef]
- Wang, H.; Lau, N.; Gerdes, R.M. Examining cybersecurity of cyberphysical systems for critical infrastructures through work domain analysis. Hum. Factors 2018, 60, 699–718. [Google Scholar] [CrossRef]
- Mao, Q.; Li, N. Assessment of the impact of interdependencies on the resilience of networked critical infrastructure systems. Nat. Hazards 2018, 93, 315–337. [Google Scholar] [CrossRef]
- Klügel, J.-U.; Stäuble-Akcay, S. Towards damage-consistent performance-based design of critical infrastructures. Int. J. Comput. Methods Experiment. Meas. 2018, 6, 933–943. [Google Scholar] [CrossRef] [Green Version]
- Thacker, S.; Kelly, S.; Pant, R.; Hall, J.W. Evaluating the benefits of adaptation of critical infrastructures to hydrometeorological risks. Risk Anal. 2018, 38, 134–150. [Google Scholar] [CrossRef] [Green Version]
- Thacker, S.; Barr, S.; Pant, R.; Hall, J.W.; Alderson, D. Geographic hotspots of critical national infrastructure. Risk Anal. 2017, 37, 2490–2505. [Google Scholar] [CrossRef]
- Bloomfield, R.E.; Popov, P.; Salako, K.; Stankovic, V.; Wright, D. Preliminary interdependency analysis: An approach to support critical-infrastructure risk-assessment. Reliab. Eng. Syst. Saf. 2017, 167, 198–217. [Google Scholar] [CrossRef]
- Delvosalle, C.; Robert, B.; Nourry, J.; Yan, G.; Brohez, S.; Delcourt, J. Considering critical infrastructures in the land use planning policy around seveso plants. Saf. Sci. 2017, 97, 27–33. [Google Scholar] [CrossRef]
- Lam, J.S.L.; Liu, C.; Gou, X. Cyclone risk mapping for critical coastal infrastructure: Cases of East Asian seaports. Ocean Coast. Manag. 2017, 141, 43–54. [Google Scholar] [CrossRef]
- Gonzalez-Granadillo, G.; Garcia-Alfaro, J.; Debar, H. A polytope-based approach to measure the impact of events against critical infrastructures. J. Comput. Syst. Sci. 2017, 83, 3–21. [Google Scholar] [CrossRef] [Green Version]
- Espada, R.; Apan, A.; McDougall, K. Vulnerability assessment of urban community and critical infrastructures for integrated flood risk management and climate adaptation strategies. Int. J. Disaster Resil. Built Environ. 2017, 8, 375–411. [Google Scholar] [CrossRef]
- Ongkowijoyo, C.; Doloi, H. Determining critical infrastructure risks using social network analysis. Int. J. Disaster Resilience Built Environ. 2017, 8, 5–26. [Google Scholar] [CrossRef]
- Daniel, F.N.; Nicolae, B.-A. Identifying vulnerabilities/risk factors of the critical infrastructure in the power installations of Ultra high and high voltage from the national power system with international connections. Qual. Access Success 2017, 18, 103–108. [Google Scholar]
- van Staalduinen, M.A.; Khan, F.; Gadag, V.; Reniers, G. Functional quantitative security risk analysis (QSRA) to assist in protecting critical process infrastructure. Reliab. Eng. Syst. Saf. 2017, 157, 23–34. [Google Scholar] [CrossRef]
- Imteaj, A.; Khan, I.; Khazaei, J.; Amini, M.H. Fedresilience: A federated learning application to improve resilience of resource-constrained critical infrastructures. Electronics 2021, 10, 1917. [Google Scholar] [CrossRef]
- Depina, I.; Divić, V.; Munjiza, A.; Peroš, B. Perfomance-based wind engineering assessment of critical telecommunication infrastructure subjected to bora wind. Eng. Struct. 2021, 236, 112083. [Google Scholar] [CrossRef]
- Hendricks, M.D.; Van Zandt, S. Unequal protection revisited: Planning for environmental justice, hazard vulnerability, and critical infrastructure in communities of color. Environ. Justice 2021, 14, 87–97. [Google Scholar] [CrossRef]
- Yuan, F.; Liu, R.; Mao, L.; Li, M. Internet of people enabled framework for evaluating performance loss and resilience of urban critical infrastructures. Saf. Sci. 2021, 134, 105079. [Google Scholar] [CrossRef]
- Wahab, Y.; Hamid, Z.; Ahmad, F.; Jusoh, R.; Ghani, K.; Anuar, A.; Ramli, W. A new approach on landslide vulnerability assessment and landslide risk index for critical infrastructures in Malaysia. Malays. Constr. Res. J. 2021, 33, 23–45. [Google Scholar]
- Der Sarkissian, R.; Dabaj, A.; Diab, Y.; Vuillet, M. Evaluating the implementation of the “build-back-better” concept for critical infrastructure systems: Lessons from saint-martin’s island following hurricane irma, 2021. Sustainability 2021, 13, 3133. [Google Scholar] [CrossRef]
- Thompson, J.R.; Frezza, D.; Necioglu, B.; Cohen, M.L.; Hoffman, K.; Rosfjord, K. Interdependent Critical Infrastructure Model (ICIM): An agent-based model of power and water infrastructure. Int. J. Crit. Infrastruct. Prot. 2021, 24, 144–165. [Google Scholar] [CrossRef]
- Baggott, S.S.; Santos, J.R. A risk analysis framework for cyber security and critical infrastructure protection of the U.S. electric power grid. Risk Anal. 2020, 40, 1744–1761. [Google Scholar] [CrossRef]
- Rød, B.; Lange, D.; Theocharidou, M.; Pursiainen, C. From risk management to resilience management in critical infrastructure. J. Manag. Eng. 2020, 36, 04020039. [Google Scholar] [CrossRef]
- Lo, H.-W.; Liou, J.J.H.; Huang, C.; Chuang, Y.-C.; Tzeng, G.-H. A new soft computing approach for analyzing the influential relationships of critical infrastructures. Int. J. Crit. Infrastruct. Prot. 2020, 28, 100336. [Google Scholar] [CrossRef]
- Benmokhtar, A.; Benouar, D.; Rahmoune, A. Modeling the Propagation of the Effects of a Disturbance in a Critical Infrastructure System to Increase its Resilience. Urban. Archit. Constr. 2020, 11, 157–178. [Google Scholar]
- Hawchar, L.; Naughton, O.; Nolan, P.; Stewart, M.G.; Ryan, P.C. A GIS-based framework for high-level climate change risk assessment of critical infrastructure. Clim. Risk Manag. 2020, 29, 100235. [Google Scholar] [CrossRef]
- Gheorghe, A.V.; Georgescu, A.; Bucovețchi, O.; Lazăr, M.; Scarlat, C. New dimensions for a challenging security environment: Growing exposure to critical space infrastructure disruption risk. Int. J. Disaster Risk Sci. 2018, 9, 555–560. [Google Scholar] [CrossRef] [Green Version]
- Serre, D.; Heinzlef, C. Assessing and mapping urban resilience to floods with respect to cascading effects through critical infrastructure networks. Int. J. Disaster Risk Reduct. 2018, 30, 235–243. [Google Scholar] [CrossRef]
- Braun, A.; Stötzer, J.; Kubisch, S.; Keller, S. Critical infrastructure analysis (CRITIS) in developing regions—Designing an approach to analyse peripheral remoteness, risks of accessibility loss, and isolation due to road network insufficiencies in chile. GI_Forum 2018, 6, 302–321. [Google Scholar] [CrossRef]
- Jaïdi, F.; Ayachi, F.L.; Bouhoula, A. A methodology and toolkit for deploying reliable security policies in critical infrastructures. Secur. Commun. Netw. 2018, 2018, 7142170. [Google Scholar] [CrossRef] [Green Version]
- Krings, S. “Dear neighbours” a comparative exploration of approaches to managing risks related to hazardous incidents and critical infrastructure outages. Erdkunde 2018, 72, 103–123. [Google Scholar] [CrossRef] [Green Version]
- Häyhtiö, M.; Zaerens, K. A comprehensive assessment model for critical infrastructure protection. Manag. Prod. Eng. Rev. 2017, 8, 42–53. [Google Scholar] [CrossRef]
- Capano, D. Critical infrastructure cybersecurity—An overview. J. N. Engl. Water Environ. Assoc. 2017, 51, 52–60. [Google Scholar]
- Wilson, G.; Wilson, T.M.; Deligne, N.I.; Blake, D.M.; Cole, J.W. Framework for developing volcanic fragility and vulnerability functions for critical infrastructure. J. Appl. Volcanol. 2017, 6, 14. [Google Scholar] [CrossRef] [Green Version]
- Flatscher, M.; Neumayer, M.; Bretterklieber, T. Maintaining critical infrastructure under cold climate conditions: A versatile sensing and heating concept. Sens. Actuators A Phys. 2017, 267, 538–546. [Google Scholar] [CrossRef]
- Le Blanc, K. Human Factors Challenges in Developing Cyber-Informed Risk Assessment for Critical Infrastructure. Adv. Intell. Syst. Comput. 2021, 1213, 536–541. [Google Scholar]
- Khanam, M.; Sofia, G.; Koukoula, M.; Lazin, R.; Nikolopoulos, E.I.; Shen, X.; Anagnostou, E.N. Impact of compound flood event on coastal critical infrastructures considering current and future climate. Nat. Hazards Earth Syst. Sci. 2021, 21, 587–605. [Google Scholar] [CrossRef]
- Silver, S.R.; Li, J.; Boal, W.L.; Shockey, T.L.; Groenewold, M.R. Prevalence of underlying medical conditions among selected essential critical infrastructure workers—Behavioral risk factor surveillance system, 31 states, 2017–2018. Morb. Mortal. Wkly. Rep. 2020, 69, 1244. [Google Scholar] [CrossRef] [PubMed]
- Splichalova, A.; Patrman, D.; Kotalova, N.; Hromada, M. Managerial decision making in indicating a disruption of critical infrastructure element resilience. Adm. Sci. 2020, 10, 75. [Google Scholar] [CrossRef]
- Rehak, D. Assessing and strengthening organisational resilience in a critical infrastructure system: Case study of the Slovak republic. Saf. Sci. 2020, 123, 104573. [Google Scholar] [CrossRef]
- Ghafir, I.; Saleem, J.; Hammoudeh, M.; Faour, H.; Prenosil, V.; Jaf, S.; Jabbar, S.; Baker, T. Security threats to critical infrastructure: The human factor. J. Supercomput. 2018, 74, 4986–5002. [Google Scholar] [CrossRef] [Green Version]
- Panda, R.K.; Raut, D.K.; Biswal, P. Inclusive training using technology at workplace: A critical review for an infrastructure company. Int. J. Civ. Eng. Technol. 2018, 9, 602–607. [Google Scholar]
- Petrillo, A.; Falcone, D.; de Felice, F.; Zomparelli, F. Development of a risk analysis model to evaluate human error in industrial plants and in critical infrastructures. Int. J. Disaster Risk Reduct. 2017, 23, 15–24. [Google Scholar] [CrossRef]
- Panteli, M.; Mancarella, P. Modeling and evaluating the resilience of critical electrical power infrastructure to extreme weather events. IEEE Syst. J. 2017, 11, 1733–1742. [Google Scholar] [CrossRef]



| I/E Criteria | |
|---|---|
| Exclusion | E1. Duplicate records E2. Documents not written in English E3. A paper is not an academic article (i.e., editorial materials, conference reviews, contents, or forewords) E4. Full text of the study is not available |
| Inclusion | I1. Documents published only English I2. Documents in final publication stage I3. Journal articles I4. Article in an international journal published in the last 5 years (2017–2021) |
| Bibliometric Search CRITERIA | Search String | Number of Items without Exclusions |
|---|---|---|
| Cluster#1 Risk Assessment | (TITLE (critical AND infrastructures) AND TITLE-ABS-KEY (risk AND assessment) AND TITLE-ABS-KEY (method)) | 167 |
| Cluster#2 Risk Environment | (TITLE (critical AND infrastructures) AND TITLE-ABS-KEY (risk) AND TITLE-ABS-KEY (environment)) | 121 |
| Cluster#3 Human Factors | (TITLE (critical AND infrastructures) AND TITLE-ABS-KEY (risk) AND TITLE-ABS-KEY (human AND factor)) | 32 |
| Journal | Publisher | Cite Score 2020 | SJR 2020 | Impact Factor 2020 |
|---|---|---|---|---|
| Safety Science | Elsevier | 7.8 | 1.178 | 4.877 |
| Reliability Engineering and System Safety | Elsevier | 9.3 | 1.761 | 6.188 |
| Sustainability Switzerland | MDPI | 3.9 | 0.612 | 3.251 |
| International Journal of Critical Infrastructure Protection | Elsevier | 6.0 | 0.650 | 2.865 |
| International Journal of Disaster Resilience in The Built Environment | Emerald | 1.4 | 0.252 | 0.91 |
| Risk Analysis | Wiley-Blackwell | 6.0 | 0.972 | 4.0 |
| Science of the Total Environment | Elsevier | 10.5 | 1.795 | 7.963 |
| Natural Hazards | Springer Nature | 4.9 | 0.760 | 3.102 |
| Authors | Ref. | Year | Type of Publication | Main Focus |
|---|---|---|---|---|
| Rydén Sonesson et al. | [12] | 2021 | Theoretical | Risks cross-sector analysis |
| Michalis and Sentenac | [13] | 2021 | Theoretical/Application | Dam monitoring |
| Johnson et al. | [14] | 2021 | Theoretical | Probabilistic Risk Analysis |
| Meslem et al. | [15] | 2021 | Software/Application | Liquefaction hazard |
| Veeraraghavan et al. | [16] | 2021 | Software/Application | Seismic analysis |
| Donratanapat et al. | [17] | 2020 | Software/Application | Flood emergences/ Hurricanes |
| Chou and Ongkowijoyo | [18] | 2019 | Theoretical | Decision Making & Risk Management |
| Vamvakeridou et al. | [19] | 2020 | Case Study | Flood emergences |
| Turskis et al. | [20] | 2019 | Theoretical | Decision Making & Risk Management |
| Přibyl et al. | [21] | 2018 | Theoretical/Application | Road tunnel |
| Greiving et al. | [22] | 2021 | Case Study | Urban regions |
| Kasmi et al. | [23] | 2021 | Theoretical/Application | Risk priority analysis |
| Di Bona et al. | [24] | 2020 | Theoretical/Application | Nuclear power plants |
| Boothroyd et al. | [25] | 2021 | Theoretical/Application | River erosion |
| Fekete | [26] | 2020 | Case Study | Flood emergences/cascading effect |
| Rehak et al. | [27] | 2018 | Theoretical | Cascading effects |
| Esposito et al. | [28] | 2020 | Theoretical/Application | Non-nuclear infrastructures (Stress test) |
| Argyroudis et al. | [29] | 2020 | Case Study | Non-nuclear infrastructures (Stress test) |
| Huff et al. | [30] | 2019 | Theoretical | Decision Making & Risk Management |
| Mokhor et al. | [31] | 2019 | Review | Cybersecurity |
| de Bruijn et al. | [32] | 2019 | Review | Flood emergences |
| Karbowski et al. | [33] | 2019 | Theoretical/Application | Theoretical/Application |
| Murdock et al. | [34] | 2018 | Theoretical | Flood emergences |
| Pearson et al. | [35] | 2018 | Review | Flood emergences |
| Tweneboah-Koduah and Buchanan | [36] | 2018 | Theoretical | Cybersecurity |
| Zimmermann et al. | [37] | 2018 | Theoretical | Water infrastructure |
| Wang et al. | [38] | 2018 | Theoretical | SCADA systems |
| Mao and Li | [39] | 2018 | Theoretical | Interdependency analysis/Disturbance propagation |
| Klügel and Stäuble-Akcay | [40] | 2018 | Theoretical | Seismic analysis |
| Thacker et al. | [41] | 2018 | Theoretical/Application | Hydrometeorological risk |
| Thacker et al. | [42] | 2017 | Theoretical/Application | Interdependency analysis |
| Bloomfield et al. | [43] | 2017 | Theoretical/Application | Interdependency analysis |
| Delvosalle et al. | [44] | 2017 | Theoretical/Application | Interdependency analysis |
| Lam et al. | [45] | 2017 | Theoretical/Application | Coastal infrastructure/cyclone |
| Gonzalez-Granadillo et al. | [46] | 2017 | Case Study | SCADA systems |
| Espada et al. | [47] | 2017 | Theoretical/Application | Flood emergences |
| Ongkowijoyo and Doloi | [48] | 2017 | Theoretical/Application | Risk priority analysis |
| Daniel and Nicolae | [49] | 2017 | Theoretical | Power safety |
| van Staalduinen et al. | [50] | 2017 | Theoretical | Risk priority analysis |
| Authors | Ref. | Year | Type of Publication | Main Focus |
|---|---|---|---|---|
| Imteaj et al. | [51] | 2021 | Theoretical | Resource-limitations |
| Depina et al. | [52] | 2021 | Theoretical | Performance analysis |
| Hendricks et al. | [53] | 2021 | Theoretical | Vulnerability |
| Yuan et al. | [54] | 2021 | Case Study | Internet of People (IoP) |
| Wahab et al. | [55] | 2021 | Theoretical/Application | Vulnerability |
| Der Sarkissian et al. | [56] | 2021 | Case Study | Recovery |
| Thompson et al. | [57] | 2021 | Theoretical/Application | Long-term planning |
| Baggott et al. | [58] | 2020 | Theoretical/Application | Decision Making & Risk Management |
| Rød et al. | [59] | 2020 | Theoretical | ISO 31000 |
| Lo et al. | [60] | 2020 | Theoretical | Decision Making & Risk Management |
| Benmokhtar et al. | [61] | 2020 | Theoretical | Decision Making & Risk Management |
| Hawchar et al. | [62] | 2020 | Theoretical | Decision Making & Risk Management |
| Gheorghe et al. | [63] | 2018 | Theoretical | Interdependency analysis |
| Serre and Heinzlef | [64] | 2018 | Theoretical | Cascading effects |
| Braun et al. | [65] | 2018 | Case Study | Vulnerability |
| Jaïdi et al. | [66] | 2018 | Theoretical/Application | Decision Making & Risk Management |
| Krings et al. | [67] | 2018 | Theoretical/Application | Risk management |
| Häyhtiö and Zaerens | [68] | 2017 | Theoretical/Application | Risk management |
| Capano | [69] | 2017 | Review | Risk management |
| Wilson et al. | [70] | 2017 | Theoretical/Application | Vulnerability (volcanic) |
| Flatscher et al. | [71] | 2017 | Theoretical/Application | Risk management |
| Authors | Ref. | Year | Type of Publication | Main Focus |
|---|---|---|---|---|
| Le Blanc | [72] | 2021 | Theoretical/Application | Risk analysis |
| Khanam et al. | [73] | 2021 | Case Study | Vulnerability |
| Silver et al. | [74] | 2020 | Theoretical | Behavioral risk |
| Splichalova et al. | [75] | 2020 | Theoretical | Decision making |
| Rehak | [76] | 2020 | Theoretical | Decision making |
| Ghafir et al. | [77] | 2018 | Theoretical/Application | Behavioral risk |
| Panda et al. | [78] | 2018 | Theoretical/Application | Behavioral risk |
| Petrillo et al. | [79] | 2017 | Theoretical/Application | Human error probability |
| Panteli and Mancarella | [80] | 2017 | Theoretical/Application | Behavioral risk |
| Cluster | RQ Investigated | Documents Analyzed | Literature Gap | Main Challenges |
|---|---|---|---|---|
| Cluster#1 “Risk Assessment” | RQ1 “What types of risk assessment method are used to manage CIs?” | From [12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50] | Lack of a recognized method for risk assessment | Method: risk management should be systematic process to deal comprehensively the risks. |
| Legislative measures: it would be necessary to develop an organic legislative system to monitor and protect the CI. It should concern aspects related to the evaluation of the risk, require identification of solutions that can organically cope with the multiple needs and technological problems, environmental, social, etc. | ||||
| Cluster#2 “Risk Environment” | RQ2 “What are the environmental risk mitigation strategies for CIs?” | From [51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71] | Lack of knowledge and understanding of the territory | Multidisciplinary platform: it would be necessary to design a system that provides decision-making support to essential service managers and governments, through the real-time acquisition of different types of data for monitoring and assessing the risk of extreme natural events and the subsequent assessment of their impact on services, population and the industrial system. |
| Cluster#3 “Human Factors” | RQ3 “What is the role of the human factor in the prevention of risks for CIs?” | From [72,73,74,75,76,77,78,79,80] | Lack of a recognized method for human factors assessment | Training: A specific training program based on behavioral science techniques should be developed and the improvement to increase the operator’s level of reliability taking into account the complexity of all the elements with which they have to interface. This obviously implies the tendency to minimize the presence of errors. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
De Felice, F.; Baffo, I.; Petrillo, A. Critical Infrastructures Overview: Past, Present and Future. Sustainability 2022, 14, 2233. https://doi.org/10.3390/su14042233
De Felice F, Baffo I, Petrillo A. Critical Infrastructures Overview: Past, Present and Future. Sustainability. 2022; 14(4):2233. https://doi.org/10.3390/su14042233
Chicago/Turabian StyleDe Felice, Fabio, Ilaria Baffo, and Antonella Petrillo. 2022. "Critical Infrastructures Overview: Past, Present and Future" Sustainability 14, no. 4: 2233. https://doi.org/10.3390/su14042233






