Exploring a New Security Framework for Remote Patient Monitoring Devices
Abstract
:1. Introduction
2. Legislation on Health Data Encryption
3. Issues in Currents RPM Devices
- How can a clinician trust the data measured by a patient at home if it is not supervised and the patient is in a multi-user environment?
- How can patients use RPM devices while ensuring their privacy and controlling the use of information in a simple intuitive way?
4. Threats and Risks
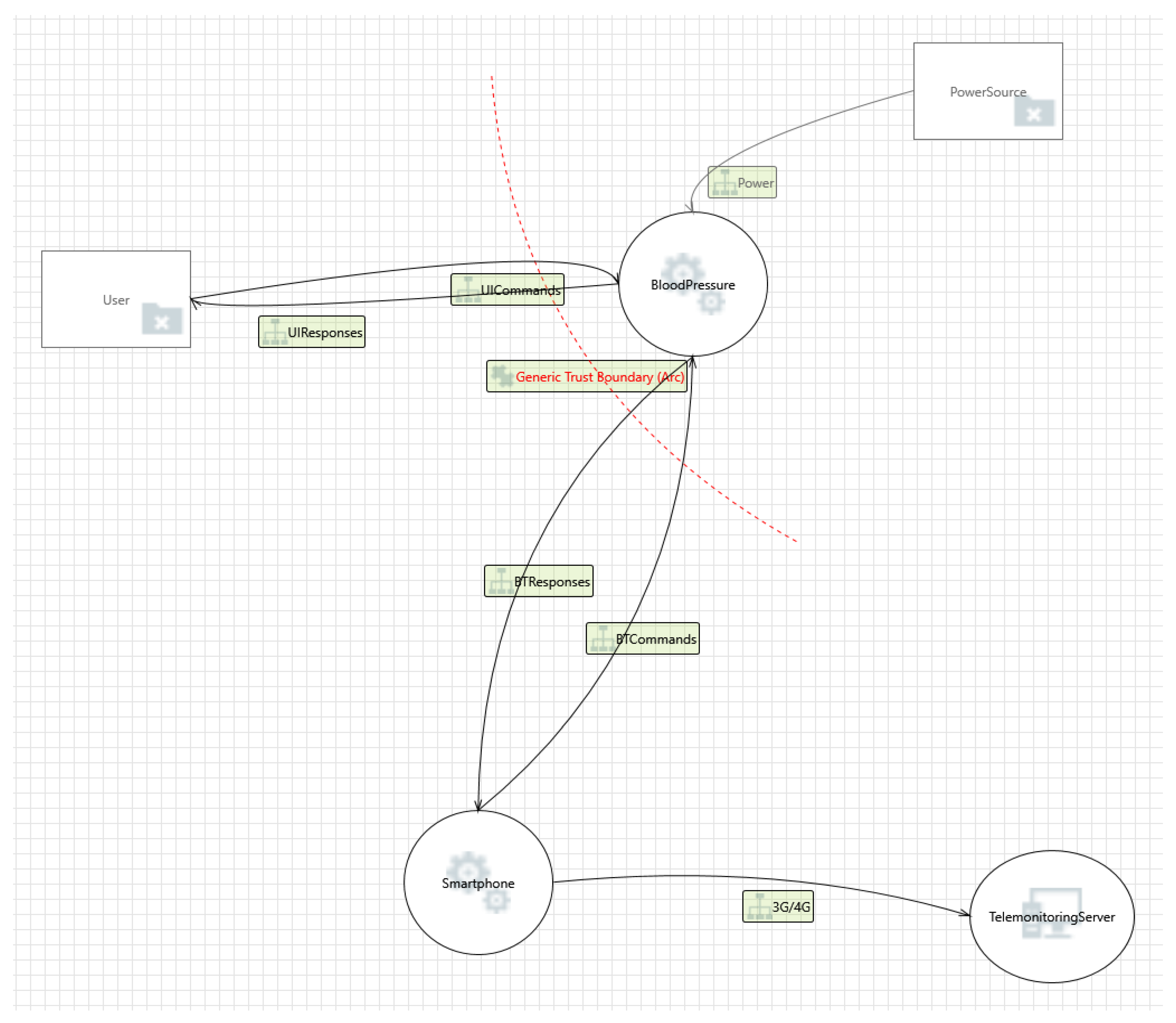
Threat Modelling
5. Security Models
5.1. United4Health Telehealth Functional Model
- Device authenticationThis threat occurs when an unauthenticated device is introduced into an RPM ecosystem. Device authentication will ensure that only authorised devices are allowed in the network. In healthcare, diseases such as diabetes rely on accurate measurements for treatment, if a device is lost or is replaced with a rogue device and then introduced into the ecosystem, there are high chances of it sending the wrong reading, which will trigger the wrong treatment that might endanger the patient’s life [20].
- Data availabilityThis are measures taken to ensure that data continues to be available at a required level of performance in situations ranging from normal to a disaster. Without appropriate security measures in the telemonitoring server and the manager device, it is highly likely that data can be made unavailable or be compromised. This model does not address the issue of data availability.
- Manager device securitySecurity issues can arise when managers are infected with malware, which have the ability to change data format. The authors of United4Health (United4Health—project aimed to exploit and further deploy innovative telemedicine services implemented and trialed under the RENEWING HEALTH project [26]) failed to mention on security requirements of the manager device which is very crucial.Figure 2 below shows the United4Health telehealth system functional model.
- Point of careThe patient takes their readings from the SpO2 sensor device which communicates the measurement through a wireless Bluetooth device to the manager device. The data from the SpO2 is stored in a local database on the manager device. The manager device then transmits the data to the HIS infrastructure. The patient authenticates themselves using a PIN on the manager device. A username and PIN is used to identify the patient.
- Health Information serviceFrom the manager device, the data is transmitted and stored in a PEHR. Clinicians and carers can access the data through a telehealth service which provides web based information.Uses HTTPS for providing end to end encryption communication between the manager device and the PEHR. The unique device identifier of the manager device and the corresponding symmetric key known to the PEHR is used for authentication and for establishing bidirectional session encryption.
- Health care and sourcesDifferent organizations, clinicians, and care professionals get access to the data from the patients. This can be viewed through a web-portal containing details of the data being monitored from the HIS infrastructure. It uses a role based access control for the users of the system.United4health functional model provides a detailed overview of the security requirements of the RPM system.
5.2. The New Security Framework for RPM Devices
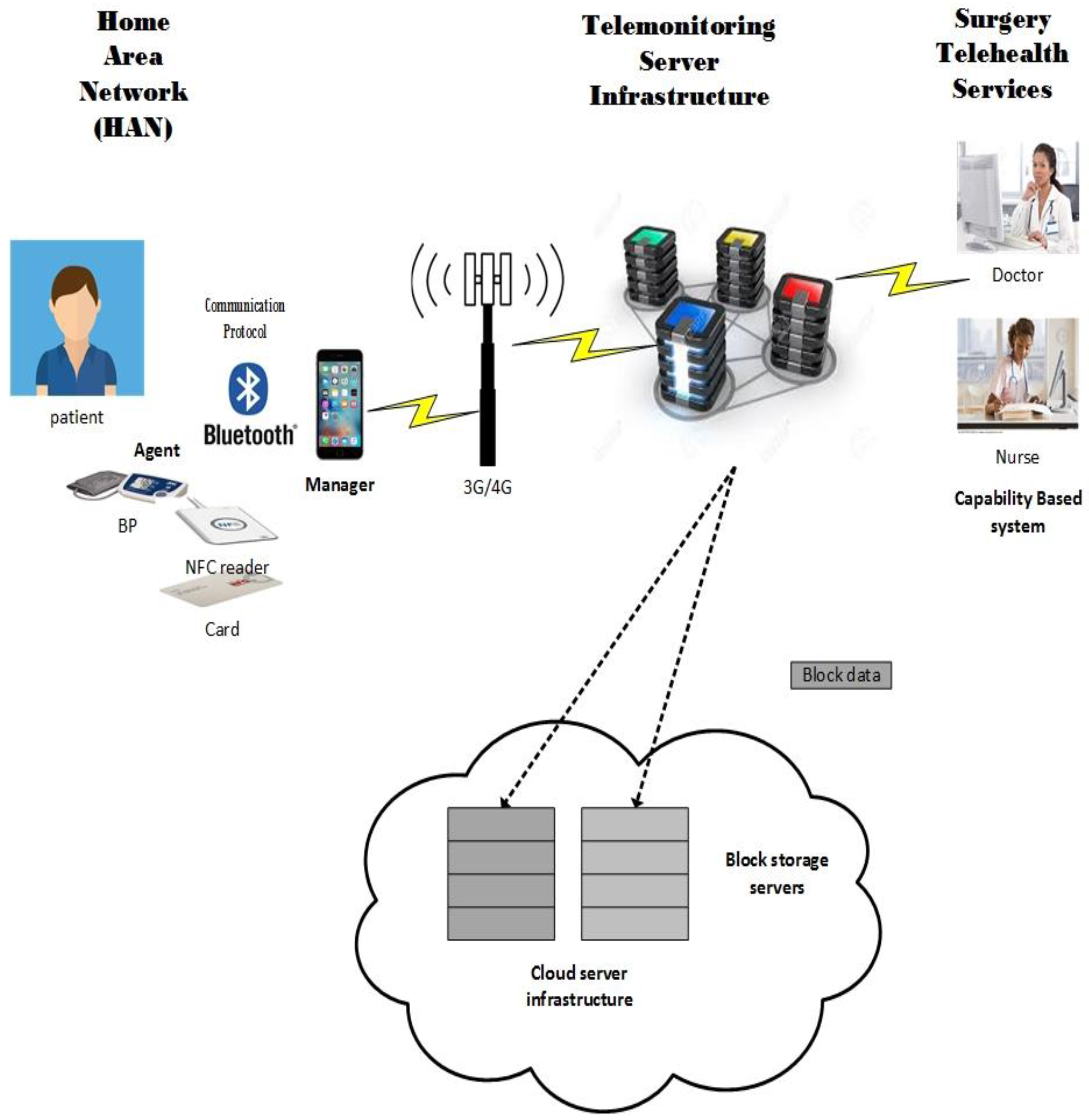
5.2.1. Home Area Network
How It Will Work
A Capability-Based System for the Secure Use of NFC
5.2.2. Telemonitoring Server Infrastructure
5.2.3. Cloud Server Infrastructure
5.2.4. Surgery Telehealth Services
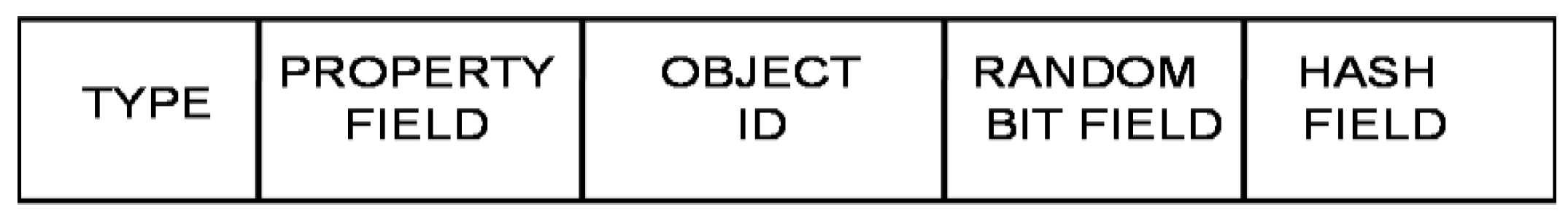
- The Type Field: This field is used to specify the type of object capability that is being used. Types could include cloud providers, cloud platforms, users, applications, etc.
- The Property Field: This field is used to define the properties of the object.
- The Object ID: This field is used to uniquely identify the object.
- The Random Bit Field: This field helps to uniquely identify the object.
- The Hash Field: The Hash field is used to prevent the casual tampering of capabilities.
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Cafazzo, J.A.; Leonard, K.; Easty, A.C.; Rossos, P.G.; Chan, C.T. Bridging the self-care deficit gap: Remote patient monitoring and hospital at home. In Electronic Healthcare; Springer: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- Food and Drug Administration (FDA). FDA Content of Premarket Submissions for Management of Cybersecurity in Medical Devices; FDA: Silver Spring, MD, USA, 2013.
- Norse SANS Institute. Health Care Cyberthreat Report: Widespread Compromises Detected, Compliance Nightmare on Horizon. Available online: https://www.sans.org/reading-room/whitepapers/analyst/health-care-cyberthreat-report-widespread-compromises-detected-compliance-nightmare-horizon-34735 (accessed on 22 February 2017).
- GS1. Global Standards Pave the Way for Unique Device Identification (UDI). Available online: http://www.gs1.org/docs/healthcare/GS1_UDI_Position_Paper.pdf (accessed on 20 February 2017).
- Jacob, J.A. Hackers Could Threaten Home Health Monitoring Devices. Available online: http://www.healthbizdecoded.com/2013/09/hackers-could-threaten-home-health-monitoring-devices (accessed 24 February 2017).
- Fadilpašić, S. NHS Trusts Lack Cyber-Attack Protection. Available online: http://www.itproportal.com/2015/12/08/nhs-trusts-lack-cyber-attack-protection/#ixzz46ejhsgiS (accessed on 8 January 2016).
- Food and Drug Administration (FDA). Postmarket Management of Cybersecurity in Medical Devices Draft Guidance for Industry and Food and Drug Administration Staff; FDA: Silver Spring, MD, USA, 2016.
- Doctors Remote Patient Monitoring: Real-Time Patient Data, Real Liability Risks. 2016. Available online: http://www.thedoctors.com/KnowledgeCenter/PatientSafety/articles/Remote-Patient-Monitoring-Real-Time-Patient-Data-Real-Liability-Risks (accessed on 8 January 2016).
- HIPPA. Health Insurance Portability and Accountability Act of 1996. Available online: https://www.healthit.gov/sites/default/files/rules-regulation/health-insurance-portability.pdf (accessed on 27 July 2016).
- Data Protection Act 1998. Available online: http://www.legislation.gov.uk/UKPGA/1998/29/contents (accessed on 27 July 2016).
- Garg, V.; Brewer, J. Telemedicine security: A systematic review. J. Diabetes Sci. Technol. 2011, 5, 768–777. [Google Scholar] [CrossRef] [PubMed]
- Continua Health Alliance. Recommendations for Proper User Identification in Continua Version 1—PAN and xHR Interfaces; Continua Health Alliance: Beaverton, OR, USA, 2008. [Google Scholar]
- Ondiege, B.; Clarke, M.; Mapp, G. Exploring Security of Remote Patient Monitoring Devices Using NFC Technology for Identification of the Frail Elderly. In Proceedings of the 8th International Conference e-Health, Funchal, Portugal, 1–3 July 2016.
- Vavilis, S.; Petkovi, M.; Zannone, N. Impact of ICT on Home Healthcare. In Proceedings of the IFIP International Conference on Human Choice and Computers (HCC 2012), Amsterdam, The Netherlands, 27–28 September 2012.
- Kliem, A.; Hänsel, J.; Hovestadt, M.; John, M.; Kao, O. Towards self-organization of networked medical devices. In Proceedings of the IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Toulouse, France, 5–9 September 2011.
- Ondiege, B.; Clarke, M. Healthcare Professionals Perception on Information Security. In Proceedings of the 5th International Conference on Internet Technologies & Society, Taipei, Taiwan, 10–12 December 2014.
- IEEE Standards on Cybersecurity. Available online: http://theinstitute.ieee.org/benefits/standards/ieee-standards-on-cybersecurity (accessed on 22 February 2017).
- Part 10103: Nomenclature—Implantable device, cardiac. Available online: https://shop.austrian-standards.at/Preview.action;jsessionid=BD0A395AEB0CBA9629F4007A60E72462?preview=&dokkey=521755&selectedLocale=en (accessed on 22 February 2017).
- Pickering, T.G.; Hall, J.E.; Appel, L.J.; Falkner, B.E.; Graves, J.; Hill, M.N.; Jones, D.W.; Kurtz, T.; Sheps, S.G.; Roccella, E.J. AHA Scientific Statement: Recommendations for blood pressure measurement in humans and experimental animals, part 1: Blood pressure measurement in humans. Hypertension 2005, 45, 142–161. [Google Scholar] [CrossRef] [PubMed]
- Petković, M. Remote Patient Monitoring: Information Reliability Challenges. In Proceedings of the 9th International Conference on Telecommunication in Modern Satellite, Cable, and Broadcasting Services (TELSIKS ’09), Nis, Serbia, 7–9 October 2009.
- Gibbs, M.; Quillen, H. The Medical-Grade Network: Helping Transform Healthcare. Available online: http://www.cisco.com/web/strategy/docs/healthcare/07CS1034_HC_Whitepaper_r5.pdf (accessed on 12 December 2016).
- OWASP. Category: Threat Modelling. Available online: https://www.owasp.org/index.php/Category:Threat_Modeling (accessed on 7 July 2016).
- SDL Threat Modeling Tool, version 3; Microsoft Corporation: Redmond, WA, USA, 2008.
- Pah, W.; Williams, P.A.; Maeder, A.J. A Conceptual framework for secure mobile health. J. Int. Soc. Telemed. eHealth 2013, 11, 44–51. [Google Scholar]
- Patient Privacy in a Mobile World: A Framework to Address Privacy Law Issues in Mobile Health. Available online: http://www.trust.org/contentAsset/raw-data/03172beb-0f11-438e-94be-e02978de3036/file (accessed on 22 February 2017).
- Gerdes, M.; Fensli, R. End-to-end Security and Privacy Protection for Co-operative Access to Health and Care Data in a Telehealth Trial System for Remote Supervision of COPD-Patients. In Proceedings of the 13th Scandinavian Conference on Health Informatics, Tromsø, Norway, 15–17 June 2015.
- Mapp, G.; Aiash, M.; Ondiege, B.; Clarke, M. Exploring a New Security Framework for Cloud Storage Using Capabilities. In Proceedings of the IEEE 8th International Symposium on Service Oriented System Engineering (SOSE), Oxford, UK, 7–11 April 2014; pp. 484–489.
- NHS Information Governance. Guidelines on Use of Encryption to Protect Person Identifiable and Sensitive Information; NHS Information Governance: Leeds, UK, 2008.

| Threat and Risk | Examples |
|---|---|
| Human Issues | Usability Since a PHD and the managing software are used by the user/patient, they need to be as user friendly and as easy to use as possible. Since this technology is for the elderly and some of them might have other disabilities, the system must adhere to usability and accessibility guidelines. Research shows that humans are the weakest link in the security chain and many attacks in computer systems are through social engineering [18]. For example, using a covert channel to deceive a healthcare provider employee to gain access to a person’s medical record. |
| Missing information about how to use a PHD | Placing the blood pressure cuff incorrectly might lead to misleading results and wrong medical treatment being triggered [19]. Therefore, detailed and user oriented manuals and descriptions of PHDs are necessary. |
| PHD technical failure | Threats and risks also might arise from technical failures of PHDs, which might vary from a device sending wrong or no data to communication limitation or even complete breakdown. This can have an impact on availability. |
| PHD abuse | Agent device abuse Device might be stolen and switched by a compromised agent that either deliberately provides wrong data that will trigger wrong treatment or intercepts patient and medical data [20]. Abuse of device manager software For technical reasons, wireless communication is much more likely to be compromised, which is similar to misuse of agent devices, and the transmitted information could either be altered and entered into the communication channel [18,21]. Manager to telemonitoring server abuse Device fraud and manipulation are possible abuse cases. For example, eavesdropping, which is common to attackers since data from various devices have already been merged and formatted for transmission [18,21]. Telemonitoring server abuse Many abuse cases transpire within healthcare provider organisations where a large number of users and devices access large amounts of user/patient-specific data through many process steps [18]. The wide range of applications or devices in the healthcare organisation has many targets for attacks and setups for abuse; hence, any component might be tampered with, every transport channel snooped, data manipulated or even deleted, which creates issues of availability when patient data is needed. Therefore, appropriate access control need to be put in place. |
| Threat | Category | Description | Requirement |
|---|---|---|---|
| Potential data repudiation | Repudiation | Smartphone claiming it did not receive data from a source outside the trust boundary. | Digital signatures can be used to counter this threat. Therefore, it is important to have audit trails from the source, indicating time and the summary of the data received. |
| Spoofing the blood pressure process | Spoofing | The blood pressure monitor may be spoofed by an attacker and this may lead to information disclosure by smartphone. | With lack of authentication mechanism to identify the destination would mean that this attack would likely occur. Encryption can also be used in preventing information disclosure. |
| Spoofing the smartphone process | Spoofing | The smartphone may be spoofed by an attacker and this may lead to information disclosure by smartphone. | With lack of authentication mechanism to identify the source would mean that this attack would likely occur. |
| Elevation using impersonation | Elevation of privilege | Smartphone may be able to impersonate the context of blood pressure monitor in order to gain additional privilege. | Access control |
| Elevation by changing the execution flow in smartphone | Elevation of privilege | An attacker may pass data into smartphone in order to change the flow of program execution within smartphone to the attacker‘s choosing. | Encryption and access control |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ondiege, B.; Clarke, M.; Mapp, G. Exploring a New Security Framework for Remote Patient Monitoring Devices. Computers 2017, 6, 11. https://doi.org/10.3390/computers6010011
Ondiege B, Clarke M, Mapp G. Exploring a New Security Framework for Remote Patient Monitoring Devices. Computers. 2017; 6(1):11. https://doi.org/10.3390/computers6010011
Chicago/Turabian StyleOndiege, Brian, Malcolm Clarke, and Glenford Mapp. 2017. "Exploring a New Security Framework for Remote Patient Monitoring Devices" Computers 6, no. 1: 11. https://doi.org/10.3390/computers6010011






