Accountability Requirements in the Cloud Provider Chain
Abstract
:1. Introduction
- Who can access personal data?
- How can personal data be used?
- Who is responsible for data governance?
2. Background
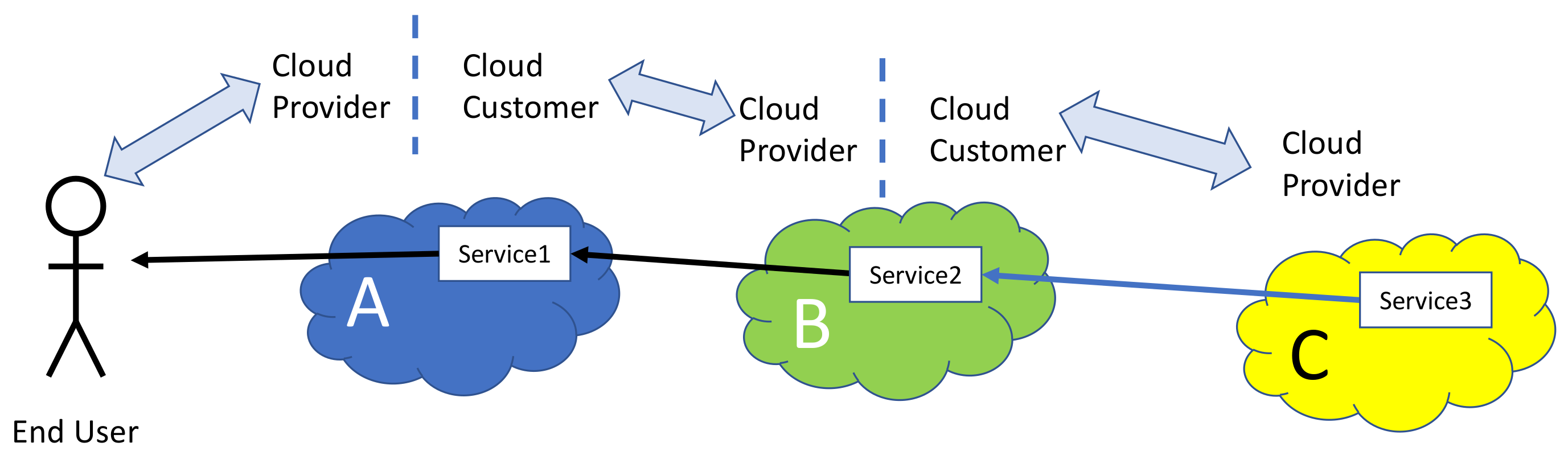
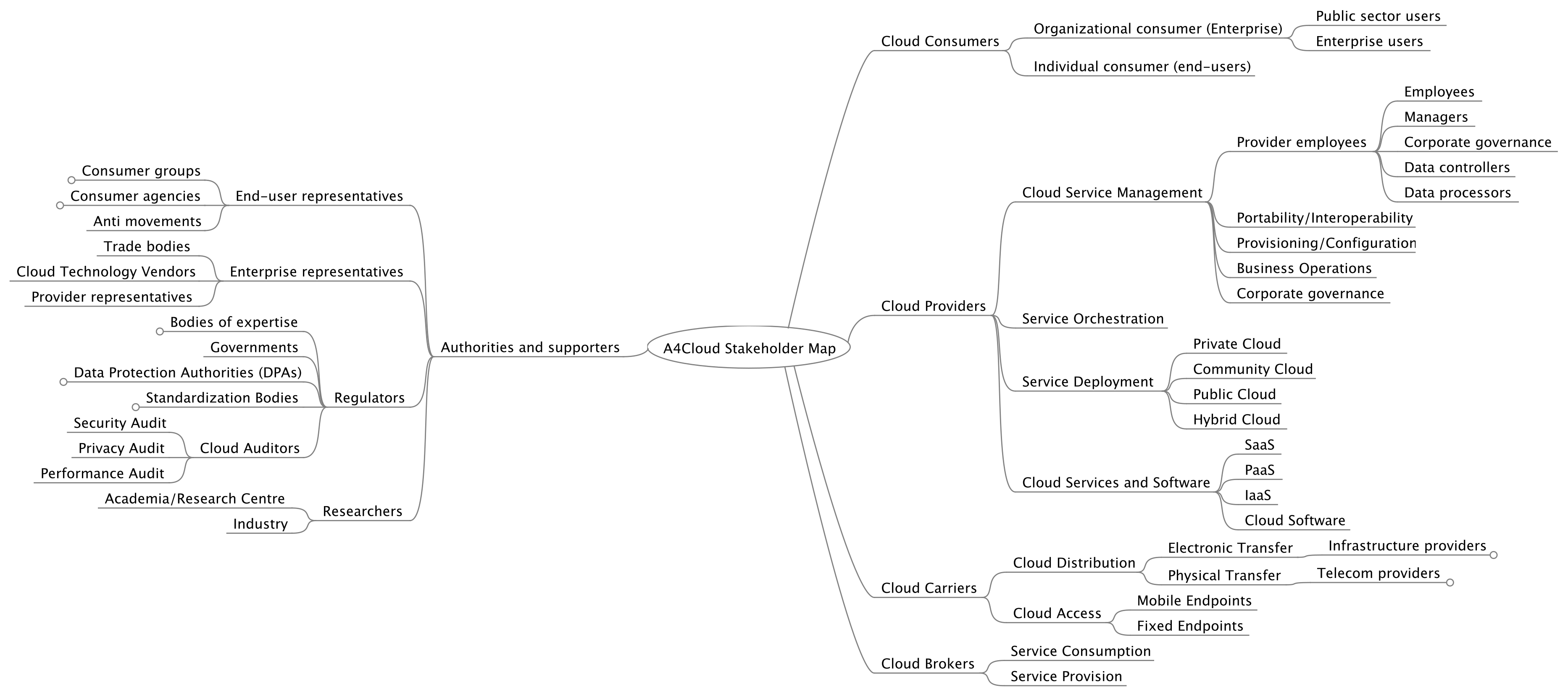
2.1. Cloud Actors
- Cloud Subject: An individual whose data are processed by a cloud provider, either directly or indirectly.
- Cloud Customer: An entity that (a) maintains a business relationship with, and (b) uses services from a Cloud Provider. When necessary we may further distinguish:
- (a)
- Individual Cloud Customer, when the entity refers to a person.
- (b)
- Organization Cloud Customer, when the entity refers to an organization.
- Cloud Provider: An entity responsible for making a cloud service available to Cloud Customers
- Cloud Carrier: The intermediary entity that provides connectivity and transport of cloud services between Cloud Providers and Cloud Customers.
- Cloud Broker: An entity that manages the use, performance and delivery of cloud services, and negotiates relationships between Cloud Providers and Cloud Customers.
- Cloud Auditor: An entity that can conduct independent assessment of cloud services, information system operations, performance and security of the cloud implementation, with regards to a set of requirements, which may include security, data protection, information system management, regulations and ethics.
- Cloud Supervisory Authority: An entity that oversees and enforces the application of a set of rules.
2.2. Cloud Accountability
- Transparency: the property of an accountable system that it is capable of “giving account” of, or providing visibility of how it conforms to its governing rules and commitments.
- Responsiveness: the property of a system, organization or individual to take into account input from external stakeholders and respond to queries of these stakeholders.
- Responsibility: the property of an organization or individual in relation to an object, process or system of being assigned to take action to be in compliance with the norms.
- Remediability: the property of a system, organization or individual to take corrective action and/or provide a remedy for any party harmed in case of failure to comply with its governing norms.
- Verifiability: the extent to which it is possible to assess norm compliance.
- Attributability: the possibility to trace a given action back to a specific entity.
- Responsibility: the property of an organization or individual in relation to an object, process or system of being assigned to take action to be in compliance with the norms.
- Observability: the extent to which the behavious of the system is externally viewable.
- Appropriateness: the extent to which the technical and organizational measures used have the capability of contributing to accountability.
- Effectiveness: the extent to which the technical and organizational measures used actually contribute to accountability.
2.3. Requirement Engineering
3. Requirements Elicitation Method
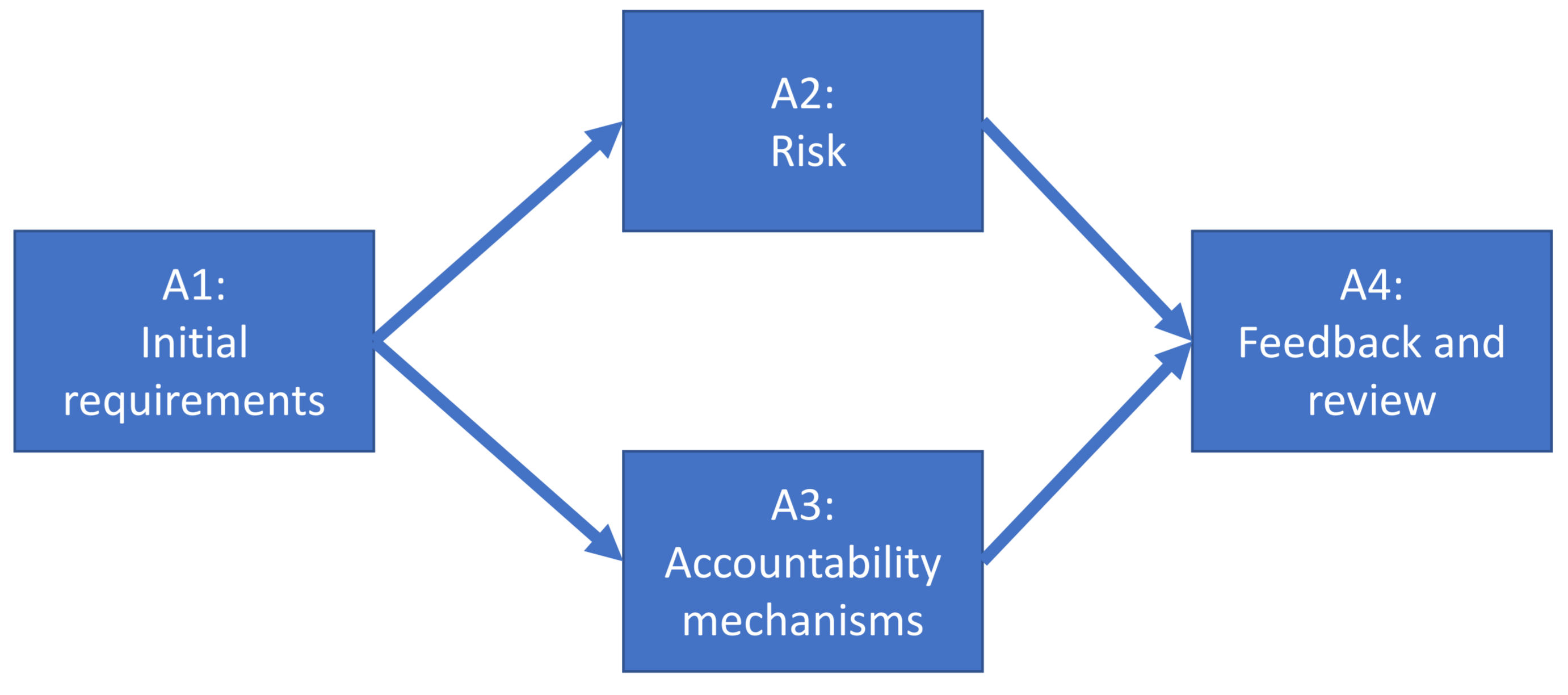
3.1. The Elicitation Activities and Events
3.2. Data Collection
3.2.1. Activity A1—Initial Requirements
3.2.2. Activity A2—Risks
3.2.3. Activity A3—Accountability Mechanisms
- What is the most important information you think should be provided to the cloud customer when buying services from cloud service providers?
- In which parts would you like to be involved in making the decisions? In which parts would you like just to be informed of the decisions?
- What would increase your trust that the data is secure in this scenario?
- What do you want to know about how the provider corrects data security problems?
- Data Track: a transparency tool that displays an overview of a subject’s data disclosures to different providers and allows subjects to access data collected about them stored at the provider, etc. [18]
- Cloud Offerings Advisory Tool (COAT): a tool to support selection of cloud services based on customer preferences [19]
3.2.4. Activity A4—Feedback, Review and Open Gaps
3.3. Requirements Repository
- Collecting all requirements from all workpackages in a single location;
- Describing all requirements in a uniform manner;
- Providing a global reference for each requirement for tracking purposes.
4. Results
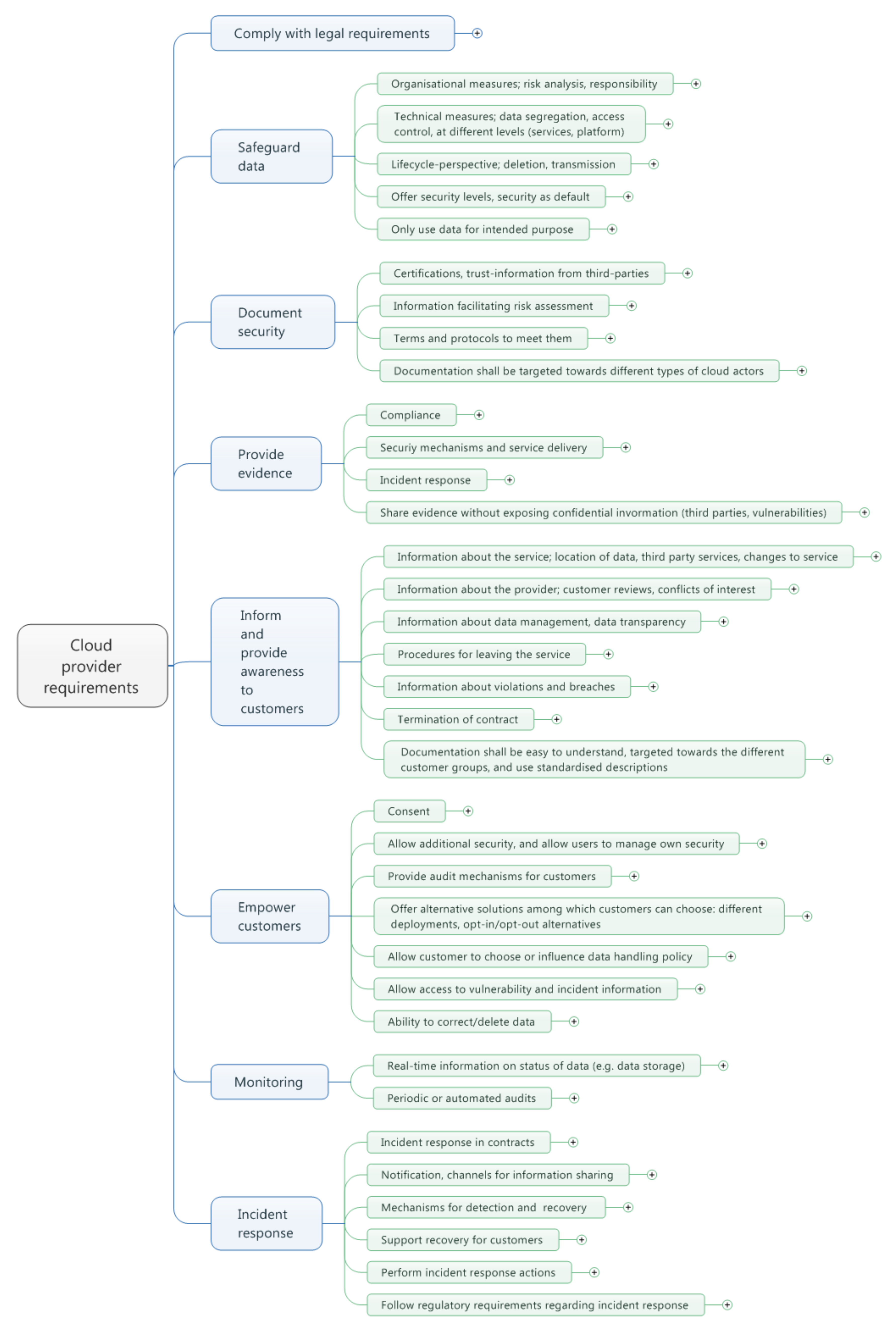
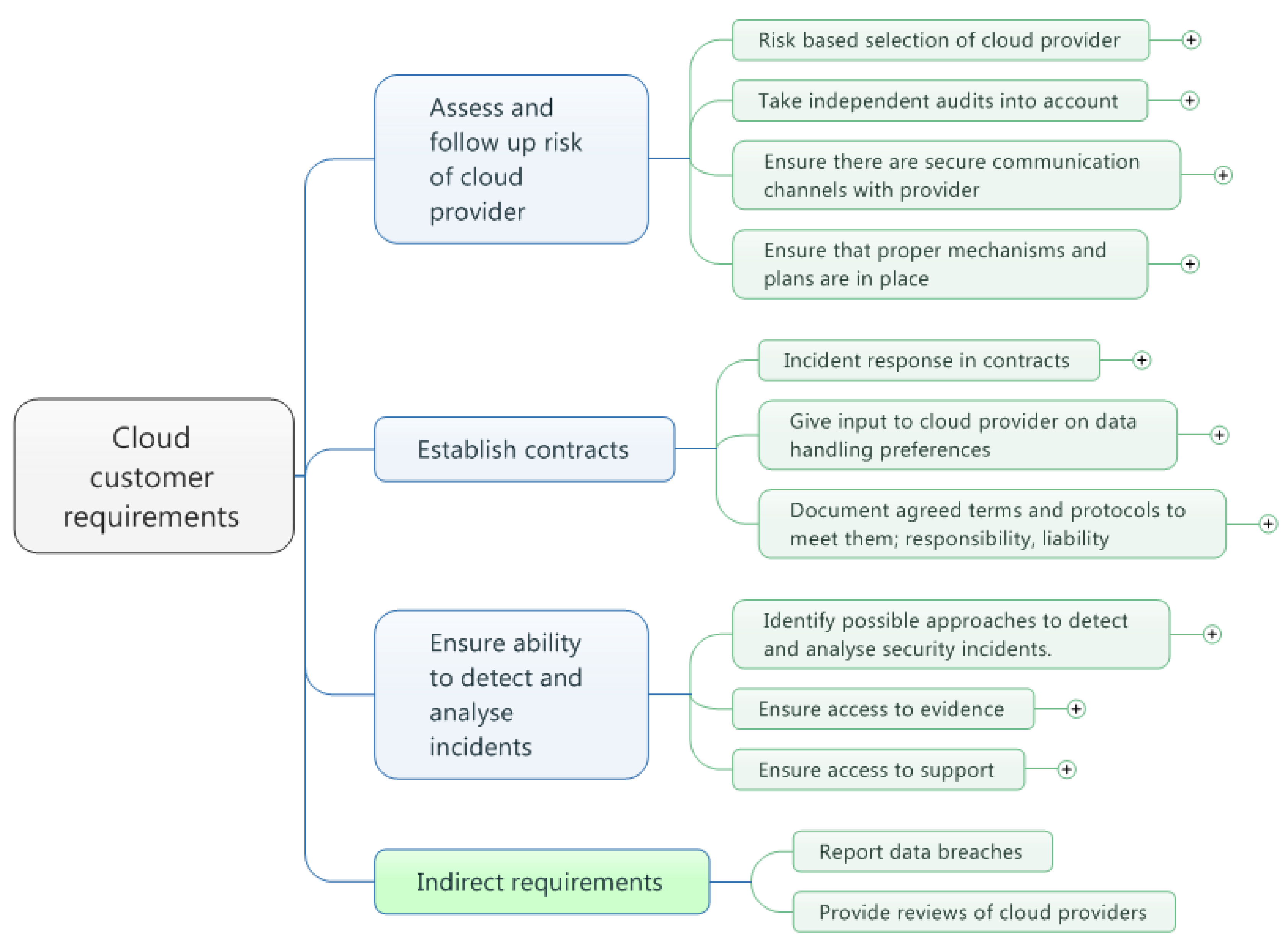
4.1. Requirements that Target Cloud Providers
4.2. Requirements that Target Cloud Subjects or Cloud Customers
- Technical: The variety and the amount of data collected make it difficult to understand the scope of the exposure and the usages after multi-source aggregation and complex data mining
- Lack of transparency: Whereas some data are de facto already sold, it is nearly impossible for a citizen to know who the buyers are and how sound the anonymization techniques are (if any), equally incidents are barely reported and unlikely linked to the data sources
- Legal: The coexistence of a “borderless” cloud and multiple jurisdiction frameworks may impeach users to make use of their rights or may expose the companies involved in the data processing chain
4.3. Requirements that Target Cloud Brokers
- Interpretation and negotiation of policy: It is expected that cloud brokers should be able to negotiate policy requirements with both cloud providers and cloud customers, and be able to interpret and possibly enhance policy terms, as well as report subsets of policies.
- Evidence of non-data aggregation: It is expected that cloud brokers are able to provide evidence that data are not aggregated, or alternatively, that there is effective data segregation in place
- Relay messages: Brokers are expected to relay messages between cloud providers and cloud customers, i.e., demonstration requests, remediation requests, data breach notifications and compliance and performance indicators.
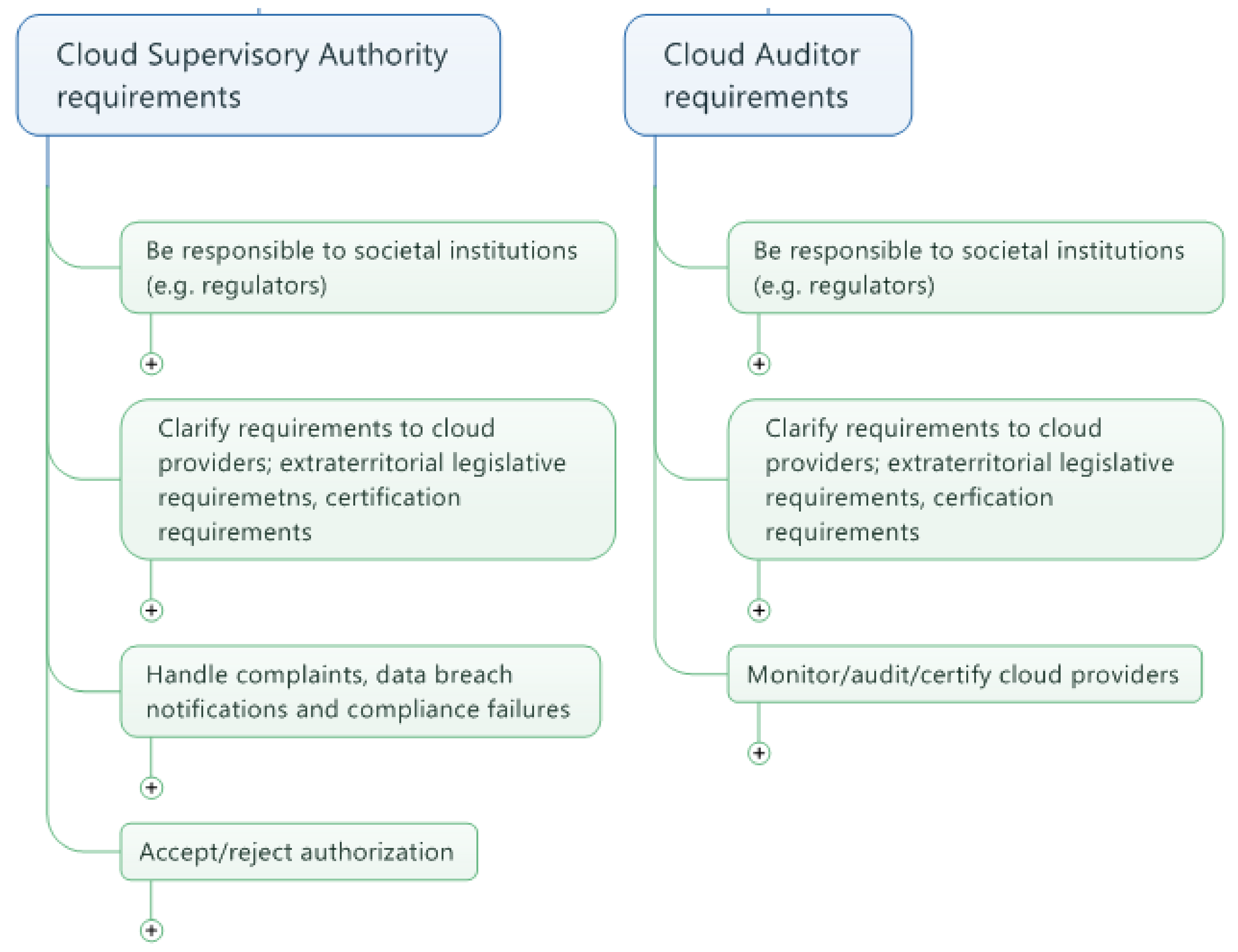
4.4. Requirements that Target Cloud Auditors or Cloud Supervisory Authorities
4.5. Requirements not Directly Targeted towards a Particular Cloud Actor
- not knowing where the resources were moved in the cloud
- the potential lack of accountability when buying from a provider that purchases services from another provider, not knowing who is responsible for what
- the risk of trusting people with a conflict of interest
4.6. The Role of Accountability
4.6.1. Unclear Relationship between Accountability, Risk and Trust
- Accountability and risk: Although accountability addresses risk, it is yet unclear how. The relationship between accountability and risk is a generalized one. That is, it is believed that accountability addresses emergent risks in cloud ecosystems. However, stakeholders had difficulties to figure out in which way. Stakeholders questioned whether accountability addresses risk (by modifying risk profiles in terms of likelihood of occurrence or severity of impact) or changes risk perception of emerging threats in cloud ecosystems.
- Accountability and trust: The relationship between accountability and trust seem to be more context-dependent than the one with risk. Accountability helps to make trust decisions, however accountability itself seems to be necessary but not sufficient for (or implying unconditionally) trust. Accountability will help to make trust decisions. A critical aspect of trust decisions seem to be related to the evidence provided to stakeholders. Therefore, accountability (in particular transparency) plays an important role in trust decisions and supports trustworthiness (in particular based on accountability evidence).
4.6.2. Accountability and the Cloud Business Model
5. Discussion
5.1. The Requirements
5.2. The Requirements Elicitation Method
5.3. Stakeholder Participation
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Felici, M.; Jaatun, M.G.; Kosta, E.; Wainwright, N. Bringing accountability to the cloud: Addressing emerging threats and legal perspectives. In Cyber Security and Privacy; Springer: Berlin/Heidelberg, Germany, 2013; pp. 28–40. [Google Scholar]
- Jaatun, M.G.; Pearson, S.; Gittler, F.; Leenes, R.; Niezen, M. Enhancing Accountability in the Cloud. Int. J. Inf. Manag. 2016. [Google Scholar] [CrossRef]
- Jaatun, M.G.; Tøndel, I.A.; Moe, N.B.; Cruzes, D.S.; Bernsmed, K.; Haugset, B. Accountability Requirements for the Cloud. In Proceedings of the 2017 IEEE International Conference on Cloud Computing Technology and Science (CloudCom), Hong Kong, China, 11–14 December 2017; pp. 375–382. [Google Scholar]
- Liu, F.; Tong, J.; Mao, J.; Bohn, R.; Messina, J.; Badger, L.; Leaf, D. NIST cloud computing reference architecture. NIST Spec. Publ. 2011, 500, 292. [Google Scholar]
- Pearson, S.; Shen, Y.; Mowbray, M. A Privacy Manager for Cloud Computing. In Cloud Computing; Jaatun, M.G., Zhao, G., Rong, C., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 90–106. [Google Scholar]
- Pearson, S. Toward Accountability in the Cloud. Int. Comput. IEEE 2011, 15, 64–69. [Google Scholar] [CrossRef]
- Mowbray, M.; Pearson, S.; Shen, Y. Enhancing privacy in cloud computing via policy-based obfuscation. J. Supercomput. 2012, 61, 267–291. [Google Scholar] [CrossRef]
- Felici, M.; Pearson, S.; Dziminski, B.; Gittler, F.; Koulouris, T.; Leenes, R.; Niezen, M.; Nuñez, D.; Pannetrat, A.; Royer, J.C.; et al. Conceptual Framework; Technical Report D:C-2.1; A4Cloud Project: Malaga, Spain, June 2014. [Google Scholar]
- Nuseibeh, B.; Easterbrook, S. Requirements engineering: A roadmap. In Proceedings of the Conference on the Future of Software Engineering, Limerick, Ireland, 4–11 June 2000; pp. 35–46. [Google Scholar]
- Gottesdiener, E. Requirements by Collaboration: Workshops for Defining Needs; Addison-Wesley Professional: Boston, MA, USA, 2002. [Google Scholar]
- Jaatun, M.G.; Pearson, S.; Gittler, F.; Leenes, R. Towards Strong Accountability for Cloud Service Providers. In Proceedings of the 2014 IEEE 6th International Conference on Cloud Computing Technology and Science (CloudCom), Singapore, 15–18 December 2014; pp. 1001–1006. [Google Scholar]
- Owen, H. Open Space Technology: A User’s Guide; Berrett-Koehler Publishers: San Francisco, CA, USA, 2008. [Google Scholar]
- OpenSpaceWorld.ORG. Available online: http://openspaceworld.org/ (accessed on 11 March 2013).
- World Café. Available online: http://www.theworldcafe.com/ (accessed on 11 March 2013).
- Morgan, D.L. Focus groups. Ann. Rev. Soc. 1996, 129–152. [Google Scholar] [CrossRef]
- Morgan, D.L. Focus Groups As Qualitative Research; Sage Publications: London, UK, 1996; Volume 16. [Google Scholar]
- Jaatun, M.G.; Cruzes, D.S.; Angulo, J.; Fischer-Hübner, S. Chapter: Accountability Through Transparency for Cloud Customers. In Cloud Computing and Services; Revised Selected Papers; Springer International Publishing: Cham, Switzerland, 2016; pp. 38–57. [Google Scholar]
- Fischer-Hübner, S.; Angulo, J.; Pulls, T. How can Cloud Users be Supported in Deciding on, Tracking and Controlling How their Data are Used. In Privacy and Identity Management for Emerging Services and Technologies; Hansen, M., Hoepman, J.H., Leenes, R., Whitehouse, D., Eds.; IFIP Advances in Information and Communication Technology; Springer: Berlin/Heidelberg, Germany, 2014; Volume 421, pp. 77–92. [Google Scholar]
- Alnemr, R.; Pearson, S.; Leenes, R.; Mhungu, R. COAT: Cloud Offerings Advisory Tool. In Proceedings of the 2014 IEEE 6th International Conference on Cloud Computing Technology and Science (CloudCom), Singapore, 15–18 December 2014; pp. 95–100. [Google Scholar]
- Jaatun, M.G.; Cruzes, D.S.; Felici, M.; Haugset, B.; Bernsmed, K.; Gago, C.F.; Reed, C.; Leenes, R. Requirements Report; Technical Report D:B-2.4; A4Cloud Project: Malaga, Spain, 2014. [Google Scholar]
- CSA. Security Guidance for Critical Areas of Focus in Cloud Computing v3.0; Technical Report; Cloud Security Alliance: Las Vegas, NV, USA, 2011. [Google Scholar]
- Grobauer, B.; Schreck, T. Towards Incident Handling in the Cloud: Challenges and Approaches. In Proceedings of the 2010 ACM Workshop on Cloud Computing Security, Chicago, IL, USA, 8 October 2010; ACM: New York, NY, USA, 2010; pp. 77–86. [Google Scholar]
- Cruzes, D.S.; Dybå, T. Recommended Steps for Thematic Synthesis in Software Engineering. In Proceedings of the 2011 International Symposium on Empirical Software Engineering and Measurement (ESEM), Banff, AB, Canada, 22–23 September 2011; pp. 275–284. [Google Scholar]
- European Union. 95/46/EC of the European Parliament and of the Council of 24 October 1995 on the Protection of Individuals with Regard to the Processing of Personal Data and on the Free Movement of Such Data; EU: Brussels, Belgium, 1995. [Google Scholar]
- European Union. Proposal for a REGULATION OF THE EUROPEAN PARLIAMENT AND OF THE COUNCIL on the Protection of Individuals with Regard to the Processing of Personal Data and on the Free Movement of Such Data (General Data Protection Regulation); EU: Brussels, Belgium, 2012. [Google Scholar]
| Activity | Goal | Method | Participants | Results |
|---|---|---|---|---|
| A1 | Accountability relationships and requirements | Open Space Technology; World Café | 7 participants; authorities, providers, customer, vendor | 57 accountability relationships, later refined into 53 requirements |
| A2 | Risk perception; relationship between accountability, risk and trust | Focus groups | 20 participants; authorities, providers, customers, vendors, academia | 15 requirements |
| A3 | Expectations about accountability; experience with accountability mechanisms | Four workshops (different actors and tools; discussions and questionnaires); interviews | About 90 participants (30 subjects, 20 customers, 40 providers) | 62 requirements |
| A4 | Previously uncovered topics: metrics; incident response; opinions of legal experts | Workshops (discussions and questionnaires); email survey and informal conversations | About 60 participants: academia and IT professionals | 23 requirements |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jaatun, M.G.; Tøndel, I.A.; Moe, N.B.; Cruzes, D.S.; Bernsmed, K.; Haugset, B. Accountability Requirements in the Cloud Provider Chain. Symmetry 2018, 10, 124. https://doi.org/10.3390/sym10040124
Jaatun MG, Tøndel IA, Moe NB, Cruzes DS, Bernsmed K, Haugset B. Accountability Requirements in the Cloud Provider Chain. Symmetry. 2018; 10(4):124. https://doi.org/10.3390/sym10040124
Chicago/Turabian StyleJaatun, Martin Gilje, Inger Anne Tøndel, Nils Brede Moe, Daniela Soares Cruzes, Karin Bernsmed, and Børge Haugset. 2018. "Accountability Requirements in the Cloud Provider Chain" Symmetry 10, no. 4: 124. https://doi.org/10.3390/sym10040124





