Cooperative Secret Sharing Using QR Codes and Symmetric Keys
Abstract
:1. Introduction
- The objective of the proposed protocol is to encrypt and conceal shares within QR codes to be able to distribute the shares via public channels without raising suspicion. While there are a number of existing techniques for hiding a secret within a QR code, the purpose of many of these methods is for data hiding and not for secret sharing [5,6,7,8,9]. Hence, cooperation between a threshold number of participants to recover the secret is not incorporated in these techniques.
- There are some drawbacks with existing QR code secret sharing approaches that are based on visual cryptography. For example, the QR code sizes that are used may have to be very large [10]. This may be useful in situations where decryption necessitates no computation; however, large QR codes are impractical and are likely to raise suspicion as these are not commonly used in public. Other approaches result in QR codes that are valid, but do not look like normal QR codes because each module is divided into smaller sub-modules in order to enable secret sharing [11].
- There are also existing (n, n) QR code secret sharing approaches where normal looking QR codes are used [12,13]. However, (n, n) secret sharing requires that all participants must be present to recover the secret. The proposed protocol is for (k, n) secret sharing, where k can be < n. In other words, while a threshold number of participants is required to recover the secret, this threshold does not have to be all the participants.
- Unlike our previous work in Chow et al. [14], in which the purpose was to use a single non-suspicious QR code to broadcast a secret to a group of authorized participants where each participant can obtain the secret themselves, the protocol proposed in this paper provides a mechanism for a shared secret using QR codes. This means that each participant can only obtain his/her respective share, which does not reveal the secret, and must cooperate with other participants before the secret can be recovered.
2. Background
2.1. Secret Sharing
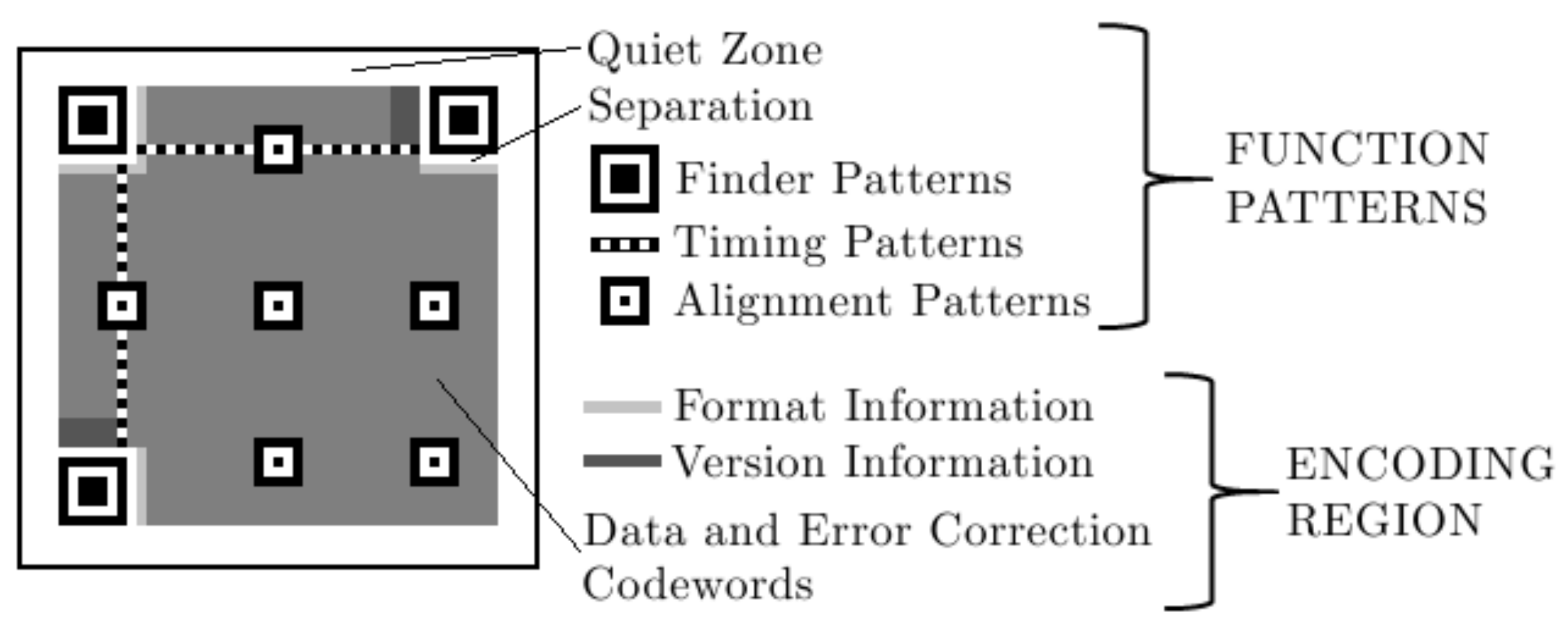
2.2. Quick Response Codes
3. Related Work
4. Protocol and Adversarial Models
4.1. Protocol Model
4.2. Adversarial Model
5. Secret Sharing Protocol Using QR codes
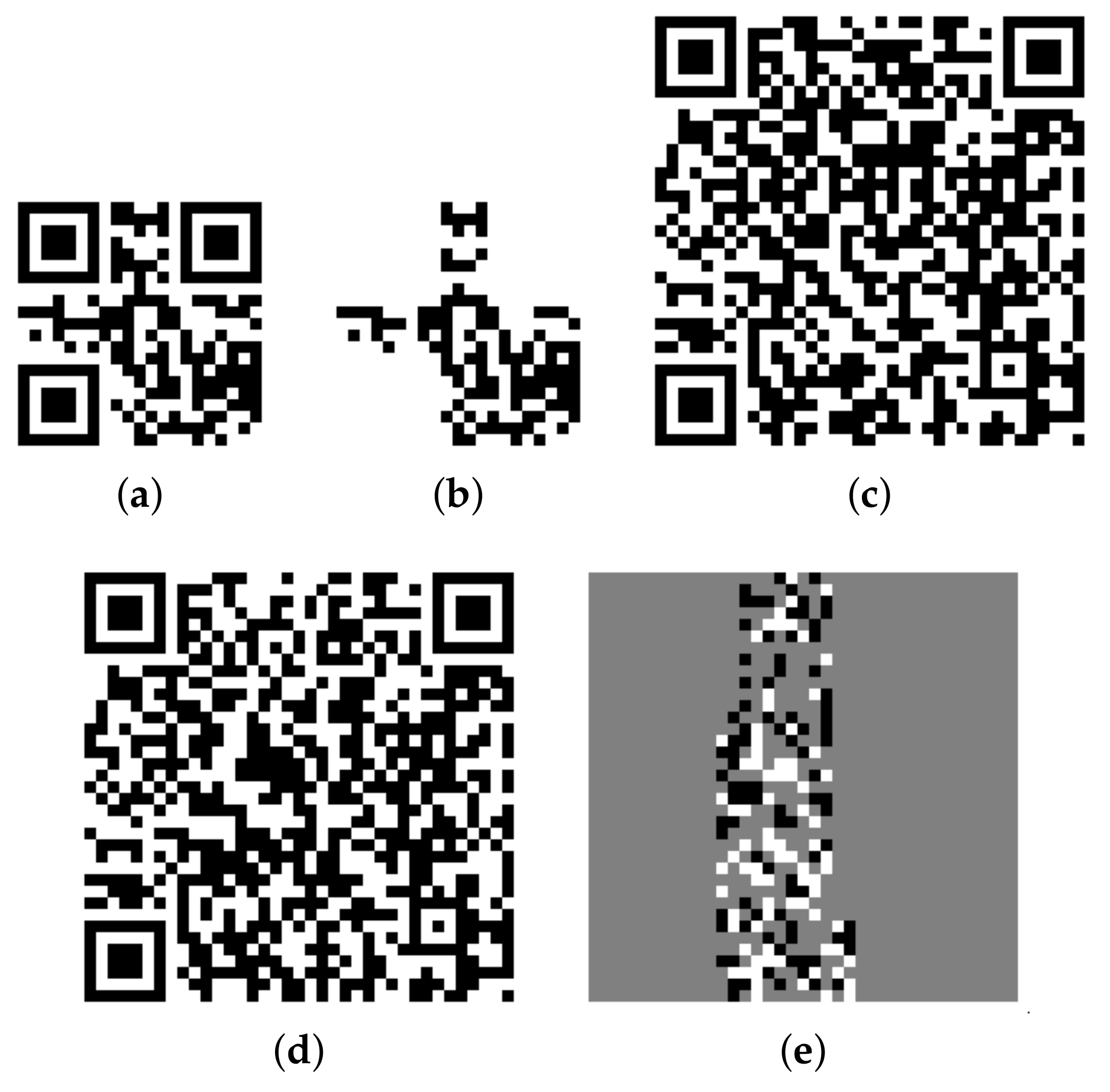
5.1. Encryption and Concealment Phase
- Enc(, ): This algorithm takes a share, , and encrypts it using a group member’s public key, . This results in the encrypted message, .
- : This process ‘XOR’s the encrypted message, , with a symmetric key, , to produce the encrypted hidden message, , which is to be embedded in a QR code.
- Gen(): Taking a public message, , this algorithm generates a cover QR code, .
- : This process embeds the encrypted hidden message, , into the cover QR code, , to produce a QR code, .
5.2. Extraction and Decryption Phase
- Ext(): Given the QR code with the conceal information, , this algorithm extracts the encrypted hidden message, , from it.
- : By ‘XOR’ing the encrypted hidden message, , with the symmetric key, , the encrypted message, , can be obtained.
- Dec(): This process obtains the share by decrypting the encrypted message, , using the private key, .
5.3. Cooperative Phase
6. Analysis and Discussion
6.1. Implementation Guidelines
6.2. Security
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Chow, Y.; Susilo, W.; Yang, G. Cooperative Learning in Information Security Education: Teaching Secret Sharing Concepts. In Lecture Notes in Computer Science, Proceedings of the 14th International Conference Cooperative Design, Visualization, and Engineering (CDVE), Mallorca, Spain, 17–20 September 2017; Luo, Y., Ed.; Springer: Berlin, Germany, 2017; Volume 10451, pp. 65–72. [Google Scholar]
- Beimel, A. Secret-Sharing Schemes: A Survey. In Lecture Notes in Computer Science, Proceedings of the Third International Workshop Coding and Cryptology (IWCC), Qingdao, China, 30 May–3 June 2011; Springer: Berlin, Germany, 2011; Volume 6639, pp. 11–46. [Google Scholar]
- Balfanz, D.; Durfee, G.; Shankar, N.; Smetters, D.K.; Staddon, J.; Wong, H. Secret Handshakes from Pairing-Based Key Agreements. In Proceedings of the 2003 IEEE Symposium on Security and Privacy (S & P 2003), Berkeley, CA, USA, 11–14 May 2003; pp. 180–196. [Google Scholar]
- Sorniotti, A.; Molva, R. A provably secure secret handshake with dynamic controlled matching. Comput. Secur. 2010, 29, 619–627. [Google Scholar] [CrossRef]
- Chen, W.Y.; Wang, J.W. Nested image steganography scheme using QR-barcode technique. Opt. Eng. 2009, 48, 057004. [Google Scholar]
- Chung, C.H.; Chen, W.Y.; Tu, C.M. Image hidden technique using QR-barcode. In Proceedings of the Fifth IEEE IIH-MSP’09 International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Kyoto, Japan, 12–14 September 2009; pp. 522–525. [Google Scholar]
- Wu, W.C.; Lin, Z.W.; Wong, W.T. Application of QR-Code Steganography Using Data Embedding Technique. In Information Technology Convergence; Springer: Berlin, Germany, 2013; pp. 597–605. [Google Scholar]
- Lin, P.Y.; Chen, Y.H.; Lu, E.J.L.; Chen, P.J. Secret Hiding Mechanism Using QR Barcode. In Proceedings of the 2013 IEEE International Conference on Signal-Image Technology & Internet-Based Systems (SITIS), Kyoto, Japan, 2–5 December 2013; pp. 22–25. [Google Scholar]
- Bui, T.V.; Vu, N.K.; Nguyen, T.T.; Echizen, I.; Nguyen, T.D. Robust Message Hiding for QR Code. In Proceedings of the 2014 IEEE Tenth International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), Kitakyushu, Japan, 27–29 August 2014; pp. 520–523. [Google Scholar]
- Wan, S.; Lu, Y.; Yan, X.; Wang, Y.; Chang, C. Visual secret sharing scheme for (k, n) threshold based on QR code with multiple decryptions. J. Real Time Image Process. 2018, 14, 25–40. [Google Scholar] [CrossRef]
- Cheng, Y.; Fu, Z.; Yu, B.; Shen, G. A new two-level QR code with visual cryptography scheme. In Multimedia Tools and Applications; Kluwer Academic Publishers: Boston, MA, USA, 2017. [Google Scholar]
- Chow, Y.; Susilo, W.; Yang, G.; Phillips, J.G.; Pranata, I.; Barmawi, A.M. Exploiting the Error Correction Mechanism in QR Codes for Secret Sharing. In Part I, Lecture Notes in Computer Science, Proceedings of the 21st Australasian Conference Information Security and Privacy (ACISP), Melbourne, Australia, 4–6 July 2016; Liu, J.K., Steinfeld, R., Eds.; Springer: Berlin, Germany, 2016; Volume 9722, pp. 409–425. [Google Scholar]
- Lin, P. Distributed Secret Sharing Approach With Cheater Prevention Based on QR Code. IEEE Trans. Ind. Inform. 2016, 12, 384–392. [Google Scholar] [CrossRef]
- Chow, Y.; Susilo, W.; Baek, J. Covert QR Codes: How to Hide in the Crowd. In Lecture Notes in Computer Science, Proceedings of the 13th International Conference Information Security Practice and Experience (ISPEC), Melbourne, Australia, 13–15 December 2017; Liu, J.K., Samarati, P., Eds.; Springer: Berlin, Germany, 2017; Volume 10701, pp. 678–693. [Google Scholar]
- Blakley, G. Safeguarding cryptographic keys. In Proceedings of the 1979 AFIPS National Computer Conference, New York, NY, USA, 4–7 June 1979; pp. 313–317. [Google Scholar]
- Shamir, A. How to Share a Secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Dawson, E.; Donovan, D. The breadth of Shamir’s secret-sharing scheme. Comput. Secur. 1994, 13, 69–78. [Google Scholar] [CrossRef]
- Naor, M.; Shamir, A. Visual Cryptography. In Eurocrypt; Santis, A.D., Ed.; Lecture Notes in Computer Science; Springer: New York, NY, USA, 1994; Volume 950, pp. 1–12. [Google Scholar]
- Ateniese, G.; Blundo, C.; De Santis, A.; Stinson, D.R. Extended capabilities for visual cryptography. Theor. Comput. Sci. 2001, 250, 143–161. [Google Scholar] [CrossRef]
- Wang, D.; Yi, F.; Li, X. On general construction for extended visual cryptography schemes. Pattern Recognit. 2009, 42, 3071–3082. [Google Scholar] [CrossRef]
- International Organization for Standardization. ISO/IEC 18004:2006—Information Technology—Automatic Identification and Data Capture Techniques—QR Code 2005 Bar Code Symbology Specification; International Organization for Standardization: Geneva, Switzerland, 2006. [Google Scholar]
- Weir, J.; Yan, W. Authenticating Visual Cryptography Shares Using 2D Barcodes. In Lecture Notes in Computer Science, Proceedings of the 10th IWDW 2011 International Workshop, Atlantic, NY, USA, 23–26 October 2011; Springer: Berlin, Germany, 2011; Volume 7128, pp. 196–210. [Google Scholar]
- Falkner, S.; Kieseberg, P.; Simos, D.; Traxler, C.; Weippl, E. E-voting Authentication with QR-codes. In Human Aspects of Information Security, Privacy, and Trust; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8533, pp. 149–159. [Google Scholar]
- Chow, Y.; Susilo, W.; Tonien, J.; Zong, W. A QR Code Watermarking Approach Based on the DWT-DCT Technique. In Part II, Lecture Notes in Computer Science, Proceedings of the 22nd Australasian Conference Information Security and Privacy (ACISP), Auckland, New Zealand, 3–5 July 2017; Pieprzyk, J., Suriadi, S., Eds.; Springer: Berlin, Germany, 2017; Volume 10343, pp. 314–331. [Google Scholar]
- Feldman, P. A Practical Scheme for Non-interactive Verifiable Secret Sharing. In Proceedings of the 28th Annual Symposium on Foundations of Computer Science, Los Angeles, CA, USA, 27–29 October 1987; pp. 427–437. [Google Scholar]


© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chow, Y.-W.; Susilo, W.; Tonien, J.; Vlahu-Gjorgievska, E.; Yang, G. Cooperative Secret Sharing Using QR Codes and Symmetric Keys. Symmetry 2018, 10, 95. https://doi.org/10.3390/sym10040095
Chow Y-W, Susilo W, Tonien J, Vlahu-Gjorgievska E, Yang G. Cooperative Secret Sharing Using QR Codes and Symmetric Keys. Symmetry. 2018; 10(4):95. https://doi.org/10.3390/sym10040095
Chicago/Turabian StyleChow, Yang-Wai, Willy Susilo, Joseph Tonien, Elena Vlahu-Gjorgievska, and Guomin Yang. 2018. "Cooperative Secret Sharing Using QR Codes and Symmetric Keys" Symmetry 10, no. 4: 95. https://doi.org/10.3390/sym10040095





