Hiding Stealth Optical CDMA Signals in Public BPSK Channels for Optical Wireless Communication
Abstract
1. Introduction
2. The Theories and Principles Background of the Proposed Stealth Communication Approach
2.1. Chromatic Dispersion
2.2. Spectral-Polarization Coding Using Walsh–Hadamard Codes
2.3. Chirped Fiber Bragg Gratings
2.4. Free Space Optical Communication (FSO)
3. The Proposed Optical Steganography System Setup and Simulation Results
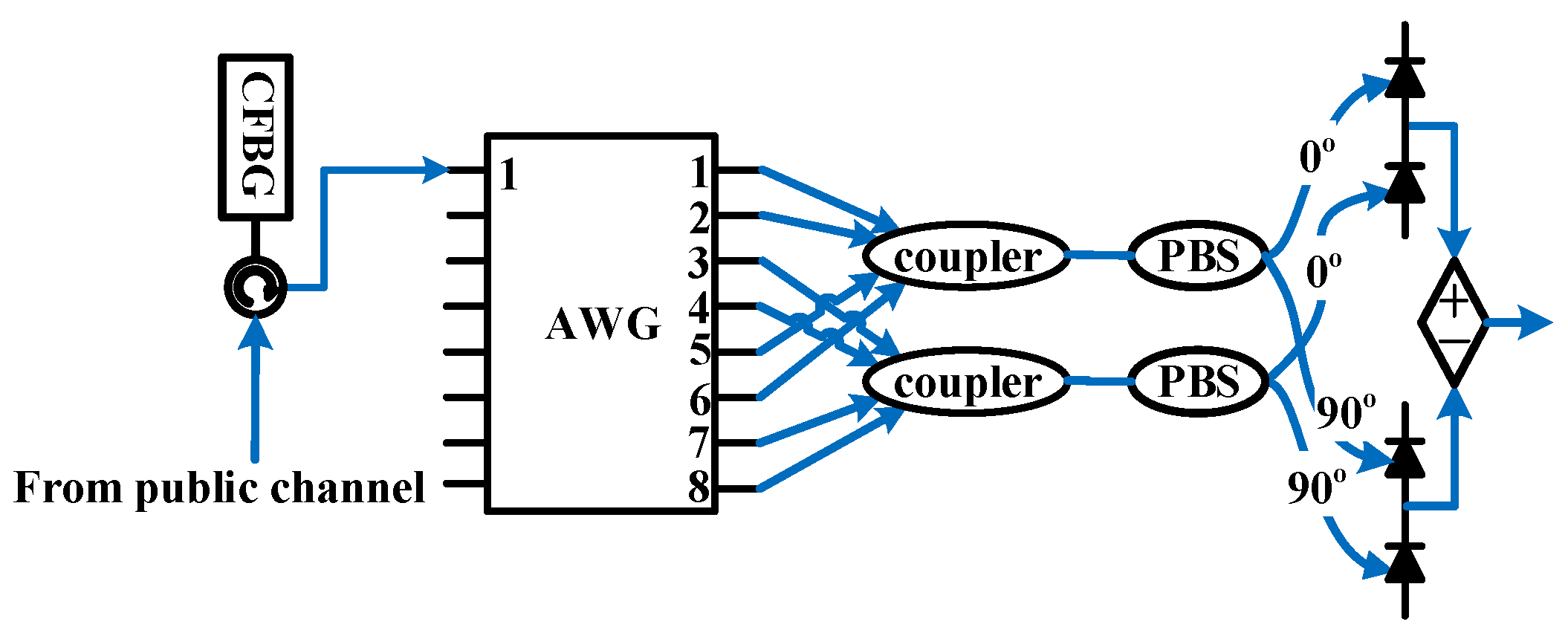
3.1. Structure of Public and Stealth Channels
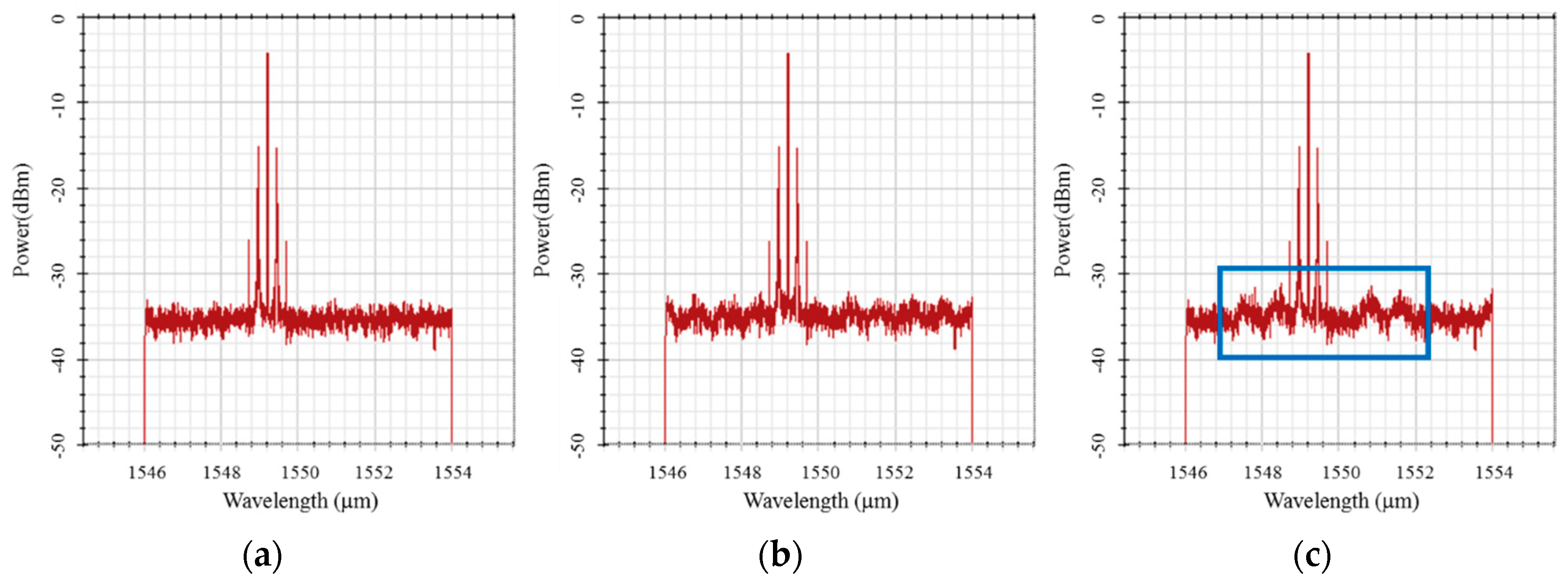
3.2. Interference Cancellation of Stealth and Public Signals
4. System Performance Analysis with Stealth Signal
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Wu, B.; Shastri, B.J.; Mittal, P.; Tait, A.N.; Prucnal, P.R. Optical Signal Processing and Stealth Transmission for Privacy. IEEE J. Sel. Top. Signal Process. 2015, 9, 1185–1194. [Google Scholar] [CrossRef]
- Zeng, G. Quantum Private Communication, 2010 ed.; Springer: New York City, NY, USA, 2010. [Google Scholar]
- Fok, M.P.; Prucnal, P.R. All-optical encryption for optical network with interleaved waveband switching modulation. In Proceedings of the Conference on Optical Fiber Communication 2009, San Diego, CA, USA, 22–26 March 2009. [Google Scholar]
- Zhen, F.; PU, T.; Wei, Z.H.; Fang, T.; Chen, Y.F.; Zheng, J.L. Optical steganographic transmission of spectral-phase-encoded OCDMA signal over a public DPSK channel. In Proceedings of the 22nd Wireless and Optical Communication Conference 2013, Chongqing, China, 16–18 May 2013. [Google Scholar]
- Liang, Y.; Poor, H.V.; Shamai, S. Information theoretic security. Found. Trends Commun. Inf. Theory 2008, 5, 355–580. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J. Physical-Layer Security. From Information Theory to Security Engineering, 1st ed.; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Jamil, T. Steganography: The art of hiding information in plain sight. IEEE Potentials 1999, 18, 10–12. [Google Scholar] [CrossRef]
- Ren, K.; Su, H.; Wang, Q. Secret key generation exploiting channel characteristics in wireless communications. IEEE Wirel. Commun. 2011, 18, 6–12. [Google Scholar] [CrossRef]
- Khisti, A.; Diggavi, S.N.; Wornell, G.W. Secret-key generation using correlated sources and channels. IEEE Trans. Inf. Theory 2012, 58, 652–670. [Google Scholar] [CrossRef]
- Pasolini, G.; Dardari, D. Secret Information of Wireless Multi-Dimensional Gaussian Channels. IEEE Trans. Wirel. Commun. 2015, 14, 3429–3442. [Google Scholar] [CrossRef]
- Channalli, S.; Jadhav, A. Steganography an Art of Hiding Data. Int. J. Computer Sci. Eng. 2009, 1, 137–141. [Google Scholar] [CrossRef]
- Wu, B.; Narimanov, E. Secure stealth transmission over an existing public fiber-optical network. In Proceedings of the Optical Fiber Communication Conference and the National Fiber Optic Engineers Conference 2006, Anaheim, CA, USA, 5–10 March 2006. [Google Scholar]
- Wu, B.; Narimanov, E. A method for secure communications over a public fiber-optical network. Opt. Express 2006, 14, 3738–3751. [Google Scholar] [CrossRef] [PubMed]
- Kravtsov, K.; Wu, B.; Glesk, I.; Prucnal, P.R.; Narimanov, E. Stealth Transmission over a WDM Network with Detection Based on an All-Optical Thresholder. In Proceedings of the IEEE Lasers and Electro-Optics Society Annual Meeting Conference Proceedings 2007, Lake Buena Vista, FL, USA, 21–25 October 2007. [Google Scholar]
- Wu, B.; Agrawal, A.; Glesk, I.; Narimanov, E.; Etemad, S.; Prucnal, P.R. Steganographic fiber-optic transmission using coherent spectral phase-encoded optical CDMA. In Proceedings of the Conference on Lasers and Electro-Optics 2008, San Jose, CA, USA, 4–9 May 2008. [Google Scholar]
- Wang, Z.; Prucnal, P.R. Optical Steganography Over a Public DPSK Channel with Asynchronous Detection. IEEE Photonics Technol. Lett. 2011, 23, 48–50. [Google Scholar] [CrossRef]
- Wu, B.; Tait, A.N.; Chang, M.P.; Prucnal, P.R. WDM optical steganography based on amplified spontaneous emission noise. Opt. Lett. 2014, 39, 5925–5928. [Google Scholar] [CrossRef] [PubMed]
- Hong, X.; Wang, D.; Xu, L.; He, S. Demonstration of optical steganography transmissionusing temporal phase coded optical signals with spectral notch filtering. Opt. Express 2010, 18, 12415–12420. [Google Scholar] [CrossRef] [PubMed]
- Chen, Y.; Wang, R.; Fang, T.; Pu, T.; Xiang, P.; Zhu, H.; Zhang, J. Stealth transmission of temporal phase en/decoded polarization modulated code-shift-keying optical code division multiple access signal over synchronous digital hierarchy network with asynchronous detection. Opt. Eng. 2014, 3, 066103. [Google Scholar] [CrossRef]
- Zhu, H.; Wang, R.; Pu, T.; Chen, Y.; Fang, T.; Zheng, J.; Su, G. Complementary coding optical stealth transmission based on amplified spontaneous emission light source. Opt. Express 2014, 22, 28346–28352. [Google Scholar] [CrossRef] [PubMed]
- Zhu, H.; Wang, R.; Pu, T.; Fang, T.; Xiang, P.; Zheng, J.; Wu, W. Optical steganography of code-shift-keying OCDMA signal based on incoherent light source. IEEE Photonics J. 2015, 7, 6801607. [Google Scholar] [CrossRef]
- Tang, Y.; Li, X.; Gao, T.; Xue, C.; Guo, B.; Yin, S.; Huang, S. Joint routing and wavelength allocation algorithm for stealth and ordinary services in optical transport networks. In Proceedings of the 2017 16th International Conference on Optical Communications and Networks (ICOCN), Wuzhen, China, 7–10 August 2017. [Google Scholar]
- Agrawal, G.P. Fiber-Optic Communications Systems, 3th ed.; Wiley, John & Sons: New York, NY, USA, 2002; pp. 38–42. [Google Scholar]
- Huang, J.F.; Yang, C.C.; Tseng, S.P. Complementary Walsh–Hadamard coded optical CDMA coder/decoders structured over arrayed-waveguide grating routers. Opt. Commun. 2004, 229, 241–248. [Google Scholar] [CrossRef]
- Yen, C.T.; Cheng, H.C.; Chang, Y.T.; Chen, W.B. Performance Analysis of Dual Unipolar/Bipolar Spectral Code in Optical CDMA Systems. J. Appl. Res. Technol. 2013, 11, 235–241. [Google Scholar] [CrossRef]
- Wang, C.; Yao, J. Fiber Bragg gratings for microwave photonics subsystems. Opt. Express 2013, 21, 22868–22884. [Google Scholar] [CrossRef]
- Fok, M.P.; Prucnal, P.R. Optical Steganography Using Chirped Fiber Bragg Grating. In Proceedings of the Optical Fiber Communication Conference and National Fiber Optic Engineers Conference 2009, San Diego, CA, USA, 22–26 March 2009. [Google Scholar]
- Malik, A.; Singh, P. Free Space Optics: Current Applications and Future Challenges. Int. J. Optics 2015, 2015, 1–8. [Google Scholar] [CrossRef]
- Sahbudin, R.K.Z.; Kamarulzaman, M.; Hitam, S.; Mokhtar, M.; Anas, S.B.A. Performance of SAC OCDMA-FSO communication systems. Optik 2013, 124, 2868–2870. [Google Scholar] [CrossRef]















| B: noise-equivalent electrical bandwidth of the receiver. | 0.5 GHz |
| Kb: Boltzmann’s constant | 1.38 × 10−23 J/K |
| Tn: absolute receiver noise temperature | 300 K |
| RL: receiver load resistor. | 1030 |
| Δv:optical source bandwidth | 1 THz |
| R:responsibility of the PD | 0.8 A/W |
| α:public noise-suppression factor | 0.01 |
| L: range | 1 km |
| Ω: attenuation | 3 dB/km (clear sky); 8 dB/km (heavy rain) [29] |
| Dt: transmitter aperture diameter | 4 cm |
| Dr: receiver aperture diameter | 8 cm |
| θ: beam divergence | 1 mrad |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yen, C.-T.; Huang, J.-F.; Zhang, W.-Z. Hiding Stealth Optical CDMA Signals in Public BPSK Channels for Optical Wireless Communication. Appl. Sci. 2018, 8, 1731. https://doi.org/10.3390/app8101731
Yen C-T, Huang J-F, Zhang W-Z. Hiding Stealth Optical CDMA Signals in Public BPSK Channels for Optical Wireless Communication. Applied Sciences. 2018; 8(10):1731. https://doi.org/10.3390/app8101731
Chicago/Turabian StyleYen, Chih-Ta, Jen-Fa Huang, and Wen-Zong Zhang. 2018. "Hiding Stealth Optical CDMA Signals in Public BPSK Channels for Optical Wireless Communication" Applied Sciences 8, no. 10: 1731. https://doi.org/10.3390/app8101731
APA StyleYen, C.-T., Huang, J.-F., & Zhang, W.-Z. (2018). Hiding Stealth Optical CDMA Signals in Public BPSK Channels for Optical Wireless Communication. Applied Sciences, 8(10), 1731. https://doi.org/10.3390/app8101731




