Formation Control Algorithm of Multi-UAV-Based Network Infrastructure
Abstract
:1. Introduction
- Mobility. UAV becomes one of the most versatile devices cooperating with various actuators such as camera [3,4], mechanic arms [5], and even weapons [6]. This trend is originated from the numerous studies in the network of the embedded computing board [7] and the UAV control research domain. While the previous infrastructures statically install a number of the base stations or APs on the ground, the UAVs can act as an AP and instantly deployed at the aerial space to provide the network to the ground. Providing network service by the multiple UAVs is a promising form of the Delay-Tolerant Network (DTN) concept described in RFC 4838 [8]. UAVs and their ad hoc network can act as a bundle layer, and provide functionality of the gateway to deliver the packets on the disrupted environments, such as a disaster area [9], wireless sensor networks [10] or highly congested traffic regions.
- Scalability. The fact that the UAVs are connected by an ad hoc network suggests the high flexibility of the network coverage. While the existing base stations or terrestrial APs should be plugged by wires that guarantee the connection to the backbone network, the multi-UAV-based network infrastructure can connect a new UAV so as to enlarge the service area of the access network. Also, with the possibility that the pre-installed network infrastructure could be act as a GCS, UAVs can be sparsely deployed in large area while augmenting the network-providing service.
- Wireless medium extensibility. Due to the immobility of the existing APs and base stations, the majority of the mobile devices share the wireless medium nearby the ground. Although Wireless LAN (WLAN) and cellular network use wired connection except one-hop wireless transmission, increment of the network traffic in a single AP or base station causes drastic decrement of the network throughput of the devices. Since UAVs are flying on the air, the wireless medium of the UAVs cannot be interfered by the channel of the existing networks. By extending the available wireless medium via multiple UAVs, the infrastructure has the potential to enhance the overall network throughput.
- We designed a network analysis model of the multi-UAV-based network infrastructure. During the derivation of the equations, we suggested a generic mathematical form of the multiple access behavior on the wireless access network. We proved that the generic form fits to the simulated behavior of the wireless access network, and applied the analysis results to the design of the algorithm.
- We proposed a multi-UAV control algorithm for the multi-UAV-based network infrastructure. The algorithm continuously transforms the formation of a fleet of UAV, while optimizing the network throughput of the infrastructure. Also, we proved that the result of the algorithm is a Nash equilibrium.
- We implemented a design of the multi-UAV-based network infrastructure, using ns-3. With the simulation tool, we evaluated our algorithm and proved that the algorithm outperforms the regular, static formation of the UAVs.
2. Related Work
3. Multi-UAV-Based Network Infrastructure Analysis
3.1. Assumptions and Notations
3.2. Wireless Access Network
3.3. Ad Hoc Network
4. Formation Control Algorithm
- All UAVs should maintain the ad hoc connectivity between each other.
- Congestions on the access networks and the ad hoc network should be reduced.
- The infrastructure should connect the mobile devices as many as possible.
- UAVs should not be redundantly deployed; Formation should use minimal UAVs to maximize the network performance.
- Formation should be changed in response to the change of M.
- The position of the gateway,
- The position of the UAV,
- The positions of the nearby UAVs,
- The positions of the next hop UAVs,
- The number of the connected devices of the UAV, n
- The numbers of the connected devices of the nearby UAVs
4.1. Ad Hoc Connectivity Force
4.2. Neighbor Distribution Force
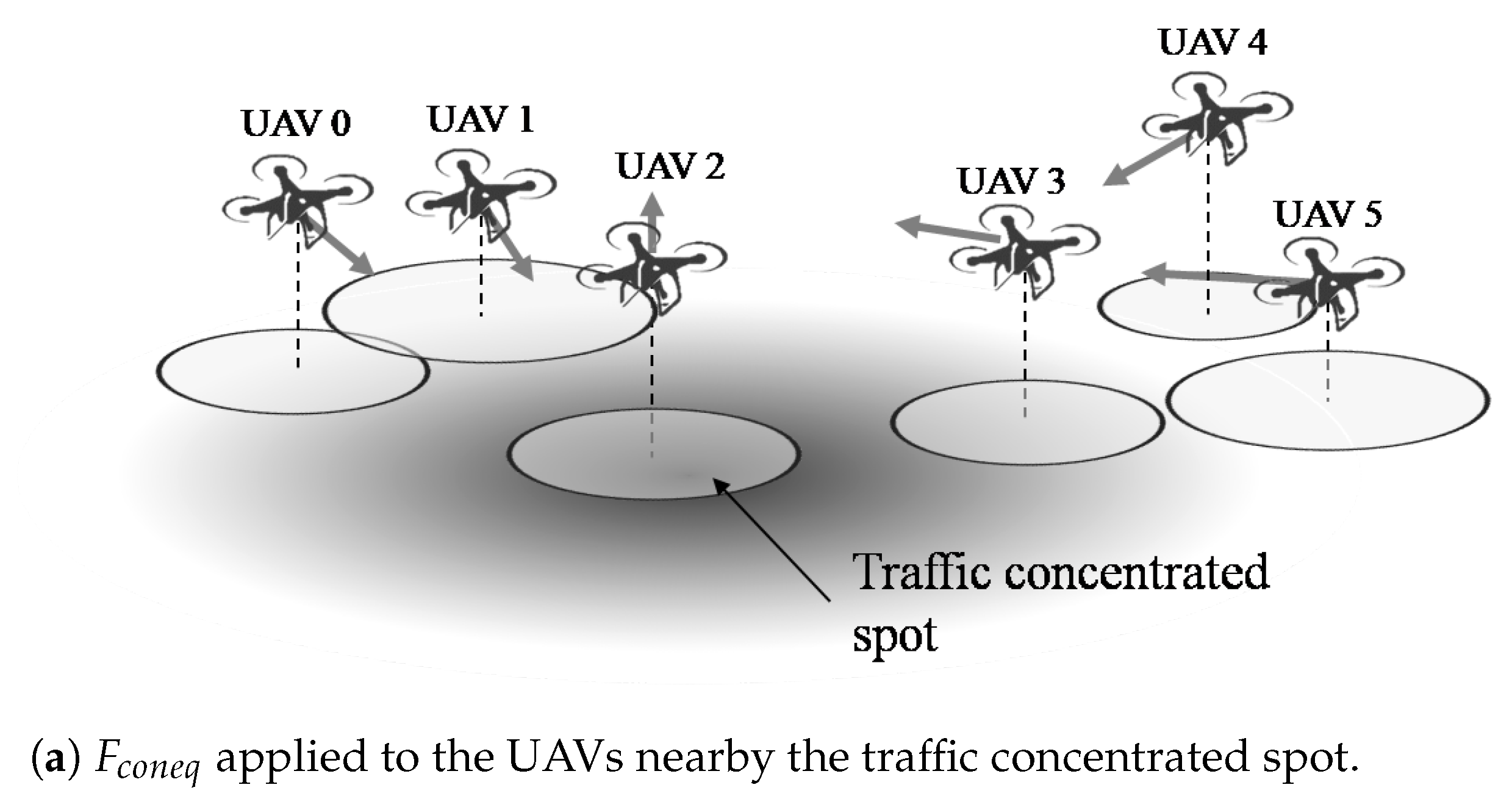
4.3. Congestion Equalization Force
4.4. Feedback-Based Control
| Algorithm 1 Formation control algorithm |
|
4.5. Algorithm Analysis
- Increment of the leads to the decrement of the except the case of the redundant R, which is already reflected by in Equation (12).
- Bringing already connected devices from other UAVs leads to the decrement of the of i and the redundant R of the other UAVs, except the case of the congestion equalizing addressed in Section 4.3, which is already reflected by .
- Yielding already connected devices to other UAVs leads to the redundant R of i and the increment of the of the other UAVs, except the case of the congestion equalizing addressed in Section 4.3, which is already reflected by .
5. System Evaluation
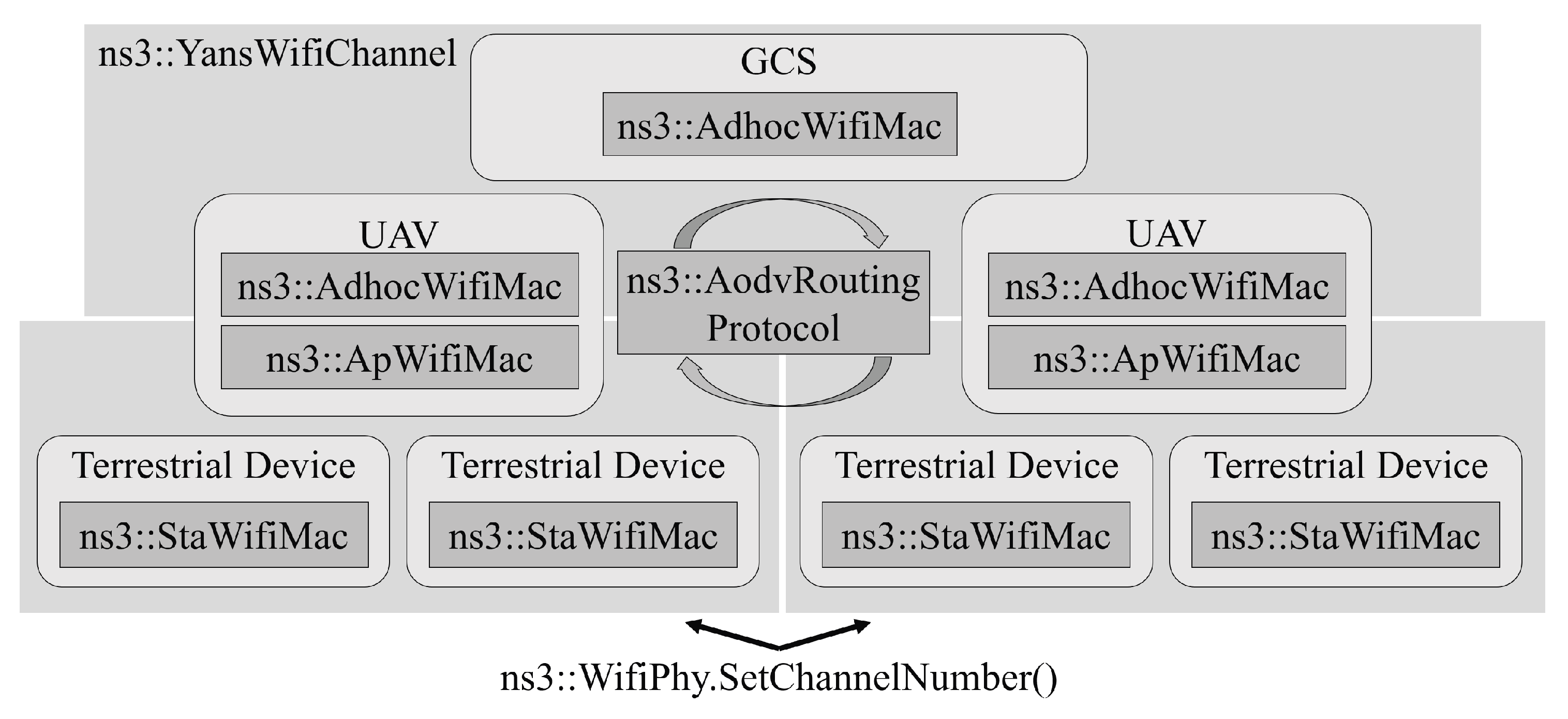
5.1. PHY and MAC Device Installation
5.2. Network and Transport Protocol
5.3. Application Scenario
5.4. Model Verification
5.5. Network Performance Simulation
6. Conclusions
- Network protocol. Formation algorithm equalizes the congestion by moving the UAVs, which could possibly incur handover between the APs more frequently. Handover procedures might decrease the throughput of the infrastructure, so the protocol that supports fast recovery from the connection change is needed. Also, we observed that the IPv6 Routing Protocol for low-power lossy networks (RPL) [40] is a promising routing scheme to adapt to the multi-UAV-based network infrastructure. The network model utilizing RPL in the network infrastructure should be analyzed and the pros and cons should be addressed.
- Terrain. This paper assumes that the ground is flat. Although the altitudes of the UAVs are sufficiently high to ignore some elevation of the terrain, some environments with high elevations or buildings could affect the formation of the UAVs. To manage the WLAN network traffic, z axis change could not be enough to approach optimal formation, which needs to improve our formation algorithm.
- Evaluation. We evaluate our formation control algorithm by ns-3. Even though ns-3 is one of the well-known network simulation tool and continually revised for improvements, it could suffer from precision issues due to lack of real-world projection. To evaluate our formation control algorithm on a more practical testbed, a dataset extracted from real-world environments [41] could be desirable.
Author Contributions
Funding
Conflicts of Interest
References
- Chung, A.Y.; Jung, J.; Kim, K.; Lee, H.K.; Lee, J.; Lee, S.K.; Yoo, S.; Kim, H. Poster: Swarming Drones Can Connect You to the Network. In Proceedings of the 13th Annual International Conference on Mobile Systems, Applications, and Services, Florence, Italy, 18–22 May 2015; ACM: New York, NY, USA; pp. 477–477. [Google Scholar]
- Yoo, S.; Kim, K.; Jung, J.; Chung, A.Y.; Lee, J.; Lee, S.K.; Lee, H.K.; Kim, H. Poster: A multi-drone platform for empowering drones’ teamwork. In Proceedings of the 21st Annual International Conference on Mobile Computing and Networking, Paris, France, 7–11 September 2015; ACM: New York, NY, USA; pp. 275–277. [Google Scholar]
- Lee, J.N.; Kwak, K.C. A trends analysis of image processing in unmanned aerial vehicle. Int. J. Comput. Inform. Sci. Eng. 2014, 8, 2–5. [Google Scholar]
- Jung, J.; Yoo, S.; La, W.; Lee, D.; Bae, M.; Kim, H. AVSS: Airborne Video Surveillance System. Sensors 2018, 18, 1939. [Google Scholar] [CrossRef] [PubMed]
- Lippiello, V.; Ruggiero, F. Exploiting redundancy in Cartesian impedance control of UAVs equipped with a robotic arm. In Proceedings of the 2012 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Vilamoura, Portugal, 7–12 October 2012; pp. 3768–3773. [Google Scholar]
- Gregory, D. From a view to a kill: Drones and late modern war. Theor. Cult. Soc. 2011, 28, 188–215. [Google Scholar] [CrossRef]
- Eshwarappa Dandur, V.; Weng, N. Networked Embedded System Security: Technologies, Analysis and Implementation. Recent Adv. Commun. Netw. Technol. 2016, 5, 90–107. [Google Scholar] [CrossRef]
- Cerf, V.; Burleigh, S.; Hooke, A.; Torgerson, L.; Durst, R.; Scott, K.; Fall, K.; Weiss, H. Rfc 4838: Delaytolerant Network Architecture; The Internet Research Task Force (IRTF), DTN Research Group; RFC Editor: Marina del Rey, CA, USA, 2007. [Google Scholar]
- Mekikis, P.V.; Antonopoulos, A.; Kartsakli, E.; Alonso, L.; Verikoukis, C. Communication recovery with emergency aerial networks. IEEE Trans. Consum. Electron. 2017, 63, 291–299. [Google Scholar] [CrossRef] [Green Version]
- Bae, M.; Yoo, S.; Jung, J.; Park, S.; Kim, K.; Lee, J.Y.; Kim, H. Devising Mobile Sensing and Actuation Infrastructure with Drones. Sensors 2018, 18, 624. [Google Scholar] [CrossRef] [PubMed]
- Chatzigiannakis, I.; Nikoletseas, S.; Spirakis, P. Distributed communication algorithms for ad hoc mobile networks. J. Parallel Distrib. Comput. 2003, 63, 58–74. [Google Scholar] [CrossRef]
- Chatzigiannakis, I.; Kinalis, A.; Nikoletseas, S. Efficient data propagation strategies in wireless sensor networks using a single mobile sink. Comput. Commun. 2008, 31, 896–914. [Google Scholar] [CrossRef]
- Lee, J.; Kim, K.; Yoo, S.; Chung, A.Y.; Lee, J.Y.; Park, S.J.; Kim, H. Constructing a reliable and fast recoverable network for drones. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- Inalhan, G.; Stipanovic, D.M.; Tomlin, C.J. Decentralized optimization, with application to multiple aircraft coordination. In Proceedings of the 41st IEEE Conference on Decision and Control, Las Vegas, NV, USA, 10–13 December 2002; pp. 1147–1155. [Google Scholar]
- Olfati-Saber, R.; Murray, R.M. Graph rigidity and distributed formation stabilization of multi-vehicle systems. In Proceedings of the 41st IEEE Conference on Decision and Control, Las Vegas, NV, USA, 10–13 December 2002; Volume 3, pp. 2965–2971. [Google Scholar]
- Michael, N.; Mellinger, D.; Lindsey, Q.; Kumar, V. The grasp multiple micro-uav testbed. IEEE Robot. Automat. Mag. 2010, 17, 56–65. [Google Scholar] [CrossRef]
- Cao, Y.; Yu, W.; Ren, W.; Chen, G. An overview of recent progress in the study of distributed multi-agent coordination. IEEE Trans. Ind. Inf. 2013, 9, 427–438. [Google Scholar] [CrossRef]
- Calvo, J.A.L.; Alirezaei, G.; Mathar, R. Wireless powering of drone-based MANETs for disaster zones. In Proceedings of the 2017 IEEE International Conference on Wireless for Space and Extreme Environments (WiSEE), Montreal, QC, Canada, 10–12 October 2017; pp. 98–103. [Google Scholar]
- Bor-Yaliniz, I.; Szyszkowicz, S.S.; Yanikomeroglu, H. Environment-aware drone-base-station placements in modern metropolitans. IEEE Wirel. Commun. Lett. 2018, 7, 372–375. [Google Scholar] [CrossRef]
- Mozaffari, M.; Saad, W.; Bennis, M.; Debbah, M. Unmanned aerial vehicle with underlaid device-to-device communications: Performance and tradeoffs. IEEE Trans. Wirel. Commun. 2016, 15, 3949–3963. [Google Scholar] [CrossRef]
- Zhang, S.; Zeng, Y.; Zhang, R. Cellular-enabled UAV communication: Trajectory optimization under connectivity constraint. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Kershner, R. The number of circles covering a set. Am. J. Math. 1939, 61, 665–671. [Google Scholar] [CrossRef]
- Mozaffari, M.; Saad, W.; Bennis, M.; Debbah, M. Efficient Deployment of Multiple Unmanned Aerial Vehicles for Optimal Wireless Coverage. IEEE Commun. Lett. 2016, 20, 1647–1650. [Google Scholar] [CrossRef]
- Gáspár, Z.; Tarnai, T. Upper bound of density for packing of equal circles in special domains in the plane. Period. Polytech. Civ. Eng. 2000, 44, 13–32. [Google Scholar]
- Challita, U.; Saad, W. Network formation in the sky: Unmanned aerial vehicles for multi-hop wireless backhauling. arXiv, 2017; arXiv:1707.09132. [Google Scholar]
- Cervello, G.G.; Choi, S.; Mangold, S.; Soomro, A.A. Dynamic Channel Selection Scheme for IEEE 802.11 WLANs. US Patent 6,985,465, 10 January 2006. [Google Scholar]
- Kim, H.; Lee, W.; Bae, M.; Kim, H. Wi-Fi seeker: A link and load aware AP selection algorithm. IEEE Trans. Mob. Comput. 2017, 2366–2378. [Google Scholar] [CrossRef]
- Rossi, G.V.; Leung, K.K. Optimised Csma Protocol to Support Efficient Clustering for Vehicular Internetworking; IEEE WCNC: San Francisco, CA, USA, 2017. [Google Scholar]
- Darus, M.Y.; Kamarudin, A.; Awang, N.; Ali, F.H.M. Analysis performance on contention-based MAC protocols in MANETs. In Proceedings of the 2014 Fourth World Congress on Information and Communication Technologies (WICT), Bandar Hilir, Malaysia, 8–11 December 2014; pp. 303–307. [Google Scholar]
- Li, B.; Qu, Q.; Yan, Z.; Yang, M. Survey on OFDMA based MAC protocols for the next generation WLAN. In Proceedings of the 2015 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), New Orleans, LA, USA, 9–12 March 2015; pp. 131–135. [Google Scholar]
- Hu, H.; Hu, X.; Xiao, J.; Liu, X. CDMA-based MAC protocol for multi-hop wireless sensor networks. In Proceedings of the 2017 2nd IEEE International Conference on Intelligent Transportation Engineering (ICITE), Singapore, 1–3 September 2017; pp. 266–271. [Google Scholar]
- Bianchi, G. Performance analysis of the IEEE 802.11 distributed coordination function. IEEE J. Sel. Areas Commun. 2000, 18, 535–547. [Google Scholar] [CrossRef] [Green Version]
- Kim, H.; Hou, J.C. Improving protocol capacity with model-based frame scheduling in IEEE 802.11-operated WLANs. In Proceedings of the 9th Annual International Conference on Mobile Computing and Networking, San Diego, CA, USA, 14–19 September 2003; ACM: New York, NY, USA; pp. 190–204. [Google Scholar]
- Alonso, L.; Ferrus, R.; Agusti, R. WLAN throughput improvement via distributed queuing MAC. IEEE Commun. Lett. 2005, 9, 310–312. [Google Scholar] [CrossRef] [Green Version]
- Pang, Q.; Leung, V.C.; Liew, S.C. Improvement of WLAN contention resolution by loss differentiation. IEEE Trans. Wirel. Commun. 2006, 5, 3605–3615. [Google Scholar] [CrossRef]
- Reynolds, C.W. Flocks, herds and schools: A distributed behavioral model. In ACM SIGGRAPH Computer Graphics; ACM: New York, NY, USA, 1987; Volume 21, pp. 25–34. [Google Scholar]
- Gibbons, R. A Primer in Game Theory; Harvester Wheatsheaf: London, UK, 1992. [Google Scholar]
- Perkins, C.; Belding-Royer, E.; Das, S. Ad Hoc on-Demand Distance Vector (AODV) Routing; Technical Report; RFC Editor: Marina del Rey, CA, USA, 2003. [Google Scholar]
- Wang, W.; Shen, G. Energy efficiency of heterogeneous cellular network. In Proceedings of the 2010 IEEE 72nd Vehicular Technology Conference Fall (VTC 2010-Fall), Ottawa, ON, Canada, 6–9 September 2010; pp. 1–5. [Google Scholar]
- Winter, T.; Thubert, P.; Brandt, A.; Hui, J.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, J.P.; Alexander, R. RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks; Technical Report; RFC Editor: Marina del Rey, CA, USA, 2012. [Google Scholar]
- Adjih, C.; Baccelli, E.; Fleury, E.; Harter, G.; Mitton, N.; Noel, T.; Pissard-Gibollet, R.; Saint-Marcel, F.; Schreiner, G.; Vandaele, J.; et al. FIT IoT-LAB: A large scale open experimental IoT testbed. In Proceedings of the 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, 14–16 December 2015; pp. 459–464. [Google Scholar]








© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Park, S.; Kim, K.; Kim, H.; Kim, H. Formation Control Algorithm of Multi-UAV-Based Network Infrastructure. Appl. Sci. 2018, 8, 1740. https://doi.org/10.3390/app8101740
Park S, Kim K, Kim H, Kim H. Formation Control Algorithm of Multi-UAV-Based Network Infrastructure. Applied Sciences. 2018; 8(10):1740. https://doi.org/10.3390/app8101740
Chicago/Turabian StylePark, Seongjoon, Kangho Kim, Hyunsoon Kim, and Hwangnam Kim. 2018. "Formation Control Algorithm of Multi-UAV-Based Network Infrastructure" Applied Sciences 8, no. 10: 1740. https://doi.org/10.3390/app8101740




