Abstract
This paper investigates the problem of the optimal arrangement for both unmanned aerial vehicles’ (UAVs’) caching contents and service locations in UAV-assisted networks based on the context awareness, which considers the influence between users and environment. In the existing work, users within the coverage of UAVs are considered to be served perfectly, which ignores the communication probability caused by line-of-sight (LOS) and non-line-of-sight (NLOS) links. However, the links are related to the deployment of UAVs. Moreover, the transmission overhead should be taken into account. To balance the tradeoff between these two factors, we design the ratio of users’ probability and transmission overhead as the performance measure mechanism to evaluate the performance of UAV-assisted networks. Then, we formulate the objective for maximizing the performance of UAV-assisted networks as a UAV-assisted caching game. It is proved that the game is an exact potential game with the performance of UAV-assisted networks serving as the potential function. Next, we propose a log-linear caching algorithm (LCA) to achieve the Nash equilibrium (NE). Finally, related simulation results reflect the great performance of the proposed algorithm.
1. Introduction
During the past decades, unmanned aerial vehicles (UAVs) have been popular in military applications due to their characteristics of high mobility and low cost [1,2,3,4,5], e.g., reasonable use of UAVs can reduce the amount of casualties of front-line soldiers. With the development of the manufacturing process and the reduction of manufacturing costs, UAVs have realized the transition from the military to the civilian domain. Recently UAVs have been widely utilized in civilian applications, including weather monitoring [6,7], forest fire monitoring [8,9], and first aid search and rescue [10,11], which have benefited the public. Specifically, when UAVs are combined with wireless communication networks, users will experience better communication services due to the fact that traditional cellular networks have several of the following shortcomings [12]: (i) the potential damage of communication facilities caused by natural disasters; (ii) an increasingly unbearable communication burden resulting from growing smart devices and communication demands. Fortunately, it happens that the unique characteristics of UAVs can make up for these deficiencies. The characteristics of high mobility and low cost ensure that UAVs can quickly fly to the disaster area to provide services. Moreover, cache-enabled UAVs may increase the degree of file reuse and decrease the file caching cost [13]. Thus, especially in this era of data explosion, the combination of UAVs and the cache is considered to be a promising technology for dealing with the relevant challenges [13,14].
Recently, progress in related research has shown the validity and reliability of the aforementioned technology. In our existing work [15], the problem of selecting caching nodes was studied and a selection algorithm was proposed. However, it ignored the potential cooperation among caching nodes. The authors studied the problem of hybrid caching in device-to-device (D2D) networks in Reference [16], which considered the cooperation but ignored the dynamics among nodes. In Reference [17], a secure transmission scheme based on interference alignment was proposed, which made the caching UAVs provide services similar tothe small base stations (SBSs). Idle SBSs replaced by UAVs would disrupt eavesdropping. However, the caching content sharing of UAVs is not considered. Moreover, the authors studied the problem of resource allocation in a cloud network with cache-enabled UAVs in Reference [18], where the users’ content request distribution can be predicted based on the proposed algorithm. However, the research mentioned above, to a great extent, only focused on the resource allocation and optimization of caching contents but ignored the optimization of UAVs’ service locations. This problem is rarely considered in existing studies to the best of our knowledge. Although, the authors took the change of UAVs’ location into account in Reference [14], the potential cooperation among UAVs was not considered. In our prior work, we investigated the problem of both caching contents and service locations in UAV-assisted emergency networks by multi-hop in Reference [19]. However, the following shortcomings still exist. We considered the cooperation among UAVs by multi-hop based on the assumption that users within the coverage of UAVs were served perfectly. Nevertheless, in practical scenarios, the influence of propagation groups, line-of-sight (LOS) and non-line-of-sight (NLOS), which may result in users within the coverage of UAVs communicating with UAVs successfully by probability, should be taken into account. Meanwhile, a multi-hop service will result in more delay for ground users. Therefore, it is necessary and significant to improve the shortcomings mentioned above.
In this paper, we consider the joint optimization of UAVs’ caching contents and service locations with the goal of balancing the tradeoff between user’s service probability and transmission overhead. In the proposed scenario, users need to be served in a disaster area when the communication facilities are destroyed. UAVs with caching contents fly to the destination to provide communication services. Considering the cooperation among UAVs, the caching contents of neighbor UAVs can be shared by one hop. Thus, the optimal arrangement of UAVs’ caching contents and service locations are the key points to solve. However, the problem is challenging. Firstly, the transmission overhead may be affected by both UAVs’ caching contents and service locations, i.e., the source of the request file and the neighbor UAV sets. Secondly, when considering the locations of UAVs, the probability that the users can communicate with UAVs successfully will be influenced by the propagation groups, i.e., LOS and NLOS, with corresponding probabilities of occurrence.
Motivated by these observations, we consider both the probability that the users can communicate with UAVs successfully and the transmission overhead that the users use to obtain the requested files. Therefore, we apply the ratio of users’ service probability and transmission overhead as the performance indicators of UAVs’ actions to balance the tradeoff. Meanwhile, we formulate the challenging problem as a UAV caching game applying game theory and prove the existence of the Nash equilibrium (NE). In addition, a log-linear caching algorithm (LCA) can achieve great performance.
The main contributions are as follows:
- We first investigate the problem of joint optimization of UAVs’ caching contents and service locations with the goal of balancing the tradeoff between user’s service probability and transmission overhead under the consideration of the share of neighbor UAVs’ caching contents.
- The problem is modeled as a UAV caching game, which intends to find the optimal solution that maximizes UAVs’ performance indicators, i.e., the ratio of user’s service probability and transmission overhead. In addition, the proposed game is proved to be a potential game with at least one pure-strategy NE. Meanwhile, the optimal solution can be achieved by its optimal NE.
- The log-linear caching algorithm is proposed to achieve the desirable solution in joint caching contents and service locations optimization problem. The simulation results show that the proposed algorithm can converge to a great NE solution and guarantee the great performance of UAV-assisted networks, which demonstrates the algorithm’s validity and effectiveness.
The remainder of this paper is organized as follows. In Section 2, we introduce the system model and formulate the problem. In Section 3, we propose the UAV-assisted caching game and apply the log-linear caching algorithm to achieve the desirable solution. We present the simulation results and give an expansion and discussion in Section 4. Finally, we draw a conclusion in Section 5.
2. System Model and Problem Formulation
In this part, we first model the problem and present related formulations, which reflects the impact of UAVs’ caching contents and service locations. Then, we design the measure mechanism to evaluate the performance. Finally, we formulate the problem with the goal of maximizing the performance of all UAVs. Table 1 presents the key variables used in this paper.

Table 1.
Key variables used in this paper.
2.1. System Model
We consider a UAV-assisted networks with N cache-enabled UAVs, i.e., , and M users, i.e., . Denote the set of system files as , where denotes the number of system files. Suppose that all users request files from f according to a special file popularity distribution, which is as follows [20,21]:
where denotes the probability that the user requests the i-th file, and is . ϑ is the parameter of Zipf distribution.
Meanwhile, we denote user m’s requested files as where is the number of files requested by user m. denotes that user m requestes the i-th file while indicates that user m does not requeste the i-th file.
An illustration of UAV-assisted communication networks is shown in Figure 1. There are three small UAVs, a big central UAV and some users waiting to be served. As depicted in Figure 1, the service process of UAVs consists of four parts: firstly, the small UAVs use some prior information provided by the central UAV and make their own caching contents decisions individually; Secondly, small UAVs fly to the service locations with carried caching contents. Then, UAVs start to serve the users under the assumption that the caching contents can be shared among the reachable neighboring UAVs by one hop. Next, if some users’ demands are still not met, the service UAV will fly to some UAVs with caching contents that the dedicated user wants, to cooperate. Meanwhile, the following file requests of corresponding users will be rejected until the service UAV comes back. Finally, the service UAV will return to the central UAV to get files if other UAVs cannot provide such services.
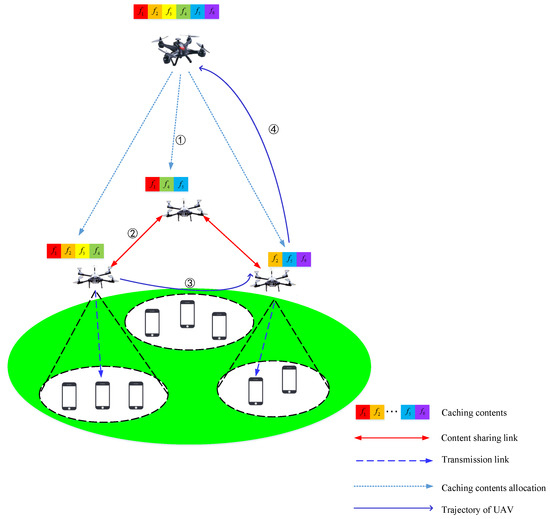
Figure 1.
An illustration of the emergency communications network (1). The small unmanned aerial vehicles (UAVs) obtain the caching contents by the given decision from the central UAV and fly to the destination with cached contents. (2). UAVs cooperate with reachable neighboring UAVs by one hop. (3). UAV will fly to some UAVs with caching contents that the dedicated user wants. (4). UAV will return to the central UAV to get files if other UAVs cannot provide such services.).
Motivated by Reference [22], we denote reachable neighboring UAVs of UAV n by one hop as , i.e.,
where denotes the distance between UAV n and i. represents the communication distance thresholds for UAVs.
2.2. Problem Formulation
Note that the performance of UAVs is affected by its caching contents as well as the service locations, i.e., where to obtain the files requested by users and the successful communication probability from UAVs to their dedicated users through the influence of propagation groups. Therefore, we need to balance the tradeoff between the transmission overhead and successful communication probability. Consider as the action of UAV n. Note that reflects the service location of UAV n, which is actually a set of space coordinates, i.e., . Meanwhile, indicates the caching action of UAV n, where and are the number of caching contents carried by UAV n, which is the cache space of UAVs. We define the transmission overhead by considering both caching contents and service location, as follows:
where is the number of files requested by user m, denotes the probability that user m requests . Denote C(m, k, a) as the transmission overhead that user m obtains fi by the joint action, i.e., , of UAVs under the consideration of different sources of files which is given by:
where and denote the function of the transmission overhead respectively, which is defined as follows:
where and m represent the UAV and its dedicated user, and denote the location of UAV and user m respectively, is the overhead per file per distance, denotes the distance from to m, which is related to and .
where and denote the UAV that caches file k and the central UAV, respectively, , , and are different overheads per file per distance according to different source of files, is the UAV that caches file k, means the set of files that UAV caches.
The explanation of can be classified into four parts. The first expression indicates that UAV caches the file that the users require; the second expression indicates that UAV tends to obtain files from its neighbors; the third expression denotes the fact that UAV tends to obtain files from other small UAVs, which are defined as potential neighbors; the truth that UAV will fly back to the big central UAV to cache missing files is reflected in the last expression. Moreover, it should be noted that the value of each part in indicator function is related to the distance between UAV and the destination for the file requested by users, i.e., and . Note that the third and last expression indicate that UAV will leave the service location. Therefore, and involve the flight overhead per distance.
Although the UAV can obtain the files requested by users, the successful communication probability is still an important factor which may influence the service performance. Suppose that each communication link uses a pre-given channel to transmit data. It can be completed by applying unicast transmission schemes [23] where each UAV serves corresponding users by different channels. Therefore, it means that the communications between UAVs and users will not interfere with each other. Then, for an interference-free scenario, we define the successful communication probability as the probability that the received signal-to-noise ratio (SNR) by the received user is over a predefined communication threshold, which is as follows:
where is the communication threshold, (SNR) is calculated by:
where is the transmitting power of UAV n, is the channel power gain from UAV to user m, is the background noise. Different from terrestrial communication network, the transmission link can be classified into two propagation groups, i.e., LOS and NLOS. Motivated by Reference [24], for LOS and NLOS links are respectively calculated by:
where reflects the distance from UAV to user m, denotes the path loss exponent, denotes an additional attenuation factor caused by the NLOS link, h, i.e., , represents the Nakagami fading. According to Reference [24], both the service location and the elevation angle between the UAV and the user influence the probability of LOS link. Thus, the probability of causing LOS links can be given as follows:
where a and b are the parameters related to the environment, denotes the elevation angle specified as follows:
where is the height of UAV . The probability of causing NLOS link is . Thus, we express the channel power gain as follows:
The good arrangements of UAVs’ caching contents and service locations will achieve an appropriate trade-off between a high successful communication probability and low transmission overhead. Therefore, we design the ratio of users’ successful communication probability and transmission overhead as the performance indicators of UAVs’ actions. We denote the performance function of UAV n as:
where denotes the set of users that UAV n serves, is the transmission overhead of user m to obtain requested files specified in Reference [24], is the successful communication probability from UAV n to user m. Thus, the performance of all UAVs can be measured by:
where denotes the joint strategy profile of all UAVs.
Therefore, the optimization object is to find the optimal strategy profile which can maximize the performance of all UAVs, i.e.,
where the condition reflects the fact that UAVs’ cache space does not exceed the number of system files, is the communication probability threshold, the condition indicates that the solution must ensure users have appropriate communication probability to communicate.
2.3. Summary
Besides the caching contents and service locations, we consider the impact of LOS and NLOS links on the performance of UAV-assisted networks. Meanwhile, the necessary formulations are presented in this part, which indicates that the tradeoff between the transmission overhead and successful communication probability should be balanced.
3. UAV-Assisted Caching Game
As a result of the high computation and complexity of combinatorial problem, the centralized framework is powerless. Therefore, we design a distributed framework with the help of game theory, which makes each UAV take action, respectively. Meanwhile, the proposed game is proved to be an exact potential game. NE points can be reached by the log-linear caching algorithm.
3.1. Game Model
It is well known that game theory is efficient for solving the challenge of resource competition for example the anti-jamming transmission problem [25,26], the opportunistic spectrum access problem [27], the distributed channel-slot selection optimizing problem [28], even the challenging UAV relay selection problem [29], and the ultra-dense small cell network problem [30]. Similarly, we propose a UAV-assisted caching game in this paper from a game-theoretic perspective. The proposed game considers not only the UAVs’ service locations, but also the caching contents. Moreover, UAVs will cooperate with their neighbors and share the caching contents, which reflects cooperation. Therefore, when one UAV selects its action, it will consider the influence that its action has upon its neighbors.
Let denotes the UAV-assisted caching game, where denotes the set of players (UAVs), is the strategy space of UAV n, is the neighbors of UAV n, indicates the utility function of player n (UAV n).
Considering the influence of marginal contribution of UAVs to the system service, we designed the utility function of UAVs as follows:
where indicates the current action of UAV n, is the joint action profile of UAV n’s neighbors, denotes the joint action profile of UAVs except UAV n, reflects the fact that the current UAV n takes no action, is the performance evaluation function of all UAVs, which is the same as Equation (14).
The utility function shows the individual contribution of each UAV to the UAV-assisted network performance, which is influenced by the caching contents and service locations of UAVs. Therefore, when UAVs take proper arrangement of caching contents and service locations, each individual contribution will increase. Therefore, the optimization object of the UAV-assisted caching game is given by:
3.2. Analysis of NE
The NE is the stable solution in game theory. The existence of NE will be analyzed in the part. According to Reference [16], we first give the definitions as follows:
Definition 1 (Nash Equilibrium).
An action profile is a pure stragety NE if and only if no player can improve its utility by deviating unilaterally, i.e.,
Definition 2 (Exact Potential Game).
A game is an exact potential game if and only if a potential function Φ: exists so that for :
Therefore, a game is an exact potential game when the change in individual utility function is the same as the change in the potential function.
According to the definitions [31], the following theorem is given to present the properties of the proposed game.
Theorem 1.
is an exact potential game that has at least one pure strategy NE. The optimal pure strategy NE of is the optimal solution of the proposed optimization problem.
Proof.
Inspired by Reference [32], we firstly denote the potential function as follows:
where is the performance evaluation function of all UAVs, which is the same as Equation (14).
The potential function indicates the performance of all UAVs. When UAV n changes its decision action from to , then the change in utility function of UAV n caused by this unilateral change is given by:
Note that and all indicate the truth that UAV n takes no action in service, which means that this UAV n is broken and can not provide service. Therefore, the performance of UAV-assisted networks is actually the same in these two conditions, i.e.,
From Equation (23), we can draw the conclusion that the change in the utility function is exactly the same as the change in the potential function. Thus, according to the definition, the fact that our proposed game is an exact potential game is proved. Moreover, the potential game has the most important two properties.
- The potential game has one pure strategy NE at least.
- Local or global maxima of potential function constitutes a pure strategy NE.
Therefore, the UAV-assisted caching game has one NE at least. Moreover, the NE is a stable solution to the potential function, which is equal to the performance of all UAVs. It means that the optimal NE can make the performance of UAV-assisted networks largest. Thus, Theorem 1 is proved. □
3.3. Log-Linear Caching Algorithm
After proposing the UAV-assisted caching game, it is desirable to find the NE point mentioned above. Therefore, the log-linear caching algorithm is proposed to optimize the performance of UAV-assisted networks motivated by Reference [16].
Different from greedy algorithms, the proposed algorithm guarantees that each UAV will not always take its best action. The mechanism avoids the dilemma of UAV-assisted networks falling into the local optimum. It will eventually result in a better NE solution by discarding a temporary good action. The detailed running mechanism of the proposed algorithm is as follows: Firstly, related parameters and actions of UAVs are initialized; secondly, one UAV is selected randomly to enter an exploratory stage, i.e., the selected UAV randomly chooses a new action with equal probability; finally, the selected UAV decides whether to explore the new action or to keep the original action according to its updating rules. More details are described in Algorithm 1.
Theorem 2.
With a sufficiently large learning parameter, the log-linear caching algorithm converges to a NE point of the UAV-assisted caching game and maximizes the performance of UAV-assisted networks locally or globally.
Proof.
According to Theorem 4 [33], the unique stationary distribution of any action profile can be determined. On the basis of the methodology provided in Reference [22], it can be proved that when the learning parameter is large enough, the log-linear caching algorithm can asymptotically obtain the maximum of potential function. As is specified in Equation (20), the potential function represents the performance of all UAVs. Therefore, the proposed algorithm can maximize the performance of UAV-assisted networks. The similar proof process has been completed and more details can be read in Reference [33]. Thus, Theorem 2 is proved. □
| Algorithm 1: Log-linear caching algorithm (LCA) |
| 1. Initialization (1) Initialize randomly users’ locations, file popularity and file requests , . Initialize randomly and , satisfying to and . (2) Moreover, set k = 0 as the round count and as the maximum round. 2. Repeat Round k = k + 1 Choose UAV n randomly. Repeat iterations:: (1) Calculate by taking the action . (2) Generate randomly from its strategy space (3) Calculate by taking the action and keep other UAVs’ actions. (4) Update strategy: where , and is the learning parameter. Meanwhile, all other UAVs keep their actions, and . (5) until or , End iterations Output: 3. End rounds |
4. Simulation and Numerical Results and Discussion
In this part, we conduct the simulation with MATLAB software and compare the impact of key parameters, i.e., the number of system files on the performance of UAV-assisted networks. Meanwhile, the simulation results verifies the effectiveness of the proposed model.
4.1. Simulation Scenario
Considering a square region of 200 × 200 m, there are users located randomly waiting to be served. Meanwhile, the communication distance threshold of UAVs is m and the learning parameter of the proposed algorithm is , where k is the number of the current iterations. The different overheads per file per distance are , , , and , respectively. Moreover, the communication threshold is dB. The communication probability threshold is . The transmitting power of UAVs and background noise are w and dbm, respectively. The path loss exponent is . The Nakagami fading is . Inspired by Reference [24], the parameter related to the environment a and b is a = 11.95 and b = 0.136.
4.2. Convergence Behavior
As shown in Figure 2, the performance of UAV-assisted networks finally converges to a stable state. Here we consider that the number of system files is , and there are UAVs available to serve the users, i.e., . Moreover, the cache space of UAVs is . At the end of iteration, the performance of UAV-assisted networks will finally converge. In addition, the final performance is near to the best NE, which is the best one of 1000 independent trials based on the proposed algorithm. The simulation result validates its convergence and the effectiveness of the proposed algorithm.
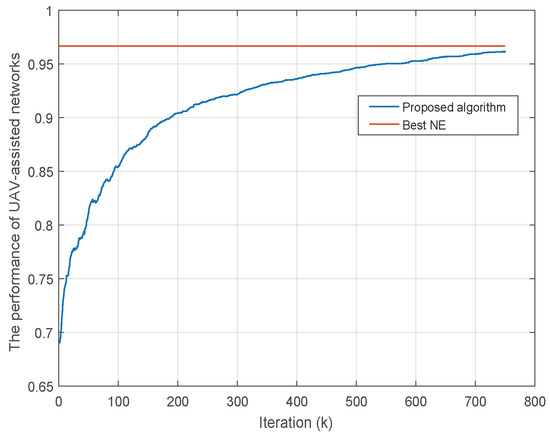
Figure 2.
The convergence of the proposed algorithm (, and ).
4.3. Performance Analysis
4.3.1. Performance of UAV-Assisted Networks versus the Number of System Files
Considering the change of the number of system files, we compare the performance of UAV-assisted networks applying four algorithms, i.e., the random selection, best NE, worst NE, and the proposed algorithm. We run the random selection algorithm 1000 times and choose the average value as the final result of the random selection algorithm. Similarly, we carry out 1000 independent trials using the proposed log-linear caching algorithm. Actually, each convergent value is a NE solution. Then the average of values is defined as the final value. In addition, we choose the best one and the worst one of the values as the best NE and the worst NE, respectively. Figure 3 depicts the performance of UAV-assisted networks when varying the number of system files from to . Several important observations can be seen in this figure: (1) the performance of UAV-assisted networks decreases as the number of system files increases. (2) Compared with the random algorithm, the log-linear caching algorithm brings the better performance of UAV-assisted networks. (3) As a result of the limited UAVs’ processing capacity, when the number of system files increases, users’ requests become more complex, which leads to a decline in performance.
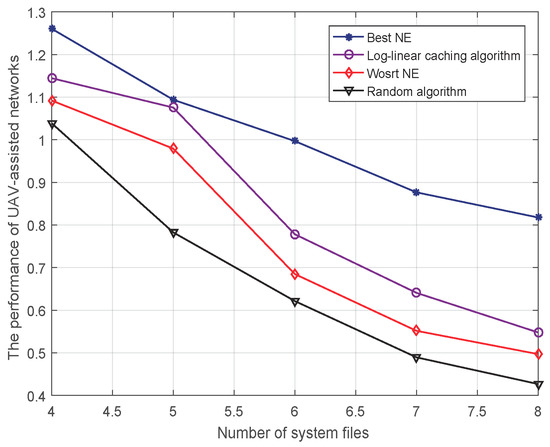
Figure 3.
The performance of UAV-assisted networks versus the number of system files ( and ).
4.3.2. Performance of UAV-Assisted Networks versus the Number of Cache Space
We assess the performance of UAV-assisted networks when changing the number of cache space from to . Figure 4 reflects the final results applying four approaches. The simulation process is similar to Figure 3. From Figure 4, the simulation curves reflect the fact that: (1) The performance of UAV-assisted networks increases as the cache space of UAVs increases. The reason is that greater cache space brings high processing capacity of UAVs, which leads to an increase in performance. (2) The log-linear caching algorithm is close to the best NE and outperforms the random selection algorithm which validate the effectiveness of the proposed algorithm.
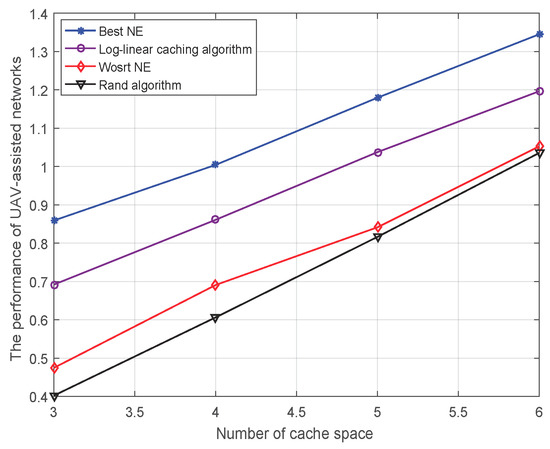
Figure 4.
The performance of UAV-assisted networks versus the size of cache space of UAVs ( and ).
4.3.3. Performance of UAV-Assisted Networks versus the Number of UAVs
Considering the number of UAVs varying from N = 5 to N = 8, we compare the performance of UAV-assisted networks. Figure 5 indicates the influence of the number of UAVs on the performance of UAV-assisted networks. The fact is reflected from the simulation curves: in general, as the number of UAVs increases, the performance of UAV-assisted networks increases. The reasonable explanation is that more UAVs yield a larger successful communication probability. Additionally, the final performance of the proposed algorithm is close to the best NE with respect to different numbers of UAVs, which again validates the proposed algorithm.

Figure 5.
The performance of UAV-assisted networks versus the number of UAVs in service ( and ).
5. Conclusions
In this paper, the problem of the optimal arrangement for both UAV’s caching contents and service locations in UAV-assisted networks was investigated. We modeled the problem as a UAV-assisted caching game with LCA. The proposed model combined with game theory was proved to be effective, which was shown in the simulation results. Meanwhile, the simulation results indicated that the performance of UAV-assisted networks was related with the number of system files, cache space of UAVs, and the number of UAVs in service. Inspired by the related simulation results, increasing the number of UAVs in service is not the only way to improve the quality of service. In real life, the performance of UAV-assisted networks can be improved by reasonable arrangement of UAVs’ caching contents and service locations.
Author Contributions
T.F. and Y.Z. conceived the model; T.F. performed the simulation results and performance analysis; X.Z. and X.C. analyzed the game proof; T.F. wrote the paper; and H.T., X.S. provided some suggestions and revised the paper.
Funding
This work was supported by the National Natural Science Foundation of China under Grant No. 61771488 and No. 61631020, in part by the Natural Science Foundation for Distinguished Young Scholars of Jiangsu Province under Grant No. BK20160034, and in part by the Open Research Foundation of Science and Technology on Communication Networks Laboratory.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Orfanus, D.; de Freitas, E.P.; Eliassen, F. Self-organization as a supporting paradigm for military UAV relay networks. IEEE Commun. Lett. 2016, 20, 804–807. [Google Scholar] [CrossRef]
- Ma’sum, M.A.; Arrofi, M.K.; Jati, G.; Arifin, F.; Kurniawan, M.N.; Mursanto, P.; Jatmiko, W. Simulation of intelligent unmanned aerial vehicle (UAV) for military surveillance. In Proceedings of the 2013 International Conference on Advanced Computer Science and Information Systems, Bali, Indonesia, 28–29 September 2013; pp. 161–166. [Google Scholar]
- Giese, S.; Carr, D.; Chahl, J. Implications for unmanned systems research of military UAV mishap statistics. In Proceedings of the 2013 IEEE Intelligent Vehicles Symposium, Gold Coast, QLD, Australia, 23–26 June 2013; pp. 1191–1196. [Google Scholar]
- Johnson, C.W. Military risk assessment in counter insurgency operations: Case study in the retrieval of a UAV, Nr Sangin, Afghanistan, 11 June 2006. In Proceedings of the 2008 3rd IET International Conference on System Safety, Birmingham, UK, 20–22 October 2008; pp. 1–6. [Google Scholar]
- Chen, Z.; Luo, J.; Jiang, H.; Shi, W. Design & application of MIS on UAV quality & reliability for total life span. In Proceedings of the 2009 8th International Conference on Reliability, Maintainability and Safety, Chengdu, China, 20–24 July 2009; pp. 1290–1292. [Google Scholar]
- Cecil, J. A conceptual framework for supporting UAV based cyber physical weather monitoring activities. In Proceedings of the 2018 Annual IEEE International Systems Conference, Vancouver, BC, Canada, 23–26 April 2018; pp. 1–8. [Google Scholar]
- Zhou, S.; Wang, Y.; Ye, S.; Zhu, G.; Cheng, L. The intelligent wind detection system of weather UAV based on the multi-mode variable structure. In Proceedings of the 2011 Fourth International Conference on Intelligent Computation Technology and Automation, Shenzhen, China, 28–29 March 2011; pp. 765–768. [Google Scholar]
- Zhang, W.; Yu, H.; Yan, Z.; Xu, J. Study on disaster monitoring technology of mountain fire based on UAV transmission line inspection. In Proceedings of the 2017 IEEE International Conference on Unmanned Systems, Beijing, China, 27–29 October 2017; pp. 400–403. [Google Scholar]
- Yuan, C.; Liu, Z.; Zhang, Y. UAV-based forest fire detection and tracking using image processing techniques. In Proceedings of the 2015 International Conference on Unmanned Aircraft Systems, Denver, CO, USA, 9–12 June 2015; pp. 639–643. [Google Scholar]
- Ji, X.; Hua, Q.; Li, C.; Tang, J.; Wang, A.; Chen, X.; Fang, D. 2-OptACO: An improvement of ant colony optimization for UAV path in disaster rescue. In Proceedings of the 2017 International Conference on Networking and Network Applications, Kathmandu, Nepal, 16–19 October 2017; pp. 225–231. [Google Scholar]
- Nakadai, K.; Kumon, M.; Okuno, H.G.; Hoshiba, K.; Wakabayashi, M.; Washizaki, K.; Ishiki, T.; Gabriel, D.; Bando, Y.; Morito, T.; et al. Development of microphone-array-embedded UAV for search and rescue task. In Proceedings of the 2017 IEEE/RSJ International Conference on Intelligent Robots and Systems, Vancouver, BC, Canada, 24–28 September 2017; pp. 5985–5990. [Google Scholar]
- Zeng, Y.; Zhang, R.; Lim, T.J. Wireless communications with unmanned aerial vehicles: Opportunities and challenges. IEEE Commun. Mag. 2016, 54, 36–42. [Google Scholar] [CrossRef]
- Xu, X.; Zeng, Y.; Guan, Y.L.; Zhang, R. Overcoming Endurance Issue: UAV-Enabled Communications with Proactive Caching. IEEE J. Sel. Areas Commun. 2018, 36, 1231–1244. [Google Scholar] [CrossRef]
- Chen, M.; Mozaffari, M.; Saad, W.; Yin, C.; Debbah, M.; Hong, C.S. Caching in the sky: Proactive deployment of cache-enabled unmanned aerial vehicles for optimized quality-of-experience. IEEE J. Sel. Areas Commun. 2017, 35, 1046–1061. [Google Scholar] [CrossRef]
- Fang, T.; Tian, H.; Yang, Y.; Liu, X.; Wu, D.; Chen, X. An influence factor based caching node selection algorithm in D2D networks. In Proceedings of the 2017 IEEE 17th International Conference on Communication Technology (ICCT), Chengdu, China, 27–30 October 2017; pp. 805–809. [Google Scholar]
- Zhang, Y.; Xu, Y.; Wu, Q.; Liu, X.; Yao, K.; Anpalagan, A. A game-theoretic approach for optimal distributed cooperative hybrid caching in D2D networks. IEEE Wirel. Commun. Lett. 2018, 7, 324–327. [Google Scholar] [CrossRef]
- Zhao, N.; Cheng, F.; Yu, F.R.; Tang, J.; Chen, Y.; Gui, G.; Sari, H. Caching UAV assisted secure transmission in hyper-dense networks based on interference alignment. IEEE Trans. Commun. 2018, 66, 2281–2294. [Google Scholar] [CrossRef]
- Chen, M.; Saad, W.; Yin, C. Liquid state machine learning for resource allocation in a network of cache-enabled LTE-U UAVs. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar]
- Fang, T.; Tian, H.; Yang, Y.; Zhang, X.; Zhang, Y.; Xu, Y. Location-aware emergency content delivery in UAV-assisted networks: A game-theoretic approach. IEEE Access 2018. submitted. [Google Scholar]
- Cha, M.; Kwak, H.; Rodriguez, P.; Ahn, Y.Y.; Moon, S. I tube, you tube, everybody tubes: Analyzing the world’s largest user generated content video system. In Proceedings of the 7th ACM SIGCOMM Conference on Internet Measurement, San Diego, CA, USA, 24–26 October 2007. [Google Scholar]
- UMassTraceRepository. Available online: http://traces.cs.umass.edu/index.php/network/network (accessed on 17 April 2013).
- Xu, Y.; Wang, J.; Wu, Q.; Anpalagan, A.; Yao, Y.D. Opportunistic spectrum access in cognitive radio networks: Global optimization using local interaction games. IEEE J. Sel. Top. Signal Process. 2012, 6, 180–194. [Google Scholar] [CrossRef]
- Emara, M.; Elsawy, H.; Sorour, S.; Al-Ghadhban, S.; Alouini, M.; Al-Naffouri, T.Y. Optimal caching in 5G networks with opportunistic spectrum access. IEEE Trans. Wirel. Commun. 2018, 17, 4447–4461. [Google Scholar] [CrossRef]
- Al-Hourani, A.; Kandeepan, S.; Lardner, S. Optimal LAP altitude for maximum coverage. IEEE Wirel. Commun. Lett. 2014, 3, 569–572. [Google Scholar] [CrossRef]
- Xu, Y.; Ren, G.; Chen, J.; Luo, Y.; Jia, L.; Liu, X.; Yang, Y.; Xu, Y. A one-leader multi-follower bayesian-stackelberg game for anti-jamming transmission in UAV communication networks. IEEE Access 2018, 6, 21697–21709. [Google Scholar] [CrossRef]
- Jia, L.; Xu, Y.; Sun, Y.; Feng, S.; Anpalagan, A. Stackelberg game approaches for anti-jamming defence in wireless networks. arXiv. 2018. Available online: https://arxiv.org/abs/1805.12308 (accessed on 31 May 2018).
- Xu, Y.; Wang, J.; Wu, Q.; Zheng, J.; Shen, L.; Anpalagan, A. Dynamic spectrum access in time-varying environment: Distributed learning beyond expectation optimization. IEEE Trans. Commun. 2017, 65, 5305–5318. [Google Scholar] [CrossRef]
- Chen, J.; Wu, Q.; Xu, Y.; Zhang, Y.; Yang, Y. Distributed demand- aware channel-slot selection for multi-UAV networks: A game-theoretic learning approach. IEEE Access 2018, 6, 14799–14811. [Google Scholar] [CrossRef]
- Liu, D.; Xu, Y.; Wang, J.; Xu, Y.; Anpalagan, A.; Wu, Q.; Wang, H.; Shen, L. Self-organizing relay selection in UAV communication networks: A matching game perspective. arXiv, 2018; arXiv:1805.09257. [Google Scholar]
- Zhang, Y.; Xu, Y.; Anpalagan, A.; Wu, Q.; Xu, Y.; Sun, Y.; Feng, S.; Luo, Y. Context-aware group buying in ultra-dense small cell networks: Unity is strength. IEEE Wirel. Commun. 2018, in press. [Google Scholar]
- Monderer, D.; Shapley, L.S. Potential games. Games Econ. Behav. 1996, 14, 124–143. [Google Scholar] [CrossRef]
- Wu, Q.; Wu, D.; Xu, Y.; Wang, J. Demand-aware multichannel opportunistic spectrum access: A local interaction game approach With reduced information exchange. IEEE Trans. Veh. Technol. 2015, 64, 4899–4904. [Google Scholar] [CrossRef]
- Xu, Y.; Wu, Q.; Wang, J.; Shen, L.; Anpalagan, A. Opportunistic spectrum access using partially overlapping channels: Graphical game and uncoupled learning. IEEE Trans. Commun. 2013, 61, 3906–3918. [Google Scholar] [CrossRef]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).