1. Introduction
In widely used networks such as Internet or cellular networks, connectivity between a source node and a destination node should always be maintained in order to deliver data or message from a source node to a destination node. If connectivity fails due to any reason, however, a communication session between them is broken and message delivery is not possible any more. For a special network environment, such as disaster environment, deep space environment, or wildlife sensing environment, where connectivity between nodes is not available always, conventional network protocols, such as Internet or cellular networks, are not feasible. Delay tolerant network (DTN) protocol was proposed for this environment [
1,
2,
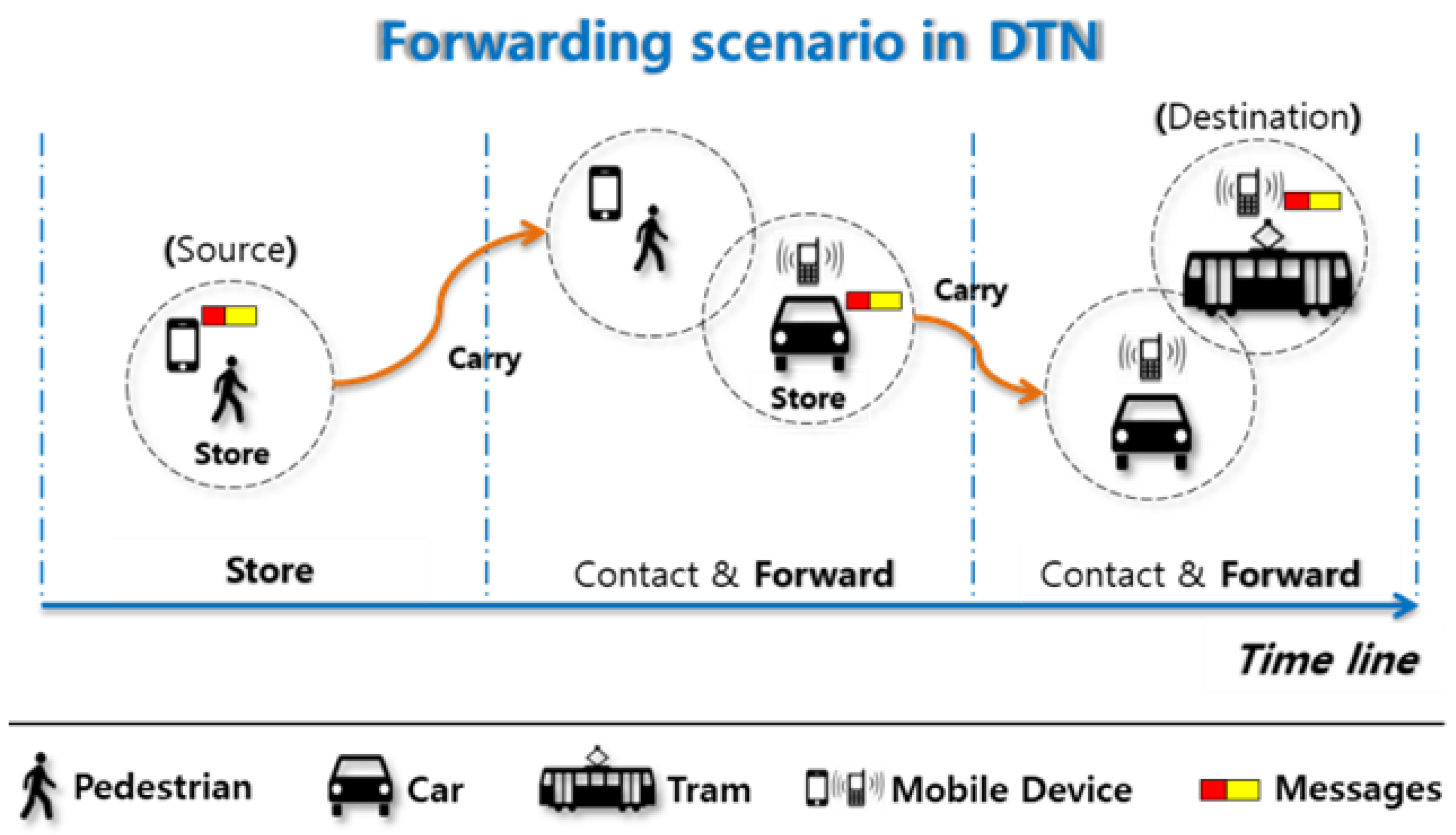
3]. In DTN, a message is delivered using opportunistic contacts between nodes. When a node has a message to send, it is stored in its buffer and it is not removed from the buffer, even though there is no current connection with the destination node. Then, a message is forwarded to another node when the two nodes are within communication range, if a pre-defined forwarding condition is met. Through a series of forwarding via intermediate nodes using opportunistic contacts, a message can be delivered to a destination node finally. This is called a ‘store-carry-forward’ mechanism of DTN, as shown in
Figure 1 [
1,
2,
3].
There are a lot of routing protocols in DTN. Out of these, epidemic [
4], spray & wait [
5], and probabilistic routing protocol for intermittently connected networks (PRoPHET) [
6] are basic but important routing protocols. Epidemic protocol is a flooding-based protocol and a message is forwarded to any contact node [
4]. It is simple but it has high traffic overhead. To solve the traffic overhead problem of Epidemic protocol, spray & wait protocol was proposed, where the number of total message copies in a network is limited by L [
5]. When a node generates a message to send, only L copies of the message can be distributed in spray phase until L nodes have only one message copy. Then, a node with the message copy delivers it to the destination node only in the wait phase. Although spray & wait can efficiently reduce the traffic overhead, message copies are distributed blindly. In PRoPHET protocol, messages are not forwarded to another node blindly, but are based on the delivery predictability of a node to a destination node [
6]. In PRoPHET protocol, each node calculates the delivery predictability of other nodes based on the contact history between them. The delivery predictability of a node A to a destination node B,
, is a metric to estimate a likelihood of delivering a message to a node B. It is assumed that a node with a higher delivery predictability to a destination node is a better node for delivering a message to the destination node. Whenever any two nodes contact each other, the delivery predictability between them increases, as in Equation (1) [
6]:
where
is a scaling factor controlling the increasing rate of the delivery predictability after contact, and
is a parameter for an upper bound of P(A, B). As time elapses, the delivery predictability decreases, as in Equation (2) [
6]:
where
is the aging constant and
is the number of elapsed time units since last contact time. Also, the delivery predictability has a transitive property. That is, if nodes A and B contact frequently, and if nodes B and C contact frequently, the delivery predictability between nodes A and C becomes high, as in Equation (3) [
6]:
where
is a scaling constant.
In this paper, we consider PRoPHET protocol as a base protocol [
6]. In PRoPHET protocol, there are several message forwarding strategies. In the GRTR strategy, the message of node A is delivered to node B, if node B has higher delivery predictability to the destination node of the message. In GTMX strategy, the message of node A is delivered to node B, if node B has higher delivery predictability and the number of message forwarding so far is less than a threshold value. We note that GRTR and GTMX are not a specific acronyms but they are just mnemonic.
There have been lots of related works. In AntProPHET scheme [
7], ant colony optimization algorithm, which is one of the widely used bio-inspired optimization algorithm, is applied to PRoPHET protocol. In [
8], a message is forwarded to another node if the delivery predictability of the another node to the destination node of the message is higher than that of sending node and a threshold value, and also if the sum of the delivery predictabilities of the receiving node so far is less than a threshold value. In [
9], the density of neighbor nodes is considered to decide whether Epidemic protocol or PRoPHET protocol is used. Epidemic protocol is selected if the density is less than a threshold value. Otherwise, PRoPHET protocol is selected.
In [
10], the movement trajectory of a node is estimated by using the Markov chain based on the speed and direction of movement of nodes and the movement trajectory is used to decide whether a message is forwarded or not. In [
11], the information of current location, movement direction, speed, and estimated direction change of a mobile node with GPS (global positioning system) is used to decide whether the node approaches near the destination node and a message is forwarded if a node has the closest estimated approach to the destination node. In [
12], a forwarding node is selected based on the information of location, speed, movement direction, and time. In [
13], if the movement pattern is periodic in a considered network topology, a scheme to minimize the delivery time to reach the destination node from a source node was proposed. In [
14], the contact period between nodes is estimated and a message is forwarded to a node closer to the next contact time with the destination node. In [
15], last contact duration, last contact time, and current contact time between any two nodes are used to calculate the neighborhood index formula and a message is forded to a node with a higher neighborhood index formula.
In [
16], friendship and selfishness (FSF) value is classified as weak, middle, and high level, based on contact counts to a destination node, contact duration, and the amount of exchanged messages. Then, a message is forwarded if another node has a higher FSF value. In [
17], contact history is managed in a table and a message forwarding is determined based on the contact existence with the destination node in the same time zone when the two nodes contact. In [
18], in the early phase of message dissemination, a message is forwarded to a node with a higher chance of message dissemination. On the other hand, in the latter phase of message dissemination, message is forwarded to a node with higher chance of message delivery to the destination node. In [
19], reachable probability centrality (RPC) is calculated based on the contact history with the destination node and a message is forwarded to a node with a higher RPC value. In [
20], node type such as pedestrian, car, and tram as well as delivery predictability is used together to determine forwarding. The basic idea is to give higher priority to tram for message forwarding, that is, if receiving node is a tram, messages are forwarded with higher probability, since the buffer size of tram is relatively higher than other nodes and has more chances of contact with other nodes due to its high mobility.
In [
21], the authors use historical throughput and historical contact time to calculate forward probability and a message is forwarded to a node with a higher forward probability. The forwarding probability has similar characteristics with delivery predictability in PRoPHET protocol, i.e., increase for each contact, decay after contact, and transitivity. In [
22], the authors propose a novel encounter based fuzzy logic routing, where the transfer opportunism of a node is computed while using fuzzy logic using the encounter and non-encounter duration, and messages are forwarded based on the transfer opportunism. In [
23], the authors propose an encounter-based routing based on the observation that the future rate of node encounters can be roughly predicted by past encounters. In the encounter-based routing, the total copies of a message are limited and forwarding is decided based on the rates of encounters. In [
24], the authors basically consider the spray and wait protocol, and propose a new metric called multi-probability, where a message can be forwarded to a node if any of its previously contact nodes has higher delivery predictability, even though the node does not have higher delivery predictability currently.
Works on using mobility characteristics of mobile nodes for DTN have been carried out significantly [
25,
26,
27,
28,
29]. In [
25], mobility traces taken from UMass DieselNet, which consist of buses with WiFi interfaces that travel their routes, are used to forward messages, and the performance of the DieselNet routing is analyzed. They show the periodic behavior of inter-contact times aggregated at the router level. In [
26], mobility traces from real public transport systems are characterized and used to improve the routing performance of DTN. Then, large scale mobility traces are produced using micro-mobility simulator and the performance of various DTN routing protocols are compared with the proposed algorithm. In [
27], the authors propose a journey predictor for DTN based on mobility traces of public transportation system, where the journey predictor is based on a graph of predicted journeys and the best journey is selected to a specific destination. Artificial neural networks are used to predict a journey. In [
28], a multi-copy routing scheme for a DTN based on an urban bus transportations system is presented and contact history of nodes is used to improve the routing of DTN. They propose a journey predictor based on artificial neural networks to select the best journey to a destination. In [
29], nanosatellite communications link is used to cover a terrestrial sensor network that is based on DTN routing. The authors propose an optimal proactive fragmentation of DTN bundles, due to short contact duration between a nanosatellite and a sensor node, and show the performance enhancement over the reactive fragmentation approach.
In related works, movement trajectory [
10], movement direction, speed, estimated direction change, location [
11,
12], movement pattern [
13], contact period [
14], last contact duration, last contact time, current contact time [
15], contact count, contact duration, the amount of exchanged messages [
16], contact history [
17], node type [
20], historical throughput, historical contact time [
21], encounter duration, non-encounter duration [
22], rate of encounters [
23], and delivery predictability of previously contact nodes [
24] are used to decide a message forwarding. Most of the mentioned context information, however, reflect individual characteristics of contact nodes or node itself, and collective characteristics of nodes have not been considered well to deliver a message to a destination node. In this paper, we propose an improved opportunistic routing protocol, where the context information of average distance travelled and average time elapsed from the reception of a message to the delivery of the message to the destination node is used. The context information such as average distance travelled and average time elapsed considered in this paper reflects the collective characteristics of a node to destination nodes, and we estimate that the collective characteristics are effective to decide a message forwarding in the DTN environment. This is because the mobility and traffic characteristics of nodes are not predictable and thus the collective characteristics of a node can be considered as a capability to deliver a message to a destination node. In the proposed protocol, average distance and average time are updated whenever a message is delivered to a destination node. Then, both average distance and average time as well as delivery predictability of PRoPHET protocol are used to decide message forwarding. Basically, a message is forwarded to a contact node, if the contact node has smaller average time and distance values, as well as a higher delivery predictability value. Then, the performance of the proposed protocol is compared with PRoPHET protocol with GRTR strategy and RPC [
19] protocol, which is one of the latest protocols using contact history information of a mobile node.
The idea of using both average distance and average time information of the proposed protocol is similar to our preliminary work presented as an extended abstract in [
30], but the proposed work is significantly different from the previous work from the following aspects:
- -
the proposed protocol extends the forwarding algorithm further by additionally considering the existence of both average distance and average time information firstly. Then, the hop count of a message is checked to choose an appropriate forwarding condition, which is extended from the preliminary work; and,
- -
the performance of the proposed protocol is compared with RPC protocol additionally. Also, the performance of the proposed protocol is compared additionally from the aspect of delivery latency. Simulations are carried out extensively by additionally considering the change of number of nodes.
- -
Related works are significantly extended in this paper.
The remainder of this paper is organized as follows: In
Section 2, a detailed algorithm of the proposed protocol is proposed and the proposed protocol is illustrated using examples. In
Section 3, the performance of the proposed protocol is analyzed extensively using simulation. Finally,
Section 4 summarizes this work and presents future work.
2. Proposed Protocol
In the proposed protocol, whenever a node delivers a message to its destination node, it updates average distance travelled and average time elapsed from the reception of the message. Average distance and average time of node A are denoted as E[D
A] and E[T
A], respectively, and they are updated, as follows:
where TotD, TotT, and cntDest are total distance travelled, total time elapsed, and total number of messages for all of the delivered messages, respectively.
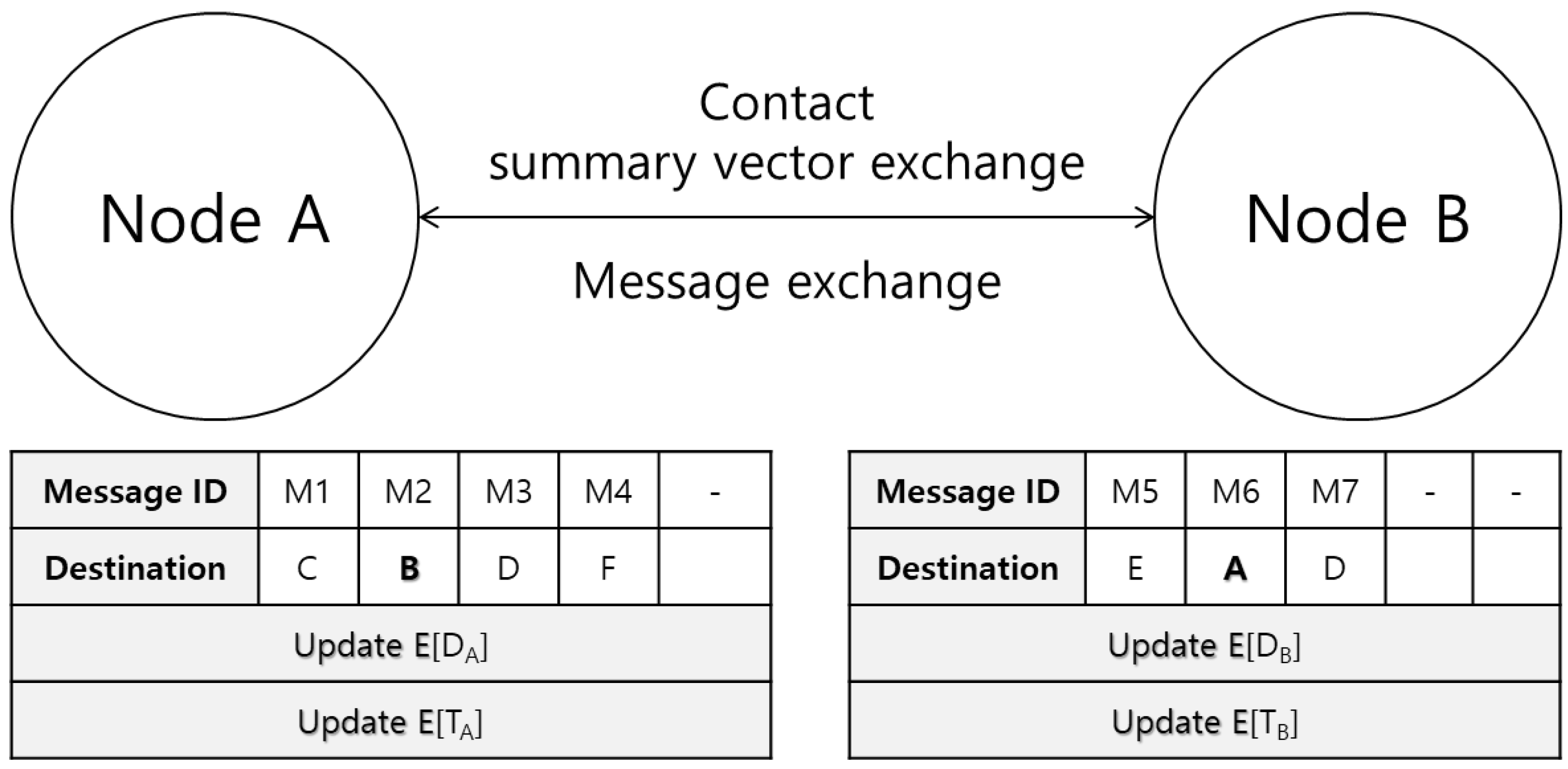
Figure 2 shows a scenario of update of average distance and average time when node A and node B contact each other. Since node A has message M2 with node B as a destination node, it firstly delivers the message M2 to node B. Then, node A updates average distance and average time by using the distance travelled and time elapsed, since it received the message M2 from another node firstly. Also, since node B has message M6 with node A as a destination node, it updates average distance and average time similarly. In the proposed protocol, we deliver a message to a node with smaller values of average distance and average time, as well as higher delivery predictability to a destination node, since a node with a smaller average distance and average time is more expected to contact the destination node because of its higher contact characteristic. That is, the proposed protocol considers both a collective property using average distance and average time, and it considers an individual property using delivery predictability to determine a better forwarder. In order to promote message dissemination in its early dissemination phase, a message generated originally at a node is forwarded based on a less strict condition, which will be explained in detail later.
In the proposed protocol, we consider delivery predictability of PRoPHET protocol for message forwarding basically. Also, we consider the average distance travelled and the average time elapsed from the reception of the message to the delivery to the destination message additionally. In order to apply the message forwarding condition efficiently, we firstly check the existence of average distance and average time value at a node and we classify a message into two classes, depending on the hop count of the messages. Hop count is defined as the number of nodes that a message has forwarded so far. If a message is generated at a node, the hop count of the message is defined as 0, and the hop count increases by 1 whenever it is forwarded to another node.
If average distance and average time information are not available since it has not delivered a message to a destination yet, different forwarding conditions are applied, depending on the hop count of the message. If the hop count is 0, a message is forwarded if the delivery predictability of the contact node is higher. This is because if the hop count is 0, which means that the message is originally generated at the current node, we promote the dissemination of such message since it has not been forwarded much, and thus active message forwarding is more favorable for message delivery. Thus, we forward such as message, if the basic condition of delivery predictability is met. On the other hand, if the hop count is larger than 0, which means that the message was forwarded from another node, the message is not forwarded in the proposed protocol. This is because the average distance and average time information are not available, and thus we defer the forwarding for such an already forwarded message until we have enough information to make a good forwarding decision.
If average distance and average time information are available, we apply different forwarding conditions, depending on the hop count of a message. If the hop count of a message at a node is 0, we promote a dissemination of such a message, and thus, a message is forwarded, if either (1) the delivery predictability of the contact node is higher or (2) both average distance and average time of the contact node are smaller is met. On the other hand, if the hop count is larger than 0, we selectively forward the message by using more strict condition. That is, a message is forwarded, if both of the conditions are met.
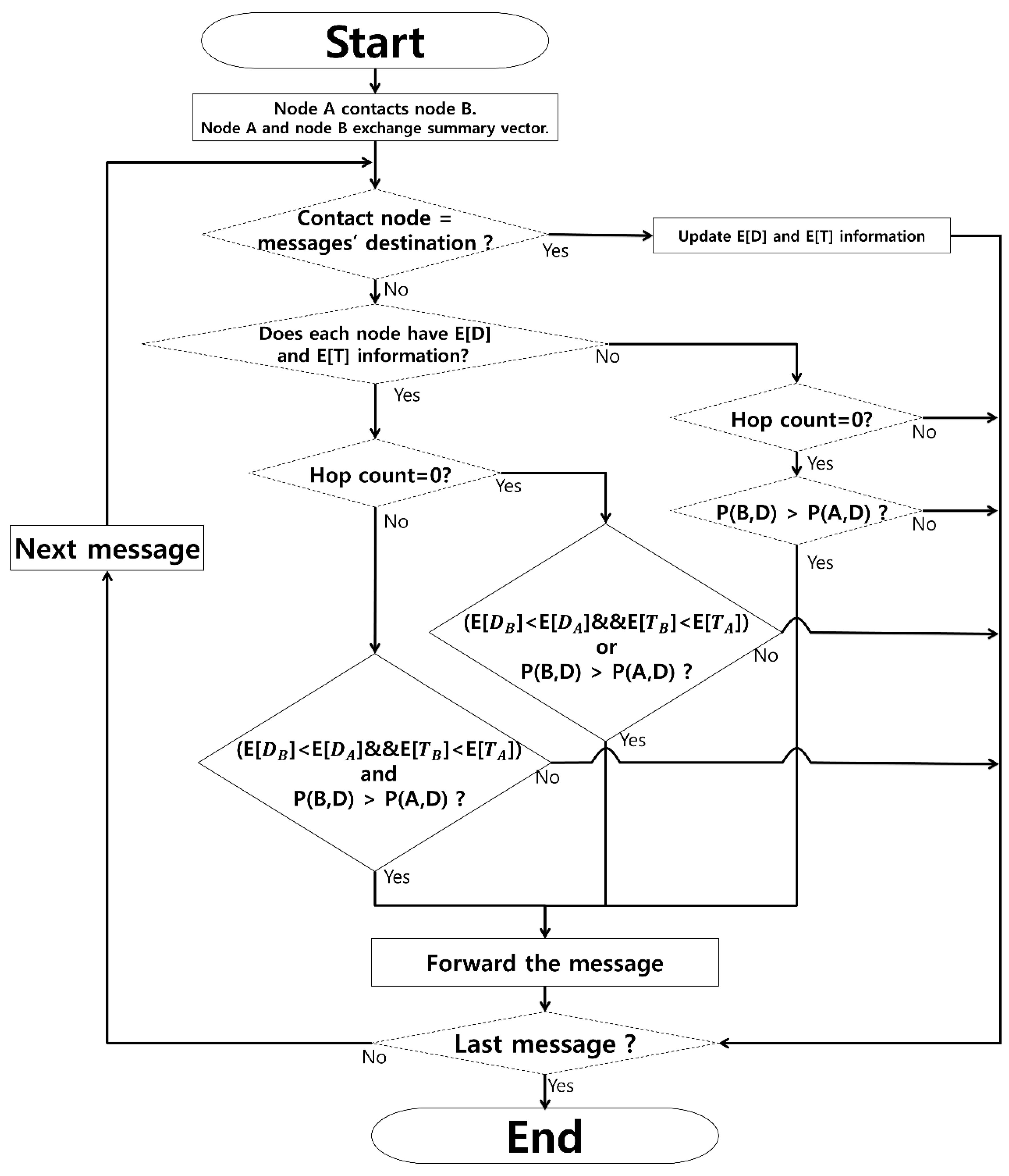
Figure 3 shows the flowchart of the proposed protocol. Whenever node A contacts node B, they exchange summary vectors that include the list of messages they have and the destination node information for the stored messages. If node A has a message with node B as a destination node it delivers the message to node B, and updates the average distance and average time. Otherwise, node A and B check if they have average distance and average time already. If they both have those values, they compare average distance, average time, and delivery predictability. Then, node A checks the hop count of a considered message. If the hop count of a message is 0, a message is forwarded if the following condition is met:
In Equation (6), the basic idea is to promote a dissemination of a message by allowing for a forwarding if any of the two conditions, i.e., E[D
A] > E[D
B] AND E[T
A] > E[T
B] or P(A, D) < P(B, D), is met, if the hop count of the message is 0. If the hop count of a message is larger than 0, a message is forwarded only if the following condition is met:
In Equation (7), the basic idea is to restrict a dissemination of a message by allowing a forwarding only if all of two conditions are met, if the hop count is larger than 0, since it has been forwarded already, and thus, forwarding should be carried out more selectively in order to reduce traffic overload, which is a major factor to decrease delivery ratio.
If two contact nodes do not have average distance and average time value yet, only a message with hop count of 0 is forwarded, if the delivery predictability of the contact node is higher. The same procedure is repeated for all of the messages of node A.
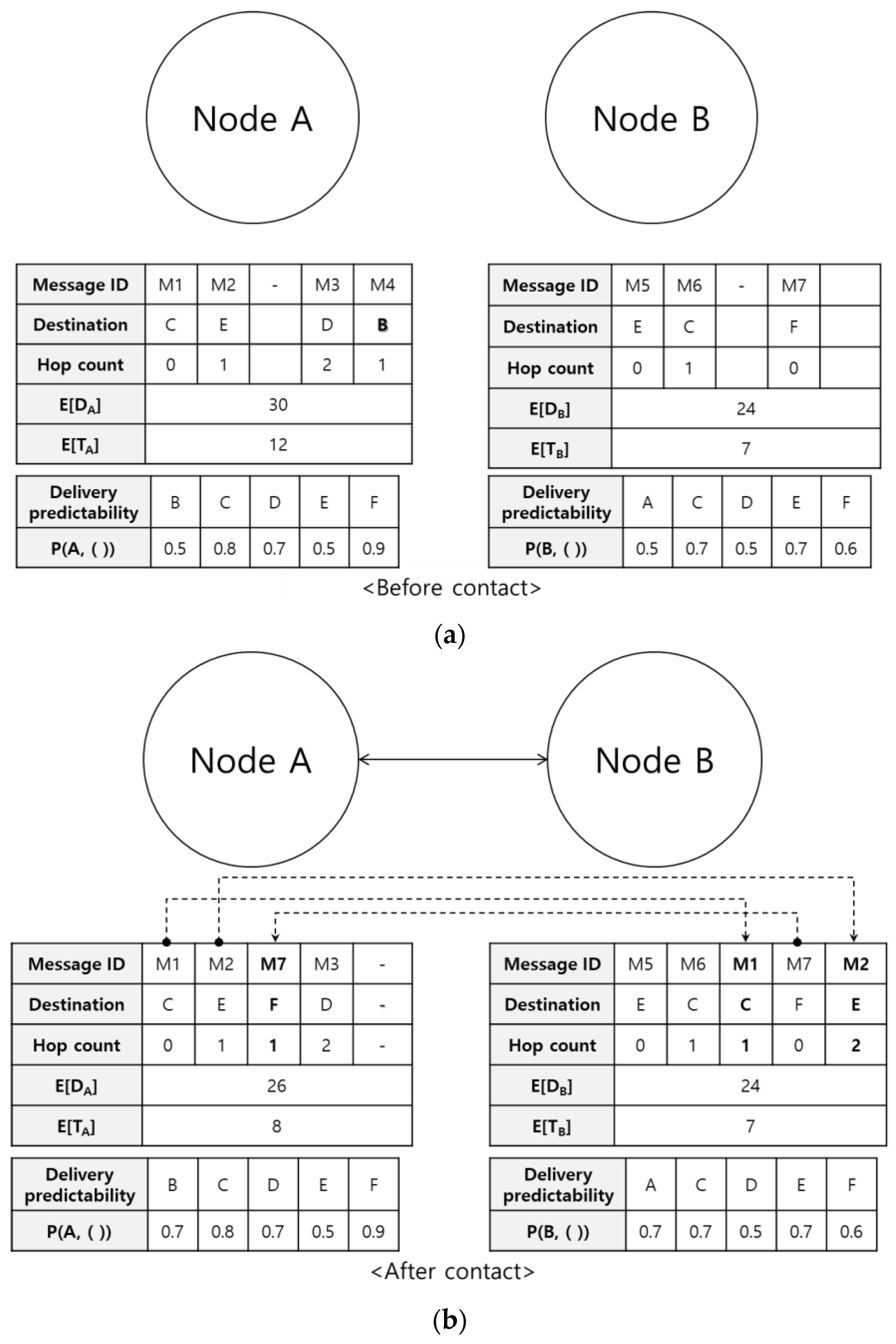
Figure 4 shows an example of the operation of the proposed protocol. Before contact occurs, node A and node B have messages with delivery predictability information as well as average distance and average time information, as shown in
Figure 4a. In the example, it is assumed that both nodes have delivered a message to a destination node, and thus they have average distance and average time information, and those values of node B are smaller than those of node A. Since the destination node of message M4 of node A is node B, it is delivered to node B, and then, both average distance and average time values of node A are updated. The message M4 is removed from the buffer of node A after delivery. The message M1 of node A is forwarded to node B, since both average distance and average time values of node B are smaller than those of node A, although the delivery predictability of node B is not larger than that of node A, in order to disseminate the message M1 more, which is the forwarding condition when the hop count of a message is 0 and both average distance and average time information are available, as in Equation (6). The message M2 of node A is forwarded to node B, since both the average distance and average time values of node B are smaller than those of node A and the delivery predictability of node B is larger than that of node A, which is the forwarding condition when the hop count of a message is larger than 0 and both the average distance and average time information are available, as in Equation (7). On the other hand, the message M3 of node A is not forwarded to node B, since the forwarding condition Equation (7) is not met, i.e., the delivery predictability of node B to the destination node D is smaller than that of node A, although both the average distance and average time values of node B are smaller than those of node A. The message M5 of node B is not forwarded to node A, since the forwarding condition Equation (4) is not met, i.e., the delivery predictability of node A to a node E, which is the destination node of M5, is not larger than that of node B and both average distance and average time values of node A are not smaller than those of node B. The message M7 of node B is forwarded to node A, since the delivery predictability of node A to node F, which is the destination node of message M7, is larger than that of node B, although both average distance and average time values of node A are not smaller than those of node B, as in Equation (6), in order to disseminate the message M7 more.
3. Performance Analysis
The performance of the proposed protocol is analyzed and compared with PRoPHET protocol with GRTR strategy and RPC protocol [
19], which is one of the latest protocols while using history information. For performance analysis, opportunistic network environment (ONE) simulator is used to analyze the performance, which is one of the most widely used simulators for DTN [
31,
32]. The parameter values assumed in the simulation are given in
Table 1.
Figure 5,
Figure 6 and
Figure 7 show delivery ratio, overhead ratio, and delivery latency of the proposed protocol, PRoPHET, and RPC, for varying the buffer size of a mobile node, where delivery predictability, overhead ratio, and delivery latency are defined as follow:
where
,
,
, and
represent the number of successfully delivered messages, the number of created messages, the number of relayed messages, and the sum of the delays of the all delivered messages, respectively.
Figure 5 shows delivery ratio for varying buffer size. The delivery ratios of all three protocols increase as the buffer size increases, since more buffer size can accommodate more messages, and thus more messages can be delivered successfully without removal at the buffer. The delivery ratio saturates as the buffer size increases, since the change of buffer size does not have significant effect on the delivery. The proposed protocol has better delivery ratio than both PRoPHET and RPC for fixed buffer size, since the proposed protocol can deliver messages more efficiently.
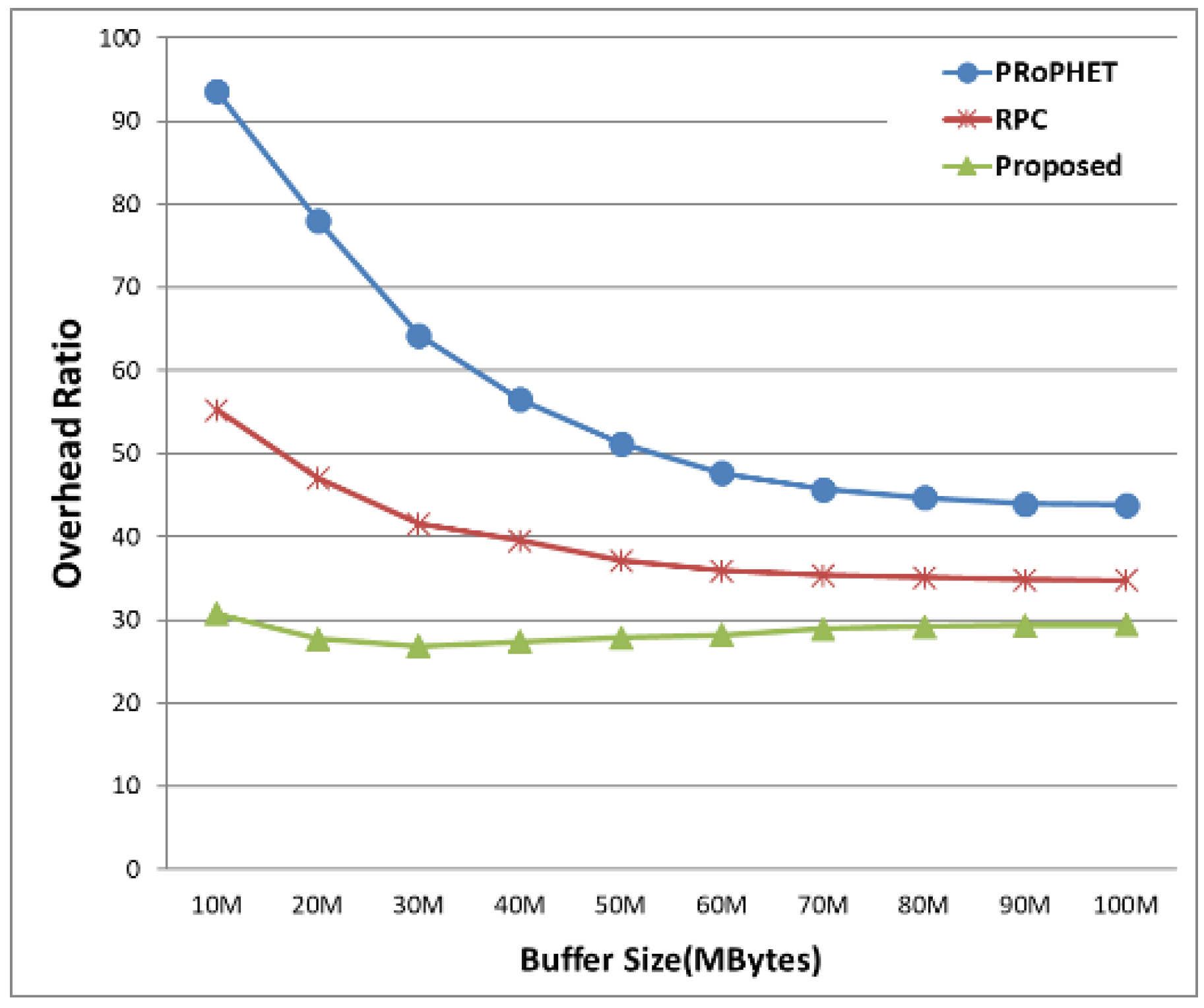
Figure 6 shows overhead ratio by varying buffer size. The overhead ratios of all three protocols decrease as buffer size increases since the delivery probability increases as buffer size increases and the effect of increased number of successfully is more dominant in the calculation of overhead as in Equation (9). The proposed protocol has the smaller overhead than both PRoPHET and RPT for fixed buffer size, since it has higher delivery probability and it efficiently limits the number of forwarding by comparing the average distance and average time as well as delivery predictability.
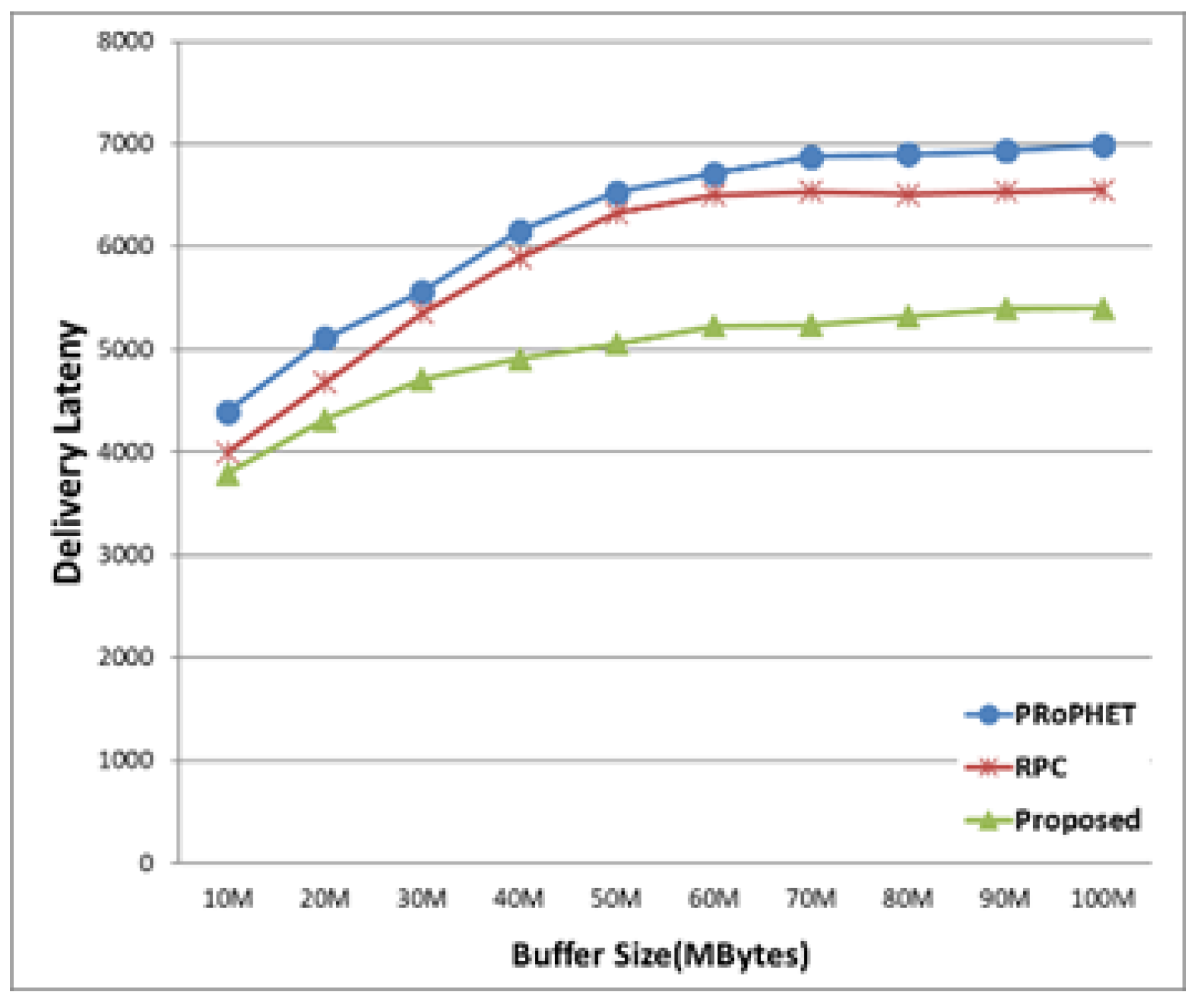
Figure 7 shows delivery latency by varying buffer size. The delivery latencies of three protocols increase as buffer size increases, since more buffer size can accommodate more messages, and thus more time is needed for forwarding to another node during short contact duration. The proposed protocol has smaller delivery latency than both PRoPHET and RPC for fixed buffer size, since the proposed protocol efficiently limits the forwarding by comparing the average distance and average time, as well as delivery predictability.
Figure 8,
Figure 9 and
Figure 10 show the delivery ratio, overhead ratio, and delivery latency of the proposed protocol, PRoPHET, and RPC, by varying the message generation interval. As shown in
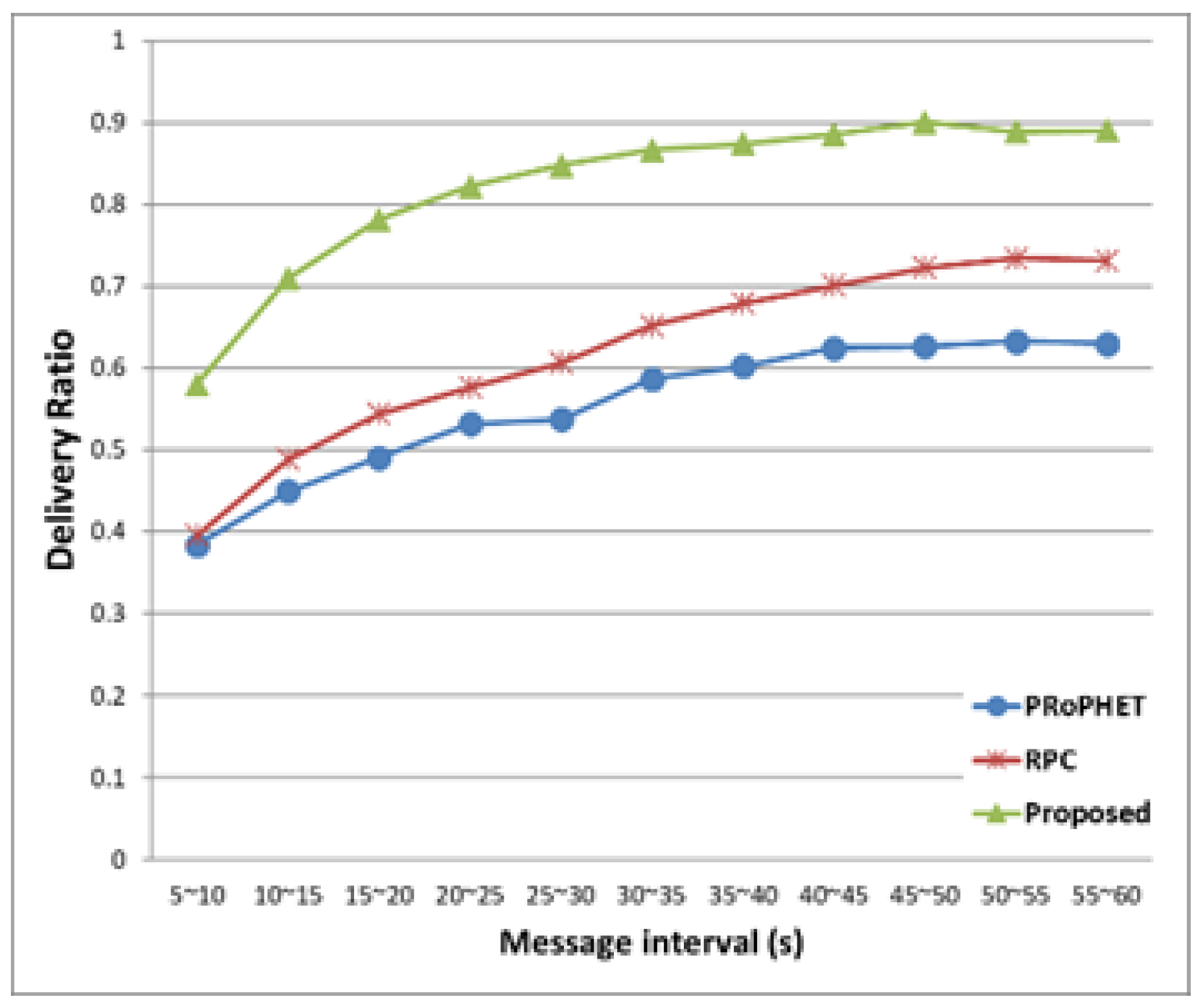
Figure 8, the delivery ratios of all three protocols increase as the message generation interval increases, since the number of generated message decreases as the message generation interval increases, and thus, the number of removed message decreases for a fixed buffer size. The proposed protocol has larger delivery ratio than PRoPHET and RPC for a fixed value of message generation interval.
As shown in
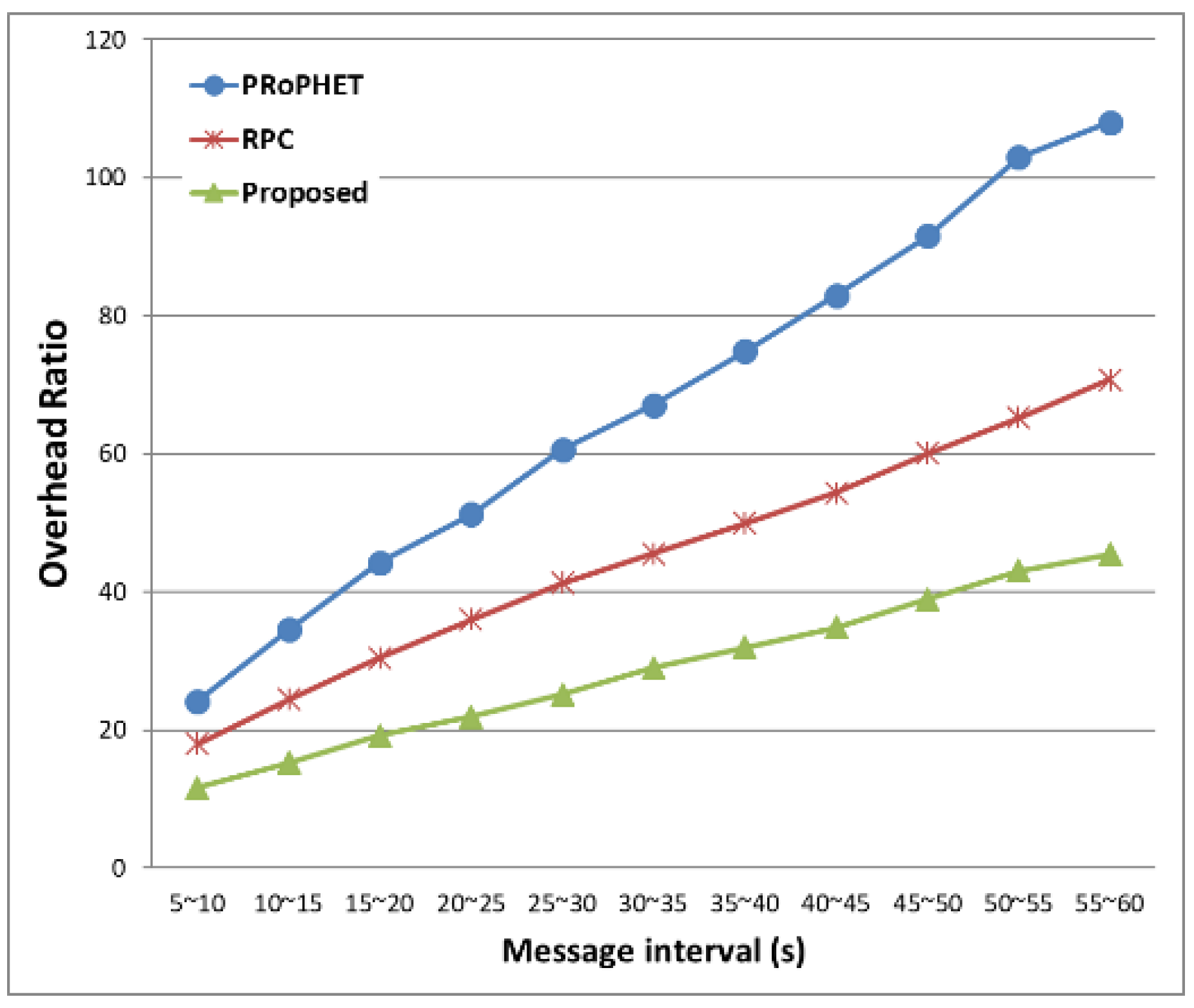
Figure 9, the overhead ratios of all three protocols increase as message generation interval increases, since the number of delivered messages decreases as message generation interval increases. The proposed protocol has smaller overhead ratio than both PRoPHET and RPC, since it has higher delivery probability and it efficiently limits the number of forwarding by comparing the average distance and average time, as well as delivery predictability.
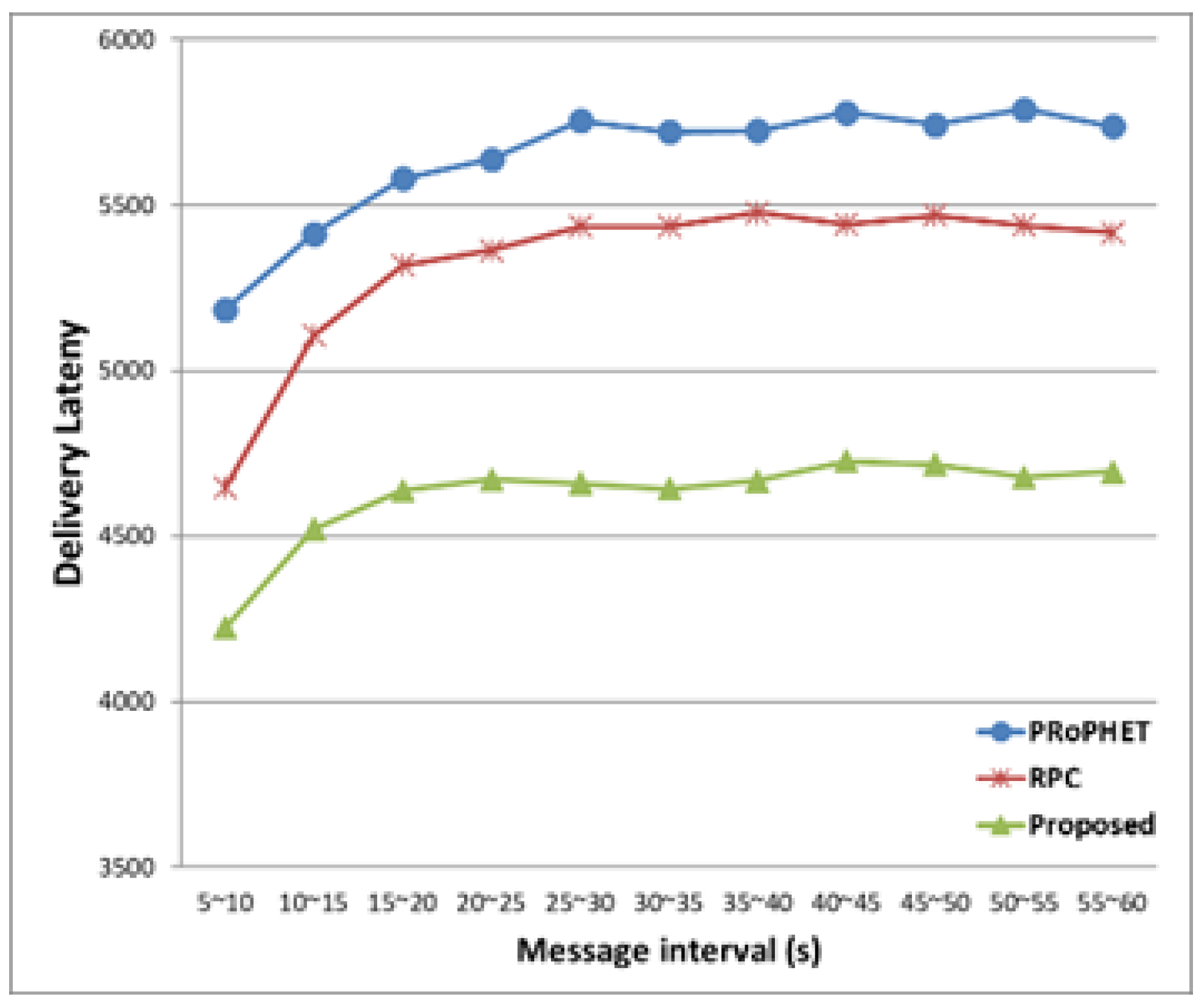
The delivery latencies of all three protocols increase as message generation interval increases, as shown in
Figure 10, since the number of messages dropped at the buffer decreases since the number of messages decreases, and thus, more time is needed for forwarding to another node during short contact duration. The proposed protocol has smaller delivery latency than both PRoPHET and RPC, since it efficiently limits the number of forwarding by comparing average distance and average time as well as delivery predictability.
Figure 11,
Figure 12 and
Figure 13 show the delivery ratio, overhead ratio, and delivery latency of the proposed protocol, PRoPHET, and RPC, by varying the number of nodes. As shown in
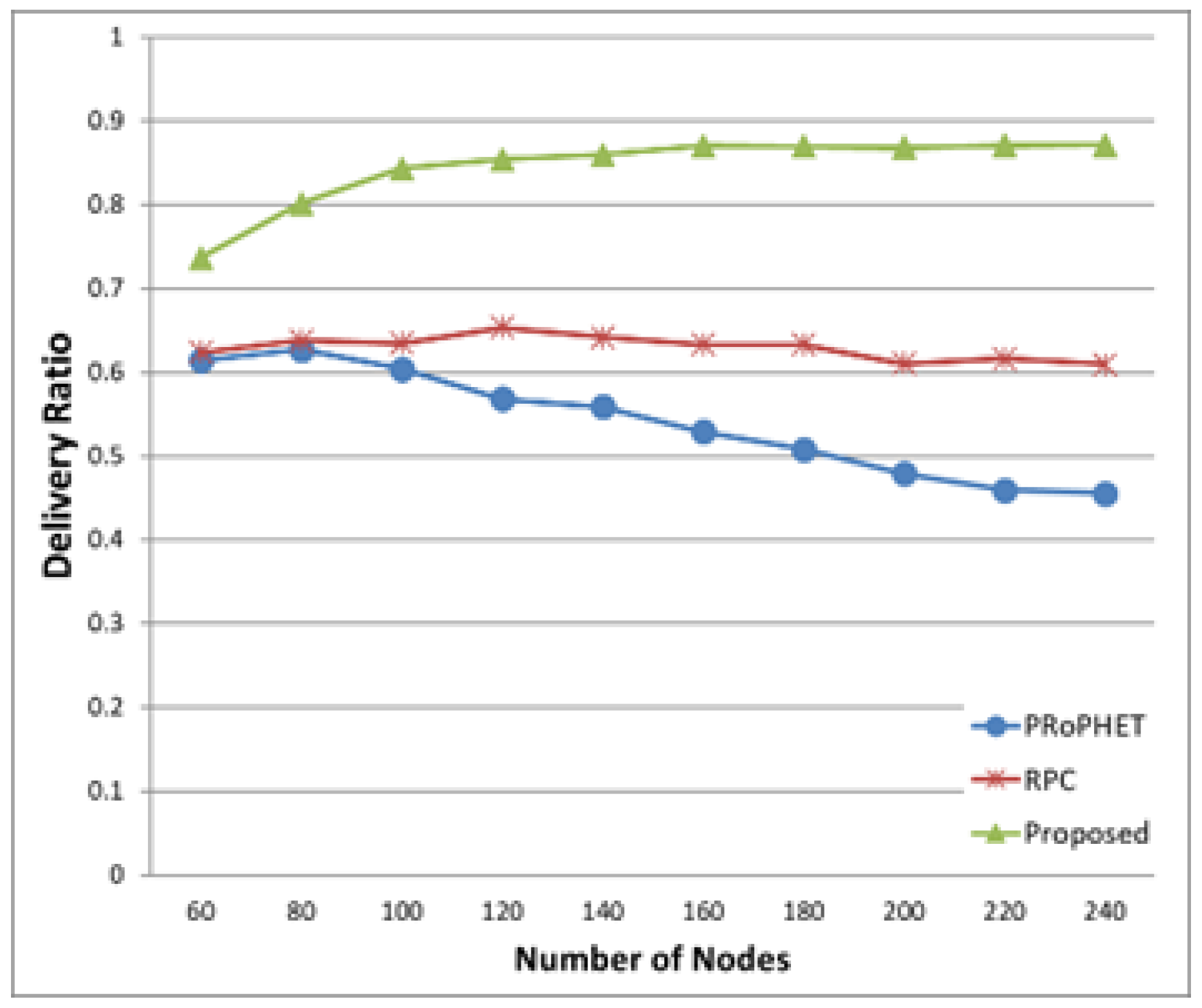
Figure 11, the delivery ratios of PRoPHET and RPC protocol does not increase as the number of nodes increases since more nodes generate more message copies and thus the number of delivered message decreases due to more message removal at the buffer. The delivery ratio of the proposed protocol increases as the number of node increases since the proposed protocol efficiently selects forwarding node out of more number of possible forwarding nodes. The proposed protocol has larger delivery ratio than both PRoPHET and RPC.
As shown in
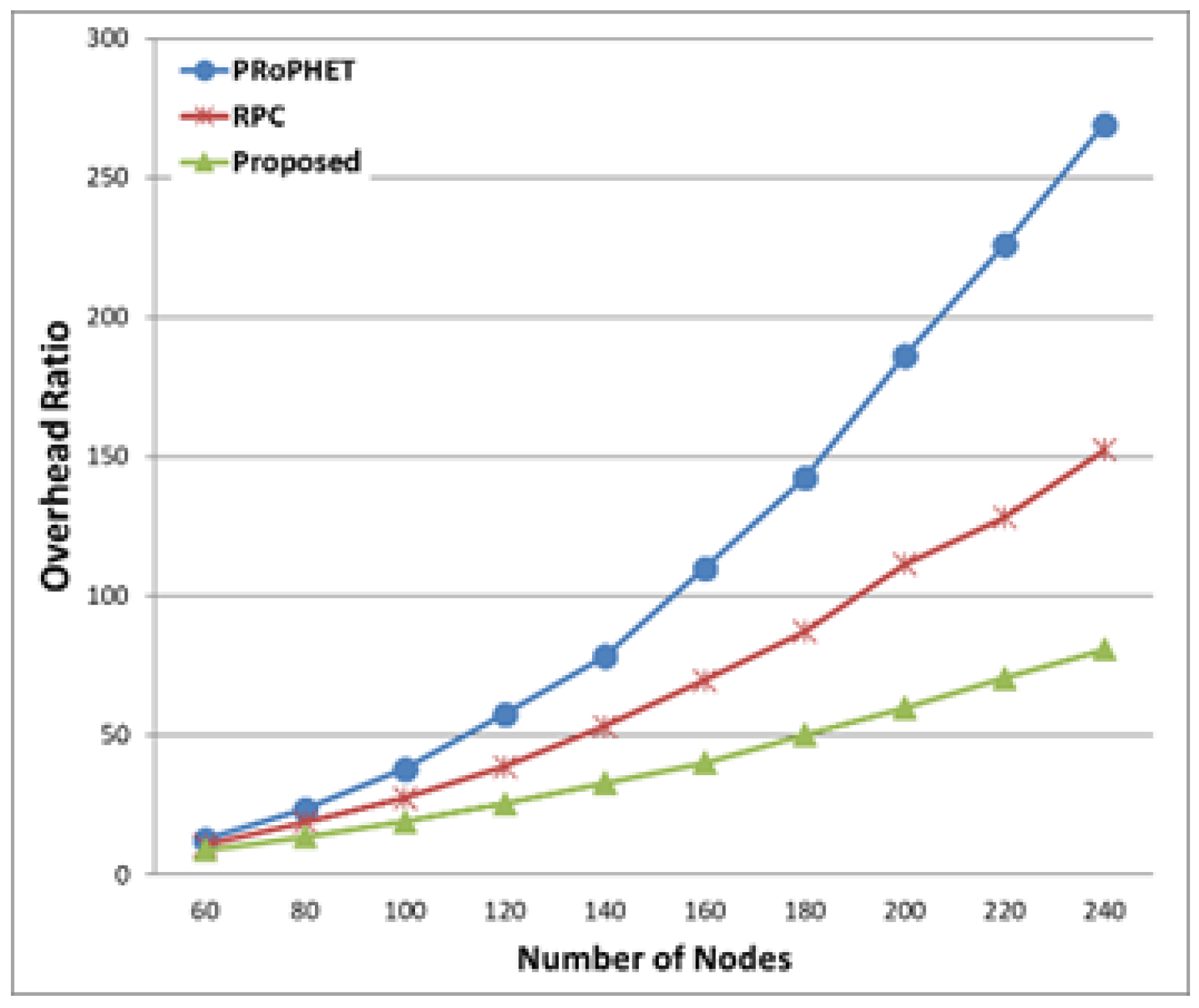
Figure 12, the overhead ratios of all three protocols increase as the number of nodes increase. In both PRoPHET and RPC, the overhead ratio increases due to more relayed messages and decreased number of delivered messages in Equation (9). The overhead ratio of the proposed protocol also increases, since the effect of increased relayed messages due to more number of nodes is more dominant that the effect of more delivered messages. The proposed protocol has smaller overhead ratio than both PRoPHET and RPC.
As shown in
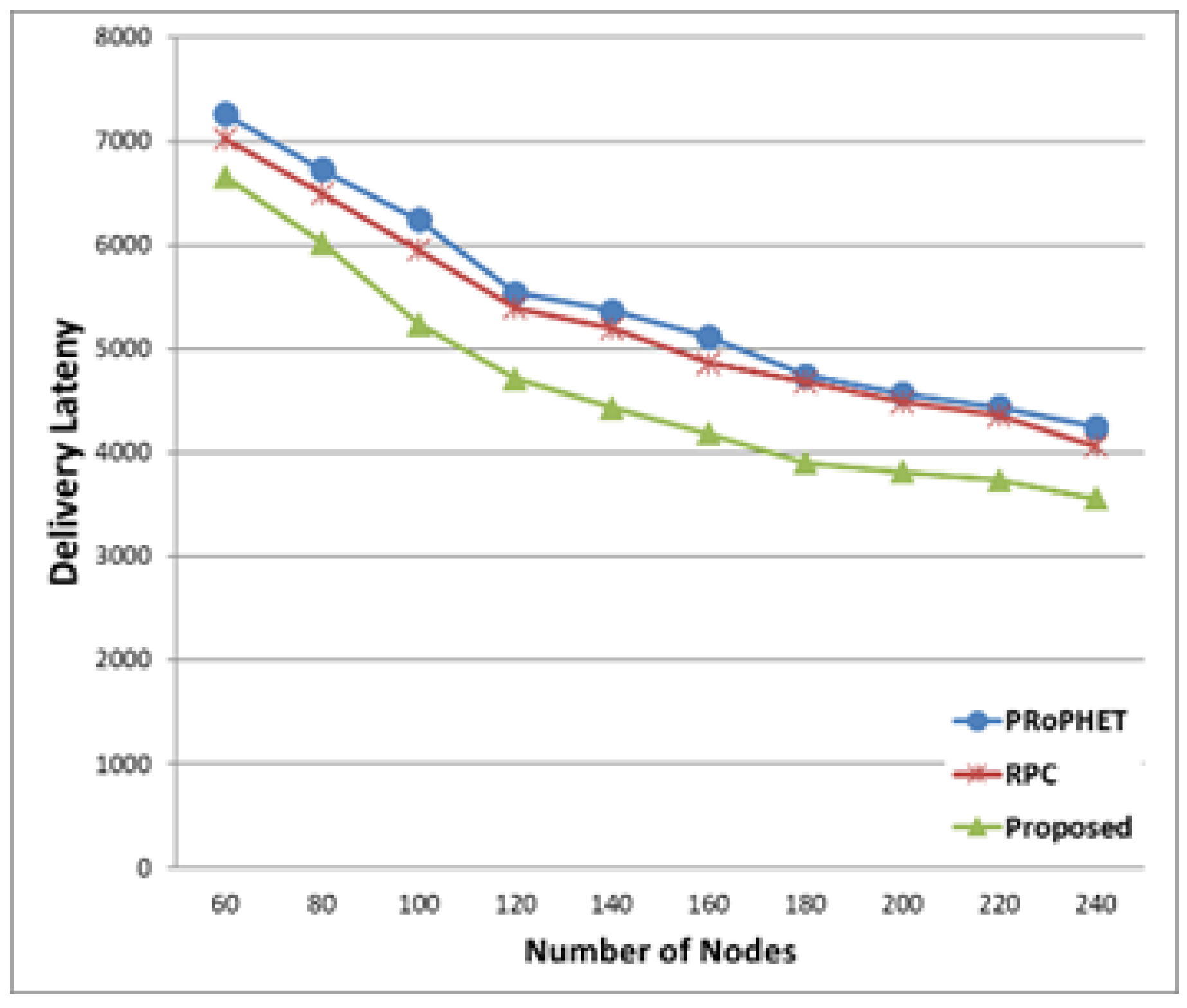
Figure 13, the delivery latencies of all three protocols decrease as the number of nodes increases, since more contacts are possible when the number of nodes is higher and messages can be delivered more quickly. The proposed protocol has smaller delivery latency than both PRoPHET and RPC.