Hybrid Destination-Based Jamming and Opportunistic Scheduling with Optimal Power Allocation to Secure Multiuser Untrusted Relay Networks
Abstract
:1. Introduction
1.1. Background
1.2. Related Works
1.3. Motivation and Contributions
- To harvest the MUD while satisfying the security constraint, we propose to apply the DJOS scheme in the considered multiuser untrusted AF relay networks with VGR. Under Rayleigh fading channels, we first derive a new closed-form approximated SOP expression for the considered system with DJOS. Note that an analytical SOP expression for multiple untrusted relay networks with VGR scheme has already derived in [26]. However, as we explained before, both the derivation method and the conclusion in [26] cannot be directly extended to the single-user and single-untrusted-relay case which has been included and studied in this paper.
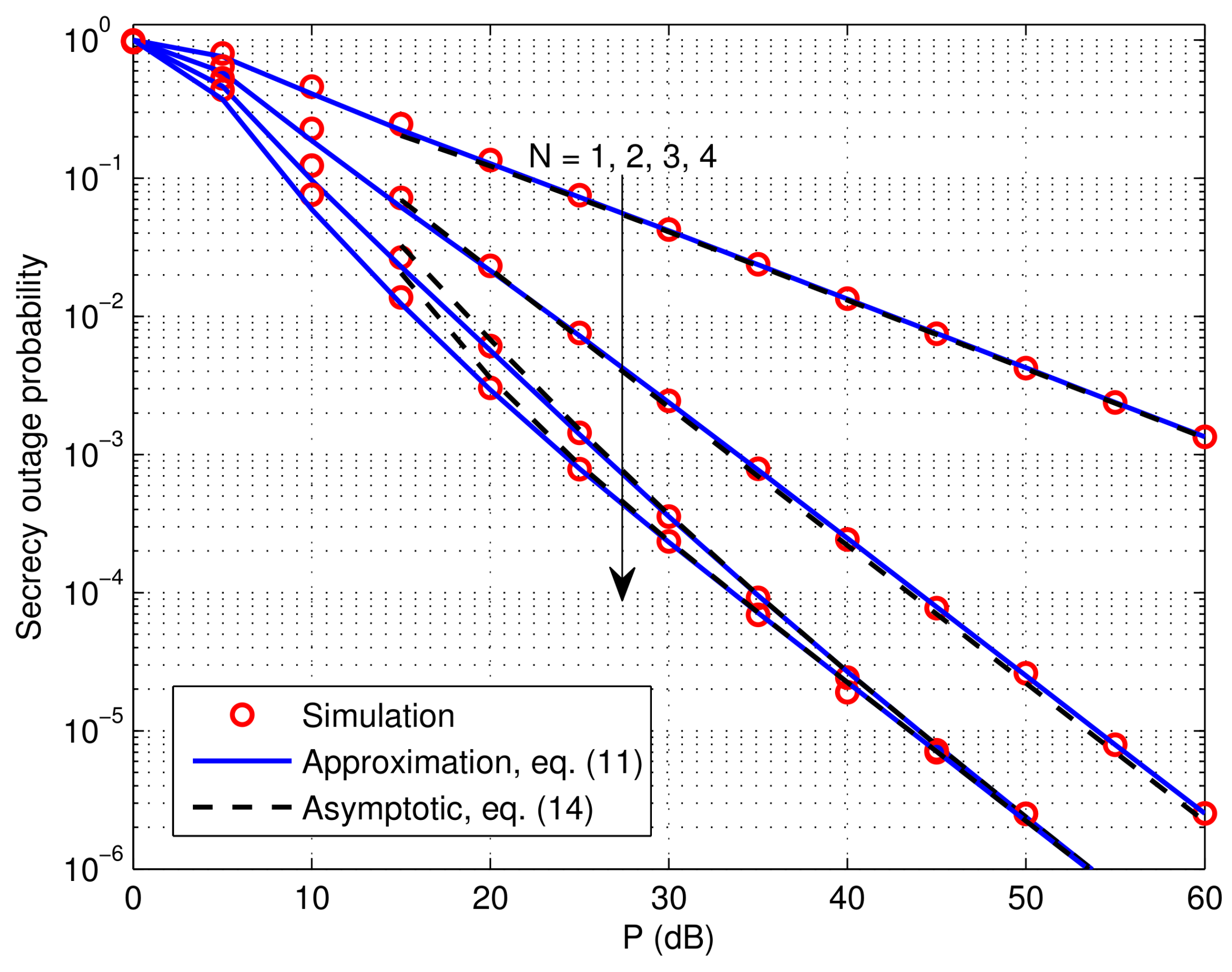
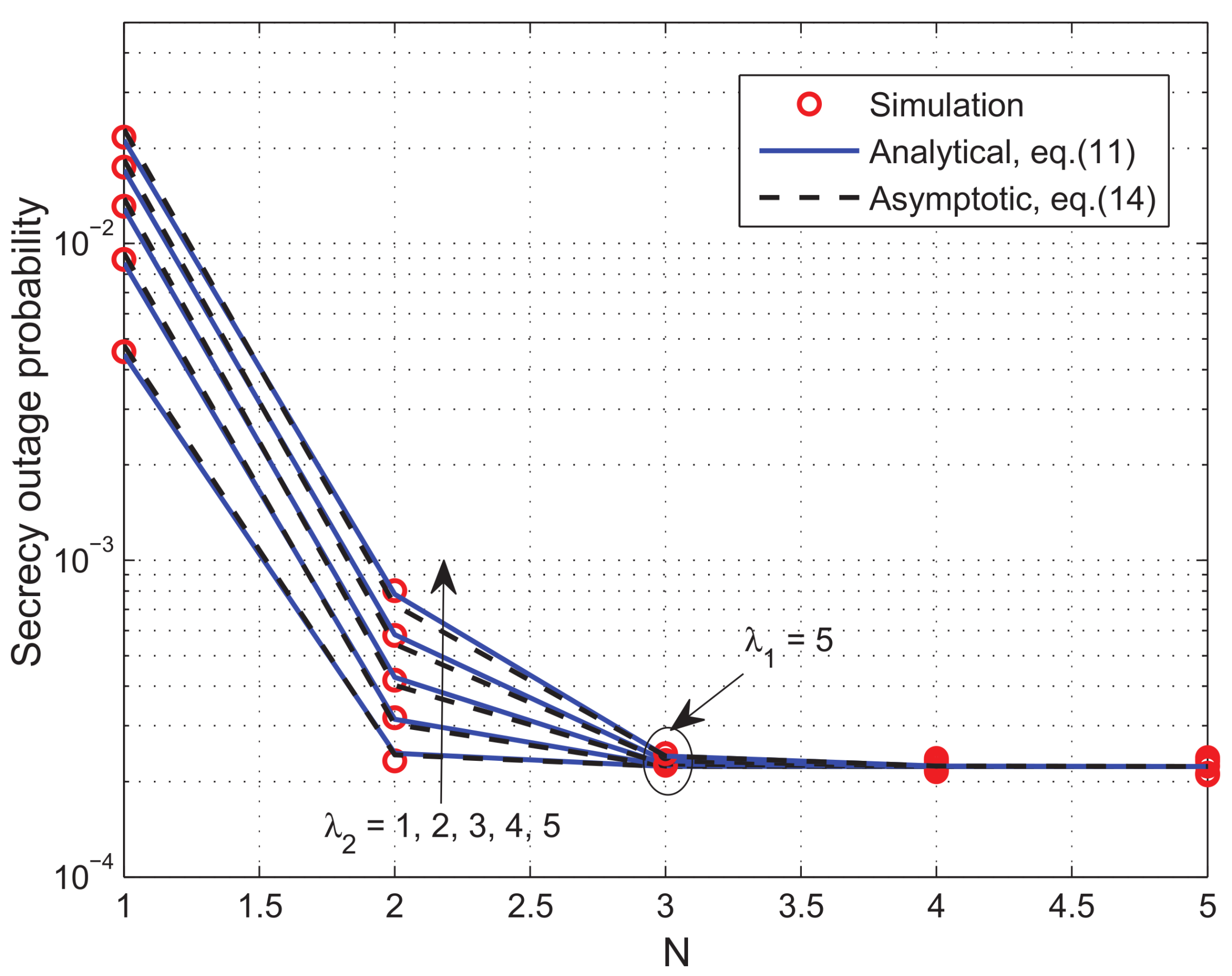
- To gain further insights, we then present the asymptotic SOP expression and prove that the achievable secrecy order is , where N denotes the number of destinations (users) (In this paper, the diversity order only mathematically indicates the curve slope of the outage performance metric studied at high SNRs. Prior works [8,20,24,26] have confirmed that the (secrecy) diversity order behavior in terms of SOP in cooperative relaying networks with security requirement is very different from the diversity order behavior in terms of connection outage probability (COP) in scenarios without security requirement). That is, for the single-user network (), the achievable secrecy diversity order in terms of SOP is 1/2, while with DJOS, the secrecy diversity order in multiuser networks () can be improved from 1/2 up to full secrecy diversity order of 1. Thus, MUD has been harvested by the OS strategy. It is worth noting that our rigorous mathematical analyses explicitly show that the obtained secrecy diversity order for the the typical single-untrusted-relay network with VGR is actually 1/2, rather than 1 as revealed in the multi-untrusted-relay case [26]. Therefore, our theoretical analysis on the single-untrusted-relay network supplements and complements the results in [26].
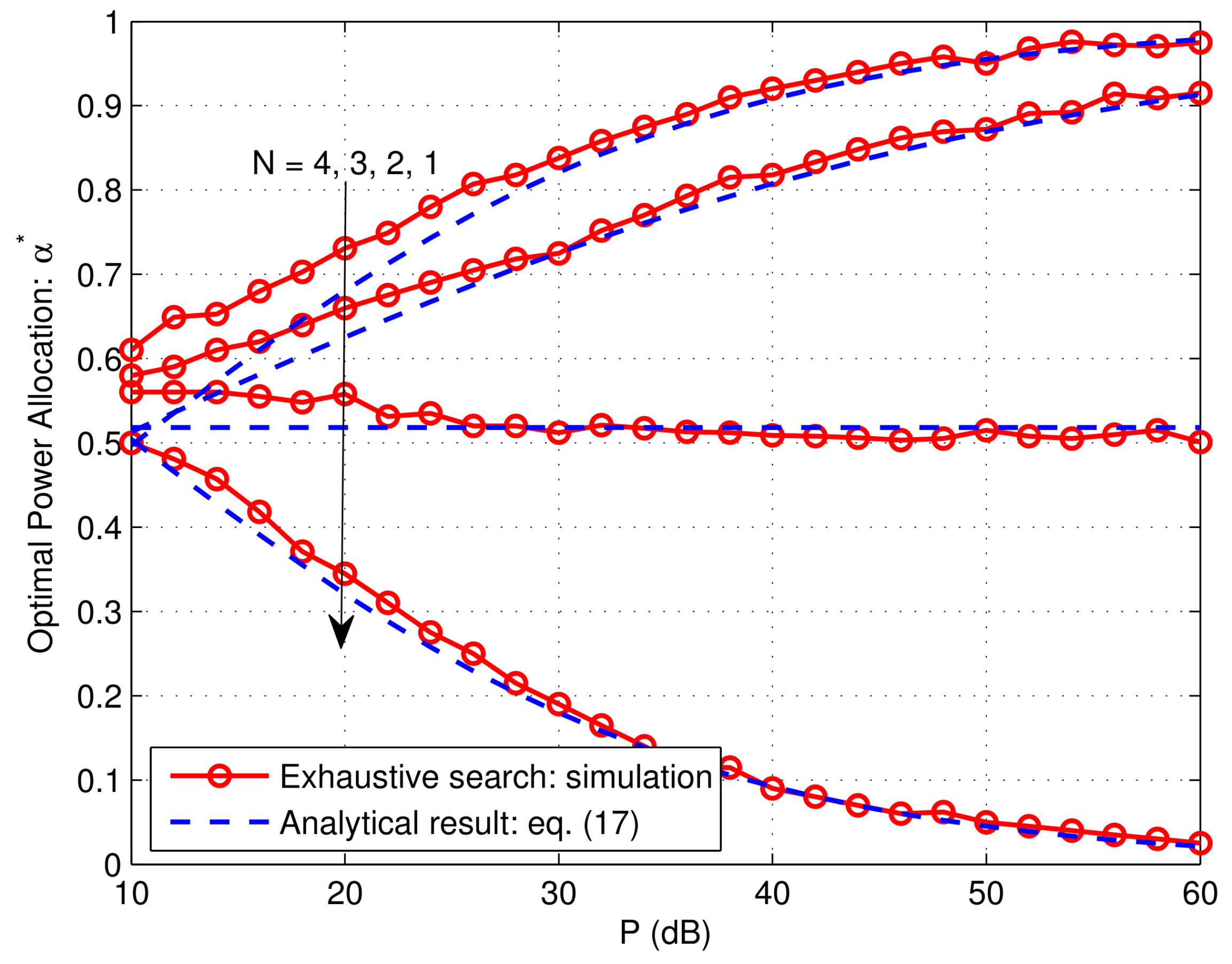
- Finally, we propose an asymptotically OPA scheme to minimize the asymptotic SOP. Interestingly, with the proposed OPA scheme, we find that the system secrecy diversity order can be improved from (without OPA) to . This conclusion provides some new findings that allow us to understand the impact of power allocation on the SOP performance. Specifically, for the case, our OPA scheme can help to improve the secrecy diversity order from 1/2 up to 2/3. It is well-known that the application of OPA in conventional trusted relay networks can only help to improve the array gain rather than the diversity gain/order [31]. This is because full diversity order of 1 is already obtained there even without OPA. However, our work explicitly show that, in the untrusted relay case, the effect of OPA is to increase the secrecy diversity order. It is intuitive that the diversity order deterioration due to eavesdropping has left some space for OPA to improve the diversity order. Moreover, when , we prove that OPA does not affect the secrecy diversity order. This is because full secrecy diversity order of 1 is already obtained by the OS scheme even without OPA. However, as we will show in Section 5, the effect of OPA is to increase the secrecy array gain and hence significantly reduces the SOP.
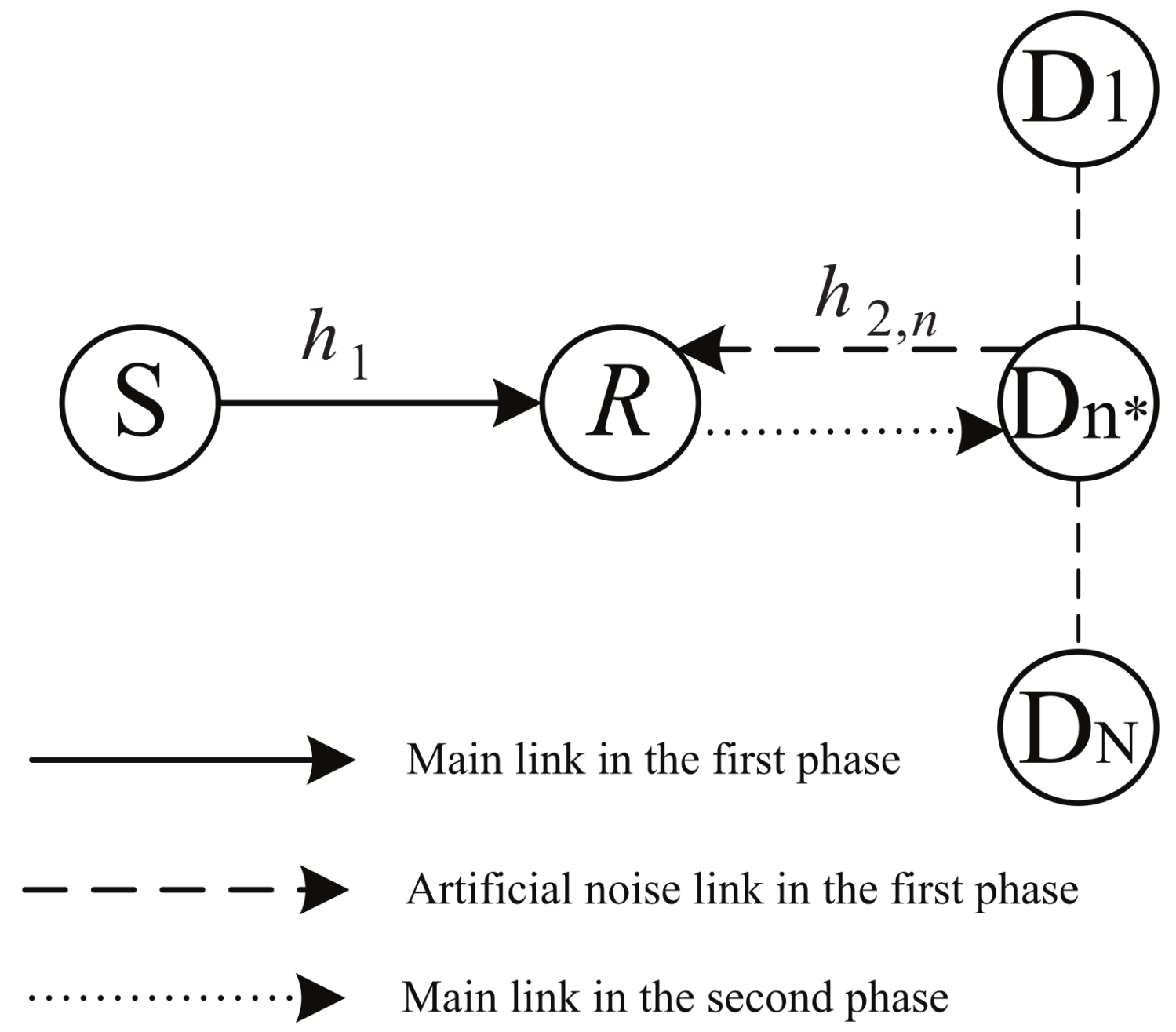
2. System Model
3. Opportunistic Scheduling Scheme
4. Secrecy Outage Performance Analysis
4.1. Approximated Secrecy Outage Probability
4.2. Asymptotic Secrecy Outage Probability
4.3. Asymptotic Optimal Power Allocation
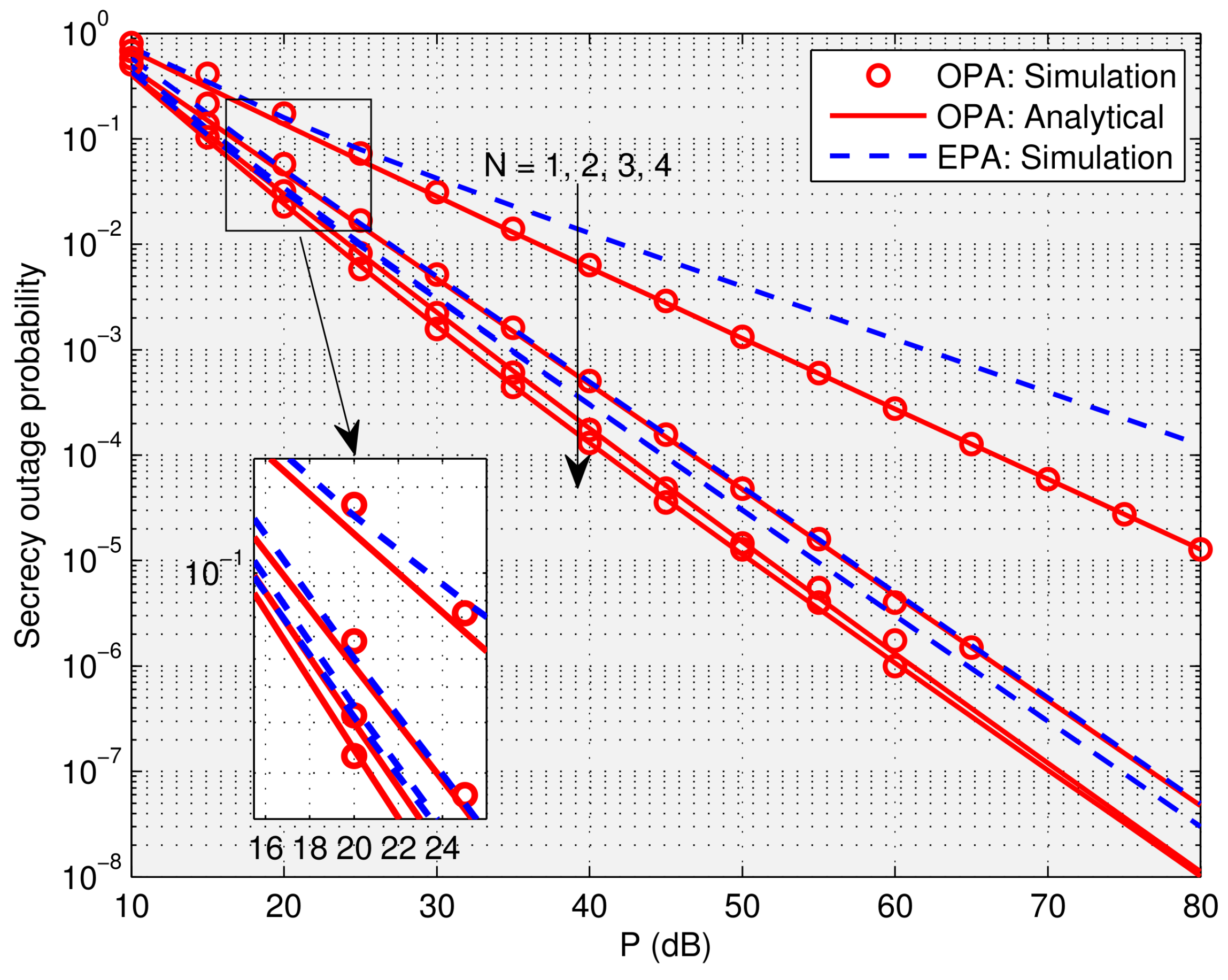
5. Numerical Results and Discussions
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Appendix A. Proof of Theorem 1
Appendix A.1. Derivation of J1 in Equation (12):
Appendix A.2. Derivation of J3 in Equation (13):
Appendix B. Proof of Theorem 2
Appendix B.1. Asymptotic analysis of J1 in Equation (12)
Appendix B.2. Asymptotic analysis of J2 in Equation (13)
Appendix C. Proof of Theorem 3
References
- Koyluoglu, O.O.; Koksal, C.E.; Gamal, H.E. On secrecy capacity scaling in wireless networks. IEEE Trans. Inf. Theory 2012, 58, 3000–3015. [Google Scholar] [CrossRef]
- Ding, Z.; Leung, K.K.; Goeckel, D.L.; Towsley, D. On the application of cooperative transmission to secrecy communications. IEEE J. Sel. Areas Commun. 2012, 30, 359–368. [Google Scholar] [CrossRef]
- Fan, L.; Yang, N.; Duong, T.Q.; Elkashlan, M.; Karagiannidis, G.K. Exploiting Direct Links for Physical Layer Security in Multiuser Multirelay Networks. IEEE Trans. Wirel. Commun. 2016, 15, 3856–3867. [Google Scholar]
- Hoang, T.M.; Duong, T.Q.; Suraweera, H.A. Cooperative beamforming and user selection for improving the security of relay-aided systems. IEEE Trans. Wirel. Commun. 2015, 63, 5039–5051. [Google Scholar]
- Krikidis, I.; Thompson, J.S.; McLaughlin, S. Relay selection for secure cooperative networks with jamming. IEEE Trans. Wirel. Commun. 2009, 8, 5003–5011. [Google Scholar]
- Huang, J.; Swindlehurst, A.L. Cooperative jamming for secure communications in MIMO relay networks. IEEE Signal Process. Lett. 2011, 59, 4871–4884. [Google Scholar]
- Dong, L.; Han, Z.; Petropulu, A.; Poor, H.V. Improving wireless physical layer security via cooperating relays. IEEE Trans. Signal Process. 2010, 58, 1875–1888. [Google Scholar]
- Ding, Z.; Leung, K.K.; Goeckel, D.L. Opportunistic relaying for secrecy communications: Cooperative jamming vs. relay chatting. IEEE Trans. Wirel. Commun. 2011, 10, 1725–1729. [Google Scholar]
- Liu, Y.; Li, J.; Petropulu, A.P. Destination assisted cooperative jamming for wireless physical-layer security. IEEE Trans. Inf. Forensics Secur. 2013, 8, 682–694. [Google Scholar]
- Deng, H.; Wang, H.M.; Guo, W. Secrecy transmission with a helper: To relay or to jam. IEEE Trans. Inf. Forensics Secur. 2015, 10, 293–307. [Google Scholar]
- Wang, H.M.; Luo, M.; Xia, X.G. Joint cooperative beamforming and jamming to secure AF relay systems with individual power constraint and no eavesdropper’s CSI. IEEE Signal Process. Lett. 2013, 20, 39–42. [Google Scholar]
- Wang, C.; Wang, H.M.; Xia, X.G. Hybrid opportunistic relaying and jamming with power allocation for secure cooperative networks. IEEE Trans. Wirel. Commun. 2015, 14, 589–605. [Google Scholar]
- Park, K.; Wang, T.; Alouini, M. On the jamming power allocation for secure amplify-and-forward relaying via cooperative jamming. IEEE J. Sel. Areas Commun. 2013, 31, 1741–1750. [Google Scholar]
- Jeong, C.; Kim, I.M.; Kim, D.I. Joint secure beamforming design at the source and the relay for an amplify-and-forward MIMO untrusted relay system. IEEE Trans. Signal Process. 2012, 60, 310–325. [Google Scholar]
- Mo, J.; Tao, M.; Liu, Y. Secure beamforming for MIMO two-way communications with an untrusted relay. IEEE Signal Process. Lett. 2014, 62, 2185–2199. [Google Scholar]
- He, X.; Yener, A. Cooperation with an untrusted relay: A secrecy perspective. IEEE Trans. Inf. Theory 2014, 56, 3807–3827. [Google Scholar]
- Sun, L.; Zhang, T.; Li, Y.; Niu, H. Performance study of two-hop amplify-and-forward systems with untrustworthy relay nodes. IEEE Trans. Veh. Technol. 2012, 61, 3801–3807. [Google Scholar]
- Ju, M.C.; Kim, D.H.; Hwang, K.S. Opportunistic transmission of nonregenerative network with untrusted relay. IEEE Trans. Veh. Technol. 2015, 64, 2703–2709. [Google Scholar]
- Hu, H.; Gao, Z.; Liao, X. Secure Communications in CIoT Networks with a Wireless Energy Harvesting Untrusted Relay. Sensors 2017, 17, 2023. [Google Scholar]
- Zhang, S.; Fan, L.; Peng, M.; Vincent Pooret, H. Near-optimal modulo-and-forward scheme for the untrusted relay channel. IEEE Trans. Inf. Theory 2016, 62, 2545–2556. [Google Scholar]
- Xiong, J.; Cheng, L.; Ma, D. Destination aided cooperative jamming for dual-hop amplify-and-forward MIMO untrusted relay systems. IEEE Trans. Veh. Technol. 2016, 65, 7274–7284. [Google Scholar]
- Huang, J.; Mukherjee, A.; Swindlehurst, A.L. Secure communication via an untrusted non-regenerative relay in fading channels. IEEE Trans. Signal Process. 2013, 61, 2536–2550. [Google Scholar]
- Wang, W.; Teh, K.C.; Li, K.H. Relay Selection for Secure Successive AF Relaying Networks With Untrusted Nodes. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2466–2476. [Google Scholar]
- Ding, F.; Wang, H.; Zhang, S. Multiuser untrusted relay networks with joint cooperative jamming and opportunistic scheduling under perfect and outdated CSI. Electron. Lett. 2016, 52, 1925–1927. [Google Scholar]
- Kalamkar, S.S.; Banerjee, A. Secure communication via a wireless energy harvesting untrusted relay. IEEE Trans. Veh. Technol. 2017, 66, 2199–2213. [Google Scholar]
- Kim, J.B.; Lim, J.; Cioff, J.M. Capacity scaling and diversity order for secure cooperative relaying with untrustworthy relays. IEEE Trans. Wirel. Commun. 2015, 14, 3866–3876. [Google Scholar]
- Wang, L.; Elkashlan, M.; Huang, J.; Tran, N.H.; Duong, T.Q. Secure transmission with optimal power allocation in untrusted relay networks. IEEE Wirel. Commun. Lett. 2014, 3, 289–292. [Google Scholar]
- Kuhestani, A.; Mohammadi, A.; Noori, M. Optimal power allocation to improve secrecy performance of non-regenerative cooperative systems using an untrusted relay. IET Commun. 2016, 10, 962–968. [Google Scholar]
- Yao, R.; Xu, F.; Mekkawy, T. Optimised power allocation to maximise secure rate in energy harvesting relay network. Electron. Lett. 2016, 52, 1879–1881. [Google Scholar]
- Kim, S.I.; Kim, I.M.; Heo, J. Secure transmission for multiuser relay networks. IEEE Trans. Wirel. Commun. 2015, 14, 3724–3737. [Google Scholar]
- Ikki, S.S.; Aissa, S. A study of optimization problem for amplify-and-forward relaying over Weibull fading channels with multiple antennas. IEEE Commun. Lett. 2011, 15, 1148–1151. [Google Scholar]
- Zhang, S.; Liew, S.; Lam, P. Hot topic: Physical-layer network coding. In Proceedings of the ACM Mobicom, Dresden, Germany, 23–29 September 2006; pp. 1–5. [Google Scholar]
- Popovski, P.; Yomo, H. Wireless network coding by amplify-and-forward for bi-directional traffic flows. IEEE Commun. Lett. 2007, 11, 16–18. [Google Scholar]
- Liu, P.; Kim, I.M. Performance analysis of bidirectional communication protocols based on decode-and-forward relaying. IEEE Trans. Commun. 2010, 58, 2683–2696. [Google Scholar]
- Yang, N.; Elkashlan, M.; Yuan, J. Outage probability of multiuser relay networks in Nakagami-m fading channels. IEEE Trans. Veh. Technol. 2010, 59, 2120–2132. [Google Scholar]
- Singh, K.; Gupta, A.; Ratnarajah, T.; Ku, M.-L. A General Approach Toward Green Resource Allocation in Relay-Assisted Multiuser Communication Networks. IEEE Trans. Wirel. Commun. 2018, 17, 848–862. [Google Scholar]
- Singh, K.; Gupta, A.; Ratnarajah, T. QoS-driven resource allocation and EE-balancing for multiuser two-way amplify-and-forward relay networks. IEEE Trans. Wirel. Commun. 2017, 16, 3189–3204. [Google Scholar]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products, 7th ed.; Academic Press: New York, NY, USA, 2007. [Google Scholar]
- Hemachandra, K.T.; Beaulieu, N.C. Outage analysis of opportunistic scheduling in dual-hop multiuser relay networks in the presence of interference. IEEE Trans. Commun. 2013, 61, 1786–1796. [Google Scholar]
- Abramowitz, M.; Stegun, I.A. Handbook of Mathematical Functions with Formulas, Graphs, and Mathematical Tables, 7th ed.; Dover: Mineola, NY, USA, 1972. [Google Scholar]
- Karagiannidis, G.K.; Lioumpas, A.S. An improved approximation for the Gaussian Q-function. IEEE Commun. Lett. 2007, 11, 644–646. [Google Scholar]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ding, F.; Zhou, Y. Hybrid Destination-Based Jamming and Opportunistic Scheduling with Optimal Power Allocation to Secure Multiuser Untrusted Relay Networks. Information 2018, 9, 84. https://doi.org/10.3390/info9040084
Ding F, Zhou Y. Hybrid Destination-Based Jamming and Opportunistic Scheduling with Optimal Power Allocation to Secure Multiuser Untrusted Relay Networks. Information. 2018; 9(4):84. https://doi.org/10.3390/info9040084
Chicago/Turabian StyleDing, Fan, and Yongming Zhou. 2018. "Hybrid Destination-Based Jamming and Opportunistic Scheduling with Optimal Power Allocation to Secure Multiuser Untrusted Relay Networks" Information 9, no. 4: 84. https://doi.org/10.3390/info9040084



