Abstract
Our research builds upon a theory of emerging-state actors. We look to apply the theory in analyzing intervention and containment policies to use against emerging-state actors, using the Islamic State of Syria & Iraqi (ISIS) as the case study. We show utility across four military applications of simulation: understanding, forecasting and responding to adversary and societal behavior; understanding enemy command and control structures; and analyzing, forecasting and planning courses-of-action (COA). To do this, we created two baseline scenarios—one replicating the historical foreign intervention against ISIS and a counter-factual where no foreign intervention occurred. We then conducted a suite of experiments on contemporary military intervention policies in isolation, combination, at different timing windows and under hypothetical “best case” conditions as well as operationally constrained. Insights of these experiments’ tests include the influence of ethnographic envelopes, timing windows, the importance of actor legitimacy and the marginally diminishing returns of combat actions. Finally, we test a policy based on emerging-state actor theory incorporating these insights against the contemporary policies, historical baseline and two falsification policies. The emerging-state actor COA performs significantly better than others. Our research contributes a simulation, called the Emerging-State Actor Model (E-SAM). This simulation includes military, economic, political, social and information aspects (known asDIME-PMESII simulations) for both researchers and military planners concerned with irregular conflict.
1. Introduction
The rapid rise of the Islamic State of Syria & Iraq (ISIS) and its staying power created great uncertainty in terms of regional stability. Although its predecessor Al-Queda in Iraq presented a strong threat via a traditional insurgency, ISIS appeared to work in an entirely different manner. In a brief period, it managed to capture two-thirds of Iraq and a third of Syria. Even when confronted with a multi-party intervention by regional and global powers such as Iran, Russia and the United States, ISIS showed remarkable staying power. Earlier research on the theory of emerging-state actors has proposed that ISIS is one such case of these actors [1]. Furthermore, that an emerging-state actor functions differently than a classical insurgency and may be resilient to counter-insurgency strategies. The question policymakers must answer is how to confront, contain and or mitigate the growth and risk of emerging-state actors such as ISIS.
Our research uses a robust simulation called the Emerging-State Actor Model (E-SAM) to examine ISIS as an emerging-state actor and uses that model to examine a portfolio of policy options under realistic conditions [1]. First, a review of the performance of ISIS is provided, followed by a literature review of articles detailing simulation models for both research and military planning in irregular conflict. This review identifies seven potential military applications for simulation models and we demonstrate four of them with E-SAM: understanding, forecasting and responding to adversary and societal behavior; understanding enemy command and control structures; and analyzing, forecasting and planning courses-of-action (COA). Next, we review a previously published emerging-state actor theory in both written and causal loop form. To demonstrate the four applications, we constructed two baseline scenarios using E-SAM. The first replicates the baseline historical case where ISIS confronted multiple local and foreign interventions, eventually losing most if not all their territory and fighters. Nearly 108,000 foreign troops representing the interventions of Iran, Turkey, the United States coalition, Russia as well as the local Arab Shias and Kurdish Sunni’s incorporated in these efforts are included. This scenario, called “baseline historical” looks to accurately replicate what happened from a historical perspective. (See Supplementary Materials Section B-8 Behavior Reproduction Results.) The second baseline, the “baseline without intervention”, is a counter-factual that assumes no such foreign intervention occurred. It takes the same initial conditions of the baseline historical, contains the same policy choices of the Red and Green actor, but removes the incremental addition of 108,000 foreign troops into the theater that exist in the historical baseline. The baseline historical and baseline without intervention allow a policy space for evaluation of intervention options. An intervention policy that performs better than the baseline historical may have promise while one that performs worse than the counter-factual is clearly ineffective. Next, we test contemporary solutions proposed at the time of ISIS’s rise in a hypothetical ‘best-case’ scenario absent operational constraints. We then discuss the insights generated from these experiments. Then, we test policies in a joint portfolio, and at different timing intervals. Finally, we create an intervention policy designed leveraging emerging-state actor theory and systems thinking. We test this policy against the baseline scenarios and falsified versions of itself to build confidence that results arise from emerging-state actor theory and not some other dynamic. The paper finishes with a conclusion that summarizes the insights, discusses weaknesses and discusses future opportunities.
2. Problem Description
About a year after the US invasion of Iraq in 2003, Al-Queda in Iraq (AQI) appeared as a potent threat to stability operations. AQI never governed openly in the territory it influenced, instead conducting a classic guerilla insurgency. The strength of AQI peaked in 2006 before declining as the result of three circumstances: a troop surge of US Forces, a Sunni–Shia civil war that AQI helped spark and the indigenous resistance to AQI growing out of the Anbar Awakening. From 2008–2012, the organization almost declined to the point of non-existence.
However, in 2013, the Islamic State of Iraq and Syria (ISIS) took control of Ar-Raqqah, a medium sized city in eastern Syria with an estimated 13,200 combatants (See Supplementary Materials Section D-6 for details on all scenarios.) By late 2014 ISIS had grown to between 50,000–80,000 combatants, taken control of 30% of the territory in Syria and Iraq and threatened regional stability. It took three years of conflict including with local State Actors (Iraq and Syria), indigenous opposition groups and a multi-lateral, albeit uncoordinated, international intervention to defeat ISIS territory. Even after its losses in Iraq and Syria ISIS stays a global-insurgency capable of engaging in terrorist acts and threatening stability through its affiliates in over a dozen countries. What policies would’ve limited, or stopped altogether, ISIS’s growth? Once ISIS established itself, what policies would remain effective for containing it?
3. Literature Review
In 1916, Frederick Lanchester first used differential equations as a method of forecasting battle outcomes based on force ratios. Since then academics and militaries have looked to use increasingly sophisticated mathematical tools and computer simulations to understand the uncertainty of operations and evaluate policies and strategies. Irregular conflicts, which include asymmetric dynamics and nonlinear relationships are often the most difficult to understand. Academics and industry showed the early promise of using sophisticated computer simulations. In the 1950s, Jay Forrester pioneered modeling complex systems with a new method, called system dynamics, at MIT. Early models focused on corporate, urban and even-macro global problems [2] (p. 129). While the use of Lanchester equations in various forms still dominated military work, academic Khalid Saeed conducted an early multi-polar examination of irregular conflict in 1983. The paper analyzed how the conditions that give rise to internal violence in developing economies and how social and political factors influenced long-term growth. Instability in the form of dissidence and subversive activities were modeled, but not explicitly as a violent insurgency or with resources becoming controlled by the dissidents [3].
In 1995 the Department of Defense (DoD) created the Defense Modeling and Simulation Office (DMSO) and gave it the task of organizing and focusing efforts on modeling and simulation [2] (pp. 48–49). Thirteen years later, in 2008, the National Research Council (NRC), an arm of the National Academy of Sciences, conducted a study at the request of the DoD on the ‘state-of-the-art’ and current challenges of military simulations that focused on behavioral and organizational depictions of conflict [2].
The NRC categorized seven potential applications for simulation models in the military:
“1. Analysis, forecasting and planning courses-of-action (COA).2. Understanding, forecasting and responding to adversary behavior.3. Understanding, forecasting and responding to societal behavior.4. Understanding enemy command and control structures.5. Training and mission rehearsal.6. Military systems development, evaluation and acquisition.7. Enabling command and control weapons systems”.[2] (pp. 34–44)
There are few models that can support one or more application in categories 1–4, considered key for policy analysis. Even more limited are those that could handle multiple different domains of interest (e.g., economic, politic, military, etc.) simultaneously. In addition, the release in 2000 of Sterman’s textbook on Business Dynamics showed sparked a new interest in complex system simulations [2] (p. 130). Especially within the DoD, system dynamics was viewed as an approach well suited for “for modeling diplomatic, information, military, and economic (DIME) actions, and political, military, economic, social, information, and infrastructure (PMESII) interactions” [2] (p. 130). The benefits of system dynamics for studying DIME-PMESII interactions was summarized as:
- Representing dynamic behaviors, including feedback and cross-connectivity over time.
- Ability to disaggregate structure into substructures to examine any level of detail.
- Leveraging interconnected structures and feedback that leads to emergent behavior.
- Simple structures that can be elaborated as analysis requires [2] (p. 133).
The limitations of system dynamics described by the NRC were a consequence of “its strong grounding in a mathematical description of the organizational dynamics (namely, first-order differential equations) (that) tends to preclude participation by researchers and modelers who are more linguistically and semantically oriented … [and another] … limitation is verification and validation, since these models are particularly easy to build by making simple assumptions about structures, feedback path, and parameter values, without ever relying on “real” data” [2] (p. 134).
Even models built on ‘real’ data with strong theoretical groundings had limitations in their predictive power. This led the NRC to caution that these simulations are best for forecasting rather than prediction. That:
“a model may be able to forecast the most likely range of outcomes of a potential course of action. It may be able to direct attention to situational variables that are known to be important but may have been overlooked in a particular engagement. A well-designed model may draw a decision maker’s attention to possible unintended consequences (“second-order effects”) of a planned course of action. But it will not be able to make point predictions, such as ‘If we take Action A, the adversary will attack at Point B early tomorrow morning with three simultaneous improvised explosive devices (IEDs).’ So we speak of models forecasting a range of outcomes, rather than making precise predictions”.[2] (p. 19)
This category of models is well suited then for supporting the first four applications of military simulations: analyzing and forecasting Courses of Action (COA); understanding, forecasting and responding to adversary or societal changes; and understanding enemy control structures. They are not as well suited for the final three applications: mission training and rehearsal; development and evaluation of military systems; and enabling command and control weapon systems.
Several early DIME-PMESII models were listed such as the Air Force Stabilization and Reconstruction Operations Model (SROM) which “analyzes the organizational hierarchy, dependencies, interdependencies, exogenous drivers, strengths, and weaknesses of a country’s PMESII systems using a complex set of interdependent system dynamics representations” [2] (p. 57). The Defense Advanced Research Projects Agency (DARPA) hosted two programs. The first was the Pre-Conflict Anticipation and Shaping (PCAS) program evaluating models for suitability in “forecasting the likelihood of nation-state collapse” [2] (p. 57). This was followed by the Integrated Crisis Early Warning System which sought to develop “state-of-the-art computational modeling capabilities that can monitor, assess, and forecast, in near-real time, a variety of phenomena associated with country instability” [2] (p. 57). In addition, very few system dynamic DIME-PMESII models of the time were listed as focusing on irregular or insurgent conflict.
As the Iraq and Afghanistan insurgencies continued to stymie progress attention turned to the ethnographic makeup of both insurgents and the populations in which they operated within. Lt. Col. Renzi in 2006 emphasized the need to provide local texture to these groups, advocating ethnographic intelligence a human terrain which shares “indigenous forms of association, local means of organization, and traditional methods of mobilization…or latent forms of social organization” to hostile organizations [4]. In addition, it wasn’t until 2010 that newer system dynamic models incorporating elements of the DIME-PMESII structure and focused on irregular conflict would become more publicly recognized and utilized outside the military.
In 2010, Turnley et al. specifically modeled an irregular warfare environment, enabling a computational representation of the interdependence between kinetic and non-kinetic aspects of a battlefield. The model highlights the interaction of latent structure as it is affected by kinetic activity, but Turnley does not model the organization of the insurgency itself as a key factor in the dynamics of how it operates [5].
In an infamous case, a model produced within the military on insurgent dynamics was leaked and misreported on by the New York Times, which mistook it for a power-point slide [6]. Never published, portions of the model were leaked. What appears to be an appendix explaining many of the causal loops in the “spaghetti diagram” surfaced as well. While it is a sophisticated approach to understanding the causal interactions between dynamic factors of an insurgency, and one can assume it could be simulated, no simulation runs were provided—nor is there enough detail in the leaked documents to replicate the model, articulate its key insights or answer whether it can support operational planning. A thirty page appendix with a high-level overview is attributed to Brett Pierson, a military Captain at the time, but has a “PA Consulting” copyright mark on it [7]. Due to the leaked nature and copyright, we didn’t incorporate elements of this model in creating E-SAM.
In 2011, Anderson used actual data from the Anglo-Irish War of 1919–1921 to model insurgency and counterinsurgency theories showing potential gaps in the theory when compared to simulation results. This achieved the application of understanding societal and adversary behavior and could even be used to forecast and evaluate COAs specific to insurgencies. However, the insurgency of the Anglo-Irish War represents a ‘classical’ insurgency that differs significantly from ISIS’s behavior as an emerging-state actor [8]. In addition, Anderson focused on intelligence collection (information) and military aspects of DIME-PMESII and did not model financial funding (economic) or social aspects. Finally, Anderson’s model is built on the theories and perspectives of Counterinsurgency (U.S. Army Field Manual 3-24 also referred to as FM 3-24), which precedes the rise of ISIS as a force that fought both openly and clandestinely. This meant the military applications within the DIME-PMESII framework are limited to countering opponents who fight in the same guerilla or unconventional manner as the IRA did. However, the Anglo-Irish and the IRA was never able to seize and hold territory this approach may not best represent the dynamics of a true emerging-state actor [8].
In 2013, Saeed et al. developed a generic structure to model political conflict, which could include insurgencies [9]. This model focused on the economic, military, political and social aspects of DIME-PMESII at a very aggregate level. Aimed at understanding a question of political-economy and decision-making of what drove Farmers to become Bandits or Soldiers, the model like Turnley focuses on decision-making and choices of the population, rather than the explicit structure of how an insurgency like ISIS might fight. Saeed’s model shows societal and adversary responses as dynamic behaviors and how they respond at an aggregate level—but cannot forecast detailed COA outcomes and does not go into the enemy’s command and control structure.
In 2014, Aamir presented a paper on modeling terrorist organizations using existing system dynamic models of business entities. Aamir showed parallels between the managerial challenges of the firm as being like those of terrorist organizations. This approach divided into sectors the “functions” of a terrorist or insurgent activity including Territory/Capital Management, Financial Resources, Population Support, Supply Management, Human Resources, and Attacks and Agency. As such, it well suited the applications of understanding adversary behavior and enemy command and control structures. However, the models Aamir used were from existing system dynamics literature on business models, built generically, rather than aiming to model the performance of any one insurgent group [10]. This limited them to exploring information, infrastructure and limited parts of social and military elements of the DIME-PMESII framework.
Our research began in 2014 by proposing a new theory of non-state actors engaging in irregular conflict, termed “emerging-state actor” using the case of ISIS. The theory states that emerging-state actors “uses methods of irregular warfare to capture territory to influence populations (“coercive power”), which it then attempts to govern in furtherance of its objective to become a functioning state (“legitimate power”)” [11].
This research led to the creation and refinement of a system dynamic model in the DIME-PMESII category designed to support the first four military applications for simulations. To allow military planners or researchers to simulate policies or courses of action (COA) and analyze the results, to understand and forecast both adversary and social behaviors and give detailed structure of enemy command and control. We limited the model to irregular conflicts. It considers how non-state actors compete with state-actors within a variety of terrains (physical as well as human terrains). It does not simulate conventional state-on-state conflict, although foreign state-actors can intervene on either side of the irregular conflict. Within the DIME-PMESII framework, E-SAM incorporates information, military, economic, political, and social aspects. It does not represent diplomacy or infrastructure to any detail. The level of aggregation is set at that of a theatre commander on either the state actor or non-state actor side of a conflict (or both if played as a wargame). The geography represented is at the level of a country or region. The policy choices available for analysis and evaluation are the allocation of resources among a variety of operational orders of military, civil and political nature but not the tactical execution of those orders that follows. The results of E-Sam then fell well inside the cautionary note of the NRC report that models should focus on forecasting and not predicting. E-SAM can explore a range of different outcomes, but the results are forecasts, not exact time-and-place predictions. Finally, documented and replicable, all the supporting materials of E-SAM are available in the Supplementary Materials. It relies on no classified information or sources.
In this paper, we use E-SAM in the first three applications of military simulation: to develop and analyze policies or COAs and to understand and forecast both adversary and social behaviors in response to such. It uses the ISIS case to explore a variety of intervention strategies to show how COAs designed with emerging-state actor theory in mind may have higher utility in certain circumstances than traditional counter-insurgency interventions.
4. The Emerging-State Actor Theory
Our research adopts the dynamic hypothesis that ISIS is an emerging-state actor, which differs significantly from a classical insurgency. Figure 1 shows a causal loop diagram of the theory [11].
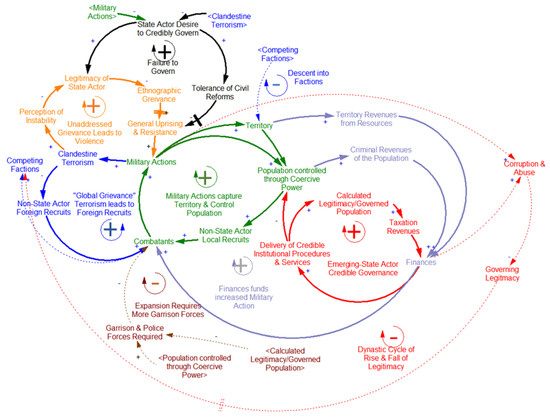
Figure 1.
Emerging-state actor theory causal loop diagram.
The theory expressed in this diagram is that as an emerging-state actor uses methods of irregular warfare to capture territory to influence populations (“coercive power”), which it then attempts to govern in furtherance of its objective to become a functioning state (“legitimate power”). Several propositions arise from this theory [11]:
- A failure of governance by the state-actor and inability to tolerate civil reforms decreases legitimacy, increases grievance and leads to general uprising and resistance.
- This resistance manifests first in the form of clandestine terrorism, which increases the perception of instability, further decreasing the legitimacy of the state. Likewise, violent acts reduce incentives of the State Actor to credibly govern the ethnographic group from within which these actions emerge.
- Local grievances bring combatants and a non-state actor either emerges or is drawn into conflict.
- The non-state actor uses combatants and finances to conduct military actions.
- As the non-state actor gains controlled population begins extracting coercive revenues through criminal activities and recruiting locally from within the controlled population.
- Within its territory, the non-state actor attempts to monopolize the use of force, taxation, control of movement, and regulation of the economy. By operating in a sovereign manner, the non-state actor shifts to an emerging state actor.
- Coercive revenues and territorial revenues are used to finance governing mechanisms, which can begin building legitimacy to shift the controlled population into a governed population.
- As the emerging-state actor gains a governed population, it also gains taxation revenue and increases its draw of non-local foreign recruits by propagandizing its non-local grievances, which may or may not align to local grievances.
- The loops complete into a positive feedback loop of exponential growth. More combatants mean more military actions, which means more territory and access to controlled populations, which can begin to be governed, fueling finances, which fund more combatants and military actions.
Negative loops limit the growth, the most immediate and pressing is the “Resistance and Uprising” loop. As ISIS controls more population, it needs more forces to garrison that population and prevent uprisings against their rule, this reduces the number of Combatants available to gain more territory. Another negative feedback loop, “Descent into Factions” has its precedence in ISIS’s own emergence within the Al-Queda global franchisee network splitting in 2013. Growth and size of any entity may lead to disagreements over both policy and personality, and if those factions are significant enough, it may break the emerging state actor apart. The Dynastic Cycle begins with the corruption and abuse of arbitrary power available to a state, like that described by Katouzian’s theory of arbitrary state and society [12]. The negative feedback loops of Descent into Factions and the Dynastic Cycle have a significant delay function and therefore may develop well after emerging-state actor has established itself. As modeled by Langarudi, the Katouzian dynastic cycle can take decades to manifest [12].
5. E-SAM and Baseline Scenarios in the ISIS Case
The Emerging-State Actor Model (E-SAM) is a system dynamics simulation model created to replicate conflict conditions for a variety of environments. The model consists of two sections: a strategic architecture of both the state government named the “Green Actor” and ISIS, named the “Red Actor”. The strategic architecture names the resources and capabilities that determine performance at any point in time. The second section is a World Model within which these two Actors compete against one another over control of a variety of ethnographic groups and with varying degrees of foreign intervention. Sub-systems representing the constants, parameters, information flow, and leadership decisions, behaviors and side-choosing of ethnographic groups, as well as the influence of other resource levels, all combine to affect the rates of change. The dynamics of strategic performance tie to reinforcing and balancing feedback interactions between these resources. This aggregate strategic architecture appears in Figure 2 [11].
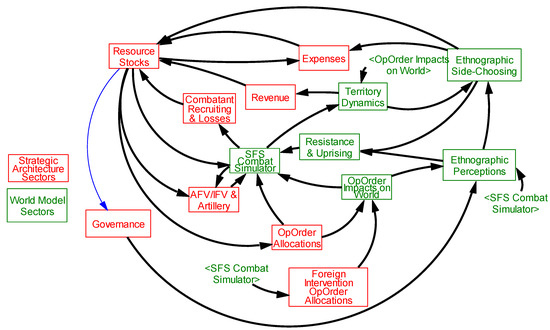
Figure 2.
Emerging-State Actor Model (E-SAM) strategic architecture and world model sectors.
We created two baseline scenarios. Both seek to replicate the conditions in Syria and Iraq beginning in 2010, the grievances of the Arab Sunnis that led to the rise and expansion of ISIS. The baseline historical scenario then includes the significant foreign interventions that occurred beginning in 2014. The baseline without intervention takes a counter-factual that this intervention never occurred and projects what might have occurred with ISIS absent foreign involvement. Through behavior tests, we gained confidence in the historical baseline as suitable to replicate ISIS’s behavior. (See Supplementary Materials Section B Validation & Confidence Building.) Comparing it against the baseline without intervention in Figure 3 allows a reasonable comparison to forecast of what might have happened had foreign actors not intervened in the conflict.
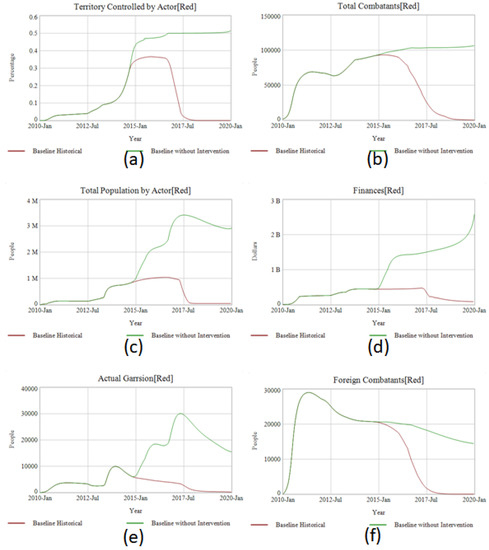
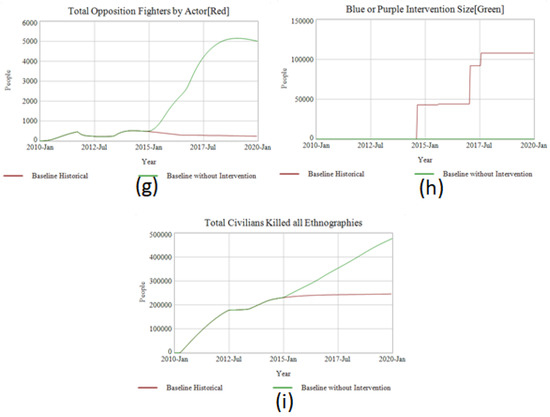
Figure 3.
Comparison between baseline and baseline without intervention across a dashboard of primary measures including (a) territory controlled, (b) total combatants, (c) total population, (d) finances, (e) actual garrison, (f) foreign combatants, (g) total opposition fighters by actor, (h) blue or purple intervention size (from Green’s perspective), and (i) total civilians killed all ethnographies.
We know what happened in the historical case—under the weight of ever-increasing local and foreign opposition (Figure 3h) ISIS’s territorial holdings collapsed (Figure 3a) leading to the sizeable reduction of its forces (Figure 3b). In the counter-factual, however, ISIS, without foreign intervention, can continue gaining territory against the joint governments of Iraq and Syria. However, as predicted by the emerging-state actor theory above, the growth in ISIS’s controlled population needs ever more garrisoning troops (Figure 3e) and sparks more local opposition (Figure 3g). This plus the movement of ISIS across the ethnographic envelope from Sunni Arab areas into regions more populated by Shia Arabs and Sunni Kurds prevents ISIS from gaining the same local support. These tensions reach an equilibrium point in the model around ~50% of all of Iraq and Syria (somewhere between Kobani and Aleppo in Syria and with most of Anbar in Iraq). At this point, there are 3 million people underneath ISIS’s rule (Figure 3c) from a conflict that has created 500,000 casualties (Figure 3i). ISIS has a force of 100,000 (Figure 3b). Most worrisome, ISIS continues generating free cash flow measured in the billions of dollars from oil-sales (Figure 3d). In the E-SAM model, these funds sent abroad fund overseas fuel growth-strategy through acquisition of a global network to both compete with Al-Queda and other state-actors world-wide.
This historical baseline will be the baseline scenario to test policies for intervention and containment. The baseline without intervention identifies results that perform no better, or worse, than if there was never any intervention at all.
6. ‘Best Case’ Tests of Policies in Isolation
During the period of first conflict with ISIS many policy ideas arose for consideration on how to contain or reverse ISIS’s growth. The policy of doing nothing and hoping ISIS would collapse on its own is the baseline without intervention. We excluded politically unviable policies—so we did not test a full-scale ground invasion by US forces for example. Each test is identified as the Best Case Policy (BCP) and then the primary focus of that intervention, e.g., “BCP Oil.” This results in six major policies with some having differing levels of implementation resulting in twelve policies:
- Use airpower to attack ISIS’s oil production (BPD) to decrease revenue to ISIS Finances (BCP Oil).
- Convince allies not to pay ransom for ISIS hostages to decrease revenue to ISIS Finances (BCP Ransom).
- Embed military advisers and personnel to improve the fighting quality of forces opposing ISIS (BCP Embedded Advisers A: 10,000; B: 25,000 and C: 50,000).
- Return military advisers to Iraq to train and oversee counter-terrorism operations against ISIS (BCP Counter Terrorism A: 5000; B: 10,000 and C: 15,000).
- Work to reduce the effectiveness of foreign recruiting for ISIS (BCP Foreign Recruiting A: 50% and B: 100%).
- Use close air support missions to aid opposing forces engaged in combat with ISIS (BCP Air Campaign A: 10% and B: 50%).
These policies occur in a “hypothetical best case” scenario. This means that they lack realistic operational constraints and begin at the earliest plausible intervention time given ISIS’s history. Normal deployment times for Blue Personnel deploying to a country are six months, for these tests, this is reduced to one month. In addition, no Blue Personnel will be involved in the logistics, administration and headquarters components (T3R) of a deployment. Meaning that 100% of foreign troops implement the policy recommended. Although this may be applicable in some cases of Special Forces using local bases with a light logistical footprint, it is highly unrealistic for a major deployment of forces. Finally, these tests begin in 2013, when ISIS split from Al-Queda’s branch in Syria and capture of Ar-Raqqah. Currently, they were just one of dozens if not hundreds of rebel groups within the Syrian Civil War and not noteworthy, other than their legacy reaching back to AQI and recent tensions with Al-Queda.
All of these are unrealistic assumptions for real-world constraints but are useful to decide if these polices could ever be successful. Comparing the “best case” results against both the historical baseline and baseline without intervention examines efficacy. If even a ‘best case’ scenario does not perform better than the baseline historical, it is unlikely to do so under more realistic operational constraints. In addition, some ‘best case’ policies may perform as bad, or worse, than doing nothing at all. (See Supplementary Materials D-7 for full specifications on experiments and results.)
The outcome of the best-case policies fit into three broad categories of behavior patterns. Shown in Figure 4, these behavior patterns chart a single primary measure of effectiveness and territory controlled by the actor.
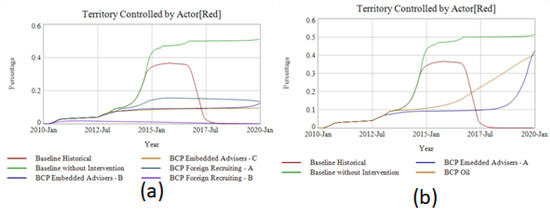
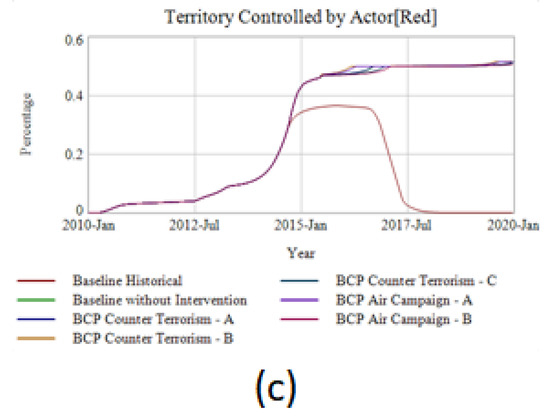
Figure 4.
Pct of territory controlled in select policy scenarios. (a) policies that significantly contain ISIS; (b) better-before-worse policies initially contain ISIS but fail to sustain containment; (c) policies that do not prevent or delay an ISIS breakout.
Experiment results included a variety of additional primary measures than in Figure 4a–c but showed similar clustering patterns. (See Supplementary Materials Section C-7 Experiment Test Results and Parameters.) The best-case policy outcomes falling into each category are in Table 1.

Table 1.
Best case policies by outcome.
The seemingly “successful” policies need some discussion. Firstly, even though eliminating Foreign Recruiting completely contained ISIS, it is not exactly obvious how this could be achieved at 50%, let alone 100% effectiveness under realistic conditions.
Deploying combat advisers to fight side-by-side with local troops showed success in containing ISIS territorially if deployment size was large enough. Deploying 25,000–50,000 troops (BCP Embedded Advisers B and C) successfully contained ISIS, but at the high cost of 15,000–30,000 intervention soldiers becoming casualties. Though modeling domestic reactions to such a loss of US servicemembers is beyond the boundaries of the E-SAM, it calls into question whether such a policy would enjoy sustained political support. A smaller contingent of only 10,000 deployed advisers (BCP Embedded Advisors A) didn’t have sufficient manpower to sustain containment of ISIS. As their casualties mounted to 66% of the deployed force—ISIS “broke out” in the simulation and was able to rapidly gain territory. Additionally—even though ISIS was contained territorially—it still managed to amass over tens of thousands of combatants under arms in both the interventions where their territory was contained. The reason why this occurred is that, even though ISIS was contained, they were contained within their inner ethnographic envelope, a human terrain favorable to its success and growth.
7. Importance of Ethnographic Envelopes
This exercise serves to illustrate the general challenges facing policy planners in containing a threat by ISIS. Many of the polices fail simply because, even by 2013, ISIS had enough revenue streams and interior resources to feed its strategic architecture. Policies that try to change this from afar do not account that by the time ISIS has become an emerging-state actor seizing territory—most of what it needs is within the territory it controls, which means that to contain or reverse this expansion requires going into that territory itself. Furthermore, even if ISIS is contained, if where they are contained represents a favorable human terrain, they can still gain combatants, funds and grow in strength.
This dynamic of “ethnographic envelopes” is key to many policy tests and illustrates the importance of the underlying ethnographic human terrain as envisioned by Renzi. E-SAM simulates as many ethnographic groups as desired, and, in both the baseline scenarios, there are three groups represented: Arab Sunni, Arab Shia and Kurdish Sunni. The ethnographic envelop is the dominant characteristics across the population between these three ethnographies. Figure 5 notionally represents these envelopes with a chart of the population size by ethnography as it will be met based on the percent of territory ISIS has conquered as it pursues its theatre strategy (See Supplementary Materials for further discussion on theatre strategy.)
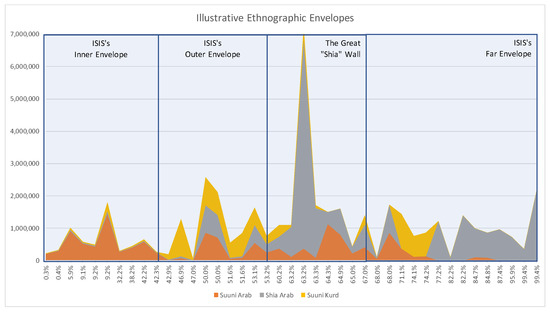
Figure 5.
Ethnographic envelopes in Syria and Iraq.
Figure 5 shows a stacked-area representation of the three ethnographic groups by population in any given area. Note that the populations are not cumulative. Divided notionally into four regions, or “ethnographic envelopes,” labeled as the inner envelope, the outer envelope, the “Great Shia Wall” and the far envelope.
These ethnographic envelopes highlight two applications for military simulations highlighted by the NRC: to understand, forecast and respond to both adversary and societal behavior. This is because, in E-SAM, an actor’s choices such as use of terrorism and ethnic cleansing against an ethnography, their willingness to provide (or deny) credible governmental services, and the location of non-indigenous troops in an ethnographic area all contribute to how that ethnography views the actor. The ethnographic, or societal response, to such actions can range from making it more difficult to collect taxes, gain recruits or even lead to all-out armed uprisings against the actor. Opposition, or support, emerges endogenously based on starting conditions and actor choices, and the extent to which the ethnographic envelopes matter is reflective of actor choices and societal responses to them. In both baseline scenarios, Arab Sunni at times may split in their support to ISIS than the Iraq or Syrian government. This is because the Shia led Iraqi and Syrian governments oppressed Sunni’s. This is represented in the model by a key parameter, the actual desire to credibly govern for Sunni Arabs dropping to0.75 during the initial crisis for the Green Actor, while it is set to 1 for the Red Actor. In addition, even as Red targets the Sunni Arabs with terrorism, they blame the Green Actor for being unable to protect them during the initial crisis. Conversely, Shia Arab favor Green more than they do Red. When ISIS targets the Arab Shia for ethnic cleansing and war crimes, it erodes the ethnographic perception. That most ISIS fighters are Arab Sunni or foreign fighters further weakens support among the Arab Shia. The Kurdish Sunni are somewhere in the middle, not initially disposed to either Green or Red. Although this is not universally true of every individual of these ethnographic groups, it is a plausible aggregation of the underlying realities leading into the conflict with ISIS. Furthermore, these ethnographic perceptions react endogenously and dynamically to choices actors make. If ISIS instead gives credible governmental services and protection to the Arab Shia, they could come around to supporting them.
However, given both Green and Red’s actual behavior in the two baselines, as depicted in Figure 5, the inner envelope for ISIS is the geographic part of their potential expansion path consisting almost entirely of their most favorable ethnographic group, the Sunni Arabs. This includes a large population center of Mosul at 9.2% of territorial capture. The outer envelope is an increasingly mixed region Kurdish Sunni, Shia Arab and Sunni Arab populations with large expanses of uninhabited deserts. ISIS can (and does) quickly expand over these areas gaining territory, but not much in terms of population. In addition, like a wave losing strength as it rolls up the beach, the mixed ethnographic nature means ISIS is less able to recruit, tax and must spend more combatants to garrison these areas. The “Great Shia Wall” acts like a sea-wall on the beach being an enormous obstacle to ISIS expansion. Holding the large metropolitan areas of Damascus and Baghdad, these are densely populated urban centers consisting of Shia Arab unfavorable to ISIS or its causes—beyond the “wall” is a far envelope that consists of completely Shia Arab populations.
At this point, it is important to note just as ethnographic feelings are not predetermined in the simulation, neither are these “envelopes.” Rather, as the feeling of ethnographic actors create a societal response to actor choices these envelopes appear endogenously as a dynamic. Furthermore, the importance of envelopes will differ based on the scenario considered. The policies of embedding combat advisers (BCP Embedded Advisors A–C) differ in how far ISIS can move across these ethnographic envelopes. Policies BCP Embedded Advisers B and C halt ISIS at ~12% and 10%, respectively—while Policy BCP Embedded Advisers A does not prevent a breakout and ISIS advances to take 42% of the overall territory. This isn’t as much of a difference as it seems, as depicted in Figure 6 below, which is an enlarged version of the chart in Figure 5.
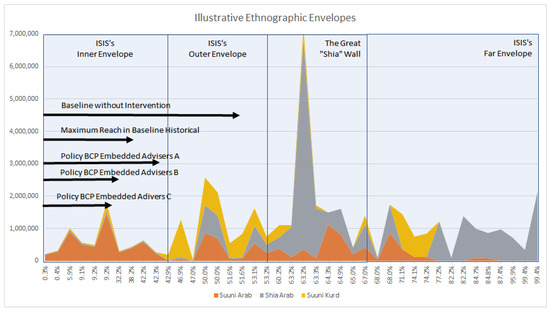
Figure 6.
Focus on inner ethnographic envelope with Islamic State of Iraq & Syria ISIS expansion overlain.
The largest expansion is the baseline without intervention, which reaches and holds in the outer envelope at around ~52% of the territory. This is where the population has already begun significantly shifting to Kurdish Sunni and Arab Shia. The baseline historical reached its greatest size just slightly less than Policy BCP Embedded Advisers A, or ~36% to ~42%. In addition, in the historical baseline simulation that expansion is turned back by a large foreign intervention, while the much smaller intervention of BCP Embedded Advisers A simply holds it to that extent. Policies BCP Embedded Advisers B and C hold ISIS’s growth to within the inner envelope. ISIS has conquered Mosul—but not gone much further. In addition, even as ISIS’s territorial growth slows their combatants and strength continue to rise. ISIS performs better over time if it is “contained” to areas within its inner ethnographic envelope.
This slowing effect of crossing from the inner to the outer ethnographic envelope is clear in comparing the actual garrison of ISIS across four scenarios as shown in Figure 7.
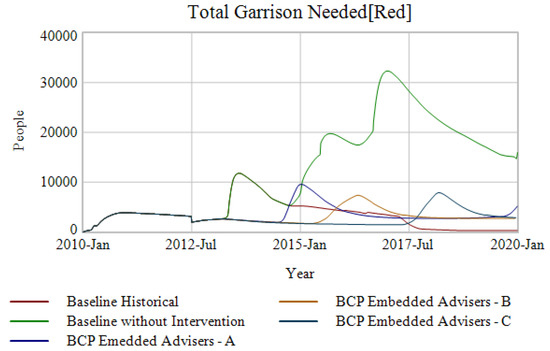
Figure 7.
Total garrison needed in relation to ethnographic envelopes.
The BCP Embedded Adviser A–C scenarios, all which limit ISIS to within its inner ethnographic envelope have significantly less total garrison required commitments than the baseline without intervention scenario.
8. Course of Action Analysis under Operational Constraints
The best case hypothetical scenarios are useful from the standpoint of distinguishing policies that might not have utility even under best conditions versus those that have promise. With those insights, a more powerful form of analysis that can be done within E-SAM is on simulated courses of action (COA). Each COA represents a portfolio of policy options, implemented at various timing windows, and with operational constraints that are realistic. We know that Policy 2, attacking ISIS oil infrastructure limited ISIS’s growth in a hypothetical best-case scenario, but this policy assumed a 100% successful destruction of ISIS’s nascent oil infrastructure in 2013. This is well before ISIS was considered a serious national security threat. However, would combining additional policies with an air campaign that began in June 2014 have resulted in reversing or containing ISIS’s growth? This is another example of how E-SAM can support applications key to military simulations. The first is by understanding, forecasting and responding to adversary behavior—how ISIS will react to an alternate policy scenario. The second is in analysis, forecasting and planning a COA. Unlike earlier policy tests, this set of experiments involves combining multiple policy options, adding operational constraints, and testing timing windows.
We constructed a COA of an intervention beginning in June 2014 consisting of the following elements:
- Deploy ~10,000 embedded combat advisers to improve the fighting quality of forces opposing ISIS in combat-roles.
- Deploy 5000 military advisers to train and oversee counter-terrorism operations against ISIS in non-combat roles.
- An air-campaign tested at three levels:
- COA1 Minimal: ~12/sorties/day,
- COA1 Significant: ~120/sorties/day,
- COA1 Intensive: ~500/sorties/day.
This suite of COAs, unlike the best-case scenarios, is operationally constrained. This includes more realistic deployment delays, both for the first and replacement troops. The effect of an air campaign now is realistically depicted by conducting sorties per day, which seek to cause the result desired. Options are available to attack ISIS’s oil production, and its governance capabilities or support ground operations—and the same sortie can only be tasked to one of these goals. The three levels of air campaign, based on historic precedent, are COA1 Minimal, COA1 Significant and COA1 Intensive representing flight operations at the levels listed in the list as 3a–c above. Air strikes will target ISIS oil production 100% until it is destroyed, and then shift into a Ground Support role afterwards. There is also a small risk that some airstrikes will miss their targets, causing collateral damage, which will weaken support for the intervening coalition and the Green government in much the same way a war crime decreases support for ISIS. (See Supplementary Materials Section D-7 Experiment Test Parameters & Results for discussion of the operational constraints and parameterization of these experiments)
Because of the operational constraints, it takes more deployed personnel to execute these COAs than the best cases, which excluded the logistic, administration and headquarters personnel known within the military as “tooth-to-tail ratio” (T3R.) This ratio of support is quite high for US interventions and means more personnel must deploy to support combatants undertaking operational orders. All scenarios have the same number of ground-troops, at 15,000—that themselves need T3R support. In addition, each scenario must also support enough personnel to conduct the air operations—as well as support those personnel. All told the personnel requirements are now:
- COA Minimal: 45,405,
- COA Significant: 49,050,
- COA Intensive: 62,010.
When simulated, COA1 Minimal, Significant and Intensive all show the capability to significantly reduce the territorial size and strength of ISIS over time. Unlike the operational best cases, the Total Combatants of ISIS are all significantly reduced by the end of the scenario runs. In addition, this reduction comes at an excessive cost with large intervention sizes and correspondingly high casualties. Furthermore, even under the best COA a third of Syria and Iraq stays under ISIS control six years after the intervention. ISIS is not by any stretch defeated to the same extent as in the Historical Baseline. Admittedly, that intervention consisted of far more combatants joining from the various countries. Reviewing a performance dashboard in the Figure 8 view shows the behaviors over time of interest that reflect this challenge.
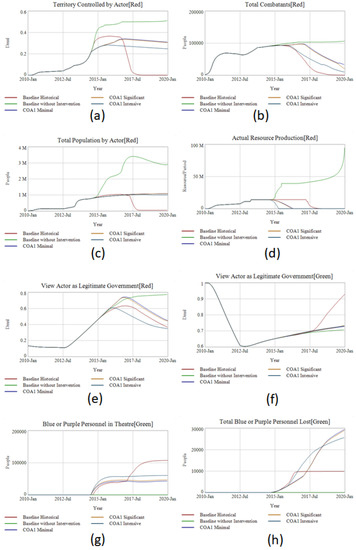
Figure 8.
Comparison between baseline and baseline without intervention against COA1 with three levels of air campaign intensity. Comparisons include (a) territory controlled, (b) total combatants, (c) total population, (d) oil production Red, (e) percent of Red controlled population that views them as legitimate government, (f) percent of Green controlled population that views them as legitimate government, (g) foreign intervention size on behalf of Green, and (h) total losses for intervening forces.
In the narrative, COA1 with both Minimal and Significant air campaigns were insufficient to rapidly destroy ISIS’s oil production in Figure 8d, taking longer than the Intensive air campaign. Only COA1 Intensive, sustaining a 500 sortie/day tempo can both destroy the oil production and then later shift to support the ground war with air strikes quickly. Since all three interventions are significantly smaller than the historical baseline (Figure 8g), they struggle to match the performance of the historical baseline simulation in reducing territory (Figure 8a) or eliminating ISIS combatants (Figure 8b). The Blue ground forces acting as embedded combat advisors and counter terrorism training are having an impact—but their exposure to combat results in continual casualty rates. This front-line exposure, however, leads, counterintuitively, to a higher casualty rate among intervening forces than the Intensive air campaign (Figure 8h). In summary, the results are better, but not great than the hypothetical best cases, and not as good as the historical baseline, which involved over 100,000 intervening forces. Besides realistic operational constraints why do a combination of effective policies perform little better than any one single policy? The reason is fourfold and key to understanding how to confront an emerging-state actor—first, keeping ISIS within its inner ethnographic envelope; second, the timing of interventions; third, not improving the perceived legitimacy of the Green Actor (Figure 8f) compared to the Red Actor (Figure 8e), and the diminishing returns of combat actions. As we have already touched on the first insight, we can turn to the remaining three to understand how they can support analysis, forecasting and planning of a second-generation COA to improve upon the performance of COA1.
8.1. Policy-Timing
First on timing—most of the feedback loops activated early in the causal loop diagram depicted in Figure 1 are positive in nature, creating a path-dependent system. Once ISIS goes down the path of becoming an emerging-state actor, it is increasingly difficult to break from this trajectory as time moves on prior to the negative loops activating. Earlier interventions with an emerging-state actor like ISIS have far greater effect than later interventions, even if the later interventions are significantly larger. These intervention windows exist prior to the significant acquisition of territory that grants ISIS access to exploitable resources and population to control and then govern. This prevents the reinforcing feedback loops from activating highlighted in Figure 1. To illustrate the importance of timing, the same portfolio of policies in COA1 Minimal, a light air campaign, using the start time of the “hypothetical best case” in the beginning of 2013. Labeling this COA1 Minimal Early, we compared it against COA1 Intensive as well as the historical baseline.
Figure 9g shows that COA1 Minimal Early is smaller in size than either COA1 Intensive of the historical baseline. In addition, the combat effectiveness at reducing territory controlled (Figure 9a), total combatants (Figure 9b) and total population controlled by ISIS (Figure 9c) favors COA Minimal Early over the larger interventions. This despite the baseline historical having over twice the deployed number of troops and the COA1 Intensive running fifty-times the daily sorties. The takeaway of this insight is not to attack-early-and-often. It is not always clear of course when a local actor will end up becoming a regional or even global threat. In addition, it does show the power of earlier, targeted smaller interventions aimed to prevent an actor from gaining a foothold. This is based on ensuring the positive feedback loops don’t activate to support ISIS’s growth. The earlier the intervention, the smaller ISIS’s oil production footprint and the faster its removal. In Figure 9d, the oil production that provides the finances for ISIS are targeted earlier and destroyed more quickly. This simultaneously reduces the inflow of cash for expansion while also allowing the intervention to switch to ground support earlier. The earlier ground support prevents ISIS from gaining more territory. As ISIS cannot gain territory, it cannot gain more oil resources, populations to recruit from and thus new combatants or other benefits. This is reflected in the sharply weaker performance of ISIS as it never can “breakout” from its earlier controlled territory (Figure 9a). Timing therefore is crucial for policy consideration, and the earlier the better with an opponent who looks to gain power through territorial conquest as an emerging-state actor like ISIS would.
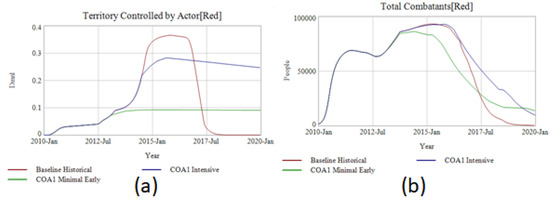
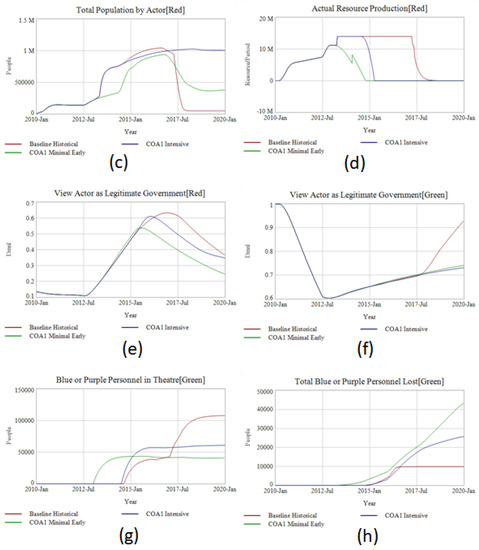
Figure 9.
Comparison of a Minimal Air Campaign intervention beginning in 2013 vs an Intensive Air Campaign beginning in June 2014. Comparisons include (a) territory controlled, (b) total combatants, (c) total population, (d) oil production Red, (e) percent of Red controlled population that views them as legitimate government, (f) percent of Green controlled population that views them as legitimate government, (g) foreign intervention size on behalf of Green, and (h)total losses for intervening forces.
8.2. Diminishing Returns of Combat Actions
A second challenge to the set of policies is the nature of diminishing returns in combat. Two of the three policies in COA1 target improving combat effectiveness of Green against Red, either by embedding combat advisers or providing close air support. However, a single ISIS combatant can only be killed, captured or wounded once regardless of how many policies target improving combat effectiveness. This presents the problem of diminishing returns when combining options that all support a military solution, the more resources applied the less return for each marginal resource gained. This is made doubly so by the logistical footprint of the Blue intervention forces that take seven logistics, administration and headquarters personnel (T3R) for every three combatants engaging in military actions. Since it is not possible to alter the diminishing returns impact, reducing the T3R can lessen the steepness of decline.
8.3. Perceived Legitimacy of Green Actor
The third challenge illuminated by COA1 is that it only focuses on military solutions to the conflict, ignoring that key ethnographic groups are unable to coalesce around the legitimacy of the Green Actor. Experiments into the emerging-state actor theory showed that when Red was unwilling to credibly govern at least 50% of its controlled population, it suffered precipitous declines in material support. Comparing the Red and Green Actor Legitimacy in Figure 9e,f demonstrates that the Red Actor exceeds this threshold before dropping back below, and the Green Actor never fully recovers its own legitimacy. Because emerging-state actors try to govern openly, where insurgencies do not, this contest of legitimacy as perceived by ethnographic actors is crucial between the Green and Red actors.
Although designed for ISIS in Iraq and Syria, another way to consider the outcome presented by COA1 scenarios is to compare them to the Afghanistan war. In both scenarios a large US intervention force varying between 45,000–75,000 soldiers (excluding surges) focused primarily on building local military capability while trying to destroy the Taliban’s main source of funding. Opium instead of oil. In addition, progress on the military front didn’t accompany progress on credible governance and legitimacy in the eyes of key tribal groups. When the US withdrew its combat forces from Afghanistan in 2014, the Taliban was able to return to power building outward from its undefeated core. The human cost of these policies is clear in Figure 9h. Despite military success, the high casualty rate is a result of the frequent exposure to combat of the embedded advisors and failure to build legitimacy in the Green government. The model does not distinguish between killed and wounded, but the 40,000 Blue Personnel killed or wounded in the simulation is close to the US coalition casualties in Afghanistan when including all countries of the coalition and contractor casualties.
8.4. Incremental Knowledge Gain
To this point, several insights became clear from analyzing, forecasting and conducting COA experiments. Because an emerging state actor relies on few exogenous factors for its success, there are only limited avenues to “harm” an actor like ISIS from outside the territory it exists within. The ethnographic envelope or human terrain an emerging-state actor operates within is just as important to understand as the physical terrain. If contained, yet on a favorable ethnographic envelope, ISIS can support its position. There are diminishing returns of combat power. More important than the total number of troops might be when and how they are employed. Earlier interventions need less resources to be successful than later interventions. Finally, while considering military options, the perceived legitimacy of both the Green and Red actor compared to one another is crucial. It is entirely possible to militarily defeat an emerging-state actor but still end up with a failed state due to lack of strong ethnographic support to the state actor.
9. Applying Emerging-State Actor Theory to Craft an Intervention
The incremental knowledge gained from experiments on momentum solutions feeds back into the forecasting, analyzing and understanding of COA planning. The next step is to enhance the COA through systems thinking and using the emerging-state actor theory expressed in feedback form in Figure 1. Examining the causal-loop structure of an emerging-state actor offers some ideas of how to craft an intervention that may have more success than already discussed. A portion of the structure is depicted in Figure 10. Originally proposed at a conference presentation in Delft, Netherlands 2016 this second course-of-action (named COA2 Emerging-State) consisted of two phases of intervention [1]. The overall deployment is only 15,000 Blue personnel, to avoid the diminishing returns effect illustrated above. Phase I also takes advantage of timing-windows, deploying 5,000 troops in 2013. Although this is prior to ISIS’s global recognition as an emerging-state actor, they certainly were active in clandestine terrorist activities, as were many other groups in the area. For this reason, the goal of this deployment is not military confrontation, but to create legitimacy for the Green actor and undercut the grievances feedback loop that fuels the Red actor as depicted in Figure 11 and indicated in Saeed’s work [3] (p. 790).
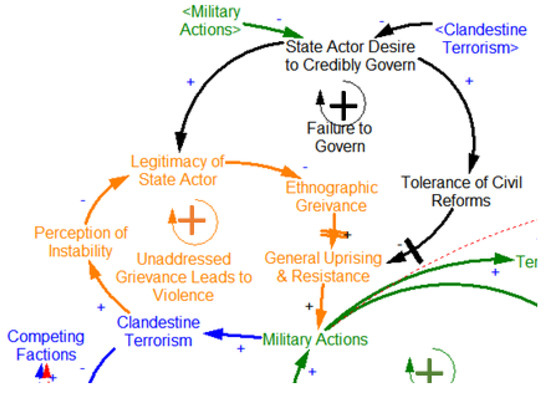
Figure 10.
Zoomed in section of emerging-state actor causal loop diagram (CLD).
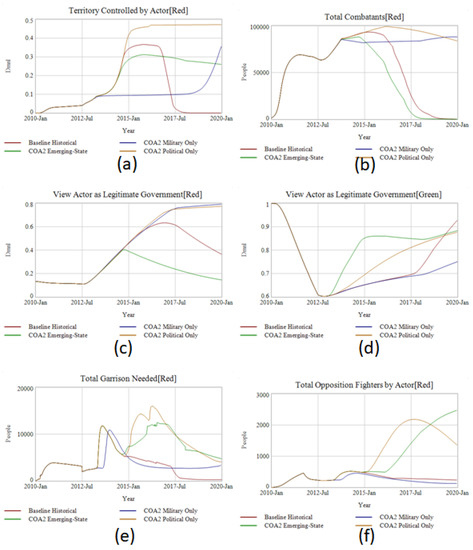
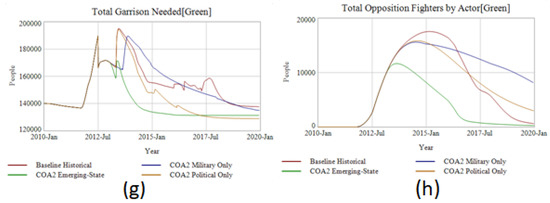
Figure 11.
Dashboard Comparing an Emerging-State theory formulated policy (COA2 Emerging-State) against the baseline historical and two falsification tests (COA2 Military Only and COA2 Political Only). Comparisons include (a) territory controlled, (b) total combatants, (c) percent of Red controlled population that views them as legitimate government, (d) percent of Green controlled population that views them as legitimate government, (e) total garrison required by Red, (f) total opposition fighters rebelling against Red, (g) total garrison required by Green, (h) total opposition fighters rebelling against Green.
The black and orange loops in Figure 10 are both positive-feedback, meaning they work in vicious or virtuous modes creating exponential behavior for or against a desired outcome. The Phase I intervention intends to switch these two loops from vicious to virtuous for the Green Actor while turning them from virtuous to vicious to the Red Actor. This will be carried out through a variety of means including requiring the Green Actor to marginally increase its Desire to Credibly Govern Arab Sunni’s and Kurdish Sunni’s. This accompanies operational orders of Blue and Green personnel to conduct Armed Civil Affairs (provision of governmental services through military means) as well as communications through Information Operations and Propaganda. Against Red, Blue airpower is not focused on destroying oil production, but attacking the mechanisms of governance itself. The goal is not to reduce revenue, but to reverse the flow of accumulating legitimacy, which moves the population out of the Coerced to Calculated Legitimacy to Governed stocks in the simulation model [11]. This is based on the theoretical assumption that an emerging-state actor benefits over an insurgency by openly governing the territory it holds, and that, were it not for this governing, it would face higher internal resistance and be required to allocate more garrisoning troops to match. This might mean targeting ISIS governing buildings, public works efforts—even the execution scaffolding and plazas. Anywhere ISIS uses the institutions of governance to create credible processes that fuel the transition from coercion to legitimacy.
The other focus of Phase I troops is to improve the host-nation security capability to counter terrorism, thus protecting the population and reducing the overall violence level—which also leads to increased legitimacy of the state actor through the blue loop that connects to orange. A secondary mission is to train Green to work with a smaller logistical footprint, the percentage of personnel that are involved in logistics, administration and headquarters personnel known as “T3R.”
The goal of these Phase I efforts is to undercut Red’s ability to govern within its own territory, reducing its legitimacy, needing greater efforts of coercive power as it expands outside its inner-ethnographic envelope. This will create conditions for an internal uprising within its borders. Meanwhile, the increased legitimacy of Green should result in lower Garrison requirements of restive populations, decreased defections and thus more troops available to confront Red. The importance of this lighter Phase I deployment is that if ISIS doesn’t materialize as the kind of threat expected, then the military deployment has been limited in size and focused on delivering outcomes that would be beneficial to Green all the same. Greater legitimacy and reduced violence through terrorism. This Phase makes several key assumptions, but, for this hypothetical synthetic experiment, the premise is assumed that Green, under threat from Red, will make some concessions in return for US support in terms of giving more credible government to the ethnographic groups.
Phase II of the intervention adds 10,000 more troops. The aim is to pin ISIS on its outer-ethnographic envelope, in unfavorable human terrain, and keep it there while the internal uprising occurs—confronting ISIS from both sides. Blue troops will directly embed with Green forces engaging in combat. Additionally, Green and Blue work together to raise local forces from within the ethnographic populations. This allows Arab Sunni forces to fight in their own ethnographic envelope, Kurdish Sunni in their favorable human terrain etc. These efforts would be analogous to the creation of the Shia popular mobilization forces (PMF) and the Kurdish Syrian Democratic Forces (SDF), which exist in the baseline historical intervention or the Anbar Awakening against AQI. This simply expands that concept to the Arab Sunnis in the current situation.
To ensure that any benefits seen aren’t just a result of exploiting the timing-window, a second and third portfolio of policies are falsification tests, named COA2 Military Only and COA2 Political Only. Both seek to show that the combined emerging-state actor theory does not plays a role and that benefits could be achieved with a military only, or political only approach. COA2 Military Only deploys all 15,000 Blue Personnel at the same earlier time, 2013, as COA Emerging-State. It does not, however, include any efforts related to emerging-state actor theory to increase Green legitimacy, decrease Red’s legitimacy or raise local forces. Instead, it mirrors more traditional counterinsurgency interventions splitting all personnel between embedded combat advisers, counter-terrorism training to protect the population and airpower support to the ground-campaign. The second falsification experiment, COA2 Political Only tests the opposite—that an entirely political solution, absent any military involvement, would be just as effective. This will consist of using all 15,000 Blue Personnel in Armed Civil Affairs and Information Operations beginning at the earlier point—and conducting no military operational orders or air campaigns. If all three COA2 scenarios perform the same, then it is not clear of benefits derived specifically from incorporating the emerging-state actor theory. If COA2 Emerging-State Theory, however, shows a higher utility than either COA2 Military Only or Political Only, there is at least some confidence that the specific strategies arrived at from emerging-state actor theory have contributed to that benefit. (See Supplementary Details D-7 Experiment Test Parameters and Results for parameters of all three COAs.)
With all three versions of COA2 executed and compared to the baseline historical behavior, the power of emerging-state actor theory becomes clear. A dashboard of primary measures of effectiveness appears in Figure 11 (See Supplementary Details D-7 Experiment Test Parameters & Results for complete numeric results.)
The approach incorporating emerging-state actor theory (COA2 Emerging-State) shows significant effectiveness in reducing Total Combatants and Total Population for ISIS to levels lower than even the Baseline Historical. Both policy-falsification approaches (COA2 Military Only and Political Only) do not deliver a successful intervention by the end of the scenario, resulting instead in the worst performance out of all considered COAs. However, this is only clear at the end of the simulation period. At its start, COA2 Military Option appears to be the more successful policy across a dashboard of primary measures of effectiveness displayed in Figure 11.
COA2 Military initially appears to be more successful at reducing ISIS’s territory and number of combatants (Figure 11a,b) and continues to successfully contain ISIS’s territory for much of the simulation. Commanders on the ground and policy makers in the rear might mistakenly think this approach is superior. In addition, those performances are only in the manifest, or visible, system. The latent system, what is not visible, depicted in Figure 11c,d, which together show the competition in perceived legitimacy between Red and Green, respectively. This creates a “better-before-worse” behavior pattern of early promise leading to later failure. By not improving the legitimacy of the Green actor or reducing the legitimacy of the Red actor COA2 Military Only allows several dynamics to appear. COA2 Emerging-State benefits from targeting ISIS’s governance structure, eroding its legitimacy (Figure 11c). This forces ISIS to take more troops off the front-line advances and focus on garrisoning (Figure 11e) and dealing with more internal uprisings against ISIS control (Figure 11f). These uprisings are not specified in the simulation but could be considered similar to the Anbar Awakening backlash that occurred against ISIS’s predecessor AQI in 2006–2007. Likewise, because Green isn’t a credible government in the COA2 Military Only scenario to Arab Sunni’s or Kurdish Sunni’s (Figure 11d), it requires more garrison (Figure 11g) and also has to contend with higher a rate of internal opposition unaffiliated with ISIS conducting attacks against Green (Figure 11h) COA2 Emerging-State on the other hand, focusing on legitimacy improvement in Phase I has created conditions greater success when the military intervention does happen. This means Green in COA2 Emerging-State has more local troops available to confront ISIS than COA2 Military Only. The consequences of this latent system appear shortly after 2017, four years after the initial deployment. In COA2 Military Only, ISIS affects a break-out territorially while consistently increasing its combatant force towards the 100k mark. A common proposal is that state-actors should be willing to accept the reality of political reconciliation with competing non-state actors to end a conflict. What these results show, however, is that a state-actor should also seek political reconciliation with its own people to cut off the grievance feedback loop that fuels the competing non-state actors support base. A political-only solution, however, won’t be enough either. COA2 Political Only performs poorly on all fronts, as, although it focuses on legitimacy, it does not have an answer for improving security or containing the military actions of ISIS. This undermines the benefits of legitimacy-building when it comes to total garrison required (Figure 11g) and opposition fighters opposed to Green (Figure 11h). This is because ISIS can keep a high-level of violence against all ethnographies, but especially the Arab Shia population, which Green depends on for support. This appears by looking at the Killed in Action (KIA) per Million Population in Figure 12.
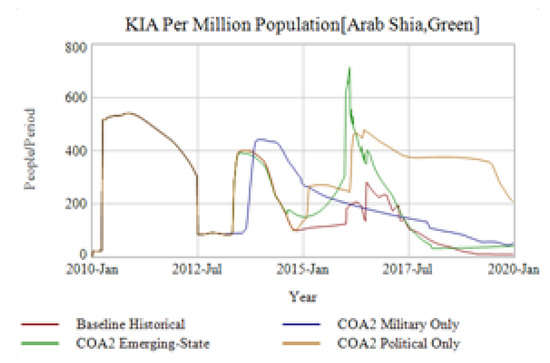
Figure 12.
Military and civilians total Killed-in-Action (KIA) KIA per Million Population.
Populations regularly subjected to violent terrorist and other attacks have less trust of a government that proves unable to protect them. The rise of local opposition fighters to Green (Figure 11h) is similar to the rise of Shia death-squads and other irregular guerillas during the Sunni–Shia civil war in Iraq corresponding with AQI’s terrorism in 2006–2008.
This final note on the level of violence in the system is important. The consequences of policies in terms of overall violence across secondary measures of effectiveness are in Table 2.

Table 2.
Casualty rate all sources.
In this context, it is clear that civilian casualties, green casualties and total refugees stay roughly the same for most policies except the falsification COA2 Political Only. Despite COA2 Political Only having the lowest blue personnel deaths (because none are in combat positions) in total results in the largest amount of human suffering of all policies. Although it is natural to want the lowest possible deaths of blue personnel when considering the political ramifications, the inability to deliver actual results and overall human consequences are also important. Though the 500 deaths in COA2 Emerging-State actor are not nothing, they are significantly less than any other policy.
10. Conclusions
Simulation enables testing policies for intervention against emerging-state actors in a synthetic environment without the real-world risks of inherent in such activities. By modeling the ISIS case across two baseline scenarios, the theory of emerging-state actor we tested and evaluated against other contemporary policy solutions, the historical and counterfactual baseline cases, as well as a falsified version of itself. The first baseline scenario tried to mirror the historical case of the multilateral intervention in Syria and Iraq. The second assumed the counterfactual of no foreign intervention. We constructed contemporary policies of momentum solutions, in isolation and combination, tested both under ideal and operationally constrained scenarios and then compared to these two baselines. Portfolios of interventions combined into a Course of Action (COA) ranged in size from 40,000–108,000 (the historical baseline estimate). Evaluating these experiments found some momentum solutions that failed to achieve any meaningful benefit and others that showed promise. These experiments revealed key insights into the dynamics of intervention against these actors.
Two widespread characteristics of an emerging-state actor are the way in which they obtain territory and the human-landscape of which that territory consists of decides their performance. As an emerging-state actor, ISIS differs from terrorist groups and insurgencies in that it seizes territory and governs openly. This presents a policy dilemma in planning effective interventions. Reducing or degrading ISIS’s capabilities from abroad is difficult because their resources come from within the territory they control. There are few levers to pull from outside this territory. Ethnographic envelopes, the composition of the human terrain, are also key to understanding how an emerging-state actor might react to an intervention. Policies that slow, but do not reverse, the growth of an emerging-state actor such as ISIS while they exist within their inner-ethnographic envelop allows them to benefit from more favorable conditions of recruitment, taxation and lower garrison requirements.
Dynamics of the interventions themselves also bear scrutiny, as proposed emerging-state actors operate in a path-dependent system benefitting from positive feedback loops. Policy timing is crucial as the earlier policies start the more effective they are and with comparatively less resources. Additionally, there are diminishing returns of purely combat actions that all seek to kill or wound ISIS fighters. Even a portfolio of such combat-focused policies may not have an aggregate effect equal to the sum of its parts.
We tested a final intervention policy based on emerging-state actor theory incorporating the above insights. The goal was to intentionally target the positive feedback loops that govern an emerging-state actor’s performance. The first phase of this proposal consisted of a smaller, earlier deployment focused on building state-actor legitimacy while decreasing non-state actor legitimacy deployed in 2013 simultaneously to cut the cycle of violence by improving counter-terrorism operations. The second phase consisted of deploying the rest of troops in mid-2014 to conduct combat operations within locally recruited ethnographic Sunni Arab groups like the Syrian Democratic Forces (SDF) and Popular Mobilization Forces (PMF). This emerging-state actor informed intervention only consisted of ~15,000 troops but performed far better than interventions two-to-seven times as large in deployed personnel, reducing ISIS fighters to effectively zero. To ensure these results did not originate solely from timing-effects or one aspect of the emerging-state theory and not the other, we conducted two falsification experiments. In the first, the entire 15,000 force deployed beginning in 2013 in a purely military role. This intervention did not produce the same results, instead creating a better-before-worse behavior mode that stalled ISIS for a time before it broke out and expanded to its largest size and territorial holdings of any intervention. The second falsification focused entirely on political activities with no security aspect. This falsification policies performed worst of all. Although responses to non-state actors typically favor military responses or diplomacy seeking political reconciliation, a third path appears to be focusing on political reconciliation between the state-actor and its own populace while using the military to contain the non-state actor and protect the population from harm. Leveraging these dynamic insights with systems thinking may result in an atypical intervention strategy that, at least within the boundaries of the model, appears to perform better at containing emerging-state actors like ISIS.
The emerging-state actor intervention did not come without its own consequences. Trade-offs included a higher Green casualty count (military casualties not civilian) and higher funds sent abroad as oil-production wasn’t targeted by airpower.
Our research also showed utility in four kinds of applications in military simulations: understanding, analyzing and forecasting adversary and societal responses to conflict; understanding enemy command and control; and the ability to analyze, forecast and plan COA.
These findings could be enhanced by further research. The entire premise of a synthetic policy experiments via a simulation relies on certain premises, assumptions and abstractions represented in the design of the simulation. This design should be rooted in existing theory and where possible empirical observation. In addition, the nature of conflict challenges empirical observation and robust data collection until long after the conflict has ended. (See Supplementary Materials Section A: Discussion of Model Structure & Parameter Values for more discussion on limitations and future research paths). The policies selected for analysis were not comprehensive of all policies and combinations. As well, parameter values to represent the policies in cases where detailed information might either not exist or be classified were arbitrarily selected. Combinations of different policies, or tested with different parameters, could yield contrary results. Future work could cover a broader policy space with thousands of permutations rather than a handful. Generalizing the model to different scenarios—both in region and time—could yield added insights into the contingencies within which intervention policies may find success or failure.
Supplementary Materials
The following are available online at http://www.mdpi.com/2079-8954/6/2/17/s1 (tbd): Section A Discussion of Model Structure & Parameter Values; Section B Validation & Confidence Building; Section C Draft E-SAM User Manual; and Section D Model Documentation & Experiment Results. As well a zip file with the raw model, copies of all scripts, and all results outputs.
Acknowledgments
The author would like to acknowledge Khalid Saeed, Jessica Turnely, and Sara Citrenbaum for their guidance and assistance in this research. This study was not funded by any source or grants. However, the author has engaged in consulting work with the Department of Defense using the E-SAM simulation.
Conflicts of Interest
Timothy Clancy is the founder of a consulting firm that has, and may in the future, receive funds from the Department of Defense or other government agencies on topics related to those covered in this research. However, the DoD had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, and in the decision to publish the results.
References
- Clancy, T. Containing ISIS: Analysis of Intervention Policies. In Proceedings of the 34th International Conference of the System Dynamics Society, Delft, The Netherlands, 17–21 July 2016. [Google Scholar]
- Zacharias, G.L.; MacMillian, J.; van Hemel, S.B. Behavioral Modeling and Simulation: From Individuals to Societies; National Academies Press: Washington, DC, USA, 2008. [Google Scholar]
- Saeed, K. Economic Growth and Political Instability in the Developing Countries: A System View. In Sessions Papers; System Dynamics Society: Chestnut Hill, MA, USA, 1983; pp. 455–468. [Google Scholar]
- Renzi, F. Networks: Terra Incognita and the case for ethnographic intelligence. Mil. Rev. 2006, 86, 16–22. [Google Scholar]
- Turnley, J.G.; Henscheid, Z.A.; Koehler, M.T.K.; Mulutzie, S.K.; Tivnan, B.F. COIN 2.0 Formulation; MITRE Corporation: Bedford, MA, USA, 2010. [Google Scholar]
- Bumiller, E. We have met the enemy and he is powerpoint. New York Times, 26 April 2010. [Google Scholar]
- Pierson, B. Dynamic Planning for COIN in Afghanistan; PA Consulting Group: London, UK, 2009. [Google Scholar]
- Anderson, E.G., Jr. Modeling Insurgencies and Counterinsurgencies. Syst. Dyn. Rev. 2011, 27, 111–141. [Google Scholar] [CrossRef]
- Saeed, K.; Pavlov, O.V.; Skorinko, J.; Smith, A. Farmers, bandits and soldiers: A generic system for addressing peace agendas. Syst. Dyn. Rev. 2013, 29, 237–252. [Google Scholar] [CrossRef]
- Aamir, M. Applying Existing System Dynamics Business Formulations to Model Terror Organizations. In Proceedings of the 32nd International Conference of the System Dynamics Society, Delft, The Netherlands, 20–24 July 2014; p. 17. [Google Scholar]
- Clancy, T. Dynamics of ISIS—An Emerging State Actor. In Proceedings of the 34th International Conference of the System Dynamics Society, Delft, The Netherlands, 17–21 July 2016. [Google Scholar]
- Langarudi, S.P.; Radzicki, M.J. A Simulation Model of Katouzian’s Theory of Arbitrary State and Society. Forum Soc. Econ. 2018, 47, 115–152. [Google Scholar] [CrossRef]
© 2018 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).