Wireless Sensor Network Based Smart Grid Communications: Cyber Attacks, Intrusion Detection System and Topology Control
Abstract
:1. Introduction
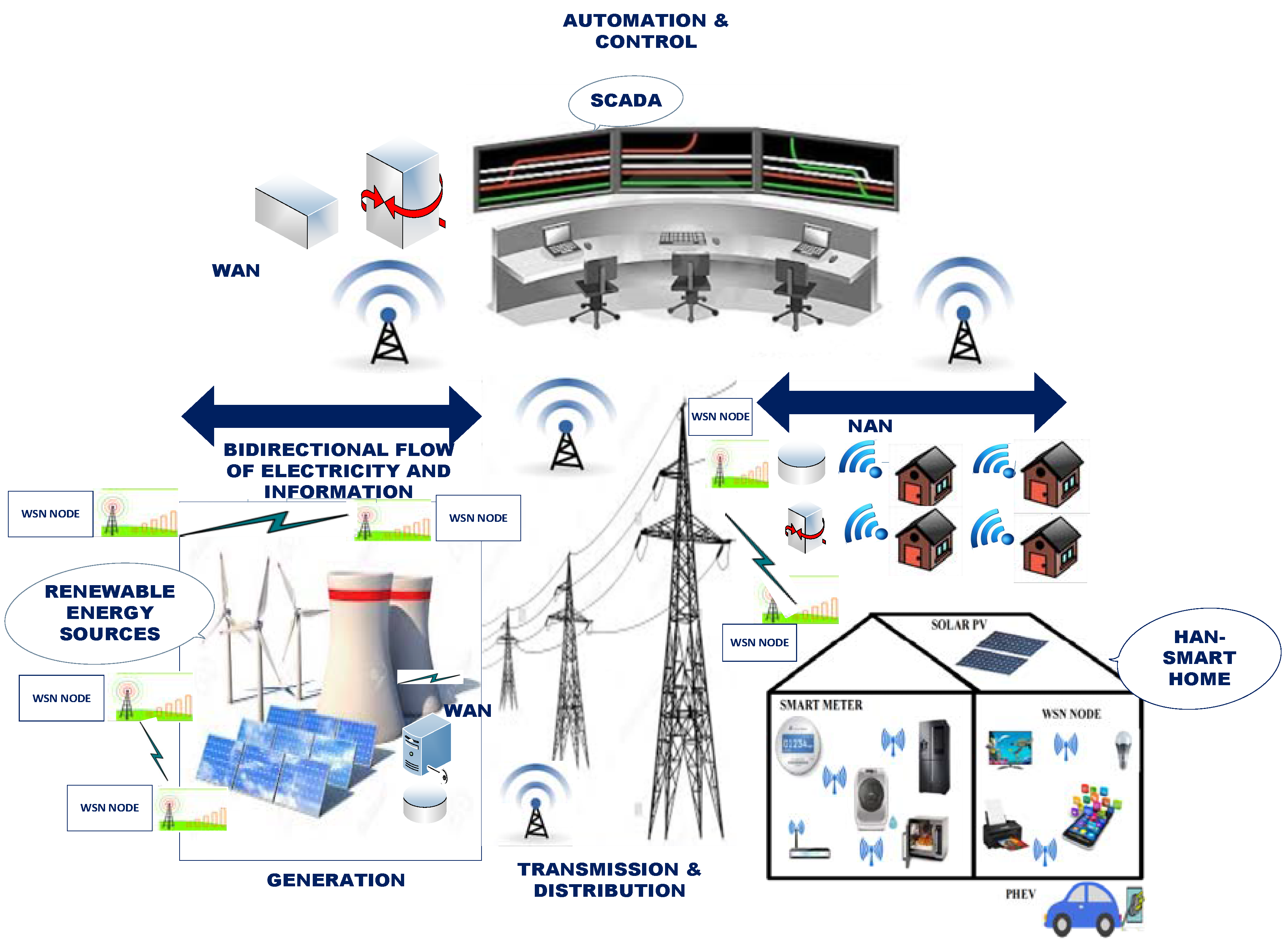
1.1. Home Area Network
1.2. Neighborhood Area Network
1.3. Wide Area Network
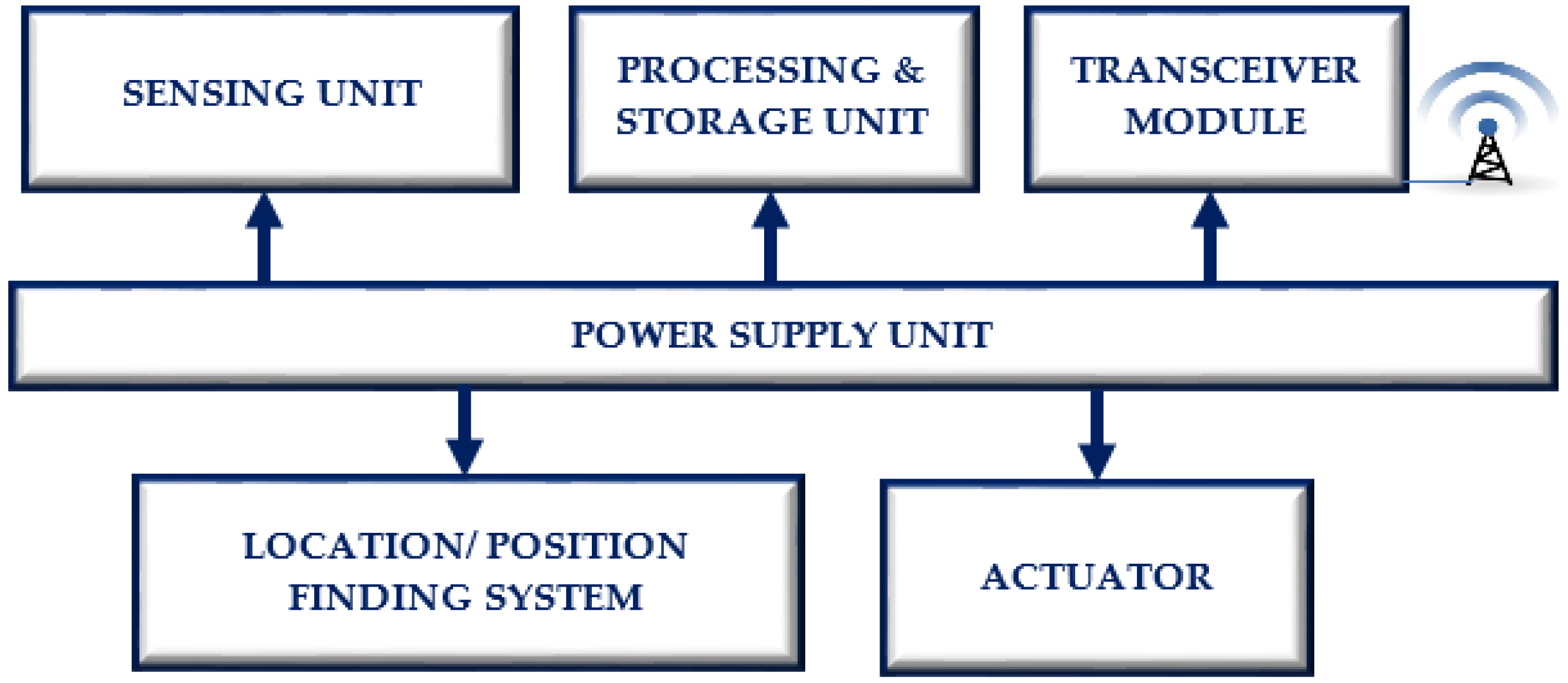
2. Application of Wireless Sensor Networks in Smart Grid
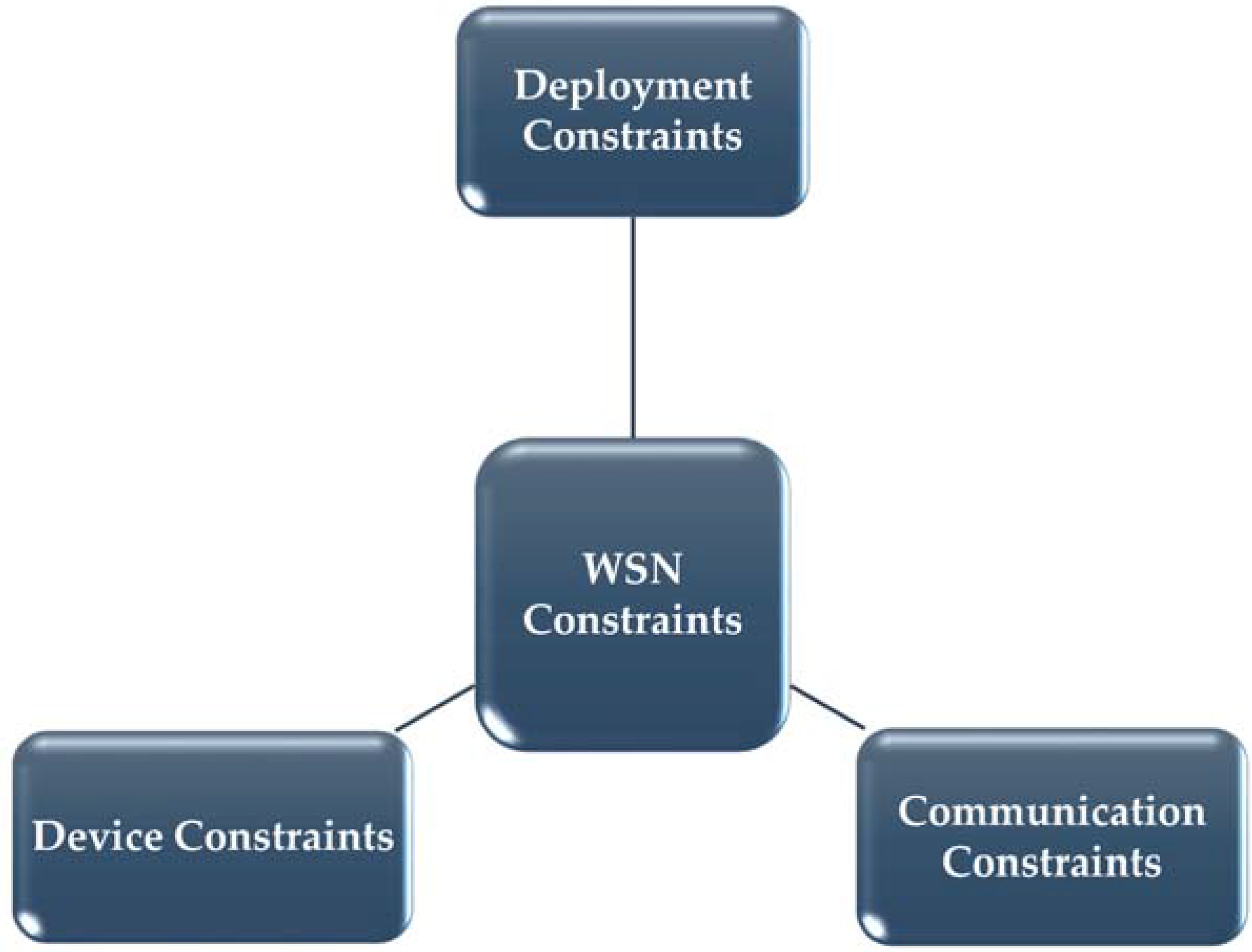
3. Challenges of Wireless Sensor Networks in Smart Grid Applications
4. Communication Standards for Wireless Sensor Networks
4.1. Zigbee
4.2. Bluetooth
4.3. Wireless Fidelity or Wireless local area network
4.4. Z-Wave
4.5. WirelessHART
4.6. 6LoWPAN
4.7. Wavenis
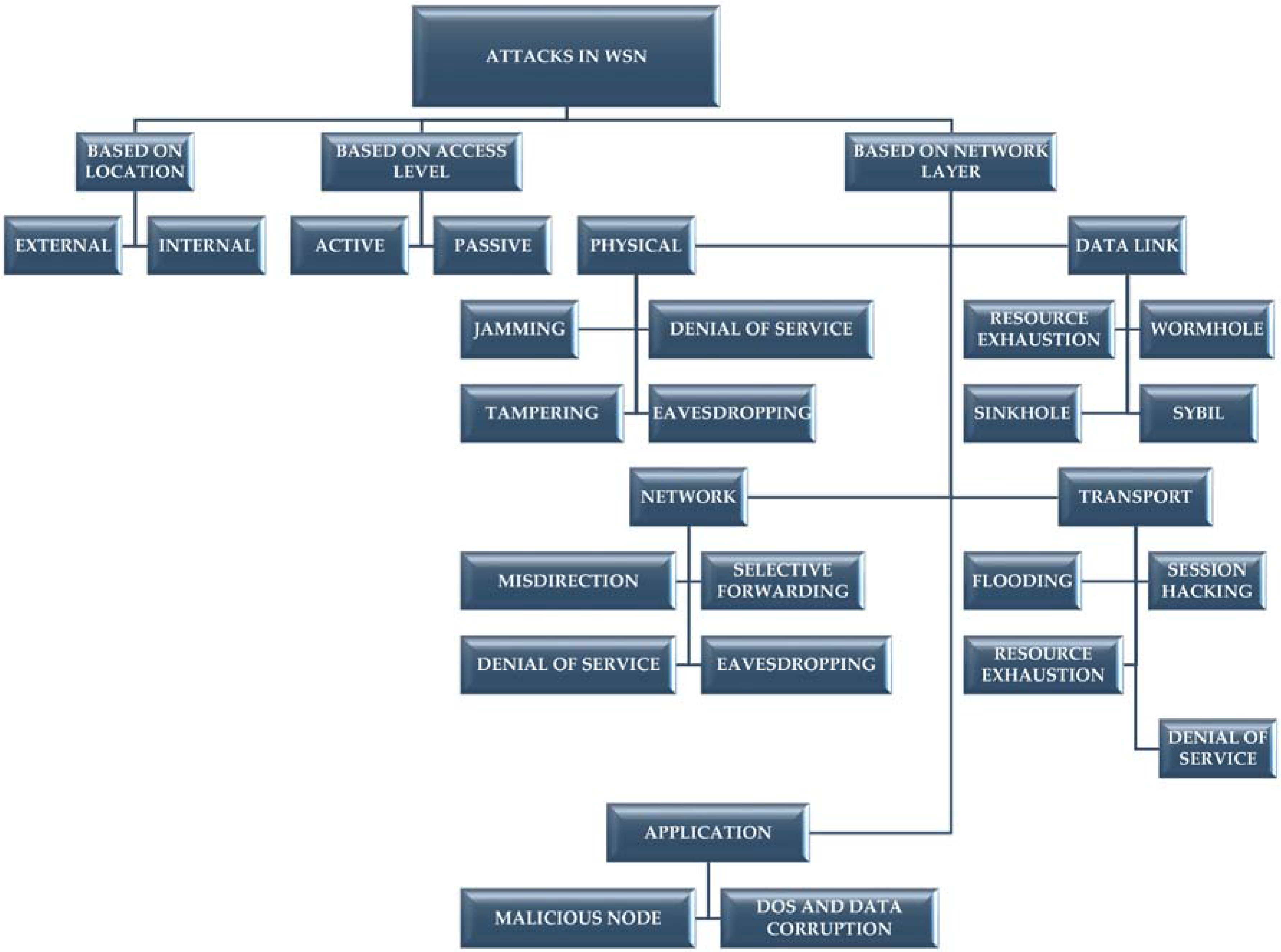
5. Security Issues and Cyber Attacks in Wireless Sensor Networks
- Device Constraints: WSN nodes have very limited storage, processing and computational capabilities. They have limited power as they are battery operated.
- Communication Constraints: WSNs communicate using radio transmissions and most of them use unlicensed ISM band which is used for many other applications. Co-existence of various wireless standards is a major challenge for secured communication.
5.1. Attacks Based on Location of an Intruder
5.1.1. External Attack
5.1.2. Internal Attack
5.2. Attack Based on Access Level of an Intruder
5.2.1. Active
5.2.2. Passive
5.3. Attacks on Various Network Layers
5.3.1. Denial of Service Attack
5.3.2. Misdirection Attack
5.3.3. Selective Forwarding
5.3.4. Sink Hole Attack
5.3.5. Sybil Attack
5.3.6. Wormhole Attack
5.3.7. Hello Flood Attack
6. Intrusion Detection System
- Sensor: It collects statistics from the system being monitored.
- Detector: It analyzes collected data to identify intrusions.
- Information Base: It supports the detector by providing attack signatures.
- Response Manager: It manages the responses to the cyber-attacks.
6.1. Anomaly Detection
- Node Anomaly: This types of anomalies can be detected during failure of WSN node or power problems. Failure of solar panel, or fluctuations in power of different components can cause this type of anomaly. Node anomalies can be due to hardware or software issues in the WSN nodes [82].
- Network Anomaly: Unexpected fluctuations in the signal strength and connection problems can be used to detect network anomaly. Complete loss of connectivity or episodic connectivity can be used to detect intrusions in the network.
- Data Anomaly: An intrusion attempt can be detected from chaotic or disordered data communication.
6.2. Misuse Detection
6.3. Hybrid Detection
7. Topology Control
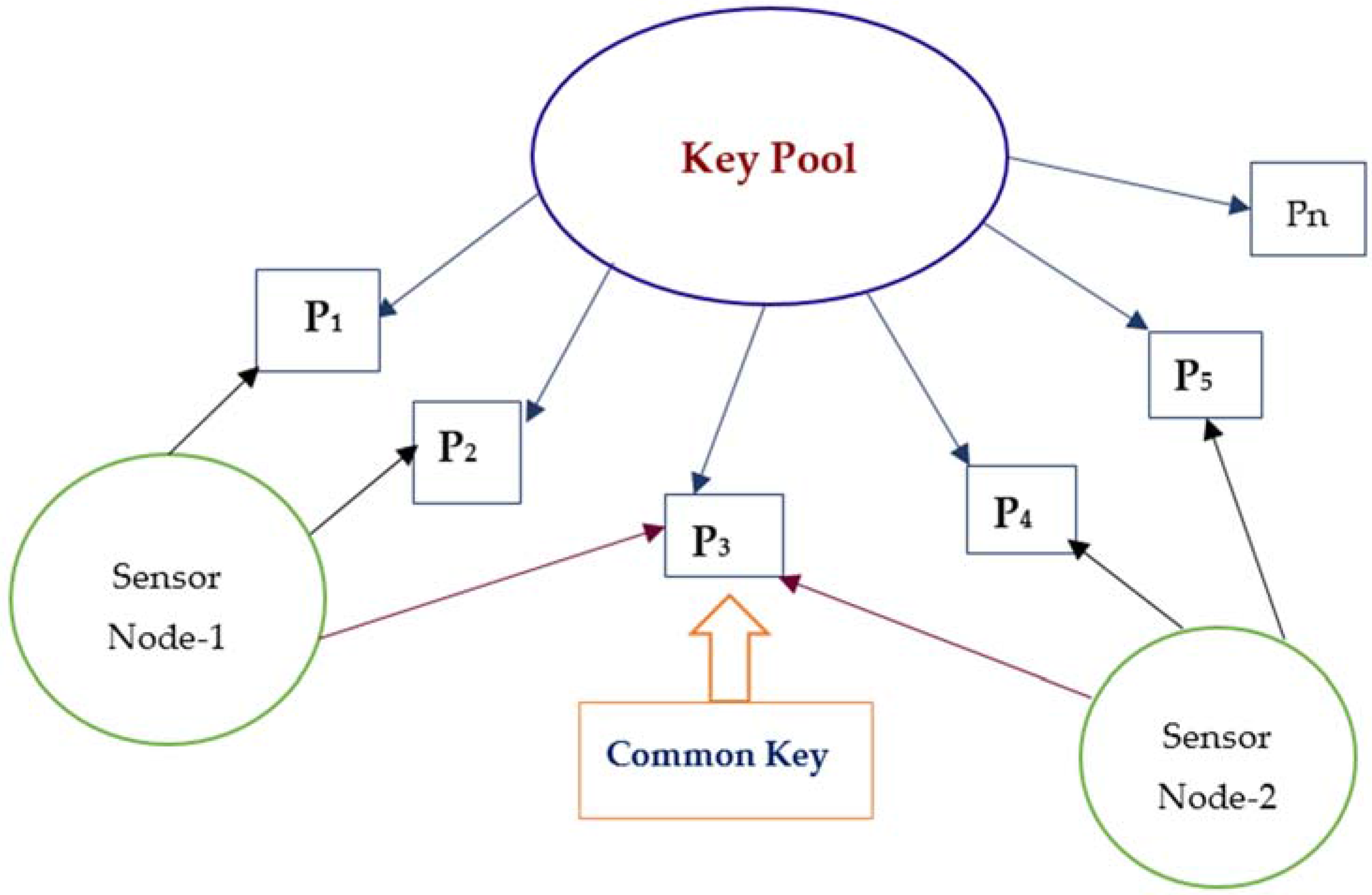
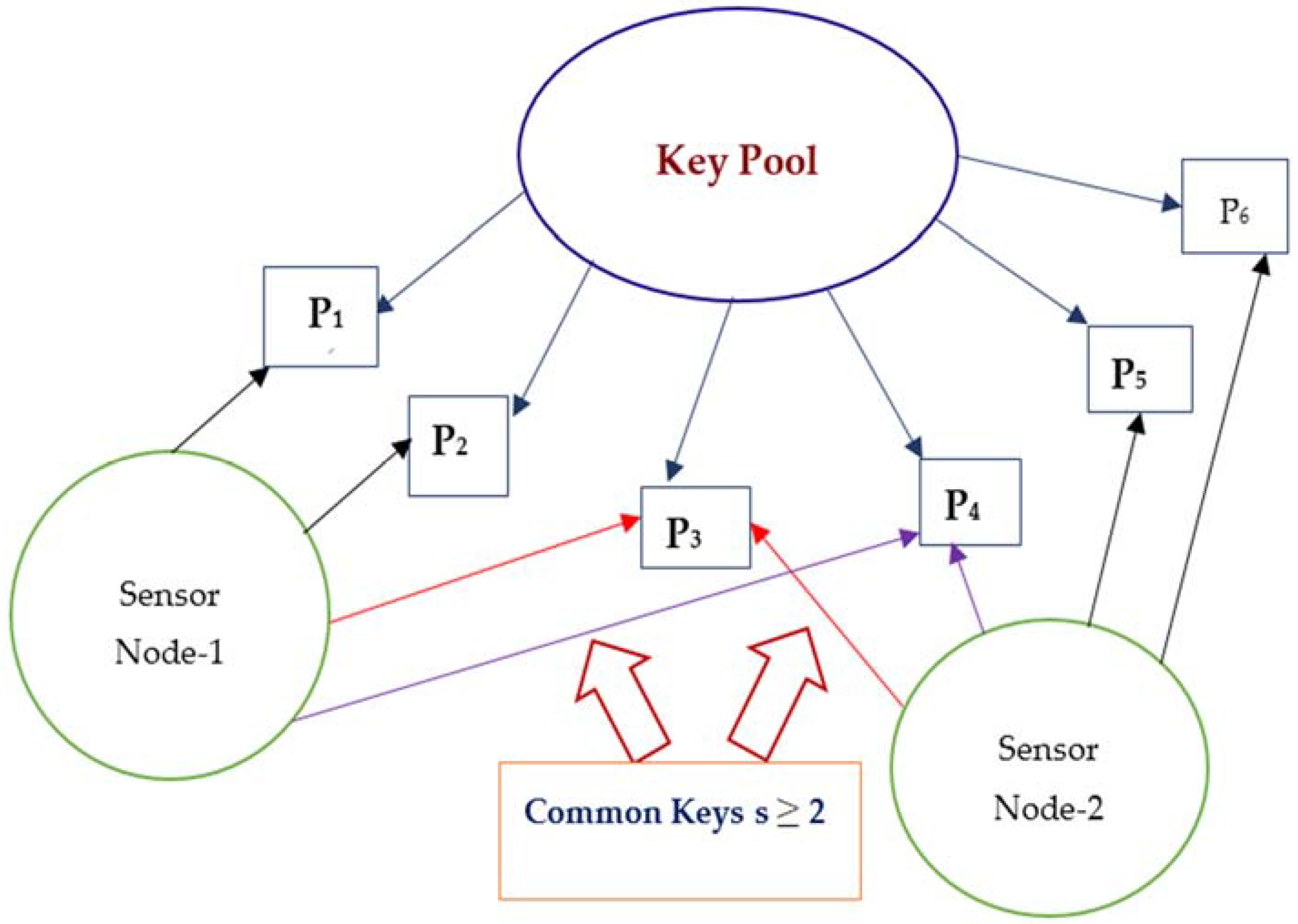
7.1. Random Key Predistribution Scheme
7.1.1. Eschenauer-Gligor Random Key Predistribution Scheme (EG Scheme)
7.1.2. s-Composite Random Key Predistribution Scheme
7.2. Link Constraint Models
7.2.1. Full Visibility Model
7.2.2. On-Off Channel Model
7.2.3. Disk Model
8. Conclusions
Conflicts of Interest
Abbreviations
| AES | Advanced Encryption Standard |
| AMI | Advanced Metering Infrastructure |
| DOS | Denial Of Service |
| EG | Eschenauer–Gligor |
| ETP | European Technology Platform |
| HAN | Home Area Network |
| IDS | Intrusion Detection System |
| IDPS | Intrusion Detection and Prevention System |
| IEC | International Electrotechnical Commission |
| IEEE | Institute of Electrical and Electronics Engineers |
| ISM | Industrial, Scientific and Medical |
| MANET | Mobile and Adhoc NETwork |
| MIMO | Multiple Input Multiple Output |
| NAN | Neighborhood Area Network |
| NIST | National Institute of Standards and Technology |
| OFDM | Orthogonal Frequency Division Multiplexing |
| PHEV | Plug in HybridElectric Vehicle |
| PLC | Power Line Communication |
| SCADA | Supervisory Control And Data Acquisition |
| TDMA | Time Division Multiple access |
| WAN | Wide Area Network |
| Wi-Fi | Wireless Fidelity |
| WSN | Wireless Sensor Network |
References
- Farooq, H.; Jung, L.T. Choices available for implementing smart grid communication network. In Proceedings of the IEEE International Conference on Computer and Information Sciences (ICCOINS), Kuala Lumpur, Malaysia, 3–5 June 2014; pp. 1–5.
- Feng, Z.; Yuexia, Z. Study on smart grid communications system based on new generation wireless technology. In Proceedings of the IEEE International Conference on Electronics, Communications and Control (ICECC), Ningbo, China, 9–11 September 2011; pp. 1673–1678.
- Fang, X.; Misra, S.; Xu, G.; Yang, D. Smart grid—The new and improved power grid: A survey. IEEE Commun. Surv. Tutor. 2012, 14, 944–980. [Google Scholar] [CrossRef]
- Fan, Z.; Kulkarni, P.; Gormus, S.; Efthymiou, C.; Kalogridis, G.; Sooriyabandara, M.; Zhu, Z.; Lambotharan, S.; Chin, W.H. Smart grid communications: Overview of research challenges, solutions, and standardization activities. IEEE Commun. Surv. Tutor. 2013, 15, 21–38. [Google Scholar] [CrossRef]
- U.S. Department of Energy. Smart Grid System Report. Available online: http://energy.gov/sites/prod/files/2014/08/f18/SmartGrid-SystemReport2014.pdf (accessed on 10 August 2016).
- Giustina, D.D.; Rinaldi, S. Hybrid Communication Network for the Smart Grid: Validation of a Field Test Experience. IEEE Trans. Power Deliv. 2015, 30, 2492–2500. [Google Scholar] [CrossRef]
- Goel, N.; Agarwal, M. Smart grid networks: A state of the art review. In Proceedings of the IEEE International Conference on Signal Processing and Communication (ICSC), Noida, India, 16–18 March 2015; pp. 122–126.
- Mulla, A.; Baviskar, S.; Khare, N.; Kazi, F. The Wireless Technologies for Smart Grid Communication: A Review. In Proceedings of the IEEE International Conference on Communication Systems and Network Technologies (CSNT), Gwalior, India, 4–6 April 2015; pp. 442–447.
- Kuzlu, M.; Pipattanasomporn, M.; Rahman, S. Review of communication technologies for smart homes/building applications. In Proceedings of the IEEE International Conference on Smart Grid Technologies—Asia (ISGT ASIA), Bangkok, Thailand, 3–6 November 2015.
- Chhaya, L.; Sharma, P.; Bhagwatikar, G.; Kumar, A. Design and Implementation of Remote Wireless Monitoring and Control of Smart Power System Using Personal Area Network. Indian J. Sci. Technol. 2016, 9, 1–5. [Google Scholar] [CrossRef]
- Parvez, I.; Sundararajan, A.; Sarwat, A.I. Frequency band for HAN and NAN communication in Smart Grid. In Proceedings of the IEEE Computational Intelligence Applications in Smart Grid (CIASG) Symposium, Orlando, FL, USA, 9–12 December 2014.
- Hiew, Y.K.; Aripin, N.M.; Din, N.M. Performance of cognitive smart grid communication in home area network. In Proceedings of the IEEE 2nd International Symposium on Telecommunication Technologies (ISTT), Langkawi, Malaysia, 24–26 November 2014; pp. 417–422.
- Aalamifar, F.; Hassanein, S.; Takahara, G. Viability of powerline communication for the smart grid. In Proceedings of the 26th Biennial Symposium on Communications (QBSC), Kingston, ON, Canada, 28–29 May 2012; pp. 19–23.
- Hartmann, T. Generating realistic Smart Grid communication topologies based on real-data. In Proceedings of the IEEE International Conference on Smart Grid Communications (SmartGridComm), Venice, Italy, 3–6 November 2014; pp. 428–433.
- Parikh, P.P.; Kanabar, M.G.; Sidhu, T.S. Opportunities and challenges of wireless communication technologies for smart grid applications. In Proceedings of the IEEE Power and Energy Society General Meeting, Minneapolis, MN, USA, 25–29 July 2010.
- Yan, Y.; Qian, Y.; Sharif, H.; Tipper, D. A Survey on Smart Grid Communication Infrastructures: Motivations, Requirements and Challenges. IEEE Commun. Surv. Tutor. 2013, 15, 5–20. [Google Scholar] [CrossRef] [Green Version]
- Saputro, N.; Akkaya, K.; Uludag, S. A survey of routing protocols for smart grid communications. Comput. Netw. 2012, 56, 2742–2771. [Google Scholar] [CrossRef]
- Gungor, V.C.; Sahin, D.; Kocak, T.; Ergut, S.; Buccella, C.; Cecati, C.; Hancke, G.P. A Survey on Smart Grid Potential Applications and Communication Requirements. IEEE Trans. Ind. Inform. 2013, 9, 28–42. [Google Scholar] [CrossRef]
- Erol-Kantarci, M.; Mouftah, H.T. Wireless multimedia sensor and actor networks for the next generation power grid. Ad Hoc Netw. 2011, 9, 542–551. [Google Scholar] [CrossRef]
- Binti, M.I.N.; Wei, T.C.; Yatim, A.H.M. Smart grid technology: Communications, power electronics and control system. In Proceedings of the IEEE International Conference on Sustainable Energy Engineering and Application (ICSEEA), Bandung, Indonesia, 14–15 October 2015; pp. 10–14.
- Gungor, V.V. Smart Grid Technologies: Communication Technologies and Standards. IEEE Trans. Ind. Inform. 2011, 7, 529–539. [Google Scholar] [CrossRef]
- Amin, R.; Martin, J.; Zhou, X. Smart Grid communication using next generation heterogeneous wireless networks. In Proceedings of the IEEE Third International Conference on Smart Grid Communications (SmartGridComm), Tainan, Taiwan, 5–8 November 2012; pp. 229–234.
- Bera, S.; Misra, S.; Obaidat, M.S. Energy-efficient smart metering for green smart grid communication. In Proceedings of the IEEE International Conference on Global Communications Conference (GLOBECOM), Austin, TX, USA, 8–12 December 2014; pp. 2466–2471.
- Batista, N.C.; Melicio, R.; Mendes, V.M.F. Layered Smart Grid architecture approach and field tests by Zigbee technology. Energy Convers. Manag. Elsevier 2014, 88, 49–59. [Google Scholar] [CrossRef]
- Kaebisch, S.; Schmitt, A.; Winter, M.; Heuer, J. Interconnections and Communications of Electric Vehicles and Smart Grids. In Proceedings of the IEEE International Conference on Smart Grid Communications (SmartGridComm), Gaithersburg, MD, USA, 4–6 October 2010; pp. 161–166.
- Wang, B.; Sechilariu, M.; Locment, F. Intelligent DC Microgrid with Smart Grid Communications: Control Strategy Consideration and Design. IEEE Trans. Smart Grid 2012, 3, 2148–2156. [Google Scholar] [CrossRef]
- Elkhorchani, H.; Idoudi, M.; Grayaa, K. Development of communication architecture for intelligent energy networks. In Proceedings of the IEEE International Conference on Electrical Engineering and Software Applications (ICEESA), Hammamet, Tunisia, 21–23 March 2013.
- Elkhorchani, H.; Grayaa, K. Smart micro Grid power with wireless communication architecture. In Proceedings of the IEEE International Conference on Electrical Sciences and Technologies in Maghreb (CISTEM), Tunis, Tunisia, 3–6 November 2014.
- Elarabi, T.; Deep, V.; Rai, C.K. Design and simulation of state-of-art ZigBee transmitter for IoT wireless devices. In Proceedings of the IEEE International Symposium on Signal Processing and Information Technology (ISSPIT), Abu Dhabi, UAE, 7–10 December 2015; pp. 297–300.
- Garcia-Hernandez, J. Recent Progress in the Implementation of AMI Projects: Standards and Communications Technologies. In Proceedings of the International Conference on Mechatronics, Electronics and Automotive Engineering (ICMEAE), Prague, Czech Republic, 9–10 July 2015; pp. 251–256.
- Line, M.B.; Tøndel, I.A.; Jaatun, M.G. Cyber security challenges in Smart Grids. In Proceedings of the International Conference on Innovative Smart Grid Technologies (ISGT), Berlin, Germany, 14–17 October 2012.
- Yan, Y.; Qian, Y.; Sharif, H.; Tipper, D. A Survey on Cyber Security for Smart Grid Communications. IEEE Commun. Surv. Tutor. 2012, 14, 998–1010. [Google Scholar] [CrossRef] [Green Version]
- Garner, G. Designing last mile communications infrastructures for intelligent utility networks Smart Grid. In IBM Intelligent Utility Network (IUN) Communication Services; IBM Australia Limited: Sydney, Australia, 2010. [Google Scholar]
- Dzung, D.; Naedele, M.; Von Hoff, T.P.; Crevatin, M. Security for Industrial Communication Systems. IEEE Commun. Surv. Tutor. 2005, 93, 1152–1177. [Google Scholar] [CrossRef]
- Wang, J. Computer Network Security; Springer: Berlin/Heidelberg, Germany, 2009; pp. 3–24. [Google Scholar]
- Lee, E.K.; Gerla, M.; Oh, S.Y. Physical layer security in wireless Smart Grid. IEEE Commun. Mag. 2012, 50, 46–52. [Google Scholar] [CrossRef]
- Wang, W.; Lu, Z. Cyber security in the Smart Grid: Survey and challenges. Comput. Netw. 2013, 57, 1344–1371. [Google Scholar] [CrossRef]
- Shapsough, S.; Qatan, F.; Aburukba, R.; Aloul, F.; Al Ali, A.R. Smart Grid cyber security: Challenges and solutions. In Proceedings of the International Conference on Smart Grid and Clean Energy Technologies (ICSGCE), Offenburg, Germany, 20–23 October 2015; pp. 170–175.
- Saponara, S.; Bacchillone, T. Network Architecture, Security Issues, and Hardware Implementation of a Home Area Network for Smart Grid. Hindawi J. Comput. Netw. Commun. 2012, 1, 1–19. [Google Scholar] [CrossRef]
- Schumacher, M.; Fernandez-Buglioni, E.; Hybertson, D.; Buschmann, F.; Sommerlad, P. Security Patterns: Integrating Security and Systems Engineering; John Wiley: Hoboken, NJ, USA, 2006. [Google Scholar]
- Ahmadi, L.; Croiset, E.; Elkamel, A.; Douglas, P.L.; Unbangluang, W.; Entchev, E. Impact of PHEVs Penetration on Ontario’s Electricity Grid and Environmental Considerations. Energies 2012, 5, 5019–5037. [Google Scholar] [CrossRef]
- Browne, D.; O’Mahony, M.; Caulfield, B. How should barriers to alternative fuels and vehicles be classified and potential policies to promote innovative technologies be evaluated? J. Clean. Prod. 2012, 35, 140–151. [Google Scholar] [CrossRef]
- Guerfi, A.; Dontigny, M.; Charest, P.; Petitclerc, M.; Lagacé, M.; Vijh, A.; Zaghib, K. Improved electrolytes for Li-ion batteries: Mixtures of ionic liquid and organic electrolyte with enhanced safety and electrochemical performance. J. Power Sources 2010, 195, 845–852. [Google Scholar] [CrossRef]
- Amjad, S.; Neelakrishnan, S.; Rudramoorthy, R. Review of design considerations and technological challenges for successful development and deployment of plug-in hybrid electric vehicles. Renew. Sustain. Energy Rev. 2010, 14, 1104–1110. [Google Scholar] [CrossRef]
- Delin, K.; Jackson, S.; Some, R. Sensor webs. NASA Tech. Briefs 1999, 20, 80. [Google Scholar]
- Gibbons, P.; Karp, B.; Ke, Y.; Nath, S.; Seshan, S. Irisnet: An architecture for a worldwide sensor web. IEEE Pervasive Comput. 2003, 4, 22–33. [Google Scholar] [CrossRef]
- Moodley, D.; Simonis, I. A New Architecture for the Sensor Web: The Swap Framework. In Proceedings of the International Semantic Web Conference, Athens, GA, USA, 5–9 November 2006.
- Martinez-Sandoval, R.; Garcia-Sanchez, A.-J.; Garcia-Sanchez, F.; Garcia-Haro, J.; Flynn, D. A Comprehensive WSN-Based Approach to Efficiently Manage a Smart Grid. Sensors 2014, 14, 18748–18783. [Google Scholar] [CrossRef] [PubMed]
- Chang, K.-S.; Kang, S.-M.; Park, K.-J.; Shin, S.-H.; Kim, H.; Kim, H.-S. Electric Field Energy Harvesting Powered Wireless Sensors for Smart Grid. J. Electr. Eng. Technol. 2012, 7, 75–80. [Google Scholar] [CrossRef]
- Kim, K.J.; Cottone, F.; Goyal, S.; Punch, J. Energy scavenging for energy efficiency in networks and applications. Bell Labs Tech. J. 2010, 15, 7–29. [Google Scholar]
- Sallabi, F.M.; Gaouda, A.M.; El-Hag, A.H.; Salama, M.M.A. Evaluation of ZigBee Wireless Sensor Networks under High Power Disturbances. IEEE Trans. Power Deliv. 2011, 29, 13–20. [Google Scholar] [CrossRef]
- Monshi, M.M.; Mohammed, O.A. A study on the efficient wireless sensor networks for operation monitoring and control in smart grid applications. In Proceedings of the IEEE International Southeast Conference, Silicon Valley, CA, USA, 6–9 October 2013.
- Gungor, V.V.; Lu, B.; Hancke, G.P. Opportunities and Challenges of Wireless Sensor Networks in Smart Grid. IEEE Trans. Ind. Electron. 2010, 57, 3557–3564. [Google Scholar] [CrossRef]
- Brak, M.E.; Brak, S.E.; Essaaidi, M.; Benhaddou, D. Wireless Sensor Network applications in smart grid. In Proceedings of the IEEE International Renewable and Sustainable Energy Conference (IRSEC), Ouarzazate, Morocco, 10–13 December 2014; pp. 587–592.
- Zhang, Y.; Li, X.; Zhang, S.; Zhen, Y. Wireless sensor network in smart grid: Applications and issue. In Proceedings of the World Congress on Information and Communication Technologies (WICT), Trivandrum, India, 3 October–2 November 2012; pp. 1204–1208.
- Erol-Kantarci, M.; Mouftah, H.T. Wireless Sensor Networks for smart grid applications. In Proceedings of the IEEE International Conference on Electronics, Communications and Photonics (SIECPC), Riyadh, Saudi Arabia, 24–26 April 2011.
- Erol-Kantarci, M.; Mouftah, H.T. Using wireless sensor networks for energy-aware homes in smart grids. In Proceedings of the IEEE Symposium on Computers and Communications (ISCC), Riccione, Italy, 22–25 June 2010; pp. 456–458.
- Brak, M.E.; Essaaidi, M. Wireless sensor network in smart grid technology: Challenges and opportunities. In Proceedings of the IEEE International Conference on Sciences of Electronics, Technologies of Information and Telecommunications (SETIT), Sousse, Tunisia, 21–24 March 2012; pp. 578–583.
- Mahmood, A.; Javaid, N.; Razzaq, S. A Review of Wireless Communications for Smart Grid. Renew. Sustain. Rev. 2015, 41, 248–260. [Google Scholar] [CrossRef]
- IEEE Std. 802.15.4-2006. Part 15.4: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications for Low-Rate Wireless Personal Area Networks (WPANs); IEEE Press: New York, NY, USA, 2006. [Google Scholar]
- Krishnamurthy, L.; Adler, R.; Buonadonna, P.; Chhabra, J.; Flanigan, M.; Kushalnagar, N.; Nachman, L.; Yarvis, M. Design and deployment of industrial sensor networks: Experiences from a semiconductor plant and the north sea. In Proceedings of the 3rd International Conference on Embedded Networked Sensor Systems, San Diego, CA, USA, 2–4 November 2005; pp. 64–75.
- Horvath, P.; Yampolskiy, M.; Koutsoukos, X. Efficient Evaluation of Wireless Real-Time Control Networks. Sensors 2015, 15, 4134–4153. [Google Scholar] [CrossRef] [PubMed]
- IEEE 802.15.4g-2012. IEEE Standard for Local and Metropolitan Area Networks Part 15.4: Low Rate Wireless Personal Area Networks (LR-WPANs) Amendment: Physical Layer (PHY) Specifications for Low Data Rate, Wireless, Smart Metering Utility Networks; IEEE Press: New York, NY, USA, 2012; pp. 1–258. [Google Scholar]
- Han, S.; Zhu, X.; Mok, A.K.; Chen, D.; Nixon, M. Reliable and Real-Time Communication in Industrial Wireless Mesh Networks. In Proceedings of the 17th IEEE Real-Time and Embedded Technology and Applications Symposium (RTAS), Chicago, IL, USA, 11–14 April 2011; pp. 3–12.
- Lu, Z.; Lu, X.; Wang, C. Review and evaluation of security threats on the communication networks in the smart grid. In Proceedings of the IEEE International Military Communications Conference, San Jose, CA, USA, 31 October–3 November 2010; pp. 1830–1835.
- Dini, G.; Tiloca, M. On simulative analysis of attack impact in Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Emerging Technologies & Factory Automation (ETFA), Cagliari, Italy, 10–13 September 2013.
- Radmand, P.; Talevski, A.; Petersen, S.; Carlsen, S. Taxonomy of Wireless Sensor Network Cyber Security Attacks in the Oil and Gas Industries. In Proceedings of the 24th IEEE International Conference on Advanced Information Networking and Applications, Perth, Australia, 20–23 April 2010; pp. 949–957.
- Mahmood, A.; Akbar, A.H. Threats in end to end commercial deployments of Wireless Sensor Networks and their cross layer solution. In Proceedings of the IEEE International Conference on Information Assurance and Cyber Security (CIACS), Rawalpindi, Pakistan, 12–13 June 2014; pp. 15–22.
- Neogy, S. Security management in Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Cyber Situational Awareness, Data Analytics and Assessment (CyberSA), London, UK, 8–9 June 2015.
- Can, O.; Sahingoz, O.K. A survey of intrusion detection systems in wireless sensor networks. In Proceedings of the 6th IEEE International Conference on Modeling, Simulation, and Applied Optimization (ICMSAO), Istanbul, Turkey, 27–29 May 2015.
- Padmavathi, G.; Shanmugapriya, D. A survey of attacks, security mechanisms and challenges in wireless sensor networks. Int. J. Comput. Sci. Inf. Secur. 2009, 4, 117–125. [Google Scholar]
- Malik, M.Y. An outline of security in wireless sensor networks: Threats, countermeasures and implementations. Wirel. Sens. Netw. Energy Effic. Protoc. Routing Manag. 2011. [Google Scholar] [CrossRef]
- Shukla, J. Babli kumari security threats and defense approaches in wireless sensor networks: An overview. Int. J. Appl. Innov. Eng. Manag. 2013, 2, 165–175. [Google Scholar]
- Nguyen, H.L.; Nguyen, U.T. A study of different types of attacks on multicast in mobile ad hoc networks. Ad Hoc Netw. 2008, 6, 32–46. [Google Scholar] [CrossRef]
- Mohanty, P.; Panigrahi, S.; Sarma, N.; Satapathy, S.S. Security issues in wireless sensor network data gathering protocols: A survey. J. Theor. Appl. Inf. Technol. 2010, 13, 14. [Google Scholar]
- Han, S.; Chang, E.; Gao, L.; Dillon, T. Taxonomy of Attacks on Wireless Sensor Networks. In EC2ND2005; Springer: London, UK, 2006; pp. 97–105. [Google Scholar]
- Lupu, T.G. Main types of attacks in wireless sensor networks. World Sci. Eng. Acad. Soc. 2009, 9, 180–185. [Google Scholar]
- Karlof, C.; Wagner, D. Secure routing in wireless sensor networks: Attacks and countermeasures. Ad Hoc Netw. 2003, 1, 293–315. [Google Scholar] [CrossRef]
- Huang, E.; Scott, C.-H.; MacCallum, E.; David, E.; Du, D.-Z. Attacks and Countermeasures in Sensor Networks: A Survey; Springer: New York, NY, USA, 2010. [Google Scholar]
- Walters, J.P.; Liang, Z.; Shi, W.; Chaudhary, V. Wireless Sensor Network Security: A Survey. In Security in Distributed, Grid and Pervasive Computing; Taylor & Francis: Oxfordshire, UK, 2006. [Google Scholar]
- Mohammadi, S.; Atani, R.E.; Jadidoleslamy, H. A comparison of link layer attacks on wireless sensor networks. J. Inf. Secur. 2011, 2, 69–84. [Google Scholar] [CrossRef]
- Rajkumar; Vani, B.A.; Rajaraman, G.; Chandrakanth, H.G. Security Attacks and its Countermeasures in Wireless Sensor Networks. Int. J. Eng. Res. Appl. 2014, 4, 4–15. [Google Scholar]
- Kavitha, T.; Sridharan, D. Security vulnerabilities in wireless sensor networks: A survey. J. Inf. Assur. Secur. 2010, 5, 31–44. [Google Scholar]
- Ismail, B.; Salvatore, D.M.; Sankar, R. A survey of intrusion detection systems in wireless sensor networks. IEEE Commun. Surv. Tutor. 2014, 16, 266–282. [Google Scholar]
- Granjal, J.; Monteiro, E.; Sá Silva, J. Security for the internet of things: A survey of existing protocols and open research issues. IEEE Commun. Surv. Tutor. 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Diaz, A.; Sanchez, P. Simulation of Attacks for Security in Wireless Sensor Network. Sensors 2016, 16, 1932. [Google Scholar] [CrossRef] [PubMed]
- Zhang, L.; Zhang, H. A Survey on Security and Privacy in Emerging Sensor Networks: From Viewpoint of Close-Loop. Sensors 2016, 16. [Google Scholar] [CrossRef] [PubMed]
- Salehian, S.; Masoumiyan, F.; Udzir, N.I. Energy-efficient intrusion detection in Wireless Sensor Network. In Proceedings of the International Conference on Cyber Security, Cyber Warfare and Digital Forensic (CyberSec), Kuala Lumpur, Malaysia, 26–28 June 2012; pp. 207–212.
- Sun, C.-C.; Liu, C.-C.; Xie, J. Cyber-Physical System Security of a Power Grid: State-of-the-Art. Electronics 2016, 5. [Google Scholar] [CrossRef]
- Wang, Y.; Chu, W.; Fields, S.; Heinemann, C.; Reiter, Z. Detection of Intelligent Intruders in Wireless Sensor Networks. Future Internet 2016, 8. [Google Scholar] [CrossRef]
- Chelli, K. Security Issues in Wireless Sensor Networks: Attacks and Countermeasures. In Proceedings of the World Congress on Engineering (WCE), London, UK, 1–3 July 2015; pp. 519–524.
- Zhang, Y.; Chen, W.; Liang, J.; Zheng, B.; Jiang, S. A Network Topology Control and Identity Authentication Protocol with Support for Movable Sensor Nodes. Sensors 2015, 15, 29958–29969. [Google Scholar] [CrossRef] [PubMed]
- Pietro, R.D.; Mancini, L.V.; Mei, A.; Panconesi, A.; Radhakrishnan, J. Connectivity properties of secure wireless sensor networks. In Proceedings of the ACM Workshop on Security of Ad-Hoc and Sensor Networks, Washington, DC, USA, 25–29 October 2004; pp. 53–58.
- Pietro, R.D.; Mancini, L.V.; Mei, A.; Panconesi, A.; Radhakrishnan, J. Redoubtable sensor networks. ACM Trans. Inf. Syst. Secur. 2008, 11, 1–13. [Google Scholar] [CrossRef]
- Yagan, O. Performance of the Eschenauer–Gligor key distribution scheme under an on/off channel. Trans. Inf. Theory 2012, 58, 3821–3835. [Google Scholar] [CrossRef]
- Jutla, C.S. Encryption modes with almost free message integrity. In Proceedings of the International Conference on Theory and Applications of Cryptographic Techniques (Eurocrypt), Innsbruck, Austria, 6–10 May 2001; pp. 529–544.
- Komls, J.; Szemerdi, E. Limit distribution for the existence of Hamiltonian cycles in a random graph. Discret. Math. 1983, 43, 55–63. [Google Scholar] [CrossRef]
- Blackburn, S.; Gerke, S. Connectivity of the uniform random intersection graph. Discret. Math. 2009, 16, 309–319. [Google Scholar] [CrossRef]
- Bloznelis, S.M. Degree and clustering coefficient in sparse random intersection graphs. Ann. Appl. Probab. 2013, 23, 1254–1289. [Google Scholar] [CrossRef]
- Krishnan, B.; Ganesh, A.; Manjunath, D. On connectivity thresholds in superposition of random key graphs on random geometric graphs. In Proceedings of the IEEE International Symposium on Information Theory (ISIT), Istanbul, Turkey, 7–12 July 2013; pp. 2389–2393.
- Krzywdziński, V.; Rybarczyk, K. Geometric graphs with randomly deleted edges—Connectivity and routing protocols. Math. Found. Comput. Sci. 2011, 69, 544–555. [Google Scholar]


| Major Challenges | Description |
|---|---|
| Severe ecological conditions | Wireless sensor nodes can be subjected to harsh environmental condition which may cause fault in wireless sensor node. |
| Various network topologies | Heterogeneous network topologies in energy distribution network due to various features and failure of sensor nodes may cause technical challenges in design of sensor nodes. |
| Limited capability | Restricted processing and memory capabilities cause various challenges in design and deployment of wireless sensor networks. |
| Bit errors | In communication systems, high bit error rates are observed due to high noise level. This calls for various error detection and correction schemes. Detection and correction of errors require greater memory and processing facilities which make the design of sensor network challenging. |
| Security of sensor networks | Security of wireless sensor network is an indispensable and decisive requirement. The sensor nodes must be secured from physical tampering to hacking for smooth functioning of various smart grid applications. Physical tampering is also called node capture. |
| Quality of service necessities for smart grid environment | The parameters like high data rates, latency, reliability and authenticity are vital for quality of service necessities of smart grid applications. Wireless sensor networks must fulfill these criterions for successful implementation of various applications. |
| Protocol/Standard | Spectrum Type | Frequency Band | Maximum Data Throughput | Coverage Range | Advantages | Disadvantages | Market Espousal |
|---|---|---|---|---|---|---|---|
| Zigbee | Unlicensed | 868 MHz, 915 MHz, 2.4 MHz | 250 Kbps | Up to 100 m | Low cost, Low power usage, Less complex | Low data rate, Short range, Interference with other technologies using ISM band, Low battery power supply | Very High |
| Bluetooth | Unlicensed | 2.4 GHz | 21 Kbps | Up to 100 m | Low power usage | Low data rates, Very short range, Less secured, Interference with other technologies using ISM band | Very High |
| Wi-Fi | Unlicensed | 2.4 GHz, 5.8 GHz | 2 Mbps to 54 Mbps | Up to 250 m | High data rates, Robust, Point to point and point to multipoint communication, Low cost, IP support and network scalability | Complex design, Prone to interference, data rates may deteriorate due to interference or co-existence problems | Very high |
| Z-Wave | Unlicensed | 868 MHz, 908 MHz | 9.6 Kbps to 40 Kbps | Up to 30 m | Low power usage | Very Low data rates, Short range | Medium |
| WirelessHART | Unlicensed | 2.4 GHz | Up to 250 Kbps | 200 m | Simple and low cost solutions, Allows co-existence of multiple networks, Keeps the black and white list of devices, Self-organizing standard, More secured | All the devices operating on WirelessHART must have routing capability, No directive on how the network is configured by network manager | Very high for industrial control applications |
| 6LoWPAN | Unlicensed | 868 MHz, 915 MHz, 2.4 MHz | Up to 250 Kbps | Up to 100 m | Low power usage | Low data rates, Short range | Medium |
| Wavenis | Unlicensed | 868 MHz, 915 MHz, and 433 MHz | 4.8 Kbps to 100 Kbps | Up to 200 m | Low power usage | Very Low data rates, Short range | Very low |
| Layer | Attack | Countermeasures |
|---|---|---|
| Physical | DOS (denial of service), Jamming, Node Capture | Spread spectrum technology, Adaptive antennas |
| Data Link | Wormhole, Sink hole, Sybil, Resource exhaustion | Link layer cryptography |
| Network | DOS, Misdirection, Selective forwarding, Eavesdropping | Key management, Secured routing, Topology control |
| Transport | Flooding, Session hacking, Resource exhaustion, DOS | Intrusion detection, encryption |
| Application | DOS, Data corruption, Malicious node | Intrusion detection, Malicious node isolation |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chhaya, L.; Sharma, P.; Bhagwatikar, G.; Kumar, A. Wireless Sensor Network Based Smart Grid Communications: Cyber Attacks, Intrusion Detection System and Topology Control. Electronics 2017, 6, 5. https://doi.org/10.3390/electronics6010005
Chhaya L, Sharma P, Bhagwatikar G, Kumar A. Wireless Sensor Network Based Smart Grid Communications: Cyber Attacks, Intrusion Detection System and Topology Control. Electronics. 2017; 6(1):5. https://doi.org/10.3390/electronics6010005
Chicago/Turabian StyleChhaya, Lipi, Paawan Sharma, Govind Bhagwatikar, and Adesh Kumar. 2017. "Wireless Sensor Network Based Smart Grid Communications: Cyber Attacks, Intrusion Detection System and Topology Control" Electronics 6, no. 1: 5. https://doi.org/10.3390/electronics6010005
APA StyleChhaya, L., Sharma, P., Bhagwatikar, G., & Kumar, A. (2017). Wireless Sensor Network Based Smart Grid Communications: Cyber Attacks, Intrusion Detection System and Topology Control. Electronics, 6(1), 5. https://doi.org/10.3390/electronics6010005







