Energy-Efficient Method for Wireless Sensor Networks Low-Power Radio Operation in Internet of Things
Abstract
1. Introduction
2. Related Works
3. Software Platform and Simulation Tools
3.1. Platform
3.2. Energest Module
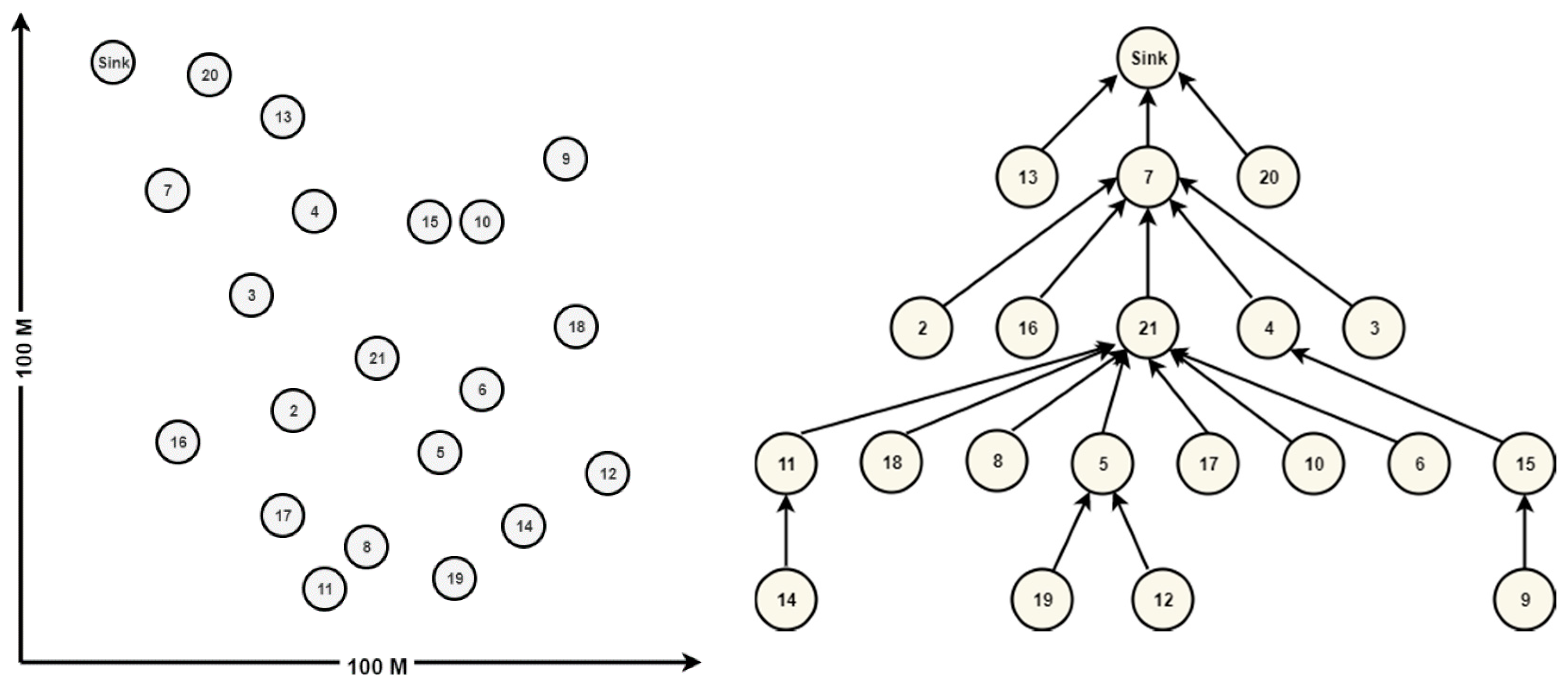
3.3. Network Scenario
3.4. Network Protocols
4. Problem Statement
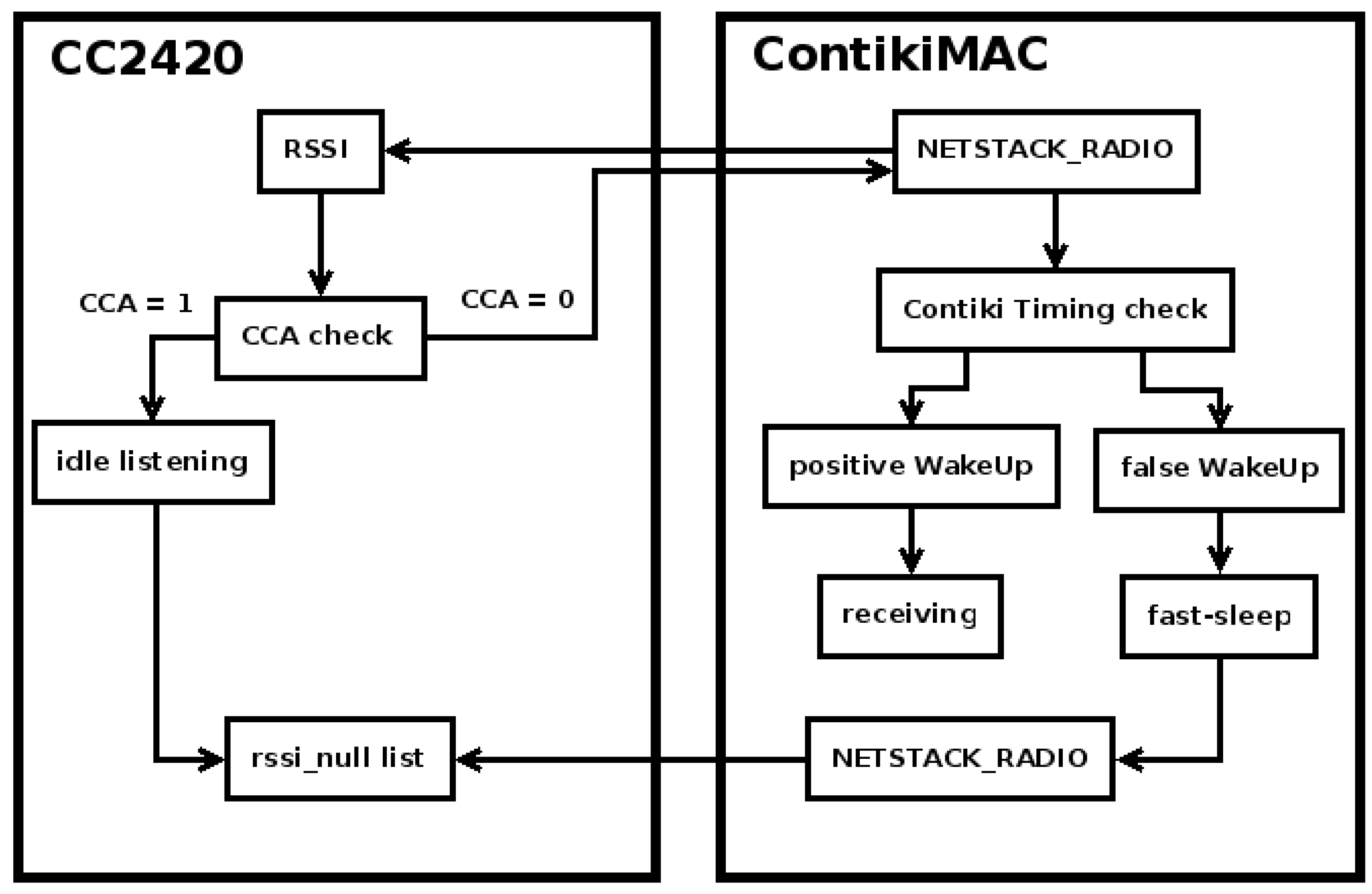
5. Lightweight Clear Channel Assessment (LW-CCA)
5.1. Time Factors in a Single RSSI Radio Check
- Phase 1: Checking permissions for radio driver access by RDC, registering radio hardware to Rx mode by the radio driver, and recording start time of Rx by Energest.
- Phase 2: Validating the RSSI and returning RSSI value from related radio register.
- Phase 3: Set the radio registers to ‘off’ state, Preparing the radio queue for the next stage of radio activity and also announce the end of Rx state to Energest module.
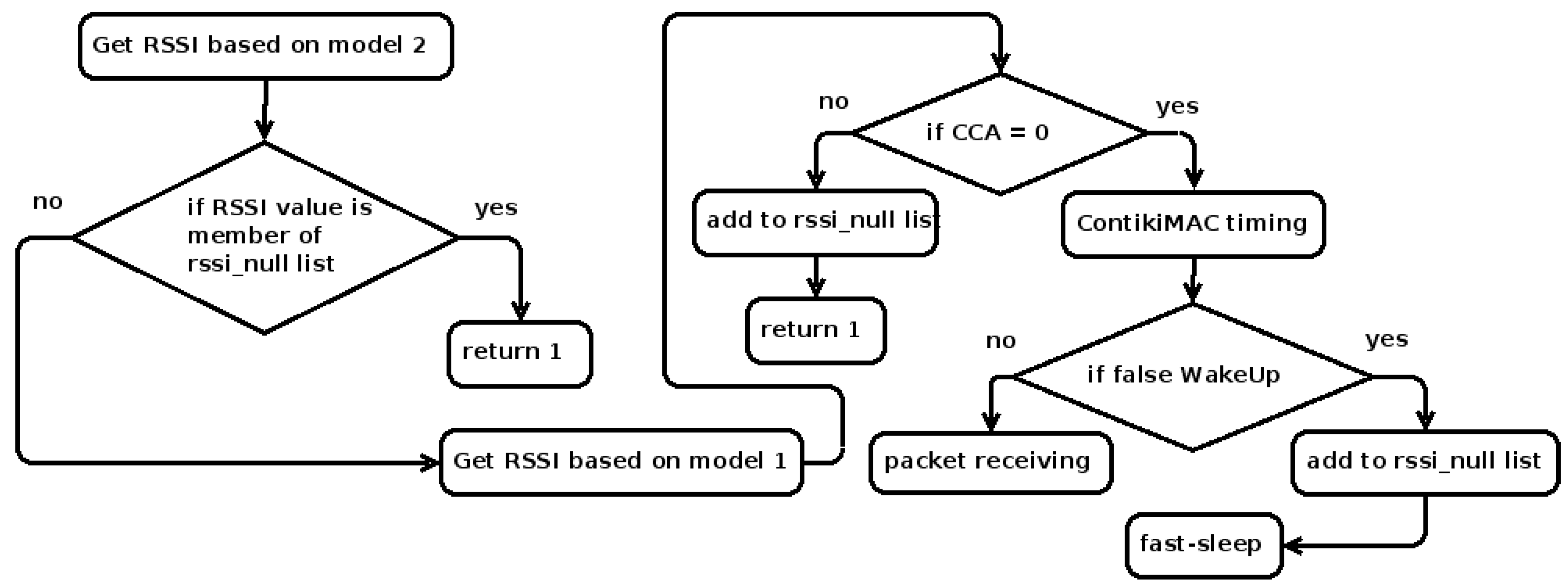
5.2. RSSI Check Time Models in LW-CCA
| static void wait_for_status(uint8_t status_bit) { rtimer_clock_t t0; t0 = RTIMER_NOW(); while(!(get_status() & status_bit) && RTIMER_CLOCK_LT(RTIMER_NOW(), t0 + RTIMER_SECOND / 10); } |
| static void wait_for_status(uint8_t status_bit) { rtimer_clock_t t0; t0 = RTIMER_NOW(); while(!(get_status() & status_bit) && RTIMER_CLOCK_LT(RTIMER_NOW(), t0); } |
5.3. Categories of RSSIs in LW-CCA
5.4. Dynamic RSSI Check Time in LW-CCA
6. Comparison of LW-CCA with ContikiMAC
- 1 emulated node that is programmed as a sink that plays the role of the root node for RPL in the network graph. In fact, it is a UDP server that collects data from client nodes;
- 21 emulated duty cycle nodes as UDP clients in network graph that send data to sink;
- power consumption of the nodes being estimated by the Energest module available at Contiki.
6.1. Average of Ticks in CPU, LPM, Rx, and Tx States in the Network
6.2. Average of Percentage for Listen and Transmit Duty Cycle in the Network
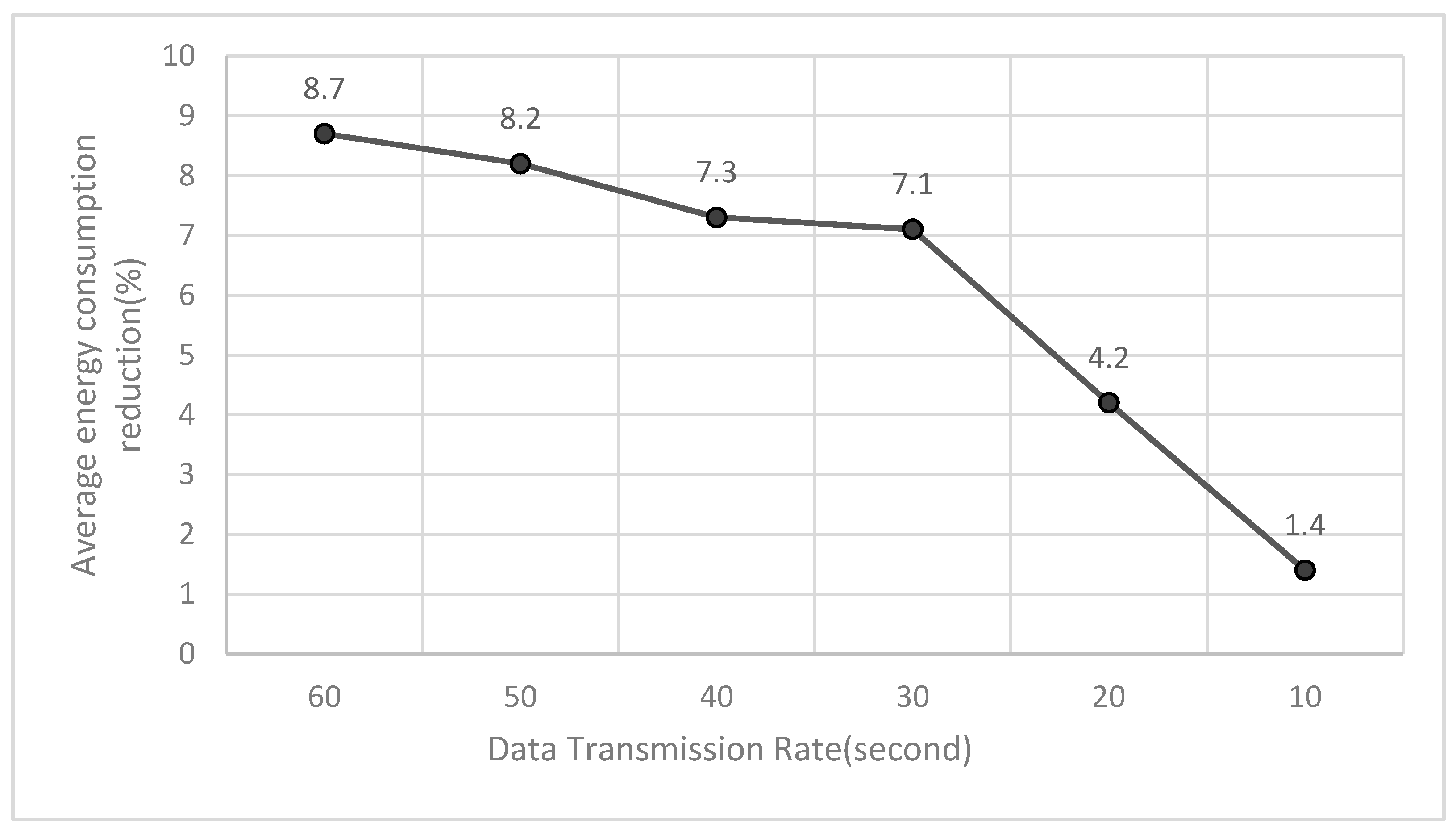
6.3. Network Power Consumption
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| Abbreviation | Definition |
| CCA | Clear Channel Assessments |
| CPU | Central Processing Unit |
| CSMA | Carrier Sense Multiple Access with Collision Avoidance |
| IoT | Internet of Things |
| LPL | Low Power Listening |
| LPM | Low Power Mode |
| LW-CCA | Light Weight CCA |
| MAC | Medium Access Control |
| MCU | Microcontroller Unit |
| PDR | Packet Delivery Rate |
| RDC | Radio Duty Cycle |
| RPL | Routing Protocol for LLNs |
| RSSI | Received Signal Strength Indicator |
| UDP | User Datagram Protocol |
| VCC | Voltage at the Common Collector |
| WSN | Wireless Sensor Network |
References
- Avallone, S.; Guadagno, S.; Emma, D.; Pescapè, A.; Ventre, G. D-ITG distributed internet traffic generator. In Proceedings of the 1st International Conference on Quantitative Evaluation of Systems (QEST 2004), Enschede, The Netherlands, 27–30 September 2004; pp. 316–317. [Google Scholar]
- Dutta, P.; Dunkels, A. Operating systems and network protocols for wireless sensor networks. Philos. Trans. R. Soc. A Math. Phys. Eng. Sci. 1958, 370, 68–84. [Google Scholar] [CrossRef]
- Homaei, M.H.; Salwana, E.; Shamshirband, S. An Enhanced Distributed Data Aggregation Method in the Internet of Things. Sensors 2019, 19, 3173. [Google Scholar] [CrossRef]
- Thang, V.C. A Comparative Study of Network Performance between ContikiMAC and XMAC Protocols in Data Collection Application with ContikiRPL. Int. J. Comput. Netw. Inf. Secur. 2019, 11, 32. [Google Scholar]
- Bhar, J. A Mac Protocol Implementation for Wireless Sensor Network. J. Comput. Netw. Commun. 2015, 2015, 1–12. [Google Scholar] [CrossRef]
- Sha, M.; Hackmann, G.; Lu, C. Energy-efficient Low Power Listening for Wireless Sensor Networks in Noisy Environments. Proc. 12th Int. Conf. Inf. Process. Sens. Netw. 2013, 61, 277–288. [Google Scholar]
- Zheng, X.; Cao, Z.; Wang, J.; He, Y.; Liu, Y. Interference resilient duty cycling for sensor networks under co-existing environments. IEEE Trans. Commun. 2017, 65, 2971–2984. [Google Scholar] [CrossRef]
- Huang, Y.; XIANG, W.; WEN, S.; JIN, Y. The Study of Traffic-Aware ContikiMAC. DEStech Trans. Comput. Sci. Eng. 2016. [Google Scholar] [CrossRef]
- Aoudia, F.A.; Magno, M.; Gautier, M.; Berder, O.; Benini, L. Wake-up receivers for energy efficient and low latency communication. In Proceedings of the 15th International Conference on Information Processing in Sensor Networks, California, CA, USA, 11–14 April 2016. [Google Scholar]
- Magno, M.; Aoudia, F.A.; Gautier, M.; Berder, O.; Benini, L. WULoRa: An energy efficient IoT end-node for energy harvesting and heterogeneous communication. Proc. 2017 Des. Autom. Test Eur. DATE 2017, 2017, 1528–1533. [Google Scholar]
- Khomami, M.M.D.; Rezvanian, A.; Meybodi, M.R. A new cellular learning automata-based algorithm for community detection in complex social networks. J. Comput. Sci. 2018, 24, 413–426. [Google Scholar] [CrossRef]
- Basagni, S. CTP-WUR: The Collection Tree Protocol in Wake-up Radio WSNs for Critical Applications. In Proceedings of the 2016 International Conference on Computing, Networking and Communications (ICNC), Beijing, China, 4–6 June 2016. [Google Scholar]
- Guo, C.; Zhong, L.C.; Rabaey, J.M. Low power distributed MAC for ad hoc sensor radio networks. In Proceedings of the GLOBECOM’01. IEEE Global Telecommunications Conference (Cat. No. 01CH37270), Oslo, Norway, 25–29 November 2001. [Google Scholar]
- Mahlknecht, S.; Durante, M.S. WUR-MAC: Anergy efficient wakeup receiver based MAC protocol. IFAC Proc. 2009, 42, 79–83. [Google Scholar] [CrossRef]
- Joshi, G.P.; Nam, S.Y.; Kim, S.W. Cognitive radio wireless sensor networks: Applications, challenges and research trends. Sensors 2013, 13, 11196–11228. [Google Scholar] [CrossRef] [PubMed]
- Sutton, F.; Buchli, B.; Beutel, J.; Thiele, L. Zippy: On-demand network flooding. In Proceedings of the 13th ACM Conference on Embedded Networked Sensor Systems, Seoul, Korea, 1–4 November 2015; pp. 45–58. [Google Scholar]
- Homaei, M.H.; Soleimani, F.; Shamshirband, S.; Mosavi, A.; Nabipour, N.; Varkonyi-Koczy, A.R. An Enhanced Distributed Congestion Control Method for Classical 6LowPAN Protocols Using Fuzzy Decision System. IEEE Access 2020, 8, 20628–20645. [Google Scholar] [CrossRef]
- Rayanchu, S.; Patro, A.; Banerjee, S. Airshark: Detecting non-WiFi RF Devices Using Commodity WiFi Hardware. In Proceedings of the 2011 ACM SIGCOMM conference on Internet measurement conference, Berlin, Germany, 2–4 November Novermber 2011. [Google Scholar]
- Rayanchu, S.; Patro, A.; Banerjee, S. Catching Whales and Minnows using Wifinet: Deconstructing Non-wifi Interference using Wifi Hardware. In Proceedings of the 9th USENIX conference on Networked Systems Design and Implementation, San Jose, CA, USA, 25–27 April 2012. [Google Scholar]
- Hong, S.; Katti, S. DOF: A Local Wireless Information Plane. In Proceedings of the ACM SIGCOMM 2011 conference, Toronto, ON, Canada, 15–19 August 2011. [Google Scholar]
- Chowdhury, K.R.; Akyildiz, I.F. Interferer classification, channel selection and transmission adaptation for wireless sensor networks. In Proceedings of the 2009 IEEE International Conference on Communications, Dresden, Germany, 14–18 June 2009. [Google Scholar] [CrossRef]
- Bloessl, B.; Joerer, S.; Mauroner, F.; Dressler, F.; Joerer, S. Low-cost interferer detection and classification using TelosB sensor motes. In Proceedings of the 18th Annual International Conference on Mobile Computing and Networking, Seattle, WA, USA, 22–26 August 2012; pp. 403–406. [Google Scholar]
- Zhou, R.; Xiong, Y.; Xing, G.; Sun, L.; Ma, J. ZiFi: Wireless LAN discovery via ZigBee interference signatures. In Proceedings of the 16th Annual International Conference on Mobile Computing and Networking, Chicago, IL, USA, 20–24 Sepetember 2010. [Google Scholar]
- Hermans, F.; Ngai, E. SoNIC: Classifying Interference in 802. 15. 4 Sensor Networks. In Proceedings of the 12th International Conference on Information Processing in Sensor Networks, Philadelphia, PA, USA, 8–11 April 2013. [Google Scholar]
- King, A.; Roedig, U. Differentiating Clear Channel Assessment Using Transmit Power Variation. ACM Trans. Sens. Netw. 2018, 14, 1–28. [Google Scholar] [CrossRef]
- Uwase, M.P.; Bezunartea, M.; Tiberghien, J.; Dricot, J.M.; Steenhaut, K. Experimental Comparison of Radio Duty Cycling Protocols for Wireless Sensor Networks. IEEE Sens. J. 2017, 17, 6474–6482. [Google Scholar] [CrossRef]
- Zheng, X.; Cao, Z.; Wang, J.; He, Y.; Liu, Y. ZiSense: Towards Interference Resilient Duty Cycling in Wireless Sensor Networks. In Sensys’14; ACM: New York, NY, USA, 2014; Volume 14, pp. 119–133. [Google Scholar]
- Oller, J.; Demirkol, I.; Casademont, J.; Paradells, J.; Gamm, G.U.; Reindl, L. Has Time Come to Switch from Duty-Cycled MAC Protocols to Wake-Up Radio for Wireless Sensor Networks? IEEE/ACM Trans. Netw. 2016, 24, 674–687. [Google Scholar] [CrossRef]
- Ojo, M.O.; Member, S.; Giordano, S.; Member, S.; Procissi, G.; Seitanidis, I.N. A Review of Low-End, Middle-End, and High-End Iot Devices. IEEE Access 2019, 6, 70528–70554. [Google Scholar] [CrossRef]
- Joshi, M.; Kaur, B. Web Integrated Smart Home Infrastructure Using Internet of Things. Int. J. Eng. Res. Gen. Sci. 2015, 3, 153–158. [Google Scholar]
- Velinov, A.; Mileva, A. Running and Testing Applications for Contiki OS Using Cooja Simulator. In Proceedings of the 7th International Conference on Information Technologies and Education Development – ITRO 2016, Zrenjanin, Serbia, 10 June 2016; pp. 279–285. [Google Scholar]
- Sadiki, S.; Ramadany, M.; Faccio, M.; Amegouz, D.; Boutahari, S. Running Smart Monitoring Maintenance Application Using Cooja Simulator. Int. J. Eng. Res. Afr. 2019, 42, 149–159. [Google Scholar]
- Instruments, T.; Slas, I. MSP430F15x, MSP430F16x, MSP430F161x Mixed Signal Microcontroller. Data Sheet. Available online: https://www.ti.com/lit/ds/symlink/msp430f1611.pdf (accessed on 14 January 2020).
- Nasseri, M.; Al-Olimat, H.; Alam, M.; Kim, J.; Green, R.; Cheng, W. Contiki Cooja Simulation for Time Bounded Localization in Wireless Sensor Network. Proc. 18th Symp. Commun. Netw. 2015, 8, 1–7. [Google Scholar]
- Mansoor, K.; Ghani, A.; Chaudhry, S.A. Securing IoT-Based RFID Systems: A Robust Authentication Protocol Using Symmetric Cryptography. Sensors 2019, 19, 4752. [Google Scholar] [CrossRef]
- Schandy, J.; Steinfeld, L.; Silveira, F. Average power consumption breakdown of Wireless Sensor Network nodes using IPv6 over LLNs. In Proceedings of the 2015 International Conference on Distributed Computing in Sensor Systems, Fortaleza, Brazil, 10–12 June 2015. [Google Scholar]
- Son, N.M.; Thinh, T.N.; Thi, N.D.; Nhan, N.C. An Approach of Low Power Wifi Sensor Mote for Internet of Things Applications Faculty of Computer Engineering, Faculty of Computer Science and Engineering. J. Emerg. Trends Eng. Appl. Sci. 2016, 7, 161–166. [Google Scholar]
- SNM. Tmote Sky Sensor Datasheet. Available online: http://www.crew-project.eu/sites/default/files/tmote-sky-datasheet.pdf (accessed on 14 January 2020).
- Michel, M.; Quoitin, B. Technical Report: ContikiMAC vs X-MAC performance analysis. Netw. Internet Archit. 2015, 5, 1–28. [Google Scholar]
- Sitanayah, L.; Sreenan, C.J.; Fedor, S. A Cooja-based tool for maintaining sensor network coverage requirements in a building. In Proceedings of the 11th ACM Conference on Embedded Networked Sensor Systems, Roma, Italy, 11–15 November 2013. [Google Scholar]
- Österlind, F.; Eriksson, J.; Dunkels, A. Cooja TimeLine: A power visualizer for sensor network simulation. In Proceedings of the 8th ACM Conference on Embedded Networked Sensor Systems, Zürich, Switzerland, 3–5 November 2010. [Google Scholar]
- T.C.O.S.O. for the Internet of Things. Dunkels, Adam, The Contiki Open Source OS for the Internet of Things. Available online: https://github.com/contiki-os/contiki/blob/master/dev/cc2420/cc2420.c (accessed on 8 December 2019).
- Quan, Y. Topology-Based Device Self-identification in Wireless Mesh Networks; School of Electrical Engineering and Computer Science: Stockholm, Sweden, 2019. [Google Scholar]
- Baccelli, E.; Gündoğan, C.; Hahm, O.; Kietzmann, P.; Lenders, M.S.; Petersen, H.; Schleiser, K.; Schmidt, T.C.; Wählisch, M. RIOT: An open source operating system for low-end embedded devices in the IoT. IEEE Internet Things J. 2018, 5, 4428–4440. [Google Scholar] [CrossRef]





| Parameter | Type | ON() | RSSI() | OFF() |
|---|---|---|---|---|
| SRXON | register | |||
| SRFOFF | register | ✓ | ||
| RSSI | register | ✓ | ||
| SNOP | register | ✓ | ✓ | |
| SFLUSHRX | register | ✓ | ||
| RXFIFO | register | ✓ | ||
| RSSI_VALID | status bit | * | ||
| _ACTIVE | status bit | * | ||
| CSN | pin | * | ||
| FIFOP | pin | * |
| Variable | Power Current Consumption State | Value | Unit |
|---|---|---|---|
| VCC | Supply voltage | 3 | volt |
| PC_CPU | MCU on, Radio off | 1.8 | mW |
| PC_LPM | MCU idle, Radio off | 0.0545 | mW |
| PC_Tx | MCU on, Radio Tx | 17.7 | mW |
| PC_Rx | MCU on, Radio Rx | 20 | mW |
| Layer | Protocol | Standard |
|---|---|---|
| Application | Collect view | - |
| Transport | UDP | IETF RFC 768 |
| Network | RPL/IPv6 | IETF RFC 6550 |
| Adaptation | 6lowpan | IETF RFC 6282 |
| Data link | IEEE 802.15.4 MAC (CSMA) | IEEE 802.15.4 |
| Radio Duty Cycling | ContikiMAC | - |
| Physical | IEEE 802.15.4 PHY | IEEE 802.15.4 |
| Variable | CPU Ticks | Unit (ms) |
|---|---|---|
| CCA_CHECK_TIME | 32768/8192 | 0.4 |
| CCA_SLEEP_TIME | (32768/2000) + 1 | 1.7 |
| MAX_NONACTIVITY_PERIODS | 10 × (CCA_CHECK_TIME + CCA_SLEEP_TIME) | 21 |
| Node Number | Idle Listenings | False WakeUp |
|---|---|---|
| 5 | 11,357 | 115 |
| 7 | 13,895 | 220 |
| 12 | 12,082 | 50 |
| (ms) | ||
|---|---|---|
| 0.32 | 0.128 | 0.448 |
| Method | Listen Duty-Cycle (%) | |
|---|---|---|
| Model 1 | RSSI | CCA | 1.451 |
| Model 2 | RSSI | CCA | 1.282 |
| RDC | CPU_time | LPM_time | Rx_time | Tx_time |
|---|---|---|---|---|
| ContikiMAC (Low Rate) | 4498.73 | 46,354.15 | 511.15 | 145.71 |
| ContikiMAC (High Rate) | 4834.95 | 47,584.65 | 719.45 | 273.50 |
| LW-CCA (Low Rate) | 4537.25 | 47,478.90 | 425.40 | 147.52 |
| LW-CCA (High Rate) | 5066.35 | 48,036.60 | 601.05 | 281.30 |
| RDC | Rx Duty Cycle (%) | Tx Duty Cycle (%) |
|---|---|---|
| ContikiMAC (low rate) | 1.005 | 0.286 |
| ContikiMAC (high rate) | 1.372 | 0.521 |
| LW-CCA (low rate) | 0.817 | 0.283 |
| LW-CCA (high rate) | 1.131 | 0.529 |
| RDC | P_CPU (mW) | P_LPM (mW) | P_Rx (mW) | P_Tx (mW) | P (mW) | PDR (%) |
|---|---|---|---|---|---|---|
| ContikiMAC (low rate) | 0.477 | 0.149 | 0.603 | 0.152 | 1.381 | 99 |
| ContikiMAC (high rate) | 0.498 | 0.148 | 0.823 | 0.277 | 1.746 | 99 |
| LW-CCA (low rate) | 0.471 | 0.149 | 0.490 | 0.150 | 1.260 | 99 |
| LW-CCA (high rate) | 0.515 | 0.147 | 0.679 | 0.281 | 1.622 | 99 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Amirinasab Nasab, M.; Shamshirband, S.; Chronopoulos, A.T.; Mosavi, A.; Nabipour, N. Energy-Efficient Method for Wireless Sensor Networks Low-Power Radio Operation in Internet of Things. Electronics 2020, 9, 320. https://doi.org/10.3390/electronics9020320
Amirinasab Nasab M, Shamshirband S, Chronopoulos AT, Mosavi A, Nabipour N. Energy-Efficient Method for Wireless Sensor Networks Low-Power Radio Operation in Internet of Things. Electronics. 2020; 9(2):320. https://doi.org/10.3390/electronics9020320
Chicago/Turabian StyleAmirinasab Nasab, Mehdi, Shahaboddin Shamshirband, Anthony Theodore Chronopoulos, Amir Mosavi, and Narjes Nabipour. 2020. "Energy-Efficient Method for Wireless Sensor Networks Low-Power Radio Operation in Internet of Things" Electronics 9, no. 2: 320. https://doi.org/10.3390/electronics9020320
APA StyleAmirinasab Nasab, M., Shamshirband, S., Chronopoulos, A. T., Mosavi, A., & Nabipour, N. (2020). Energy-Efficient Method for Wireless Sensor Networks Low-Power Radio Operation in Internet of Things. Electronics, 9(2), 320. https://doi.org/10.3390/electronics9020320







