The SSP-Tree: A Method for Distributed Processing of Range Monitoring Queries in Road Networks
Abstract
:1. Introduction
2. Problem Statement and System Overview
2.1. Background and Problem Statement
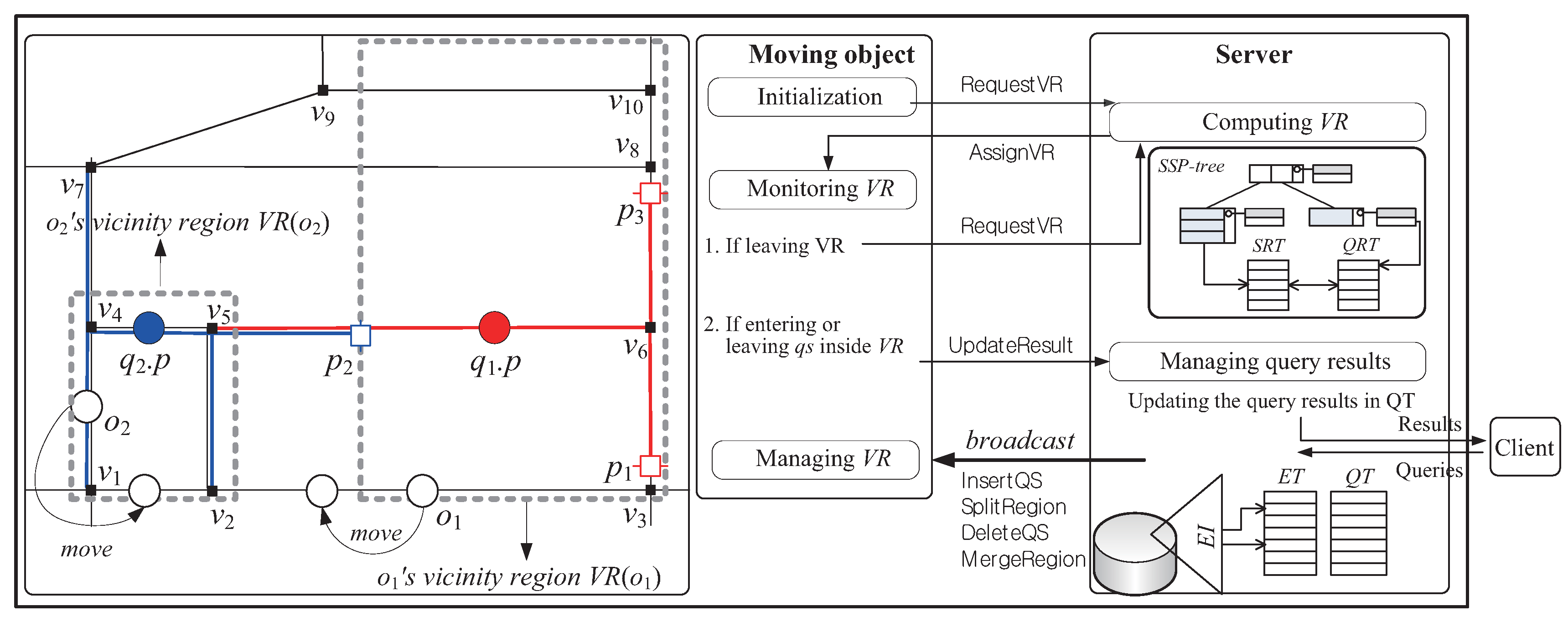
2.2. System Overview
- Moving objects: Each moving object o, which is identified by its unique identifier , is capable of sensing the point of its current location and has some available computational capability . We assume (i) that each moving object o has a heterogeneous capability , which is measured by the maximum number of query segments it can process, and (ii) that , where is a system parameter indicating the minimum number of query segments o should process; thus, a moving object with a more powerful capability can be assigned a larger vicinity region that contains a more number of query segments. There are two types of location-update messages sent from the moving objects to the server: RequestVR and UpdateResult. The former is for the purpose of receiving a new vicinity region, whereas the latter is to let the server update the result of a query (if necessary). For example, assuming the moving object in Figure 3 is assigned the vicinity region together with query segments , , and , it sends the RequestVR message to the server because it leaves . On the other hand, assuming the moving object in Figure 3 is assigned the vicinity region together with query segments , , and , it sends the UpdateResult message to the server because it leaves .
- Clients: Each client is able to issue multiple range monitoring queries over the moving objects, and continually receives the up-to-date results of these queries from the server via wireless or high-speed wired connections. Each query q, issued by a client, is identified by its unique identifier , and its query point is assumed to be static; thus, the movement of can be treated as a deletion of the old query followed by an insertion of a new query.
- Central server: The server acts as an intermediary between moving objects and clients, i.e., moving objects and clients do not communicate directly, but indirectly through the server. In addition to the SSP-tree, the server maintains the following basic memory-resident data structures, which are commonly used in the existing methods for the road network [13,14].
- -
- Edge Index (EI): EI is the PMR-quadtree built on the edges in the road network . Each leaf node of EI stores the identifiers of the edges it intersects. Given a query q, EI is used to identify the edge e (i.e., ), where resides. Specifically, EI is traversed down to the leaf node that contains , and e is identified among the edges stored in this leaf node.
- -
- Edge Table (ET): ET is a table hashed on the identifier of each edge e. ET stores for e: (i) its endpoints (i.e., and ); (ii) its length (i.e., = ) and (iii) the sets of edges adjacent to each of its endpoints. ET is used to maintain the connectivity information of the road network G.
- -
- Query Table (QT): QT is a table hashed on the identifier of each query q. QT stores for q: (i) its query point ; (ii) its query distance ; (iii) a set of its query segments; and (iv) its current result. QT is used to maintain the information of the registered queries.
As the intermediary between moving objects and clients in the system, the server performs the following three main tasks.- -
- Query registration: When a new query q is issued (or q is terminated) by a client, the server inserts q into (or deletes q from) QT, updates the SSP-tree (and the additional data structures that will be described in Section 3), and broadcasts messages (e.g., InsertQS, SplitRegion, DeleteQS, and MergeRegion) to all the moving objects to notify them of these changes. Please note that notifying such common information through broadcasting is desirable because the communication overhead is irrelevant to the number of moving objects in a sense that a single message transmission from the server can be received by all the moving objects.
- -
- Region assignment: When a RequestVR message is arrived from the moving object o that leaves its current vicinity region, the server searches a new vicinity region by traversing the SSP-tree, after which it sends an AssignVR message to o for the purpose of assigning this new vicinity region (together with new query segments) to o.
- -
- Query result update: When an UpdateResult message is arrived from a moving object o that may affect the result of a query q, the server checks whether the current result of q is affected by o. If so, the server updates the result of q. For example, in response to the UpdateResult message sent by the moving object in Figure 3, the server updates the result of (i.e., the server removes from the result of ).
3. The Proposed Method
3.1. Query Segment Computation
- If ∈ , = 0. This immediately contradicts the assumption because cannot be less than 0.
- If ∉ , = . Let us consider the subcase, where = . Then, when we simplify the Equation (3) to obtain: = + + , = + . This leads to a contradiction to the assumption because ≤ + . The subcase, where = , leads to the same contradiction as the former subcase.
| Algorithm 1 ComputeSeg(, ) |
| Input : query point of q, : query distance of q |
| Output : a set of query segments q |
| 1: initialize an empty min-heap H; |
| 2: let e be the edge containing ; |
| 3: enheap the endpoints (vertices) of e into H with keys equal to their network distance from ; |
| 4: repeat |
| 5: deheap the top entry from H; |
| 6: mark as visited; |
| 7: for each adjacent vertex of do |
| 8: if has not been visited and then |
| 9: set to ; // |
| 10: enheap into H with a key ; |
| 11: else if has been visited then |
| 12: compute ; |
| 13: if then |
| 14: compute the query segment of q; |
| 15: insert into ; |
| 16: until (H is empty) |
| 17: return ; |
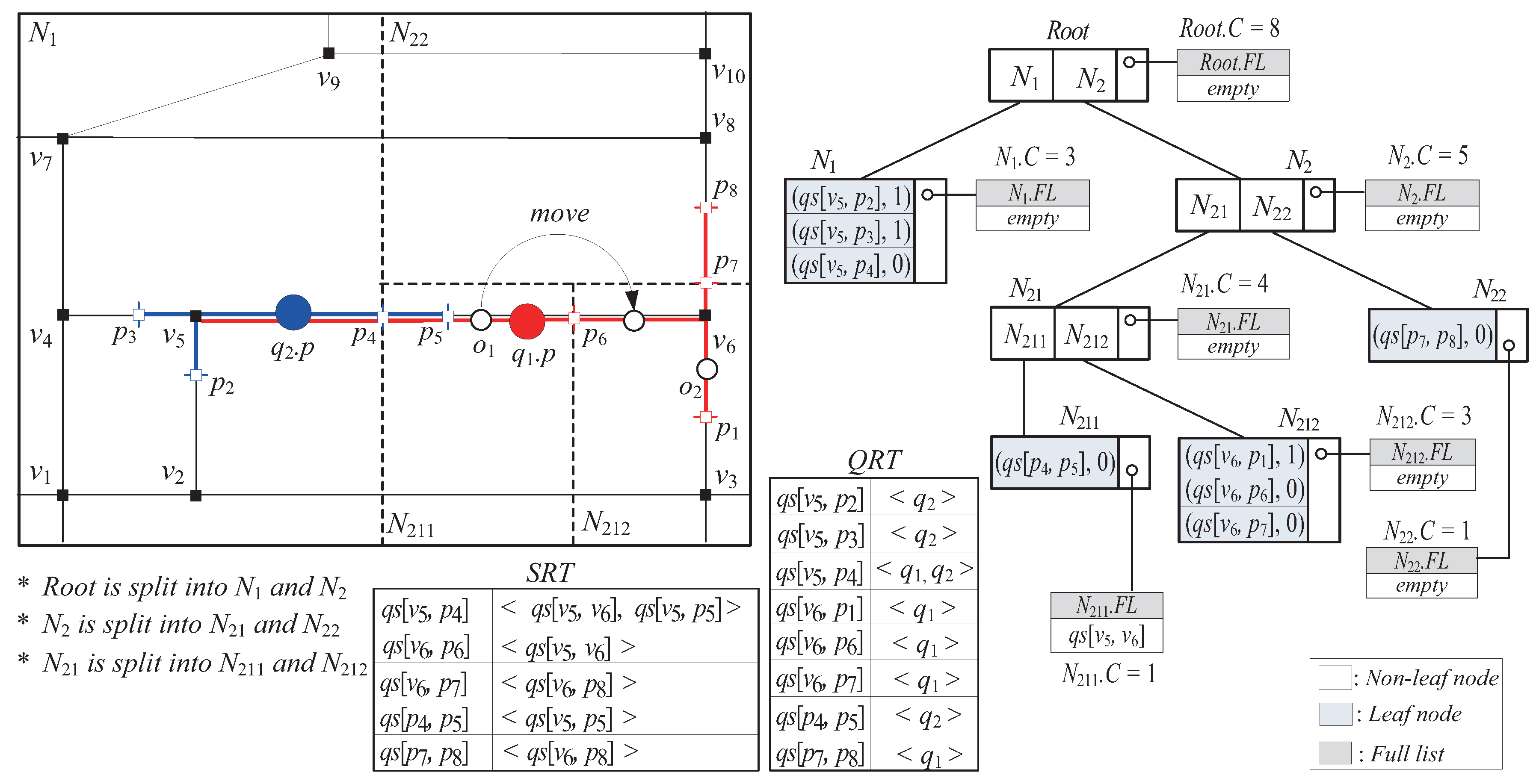
3.2. The Segment-Based Space Partitioning Tree (SSP-Tree)
3.2.1. Description
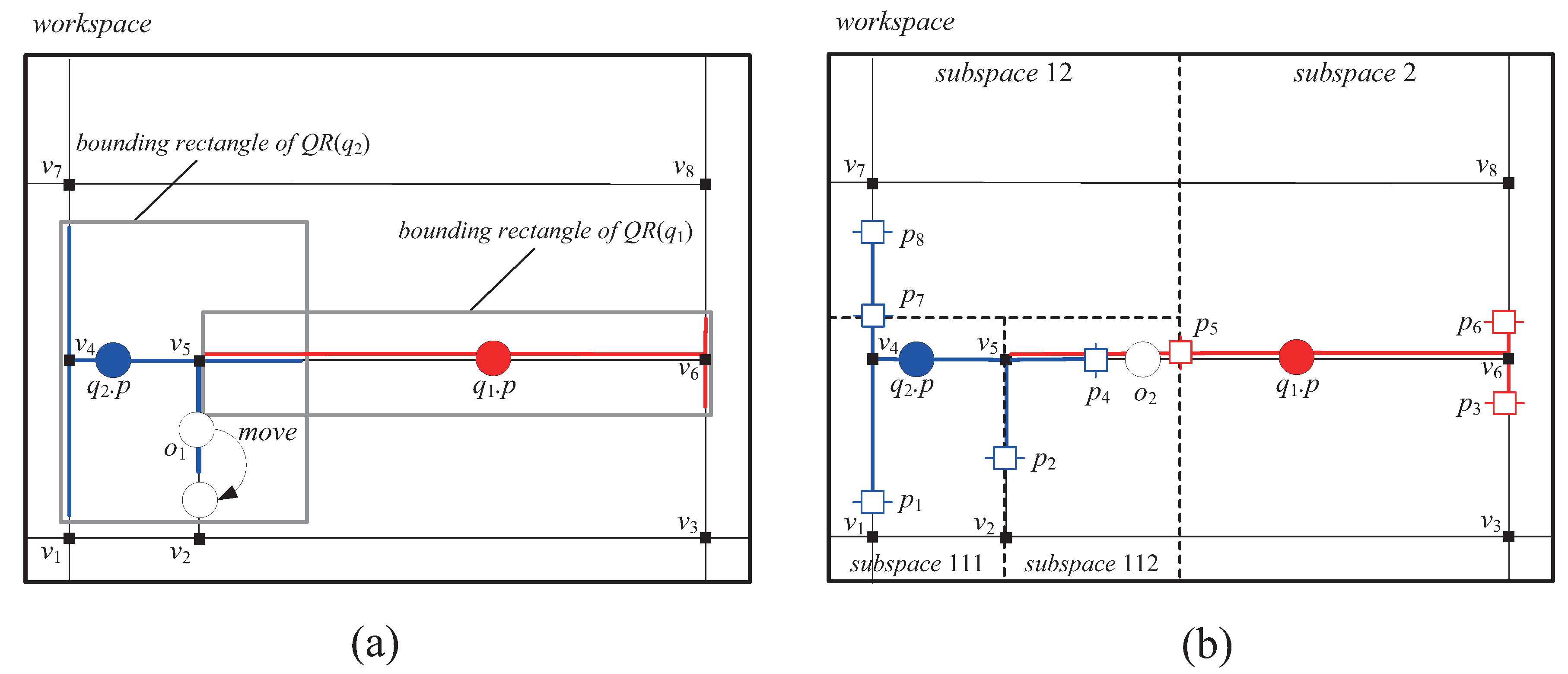
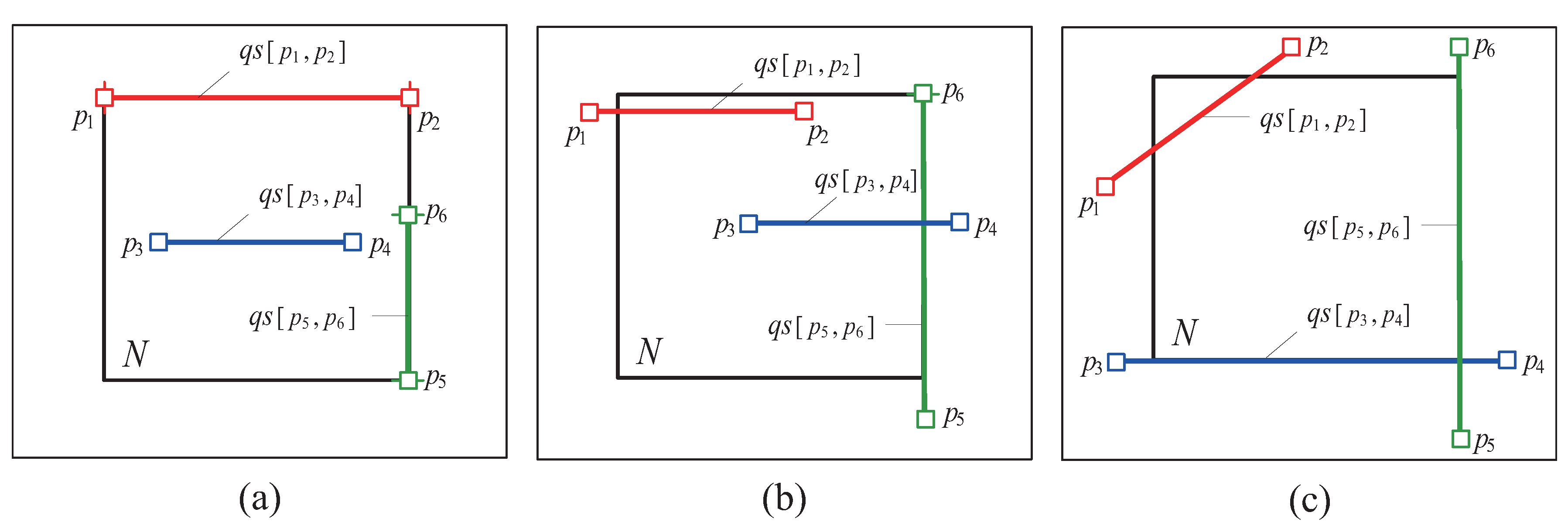
- A tuple is stored in a leaf node N if is inside N.
- A tuple can be redundantly stored in two leaf nodes if lies along the splitting line that separates these two leaf nodes (i.e., if ).
- For each entry stored in a non-leaf node N, represents one of the equal halves of N’s subspace.
- Each (leaf and non-leaf) node N maintains (i) a variable, called the count variable (denoted by ), which records the total number of query segments inside N, and (ii) a list, called the full list (denoted by ), which stores the original query segments that fully intersects N.
3.2.2. Vicinity Region Search
| Algorithm 2 Search(N, o) |
| Input N: a SSP-tree node initially set to the root, o: a moving object |
| Output : o’s vicinity region, : a set of distinct query segments |
| 1: if then |
| 2: find the entry stored in N such that contains ; |
| 3: Search(, o); // Recursion |
| 4: else // if |
| 5: set to N; |
| 6: set to SearchSeg(N); |
| 7: return and ; |
| Function SearchSeg |
| Input N: a SSP-tree node that becomes |
| Output : a set of distinct query segments |
| 1: if N is a non-leaf node then |
| 2: for each entry stored in N do |
| 3: SearchSeg // Recursion |
| 4: else // if N is a leaf node |
| 5: retrieve tuples stored in N and insert the query segments into ; |
| 6: return ; |
3.2.3. SSP-Tree Manipulations
| Algorithm 3 Insert(N, ) |
| Input N: a SSP-tree node initially set to the root, : a query segment of a query q |
| 1: update QT and QRT; |
| 2: if N is a non-leaf node then |
| 3: if fully intersects N then |
| 4: insert into ; |
| 5: for each entry stored in N do |
| 6: if intersects then // if is inside, partially intersects, or fully intersects |
| 7: Insert(, ); |
| 8: else // if N is a leaf node |
| 9: if fully intersects N then |
| 10: insert into ; |
| 11: else // if is inside or partially intersects N |
| 12: if the tuple is not already stored in N then |
| 13: insert a tuple into N and increases by 1; |
| 14: if partially intersects N then |
| 15: update QT, QRT, and SRT; |
| 16: repeat |
| 17: set to N’s parent; |
| 18: increase by 1; |
| 19: until ( is the root) |
| 20: if then |
| 21: SplitNode; |
- If is set, indicating that is the original query segment, SplitNode checks if fully intersects . If so, SplitNode inserts into (lines 10–11). Otherwise, SplitNode inserts a tuple into and increases by 1 only when is not already stored in (lines 12–13). In case that partially intersects , SplitNode additionally updates QT, QRT, and SRT (lines 14–15).
- If is not set, SplitNode checks for each of ’s relevant original query segments if fully intersects . If so, SplitNode inserts into (lines 18–19). Otherwise, similarly to the former case, SplitNode inserts a tuple into and increases by 1 only when is not already stored in (lines 20–21). In case that partially intersects , SplitNode additionally updates QT, QRT, and SRT (lines 22–23).
| Algorithm 4 SplitNode(N) |
| Input N: an overflowed SSP-tree leaf node |
| 1: create two new empty leaf nodes and ; |
| 2: create a new empty non-leaf node ; |
| 3: insert entries and into ; |
| 4: insert all the query segments stored in into , , and ; |
| 5: find the entry stored in N’s parent and redirect to point to ; |
| 6: for each entry stored in do // or |
| 7: for each tuple stored in N do |
| 8: if intersects then // if is inside, partially intersects, or fully intersects |
| 9: if is set then |
| 10: if fully intersects then |
| 11: insert into ; |
| 12: else // if is inside or partially intersects |
| 13: insert a tuple into and increase by 1 if it is not stored in ; |
| 14: if partially intersects then |
| 15: update QT, QRT, and SRT; |
| 16: else // is not set |
| 17: for each ’s relevant original query segment of the tuple (, ) in SRT do |
| 18: if fully intersects then |
| 19: insert into ; |
| 20: else // if is inside or partially intersects |
| 21: insert a tuple into and increase by 1 if it is not stored in ; |
| 22: if partially intersects then |
| 23: update QT, QRT, and SRT; |
| 24: set to ; |
| 25: repeat |
| 26: set to ’s parent; |
| 27: increase by ; |
| 28: until ( is the root) |
| 29: discard N; |
| 30: for each entry stored in do // or |
| 31: SplitNode() if ; |
- If fully intersects N, Delete from (lines 10–11).
- If is inside N (i.e., ), Delete deletes the tuple from N and decreases by 1 if q is the only relevant query of (lines 12–14).
- If partially intersects N, Delete updates QRT and SRT (line 16). Then, it deletes the tuple from N and decrease by 1 if is the only relevant original query segment of (lines 17–18).
| Algorithm 5 Delete(N, ) |
| Input N: a SSP-tree node initially set to the root, : a query segment of a query q |
| 1: update QRT; |
| 2: if N is a non-leaf node then |
| 3: if fully intersects N then |
| 4: delete from ; |
| 5: else // if is inside or partially intersects N |
| 6: for each entry stored in N do |
| 7: if intersects then // if is inside, partially intersects, or fully intersects |
| 8: Delete(, ); |
| 9: else // if N is a leaf node |
| 10: if fully intersects N then |
| 11: delete from ; |
| 12: else if is inside N then // if |
| 13: if q is the only relevant query of (= ) then |
| 14: delete the tuple from N and decrease by 1; |
| 15: else // if partially intersects N |
| 16: update QRT and SRT; |
| 17: if is the only relevant original query segment of then |
| 18: delete the tuple from N and decrease by 1; |
| 19: if the tuple is deleted from N then |
| 20: repeat |
| 21: set to N’s parent; |
| 22: decrease by 1; |
| 23: until ( is the root) |
| 24: MergeNode(N’s parent); |
| Algorithm 6 MergeNode(N) |
| Input N: a non-leaf node of the SSP-tree |
| 1: if and both of N’s children are leaf nodes then |
| 2: create a new empty leaf node ; |
| 3: insert all the original query segments stored in into ; |
| 4: set to ; |
| 5: find the entry stored in N’s parent and redirect to point to ; |
| 6: for each entry stored in N do |
| 7: for each tuple stored in do |
| 8: insert into if it is not stored in ; |
| 9: discard N and N’s children; |
| 10: MergeNode(’s parent); |
3.3. Vicinity Region-based Communications and Query Processing
3.3.1. Server-Side Tasks
- Query registration: When a new query q is issued by a client, the server inserts q into QT and invokes ComputeSeg (see Algorithm 1) to compute the relevant query segments of q. Then, for each query segment generated by ComputeSeg, the server (i) invokes Insert (see Algorithm 3) to insert into the SSP-tree and (ii) broadcasts the InsertQS message. In case that a leaf node of the SSP-tree is split into and , the server broadcasts the SplitRegion message. On the other hand, when an existing query q is terminated by a client, for each relevant query segment of q, the server (i) invokes Delete (see Algorithm 5) to delete from the SSP-tree; (ii) broadcasts the DeleteQS message; and finally (iii) deletes q from QT. In case that two leaf nodes and are merged, the server broadcasts the MergeRegion message, where is the combined set of query segments inside and .
- Region assignment: When the server receives the RequestVR message from a moving object o, where , , and denote the point of o’s current location, o’s capability, and o’s previous vicinity region, respectively, it first checks if o leaves each original query segment stored in . If so, the server updates the result of the corresponding query when necessary. Then, the server invokes Search (see Algorithm 2), after which it sends the AssignVR message to o, where is o’s new vicinity region and is a set of query segments inside .
- Query Result Update: When the server receives the UpdateResult message from a moving object o, it visits QRT to find the relevant queries of . Then, the server checks each ’s relevant query q if . If so, the server inserts o into the result of q (if it is not already there). On the other hand, if , the server removes o from the result of q (if it is there).
3.3.2. Object-Side Tasks
- InsertQS: When o listens to the InsertQS message, it first checks if is inside . If so, o sends UpdateResult message to the server to let the server insert o into the results of ’s relevant queries. Then, o checks if is inside or partially intersects its vicinity region N. If so, o inserts into . In case that the cardinality of is greater than , i.e., , o sends the RequestVR to the server.
- SplitRegion: When o listens to the SplitRegion message, it first checks if its vicinity region N equals . If this is the case, if is inside , o sets as its new vicinity region ; otherwise, it sets as . Then, for each query segment () that intersects , o replaces it with .
- DeleteQS: When o listens to the DeleteQS message, it just deletes from if is inside its vicinity region N.
- MergeRegion: When o listens to the MergeRegion message, it first checks if its vicinity region N equals or . If so, o sets as its new vicinity region and replaces with .
4. Performance Evaluation
4.1. Simulation Setup
4.2. Simulation Results
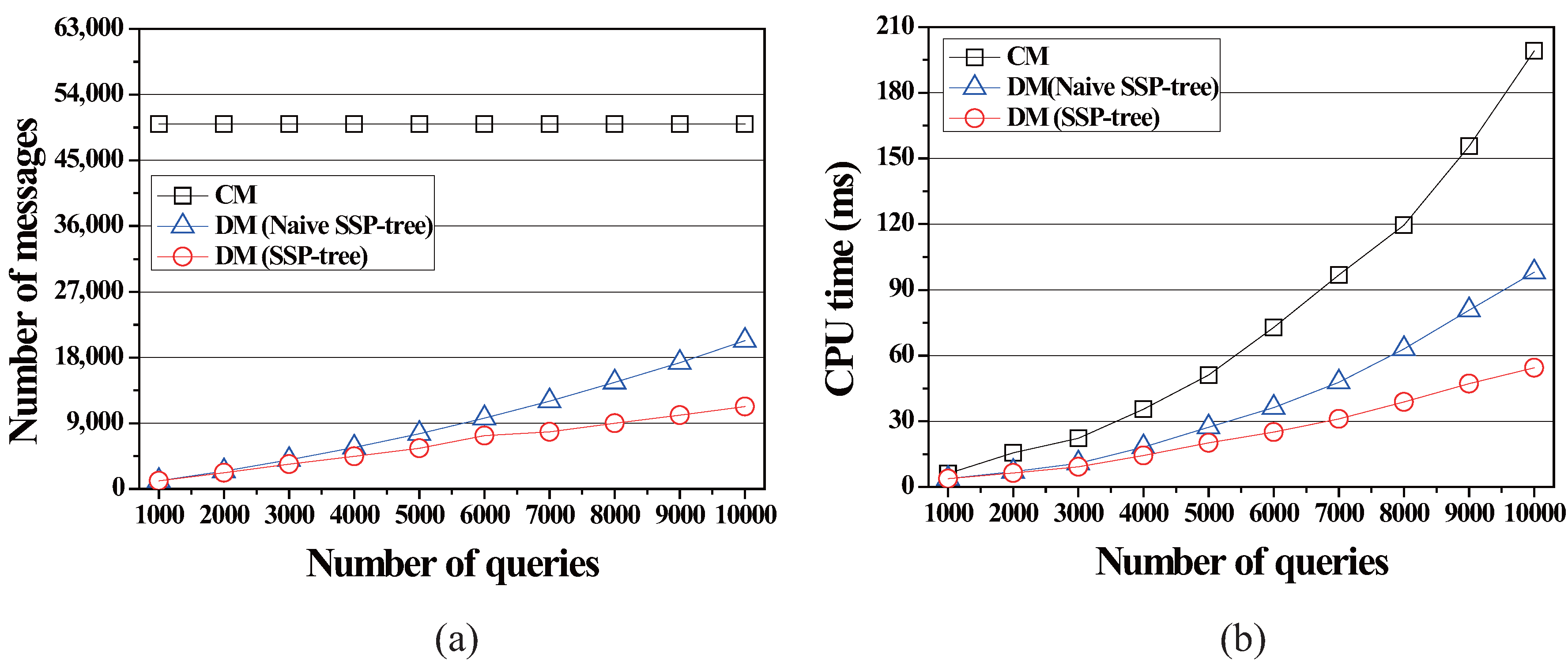
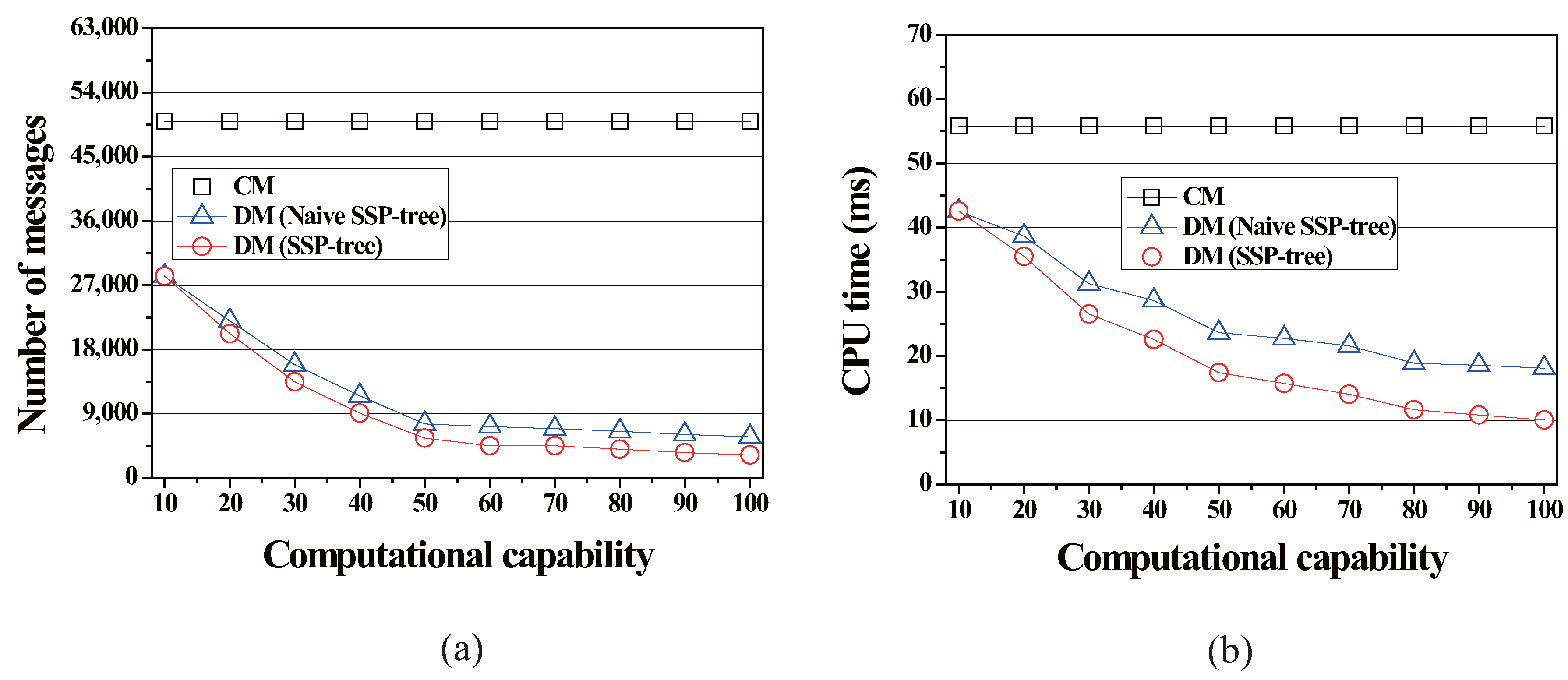
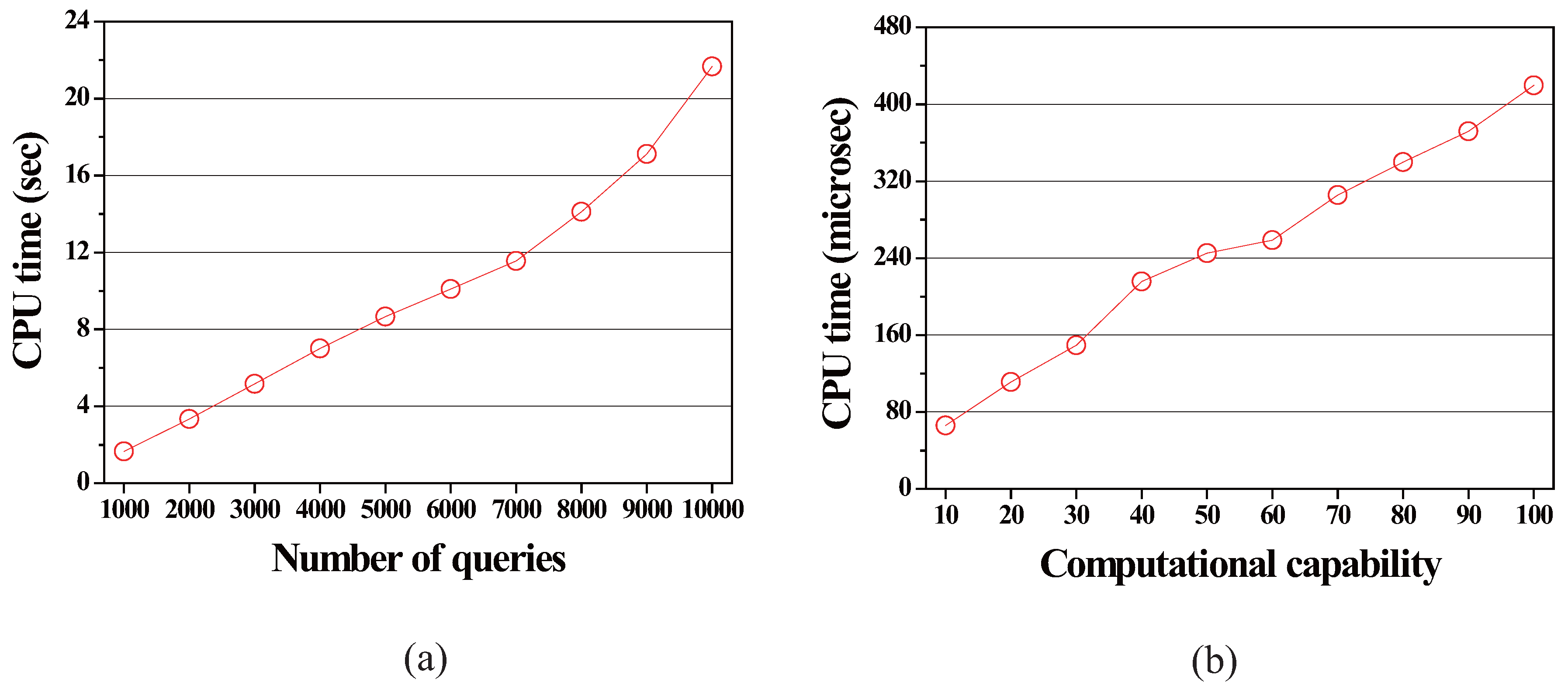
4.2.1. Effect of the Number of Queries
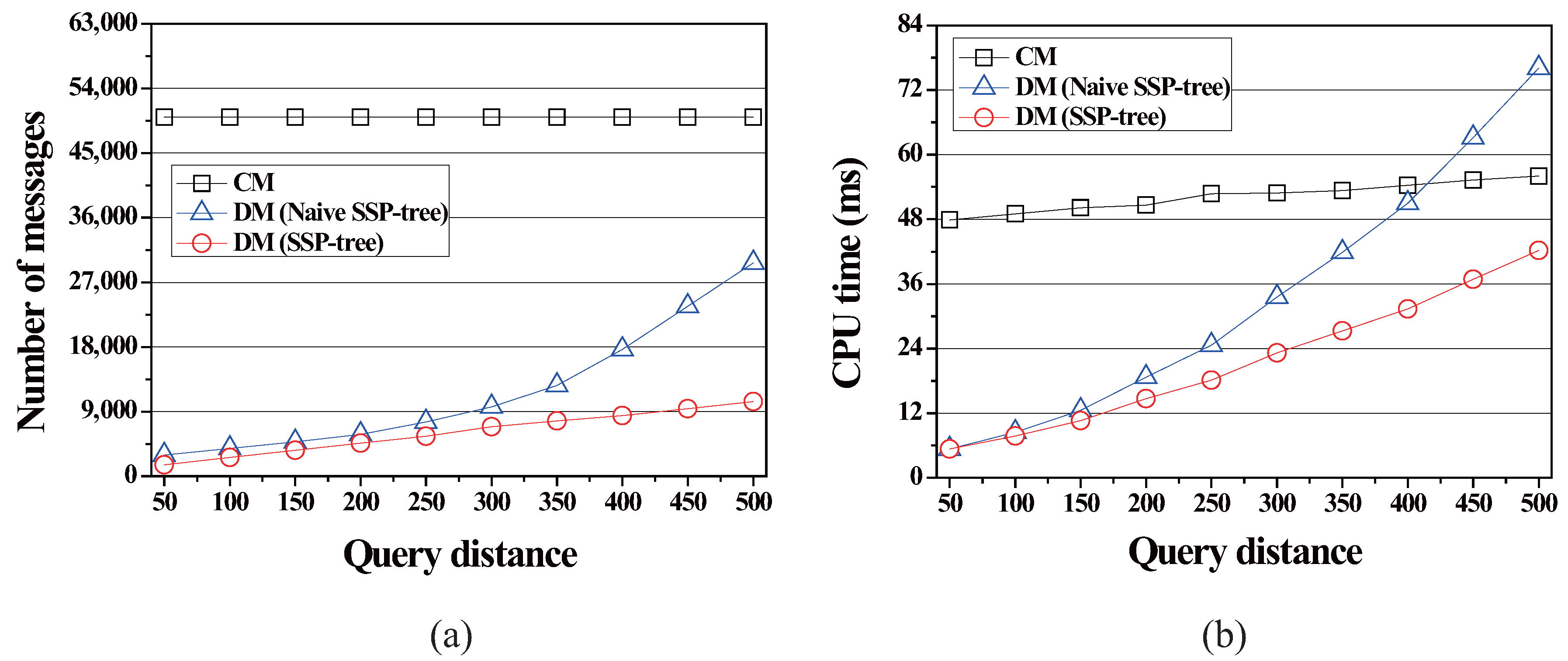
4.2.2. Effect of the Query Distance
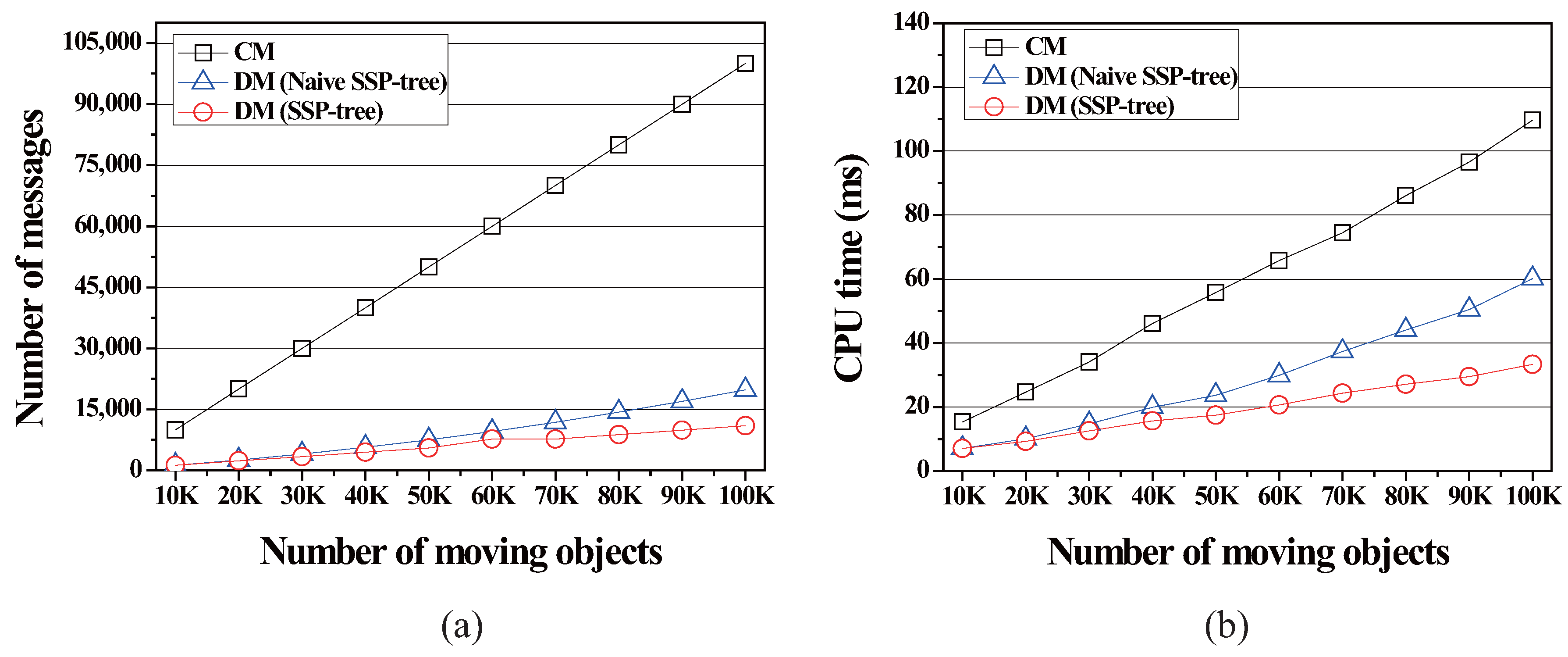
4.2.3. Effect of the Number of Moving Objects
4.2.4. Effect of the Minimum Computational Capability
5. Discussion
6. Related Work
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Ilarri, S.; Mena, E.; Illarramendi, A. Location-dependent query processing: Where we are and where we are heading. ACM Comput. Surv. 2010, 42, 1–73. [Google Scholar] [CrossRef]
- Cai, Y.; Hua, K.A.; Cao, G.; Xu, T. Real-time processing of range-monitoring queries in heterogeneous mobile databases. IEEE Trans. Mob. Comput. 2006, 5, 931–942. [Google Scholar]
- Jung, H.; Kim, Y.S.; Chung, Y.D. QR-tree: An efficient and scalable method for evaluation of continuous range queries. Inf. Sci. 2014, 274, 156–176. [Google Scholar] [CrossRef]
- Hu, H.; Xu, J.; Lee, D.L. A generic framework for monitoring continuous spatial queries over moving objects. In Proceedings of the 2005 ACM SIGMOD International Conference on Management of Data, Baltimore, MD, USA, 13–16 June 2005. [Google Scholar]
- Prabhakar, S.; Xia, Y.; Aref, W.G.; Hambrusch, S. Query indexing and velocity constrained indexing: Scalable techniques for continuous queries on moving objects. IEEE Trans. Comput. 2002, 51, 1124–1140. [Google Scholar] [CrossRef]
- Kalashnkov, D.V.; Prabhakar, S.; Hambrusch, S.E. Main memory evaluation of monitoring queries over moving objects. Disrtib. Parallel Database 2004, 15, 117–135. [Google Scholar] [CrossRef]
- Wang, H.; Roger, Z. Processing of continuous location-based range queries on moving objects in road networks. IEEE Trans. Knowl. Data Eng. 2011, 23, 1065–1078. [Google Scholar] [CrossRef]
- Cheema, M.A.; Brankovic, L.; Lin, X.; Zhang, W.; Wang, W. Continuous monitoring of distance-based range queries. IEEE Trans. Knowl. Data Eng. 2011, 23, 1182–1199. [Google Scholar] [CrossRef]
- Al-Khalidi, H.; Taniar, D.; Betts, J.; Alamri, S. Monitoring moving queries inside a safe region. Sci. World J. 2014, 2014. [Google Scholar] [CrossRef] [PubMed]
- Yung, D.; Man, L.Y.; Lo, E. A safe-exit approach for efficient network-based moving range queries. Data Knowl. Eng. 2012, 72, 126–147. [Google Scholar] [CrossRef]
- Cho, H.J.; Kwon, S.J.; Chung, T.S. A safe exit algorithm for continuous nearest neighbor monitoring in road networks. Mob. Inf. Syst. 2013, 9, 37–53. [Google Scholar] [CrossRef]
- Cho, H.J.; Ryu, K.; Chung, T.S. An efficient algorithm for computing safe exit points of moving range queries in directed road networks. Inf. Syst. 2014, 41, 1–19. [Google Scholar] [CrossRef]
- Mouratidis, K.; Yiu, M.L.; Papadias, D.; Mamoulis, N. Continuous nearest neighbor monitoring in road networks. In Proceedings of the 32nd international conference on Very large data bases, Seoul, Korea, 43–54 September 2006. [Google Scholar]
- Liu, F.; Hua, K.A. Moving query monitoring in spatial network environments. Mob. Netw. Appl. 2012, 17, 234–254. [Google Scholar] [CrossRef]
- Brinkhoff, T. A framework for generating network-based moving objects. GeoInformatica 2002, 6, 153–180. [Google Scholar] [CrossRef]
- Broch, J.; Maltz, D.A.; Johnson, D.; Hu, Y.-C.; Jetcheva, J. A performance comparison of multi-hop wireless ad hoc network routing protocols. In Proceedings of the 4th Annual ACM/IEEE International Conference on Mobile Computing and Networking, Dallas, TX, USA, 25–30 October 1998. [Google Scholar]
- Guttman, A. R-trees: A dynamic index structure for spatial searching. In Proceedings of the 1984 ACM SIGMOD International Conference on Management of Data, Boston, MA, USA, 18–21 June 1984. [Google Scholar]
- Beckmann, N.; Kriegel, H.-P.; Schneider, R.; Seeger, B. The R*-tree: An efficient and robust access method for points and rectangles. In Proceedings of the 1990 ACM SIGMOD International Conference on Management of Data, Atlantic City, NJ, USA, 23–25 May 1990. [Google Scholar]
- Roussopoulos, N.; Faloutsos, C. The R+-tree: A dynamic index for multi-dimensional objects. In Proceedings of the 13th International Conference on Very Large Data Bases, San Francisco, CA, USA, 1–4 September 1987. [Google Scholar]
- Papadias, D.; Zhang, J.; Mamoulis, N.; Tao, Y. Query processing in spatial network databases. In Proceedings of the 29th international conference on Very large data bases, Berlin, Germany, 9–12 September 2003. [Google Scholar]
- Zhong, R.; Li, G.; Tan, K.L.; Zhou, L.; Gong, Z. G-tree: An efficient and scalable index for spatial search on road networks. IEEE Trans. Knowl. Data Eng. 2015, 27, 2175–2189. [Google Scholar] [CrossRef]
- Sun, W.; Chen, C.; Zheng, B.; Chen, C.; Liu, P. An air index for spatial query processing in road networks. IEEE Trans. Knowl. Data Eng. 2015, 27, 382–395. [Google Scholar] [CrossRef]
- Saltenis, S.; Jensen, C.; Leutenegger, S.; Lopez, M.A. Indexing the positions of continuously moving objects. In Proceedings of the 2000 ACM SIGMOD International Conference on Management of Data, Dallas, TX, USA, 16–18 May 2000. [Google Scholar]
- Tao, Y.; Papadias, D.; Sun, J. The TPR*-tree: An optimized spatio-temporal access method for predictive queries. In Proceedings of the 29th International Conference on Very Large Data, Berlin, Germany, 9–12 September 2003. [Google Scholar]
- Lee, M.L.; Hsu, W.; Jensen, C.S.; Cui, B.; Teo, K.L. Supporting frequent updates in R-trees: A bottom-up approach. In Proceedings of the 29th International Conference on Very Large Data Bases, Berlin, Germany, 9–12 September 2003. [Google Scholar]
- Wang, H.; Zimmermann, R. A novel dual-index design to efficiently support snapshot location-based query processing in mobile environments. IEEE Trans. Mob. Comput. 2010, 9, 1280–1292. [Google Scholar] [CrossRef]

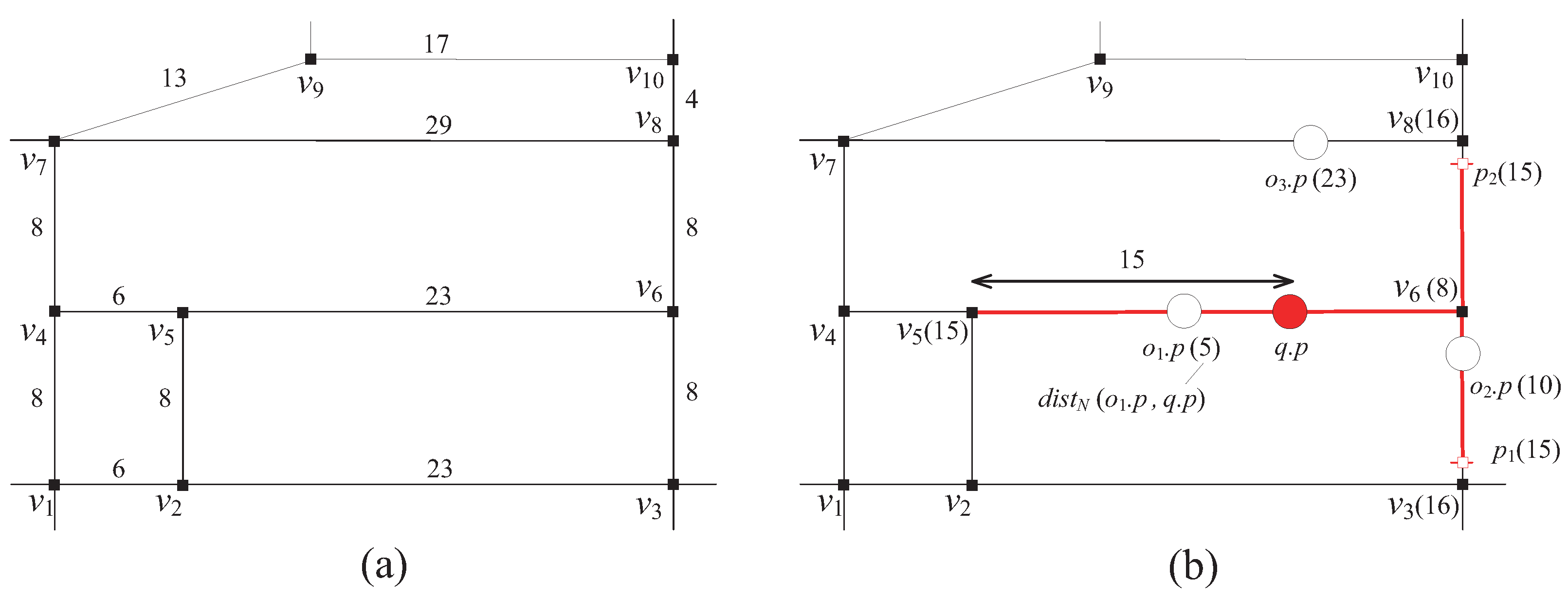
| Notation | Explanation |
|---|---|
| A graph model of the road network (V: a set of vertices, E: a set of edges) | |
| A vertex in G | |
| or e | An edge in G |
| o | A moving object |
| The point of o’s current location | |
| o’s computational capability | |
| A range monitoring query (: query point, : query distance) | |
| The query range of q | |
| or (of q) | A query segment (of q) |
| The Euclidean distance between any two points in G | |
| The network distance between any two points in G | |
| N | A SSP-tree node or its corresponding subspace |
| The count variable maintained in N | |
| The full list maintained in N | |
| Query relevance table | |
| Segment relevance table |
| Simulation Parameter | Value Used (Default) |
|---|---|
| Number of queries | 1000∼10,000 (5000) |
| Query distance | 50∼500 (250) |
| Number of moving objects | 10,000∼100,000 (50,000) |
| Minimum computational capability | 10∼100 (50) |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jung, H.; Kim, U.-M. The SSP-Tree: A Method for Distributed Processing of Range Monitoring Queries in Road Networks. ISPRS Int. J. Geo-Inf. 2017, 6, 322. https://doi.org/10.3390/ijgi6110322
Jung H, Kim U-M. The SSP-Tree: A Method for Distributed Processing of Range Monitoring Queries in Road Networks. ISPRS International Journal of Geo-Information. 2017; 6(11):322. https://doi.org/10.3390/ijgi6110322
Chicago/Turabian StyleJung, HaRim, and Ung-Mo Kim. 2017. "The SSP-Tree: A Method for Distributed Processing of Range Monitoring Queries in Road Networks" ISPRS International Journal of Geo-Information 6, no. 11: 322. https://doi.org/10.3390/ijgi6110322





