Revocable-Attribute-Based Encryption with En-DKER from Lattices
Abstract
:1. Introduction
1.1. Related Work
1.2. Technical Overview
1.3. Our Contributions
2. Preliminaries
2.1. Notations
2.2. Useful Facts
- Smudging. The given lemma, originally established in [34], asserts that adding large noise often “smudges out” any small values.
- Leftover Hash Lemma. Here, we recall the leftover hash lemma from [21].
- Full-Rank Different Map. We need this tool to encode identities and time periods as matrices in .
2.3. Background on Lattices
- Lattice. Let n, m, and q be positive integers. An m-dimensional lattice, denoted as , is a discrete subgroup within . Consider , the q-ary lattice defined as {: in , where is a matrix in . For any in , let denote the coset {: in .
- Discrete Gaussians. For any parameter , the discrete Gaussian distribution is defined , where and .
- The following lemmas represent crucial properties of the discrete Gaussian distribution [35].
- Trapdoor Generators. The ensuing lemma outlines properties of algorithms designed for generating short bases of lattices.
- : On inputting n, m, q, output a matrix and its trapdoor , satisfying .
- There exists a gadget matrix , which is a full-rank matrix in and has a publicly known trapdoor with .
- : Given a matrix with trapdoor , a vector , and a parameter , output a vector satisfying and .
- : Given a matrix with trapdoor , a matrix , a vector , and a parameter , output a vector distributed statistically close to .
- : Given a matrix , the gadget matrix with trapdoor , a uniform random matrix , a vector , and a parameter , output a vector distributed statistically close to .
- Hardness Assumption. The security of our revocable ABE scheme is reduced to the learning with errors (LWE) assumption.
- : Given a Boolean circuit f and ℓ matrices , output the matrix .
- : For a Boolean circuit f, ℓ matrices , an attribute set , and ℓ vectors , output . Here, , where , and with almost negligible probability.
- : Given a Boolean circuit f, ℓ matrices , a matrix , and an attribute set , output . Ensure , where . If , then with almost negligible probability.
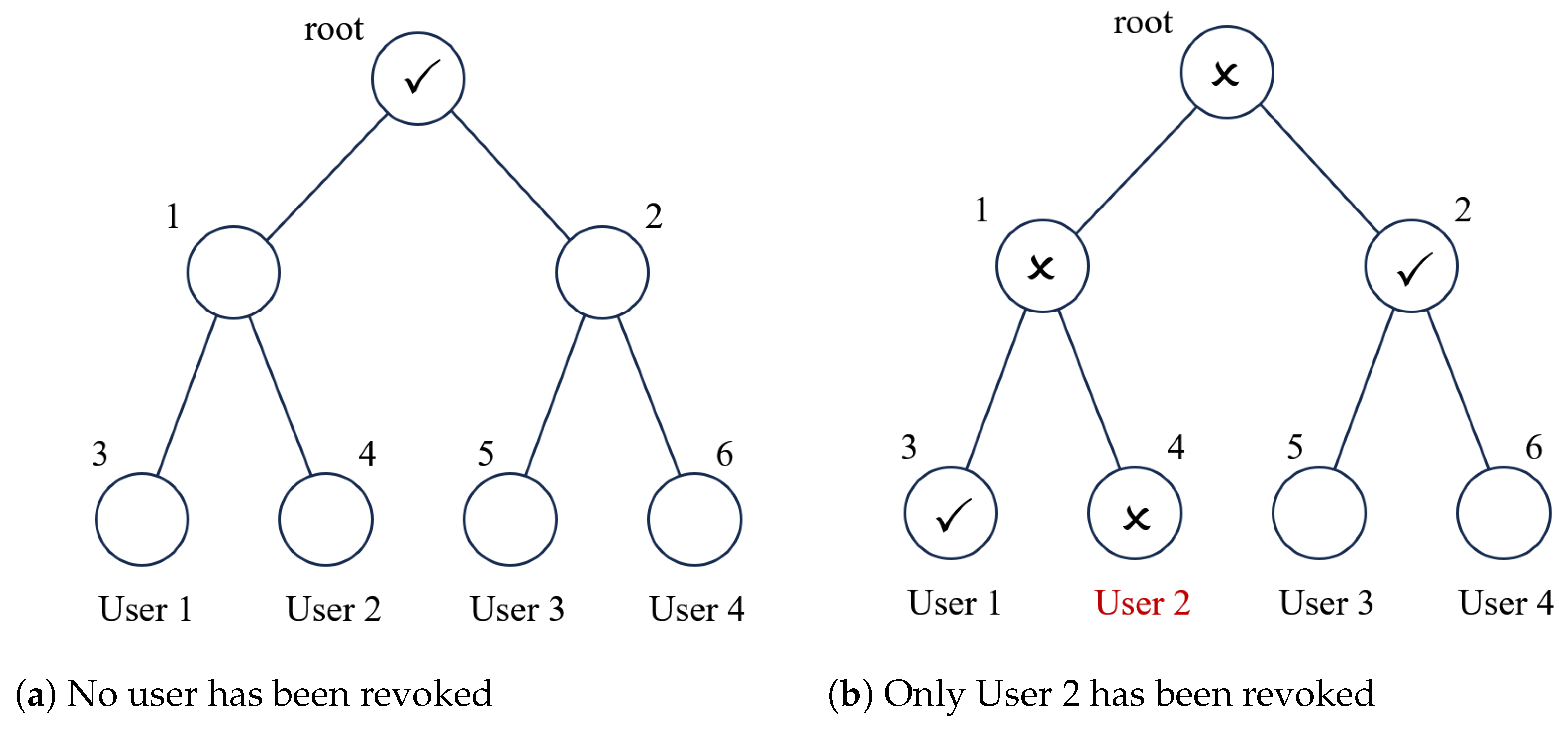
2.4. The Complete Subtree Method
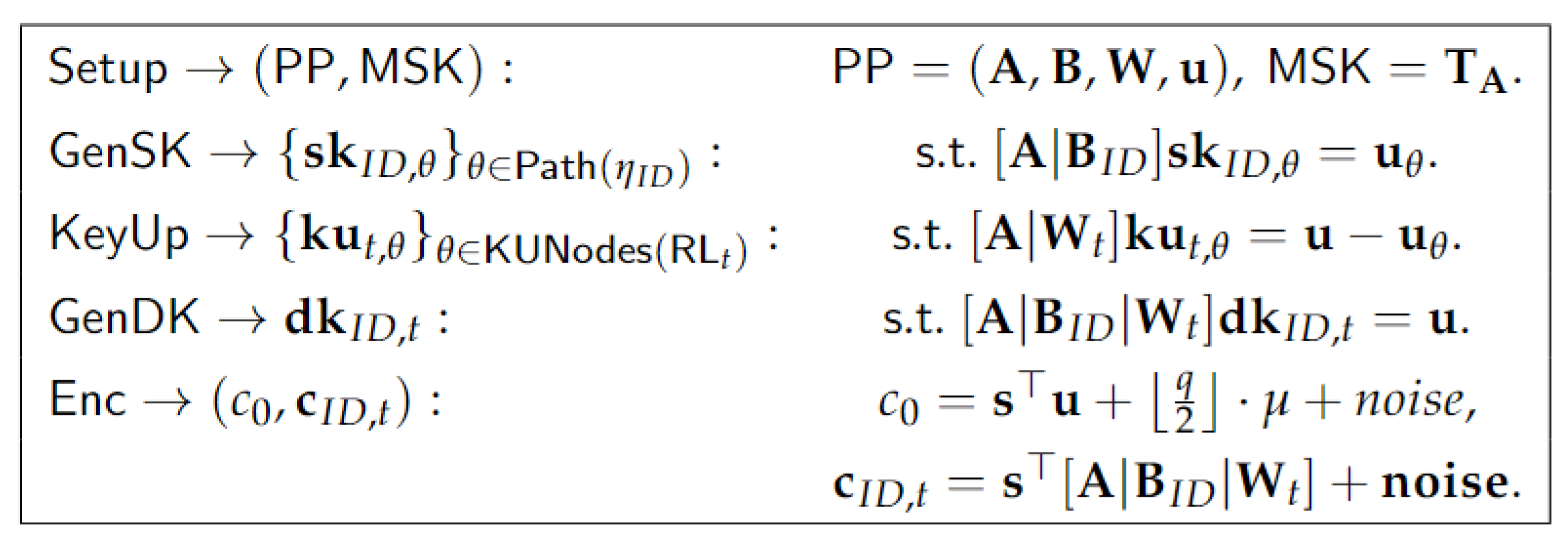
3. The Notion of Revocable ABE with En-DKER
3.1. Syntax and Correctness
- : Executed by the KGC, this algorithm takes as input a security parameter . It produces public parameters and a master secret key .
- : Executed by the KGC, this algorithm takes as input the public parameters , the master secret key , an identity , and a policy function . It produces a secret key .
- : Executed by the KGC, this algorithm takes as input the binary tree , a time period , and the revocation list for the time period t. It produces and broadcasts a node set .
- : Executed by the receiver, this algorithm takes as input the public parameters , the secret key , and the node set . It produces a decryption key .
- : Executed by the sender, this algorithm takes as input the public parameters , an attribute set , the node set , and a message . It produces a ciphertext .
- : Executed by the receiver, this algorithm takes as input the ciphertext and the decryption key . It produces a message .
- Correctness. A revocable ABE scheme is correct if, for all , , , , , and that satisfy , it holds that
3.2. Security Model of Revocable ABE with En-DKER
- Initialize: establishes a binary tree . sets the challenge attribute sets and , the challenge time period , and the challenge node set .
- Setup Phase: executes the algorithm, providing the public parameters to .
- Query Phase: adaptively makes the following queries to :
- sets for user registration queries. randomly selects an unassigned leaf node for . (At the conclusion of the query, acquires based on and ).
- sets for the secret key queries; replies with the corresponding secret key . This is subject to the constraint ; if or , .
- Let , and loop through the following steps:
- (a)
- sets for the decryption key queries; replies with the decryption key . This is subject to the constraint ; ; if , and .
- (b)
- sets for revocation queries, adds to the revocation list and updates . Then, sent to . This is subject to the constraint ; .
- (c)
- .
- Challenge Phase: sets challenge plaintexts and . randomly chooses a bit and replies with the ciphertext .
- Guess: outputs a guess of b and succeeds if . The advantage of is defined as
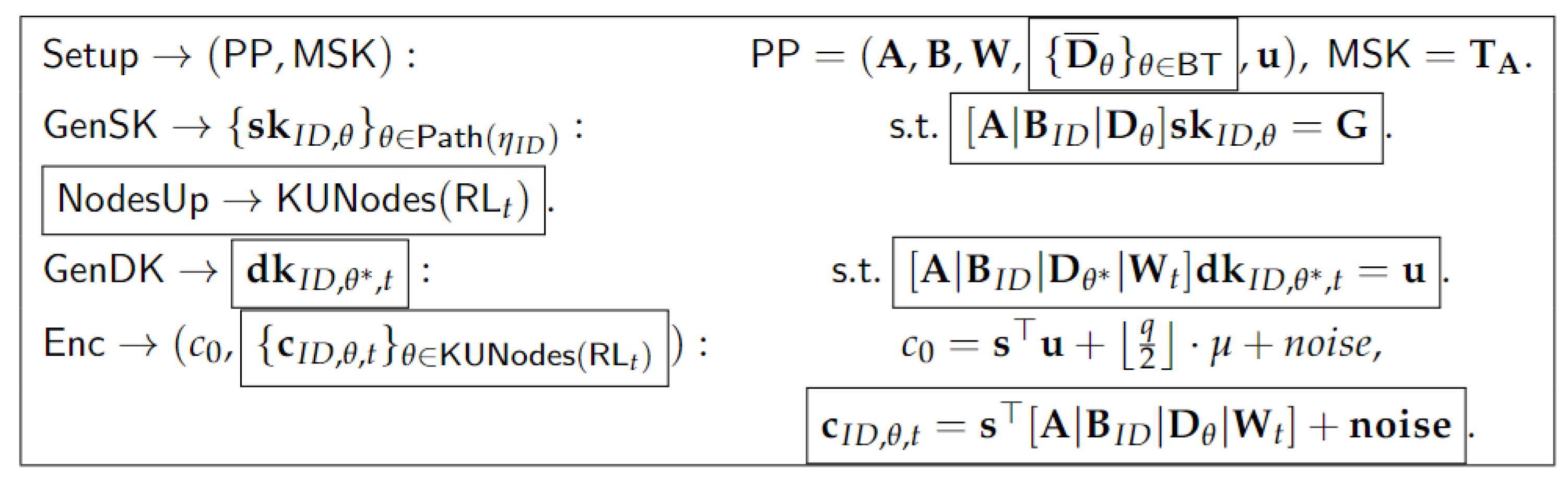
4. Revocable ABE with En-DKER from Lattices
4.1. Our Construction
- For sampling: and .
- For correctness: , .
- For security: , , where .
- For smudging: , where .
- : On inputting a security parameter , the detailed process is as follows:
- Run the algorithm to generate , where .
- Choose random matrices in , and a random matrix in .
- Build a binary tree with at least N leaf nodes. For each node , select a random matrix in .
- Output , .
- : On inputting the public parameters , the master secret key , an identity , and a policy function , the detailed process is as follows:
- If belongs to a newly registered user in the system, then randomly pick an unassigned leaf node from and store in it.
- Compute .
- For each , generate , satisfying .
- (a)
- Choose a random matrix in and set .
- (b)
- Sample .
- (c)
- Divide and into two parts, , and , with m rows per part. Then, generate
- Output .
- : On inputting the binary tree , a time period , and the revocation list for the time period t, the KGC generates and broadcasts a set for the time period t.
- : On inputting the public parameters , the secret key , and the node set , the detailed process is as follows:
- Set . If , outputs ⊥. Otherwise, continue the following steps.
- Compute .
- Generate , satisfying .
- (a)
- Choose a random matrix . Set and send to the server.
- (b)
- The server samples and sends to the user.
- (c)
- Compute , satisfying , where .
- (d)
- Divide into four parts: , , , , and into three parts: , , , with m rows per part. Then, generate
- Output .
- : On inputting the public parameters , an attribute set , the node set , and a message , the detailed process is as follows:
- Choose a random vector in .
- Choose random matrices , , and in , where , .
- Choose noise and a noise vector .
- Generate , where
- Output .
- : On inputting the ciphertext and the decryption key , the detailed process is as follows:
- If , outputs ⊥. Otherwise, continue the following steps.
- Compute .
- Compute .
- Output by computing .
- Correctness. We analyze the correctness of the scheme.
- When , the probability of the last coordinates being 0 is , which is negligible in . Consequently, the decryption algorithm outputs ⊥ with all but negligible probability.
- When , according to the correctness of the algorithm, we have . Therefore,
- From Lemma 2, we have and .
- From Lemma 7, we have .
- Because and , we have and .
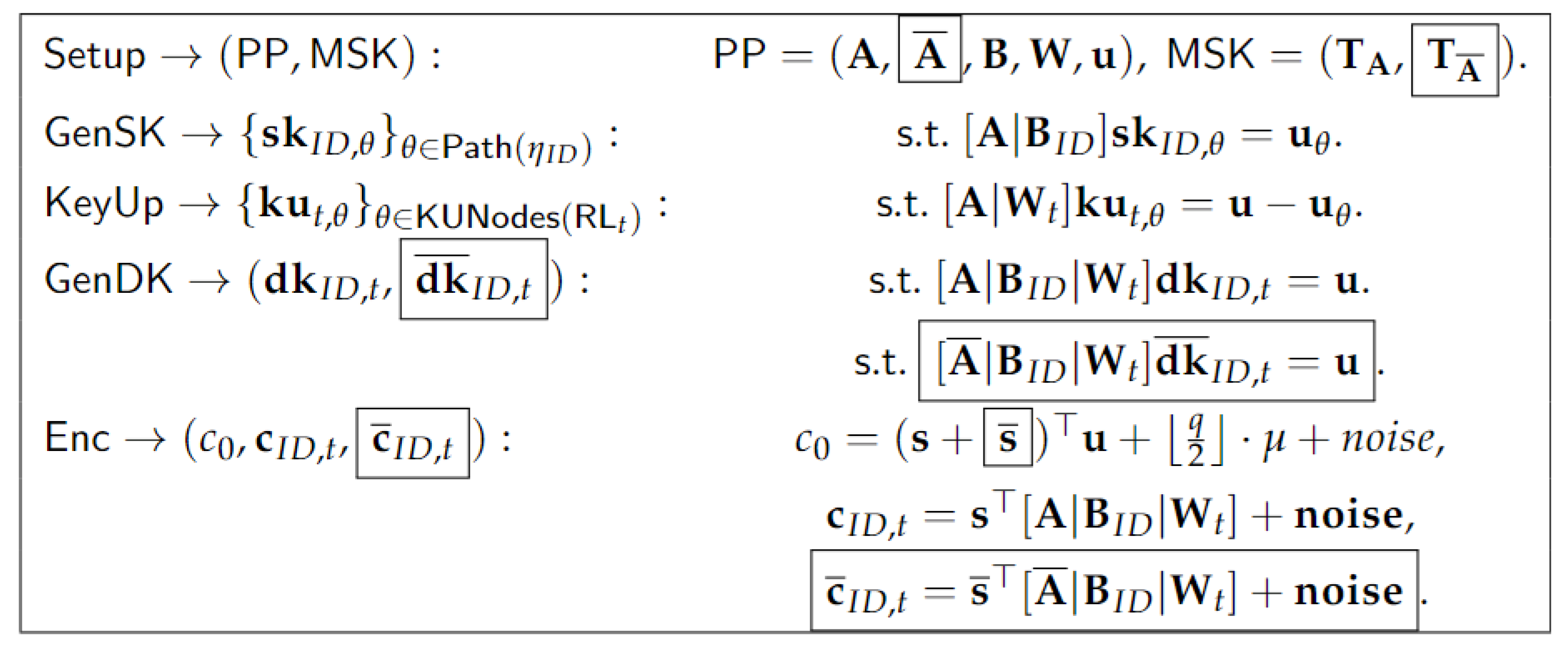
4.2. Security Proof
- The Series of Games. Let be the adversary in the security definition of the RABE with En-DKER and adhere to the security model defined in Section 3.2. We consider the following series of games.
- : This is the original - secure game for our RABE scheme, and chooses a random bit .
- : In this game, we change the generation way of matrices , , and .
- Choose random matrices , , and in , where and .
- For each , , we set , ,
- : In this game, we change the generation way of the secret key for secret key query of , mainly divided into the following three cases:
- Case 1: . In this case, the user must have been revoked before the challenge time period , i.e., , as per the secret key query restriction in the security model. So, for each , .
- Perform operation 3.(a) in algorithm .
- Sample .
- Case 2: and . In this case, , where . So, the challenger cannot use and algorithm to sample . Furthermore, can only be randomly selected once, so we need to use the algorithm to sample .
- Sample and set .
- For other nodes and , the challenger computes .
- Compute and obtain a low-norm matrix such that . By the definition, we have . Moreover, as needed for algorithm .
- Sample .
- Case 3: and . In this case, , and , for each .
- Perform the operation 3.(a) in algorithm .
- Sample .
- : In this game, we change the generation way of the decryption key for decryption key query of , when , and .
- Sample .
- Perform the operation 2.(a) and 2.(b) in algorithm to generate and .
- Compute , satisfying .
- Divide into two parts: and , with m rows per part. Set
- : In this game, we change the generation way of the matrix and the ciphertexts.
- Choose a random matrix in .
- Choose and , where and .
- LWE Instance: begins by obtaining an challenger of two random matrices , and two vectors , , where and are either random or and for some random vector and , .
- Public Parameters: sets the challenge attributes and , time period , and node set . Then, sets the public parameters as in : Uniformly random matrices , , and in , , ,where and .
- Query Phase: answers ’s user registration, secret key, decryption key, and revocation queries as in .
- Challenge Phase: sets two messages , . computes , , , and , , where and .
- Guess: outputs a guess of b. Then, outputs ’s guess as the answer to the challenge it is trying to solve.
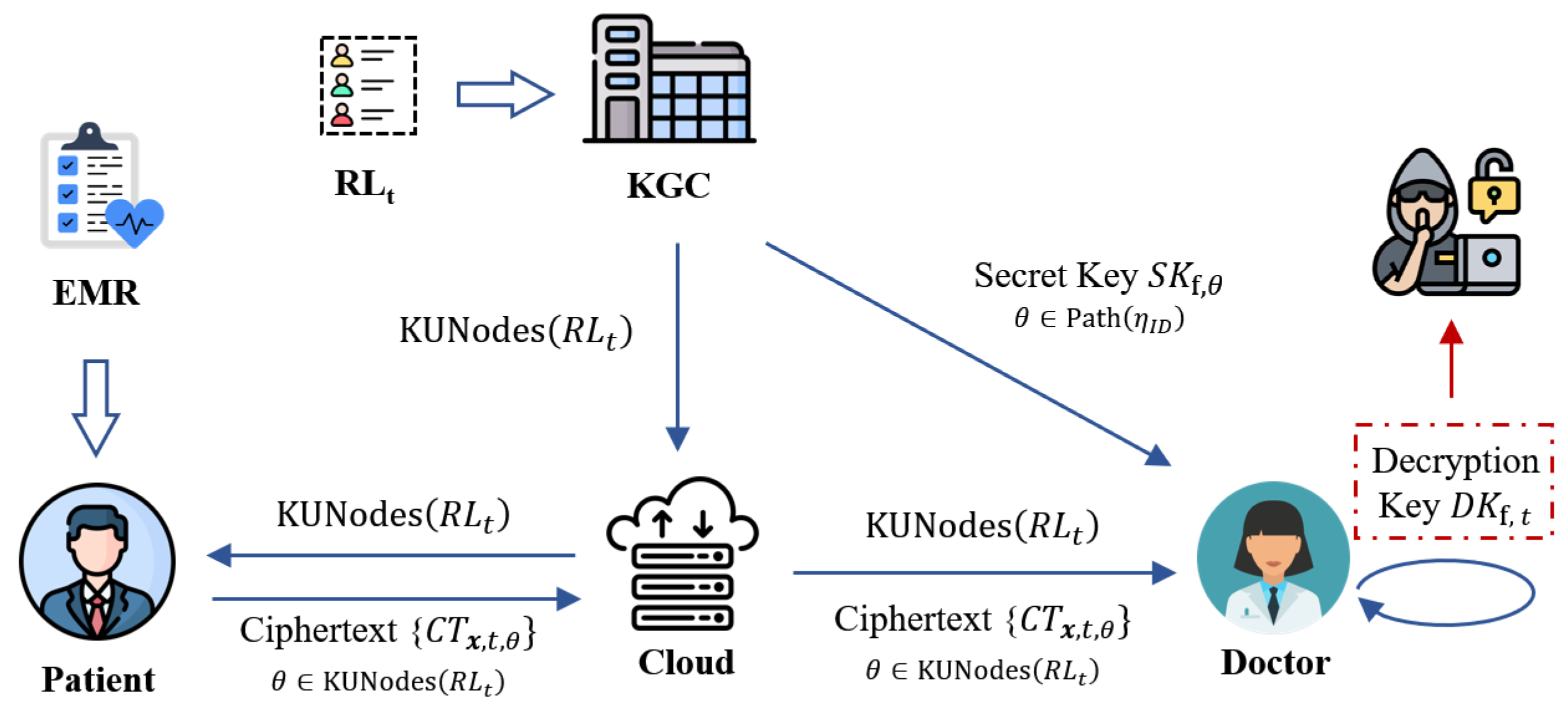
5. Application in Practice
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Proceedings of the Advances in Cryptology–EUROCRYPT 2005: 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Proceedings 24. Springer: Berlin/Heidelberg, Germany, 2005; pp. 457–473. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Oakland, CA, USA, 20–23 May 2007; IEEE: Piscataway Township, NJ, USA, 2007; pp. 321–334. [Google Scholar]
- Waters, B. Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization. In Proceedings of the International Workshop on Public Key Cryptography, Taormina, Italy, 6–9 March 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 53–70. [Google Scholar]
- Attrapadung, N.; Libert, B.; De Panafieu, E. Expressive key-policy attribute-based encryption with constant-size ciphertexts. In Proceedings of the Public Key Cryptography–PKC 2011: 14th International Conference on Practice and Theory in Public Key Cryptography, Taormina, Italy, 6–9 March 2011; Proceedings 14. Springer: Berlin/Heidelberg, Germany, 2011; pp. 90–108. [Google Scholar]
- Hohenberger, S.; Waters, B. Attribute-based encryption with fast decryption. In Proceedings of the Public-Key Cryptography–PKC 2013: 16th International Conference on Practice and Theory in Public-Key Cryptography, Nara, Japan, 26 February–1 March 2013; Proceedings 16. Springer: Berlin/Heidelberg, Germany, 2013; pp. 162–179. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Taormina, Italy, 6–9 March 2006; pp. 89–98. [Google Scholar]
- Lewko, A.; Waters, B. New proof methods for attribute-based encryption: Achieving full security through selective techniques. In Proceedings of the Annual Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 180–198. [Google Scholar]
- Itkis, G.; Shen, E.; Varia, M.; Wilson, D.; Yerukhimovich, A. Bounded-collusion attribute-based encryption from minimal assumptions. In Proceedings of the Public-Key Cryptography–PKC 2017: 20th IACR International Conference on Practice and Theory in Public-Key Cryptography, Amsterdam, The Netherlands, 28–31 March 2017; Proceedings, Part II 20. Springer: Berlin/Heidelberg, Germany, 2017; pp. 67–87. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. SIAM J. Comput. 2003, 32, 586–615. [Google Scholar] [CrossRef]
- Boldyreva, A.; Goyal, V.; Kumar, V. Identity-based encryption with efficient revocation. In Proceedings of the 15th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 27–31 October 2008; pp. 417–426. [Google Scholar]
- Chen, J.; Lim, H.W.; Ling, S.; Wang, H.; Nguyen, K. Revocable identity-based encryption from lattices. In Proceedings of the Information Security and Privacy: 17th Australasian Conference, ACISP 2012, Wollongong, NSW, Australia, 9–11 July 2012; Proceedings 17. Springer: Berlin/Heidelberg, Germany, 2012; pp. 390–403. [Google Scholar]
- Luo, F.; Al-Kuwari, S.; Wang, H.; Wang, F.; Chen, K. Revocable attribute-based encryption from standard lattices. Comput. Stand. Interfaces 2023, 84, 103698. [Google Scholar] [CrossRef]
- Ling, S.; Nguyen, K.; Wang, H.; Zhang, J. Revocable predicate encryption from lattices. In Proceedings of the Provable Security: 11th International Conference, ProvSec 2017, Xi’an, China, 23–25 October 2017; Proceedings 11. Springer: Berlin/Heidelberg, Germany, 2017; pp. 305–326. [Google Scholar]
- Meng, F. Directly Revocable Ciphertext-Policy Attribute-Based Encryption from Lattices. Cryptology ePrint Archive, Paper 2020/940. 2020. Available online: https://eprint.iacr.org/2020/940 (accessed on 31 July 2020).
- Attrapadung, N.; Imai, H. Attribute-based encryption supporting direct/indirect revocation modes. In Proceedings of the Cryptography and Coding: 12th IMA International Conference, Cryptography and Coding 2009, Cirencester, UK, 15–17 December 2009; Proceedings 12. Springer: Berlin/Heidelberg, Germany, 2009; pp. 278–300. [Google Scholar]
- Seo, J.H.; Emura, K. Revocable identity-based encryption revisited: Security model and construction. In Proceedings of the Public-Key Cryptography–PKC 2013: 16th International Conference on Practice and Theory in Public-Key Cryptography, Nara, Japan, 26 February–1 March 2013; Proceedings 16. Springer: Berlin/Heidelberg, Germany, 2013; pp. 216–234. [Google Scholar]
- Qin, B.; Zhao, Q.; Zheng, D.; Cui, H. (Dual) server-aided revocable attribute-based encryption with decryption key exposure resistance. Inf. Sci. 2019, 490, 74–92. [Google Scholar] [CrossRef]
- Cheng, L.; Meng, F. Server-aided revocable attribute-based encryption revised: Multi-user setting and fully secure. In Proceedings of the Computer Security–ESORICS 2021: 26th European Symposium on Research in Computer Security, Darmstadt, Germany, 4–8 October 2021; Proceedings, Part II 26. Springer: Berlin/Heidelberg, Germany, 2021; pp. 192–212. [Google Scholar]
- Xu, S.; Yang, G.; Mu, Y. Revocable attribute-based encryption with decryption key exposure resistance and ciphertext delegation. Inf. Sci. 2019, 479, 116–134. [Google Scholar] [CrossRef]
- Katsumata, S.; Matsuda, T.; Takayasu, A. Lattice-Based Revocable (Hierarchical) IBE with Decryption Key Exposure Resistance. In Proceedings of the Public-Key Cryptography–PKC 2019: 22nd IACR International Conference on Practice and Theory of Public-Key Cryptography, Beijing, China, 14–17 April 2019; Proceedings, Part II 22. Springer: Berlin/Heidelberg, Germany, 2019; pp. 441–471. [Google Scholar]
- Agrawal, S.; Boneh, D.; Boyen, X. Efficient lattice (h) ibe in the standard model. In Proceedings of the Eurocrypt, Nice, Frence, 30 May–3 June 2010; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6110, pp. 553–572. [Google Scholar]
- Cash, D.; Hofheinz, D.; Kiltz, E.; Peikert, C. Bonsai trees, or how to delegate a lattice basis. J. Cryptol. 2012, 25, 601–639. [Google Scholar] [CrossRef]
- Qin, B.; Deng, R.H.; Li, Y.; Liu, S. Server-aided revocable identity-based encryption. In Proceedings of the Computer Security–ESORICS 2015: 20th European Symposium on Research in Computer Security, Vienna, Austria, 21–25 September 2015; Proceedings, Part I 20. Springer: Berlin/Heidelberg, Germany, 2015; pp. 286–304. [Google Scholar]
- Wang, Q.; Huang, H.; Li, J.; Yuan, Q. Revocable IBE with En-DKER from Lattices: A Novel Approach for Lattice Basis Delegation. Cryptology ePrint Archive, Paper 2023/1028. 2023. Available online: https://eprint.iacr.org/2023/1028 (accessed on 3 July 2023).
- Takayasu, A.; Watanabe, Y. Lattice-based revocable identity-based encryption with bounded decryption key exposure resistance. In Proceedings of the Information Security and Privacy: 22nd Australasian Conference, ACISP 2017, Auckland, New Zealand, 3–5 July 2017; Proceedings, Part I 22. Springer: Berlin/Heidelberg, Germany, 2017; pp. 184–204. [Google Scholar]
- Takayasu, A.; Watanabe, Y. Revocable identity-based encryption with bounded decryption key exposure resistance: Lattice-based construction and more. Theor. Comput. Sci. 2021, 849, 64–98. [Google Scholar] [CrossRef]
- Boyen, X.; Waters, B. Anonymous hierarchical identity-based encryption (without random oracles). In Proceedings of the Advances in Cryptology-CRYPTO 2006: 26th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2006; Proceedings 26. Springer: Berlin/Heidelberg, Germany, 2006; pp. 290–307. [Google Scholar]
- Wang, S.; Zhang, X.; Zhang, Y. Efficient revocable and grantable attribute-based encryption from lattices with fine-grained access control. IET Inf. Secur. 2018, 12, 141–149. [Google Scholar] [CrossRef]
- Yang, K.; Wu, G.; Dong, C.; Fu, X.; Li, F.; Wu, T. Attribute Based Encryption with Efficient Revocation from Lattices. Int. J. Netw. Secur. 2020, 22, 161–170. [Google Scholar]
- Yang, Y.; Sun, J.; Liu, Z.; Qiao, Y. Practical revocable and multi-authority CP-ABE scheme from RLWE for Cloud Computing. J. Inf. Secur. Appl. 2022, 65, 103108. [Google Scholar] [CrossRef]
- Dong, X.; Hu, Y.; Wang, B.; Liu, M.; Gao, W. Lattice-based revocable attribute-based encryption with decryption key exposure resistance. IET Inf. Secur. 2021, 15, 428–441. [Google Scholar] [CrossRef]
- Huang, B.; Gao, J.; Li, X. Efficient lattice-based revocable attribute-based encryption against decryption key exposure for cloud file sharing. J. Cloud Comput. 2023, 12, 1–15. [Google Scholar] [CrossRef] [PubMed]
- Boneh, D.; Gentry, C.; Gorbunov, S.; Halevi, S.; Nikolaenko, V.; Segev, G.; Vaikuntanathan, V.; Vinayagamurthy, D. Fully key-homomorphic encryption, arithmetic circuit ABE and compact garbled circuits. In Proceedings of the Advances in Cryptology–EUROCRYPT 2014: 33rd Annual International Conference on the Theory and Applications of Cryptographic Techniques, Copenhagen, Denmark, 11–15 May 2014; Proceedings 33. Springer: Berlin/Heidelberg, Germany, 2014; pp. 533–556. [Google Scholar]
- Asharov, G.; Jain, A.; López-Alt, A.; Tromer, E.; Vaikuntanathan, V.; Wichs, D. Multiparty computation with low communication, computation and interaction via threshold FHE. In Proceedings of the Advances in Cryptology–EUROCRYPT 2012: 31st Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Proceedings 31. Springer: Berlin/Heidelberg, Germany, 2012; pp. 483–501. [Google Scholar]
- Gentry, C.; Peikert, C.; Vaikuntanathan, V. Trapdoors for hard lattices and new cryptographic constructions. In Proceedings of the Fortieth Annual ACM Symposium on Theory of Computing, Victoria, BC, Canada, 17–20 May 2008; pp. 197–206. [Google Scholar]
- Micciancio, D.; Peikert, C. Trapdoors for Lattices: Simpler, Tighter, Faster, Smaller. In Proceedings of the Eurocrypt, Cambridge, UK, 15–19 April 2012; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7237, pp. 700–718. [Google Scholar]
- Ajtai, M. Generating hard instances of the short basis problem. In Proceedings of the Automata, Languages and Programming: 26th International Colloquium, ICALP’99, Prague, Czech Republic, 11–15 July 1999; Proceedings 26. Springer: Berlin/Heidelberg, Germany, 1999; pp. 1–9. [Google Scholar]
- Alwen, J.; Peikert, C. Generating shorter bases for hard random lattices. Theory Comput. Syst. 2011, 48, 535–553. [Google Scholar] [CrossRef]
- Regev, O. On lattices, learning with errors, random linear codes, and cryptography. J. ACM (JACM) 2009, 56, 1–40. [Google Scholar] [CrossRef]
- Peikert, C. Public-key cryptosystems from the worst-case shortest vector problem. In Proceedings of the Forty-First Annual ACM Symposium on Theory of Computing, Bethesda, MD, USA, 31 May–2 June 2009; pp. 333–342. [Google Scholar]
- Gorbunov, S.; Vaikuntanathan, V.; Wee, H. Predicate encryption for circuits from LWE. In Proceedings of the Annual Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 503–523. [Google Scholar]
- Naor, D.; Naor, M.; Lotspiech, J. Revocation and tracing schemes for stateless receivers. In Proceedings of the Advances in Cryptology—CRYPTO 2001: 21st Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; Proceedings 21. Springer: Berlin/Heidelberg, Germany, 2001; pp. 41–62. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Q.; Li, J.; Wang, Z.; Zhu, Y. Revocable-Attribute-Based Encryption with En-DKER from Lattices. Mathematics 2023, 11, 4986. https://doi.org/10.3390/math11244986
Wang Q, Li J, Wang Z, Zhu Y. Revocable-Attribute-Based Encryption with En-DKER from Lattices. Mathematics. 2023; 11(24):4986. https://doi.org/10.3390/math11244986
Chicago/Turabian StyleWang, Qi, Juyan Li, Zhedong Wang, and Yanfeng Zhu. 2023. "Revocable-Attribute-Based Encryption with En-DKER from Lattices" Mathematics 11, no. 24: 4986. https://doi.org/10.3390/math11244986




