1. Introduction
The smart grid is a newly evolving next-generation intelligent power grid, and many technological research works were conducted in different countries over the last decade to increase the efficiency of their power grids. The primary consideration in adopting the smart grid should be protection of the users′ privacy [
1,
2,
3]. In other words, unlike existing security measures, the smart grid system should basically focus on the security of users rather than suppliers. More personal and specific information can be exposed in the smart grid environment by smart devices or hacking attacks when diverse types of information are combined [
4,
5,
6]. The major issue of personal information protection in the distribution of smart grid technology is that it is possible to infer a user’s behavioral pattern based on his/her energy consumption data by collecting and analyzing more detailed personal data, such as the characteristics of the user’s energy usage or the frequency of energy production obtained, by applying the latest electric meters and other related equipment and technologies. In addition, the data read by smart meters inevitably require a certain monitoring or surveillance scheme as they are electronically collected and transmitted, rather than manually processed as in the past. The capacity of a meter capable of assessing consumer patterns or types of appliance depends on the frequency with which it collects data and the types of data being collected. Also, the user’s behavior at home can make it is easier to infer his/her activity patterns in other places.
The factors associated with privacy intrusion scenarios in a smart grid environment include the following: (1) information concerning the use of a particular medical device or piece of electronic equipment which indicates their activation times and personal patterns, segmented data pertaining to the power consumption of each household appliance and its measurement location, and detailed information on the use of the appliances or equipment in use at a specific location; (2) the possibility of tracking a physical location through newly consumed energy, for instance, the charging of an electric automobile; (3) the activities in a certain house or building can be inferred from the electronic signature or use time pattern upon activation of a device or piece of equipment, which can form the basis for understanding a specific user’s activities. Thus, the collection of a consumer’s energy use data by a third party should be limited to the information required to serve the third party’s purpose and which is authorized by the consumer.
The anonymous signature scheme comprises a function for authenticating signed messages while hiding the actual identity of the signer, which in itself is a common method in current systems that require the input signature to be authenticated. This scheme was developed by Chaum and Heyst in 1991 [
7]. As for the group signature scheme, a member of a certain group is able to attach his/her signature in a message to prove that he is actually a member, and the verifier of the message will be able to confirm that person’s membership only, without actually identifying the signer. However, it is possible for the opener, who authenticates the input signature, to identify the signer with the information of the signer previously stored in the system. The opener can be an organization or institution that deals with incidents associated with signatures. The group signature scheme is widely used as an anonymous signature scheme because of its reliability [
8]. Despite its reliable performance, however, the security of personal information is called into question as many users consider that the opener has sufficient power to identify the signer and obtain the latter’s personal information or information on anonymous activities for other purposes. To resolve this problem, Sakai et al. [
9] introduced a complementary scheme by adding an “admitter” to the anonymous signature scheme. Thus, Sakai added the admitter and limited the opener’s access to the signer’s identification only by obtaining the consent of the admitter. In 2013, Ohara et al. [
10] resolved the problem raised by Sakai (2012), which was the admitter’s limited amount of token issuance.
The group signature scheme is often used when it is necessary for the authenticator to verify that the signer is a member of a particular group without revealing the actual identity. The real identity of the signer can be disclosed to the authenticator only if there are incidents or disputes that need to be solved. Nevertheless, it is quite clear that the signer will feel the burden of revealing his/her identity or anonymous activities to the authenticator without his/her consent and consider that the authority of the authenticator is too great. Thus, to limit the authority of the authenticator while maintaining the effectiveness of the group signature schemes, an anonymous signature scheme which authorizes the authenticator to identify the signer only with the token issued by the signer him/herself when generating a signature is proposed in this study.
2. Related Research
In a conventional power grid where electric power is delivered to the end users via substations (
Figure 1), the power generation and distribution processes are centralized by the system, which assumes the role of mapping and visualizing the routine operations while controlling these processes to meet the power supply/demand schedule and its storage.
However, following the rapid development of information technology (IT), such a grid architecture transformed in a way that can provide a more efficient and effective means of power management by integrating with Internet Protocol (IP)-based technologies. The network convergence based on these technologies [
11] allows the grid to interwork with an external network(s) by adopting the Transmission Control Protocol (TCP)/IP for a more efficient power management and provision of flexible but efficient service operations.
For the last decade, the development in the hardware, software, and communication technologies led to more advanced and sophisticated information and communications technology (ICT) which were the major factor of widespread mobile smart devices, software applications, or communication architectures [
12,
13].
The next-generation (21st century) power grid being called the smart grid (
Figure 2) enables a smarter, interactive, and dynamic grid management and services based on the ubiquitous computing and advanced ICT technology to respond to the era of the fourth industrial revolution. One of the major advantages of the smart grid is that its bi-directional communication capability can not only improve the power management or operating process but also be utilized for establishing an Internet of things (IoT) system for the users’ residences.
The conceptual smart grid model developed by the United States (US) National Institute of Standards and Technology (NIST) defined a smart grid as a complex infrastructure based on a set of seven chief domains [
14], namely bulk generation, energy distribution, power transmission, operation and control, market, service providers, and customers and individual domains, composed of heterogeneous elements (e.g., organizations, buildings, individuals, and systems, including system resources and other entities). Also, the backhaul network is essential for achieving smooth but efficient communications between customers and utility companies when advanced power management systems such as advanced metering infrastructure (AMI) are to be embedded into the smart grid [
15,
16].
The problem pertaining to breach of privacy is one of the major issues when people are using a service which requires the user to be authenticated. A series of privacy protection schemes were introduced to let users remain anonymous by allowing only encrypted information or minimum user information to be disclosed to the system administrators; however, the security levels and the means of protection provided by those schemes vary and can be inadequate sometimes. The blind signature [
17] or the homomorphic encryption [
18] scheme is mainly used [
19]. To simply describe them, for instance, the former is a scheme where the first party (Party 1) attaches his signature to the message generated by the second party (Party 2) without having any knowledge about the content of the message. Then, the third party (Party 3) can receive the message but the identity of the message sender (Party 2) will remain secure as his/her signature will not be authenticated. Meanwhile, in the latter scheme, a specific mathematical or a computational manipulation is applied to the message or the text to create a ciphertext so that only the authorized party with the right decryption key will be able to decipher the encrypted message. The smart meters usually adopt the latter scheme to encrypt and transmit their requirements to their central control system (utility company administrator) along with a specific encryption function to let the system to decrypt the contents of the requirement with an appropriate decryption key. These schemes were originally developed for the electronic voting systems to conceal the voters’ information in the application layer but did not consider the possibility leaking the information from the lower layers (i.e., link layer or network layer) of the protocol stack. It is quite possible that the repeated use of the same IP address overtime may provide access to the identities of the communicating parties or a means for hackers to analyze the traffic [
20].
Nonetheless, it is also true that such benefits may be provided at the cost of breaching privacy. That is, a large volume of generated data and its high granularity in which more information is contained would allow any third party with malicious intent to grasp the lifestyles of the customers. Also, there were some claims in some countries that the use of smart meters further endangered the security/privacy of the customers [
21]. The balance between achieving an efficient and effective smart metering and guaranteeing the adequate level of personal information protection is always the focus of such a controversy. Using the terminology from Reference [
22], the solutions that aim to protect the privacy should guarantee the customers a suitable level of anonymity together with a temporary unlinkability which disconnects them from the metering infrastructure (i.e., disabling power usage reading, etc.). However, the question here is whether the unlinkability can or should be fully achieved even when customers are required to settle their bills at some time or another. The same question can be addressed to unobservability, which refers to the condition where one’s power usage cannot be observed by others. Although it is possible to keep the record of the total aggregated amount of one’s power usage at the substation level, it still needs to be delivered to the main system for the smart metering system to be fully functional [
22,
23].
2.1. Anonymous Authentication and Anonymous Signature Schemes
The term “anonymous authentication” refers to a cryptographic technology that allows the person or entity requesting authentication to authenticate him or herself as a legitimate entity while remaining anonymous. Commonly, simple aliases designed to preserve anonymity cannot be used for this type of authentication as the user trail can be traced easily; thus, using them cannot be considered an anonymous authentication scheme. A group signature, anonymous letter of credit, and more were introduced for the purpose of anonymous authentication in a number of research works. The group signature is an electronic signature scheme which the signer can verify him/herself as a member of a particular group without having to reveal his/her identity, thus enabling the authenticator to determine that the person concerned is actually a member without being able to identify him/her. Also, the group signature scheme often involves a credible third-party organization referred to as an “opener”, e.g., the police or an internet-related authority. The opener is authorized to identify a signer from the group signature and can track the identity of any user who displays inappropriate behavior (or commits illegal acts) while using anonymous services. The group signature scheme is currently considered the most practical for real-world applications such as web application services as it offers traceable anonymity. In general, the group signature scheme offers anonymity, traceability, and linkability.
Figure 3 shows a schematic representation of the group signature scheme, whose members are normally distinguished as the group manager who sets the parameters, the opener who is authorized to trace a specific signature in a group, the signer, and the authenticator. Each signer in the same group has his/her own private signature key, whereas the authenticator can verify the signatures with an open group key. Also, information that can be used to identify a signer is encrypted in the signature value so that only the opener can trace the identity of a group signer with his open group key.
Figure 4 represents a group signature scheme that provides linkability, which was studied with a view of applying it to a variety of applications. Linkability is a basis for determining uniformity in a number of signatures so as to determine whether the signatures were written by the same person. Although the linker may detect uniformity in the signatures, he/she is not able to identify the signer.
In the smart grid environment, service providers can enhance the quality of their services by performing big data analyses of users’ data, such as their real-time power usage patterns, etc., and then processing them into meaningful information. Thus, the level of privacy protection can be increased by offering anonymity through group signatures, while the service providers are able to provide flexible services by linking with the data of an anonymous user (signer). Jeong-Yeon Hwang et al. introduced a group signature scheme that provides local linkability [
6]; however, in this study, the linker refers to an organization or institution that has a linking key generated by the group manager so that, in general, it becomes the service provider. The linker has the authority to check the link status for all signature values.
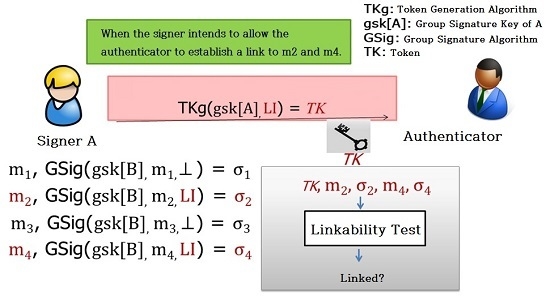
Figure 5 shows a group signature scheme offering limited linkability. Unlike existing group signature schemes where the opener is a credible third-party organization, the linker in this scheme is the service provider itself or the organization or institution designated by the service provider, with could result in privacy violations of the service users. For example, let us assume that an anonymous user in the smart grid environment uses a power usage analysis service along with an IoT service. In this case, the service provider will be able to link the power usage information of person A (who just entered his/her signature with the group signature key) with the information about his/her IoT service use. At this time, the service provider does not know the identity of A but it is able to determine whether the user currently using these two services is one and the same, potentially leading to an undesirable breach of privacy. As such, while studies related to existing group signature schemes focused on managing the system for the designated linker so as to be able to test the linkability of all signature values, this study aims to secure a fundamental technology capable of preventing unnecessary information exposures by developing a group signature scheme that allows the designated linker to test the linkability only for those signatures desired by the signer. Thus, in the example shown above, an anonymous signer A can transfer the power usage values to the linker for the linkability test, using a group signature key while transmitting the IoT usage information separately with the same key for the same test. Thus, this scheme can provide a more secure method of preventing privacy breaches by minimizing the level of personal information exposure.
3. Anonymous Signature with Signer-Controlled Opening Capability
The anonymous signature scheme allows authentication of the signer without revealing his/her identity, whereas the group signature scheme is a method of verifying that the signer is a member of a certain group, also without exposing the signer’s identity. Nevertheless, it is possible for an opener to identify an anonymous signer based on the information of the signer, which is neither desirable nor favorable for the signer who wishes his/her signature to be authenticated but does not want to reveal his/her actual identity. Thus, this section discusses a solution whereby the signer obtains a (security) token upon entering his/her signature so that the opener is not able to find the information of the signer without permission.
3.1. Application
The proposed anonymous signature scheme prevents the opener from identifying the signer without his/her permission so that the opener has to obtain a token specifically issued for the signature that the signer wishes to be identified. For example, this scheme can be applied to an anonymous donation system. The identities of the donors are hidden to ensure that the fundraiser cannot know who donated the funds. However, if the donors wish to apply for an income tax deduction, all they have to do is issue a token to the relevant tax administration to prove their donations through signature authentication. Currently, many countries operate an anonymous reporting system against corruption among civil servants, but the problem is that the filed reports and the identity of a whistle-blower or an accuser can be leaked while processing the report, thus endangering that person or making the system useless. The proposed anonymous signature scheme can prevent such an incident by offering a more secure protection mechanism that makes it almost impossible for an intruder or a report handler to find the identity of the person filing the report. If the reporting system requires the accuser to be identified, and if he/she agrees to disclose his/her identity for a final confirmation or compensation, all he/she has to do is issue a token allowing the relevant authority to confirm the true identity.
3.2. Formal Model
The proposed method has the following four algorithms:
GKg(1λ, 1n): This is the algorithm where the group manager puts the security parameter λ and the number of anonymous signers n to create the signer’s signing key gski, the opener’s opening key ok, and the public parameters gpk for the system.
GSig(gpk, i, gski, M): This is the algorithm where the anonymous signer uses the group public key gpk, the signer’s index i, the signer’s signing key gski, and the message M to create the anonymous signature σ, and the token TKM that permits disclosure.
GVf(gpk, i, gski, M): This is the algorithm where the verifier puts the group public key gpk, the message M, and the anonymous signature σ to verify the signature.
Open(gpk, ok, M, σ, TKM): This is the algorithm where the opener puts the group public key gpk, the opener’s opening key ok, the message M, the anonymous signature σ, and the token TKM to check the signer’s identification.
3.3. Security Notion
The four security concepts based on the definition of a general security model [
12,
13] for the group signature schemes proposed by Mihir Bellare et al. are introduced in the proposed group signature scheme.
- -
Full anonymity: The identity of a signer should not be accessed unless a token is issued by the signer. Then, the opener, upon receiving the token, is allowed to trace the signer’s identity.
- -
Correctness: A correct signature and a token issued in the proper way should be used for verification when identifying the signer.
- -
Unforgeability of signature: A valid anonymous signature can only be written by the signer him/herself to attach it to a specific message.
- -
Unforgeability of token: A valid token can be created and issued to allow the opener to access a specific message or a signature.
3.4. Proposed Scheme
GKg(1λ, 1n)
- -
Define two hash functions:
H1: {0, 1}*→ G, H2: {0, 1}*→ Zp.
- -
Select a parameter of the bilinear group (p, G, GT, e, g).
- -
Select a random element u, v, h ∈ G\{1}, a random integer ξ1, ξ2, ξ3, γ ∈ Zp, and calculate g1 = uξ1hξ3, g2 = vξ2hξ3, ω ← gλ.
- -
Select a random xi ∈ Zp for each signer i (1≤ i ≤ n), then calculate Ai ← g1/(γ+xi).
- -
Print out the group public key
gpk ← (p, G, GT, e, g, gz, u, v, h, g1, g2, ω, H1, H2),
the opener’s opening key ok ← (ξ1, ξ2, ξ3, e(Ai, g)1≤i≤n),
and each signer’s signing key gski(1≤i≤n) ← (Ai, xi)1≤i≤n.
GSig(gpk, i, gski, M)
- -
Select a random integer α, β, ρ, η, μ ∈ Zp.
- -
Calculate (T1, T2, T3, T4) ← (uα, vβ, hα+β, g1αg2βAigη) and (T5, T6) ← (gρ, e(gμ, H1(M))ρ).
- -
Select a random integer rα, rβ, rρ, rη, rx, rαx, rβx, rρx, rηx ∈ Zp.
- -
Calculate
R1 ← urα; R2 ← vrβ; R3 ← hrα+rβ
R4 ← e(T4, g)rx e(g1, ω)−rα e(g1, g)−rαx e(g2, ω)−rβ e(g2, g)−rβx e(g, ω)−rη e(g, g)−rηx
R5 ← grρ; R6 ← e(g μ, H1(M))rρe(g, g)−rη
R7 ← T1rxu−rαx; R8 ← T2rxu−rβx; R9 ← T5rxu−rρx
R10 ← T6rxe(gμ, H1(M))rρxe(g, g)−rηx
c ← H2(M, T1, …, T6, R1, …, R10)
sα ← rα + cα; sβ ← rβ + cβ; sρ ← rρ + cρ
sη ← rη + cη; sx ← rx + cxi; ← sαx ← rαx + cαxi
sβx ← rβx + cβxi; sρx ← rρx + cρxi; sηx ← rηx + cηxi.
- -
Print out a signature
σ ← (gμ, T1, …, T6, c, sα, sβ, sρ, sη, sx, sαx, sβx, sρx, sηx).
- -
In addition, calculate and print out the opening-allowed token TKM = H1(M)μ.
GVf(gpk, M, σ)
- -
Calculate
R1’ ← usαT1−c; R2’ ← vsβT2−c; R3’ ← hsα+sβT3−c
R4’ ← e(T4, g)sx e(g1, ω)−sα e(g1, g)−sαx e(g2, ω)−sβ
∙ e(g2, g)−sβx e(g, ω)−sη e(g, g)−sηx (e(g, g)/e(T4, ω))−c
R5’ ← gsρT5−c; R6’← e(g μ, H1(M))sρe(g, g)−sη T6−c
R7’ ← T1sxu−sαx; R8’ ← T2sxv−sβx; R9’ ← T5sxg−sρx
R10’ ← T6sxe(gμ, H1(M))−sρx e(g, g)sηx.
- -
Print out “valid” if the equation c ← H2(M, T1, …, T6, R1’, …, R10’) is completed, or “invalid” if the equation is not completed.
Open(gpk, ok, M, σ, TKM)
- -
Verify the signature’s validity first using the GVf algorithm. Print out ⊥ when invalid.
- -
Verify the token’s validity using e(gμ, H1(M)) = e(g, TKM). Print out ⊥ when invalid.
- -
Identify the signer
i, who satisfies the equation below when the signature and the token are valid.
- -
Print out i if there is an i that satisfies the equation. Print out ⊥ if not.
Based on the assumption that the correctness of the proposed scheme is adequate while the decisional bilinear Diffie–Hellman problem and the decisional linear problem are difficult to solve, full anonymity can be achieved with a random oracle model. Also, the unforgeability of a signature (token) can be dealt with using the same model by assuming that the q-strong (computational) Diffie–Hellman problem is difficult to solve. The details of proof were omitted as they deviate from the research purpose.
In the following section, an anonymous signature scheme is proposed whereby a signer allows the opener to trace his/her identity by accessing his/her information or message to which he/she gave permission by issuing a token. The proposed scheme is expected to raise the level of privacy protection for the signer and can be used in a variety of systems, such as anonymous donation or corruption reporting systems.
4. Group Signature with Signer-Controlled Opening Capability: Separate Token Generator
Group signature schemes are considered a high-security cryptographic signature authentication system for protection of the signer′s privacy. The authenticator or the verifier of a signature is provided with a limited amount of information or authority when he/she verifies the signer’s affiliation with a certain group without knowing the latter’s true identity. Nevertheless, it is still possible for the opener to trace the identity when the situation makes it necessary to deal with malicious accesses. However, concerns about breaches of the signer’s privacy through the exposure of his/her personal information still remain. This chapter deals with such a problem by allowing the signer to issue a token with which the opener can access only those messages or items of information, including the signer′s identity, whose disclosure is approved.
4.1. Formal Model
The proposed anonymous signature method is composed of the following four algorithms:
KGen(1λ): This is an algorithm where a trusted third party puts a security parameter λ to create public parameters for the running system gpk, an issuing key for the key issuer ik, and an opening key for the opener ok.
ISS/Join: This is an interactive algorithm between users and issuers that functions as an issuer issues gski to a user in response to a user request.
GSig(gpk, i, gski, M): This is an algorithm where an anonymous signer creates a signature σ using a group public key gpk, an index of the signer i, a signing key of the signer i, gski, and a message M.
TKGen(gpk, i, gski, M): This is an algorithm where an anonymous signer creates an opening-permission token TKM using a group public key gpk, and an index of a signer i.
GVf(gpk, i, gski, M): This is an algorithm where a signature verifier performs a verification of an anonymous signature using a group public key gpk, a message M, and an anonymous signature σ.
Open(gpk, ok, M, σ, TKM): This is an algorithm where an opener checks the identity of an anonymous signer from an anonymous signature using an opening key of an opener ok, a message M, an anonymous signature σ, and a token TKM.
4.2. Security Notion
Mihir Bellare et al. defined the general security model of a group signature method [
12,
13]. This paper suggests the following four security notions based on Bellare’s definition:
Correctness: The proper signature and proper token are always valid when verifying, and the opener with the right signature and the right token can always check the identification from the signature.
Full anonymity: The identity on the anonymous signature must remain inaccessible until the anonymous signer issues a token. When a token is issued, the identity must be inaccessible except by the opener with the token.
Signature unforgeability: Only the proper signer can create a valid anonymous signature for a specific message.
Token unforgeability: Only the proper signer can create a valid token for a specific signature.
4.3. Proposed Scheme
GKg(1λ, 1n)
- -
Define the two hash functions:
H1: {0, 1}*→ G, H2: {0, 1}*→ Zp.
- -
Select a parameter of the bilinear group (p, G, GT, e, g, gz).
- -
Select a random element u, v, h ∈ G\{1}, a random integer ξ1, ξ2, ξ3, γ ∈ Zp, and calculate g1 = uξ1hξ3, g2 = vξ2hξ3, ω ← gλ.
- -
Print out the group public key gpk ← (p, G, GT, e, g, gz, u, v, h, g1, g2, ω, H1, H2), and issue key λ, the opener’s opening key
ok ← (ξ1, ξ2, ξ3, e(Ai, g)1≤i≤n).
ISS/Join
- -
User i selects random yi ∈ Zp and calculates Si ← gzyi.
- -
User i sends Si to the issuer.
- -
Issuer selects random xi ∈ Zp and calculates
Ai ← (ggzyi)1/(γ+xi).
- -
Issuer sends Ai, xi to user i.
- -
User i obtains the signing key gski = (Ai, xi, yi).
GSig(gpk, i, gski, M)
- -
Select a random integer α, β, ρ, η ∈ Zp.
- -
Calculate (T1, T2, T3, T4) ← (uα, vβ, hα+β, g1αg2βAigη) and (T5, T6, T7) ← (gρ, e(T5, g)yi, e(T5, H1(M))yie(g, g)−η).
- -
Select a random integer rα, rβ, ry, rη, rx, rαx, rβx, rηx ∈ Zp.
- -
Calculate
R1 ← urα; R2 ← vrβ; R3 ← hrα+rβ
R4 ← e(T4, g)rx e(g1, ω)−rα e(g1, g)−rαx e(g2, ω)−rβ
∙ e(g2, g)−rβx e(g, ω)−rη e(g, g)−rηx e(gz, g)−ry
R5 ← e(T5, g)ry; R6 ← e(T5, H1(M))rye(g, g)−rη
R7 ← T1rxu−rαx; R8 ← T2rxu−rβx; R9 ← T6rxe(T5, g)−ryx
R10 ← T7rxe(T5, H1(M))ryxe(g, g)−rηx
c ← H2(M, T1, …, T7, R1, …, R10)
sα ← rα + cα; sβ ← rβ + cβ; sy ← ry + cy
sη ← rη + cη; sx ← rx + cxi; sαx ← rαx + cαxi
sβx ← rβx + cβxi; sρx ← rρx + cρxi; sηx ← rηx + cηxi.
- -
Print out σ ← (T1, …, T7, c, sα, sβ, sy, sη, sx, sαx, sβx, sρx, sηx).
TKGen(gpk, i, gski, M)
- -
Print out TKM = H1(M)yi.
GVf(gpk, M, σ)
- -
Calculate
R1’ ← usαT1−c; R2’ ← vsβT2−c; R3’ ← hsα+sβT3−c
R4’ ← e(T4, g)sx e(g1, ω)−sα e(g1, g)−sαx e(g2, ω)−sβ e(g2, g)−sβx
∙ e(g, ω)−sη e(g, g)−sηx e(gz, g)−sy (e(g, g)/e(T4, ω))−c
R5’ ← e(T5, g)syT6−c; R6’ ← e(T5, H1(M))sye(g, g)−sη T7−c
R7’ ← T1sxu−sαx; R8’ ← T2sxu−sβx; R9’ ← T6sxe(T5, g)−syx
R10’ ← T7sxe(T5, H1(M))syxe(g, g)−sηx.
- -
Print out “valid” if the equation c ← H2(M, T1, …, T7, R1’, …, R10’) is completed, or “invalid” if the equation is not completed.
Open(gpk, ok, M, σ, TKM)
- -
Verify the signature’s validity first using the GVf algorithm. Print out ⊥ if invalid.
- -
Find out the signer
i, who satisfies the equation below, when the signature and the token are valid.
- -
Print out i if there is an i that satisfies the equation. Print out ⊥ if not.
Determining correctness in an anonymous signature scheme is not that difficult in the proposed scheme when compared to proving the level of full anonymity. Nevertheless, it can be proven with a random oracle model when an assumption is made that the decisional bilinear Diffie–Hellman problem is not easy to solve. The unforgeability of a signature can be proven with the same model as above when it is assumed that the q-strong Diffie–Hellman problem is not easy to prove. The problem of the unforgeability of a token can be solved in a similar way, but the assumption should be made that the computational Diffie–Hellman problem is not easy to solve. The details of proof were omitted as they deviate from the research purpose.
This chapter provides a solution to signers’ concerns about the exposure of their identities in the anonymous signature schemes. The issues pertaining to the excessive authority of the openers were covered by another study in which an admitter was added to the scheme to limit the power of the openers. However, as the possibility of successfully tracing the signer’s identity still remained, this study proposed a method by which the signer issues a token him/herself without the intervention of the admitter. It is expected that, if the proposed method is applied to the existing anonymous signature schemes, their level of security will be improved significantly, thus alleviating the users’ concerns.
5. Efficiency Comparison
A comparison of theoretical computational costs involved in the algorithms for the generation and verification of the group signatures is shown in
Table 1. The group signature scheme in Reference [
24] is a sort of a pairing-based group signature scheme which does not offer linkability, and is used for the comparison as a reference scheme. On the other hand, the group signature scheme in Reference [
6] offers linkability by allowing the pre-defined linker to check the linkability of all the relevant signatures. Reference [
25] introduced a scheme where the signer can control the linkability. When generating the random elements, the respective coefficients (integers) of variables G1, G2, and Zp indicate the individual number of generated random elements (i.e., 2 G1 + 1 G2 + 2 Zp indicates that two random elements were generated for G1, one random element for G2, and two random for Zp). Also, in the calculation formula, P represents the pairing operation; MG1 (or MG2) is the scalar multiplication operation for the group G1 (or G2); EGT is the exponentiation operation in the group GT. As such, the expression 6 P + 9 MG1 + 1 MG2 + 6 EGT implies that six pairings and nine scalar multiplications for G1, one scalar multiplication for G2, and six exponentiations for GT were performed by the algorithm which mainly focuses on the pairing tasks (
Table 2), where the pairing operations were performed approximately six times more than the scalar multiplications.
The operation of each group signature scheme (
Table 2) was simulated with the computer (Intel Sandy Bridge i3 2330M 2.2-GHz processor, 4 GB random-access memory (RAM), Ubuntu 12.04), whereas the operations (pairing) were performed using the Python Pairing-Based Cryptography (PYPBC) Library, adopting the d224 curve, specifically. The resulting values are the averages of 100 simulations conducted for the individual schemes. The time required for the proposed scheme to generate and verify the signature was similar to that of References [
6,
24,
25] and the same level of similarity was found in the computational costs. This means that the function “signer-controlled opening capability” being added to the computation process did not actually affect the computational costs much. Meanwhile, the proposed algorithm in this study was developed in a way that it can be adopted in previous research [
26,
27,
28,
29,
30,
31,
32] pertaining to smart grids.
6. Conclusions
The group signature scheme is an electronic signature scheme with which a signer can prove that he/she is a member of a certain group without revealing his/her own identity, and which allows the authenticator to make a judgment on whether the signature is written by the same person or not, but which does not allow the authenticator to know the identity of the signer. A number of previous studies flexibly applied group signature schemes to various applications.
Meanwhile, the proposed algorithm in this study was developed in a way that it can be adopted in previous research [
26,
27,
28,
29,
30,
31,
32] pertaining to smart grids.
Thus, two anonymous signature schemes in a smart grid environment were proposed in this study: a scheme where the anonymous signer issues a token to let the opener identify him/her only for the designated signature, and another scheme which requires the signer’s consent for identification. In the former, the signer generates the token along with his/her signature using a short-term secret key, whereas, in the latter, the token is generated using a long-term secret key only when the signer agrees to disclose his/her identity after entering the signature. Although there is a possibility of compromising the security a little when the latter scheme is adopted, the burden of the signer having to issue and keep the token all the time can be lightened, improving the convenience of the scheme.