An Adaptable System to Support Provenance Management for the Public Policy-Making Process in Smart Cities
Abstract
:1. Introduction
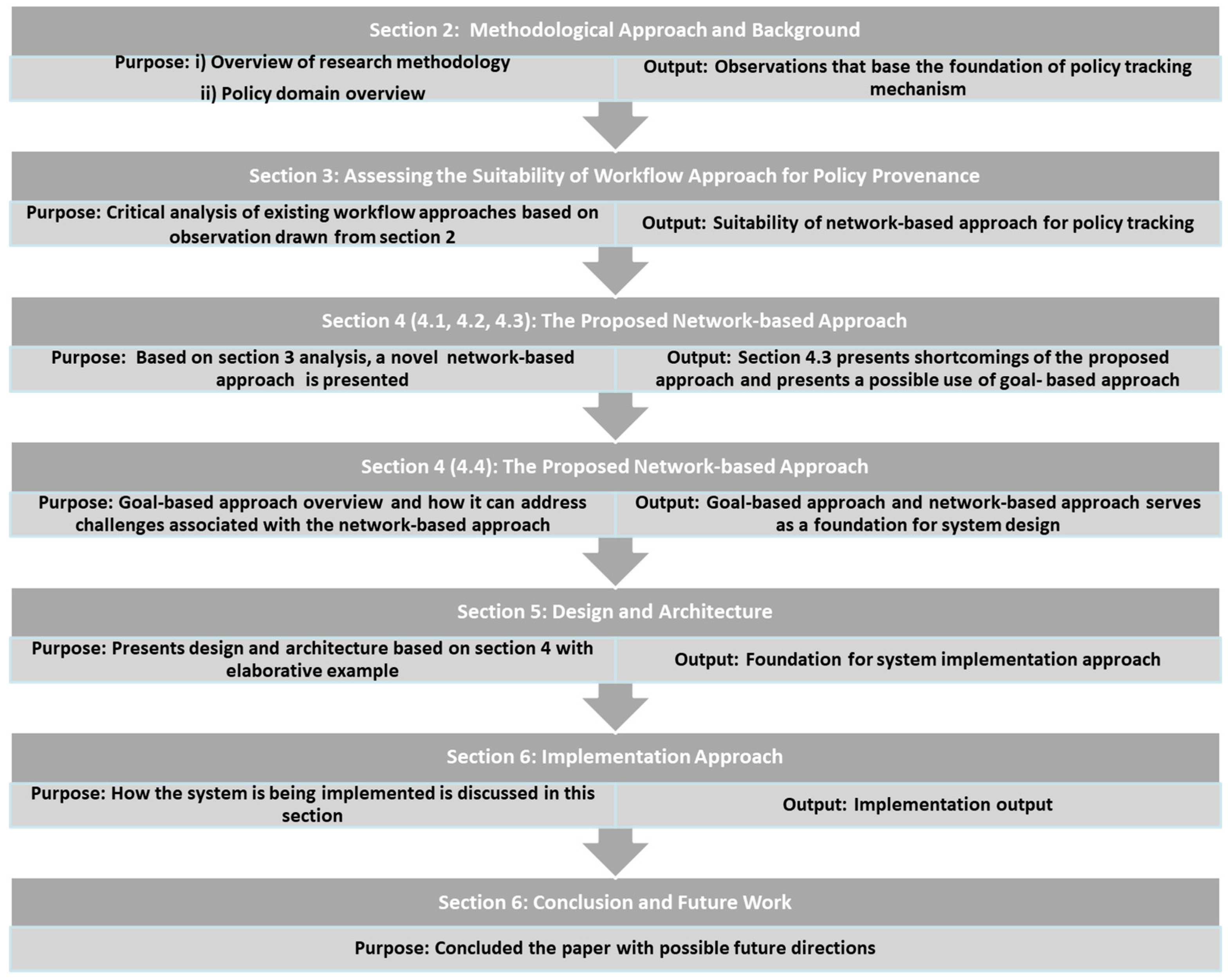
2. Methodological Approach, Background and Context
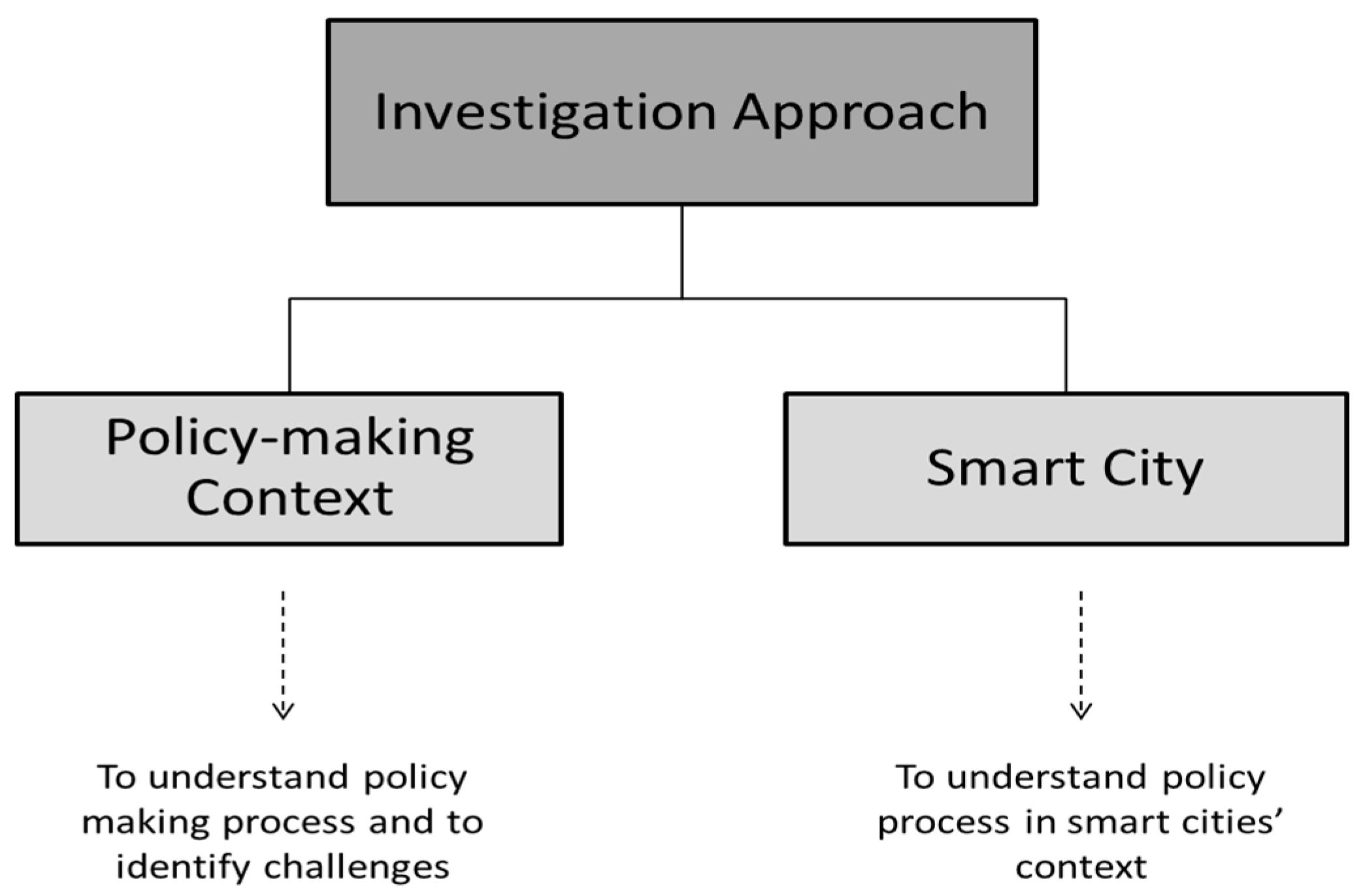
2.1. Methodological Approach
- (i).
- We have conducted a detailed investigation of the relevant literature to understand the policy domain and its challenges [11,18,19,20,21,22,23]; Section 2.2.1 covers the observations in detail. The study was also conducted in the domain of smart cities (details provided in Section 2.2.2) to explore the policy process in smart cities and how the policy process has (or is supposed to) transformed for its suitability in the smart cities context. The investigation uncovered important observations which are apposite to the design of a system that supports provenance management.
- (ii).
- We have elicited input from experts (policy makers) to understand the practical setup of the policy environment and to cross-check the observations that we have drawn from the literature (covered in Section 2.2).
- (iii).
- (iv).
- For testing our approach, we are collecting some policy formation examples from the Smarticipate project [24]. It is to be noted here that our system will not be fully deployed in the Smarticipate project; we simply aim at collecting policy examples from the project to verify our approach with the given examples.
2.2. Background and Context
2.2.1. Policy Process Domain Knowledge
Domain Challenges of the Process
- (i).
- Although policy-making shares some similar facets with business processes [11] it has been found that, unlike business processes, task specification is not straightforward and can be rather complex in policy-making.
- (ii).
- The process followed for devising policies is largely non-deterministic, unstructured and ad-hoc [22,23] in nature. This means that task specification and task assignment to actors largely depends on the policy and this consequently adds additional challenges in structuring processes. This comes about as a result of policy-making being a political process, with different policy demands and largely involves tacit knowledge of policy-makers to decide the next appropriate action [23].
- (iii).
- The relevant literature [11,18,19,20,21,23] states that knowledge intensive aspects are very much prevalent in the process of policy creation. Given this fact, the processes of devising policies are usually guided by human knowledge, experience and decisions. This largely contributes in an ad-hoc manner and leads to complex task specification (covered in points ‘i’ and ‘ii’ above).
- (iv).
- In comparison to a business process, the number of stakeholders involved in a policy process is normally significantly large [11,23,25]. These large number of stakeholders require a solution that facilitates cross-organisation communication. This leads to further challenges in process orchestration since actors involved in each policy may not be the same, thereby increasing the complexity of task identification and assignment in each policy. In the case of the specific assignment of roles and responsibilities to actors, the challenge of process orchestration remains because tasks and their sequence for each policy can vary. Furthermore, citizens can participate at any phase which may again increase the complexity associated with the policy process [11].
- (v).
- The policy formulation process is not the same for all policies [23]. Depending on the needs and requirements of policies, the tasks and the relevant stakeholders’ participation may fluctuate.
- (vi).
- Policy-making can be unpredictable [23] i.e., it is complex to orchestrate the process beforehand, due to the points ‘i,’ ‘ii,’ ‘iii,’ ‘iv’ and ‘v’ outlined above.
- (vii).
- Unlike a business process, a policy-making process may inherently be a lengthy, drawn-out process [11]. Often the execution of any particular task may last from a number of days to a couple of months. One of the factors of this lengthy process is the involvement of a large number of stakeholders. The consultation process with all the stakeholders contribute in lengthy policy-making process.
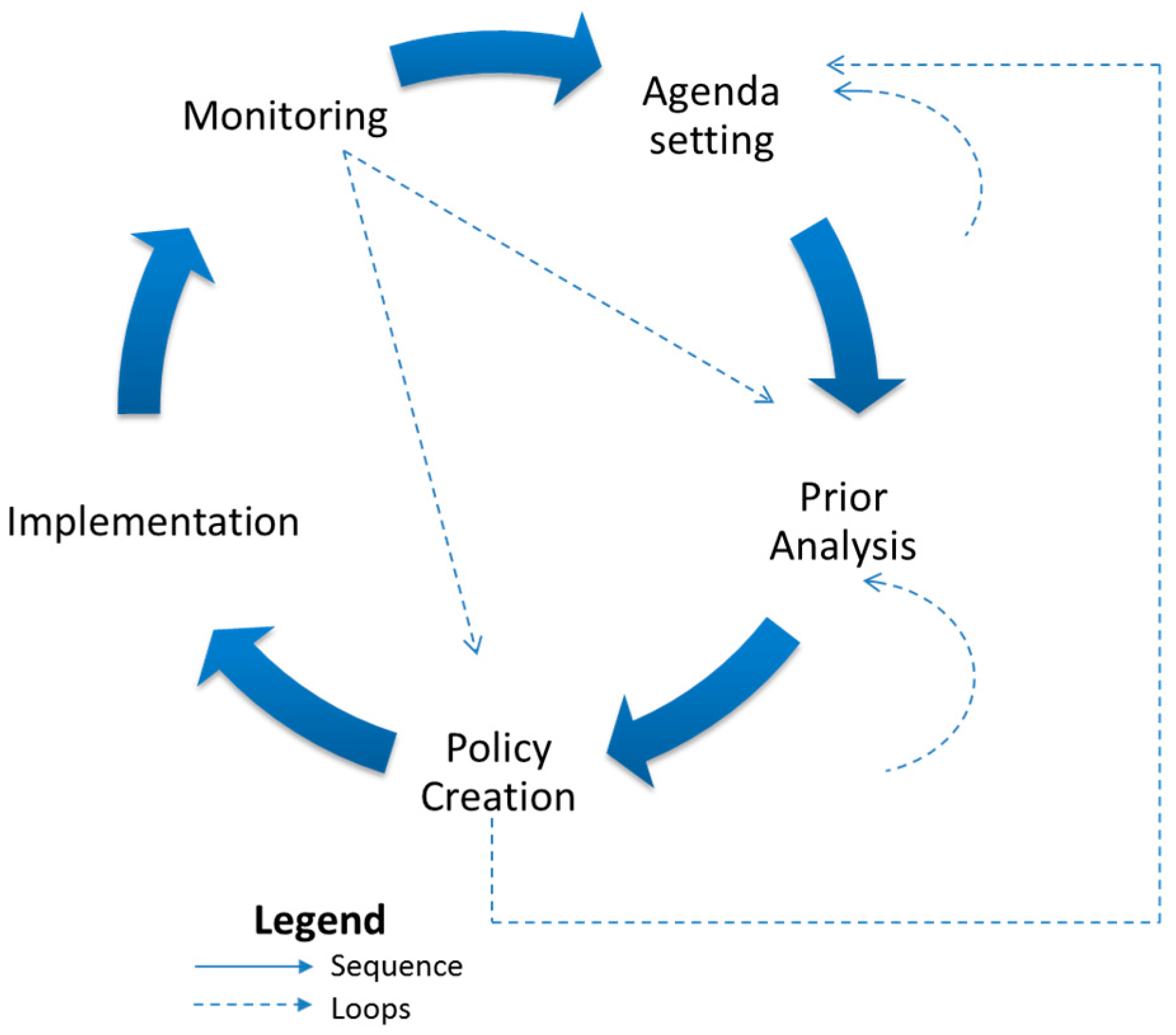
Characteristics of Policy Process
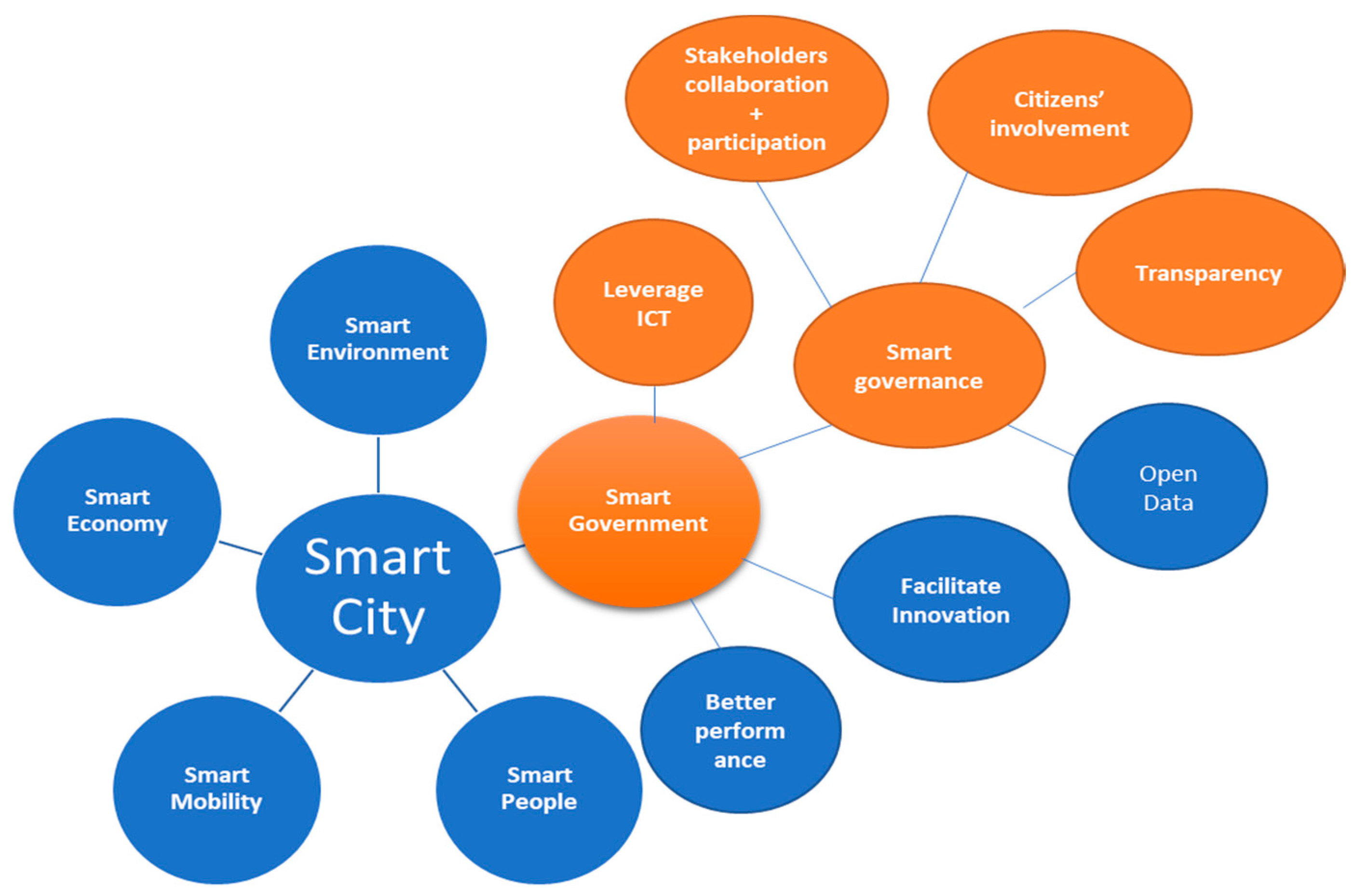
2.2.2. Smart City Concepts
- (a).
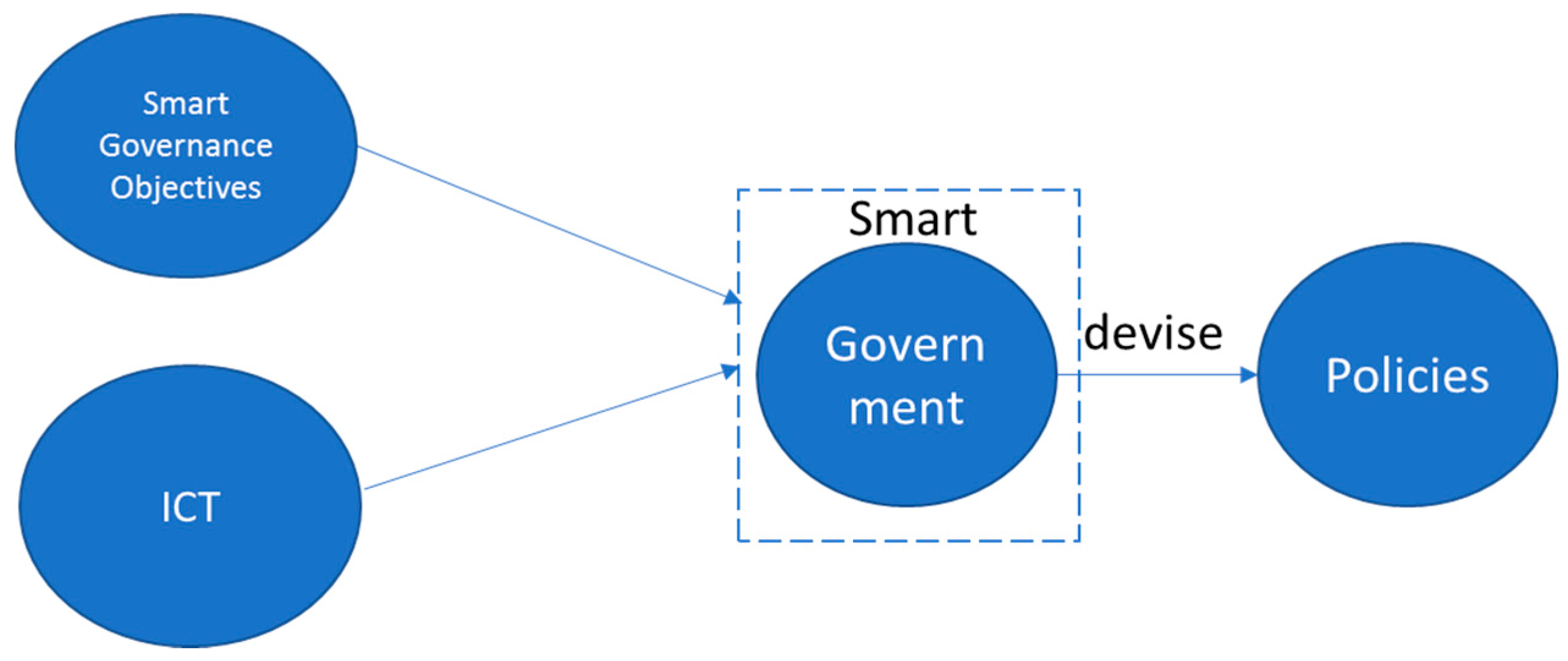
- Among many definitions of smart governance, we employ the description by Scholl [6] i.e., that smart governance serves as a foundation for smart government and fosters stakeholders’ participation and collaboration.
- (b).
- For smart government, we also use the description of Scholl [6] i.e., the use of ICT by government to manage and implement policies and use of smart governance principles for conceptualising smart government.
- (c).
- Our research proposes a solution in the context of smart cities. However, as noted earlier at present there exists no standard definition of a smart city and several descriptions fall under this [2]. For our work we focus on smart government, which employs ICT and smart governance objectives, thus providing a solution in the smart cities context.
2.3. Policy-Making Process in Smart Cities
2.4. Scope of Our Research
- (i).
- Policies are devised at various government levels. Our work is limited to local councils (also called local government) that operate at the city level.
- (ii).
- Our research focuses on smart government and smart governance aspects of smart cities.
3. Assessing the Suitability of Workflow Approach for Policy Provenance
3.1. Potential Workflow Approaches
3.2. A Critical Analysis of Workflow Approaches
4. The Proposed Network-Based Approach
4.1. The Rationale for a Network-Based Approach for Tracking Policy Cycle
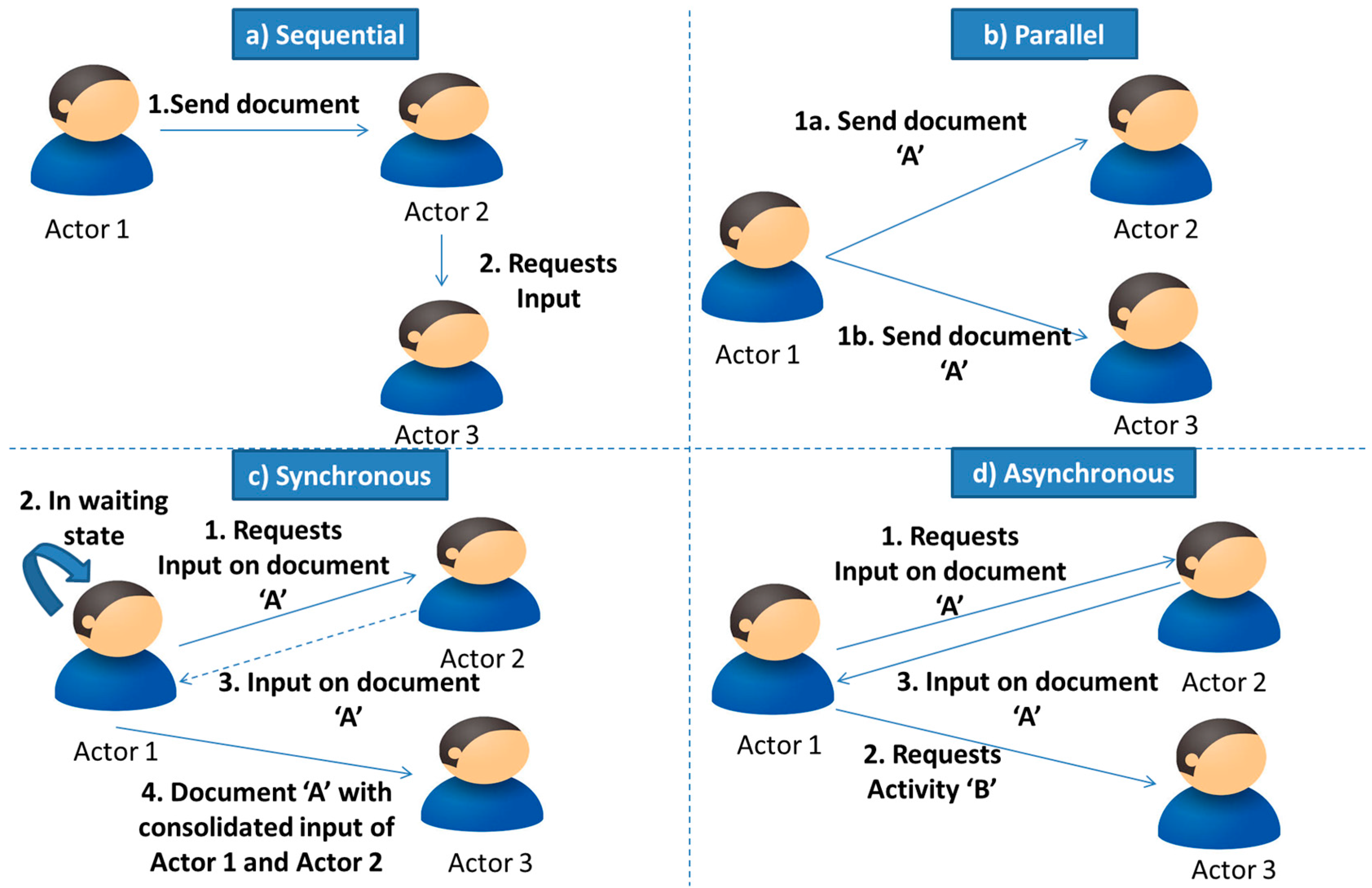
4.2. Network-Based Approach
The Effectiveness of the Proposed Network Based Approach
4.3. The Known Shortcomings of the Proposed Network-Based Approach
4.4. Goal-Based Approach
4.4.1. The Rationale or Using a Goal-Based Approach
4.4.2. Goal-Based Approach for Structuring a Policy-Making Process
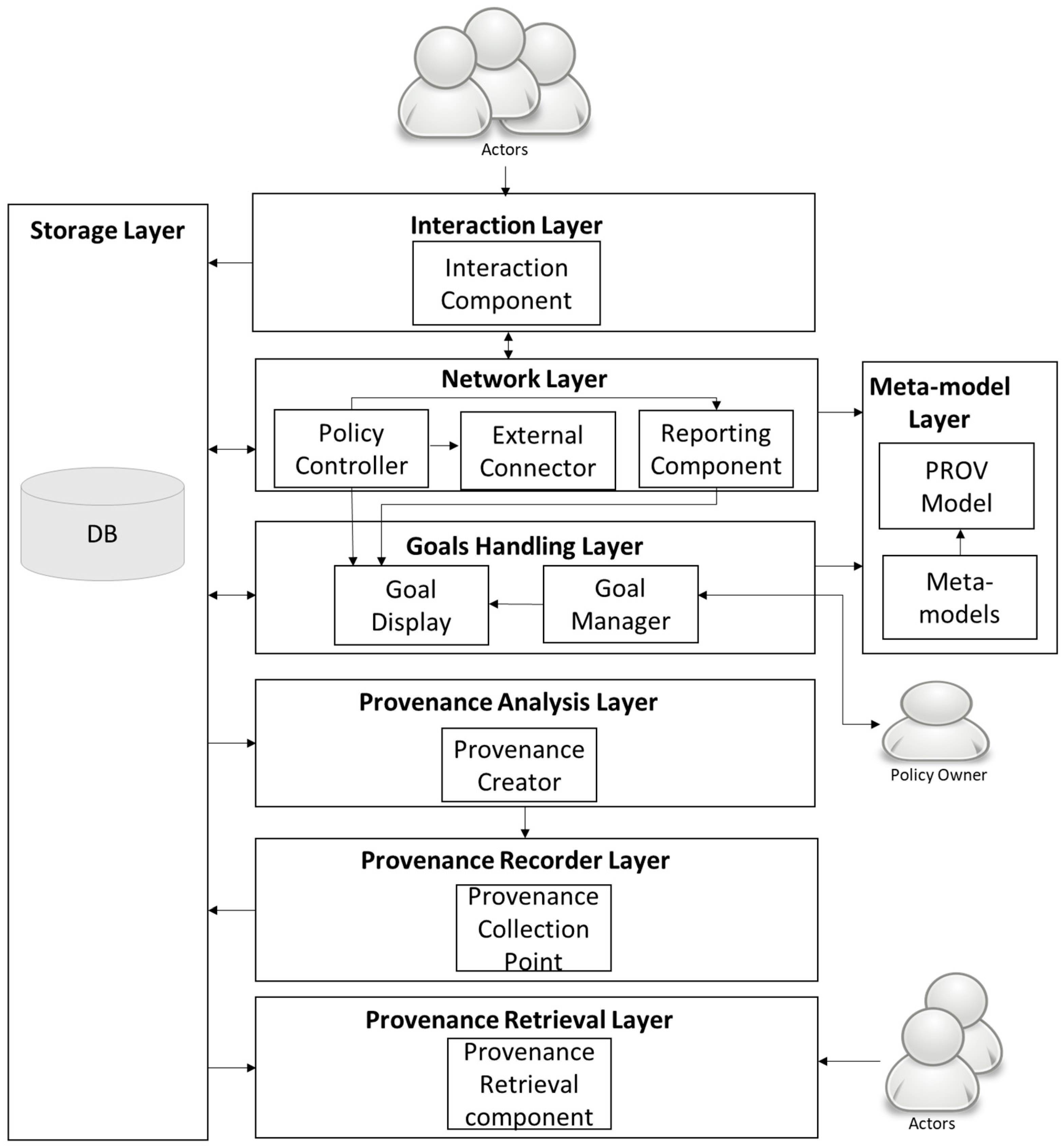
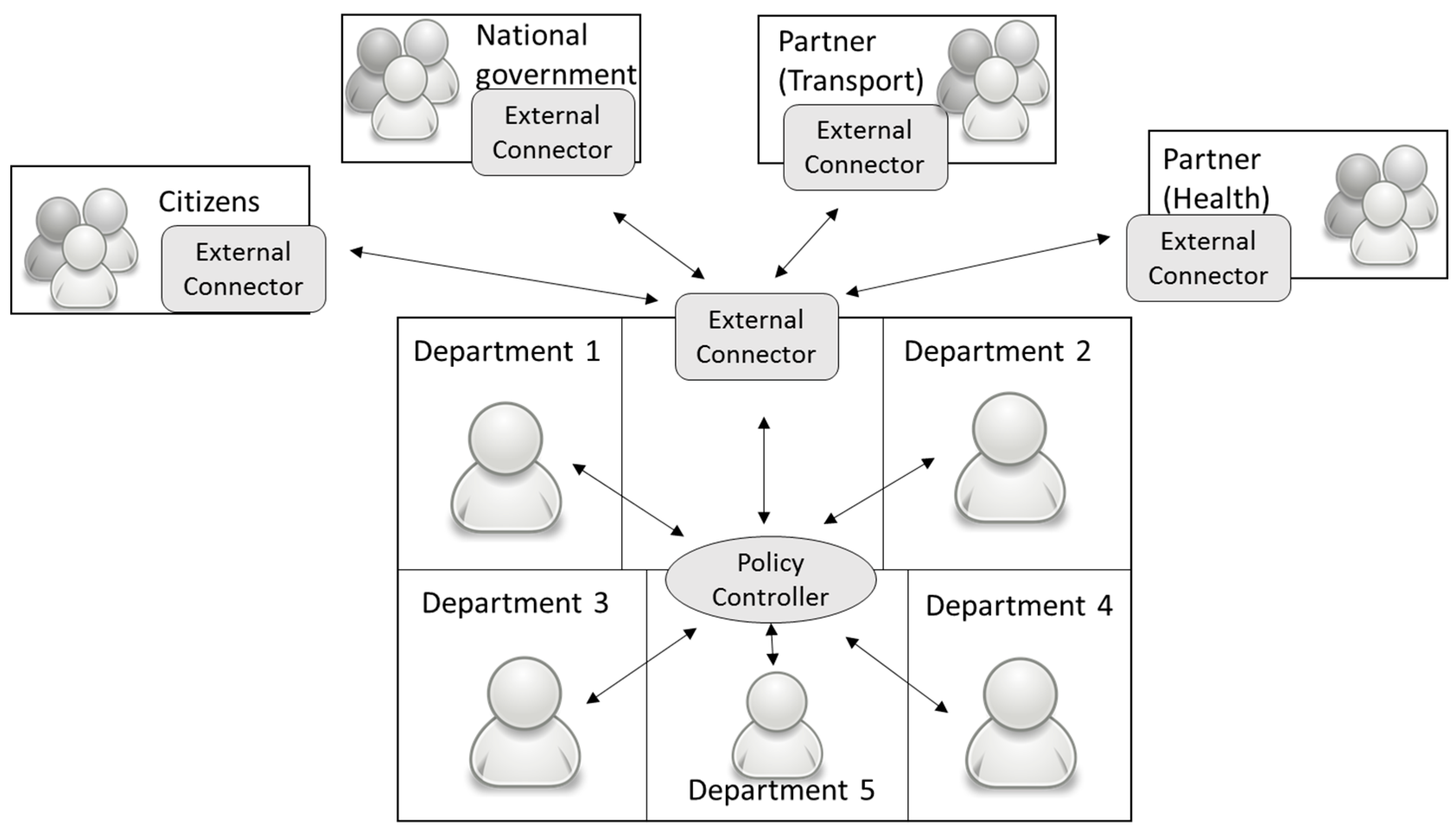
5. System Architecture
5.1. Working of the Architecture
- (i)
- the Goal Handling Layer implements the goal-based approach
- (ii)
- the Network layer implements the network approach
- (iii)
- the Interaction layer provides the interface with the actors
- (iv)
- the meta-model layer provides all details regarding the process, data, structure, provenance details. This layer uses the W3C PROV model [50] to specify the structure of the provenance information
- (v)
- Provenance analysis layer creates the provenance using tokens and as per meta-model layer
- (vi)
- Provenance recorder layer records the provenance
- (vii)
- Provenance Retrieval Layer is responsible for retrieval and display of provenance and
- (viii)
- Storage Layer that stores data and provenance (which we call as data store and provenance store). This layer is used by all layers either for storing or for retrieval of data.
5.1.1. Goal Handling Layer
5.1.2. Interaction Layer
5.1.3. Network Layer
5.1.4. Other Layers in the Architecture
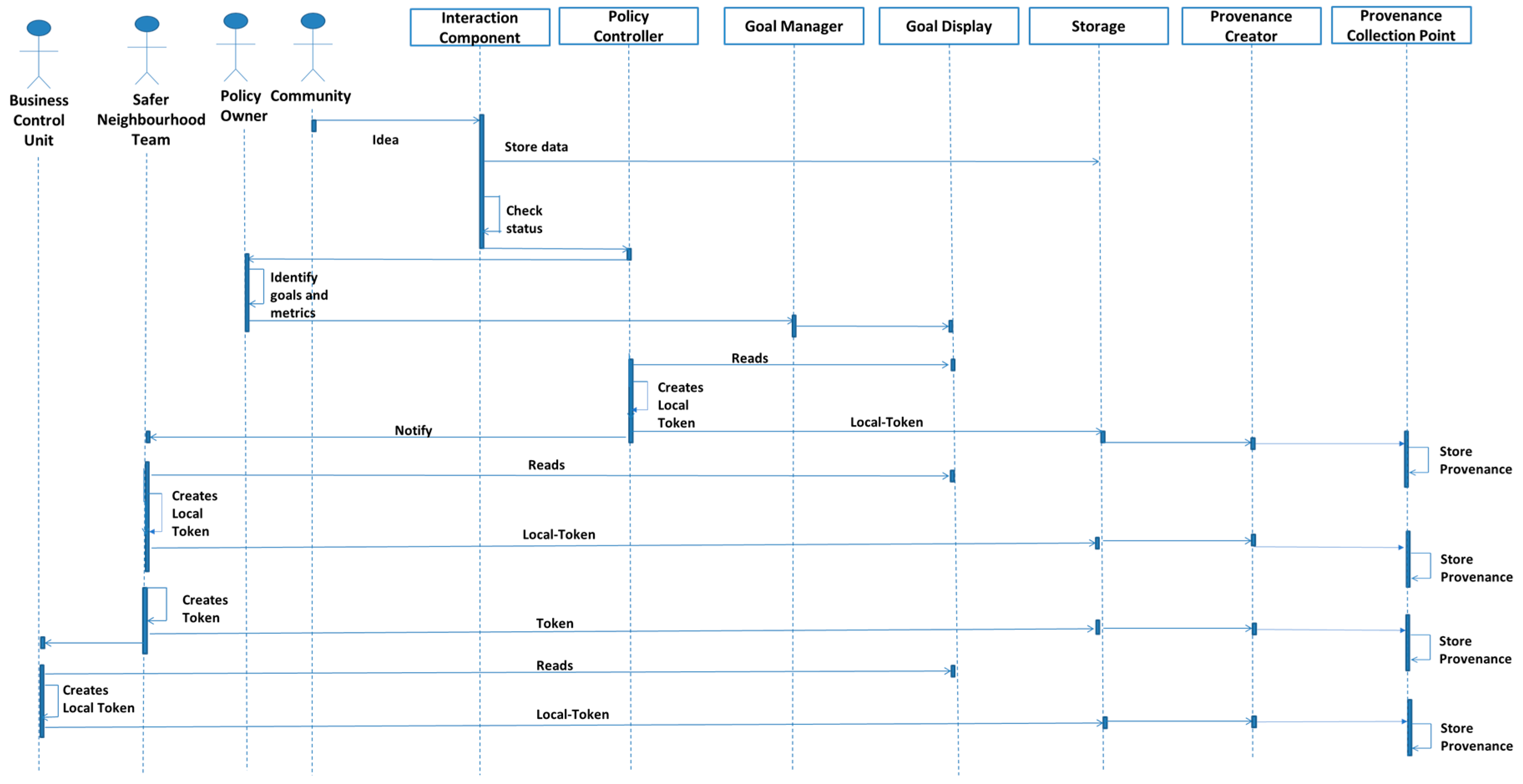
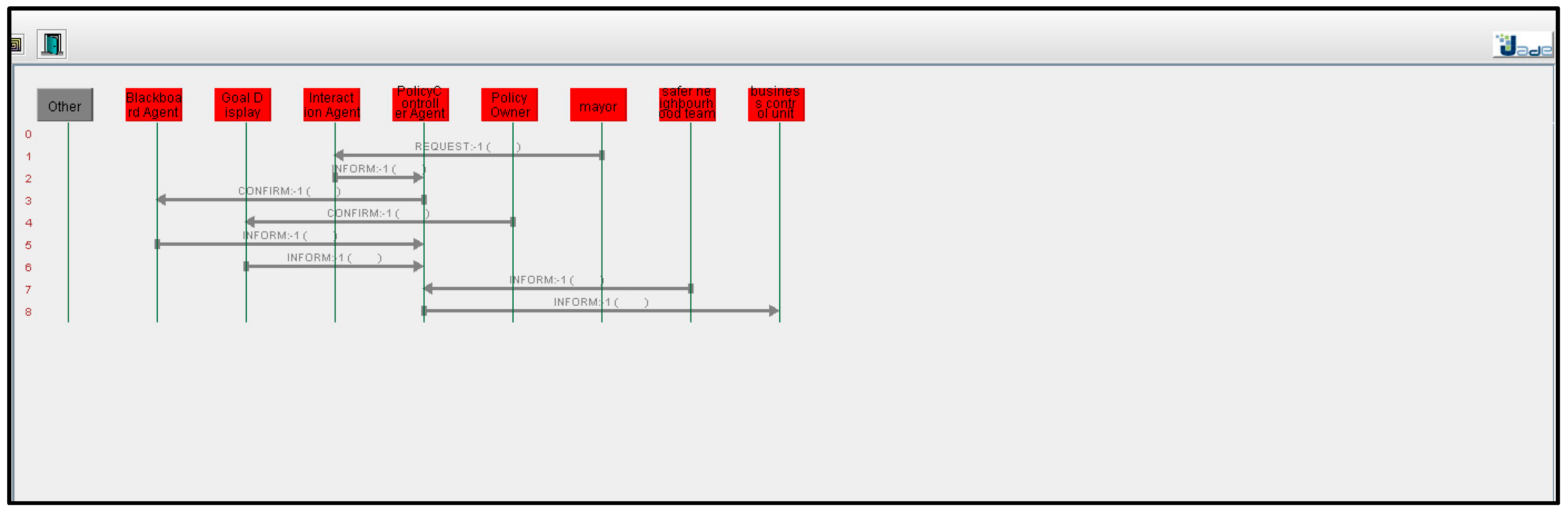
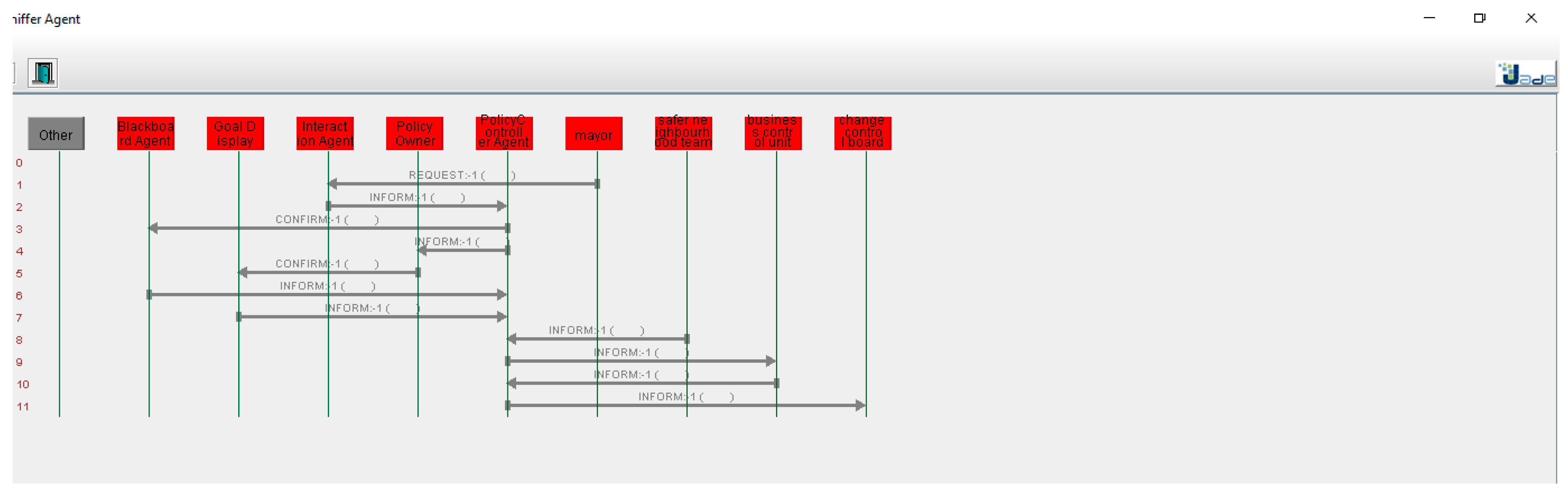
5.2. Example to Demonstrate Functioning
6. Implementation Approach
7. Conclusions and Future Research Directions
Author Contributions
Conflicts of Interest
References
- Harrison, C.; Donnelly, I.A. A theory of smart cities. In Proceedings of the 55th Annual Meeting of the International Society for the Systems Sciences, Hull, UK, 17–22 July 2011. [Google Scholar]
- Nam, T.; Pardo, T.A. Conceptualizing smart city with dimensions of technology, people, and institutions. In Proceedings of the 12th Annual International Conference on Digital Government Research, College Park, MD, USA, 12–15 June 2011; ACM Press: New York, NY, USA; pp. 282–291. [Google Scholar]
- Stevens, R.D.; Robinson, A.J.; Goble, C.A. myGrid: Personalised bioinformatics on the information grid. Bioinformatics 2003, 19, 302–304. [Google Scholar] [CrossRef]
- Angelidou, M. Smart city policies: A spatial approach. Cities 2014, 41, S3–S11. [Google Scholar] [CrossRef]
- Mellouli, S.; Luna-Reyes, L.F.; Zhang, J. Smart government, citizen participation and open data. Inf. Polity 2014, 19, 1–4. [Google Scholar]
- Scholl, H.J.; Scholl, M.C. Smart Governance: A Roadmap for Research and Practice. In Proceedings of the iConference 2014, Berlin, Germany, 4–7 March 2014; pp. 163–176. [Google Scholar]
- Rodríguez-Bolívar, M.P. Smart Cities: Big Cities, Complex Governance? In Transforming City Governments for Successful Smart Cities; Rodríguez Bolívar, M.P., Ed.; Springer International Publishing: New York, NY, USA, 2015; pp. 1–8. [Google Scholar]
- Nam, T.; Pardo, T.A. The changing face of a city government: A case study of Philly311. Gov. Inf. Q. 2014, 31, S1–S9. [Google Scholar] [CrossRef]
- Sindhu, U.; Balaouras, S.; Dines, R.A.; Hayes, N.M.; Nelson, L. Helping CIOs Understand “Smart City” Initiatives: Defining the Smart City, Its Drivers, and the Role of the CIO; Forrester Research: Cambridge, MA, USA, 2010. [Google Scholar]
- Harsh, A.; Ichalkaranje, N. Transforming e-Government to Smart Government: A South Australian Perspective. In Intelligent Computing, Communication and Devices; Springer: New Delhi, India, 2015; pp. 9–16. [Google Scholar]
- Sajjad, F. An Analytical Framework for Workflow Technology Adoption in Local Government Authorities; Brunel Business School, Brunel University: London, UK, 2014. [Google Scholar]
- Meijer, A.; Bolívar, M.P.R. Governing the smart city: A review of the literature on smart urban governance. Int. Rev. Adm. Sci. 2016, 82, 392–408. [Google Scholar] [CrossRef]
- Höchtl, J.; Parycek, P.; Schöllhammer, R. Big data in the policy cycle: Policy decision making in the digital era. J. Org. Comput. Electron. Commer. 2016, 26, 147–169. [Google Scholar] [CrossRef]
- Van der Aalst, W.M.P. Process Mining: Discovery, Conformance and Enhancement of Business Processes, 1st ed.; Springer: New York, NY, USA, 2011. [Google Scholar]
- Javed, B.; Khan, Z.; McClatchey, R. A Network-based Approach to Capture Provenance of a Policy-making Process. In Proceedings of the 21st International Database Engineering & Applications Symposium, Bristol, UK, 12–14 July 2017. [Google Scholar]
- Kjær, A.M. Governance; Polity Press: Cambridge, UK, 2004. [Google Scholar]
- Rafal, D. Agent-Based Modeling and Simulation of Species Formation Processes, Multi-Agent Systems—Modeling, Interactions, Simulations and Case Studies; Faisal, A., Ed.; InTech: London, UK, 2011. [Google Scholar]
- Tsohou, A.; Lee, H.; Al-Yafi, K.; Weerakkody, V.; El-Haddadeh, R.; Irani, Z.; Ko, A.; Medeni, T.D.; Campos, L.M. Supporting Public Policy Making Processes with Workflow Technology: Lessons Learned From Cases in Four European Countries. Int. J. Electron. Gov. Res. (IJEGR) 2012, 8, 63–77. [Google Scholar] [CrossRef]
- Macintosh, A. Characterizing e-participation in policy-making. In Proceedings of the 37th Hawaii International Conference on System Sciences, Big Island, HI, USA, 5–8 January 2004. [Google Scholar]
- Khan, Z.; Ludlow, D.; Loibl, W.; Soomro, K. ICT enabled participatory urban planning and policy development: The UrbanAPI project. Transform. Gov. People Process Policy 2014, 8, 205–229. [Google Scholar] [CrossRef]
- Sonntagbauer, S.; Sonntagbauer, P.; Nazemi, K.; Burkhardt, D. The FUPOL policy lifecycle. In Public Affairs and Administration: Concepts, Methodologies, Tools, and Applications; Information Resources Management Association, Ed.; IGI Global: Hershey, PA, USA, 2015; p. 158. [Google Scholar]
- Hallsworth, M.; Parker, S.; Rutter, J. Policy Making in the Real World: Evidence and Analysis; Institute for Government: London, UK, 2011. [Google Scholar]
- Gong, Y.; Janssen, M. The Impact of Social Business Process Management on Policy-making in e-Government. In Proceedings of the 50th Hawaii International Conference on System Sciences, Waikoloa Village, HI, USA, 4–7 January 2017. [Google Scholar]
- Khan, Z.; Dambruch, J.; Peters-Anders, J.; Sackl, A.; Strasser, A.; Fröhlich, P.; Templer, S.; Soomro, K. Developing knowledge-based citizen participation platform to support Smart City decision making: The Smarticipate case study. Information 2017, 8, 47. [Google Scholar] [CrossRef]
- Gil-Garcia, J.R.; Zhang, J.; Puron-Cid, G. Conceptualizing smartness in government: An integrative and multi-dimensional view. Gov. Inf. Q. 2016, 33, 524–534. [Google Scholar] [CrossRef]
- Barns, S. Smart Cities and Urban Data Platforms: Designing Interfaces for Smart Governance. City Cult. Soc. 2017. [Google Scholar] [CrossRef]
- British Standard Institute. PAS 181: 2014 Smart City Framework—Guide to Establishing Strategies for Smart Cities and Communities; British Standard Institute: London, UK, 2014; Available online: http://www.bsigroup.com/en-GB/smart-cities/Smart-Cities-Standards-and-Publication/PAS-181-smart-cities-framework/ (accessed on 30 November 2017).
- Kourtit, K.; Nijkamp, P.; Steenbruggen, J. The significance of digital data systems for smart city policy. Socio-Econ. Plan. Sci. 2017, 58, 13–21. [Google Scholar] [CrossRef]
- Huth, C.; Erdmann, I.; Nastansky, L. Using Process Knowledge from the Participative Design and Practical Operation of Ad-hoc Processes for the Design of Structured Workflows. In Proceedings of the Thirty-Fourth Annual Hawaii International Conference on System Sciences, Maui, HI, USA, 3–6 January 2001; Computer Society Press: Washington, DC, USA, 2001. [Google Scholar]
- Dustdar, S.; Hoffmann, T.; Van der Aalst, W. Mining of ad-hoc business processes with TeamLog. Data Knowl. Eng. 2005, 55, 129–158. [Google Scholar] [CrossRef]
- Kiepuszewski, B.; Ter Hofstede, A.H.M.; Bussler, C.J. On structured workflow modelling. In Proceedings of the International Conference on Advanced Information Systems Engineering, Stockholm, Sweden, 5–9 June 2000; Springer: Berlin/Heidelberg, Germany, 2000; pp. 431–445. [Google Scholar]
- Voorhoeve, M.; Van der Aalst, W. Ad-hoc workflow: Problems and solutions. In Proceedings of the Eighth International Workshop on Database and Expert Systems Applications, Toulouse, France, 1–2 September 1997; pp. 36–40. [Google Scholar]
- Rito, S.A. A Blended Workflow Approach. In Lecture Notes in Business Information Processing, Proceedings of the Business Process Management Workshops, Ferrand, France, 29 August 2011; Daniel, F., Barkaoui, K., Dustdar, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 99. [Google Scholar]
- Object Management Group Business Process Model and Notation. Available online: http://www.bpmn.org/ (accessed on 22 November 2017).
- Web Services Business Process Execution Language Version 2.0. Available online: http://docs.oasis-open.org/wsbpel/2.0/OS/wsbpel-v2.0-OS.html (accessed on 22 November 2017).
- Meng, J.; Helal, S.; Su, S. An ad-hoc workflow system architecture based on mobile agents and rule-based processing. In Proceedings of the 2000 International Conference on Artificial Intelligence (ICAI2000), Las Vegas, NV, USA, 12–15 July 2000; pp. 245–251. [Google Scholar]
- Dustdar, S. Caramba—A process-aware collaboration system supporting ad-hoc and collaborative processes in virtual teams. Distrib. Parallel Database 2004, 15, 45–66. [Google Scholar] [CrossRef]
- Huth, C.; Smolnik, S.; Nastansky, L. Applying topic maps to ad-hoc workflows for semantic associative navigation in process networks. In Proceedings of the Seventh International Workshop on Groupware, Darmstadt, Germany, 6–8 September 2001; pp. 44–49. [Google Scholar]
- Siebert, R. An open architecture for adaptive workflow management systems. J. Integr. Des. Process Sci. 1999, 3, 29–41. [Google Scholar]
- Minor, M.; Bergmann, R.; Görg, S. Case-based adaptation of workflows. Inf. Syst. 2014, 40, 142–152. [Google Scholar] [CrossRef]
- Kammer, P.J.; Bolcer, G.A.; Taylor, R.N.; Hitomi, A.S.; Bergman, M. Techniques for supporting dynamic and adaptive workflow. Comput. Support. Coop. Work (CSCW) 2000, 9, 269–292. [Google Scholar] [CrossRef]
- Allen, M.D.; Chapman, A.; Blaustein, B.; Mak, L. What do we do now? Workflows for an unpredictable world. Future Gener. Comput. Syst. 2015, 42, 1–10. [Google Scholar] [CrossRef]
- Sui, Q.; Yang, D.Q.; Wang, T.J. Easy flow: New generation business process model. In Advances in Web and Network Technologies, and Information Management; Springer: Berlin/Heidelberg, Germany, 2009; pp. 138–147. [Google Scholar]
- Harrison-Broninski, K. Human Interactions: The Heart and Soul of Business Process Management: How People Reallly Work and How They Can Be Helped to Work Better; Meghan-Kiffer Press: Tampa, FL, USA, 2005. [Google Scholar]
- De Man, H. Case Management: A Review of Modeling Approaches; BPTrends, January 2009. Available online: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.225.9160&rep=rep1&type=pdf (accessed on 4 January 2018).
- WebSphere® Process Server, 6.2. Dynamic Human Workflows—Introduction and Best Practices; IBM Corporation: Armonk, NY, USA, 2009.
- Peter, K.; Kawalek, P. Goal-based business process models: Creation and evaluation. Bus. Process Manag. J. 1997, 3, 17–38. [Google Scholar]
- Beate, L.; Korherr, B. A uml 2 profile for business process modelling. In Proceedings of the International Conference on Conceptual Modeling, Klagenfurt, Austria, 24–28 October 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 85–96. [Google Scholar]
- Javed, B.; Khan, Z.; McClatchey, R. Using a Model-driven Approach in Building a Provenance Framework for Tracking Policy-making Processes in Smart Cities. In Proceedings of the 21st International Database Engineering & Applications Symposium, Bristol, UK, 12–14 July 2017. [Google Scholar]
- PROV. Available online: https://www.w3.org/TR/prov-primer/ (accessed on 20 August 2017).
- JAVA Agent DEvelopment Framework. Available online: http://jade.tilab.com/ (accessed on 26 November 2017).
- Sycara, K. Multiagent Systems. AI Mag. 1998, 19, 79. [Google Scholar]



| Challenges | Complex Task Specification | Non-Deterministic | Knowledge Intensive | Large No. of Stakeholders (Including Citizens) | Different Policy Processes |
|---|---|---|---|---|---|
| Complex Task Specification | √ | √ | √ | √ | |
| Non-deterministic | √ | ||||
| Knowledge Intensive | |||||
| Large No. of Stakeholders (including citizens) | |||||
| Different Policy Processes | √ | ||||
| Unpredictable | √ | √ | √ | √ | √ |
| Lengthy | √ |
| Challenges (From Section 2.2.1) | Description |
|---|---|
| Complex Task Specification | Network-based approach does not require pre-identification of activities and their sequence. Tokens are created at run-time which contain details of task specified by the actor (Table 1 shows that knowledge-intensive policy-making nature inputs in the challenge of tasks specification). Thus, our approach considers human input in task specification at the run-time. Actors specify the tasks as per policy demands which addresses challenge associated with pre-defining a process. |
| Non-deterministic | Our approach does not consider construction and restructuring of process to guide human action. In our approach, humans guide the process (as non-determinism is due to knowledge-intensive nature as shown in Table 1) which is constructed on the fly from the collected provenance. |
| Knowledge-intensive | No process is defined beforehand but human experience guides the process. Tasks (tokens) are created by policy-makers and routed to the concerned actor. The policy-makers analyses a given piece of information and knowledge at hand to define the next right action. |
| Large no. of stakeholder | In our approach, tokens are carrier of information (this uplifts the challenge of defining a process that spans councils and organisations that are external to the council). Similar to IP packet switching, tokens carry information from one actor to another. While communicating with external authority, the local council keep record of who has been communicated with and from whom a response is required. No set defined process facilitates inclusion of several diverse stakeholders during the policy formation. Furthermore, this also promotes smart governance facets of including diverse stakeholders and citizens during policy-making. |
| Different policy processes | Our proposed approach uplifts this overhead by not considering the process based approach and by taking into account human knowledge as a foundation for policy creation. |
| Unpredictable (difficult to orchestrate process beforehand) | Network-based approach is not process-based thus addressing the challenge of process orchestration. However, policy process reconstruction from provenance data requires efficient algorithms. |
| Lengthy process | Our system maintains state of all policies by tracking activities. These states help reinstate the policy process. |
| Policy Process Characteristics (From Section 2.2.1) | Our Proposed Approach Solution |
|---|---|
| Characteristic i | The proposed network approach facilitates communication and collaboration with other stakeholders using a packet like communication. As policy process is largely manual therefore we assume in our approach that someone will have to enter provenance data into the system These details will then automatically be routed (by policy controller) to other stakeholders using the destination address in the packet. All the tokens generated as part of the process are saved in a database which provides an evidence of a process that was executed. All the information that is generated or processed (such as documents) will be stored in a database. |
| Characteristic ii | Based on the human decision, the policy controller decides if policy process continues. |
| Characteristic iii | As process-centric approach is not considered in our proposed solution. Therefore, loops are also not pre-defined. In case loop back is required then as per policy demand, re-execution of previous phase/or certain activities will be carried out. |
| No. | Challenges of Network-Based Approach | Solution Provided by Goal-Based Approach |
|---|---|---|
| 1 | No process state monitoring in a system | Goals are identified for each phase of policy cycle. These goals guide the policy-makers to carry out the tasks towards goals’ fulfilment. |
| 2 | System or process execution is less transparent | Goal-based approach provides an overview of which goals have been satisfied and which goal is currently under execution. |
| 3 | Initiation and termination of policy cycle and its phases | For each goal initiation and termination is specified. |
| 4 | Artefacts and approval bodies involved in a process cannot be stated in an ad-hoc environment | In policy-making process, approvals at various points are required from the concerned authorities. Therefore, artefacts and approval bodies’ information (where required) is associated with each goal of a policy cycle. |
| 5 | Provenance query | Process for each goal will be created at run-time but activities involved in a process contain ID of goal which associates the process to the goals. For identifying a sequence of tasks, sequence numbers (similar to packets’ sequence number) are associated with tokens. Using this approach, provenance can be queried using a goal ID. |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Javed, B.; Khan, Z.; McClatchey, R. An Adaptable System to Support Provenance Management for the Public Policy-Making Process in Smart Cities. Informatics 2018, 5, 3. https://doi.org/10.3390/informatics5010003
Javed B, Khan Z, McClatchey R. An Adaptable System to Support Provenance Management for the Public Policy-Making Process in Smart Cities. Informatics. 2018; 5(1):3. https://doi.org/10.3390/informatics5010003
Chicago/Turabian StyleJaved, Barkha, Zaheer Khan, and Richard McClatchey. 2018. "An Adaptable System to Support Provenance Management for the Public Policy-Making Process in Smart Cities" Informatics 5, no. 1: 3. https://doi.org/10.3390/informatics5010003






