Dynamic Analysis and Audio Encryption Application in IoT of a Multi-Scroll Fractional-Order Memristive Hopfield Neural Network
Abstract
:1. Introduction
2. Description of the FMHNN
2.1. Caputo Fractional-Order Derivative and ADM
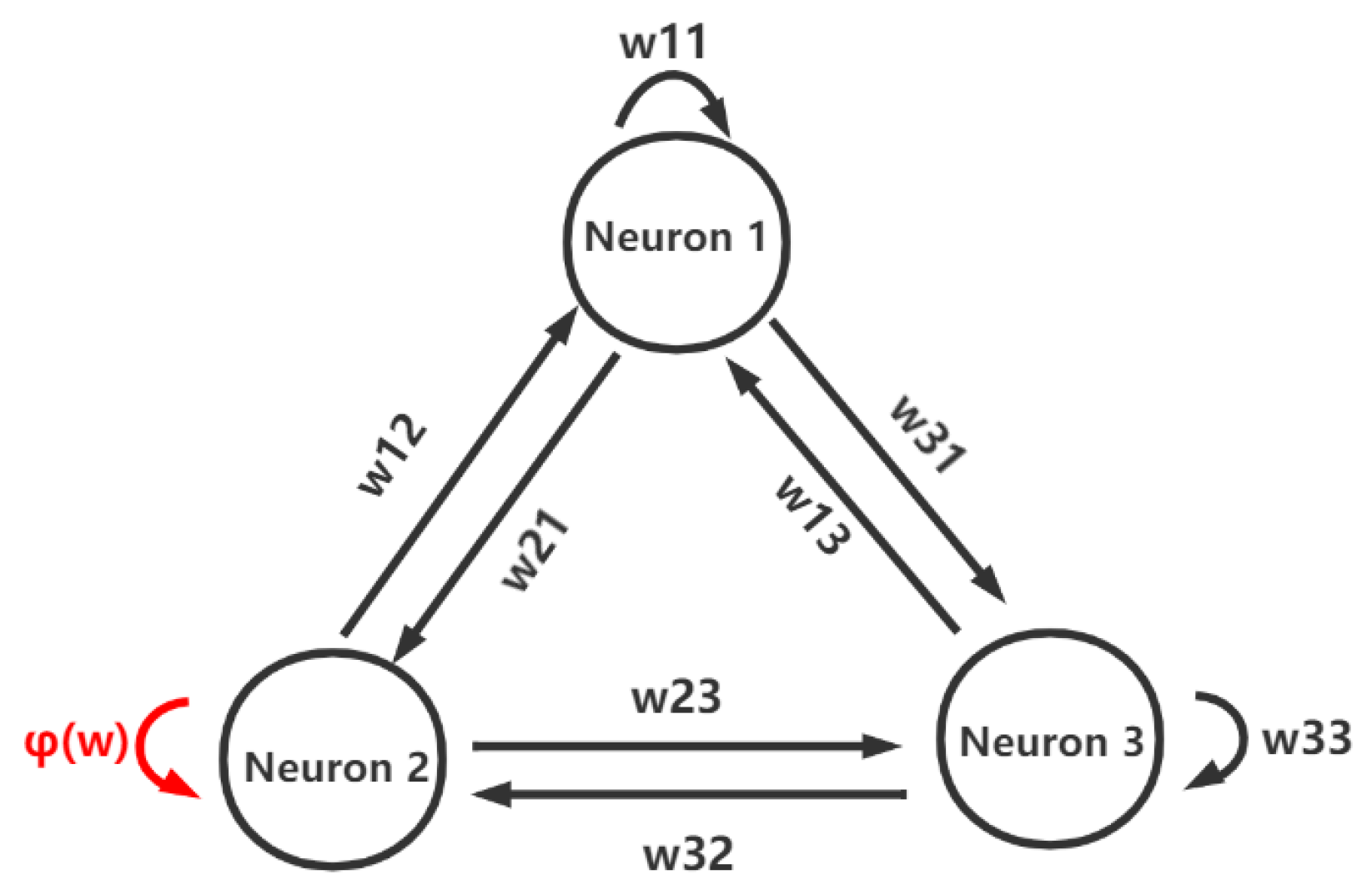
2.2. The FMHNN Model
3. Dynamics Analysis and Numerical Simulations
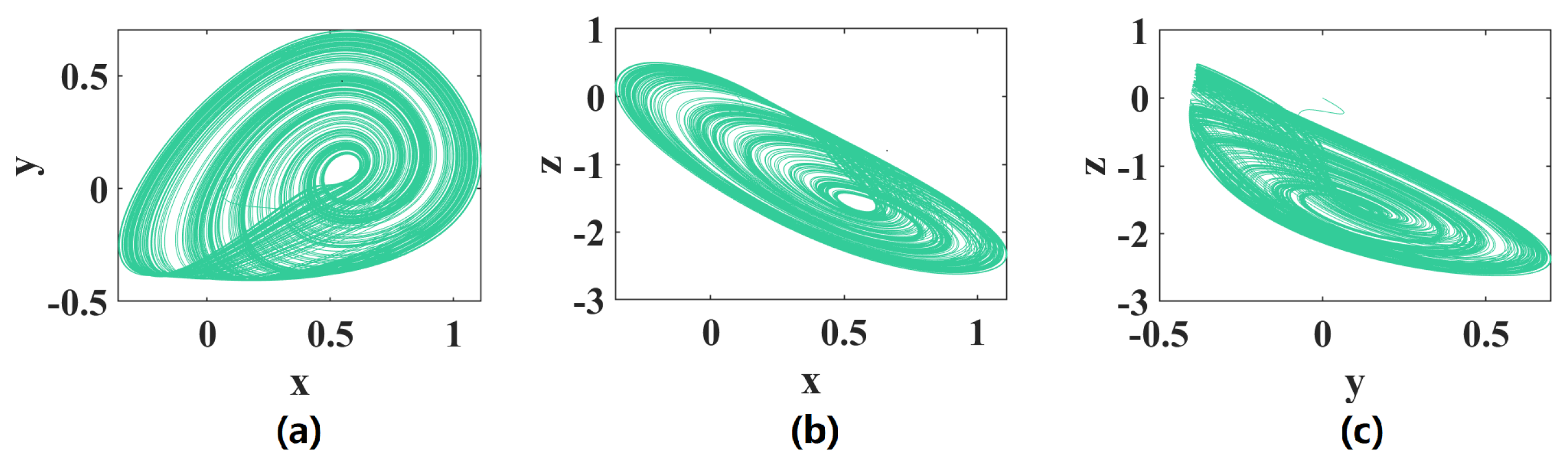
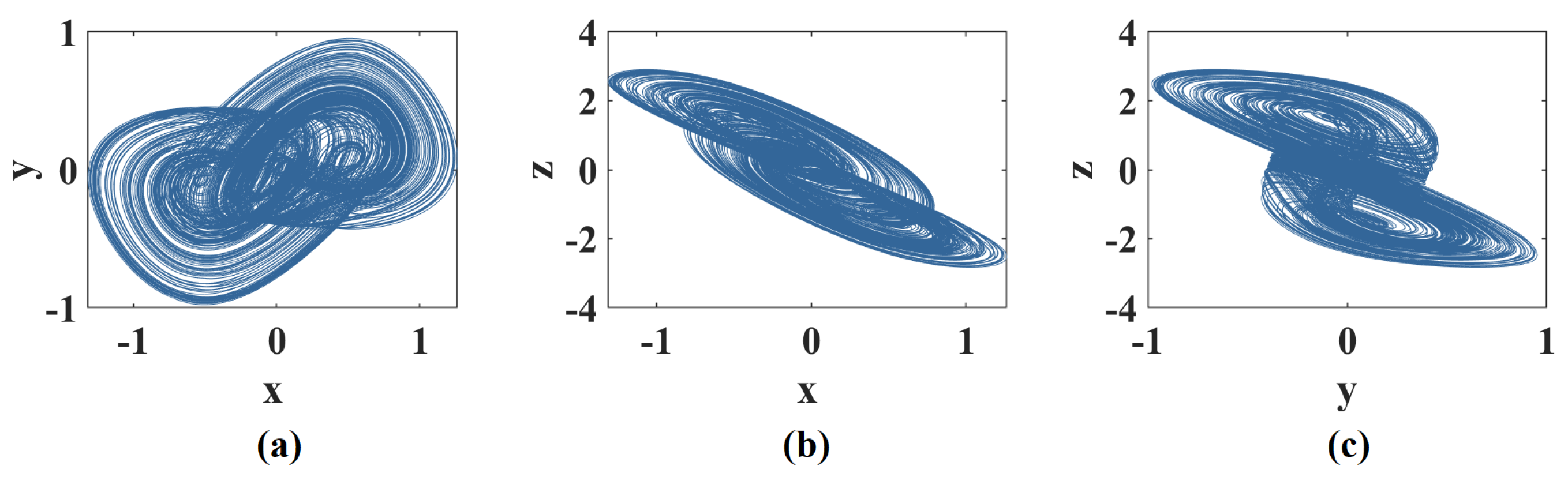
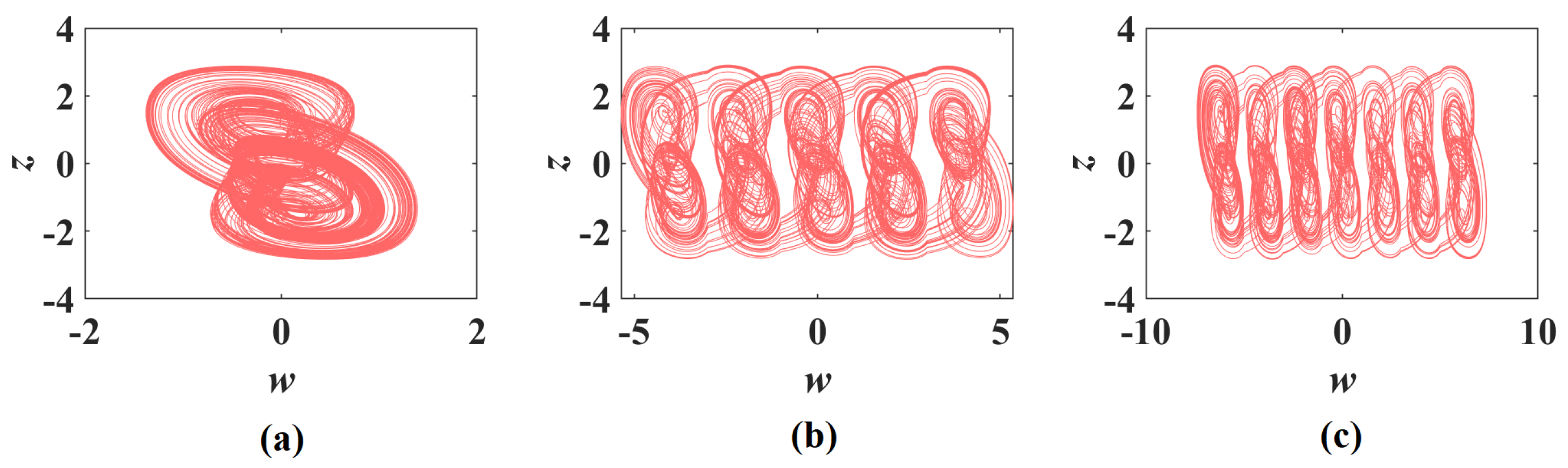
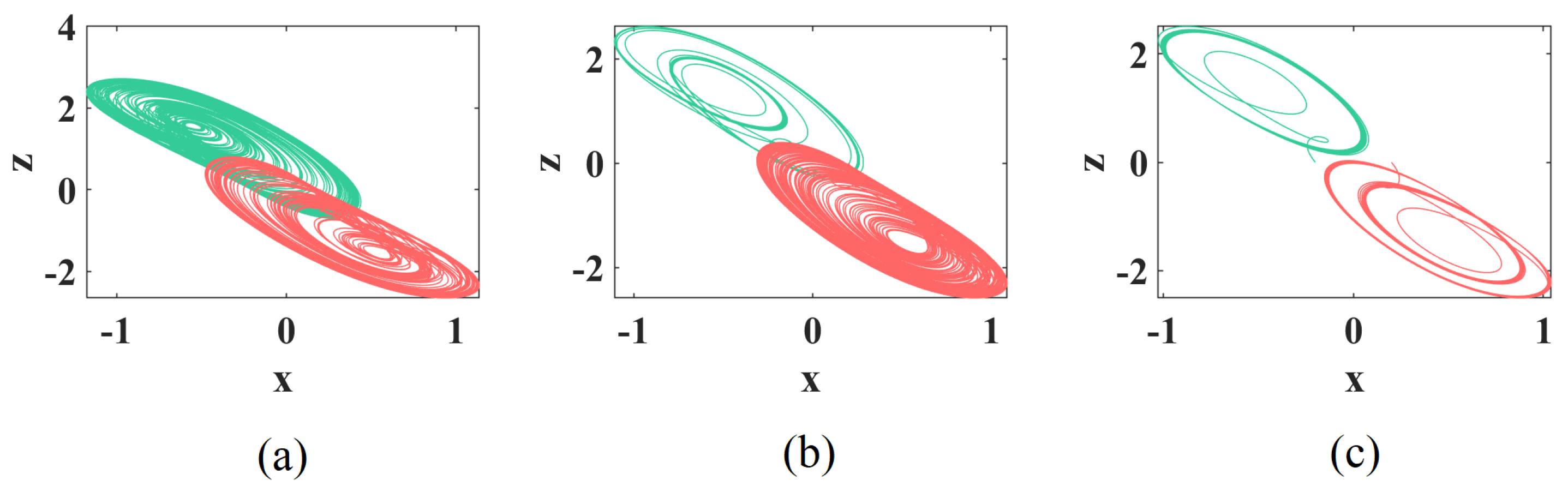
3.1. Phase Portraits of Multi-Scroll with Different Parameter
3.2. Bifurcation of FMHNN with Different Parameters
3.2.1. Bifurcation with Synaptic Coupling Strength k
3.2.2. Bifurcation with Different Order q
3.3. Multiple Coexisting Attractors and Basins of Attractor
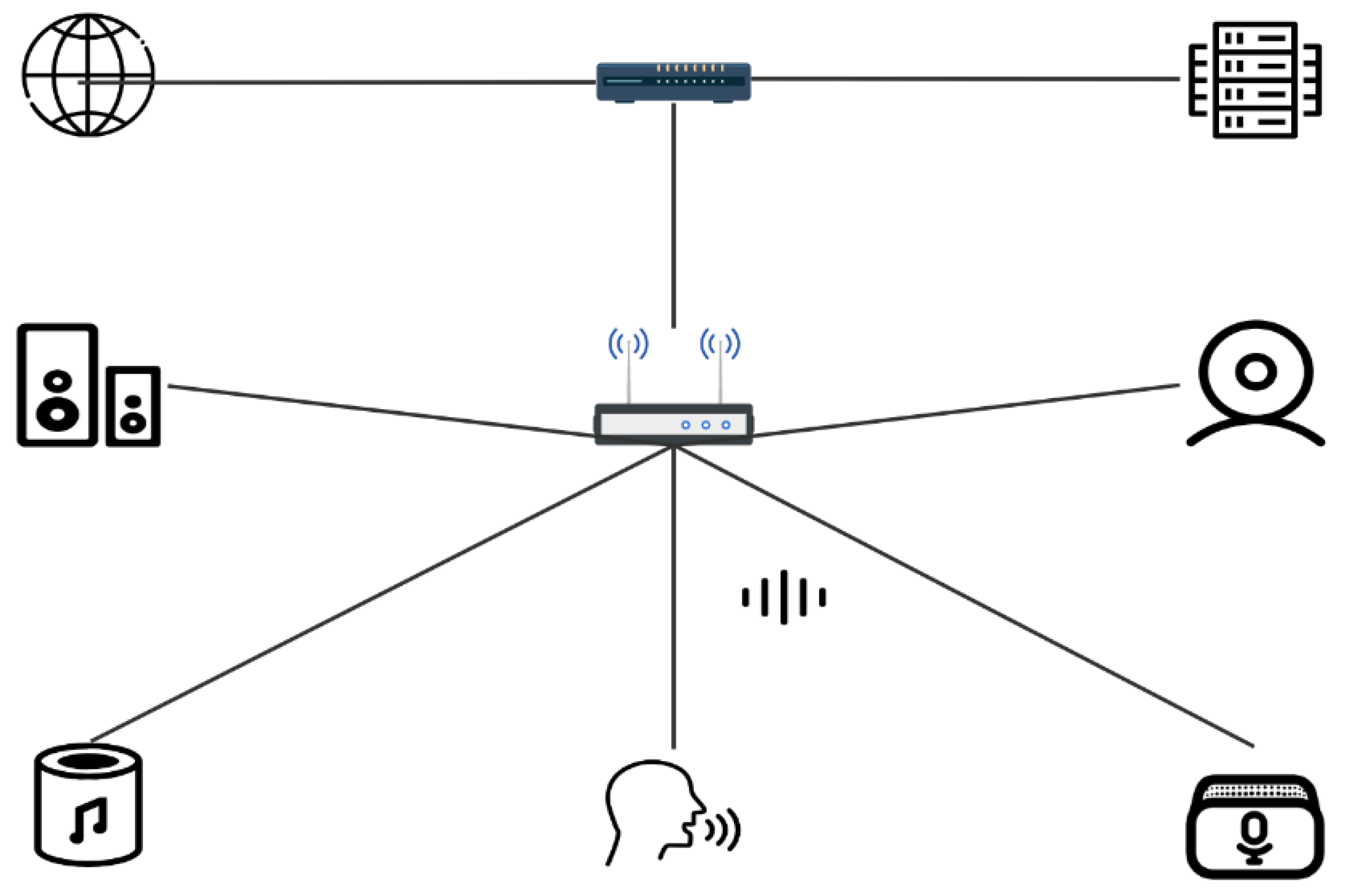
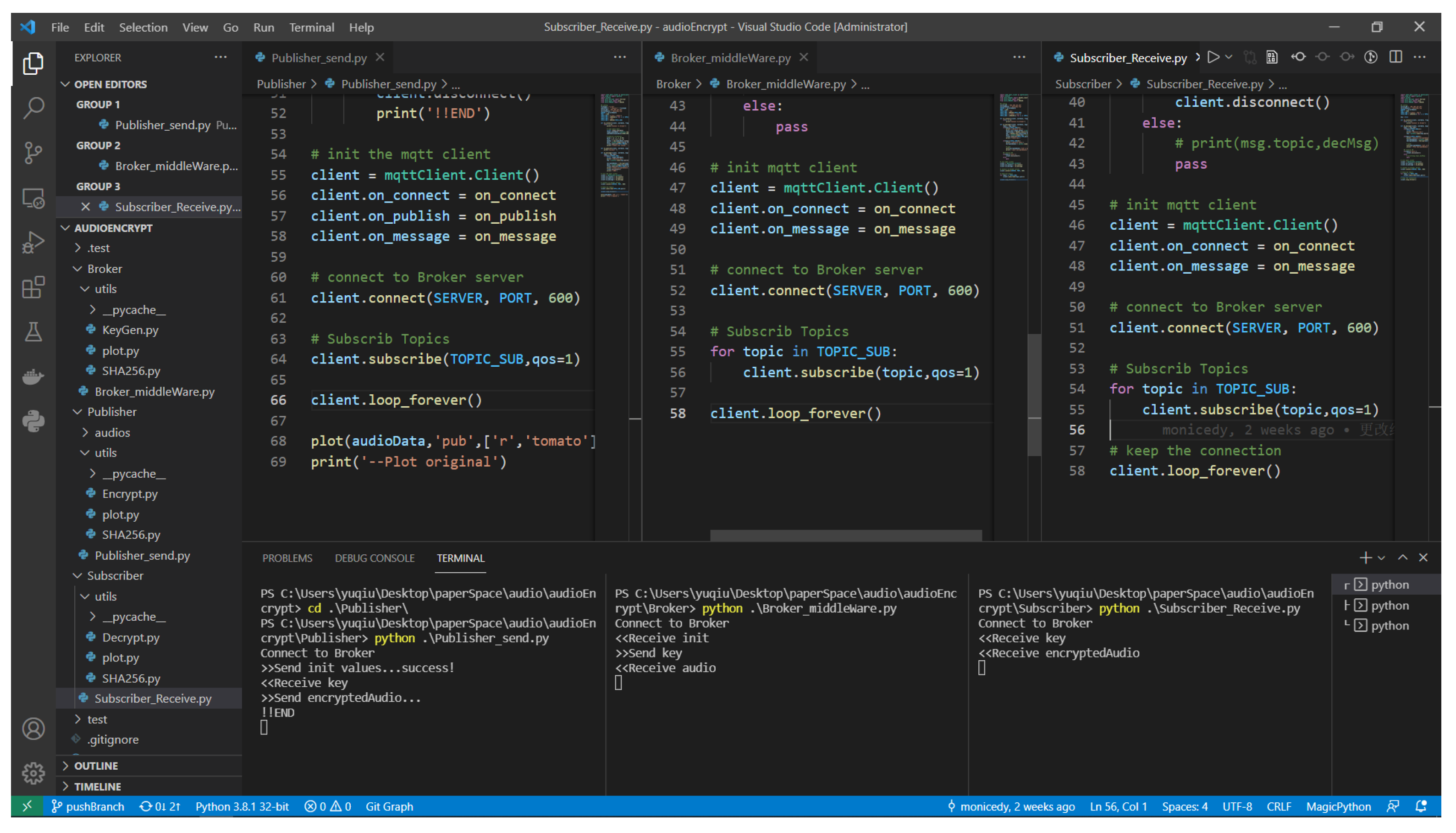
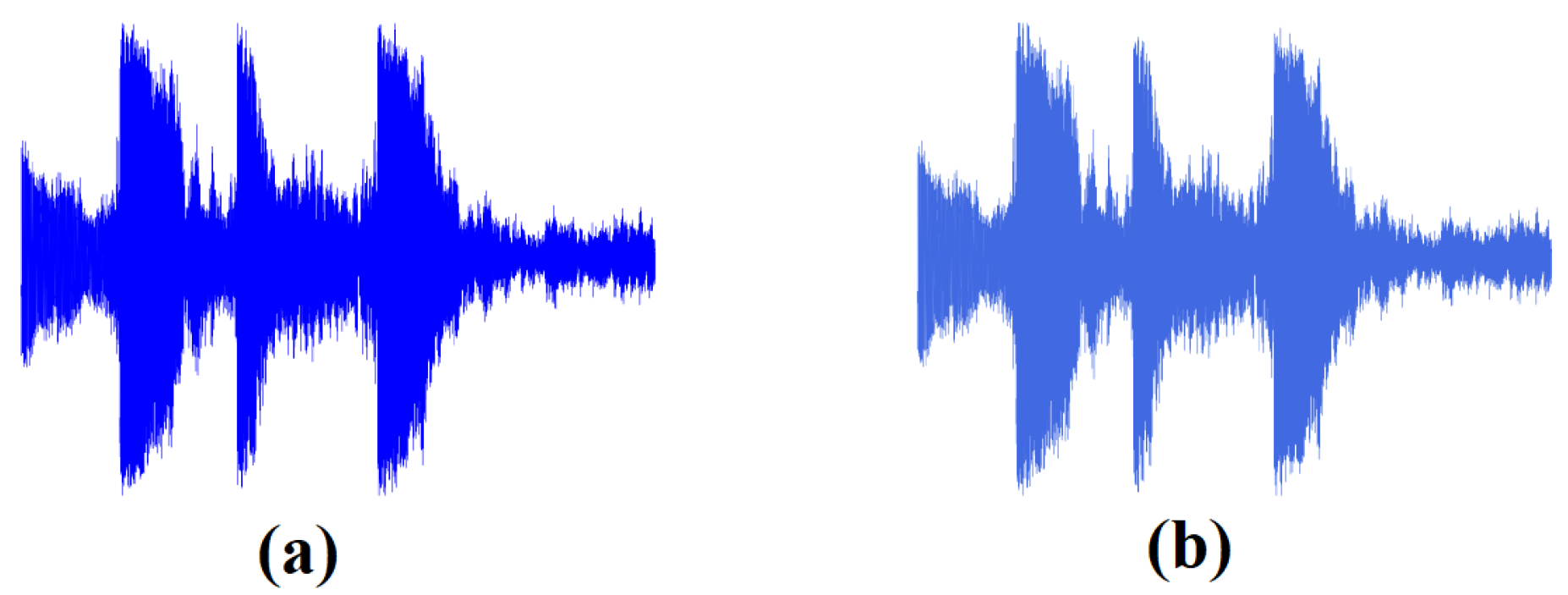
4. Audio Encryption Application in IoT under MQTT Protocol
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Yang, L.; Wang, C. Emotion model of associative memory possessing variable learning rates with time delay. Neurocomputing 2021, 460, 117–125. [Google Scholar] [CrossRef]
- Leung, K.S.; Jin, H.D.; Xu, Z.B. An expanding self-organizing neural network for the traveling salesman problem. Neurocomputing 2004, 62, 267–292. [Google Scholar] [CrossRef] [Green Version]
- Cheng, L.; Liu, W.; Hou, Z.G.; Yu, J.; Tan, M. Neural-network-based nonlinear model predictive control for piezoelectric actuators. IEEE Trans. Ind. Electron. 2015, 62, 7717–7727. [Google Scholar] [CrossRef]
- Yu, F.; Liu, L.; Xiao, L.; Li, K.; Cai, S. A robust and fixed-time zeroing neural dynamics for computing time-variant nonlinear equation using a novel nonlinear activation function. Neurocomputing 2019, 350, 108–116. [Google Scholar] [CrossRef]
- Wang, J.; Wu, Y.; He, S.; Sharma, P.K.; Yu, X.; Alfarraj, O.; Tolba, A. Lightweight Single Image Super-Resolution Convolution Neural Network in Portable Device. KSII Trans. Internet Inf. Syst. 2021, 15, 4065–4083. [Google Scholar]
- Deng, Z.; Zhu, Q.; He, P.; Zhang, D.; Luo, Y. A Saliency Detection and Gram Matrix Transform-Based Convolutional Neural Network for Image Emotion Classification. Secur. Commun. Netw. 2021, 2021, 6854586. [Google Scholar] [CrossRef]
- Long, M.; Zeng, Y. Detecting iris liveness with batch normalized convolutional neural network. CMC-Comput. Mater. Contin. 2019, 58, 493–504. [Google Scholar] [CrossRef]
- Gui, Y.; Zeng, G. Joint learning of visual and spatial features for edit propagation from a single image. Vis. Comput. 2020, 36, 469–482. [Google Scholar] [CrossRef]
- Zhou, S.; Tan, B. Electrocardiogram soft computing using hybrid deep learning CNN-ELM. Appl. Soft Comput. 2020, 86, 105778. [Google Scholar] [CrossRef]
- Wang, J.; Zou, Y.; Lei, P.; Sherratt, R.S.; Wang, L. Research on recurrent neural network based crack opening prediction of concrete dam. J. Internet Technol. 2020, 21, 1161–1169. [Google Scholar]
- Lin, H.; Wang, C.; Deng, Q.; Xu, C.; Deng, Z.; Zhou, C. Review on chaotic dynamics of memristive neuron and neural network. Nonlinear Dyn. 2021, 106, 959–973. [Google Scholar] [CrossRef]
- Yu, F.; Shen, H.; Zhang, Z.; Huang, Y.; Cai, S.; Du, S. Dynamics analysis, hardware implementation and engineering applications of novel multi-style attractors in a neural network under electromagnetic radiation. Chaos Solitons Fractals 2021, 152, 111350. [Google Scholar] [CrossRef]
- Liao, M.; Wang, C.; Sun, Y.; Lin, H.; Xu, C. Memristor-based affective associative memory neural network circuit with emotional gradual processes. Neural Comput. Appl. 2022. [Google Scholar] [CrossRef]
- Tlelo-Cuautle, E.; González-Zapata, A.M.; Díaz-Muñoz, J.D.; de la Fraga, L.G.; Cruz-Vega, I. Optimization of fractional-order chaotic cellular neural networks by metaheuristics. Eur. Phys. J. Spec. Top. 2022, 1–7. [Google Scholar] [CrossRef]
- Xu, Q.; Ju, Z.; Ding, S.; Feng, C.; Chen, M.; Bao, B. Electromagnetic induction effects on electrical activity within a memristive Wilson neuron model. Cogn. Neurodyn. 2022. [Google Scholar] [CrossRef]
- Xu, C.; Wang, C.; Sun, Y.; Hong, Q.; Deng, Q.; Chen, H. Memristor-based neural network circuit with weighted sum simultaneous perturbation training and its applications. Neurocomputing 2021, 462, 581–590. [Google Scholar] [CrossRef]
- Yu, F.; Zhang, Z.; Shen, H.; Huang, Y.; Cai, S.; Jin, J.; Du, S. Design and FPGA implementation of a pseudo-random number generator based on a Hopfield neural network under electromagnetic radiation. Front. Phys. 2021, 9, 690651. [Google Scholar] [CrossRef]
- Ju, Z.; Lin, Y.; Chen, B.; Wu, H.; Chen, M.; Xu, Q. Electromagnetic radiation induced non-chaotic behaviors in a Wilson neuron model. Chin. J. Phys. 2022, 77, 214–222. [Google Scholar] [CrossRef]
- Yu, F.; Zhang, Z.; Shen, H.; Huang, Y.; Cai, S.; Du, S. FPGA implementation and image encryption application of a new PRNG based on a memristive Hopfield neural network with a special activation gradient. Chin. Phys. B 2022, 31, 020505. [Google Scholar] [CrossRef]
- Yao, W.; Wang, C.; Sun, Y.; Zhou, C. Robust multimode function synchronization of memristive neural networks with parameter perturbations and time-varying delays. IEEE Trans. Syst. Man Cybern. Syst. 2020, 52, 260–274. [Google Scholar] [CrossRef]
- Yu, F.; Chen, H.; Kong, X.; Yu, Q.; Cai, S.; Huang, Y.; Du, S. Dynamic analysis and application in medical digital image watermarking of a new multi-scroll neural network with quartic nonlinear memristor. Eur. Phys. J. Plus 2022, 350, 108–116. [Google Scholar] [CrossRef] [PubMed]
- Xu, Q.; Lin, Y.; Bao, B.; Chen, M. Multiple attractors in a non-ideal active voltage-controlled memristor based Chua’s circuit. Chaos Solitons Fractals 2016, 83, 186–200. [Google Scholar] [CrossRef]
- Ma, X.; Mou, J.; Liu, J.; Ma, C.; Yang, F.; Zhao, X. A novel simple chaotic circuit based on memristor-memcapacitor. Nonlinear Dyn. 2020, 100, 2859–2876. [Google Scholar] [CrossRef]
- Xu, C.; Wang, C.; Jiang, J.; Sun, J.; Lin, H. Memristive Circuit Implementation of Context-Dependent Emotional Learning Network and Its Application in Multi-Task. IEEE Trans.-Comput.-Aided Des. Integr. Circuits Syst. 2021. [Google Scholar] [CrossRef]
- Xu, Q.; Cheng, S.; Ju, Z.; Chen, M.; Wu, H. Asymmetric coexisting bifurcations and multi-stability in an asymmetric memristive diode-bridge-based jerk circuit. Chin. J. Phys. 2021, 70, 69–81. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Cui, L.; Sun, Y.; Xu, C.; Yu, F. Brain-like initial-boosted hyperchaos and application in biomedical image encryption. IEEE Trans. Ind. Inform. 2022. [Google Scholar] [CrossRef]
- Wen, Z.; Li, Z.; Li, X. Transient MMOs in memristive chaotic system via tiny perturbation. Electron. Lett. 2020, 56, 78–80. [Google Scholar] [CrossRef]
- Wan, Q.; Yan, Z.; Li, F.; Liu, J.; Chen, S. Multistable dynamics in a Hopfield neural network under electromagnetic radiation and dual bias currents. Nonlinear Dyn. 2022, 2022, 1–17. [Google Scholar] [CrossRef]
- Anbalagan, P.; Ramachran, R.; Alzabut, J.; Hincal, E.; Niezabitowski, M. Improved Results on Finite-Time Passivity and Synchronization Problem for Fractional-Order Memristor-Based Competitive Neural Networks: Interval Matrix Approach. Fractal Fract. 2022, 6, 36. [Google Scholar] [CrossRef]
- Yu, F.; Li, L.; He, B.; Liu, L.; Qian, S.; Zhang, Z.; Li, Y. Pseudorandom number generator based on a 5D hyperchaotic four-wing memristive system and its FPGA implementation. Eur. Phys. J.-Spec. Top. 2021, 230, 1763–1772. [Google Scholar] [CrossRef]
- Wen, Z.; Li, Z.; Li, X. Bursting dynamics in parametrically driven memristive Jerk system. Chin. J. Phys. 2020, 66, 327–334. [Google Scholar] [CrossRef]
- Petras, I. Oscillators Based on Fractional-Order Memory Elements. Fractal Fract. 2022, 6, 283. [Google Scholar] [CrossRef]
- Zidan, M.A.; Fahmy, H.A.H.; Hussain, M.M.; Salama, K.N. Memristor-based memory: The sneak paths problem and solutions. Microelectron. J. 2013, 44, 176–183. [Google Scholar] [CrossRef] [Green Version]
- Mohammad, B.; Homouz, D.; Elgabra, H. Robust Hybrid Memristor-CMOS Memory: Modeling and Design. IEEE Trans. Very Large Scale Integr. VLSI Syst. 2013, 21, 2069–2079. [Google Scholar] [CrossRef]
- Chang, T.; Jo, S.H.; Lu, W. Short-term memory to long-term memory transition in a nanoscale memristor. ACS Nano 2011, 5, 7669–7676. [Google Scholar] [CrossRef] [PubMed]
- Yao, W.; Wang, C.; Cao, J.; Sun, Y.; Zhou, C. Hybrid multisynchronization of coupled multistable memristive neural networks with time delays. Neurocomputing 2019, 363, 281–294. [Google Scholar] [CrossRef]
- Yao, W.; Wang, C.; Sun, Y.; Zhou, C.; Lin, H. Synchronization of inertial memristive neural networks with time-varying delays via static or dynamic event-triggered control. Neurocomputing 2020, 39, 367–380. [Google Scholar] [CrossRef]
- Thomas, A. Memristor-based neural networks. J. Phys. D Appl. Phys. 2013, 46, 093001. [Google Scholar] [CrossRef] [Green Version]
- Zhou, C.; Wang, C.; Sun, Y.; Yao, W. Weighted sum synchronization of memristive coupled neural networks. Neurocomputing 2020, 403, 225–232. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Yao, W.; Tan, Y. Chaotic dynamics in a neural network with different types of external stimuli. Commun. Nonlinear Sci. Numer. Simul. 2020, 90, 105390. [Google Scholar] [CrossRef]
- Han, X.; Hymavathi, M.; Sanober, S.; Dhupia, B.; Syed Ali, M. Robust stability of fractional order memristive BAM neural networks with mixed and additive time varying delays. Fractal Fract. 2022, 6, 62. [Google Scholar] [CrossRef]
- Tan, Y.; Wang, C. A simple locally active memristor and its application in HR neurons. Chaos 2020, 30, 053118. [Google Scholar] [CrossRef] [PubMed]
- Xu, Q.; Liu, T.; Feng, C.; Bao, H.; Wu, H.; Bao, B. Continuous non-autonomous memristive Rulkov model with extreme multistability. Chin. Phys. B 2021, 30, 128702. [Google Scholar] [CrossRef]
- Chen, C.; Min, F.; Zhang, Y.; Bao, B. Memristive electromagnetic induction effects on Hopfield neural network. Nonlinear Dyn. 2021, 106, 2559–2576. [Google Scholar] [CrossRef]
- Li, X.; Mou, J.; Cao, Y.; Banerjee, S. An Optical Image Encryption Algorithm Based on a Fractional-Order Laser Hyperchaotic System. Int. J. Bifurc. Chaos 2022, 32, 2250035. [Google Scholar] [CrossRef]
- Song, C.; Cao, J. Dynamics in fractional-order neural networks. Neurocomputing 2014, 142, 494–498. [Google Scholar] [CrossRef]
- Ma, C.; Mou, J.; Yang, F.; Yan, H. A fractional-order hopfield neural network chaotic system and its circuit realization. Eur. Phys. J. Plus 2020, 135, 100. [Google Scholar] [CrossRef]
- Fan, Y.; Huang, X.; Wang, Z.; Li, Y. Nonlinear dynamics and chaos in a simplified memristor-based fractional-order neural network with discontinuous memductance function. Nonlinear Dyn. 2018, 93, 611–627. [Google Scholar] [CrossRef]
- Yu, F.; Kong, X.; Chen, H.; Yu, Q.; Cai, S.; Huang, Y.; Du, S. A 6D Fractional-Order Memristive Hopfield Neural Network and its Application in Image Encryption. Front. Phys. 2022, 10, 847385. [Google Scholar] [CrossRef]
- Zhang, S.; Zheng, J.; Wang, X.; Zeng, Z.; He, S. Initial offset boosting coexisting attractors in memristive multi-double-scroll Hopfield neural network. Nonlinear Dyn. 2020, 102, 2821–2841. [Google Scholar] [CrossRef]
- Silva, C.P. Shil’nikov’s theorem—A tutorial. IEEE Trans. Circuits Syst. Fundam. Theory Appl. 1993, 40, 675–682. [Google Scholar] [CrossRef]
- Xu, Q.; Tan, X.; Zhu, D.; Bao, H.; Hu, Y.; Bao, B. Bifurcations to bursting and spiking in the Chay neuron and their validation in a digital circuit. Chaos Solitons Fractals 2020, 141, 110353. [Google Scholar] [CrossRef]
- González-Zapata, A.M.; Tlelo-Cuautle, E.; Cruz-Vega, I.; León-Salas, W.D. Synchronization of chaotic artificial neurons and its application to secure image transmission under MQTT for IoT protocol. Nonlinear Dyn. 2021, 104, 4581–4600. [Google Scholar] [CrossRef]
- Siegel, J.E.; Kumar, S.; Sarma, S.E. The future internet of things: Secure, efficient, and model-based. IEEE Internet Things J. 2017, 5, 2386–2398. [Google Scholar] [CrossRef] [Green Version]
- Airehrour, D.; Gutierrez, J.; Ray, S.K. Secure routing for internet of things: A survey. J. Netw. Comput. Appl. 2016, 66, 198–213. [Google Scholar] [CrossRef]
- Cheng, S.; Sun, J.; Xu, C. A color image encryption scheme based on hybrid cascaded chaotic system. Int. J. Bifurc. Chaos 2021, 31, 2150125. [Google Scholar] [CrossRef]
- Deng, J.; Zhou, M.; Wang, C.; Wang, S.; Xu, C. Image segmentation encryption algorithm with chaotic sequence generation participated by cipher and multi-feedback loops. Multimed. Tools Appl. 2021, 80, 13821–13840. [Google Scholar] [CrossRef]
- Yu, F.; Shen, H.; Zhang, Z.; Huang, Y.; Cai, S.; Du, S. A new multi-scroll Chua’s circuit with composite hyperbolic tangent-cubic nonlinearity: Complex dynamics, Hardware implementation and Image encryption application. Integr.-VLSI J. 2021, 81, 71–83. [Google Scholar] [CrossRef]
- Zeng, J.; Wang, C.H. A novel hyper-chaotic image encryption system based on particle swarm optimization algorithm and cellular automata. Secur. Commun. Netw. 2021, 2021, 6675565. [Google Scholar] [CrossRef]
- Li, X.J.; Mou, J.; Banerjee, S.; Wang, Z.S.; Cao, Y.H. Design and DSP implementation of a fractional-order detuned laser hyperchaotic circuit with applications in image encryption. Chaos Solitons Fractals 2022, 159, 112133. [Google Scholar] [CrossRef]
- Gao, X.; Mou, J.; Xiong, L.; Sha, Y.; Yan, H.; Cao, Y. A Fast and Efficient Multiple Images Encryption Based on Single Channel Encryption and Chaotic System. Nonlinear Dyn. 2022, 108, 613–636. [Google Scholar] [CrossRef]
- Cheng, G.; Wang, C.; Xu, C. A novel hyper-chaotic image encryption scheme based on quantum genetic algorithm and compressive sensing. Multimed. Tools Appl. 2020, 79, 29243–29263. [Google Scholar] [CrossRef]
- Yong, Y.U.; Jian, G.; Meng-Ru, Y.U.; Gong-Kun, J.I.A.N.G. A Pseudo-random Number Generator Based on Integer Chaotic Map. J. Beijing Univ. Posts Telecommun. 2022, 45, 58–62. [Google Scholar]
- Cang, S.; Kang, Z.; Wang, Z. Pseudo-random number generator based on a generalized conservative Sprott—A system. Nonlinear Dyn. 2021, 104, 827–844. [Google Scholar] [CrossRef]
- Li, S.; Liu, Y.; Ren, F.; Yang, Z. Design of a high throughput pseudo-random number generator based on discrete hyper-chaotic system. IEEE Trans. Circuits Syst. Ii Express Briefs 2022. [Google Scholar] [CrossRef]
- Yu, F.; Qian, S.; Chen, X.; Huang, Y.; Liu, L.; Shi, C.; Wang, C. A New 4D Four-Wing Memristive Hyperchaotic System: Dynamical Analysis, Electronic Circuit Design, Shape Synchronization and Secure Communication. Int. J. Bifurc. Chaos 2020, 30, 2050147. [Google Scholar] [CrossRef]
- Zhou, L.; Tan, F.; Li, X.; Zhou, L. A fixed-time synchronization-based secure communication scheme for two-layer hybrid coupled networks. Neurocomputing 2021, 433, 131–141. [Google Scholar] [CrossRef]
- Liu, J.; Zhang, J.; Wang, Y. Secure Communication via Chaotic Synchronization Based on Reservoir Computing. IEEE Trans. Neural Netw. Learn. Syst. 2022. [Google Scholar] [CrossRef]
- Li, Y.; Li, Z.; Ma, M.; Wang, M. Generation of grid multi-wing chaotic attractors and its application in video secure communication system. Multimed. Tools Appl. 2020, 79, 29161–29177. [Google Scholar] [CrossRef]
- Kekha Javan, A.A.; Zare, A.; Alizadehsani, R.; Balochian, S. Robust Multi-Mode Synchronization of Chaotic Fractional Order Systems in the Presence of Disturbance, Time Delay and Uncertainty with Application in Secure Communications. Big Data Cogn. Comput. 2022, 6, 51. [Google Scholar] [CrossRef]
- Geng, X.; Du, C.; Ding, Q. Image Encryption System of New Chaotic Algorithm based on DSP. Second Int. Conf. Instrum. Meas. Comput. Commun. Control 2012, 2012, 614–618. [Google Scholar]
- Shi, J.; He, K.; Fang, H. Chaos, Hopf bifurcation and control of a fractional-order delay financial system. Math. Comput. Simul. 2022, 194, 348–364. [Google Scholar] [CrossRef]
- Xiao, M.; Zheng, W.; Lin, J.; Jiang, G.; Zhao, L.; Cao, J. Fractional-order PD control at Hopf bifurcations in delayed fractional-order small-world networks. J. Frankl. Inst. 2017, 354, 7643–7667. [Google Scholar] [CrossRef]
- Huang, C.; Wang, J.; Chen, X.; Cao, J. Bifurcations in a fractional-order BAM neural network with four different delays. Neural Netw. 2021, 141, 344–354. [Google Scholar] [CrossRef]
- Xu, C.; Zhang, W.; Aouiti, C.; Liu, Z.; Liao, M.; Li, P. Further investigation on bifurcation and their control of fractional-order bidirectional associative memory neural networks involving four neurons and multiple delays. Math. Methods Appl. Sci. 2021, 427, 110–117. [Google Scholar] [CrossRef]
- Huang, C.; Liu, H.; Shi, X.; Chen, X.; Xiao, M.; Wang, Z.; Cao, J. Bifurcations in a fractional-order neural network with multiple leakage delays. Neural Netw. 2020, 131, 115–126. [Google Scholar] [CrossRef]
- Xu, C.; Liu, Z.; Yao, L.; Aouiti, C. Further exploration on bifurcation of fractional-order six-neuron bi-directional associative memory neural networks with multi-delays. Appl. Math. Comput. 2021, 410, 126458. [Google Scholar] [CrossRef]




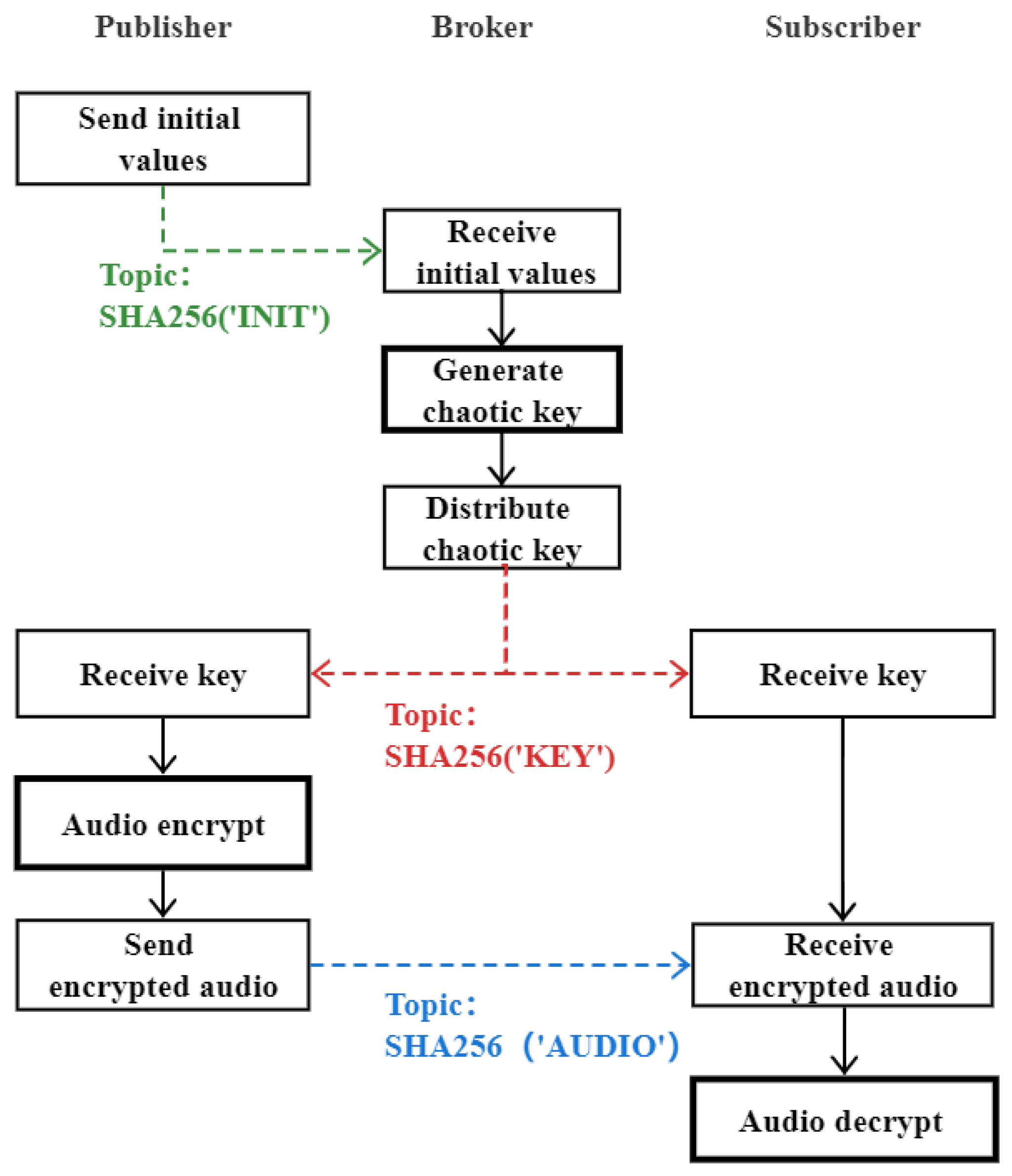
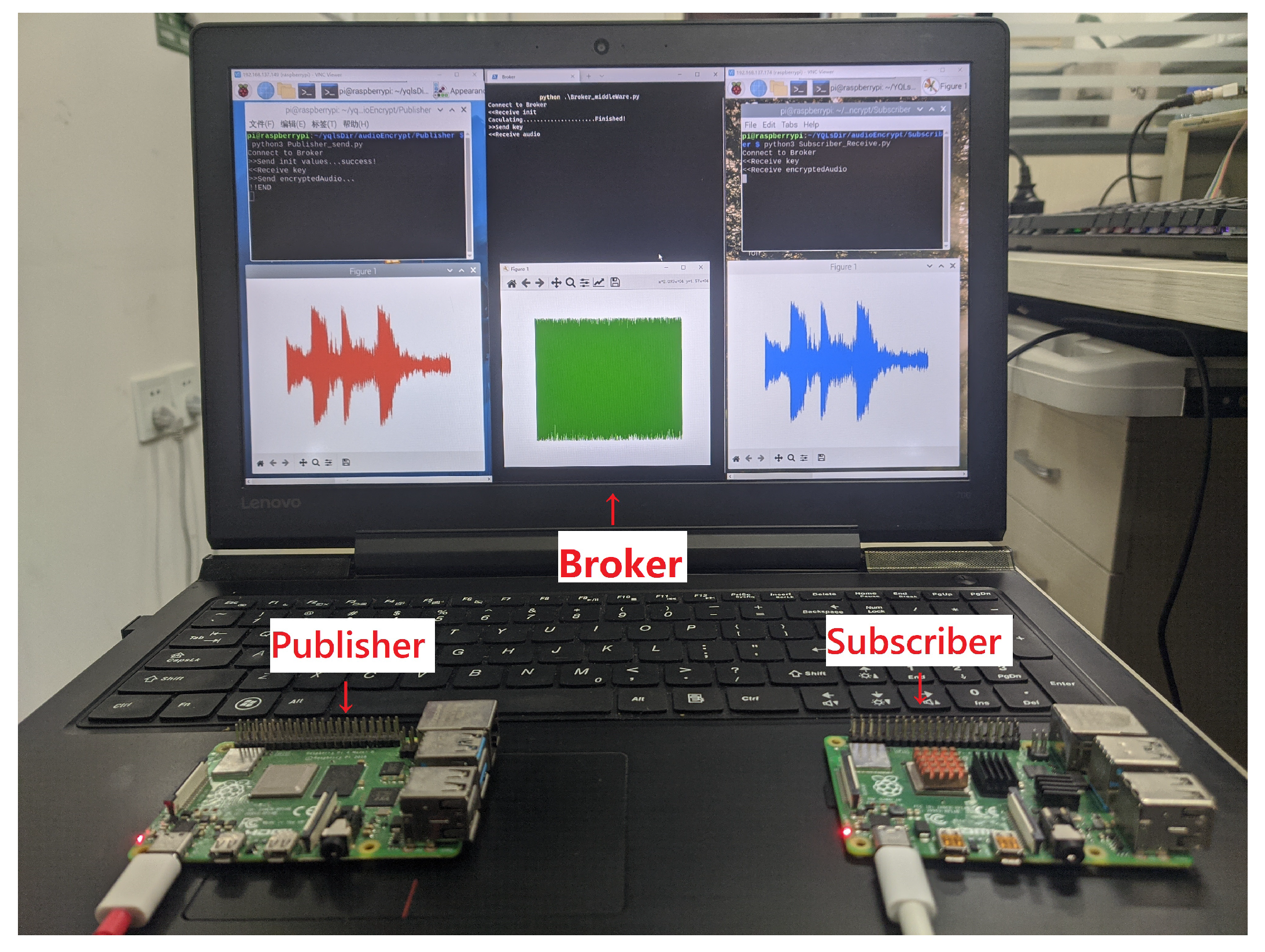


| Topic | After SHA256 |
|---|---|
| KEY | 2c70e12b7a0646f92279f427c7b38e7334d8e5389cff167a1dc30e73f826b683 |
| INIT | bb54068aea85faa7e487530083366be9962390af822e4c71ef1aca7033c83e66 |
| AUDIO | 6ed8919ce20490a5e3ad8630a4fab69475297abd07db73918dd5f36fcfaeb11b |
| Device | Role | IP Adress |
|---|---|---|
| Raspberry Pi 1 | Publisher Alice | 192.168.137.149 |
| Laptop | Broker Server&Eve | 192.168.137.1 |
| Raspberry Pi 2 | Subscriber Bob | 192.168.137.174 |
| Reference | System | Main Technique | Data Type | Implemented Device | Cost of Large-Scale Deployment | Difficulty of Implementation |
|---|---|---|---|---|---|---|
| Ref. [19] | Ordinary memristive Hopfield neural network | PRNG | Picture | FPGA | High | High |
| Ref. [53] | Multiple different systems | Local MQTT | Picture | Raspberry Pi | Low | Low |
| Ref. [71] | Logistic map | Double K-L transformation algorithm | Picture | DSP | Low | High |
| This paper | Multi-scroll fractional-order memristive hopfield neural network | Cloud MQTT | Audio | Raspberry Pi and high-performance Server | Low | Low |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yu, F.; Yu, Q.; Chen, H.; Kong, X.; Mokbel, A.A.M.; Cai, S.; Du, S. Dynamic Analysis and Audio Encryption Application in IoT of a Multi-Scroll Fractional-Order Memristive Hopfield Neural Network. Fractal Fract. 2022, 6, 370. https://doi.org/10.3390/fractalfract6070370
Yu F, Yu Q, Chen H, Kong X, Mokbel AAM, Cai S, Du S. Dynamic Analysis and Audio Encryption Application in IoT of a Multi-Scroll Fractional-Order Memristive Hopfield Neural Network. Fractal and Fractional. 2022; 6(7):370. https://doi.org/10.3390/fractalfract6070370
Chicago/Turabian StyleYu, Fei, Qiulin Yu, Huifeng Chen, Xinxin Kong, Abdulmajeed Abdullah Mohammed Mokbel, Shuo Cai, and Sichun Du. 2022. "Dynamic Analysis and Audio Encryption Application in IoT of a Multi-Scroll Fractional-Order Memristive Hopfield Neural Network" Fractal and Fractional 6, no. 7: 370. https://doi.org/10.3390/fractalfract6070370
APA StyleYu, F., Yu, Q., Chen, H., Kong, X., Mokbel, A. A. M., Cai, S., & Du, S. (2022). Dynamic Analysis and Audio Encryption Application in IoT of a Multi-Scroll Fractional-Order Memristive Hopfield Neural Network. Fractal and Fractional, 6(7), 370. https://doi.org/10.3390/fractalfract6070370







