Cyber4Drone: A Systematic Review of Cyber Security and Forensics in Next-Generation Drones
Abstract
:1. Introduction
2. Related Works
| Year | Paper | Network Forensics | Security Aspects | Privacy Aspects | Models | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Communication | Software | ||||||||||||
| A | V | T | C | A | V | T | C | A | C | ||||
| 2016 | [16] | ✓ | ✓✫ | ✓✫ | ✓✫ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| 2017 | [11] | ✓ | ✓ | ||||||||||
| 2018 | [7] ★ | ✓ | ✓ | ✓ | ✓ | ✓ | |||||||
| 2018 | [17] | ✓ | ✓ | ✓✫ | ✓ | ✓ | |||||||
| 2019 | [10] ★ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||
| 2019 | [18] ★ | ✓ | ✓ | ✓ | ✓ | ✓ | |||||||
| 2019 | [19] | ✓ | ✓ | ✓ | ✓ | ✓ | |||||||
| 2019 | [20] | ✓ | ✓ | ✓ | |||||||||
| 2020 | [15] ★ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||
| 2020 | [12] | ✓ | ✓✫ | ✓ | ✓✫ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| 2020 | [21] | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||
| 2021 | [9] | ✓ | ✓✫ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||
| 2021 | [22] | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||
| 2021 | [23] | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |||||
| 2022 | [4] | ✓ | |||||||||||
| 2022 | [24] | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||
| 2023 | Proposed ★ | ✓✫ | ✓✫ | ✓✫ | ✓✫ | ✓✫ | ✓✫ | ✓✫ | ✓✫ | ✓✫ | ✓✫ | ✓✫ | ✓✫ |
3. Overview of Drones
3.1. Drone Architecture
3.1.1. Drone Craft
3.1.2. Datalink
3.1.3. Ground Control Station
3.2. Drone Communications
- GCS communication: This datalink supports UAS and ground control station communications, and the GCS uses wireless signals to communicate with UAVs, allowing it to monitor network traffic and direct flight operations. These communications are based on short-range wireless technologies, making them prone to different attacks [25].
- ADS-B communication: Automatic Dependent Surveillance-Broadcast (ADS-B) has been adopted for aircraft Air Traffic Control (ATC) systems. Anonymous ground users and other aircraft can use ADS-B to periodically broadcast general navigation information through long-range RF signals. It operates on 1090 MHz and is a digital protocol. Standard identification and navigational data for the aircraft, such as altitude, GPS, and the aircraft’s identification number, are included in ADS-B signals. Drones have lately started using ADS-B [26]. For smaller drones, conventional ADS-B systems are too large; hence, smaller ADS-B modules are required [27]. This enables DAA (detect and avoid) capabilities, enhancing safety for airspace users and providing easier drone identification and tracking.
- GPS communication: The controller must identify the drone’s path for collision avoidance in Beyond Line-of-Sight (BLOS) operations. A drone connects with GPS satellites to transmit and receive data and information. As a result, UAVs can develop satellite network connectivity to collect their real-time GPS coordinates. Additionally, satellite communications are beneficial across large distances even without developed infrastructure and enable stable communication with higher data frequency.
- Video transmission: 1.3 GHz, 2.4 GHz, and 5.8 GHz are common RF data links for video transmission. (i) 1.3 GHz—This system can have a range of more than 40 miles and better penetration abilities, depending on the amount of power employed. Because of its low data rates, it provides poor video quality. (ii) The range of a 2.4 GHz system can be up to 15 miles. As 2.4 GHz is also utilized for control, using it for video will cause interference. (iii) The most widely used frequency for video transmission is 5.8 GHz because of its short wavelength and high data rate transfer capacity. Compared to the other options, it produces a clear video. However, it can only penetrate a restricted distance of 5 miles due to its small wavelength.
4. Threat Models and Attack Scenarios
4.1. RF Jamming
4.2. Cloning
4.3. GPS Spoofing
4.4. Software Based Attack
4.5. RTL-SDR Attack
4.6. Deauth Attack
4.7. ESC-PWM Signal Attack
4.8. Sensor-Based Attack
4.9. Denial of Service Attack
4.10. Man in the Middle (MITM) Attack
5. Security and Privacy of UAVs
- Authorization: Only authorized operators should be given access to the UAV system’s resources, including the ground control station and the aircraft. During communication, an ongoing authentication process between the operator and the UAV is necessary.
- Availability: All components of the UAS should be assured to fulfill their respective activities under defined geographical and temporal conditions, ensuring that the system’s availability is maintained throughout the operational period. It is also critical to manage the repair and update activities in a way that does not compromise the UAV system’s availability when it is in use.
- Integrity: The UAS should be designed to verify that the telemetric data, GPS, and serial communications are authentic and have not been tampered with intentionally or inadvertently.
5.1. Network Security
5.2. Communication Security
ADS-B Security
5.3. Privacy Issues of UAVs
6. Drone Forensics
6.1. Drone Forensic Framework
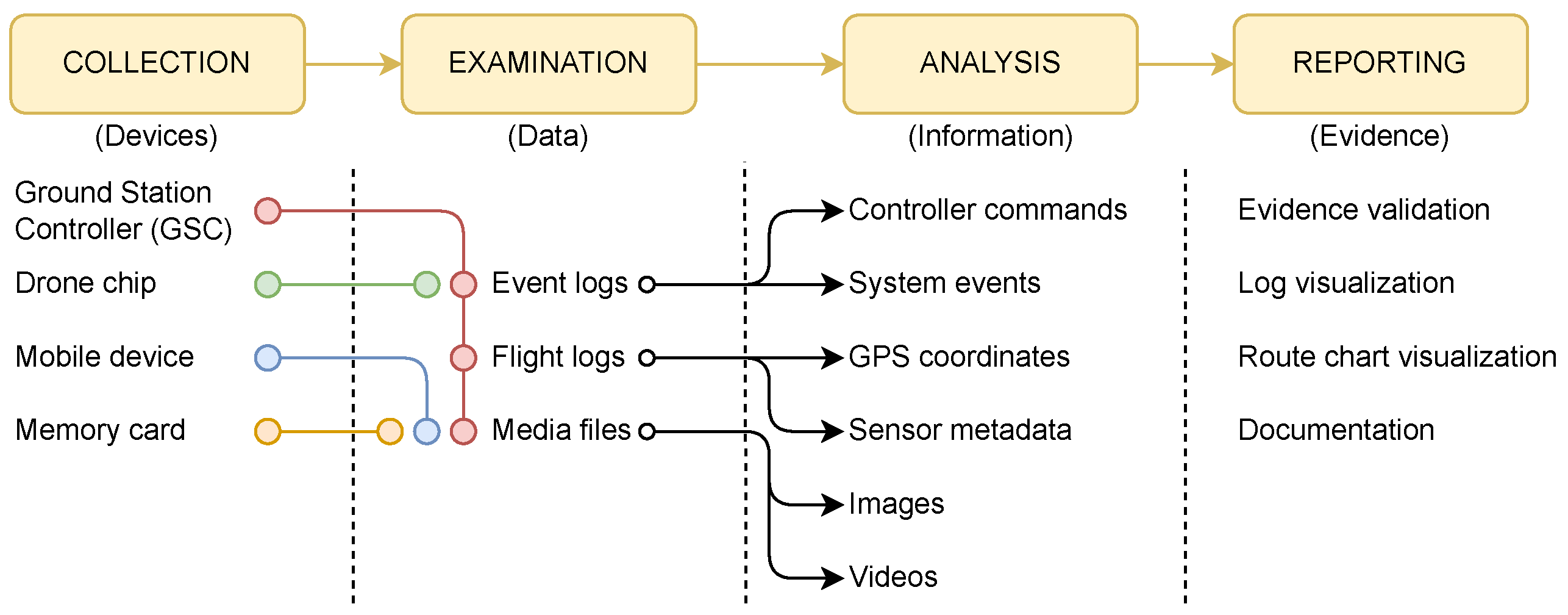
6.1.1. Collection
6.1.2. Examination
6.1.3. Analysis
6.1.4. Reporting
6.2. Drone Forensics Artifacts
6.3. Drone Forensics Tools
6.4. Drone Forensic Datasets
7. Discussion and Directions for Future Works
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Elands, P.; de Kraker, J.; Laarakkers, J.; Olk, J.; Schonagen, J. Technical Aspects Concerning the Safe and Secure Use of Drones; TNO: Den Haag, The Netherlands, 2016. [Google Scholar]
- Fu, C.H.; Tsao, M.W.; Chi, L.P.; Zhuang, Z.Y. On the dominant factors of civilian-use drones: A thorough study and analysis of cross-group opinions using a triple helix model (THM) with the analytic hierarchy process (AHP). Drones 2021, 5, 46. [Google Scholar] [CrossRef]
- Bouafif, H.; Kamoun, F.; Iqbal, F.; Marrington, A. Drone forensics: Challenges and new insights. In Proceedings of the 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; pp. 1–6. [Google Scholar]
- Alotaibi, F.M.; Al-Dhaqm, A.; Al-Otaibi, Y.D.; Alsewari, A.A. A comprehensive collection and analysis model for the drone forensics field. Sensors 2022, 22, 6486. [Google Scholar] [CrossRef]
- Citroni, R.; Di Paolo, F.; Livreri, P. A novel energy harvester for powering small UAVs: Performance analysis, model validation and flight results. Sensors 2019, 19, 1771. [Google Scholar] [CrossRef] [Green Version]
- Hartmann, K.; Steup, C. The vulnerability of UAVs to cyber attacks-An approach to the risk assessment. In Proceedings of the 2013 5th International Conference on Cyber Conflict (CYCON 2013), Tallinn, Estonia, 4–7 June 2013; pp. 1–23. [Google Scholar]
- GÜLATAŞ, İ.; BAKTIR, S. Unmanned aerial vehicle digital forensic investigation framework. J. Nav. Sci. Eng. 2018, 14, 32–53. [Google Scholar]
- Salamh, F.E.; Mirza, M.M.; Karabiyik, U. UAV Forensic Analysis and Software Tools Assessment: DJI Phantom 4 and Matrice 210 as Case Studies. Electronics 2021, 10, 733. [Google Scholar] [CrossRef]
- Yahuza, M.; Idris, M.Y.I.; Ahmedy, I.B.; Wahab, A.W.A.; Nandy, T.; Noor, N.M.; Bala, A. Internet of Drones Security and Privacy Issues: Taxonomy and Open Challenges. IEEE Access 2021, 9, 57243–57270. [Google Scholar] [CrossRef]
- Salamh, F.E.; Karabiyik, U.; Rogers, M.K. RPAS forensic validation analysis towards a technical investigation process: A case study of yuneec typhoon H. Sensors 2019, 19, 3246. [Google Scholar] [CrossRef] [Green Version]
- Clark, D.R.; Meffert, C.; Baggili, I.; Breitinger, F. DROP (DRone Open source Parser) your drone: Forensic analysis of the DJI Phantom III. Digit. Investig. 2017, 22, S3–S14. [Google Scholar] [CrossRef]
- Yaacoub, J.P.; Noura, H.; Salman, O.; Chehab, A. Security analysis of drones systems: Attacks, limitations, and recommendations. Internet Things 2020, 11, 100218. [Google Scholar] [CrossRef]
- Al-Room, K.; Iqbal, F.; Baker, T.; Shah, B.; Yankson, B.; MacDermott, A.; Hung, P.C. Drone Forensics: A Case Study of Digital Forensic Investigations Conducted on Common Drone Models. Int. J. Digit. Crime Forensics 2021, 13, 1–25. [Google Scholar] [CrossRef]
- Nassi, B.; Bitton, R.; Masuoka, R.; Shabtai, A.; Elovici, Y. SoK: Security and privacy in the age of commercial drones. In Proceedings of the 2021 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 24–27 May 2021; pp. 73–90. [Google Scholar]
- Bouafif, H.; Kamoun, F.; Iqbal, F. Towards a better understanding of drone forensics: A case study of parrot AR drone 2.0. Int. J. Digit. Crime Forensics 2020, 12, 35–57. [Google Scholar] [CrossRef]
- Altawy, R.; Youssef, A.M. Security, privacy, and safety aspects of civilian drones: A survey. ACM Trans. Cyber-Phys. Syst. 2016, 1, 1–25. [Google Scholar] [CrossRef]
- Choudhary, G.; Sharma, V.; Gupta, T.; Kim, J.; You, I. Internet of Drones (IoD): Threats, vulnerability, and security perspectives. arXiv 2018, arXiv:1808.00203. [Google Scholar]
- Mei, N. An Approach to Unmanned Aircraft Systems Forensics Framework. Ph.D. Thesis, Capitol Technology University, Laurel, MD, USA, 2019. [Google Scholar]
- Fotouhi, A.; Qiang, H.; Ding, M.; Hassan, M.; Giordano, L.G.; Garcia-Rodriguez, A.; Yuan, J. Survey on UAV cellular communications: Practical aspects, standardization advancements, regulation, and security challenges. IEEE Commun. Surv. Tutor. 2019, 21, 3417–3442. [Google Scholar] [CrossRef] [Green Version]
- Nassi, B.; Shabtai, A.; Masuoka, R.; Elovici, Y. SoK-security and privacy in the age of drones: Threats, challenges, solution mechanisms, and scientific gaps. arXiv 2019, arXiv:1903.05155. [Google Scholar]
- Ghosh, T.; Rasheed, I.; Toorchi, N.; Hu, F. UAV Security Threats, Requirements and Solutions. In UAV Swarm Networks; CRC Press: Boca Raton, FL, USA, 2020; pp. 193–206. [Google Scholar]
- Shafique, A.; Mehmood, A.; Elhadef, M. Survey of Security Protocols and Vulnerabilities in Unmanned Aerial Vehicles. IEEE Access 2021, 9, 46927–46948. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Agrawal, A.; Goyal, A.; Luong, N.C.; Niyato, D.; Yu, F.R.; Guizani, M. Fast, reliable, and secure drone communication: A comprehensive survey. IEEE Commun. Surv. Tutor. 2021, 23, 2802–2832. [Google Scholar] [CrossRef]
- Chiper, F.L.; Martian, A.; Vladeanu, C.; Marghescu, I.; Craciunescu, R.; Fratu, O. Drone detection and defense systems: Survey and a software-defined radio-based solution. Sensors 2022, 22, 1453. [Google Scholar] [CrossRef]
- Hooper, M.; Tian, Y.; Zhou, R.; Cao, B.; Lauf, A.P.; Watkins, L.; Robinson, W.H.; Alexis, W. Securing commercial wifi-based uavs from common security attacks. In Proceedings of the MILCOM 2016-2016 IEEE Military Communications Conference, Baltimore, MD, USA, 1–3 November 2016; pp. 1213–1218. [Google Scholar]
- Strohmeier, M.; Lenders, V.; Martinovic, I. On the security of the automatic dependent surveillance-broadcast protocol. IEEE Commun. Surv. Tutor. 2014, 17, 1066–1087. [Google Scholar] [CrossRef] [Green Version]
- Park, S.; Kim, H.T.; Lee, S.; Joo, H.; Kim, H. Survey on anti-drone systems: Components, designs, and challenges. IEEE Access 2021, 9, 42635–42659. [Google Scholar] [CrossRef]
- Hosseinzadeh, M.; Sinopoli, B. Active attack detection and control in constrained cyber-physical systems under prevented actuation attack. In Proceedings of the 2021 American Control Conference (ACC), New Orleans, LA, USA, 25–28 May 2021; pp. 3242–3247. [Google Scholar]
- Vedula, V.; Lama, P.; Boppana, R.V.; Trejo, L.A. On the detection of low-rate denial of service attacks at transport and application layers. Electronics 2021, 10, 2105. [Google Scholar] [CrossRef]
- Chandramohan, D.; Vengattaraman, T.; Dhavachelvan, P. A secure data privacy preservation for on-demand cloud service. J. King Saud Univ.-Eng. Sci. 2017, 29, 144–150. [Google Scholar] [CrossRef] [Green Version]
- Samland, F.; Fruth, J.; Hildebrandt, M.; Hoppe, T.; Dittmann, J.A.R. Drone: Security threat analysis and exemplary attack to track persons. Intell. Robot. Comput. Vis. XXIX Algorithms Tech. 2012, 8301, 158–172. [Google Scholar]
- Sciancalepore, S.; Ibrahim, O.A.; Oligeri, G.; Di Pietro, R. Detecting drones status via encrypted traffic analysis. In Proceedings of the ACM Workshop on Wireless Security and Machine Learning, Miami, FL, USA, 15–17 May 2019; pp. 67–72. [Google Scholar]
- Sciancalepore, S.; Ibrahim, O.A.; Oligeri, G.; Di Pietro, R. Picking a needle in a Haystack: Detecting drones via network traffic analysis. arXiv 2019, arXiv:1901.03535. [Google Scholar]
- Bisio, I.; Garibotto, C.; Lavagetto, F.; Sciarrone, A.; Zappatore, S. Unauthorized amateur UAV detection based on WiFi statistical fingerprint analysis. IEEE Commun. Mag. 2018, 56, 106–111. [Google Scholar] [CrossRef]
- Munari, S.; Palazzi, C.E.; Quadrio, G.; Ronzani, D. Network traffic analysis of a small quadcopter. In Proceedings of the 3rd Workshop on Micro Aerial Vehicle Networks, Systems, and Applications, Niagara Falls, NY, USA, 23 June 2017; pp. 31–36. [Google Scholar]
- Vanitha, N.; Ganapathi, P. Traffic analysis of UAV networks using enhanced deep feed forward neural networks (EDFFNN). In Handbook of Research on Machine and Deep Learning Applications for Cyber Security; IGI Global: Hershey, PA, USA, 2020; pp. 219–244. [Google Scholar]
- He, D.; Chan, S.; Guizani, M. Drone-assisted public safety networks: The security aspect. IEEE Commun. Mag. 2017, 55, 218–223. [Google Scholar] [CrossRef]
- Čisar, P.; Pinter, R.; Čisar, S.M.; Gligorijević, M. Principles of Anti-Drone Defense. In Proceedings of the 2020 11th IEEE International Conference on Cognitive Infocommunications (CogInfoCom), Mariehamn, Finland, 23–25 September 2020; pp. 000019–000026. [Google Scholar]
- Al-Dhaqm, A.; Ikuesan, R.A.; Kebande, V.R.; Razak, S.; Ghabban, F.M. Research challenges and opportunities in drone forensics models. Electronics 2021, 10, 1519. [Google Scholar] [CrossRef]
- Yousef, M.; Iqbal, F.; Hussain, M. Drone Forensics: A Detailed Analysis of Emerging DJI Models. In Proceedings of the 2020 11th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 7–9 April 2020; pp. 066–071. [Google Scholar]
- Lan, J.K.W.; Lee, F.K.W. Drone Forensics: A Case Study on DJI Mavic Air 2. In Proceedings of the 2021 23rd International Conference on Advanced Communication Technology (ICACT), Pyeongchang-gun, Republic of Korea, 13–16 February 2022; pp. 291–296. [Google Scholar]
- Atkinson, S.; Carr, G.; Shaw, C.; Zargari, S. Drone Forensics: The Impact and Challenges. In Digital Forensic Investigation of Internet of Things (IoT) Devices; Springer: Berlin/Heidelberg, Germany, 2021; pp. 65–124. [Google Scholar]
- Viswanathan, S.; Baig, Z. Digital Forensics for Drones: A Study of Tools and Techniques. In Applications and Techniques in Information Security, Proceedings of the 11th International Conference, ATIS 2020, Brisbane, QLD, Australia, 12–13 November 2020; Springer: Singapore, 2020; pp. 29–41. [Google Scholar]
- Barker, N.V. Development of a Drone-Mounted Wireless Attack Platform. Theses and Dissertations. 3224. 2020. Available online: https://scholar.afit.edu/etd/3224 (accessed on 10 June 2023).
- Shin, J.M.; Kim, Y.S.; Ban, T.W.; Choi, S.; Kang, K.M.; Ryu, J.Y. Position tracking techniques using multiple receivers for anti-drone systems. Sensors 2021, 21, 35. [Google Scholar] [CrossRef]
- Siddappaji, B.; Akhilesh, K. Role of cyber security in drone technology. In Smart Technologies; Springer: Berlin/Heidelberg, Germany, 2020; pp. 169–178. [Google Scholar]
- Kang, J.; Xiong, Z.; Niyato, D.; Xie, S.; Kim, D.I. Securing Data Sharing from the Sky: Integrating Blockchains into Drones in 5G and Beyond. IEEE Netw. 2021, 35, 78–85. [Google Scholar] [CrossRef]
- Feng, C.; Yu, K.; Bashir, A.K.; Al-Otaibi, Y.D.; Lu, Y.; Chen, S.; Zhang, D. Efficient and secure data sharing for 5G flying drones: A blockchain-enabled approach. IEEE Netw. 2021, 35, 130–137. [Google Scholar] [CrossRef]
- Aggarwal, S.; Shojafar, M.; Kumar, N.; Conti, M. A new secure data dissemination model in internet of drones. In Proceedings of the ICC 2019—2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Kim, S.K.; Jang, E.T.; Lim, S.H.; Park, K.W. Reduction of Data Leakage Using Software Streaming. In International Symposium on Mobile Internet Security; Springer: Singapore, 2019; pp. 99–111. [Google Scholar]
- Choudhary, G.; Sharma, V.; You, I. Sustainable and secure trajectories for the military Internet of Drones (IoD) through an efficient Medium Access Control (MAC) protocol. Comput. Electr. Eng. 2019, 74, 59–73. [Google Scholar] [CrossRef]
- Sharma, V.; Choudhary, G.; Ko, Y.; You, I. Behavior and vulnerability assessment of drones-enabled industrial internet of things (iiot). IEEE Access 2018, 6, 43368–43383. [Google Scholar] [CrossRef]
- Wazid, M.; Bera, B.; Das, A.K.; Garg, S.; Niyato, D.; Hossain, M.S. Secure Communication Framework for Blockchain-Based Internet of Drones-Enabled Aerial Computing Deployment. IEEE Internet Things Mag. 2021, 4, 120–126. [Google Scholar] [CrossRef]
- Hamza, A.; Akram, U.; Samad, A.; Khosa, S.N.; Fatima, R.; Mushtaq, M.F. Unmaned Aerial Vehicles Threats and Defence Solutions. In Proceedings of the 2020 IEEE 23rd International Multitopic Conference (INMIC), Bahawalpur, Pakistan, 5–7 November 2020; pp. 1–6. [Google Scholar]
- Majeed, R.; Abdullah, N.A.; Mushtaq, M.F.; Kazmi, R. Drone Security: Issues and Challenges. (IJACSA) Int. J. Adv. Comput. Sci. Appl. 2021, 12, 720–729. [Google Scholar] [CrossRef]
- Jan, S.U.; Qayum, F.; Khan, H.U. Design and Analysis of Lightweight Authentication Protocol for Securing IoD. IEEE Access 2021, 9, 69287–69306. [Google Scholar] [CrossRef]
- Nayyar, A.; Nguyen, B.L.; Nguyen, N.G. The internet of drone things (IoDT): Future envision of smart drones. In First International Conference on Sustainable Technologies for Computational Intelligence, Proceedings of ICTSCI 2019; Springer: Singapore, 2020; pp. 563–580. [Google Scholar]
- Gope, P.; Sikdar, B. An efficient privacy-preserving authenticated key agreement scheme for edge-assisted internet of drones. IEEE Trans. Veh. Technol. 2020, 69, 13621–13630. [Google Scholar] [CrossRef]
- Cheon, J.H.; Han, K.; Hong, S.M.; Kim, H.J.; Kim, J.; Kim, S.; Seo, H.; Shim, H.; Song, Y. Toward a secure drone system: Flying with real-time homomorphic authenticated encryption. IEEE Access 2018, 6, 24325–24339. [Google Scholar] [CrossRef]
- Tanveer, M.; Zahid, A.H.; Ahmad, M.; Baz, A.; Alhakami, H. LAKE-IoD: Lightweight authenticated key exchange protocol for the Internet of drone environment. IEEE Access 2020, 8, 155645–155659. [Google Scholar] [CrossRef]
- Khan, N.A.; Brohi, S.N.; Jhanjhi, N. UAV’s applications, architecture, security issues and attack scenarios: A survey. In Intelligent Computing and Innovation on Data Science; Springer: Singapore, 2020; pp. 753–760. [Google Scholar]
- Renyu, Z.; Kiat, S.C.; Kai, W.; Heng, Z. Spoofing attack of drone. In Proceedings of the 2018 IEEE 4th International Conference on Computer and Communications (ICCC), Chengdu, China, 7–10 December 2018; pp. 1239–1246. [Google Scholar]
- Dahlman, E.; Lagrelius, K. A Game of Drones: Cyber Security in UAVs. 2019. Available online: http://www.diva-portal.org/smash/get/diva2:1350857/FULLTEXT01.pdf (accessed on 2 June 2023).
- Kharchenko, V.; Torianyk, V. Cybersecurity of the internet of drones: Vulnerabilities analysis and imeca based assessment. In Proceedings of the 2018 IEEE 9th International Conference on Dependable Systems, Services and Technologies (DESSERT), Kyiv, Ukraine, 24–27 May 2018; pp. 364–369. [Google Scholar]
- Cho, G.; Cho, J.; Hyun, S.; Kim, H. SENTINEL: A secure and efficient authentication framework for unmanned aerial vehicles. Appl. Sci. 2020, 10, 3149. [Google Scholar] [CrossRef]
- bin Mohammad Fadilah, M.S.; Balachandran, V.; Loh, P.; Chua, M. DRAT: A Drone Attack Tool for Vulnerability Assessment. In Proceedings of the Tenth ACM Conference on Data and Application Security and Privacy, New Orleans, LA, USA, 16–18 March 2020; pp. 153–155. [Google Scholar]
- Lenhart, M.; Spanghero, M.; Papadimitratos, P. Relay/replay attacks on GNSS signals. In Proceedings of the 14th ACM Conference on Security and Privacy in Wireless and Mobile Networks, Abu Dhabi, United Arab Emirates, 28 June–2 July 2021; pp. 380–382. [Google Scholar]
- Khan, A. Hacking the Drones. In Open Web Application Security Project [Electronic Resource]; OWASP: Bel Air, MD, USA, 2016. [Google Scholar]
- Restituyo, R.; Hayajneh, T. Vulnerabilities and attacks analysis for military and commercial iot drones. In Proceedings of the 2018 9th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 8–10 November 2018; pp. 26–32. [Google Scholar]
- Reed, T.; Geis, J.; Dietrich, S. SkyNET: A 3G-Enabled Mobile Attack Drone and Stealth Botmaster; WOOT: Carrollton, TX, USA, 2011; pp. 28–36. [Google Scholar]
- Bunse, C.; Plotz, S. Security analysis of drone communication protocols. In Engineering Secure Software and Systems: 10th International Symposium, ESSoS 2018, Paris, France, 26–27 June 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 96–107. [Google Scholar]
- Hamamreh, J.M. Physical Layer Security Against Eavesdropping in the Internet of Drones (IoD) Based Communication Systems. Available online: http://acikerisim.antalya.edu.tr/handle/20.500.12566/894 (accessed on 10 June 2023).
- Li, K.; Lu, N.; Zheng, J.; Zhang, P.; Ni, W.; Tovar, E. BloothAir: A Secure Aerial Relay System Using Bluetooth Connected Autonomous Drones. ACM Trans. Cyber-Phys. Syst. 2021, 5, 1–22. [Google Scholar] [CrossRef]
- Dovgal, V.A.; Dovgal, D.V. Security Analysis of a Swarm of Drones Resisting Attacks by Intruders. Distance educational technologies. In Proceedings of the 5th International Scientific and Practical Conference, Yalta, Crimea, 22–25 September 2020; pp. 372–377. [Google Scholar]
- Rani, C.; Modares, H.; Sriram, R.; Mikulski, D.; Lewis, F.L. Security of unmanned aerial vehicle systems against cyber-physical attacks. J. Def. Model. Simul. 2016, 13, 331–342. [Google Scholar] [CrossRef]
- Fei, F.; Tu, Z.; Yu, R.; Kim, T.; Zhang, X.; Xu, D.; Deng, X. Cross-layer retrofitting of UAVs against cyber-physical attacks. In Proceedings of the 2018 IEEE International Conference on Robotics and Automation (ICRA), Brisbane, QLD, Australia, 21–25 May 2018; pp. 550–557. [Google Scholar]
- Vasconcelos, G.; Miani, R.S.; Guizilini, V.C.; Souza, J.R. Evaluation of dos attacks on commercial wi-fi-based uavs. Int. J. Commun. Netw. Inf. Secur. 2019, 11, 212–223. [Google Scholar] [CrossRef]
- Bonilla, C.A.T.; Parra, O.J.S.; Forero, J.H.D. Common security attacks on drones. Int. J. Appl. Eng. Res. 2018, 13, 4982–4988. [Google Scholar]
- Lin, C.; He, D.; Kumar, N.; Choo, K.K.R.; Vinel, A.; Huang, X. Security and privacy for the internet of drones: Challenges and solutions. IEEE Commun. Mag. 2018, 56, 64–69. [Google Scholar] [CrossRef]
- Desnitsky, V.; Rudavin, N.; Kotenko, I. Modeling and evaluation of battery depletion attacks on unmanned aerial vehicles in crisis management systems. In International Symposium on Intelligent and Distributed Computing; Springer: Berlin/Heidelberg, Germany, 2019; pp. 323–332. [Google Scholar]
- Eldosouky, A.; Ferdowsi, A.; Saad, W. Drones in distress: A game-theoretic countermeasure for protecting uavs against gps spoofing. IEEE Internet Things J. 2019, 7, 2840–2854. [Google Scholar] [CrossRef] [Green Version]
- Arteaga, S.P.; Hernández, L.A.M.; Pérez, G.S.; Orozco, A.L.S.; Villalba, L.J.G. Analysis of the GPS spoofing vulnerability in the drone 3DR solo. IEEE Access 2019, 7, 51782–51789. [Google Scholar] [CrossRef]
- Khan, S.Z.; Mohsin, M.; Iqbal, W. On GPS spoofing of aerial platforms: A review of threats, challenges, methodologies, and future research directions. PeerJ Comput. Sci. 2021, 7, e507. [Google Scholar] [CrossRef]
- Arthur, M.P. Detecting signal spoofing and jamming attacks in UAV networks using a lightweight IDS. In Proceedings of the 2019 International Conference on Computer, Information and Telecommunication Systems (CITS), Beijing, China, 28–31 August 2019; pp. 1–5. [Google Scholar]
- Chapman, A. GPS Spoofing. ECE Senior Capstone Project. 2017. Available online: https://sites.tufts.edu/eeseniordesignhandbook/files/2017/05/Red_Chapman.pdf (accessed on 1 June 2023).
- Mead, J.; Bobda, C.; Whitaker, T.J. Defeating drone jamming with hardware sandboxing. In Proceedings of the 2016 IEEE Asian Hardware-Oriented Security and Trust (AsianHOST), Yilan, Taiwan, 19–20 December 2016; pp. 1–6. [Google Scholar]
- Pirayesh, H.; Zeng, H. Jamming attacks and anti-jamming strategies in wireless networks: A comprehensive survey. arXiv 2021, arXiv:2101.00292. [Google Scholar] [CrossRef]
- Li, Z.; Lu, Y.; Shi, Y.; Wang, Z.; Qiao, W.; Liu, Y. A dyna-q-based solution for uav networks against smart jamming attacks. Symmetry 2019, 11, 617. [Google Scholar] [CrossRef] [Green Version]
- Leonardi, M.; Strohmeier, M.; Lenders, V. On Jamming Attacks in Crowdsourced Air Traffic Surveillance. IEEE Aerosp. Electron. Syst. Mag. 2021, 36, 44–54. [Google Scholar] [CrossRef]
- Mead, J. Prevention of Drone Jamming Using Hardware Sandboxing; University of Arkansas: Fayetteville, AR, USA, 2016. [Google Scholar]
- Wu, Q.; Mei, W.; Zhang, R. Safeguarding wireless network with UAVs: A physical layer security perspective. IEEE Wirel. Commun. 2019, 26, 12–18. [Google Scholar] [CrossRef] [Green Version]
- Rojas Viloria, D.; Solano-Charris, E.L.; Muñoz-Villamizar, A.; Montoya-Torres, J.R. Unmanned aerial vehicles/drones in vehicle routing problems: A literature review. Int. Trans. Oper. Res. 2021, 28, 1626–1657. [Google Scholar] [CrossRef]
- Dhein, G.; Zanetti, M.S.; de Araújo, O.C.B.; Cardoso, G., Jr. Minimizing dispersion in multiple drone routing. Comput. Oper. Res. 2019, 109, 28–42. [Google Scholar] [CrossRef]
- Pu, C. Jamming-resilient multipath routing protocol for flying ad hoc networks. IEEE Access 2018, 6, 68472–68486. [Google Scholar] [CrossRef]
- Salamh, F.E.; Karabiyik, U.; Rogers, M. A Constructive DIREST Security Threat Modeling for Drone as a Service. J. Digit. Forensics Secur. Law 2021, 16, 2. [Google Scholar] [CrossRef]
- Petrovsky, O.; Prague, V. Attack on the drones. In Proceedings of the Virus Bulletin Conference, Prague, Czech Republic, 30 September–2 October 2015; p. 16. [Google Scholar]
- Gregory, T.S.; Tse, Z.T.H.; Lewis, D. Drones: Balancing risk and potential. Science 2015, 347, 1323. [Google Scholar] [CrossRef]
- Salamh, F.E.; Karabiyik, U.; Rogers, M.K.; Matson, E.T. Unmanned Aerial Vehicle Kill Chain: Purple Teaming Tactics. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 27–30 January 2021; pp. 1081–1087. [Google Scholar]
- Dangwal, A. 1st Evidence Of Russia-Operated Iranian Suicide Drone Emerges In Ukraine; Kiev Claims Downing Shahed-136 UAV. 2022. Available online: https://eurasiantimes.com/1st-evidence-of-russia-operated-iranian-drones-emerges-in-ukraine/ (accessed on 5 June 2023).
- Wilson, R.L. Ethical issues with use of drone aircraft. In Proceedings of the IEEE 2014 International Symposium on Ethics in Engineering, Science, and Technology, Chicago, IL, USA, 23–24 May 2014; p. 56. [Google Scholar]
- Vattapparamban, E.; Güvenç, İ.; Yurekli, A.İ.; Akkaya, K.; Uluağaç, S. Drones for smart cities: Issues in cybersecurity, privacy, and public safety. In Proceedings of the 2016 International Wireless Communications and Mobile Computing Conference (IWCMC), Paphos, Cyprus, 5–9 September 2016; pp. 216–221. [Google Scholar]
- Motlagh, N.H.; Taleb, T.; Arouk, O. Low-altitude unmanned aerial vehicles-based internet of things services: Comprehensive survey and future perspectives. IEEE Internet Things J. 2016, 3, 899–922. [Google Scholar] [CrossRef]
- Goddemeier, N.; Daniel, K.; Wietfeld, C. Role-based connectivity management with realistic air-to-ground channels for cooperative UAVs. IEEE J. Sel. Areas Commun. 2012, 30, 951–963. [Google Scholar] [CrossRef]
- Bohagen, F.; Orten, P.; Oien, G.E. Design of optimal high-rank line-of-sight MIMO channels. IEEE Trans. Wirel. Commun. 2007, 6, 1420–1425. [Google Scholar] [CrossRef]
- Mitchell, R.; Chen, R. Adaptive intrusion detection of malicious unmanned air vehicles using behavior rule specifications. IEEE Trans. Syst. Man Cybern. Syst. 2013, 44, 593–604. [Google Scholar] [CrossRef]
- Son, Y.; Shin, H.; Kim, D.; Park, Y.; Noh, J.; Choi, K.; Choi, J.; Kim, Y. Rocking drones with intentional sound noise on gyroscopic sensors. In Proceedings of the 24th USENIX Security Symposium (USENIX Security 15), Washington, DC, USA, 12–14 August 2015; pp. 881–896. [Google Scholar]
- Rana, T.; Shankar, A.; Sultan, M.K.; Patan, R.; Balusamy, B. An intelligent approach for UAV and drone privacy security using blockchain methodology. In Proceedings of the 2019 9th International Conference on Cloud Computing, Data Science Engineering (Confluence), Noida, India, 10–11 January 2019; pp. 162–167. [Google Scholar]
- Cho, S.M.; Hong, E.; Seo, S.H. Random number generator using sensors for drone. IEEE Access 2020, 8, 30343–30354. [Google Scholar] [CrossRef]
- Dey, V.; Pudi, V.; Chattopadhyay, A.; Elovici, Y. Security vulnerabilities of unmanned aerial vehicles and countermeasures: An experimental study. In Proceedings of the 2018 31st International Conference on VLSI Design and 2018 17th International Conference on Embedded Systems (VLSID), Pune, India, 6–10 January 2018; pp. 398–403. [Google Scholar]
- Li, L.W.; Lugou, F.; Apvrille, L. Security modeling for embedded system design. In Graphical Models for Security, Proceedings of the 4th International Workshop, GraMSec 2017, Santa Barbara, CA, USA, 21 August 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 99–106. [Google Scholar]
- Pojsomphong, N.; Visoottiviseth, V.; Sawangphol, W.; Khurat, A.; Kashihara, S.; Fall, D. Investigation of Drone Vulnerability and its Countermeasure. In Proceedings of the 2020 IEEE 10th Symposium on Computer Applications Industrial Electronics (ISCAIE), Penang, Malaysia, 18–19 April 2020; pp. 251–255. [Google Scholar]
- Kim, K.; Kang, Y. Drone security module for UAV data encryption. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 21–23 October 2020; pp. 1672–1674. [Google Scholar]
- Thangavelu, S.; Janczewski, L.; Peko, G.; Sundaram, D. A Dynamic Security-dedicated Approach to Commercial Drone Vulnerabilities, Threat Vectors and Their Mitigation. In Proceedings of the 2020 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 16–18 December 2020; pp. 1054–1059. [Google Scholar]
- Teng, L.; Jianfeng, M.; Pengbin, F.; Yue, M.; Xindi, M.; Jiawei, Z.; Gao, C.; Di, L. Lightweight security authentication mechanism towards uav networks. In Proceedings of the 2019 International Conference on Networking and Network Applications (NaNA), Daegu, Republic of Korea, 10–13 October 2019; pp. 379–384. [Google Scholar]
- Watkins, L.; Hamilton, D.; Kornegay, K.; Rubin, A. Triaging Autonomous Drone Faults By Simultaneously Assuring Autonomy and Security. In Proceedings of the 2021 55th Annual Conference on Information Sciences and Systems (CISS), Baltimore, MD, USA, 24–26 March 2021; pp. 1–6. [Google Scholar]
- Nisa, C.; Sudarsono, A.; Yuliana, M. Zero Knowledge Authentication Modification for Drone and Server Communication Security. J. Mantik 2021, 5, 1019–1029. [Google Scholar]
- Mikhailova, V.D.; Shulika, M.G.; Basan, E.S.; Peskova, O.Y. Security architecture for UAV. In Proceedings of the 2021 Ural Symposium on Biomedical Engineering, Radioelectronics and Information Technology (USBEREIT), Yekaterinburg, Russia, 13–14 May 2021; pp. 0431–0434. [Google Scholar]
- Sharma, V.; Jayakody, D.K.; You, I.; Kumar, R.; Li, J. Secure and efficient context-aware localization of drones in urban scenarios. IEEE Commun. Mag. 2018, 56, 120–128. [Google Scholar] [CrossRef]
- Hoang, T.M.; Nguyen, N.M.; Duong, T.Q. Detection of eavesdropping attack in UAV-aided wireless systems: Unsupervised learning with one-class SVM and k-means clustering. IEEE Wirel. Commun. Lett. 2019, 9, 139–142. [Google Scholar] [CrossRef] [Green Version]
- Zhang, G.; Wu, Q.; Cui, M.; Zhang, R. Securing UAV communications via trajectory optimization. In Proceedings of the GLOBECOM 2017-2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar]
- Vasconcelos, G.; Carrijo, G.; Miani, R.; Souza, J.; Guizilini, V. The impact of DoS attacks on the AR. Drone 2.0. In Proceedings of the 2016 XIII Latin American Robotics Symposium and IV Brazilian Robotics Symposium (LARS/SBR), Recife, Brazil, 8–12 October 2016; pp. 127–132. [Google Scholar]
- Muzzi, F.A.G.; de Mello Cardoso, P.R.; Pigatto, D.F.; Branco, K.R.L.J.C. Using Botnets to provide security for safety critical embedded systems-a case study focused on UAVs. J. Phys. Conf. Ser. 2015, 633, 012053. [Google Scholar] [CrossRef] [Green Version]
- Choudhary, G.; Sharma, V.; You, I.; Yim, K.; Chen, R.; Cho, J.H. Intrusion detection systems for networked unmanned aerial vehicles: A survey. In Proceedings of the 2018 14th International Wireless Communications Mobile Computing Conference (IWCMC), Limassol, Cyprus, 25–29 June 2018; pp. 560–565. [Google Scholar]
- He, S.; Wu, Q.; Liu, J.; Hu, W.; Qin, B.; Li, Y.N. Secure communications in unmanned aerial vehicle network. In Information Security Practice and Experience, Proceedings of the 13th International Conference, ISPEC 2017, Melbourne, VIC, Australia, 13–15 December 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 601–620. [Google Scholar]
- Rodday, N.M.; Schmidt, R.d.O.; Pras, A. Exploring security vulnerabilities of unmanned aerial vehicles. In Proceedings of the NOMS 2016-2016 IEEE/IFIP Network Operations and Management Symposium, Istanbul, Turkey, 25–29 April 2016; pp. 993–994. [Google Scholar]
- Alladi, T.; Bansal, G.; Chamola, V.; Guizani, M. SecAuthUAV: A Novel Authentication Scheme for UAV-Ground Station and UAV-UAV Communication. IEEE Trans. Veh. Technol. 2020, 69, 15068–15077. [Google Scholar] [CrossRef]
- Shoufan, A.; AlNoon, H.; Baek, J. Secure communication in civil drones. In Information Systems Security and Privacy, Proceedings of the First International Conference, ICISSP 2015, Angers, France, 9–11 February 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 177–195. [Google Scholar]
- Koubâa, A.; Allouch, A.; Alajlan, M.; Javed, Y.; Belghith, A.; Khalgui, M. Micro air vehicle link (mavlink) in a nutshell: A survey. IEEE Access 2019, 7, 87658–87680. [Google Scholar] [CrossRef]
- Khan, N.A.; Jhanjhi, N.Z.; Brohi, S.N.; Nayyar, A. Emerging use of UAV’s: Secure communication protocol issues and challenges. In Drones in Smart-Cities; Elsevier: Amsterdam, The Netherlands, 2020; pp. 37–55. [Google Scholar]
- García-Magariño, I.; Lacuesta, R.; Rajarajan, M.; Lloret, J. Security in networks of unmanned aerial vehicles for surveillance with an agent-based approach inspired by the principles of blockchain. Ad. Hoc. Netw. 2019, 86, 72–82. [Google Scholar] [CrossRef]
- Highnam, K.; Angstadt, K.; Leach, K.; Weimer, W.; Paulos, A.; Hurley, P. An uncrewed aerial vehicle attack scenario and trustworthy repair architecture. In Proceedings of the 2016 46th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Workshop (DSN-W), Toulouse, France, 28 June–1 July 2016; pp. 222–225. [Google Scholar]
- Choudhary, G.; Sihag, V.; Gupta, S.; Shandilya, S.K. Aviation attacks based on ILS and VOR vulnerabilities. J. Surveill. Secur. Saf. 2022, 3, 27–40. [Google Scholar] [CrossRef]
- Yang, H.; Yao, M.; Xu, Z.; Liu, B. LHCSAS: A lightweight and highly-compatible solution for ADS-B security. In Proceedings of the GLOBECOM 2017-2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–7. [Google Scholar]
- Yang, H.; Zhou, Q.; Yao, M.; Lu, R.; Li, H.; Zhang, X. A practical and compatible cryptographic solution to ADS-B security. IEEE Internet Things J. 2018, 6, 3322–3334. [Google Scholar] [CrossRef]
- Dave, G.; Choudhary, G.; Sihag, V.; You, I.; Choo, K.K.R. Cyber security challenges in aviation communication, navigation, and surveillance. Comput. Secur. 2022, 112, 102516. [Google Scholar] [CrossRef]
- You, I.S.; Sharma, V.; Choudhary, G.; KO, Y.H. Method for Verifying Drone Included in Industrial Internet of Things System, by Using Petri-Net Modeling. U.S. Patent App. 17/255,497, 9 September 2021. [Google Scholar]
- Baig, Z.; Khan, M.A.; Mohammad, N.; Brahim, G.B. Drone forensics and machine learning: Sustaining the investigation process. Sustainability 2022, 14, 4861. [Google Scholar] [CrossRef]
- Diagnosing Problems Using Logs—Copter Documentation. Available online: https://ardupilot.org/copter/docs/common-diagnosing-problems-using-logs.html (accessed on 8 June 2023).
- ExifTool by Phil Harvey. Available online: https://exiftool.org/ (accessed on 22 June 2023).
- GeoPlayer. Available online: https://www.mathworks.com/help/driving/ref/geoplayer.html (accessed on 4 June 2023).
- Azhar, M.; Barton, T.E.A.; Islam, T. Drone forensic analysis using open source tools. J. Digit. Forensics Secur. Law 2018, 13, 6. [Google Scholar] [CrossRef] [Green Version]
- Stanković, M.; Mirza, M.M.; Karabiyik, U. UAV Forensics: DJI Mini 2 Case Study. Drones 2021, 5, 49. [Google Scholar] [CrossRef]
- Roder, A.; Choo, K.K.R.; Le-Khac, N.A. Unmanned aerial vehicle forensic investigation process: Dji phantom 3 drone as a case study. arXiv 2018, arXiv:1804.08649. [Google Scholar]
- Llewellyn, M. Dji Phantom 3-Drone Forensic Data Exploration; Edith Cowan University: Perth, Australia, 2017. [Google Scholar]
- Renduchintala, A.; Jahan, F.; Khanna, R.; Javaid, A.Y. A comprehensive micro unmanned aerial vehicle (UAV/Drone) forensic framework. Digit. Investig. 2019, 30, 52–72. [Google Scholar] [CrossRef]
- Kao, D.Y.; Chen, M.C.; Wu, W.Y.; Lin, J.S.; Chen, C.H.; Tsai, F. Drone Forensic Investigation: DJI Spark Drone as A Case Study. Procedia Comput. Sci. 2019, 159, 1890–1899. [Google Scholar] [CrossRef]
- Iqbal, F.; Yankson, B.; AlYammahi, M.A.; AlMansoori, N.; Qayed, S.M.; Shah, B.; Baker, T. Drone forensics: Examination and analysis. Int. J. Electron. Secur. Digit. Forensics 2019, 11, 245–264. [Google Scholar] [CrossRef] [Green Version]
- Barton, T.E.A.; Azhar, M. Open source forensics for a multi-platform drone system. In Digital Forensics and Cyber Crime: 9th International Conference, ICDF2C 2017, Prague, Czech Republic, 9–11 October 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 83–96. [Google Scholar]
- The CFReDS Project|Drone Data Set. Available online: https://cfreds-archive.nist.gov/ (accessed on 12 June 2023).
- Swinney, C.J.; Woods, J.C. DroneDetect Dataset: A Radio Frequency dataset of Unmanned Aerial System (UAS) Signals for Machine Learning Detection & Classification. IEEE Dataport 2021. [Google Scholar] [CrossRef]
- Sambolek, S.; Ivasic-Kos, M. Search and Rescue Image Dataset for Person Detection—SARD. IEEE Dataport 2021. [Google Scholar] [CrossRef]
- Ezuma, M.; Erden, F.; Anjinappa, C.K.; Ozdemir, O.; Guvenc, I. Drone Remote Controller RF Signal Dataset. IEEE Dataport 2020. [Google Scholar] [CrossRef]
- Vera-Amaro, R.; Burke, M.; Saad, W. Coordinated UAVs for payload delivery. IEEE Dataport 2021. [Google Scholar] [CrossRef]
- Svanström, F.; Alonso-Fernandez, F.; Englund, C. A dataset for multi-sensor drone detection. Data Brief 2021, 39, 107521. [Google Scholar] [CrossRef]
- Whelan, J.; Sangarapillai, T.; Minawi, O.; Almehmadi, A.; El-Khatib, K. UAV Attack Dataset. IEEE Dataport 2020. [Google Scholar] [CrossRef]
- Hsu, H.J.; Chen, K.T. DroneFace: An open dataset for drone research. In Proceedings of the 8th ACM on Multimedia Systems Conference, Taipei, Taiwan, 20–23 June 2017; pp. 187–192. [Google Scholar]
- Li, J.; Murray, J.; Ismaili, D.; Schindler, K.; Albl, C. Reconstruction of 3D ight trajectories from ad-hoc camera networks. In Proceedings of the 2020 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Las Vegas, NV, USA, 24 October–24 January 2020; pp. 1621–1628. [Google Scholar]
- Aksoy, M.; Orak, A.S.; Özkan, H.M.; Selimoğlu, B. Drone dataset: Amateur unmanned air vehicle detection. Mendeley Data 2019, 4. [Google Scholar] [CrossRef]
- Jones, S.; DeClerck, F.; Fremier, A.; Ouedraogo, I. Phantom III drone imagery. Harv. Dataverse 2018. [Google Scholar] [CrossRef]
- Mantas, E.; Patsakis, C. Who watches the new watchmen? The challenges for drone digital forensics investigations. Array 2022, 14, 100135. [Google Scholar] [CrossRef]





| Drone Attacks | Tools/Mechanisms | Impact | Security Requirements | Attack Surfaces | Key Papers |
|---|---|---|---|---|---|
| Traffic Analysis and Network Stalking | SNMP, Packet sniffer, NetFlow | Privacy | Anti-spyware and packet filters | Z2 | [12,31,32,33,34,35,36] |
| Interception | Drone Monitoring Equipment, Acoustic Sensors | Privacy | Encryption technique | Z1,Z2,Z3,Z4 | [37,38] |
| Data Capturing and Forensics | Using serial connection, ExtractDJI, Datcon, Prodiscover Basic | Privacy | Encryption technique | Z1,Z2,Z5 | [15,39,40,41,42,43] |
| Location Tracing | Drone Monitoring Equipment, Acoustic Sensors, Radar | Privacy | Utilize counter-drone techniques | Z1,Z2 | [44,45,46] |
| Data/Information Leakage | Substitution and alteration, Modification, Duplication | Integrity | Use Secure channel switching and Encrypted data | Z1,Z2,Z3,Z4,Z5 | [47,48,49,50] |
| ACL Modifications | DroneSploit, hacking Tools | Integrity | Validate user-controllable input | Z1, Z2, Z3, Z5 | [51,52,53] |
| Man-In-Middle Attacks | Wifi attack, Remote-AT-Commands, WiFi Pineapple Nano, Raspberry Pi 3, Maldrone, SkyJack: | Integrity | a Public Key signed by a trusted Certificate Authority, encrypting the communication link, ensuring robust mutual authentication at both ends of the communication channel, and securely exchanging public keys | Z2,Z3 | [54,55,56,57] |
| Message Forgery | DroneSploit, Remote-AT-Commands | Integrity | Use Secure channel switching and Encrypted data | Z2,Z1,Z5 | [58,59,60] |
| Identity Spoofing and Key exploitations | Side-Channel Attacks, Weak Configuration, Vulnerability Exploitations | Confidentiality | Use secure and robust protocols with strong authentication | Z1,Z2,Z3,Z4,Z5 | [61,62,63] |
| Unauthorized Access and Controls | Drone Monitoring Equipment, DroneSploit, hacking Tools, Wifi attack, | Confidentiality | Utilize strong passwords | Z1,Z2,Z3,Z4,Z5 | [17,61,64,65] |
| Replay Attacks | Protocol Manipulation | Confidentiality | Use secure and robust protocols with strong authentication, and the authentication mechanism should include fresh message requests securely before data exchange or communication | Z2 | [66,67,68,69,70,71] |
| Eavesdropping | Sniffing tools, Password Cracking, Scrambling/Distortion | Confidentiality | Use encryption technique | Z2 | [12,23,58,72,73,74] |
| Physical Attacks | Drone Countermeasures Equipment, High Power Microwave (HPM) Devices, Nets & Net Guns, High-Energy Lasers | Availability | Use physical security techniques and Trusted Secure platforms | Z1,Z3,Z4 | [9,12,16,75,76] |
| DoS Attacks/DDoS Attacks | Use logic attacks and resource attacks, Ping of Death, SYN Flood, SYN Flood, x | Availability | Use freshness and Countermeasure scheme against the resource exhaustion. | Z2 | [12,77,78,79,80] |
| GPS Spoofing | Mock GPS with Joystick. Mock Locations, Fake GPS ByteRev, Fake GPS Go Location Spoofer. | Availability | Use anti-spoofing techniques | Z2,Z3 | [62,81,82,83,84,85] |
| Channel Jamming | HPM Devices, RF Jammers, Radio Frequency (RF) Analyzers, HackRF and BladeR | Availability | Beamforming and dynamic relaying, Multipoint transmission | Z1,Z2,Z3,Z4 | [46,86,87,88,89,90,91] |
| Routing Attacks | Waypoint alterations, black or grey hole attacks | Availability | Secure Routing, Self- adaptability Mechanism | Z1,Z2,Z3 | [17,37,92,93,94] |
| Use of Fake Drones | Key loggers, Third-party Violations, Firmware replacement attacks | Trust | Trust verification, Encryption and sensor firmware robustness, timely Update firmware | Z5 | [95,96,97,98] |
| Band | Frequency | Usage |
|---|---|---|
| L1 | 1575.42 MHz | L1 Civilian (L1C) |
| L2 | 1227.60 MHz | L2 Civilian (L2C) |
| L3 | 1381.05 MHz | Nuclear/Research |
| L4 | 1379.913 MHz | Research |
| L5 | 1176.45 MHz | Safety-of-life(SOL) Data |
| Authors | Security Solution | Used Mechanism | Security Threats | Targeted Zones | Security Considerations | Considered Parameters | Open Issues | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Z1 | Z2 | Z3 | Z4 | Z5 | C | I | A | NR | T | ||||||
| [107] | Drone privacy security | blockchain methodology | DL, DM, MIM | ✗ | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ | ✓ | Encryption, Time Stamp, Digital signature | Lack of Practical Adaptability and Not discussion respective factors |
| [108] | Random No. generator for cryptographic operations on the drone | Using sensor characteristics | WA, PS, SA, DM, DL | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | Dividing, shuffling, mixing and swap, power consumption, | Random number generation and cryptographic operation on a single will cause overhead, therefore the lightweight protocols are required. |
| [109] | Proposed countermeasure against the drone vulnerabilities | Validations, SDK authentication, and Encryptions | SA, DA, WiA, DoS | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | GPS Subframe Data, WPA security, MAC-Filtering and Hidden SSID | similar architecture and communication protocols need more security ad-ones |
| [110] | Drone embedded system security | SysML-Sec Methodology | MIM, PA, UA, DA | ✓ | ✗ | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | Attack graphs, formal verification | The security requirements need verification and validations before secure design. |
| [111] | Countermeasures and Policies against drone attacks * | Vulnerabilities identifications | DoS, MIM, DA, JA, SA | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | Multi-connection Prevention, telnet and FTP password, MAC Filtering | The adoption of multiple policies over a single framework are challenging. |
| [112] | Data Communication Security | Encryption of communication data and stored data | DL, DM, MIM | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | Drone Security Modules | Drone security module is not suitable for encrypting large-scale streaming |
| [113] | Conceptual process model for Secure drone manufacturing processes | Dynamic security dedicated approach | HA, PA, GA, JA | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | Vulnerability Analysis, Threat vector mapping | Drone specific manufacturing regulations needs more security policies to reduce the risk of threats. |
| [114] | Secure Authentication | ECC algorithm | DM, DL, MIM, RA, IA | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | Identity Authentication, Key consistency check | Limited power and computational capacity is an open challenge to adopt such authentication mechanisms. |
| [115] | Triaging Autonomous Drone Faults | AI-based assurance | DA, PA, SA, JA, WiA, BA | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | Assuring Autonomy, Inspection Autonomous Drones | Embedded System Anomalies, Sensor Anomalies, GPS, and Network anomalies are still open for considerations. |
| [116] | Authentication Security | Zero-Knowledge Authentication algorithm | BF, IA | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | Secret Key Generation | High distance between drone causes more authentication time than the usual. |
| [117] | Security Framework * | CPS threats | DA, DoS, BA, SA, WiA | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | Traffic analysis | Each attack affects the traffic landscape in its way and creates unique patterns of behavior change, and it is not easy to monitor such patterns at run time. |
| [118] | Secure localization | Hierarchical aspect-oriented Petri nets | WA, DA, SA, JA | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | Context-aware security | Run-Time Petri net-based formulations required context and secure routings. There are certain open challenges with the run-time coordination with context. |
| Layer | Reference | Attacks/Threats | Proposed Solutions | Limitations |
|---|---|---|---|---|
| Network | Eavesdropping | - datasets for predictive model training using K-means [119] - framework for generating training data from wireless signals and creating features of testing data from wireless connections [119] - Anti-Eavesdropping power control algorithm [120] | - Cryptography-based techniques require more processing and may result in high power usage. | |
| Network | [121,122] | DoS Attacks | - Intrusion Detection System [123] | - GCS datalink affected - False +ves and -ves with respect to anatomy-based IDS |
| Network | [37] | Forgery Attacks | - Creating a security architecture with multiple layers [25] | - In multi-UAVs, the network is more complex. |
| Network | [37] | Replay Attacks | - Implementing secure communication [124] - Using authentication frameworks [22,121] | - DoS attack is triggred with multiple requests |
| Network | [125] | Man-in-the-Middle (MITM) Attack | - Using fingerprinting techniques for verifying the authenticity of UAVs [126] - Encryption of control data for communication [127] | - Time-critical UAV systems face bandwidth limitations. |
| Transport | [128,129] | Protocol-based Attacks | - Using blockchain technique [130] - Using IDS techniques for security - framework for durability and trustworthiness that will enable the flight operation to be repaired even after attacks [131] | - The introduction of trade-offs between performance and security. |
| Artifacts | Source | Description | |
|---|---|---|---|
| Files | Images | M | Images captured |
| Videos | M | Videos captured | |
| Text files | M | Config and log information | |
| DAT files | M | Encrypted logs | |
| Cache files | M | Temporary info of recent flight | |
| Config files | M | Drone configuration | |
| Binary files | M | Executables and system files | |
| Exif Data | Timestamp | EL | Flight time info |
| GPS data | EL | Geo location info | |
| Altitude | L | Drone height during flight | |
| Altitude reference | L | Altitude of home location | |
| Latitude Longitude | L | Geo location data | |
| Thumbnails | M | Media file info | |
| Log data | Username | FM | user info |
| Email address | M | username | |
| Drone serial number | OM | Unique id of drone | |
| Country code | F | Location info | |
| Aircraft model | FO | Maker info | |
| Manufacturer | OF | Developer info | |
| Firmware version | F | Firmware info | |
| Controller ID | OFM | GCS unique id | |
| PII | Flight log data | L | Flight info |
| Black box files | FM | Drone logs and damage status | |
| Flight air time | L | Duration of flight | |
| Sensor data | LFM | Different sensor logs | |
| Battery status | L | Battery consumption status | |
| Home location | GL | Initial flight location | |
| GPS Tracks | EL | Flight path identifiers | |
| Controller commands | GF | Commands sent during flight | |
| System events | FL | User events on drone | |
| Last connected time | FL | Recent user activity | |
| Sensor Logs | GPS | LG | Location info |
| Magnetometer | FL | Guides drone for magnetic field | |
| Accelerometer | L | Acceleration info | |
| Barometer | L | Atmospheric pressure info | |
| Altimeter | L | Altitude info | |
| Gyroscope | L | Drone stability | |
| Speedometer | L | Speed info | |
| Tilt sensors | L | Measure axis tilt | |
| Camera sensors | LM | For image capture |
| Tools | Description | OS | Os | Pr | Fw | Papers | |
|---|---|---|---|---|---|---|---|
| Decoding | DCode | Timestamps decoder | W | ✓ | [8] | ||
| DatCon | Log Decoder for .dat files | MW | ✓ | [8,40,142,143,144] | |||
| Phantomhelp | Convert .dat and .txt to CSV | O | ✓ | [40] | |||
| CsvView | CSV file viewer | MW | ✓ | [40,141,144,145,146] | |||
| DROP | DAT file parser | LW | ✓ | [11] | |||
| Network | Nmap | Port scanning tool | LMW | ✓ | [15,141,147] | ||
| Aircrack-ng | Wi-Fi Network security tool. | LMW | ✓ | [147] | |||
| Wireshark | Deep packets analyzer | LMW | ✓ | [144] | |||
| Xplico | Network forensic analysis tool | L | ✓ | [144] | |||
| Network Miner | Network sniffer and capturing tool | LMW | ✓ | [144] | |||
| Imaging and Analysis | dcfldd | dd + metadata to check integrity | L | ✓ | [144] | ||
| Bitwalk | search binary files | L | ✓ | [8,142] | |||
| UEFD 4PC | Mobile forensics framework | W | ✓ | [8,142] | |||
| Exiftool (GUI) | Checks the exif data of files | LMWO | ✓ | [8,10,15,141,142,144,145,146] | |||
| Autopsy | GUI version of Sleuth Kit | LMW | ✓ | [8,40,142,144] | |||
| FTK Imager | Imaging tool and data viewer | LMW | ✓ | [146] | |||
| Encase | Imaging and analysis tool | W | ✓ | [143] | |||
| Magnet AXIOM | Acquire and analyze evidence | W | ✓ | [8,142] | |||
| fsstat | Filesystem analysis | L | ✓ | [141,148] | |||
| fsck.f2fs | Checks and correct f2fs FS | L | ✓ | [141] | |||
| f2fs-tools | SSD and SD card analysis | L | ✓ | [141] | |||
| XRY | Analyze and recover information | W | ✓ | [147] | |||
| ExtractDJI | Extract and decompress .dat | MW | ✓ | [40] | |||
| Oxygen Forensics | Information extraction | W | ✓ | [147] | |||
| Miscellaneous | Litchi | Log data conversion | A | ✓ | [145] | ||
| HxD | Hexa decimal editor | W | ✓ | [8] | |||
| 010 editor | File content analysis | LMW | ✓ | [10] | |||
| DJI fly | Access to SkyPixel media | A | ✓ | [142] | |||
| Open WRT | Embedded devices traffic analysis | L | ✓ | [142] | |||
| Parben’s E3 Universal | Data processing and analysis | MW | ✓ | [40] | |||
| Kingo Rootkit | Android rooting | A | ✓ | [141,148] | |||
| BlueStacks | Android emulator | WM | ✓ | [146] | |||
| Winhex | Hex editor | W | ✓ | [10] | |||
| MediaInfo | Media file analysis | LMWO | ✓ | [10] | |||
| CyanogenMod OS | Custom rooted Android OS | A | ✓ | [141,148] | |||
| Visualization | Google Maps | Flight path with timestamp | ALMWO | ✓ | [145] | ||
| Google Earth | Flight path with timestamp | ALMWO | ✓ | [8,10,15,144,145] | |||
| GPS Visualizer | Geo data visualization | O | ✓ | [10] | |||
| Dashware | Telementry data representation | W | ✓ | [144] | |||
| ArcGIS PRO | 3D visualization | LMW | ✓ | [8] | |||
| WebFlightPath | Flight log parser | LMW | ✓ | [10] |
| Dataset | Remarks |
|---|---|
| CFReDS Drone Dataset [149] | Includes 82 drone images from 30 drone models. Forensic images of data storage areas, controller, connected mobile device, and computer. |
| Drone Detect [150] | Radio frequency dataset of DJI Mavic 2 Air S, DJI Mavic Pro, DJI Mavic Pro 2, DJI Inspire 2, DJI Mavic Mini, DJI Phantom 4, and the Parrot Disco. |
| SARD [151] | Search and Rescue Image dataset was created with the goal of identifying casualties and people in search and recovery operations in UAV photos and videos. Contains 1981 hand-tagged images retrieved from video frames in the collection. |
| Drone RF Signal [152] | Includes RF signals from several UAV remote controllers. There are 17 UAV radio controllers of eight multiple brands, each with 1000 RF signals lasting 0.25 milliseconds. |
| UAVs for payload delivery [153] | Dataset of payload delivery in a smart UAV delivery system. |
| Multi-Sensor Drone Detection [154] | UAVs included: a tiny version (Hubsan H107D+), a moderate drone (DJI Flame Wheel in quadcopter format), and a performance-grade model (DJI Flame Wheel in quadcopter configuration) (DJI Phantom 4 Pro). Includes 650 visible and infrared clips of UAVs, birds, aircraft, and choppers (365 IR and 285 visible). |
| UAV attack dataset [155] | The collection includes recordings from a normal flight and one in which the UAV is subjected to GPS spoofing and jamming. |
| DroneFace [156] | Face pictures acquired from a variety of angles and altitudes in an unrestricted atmosphere can be useful for future research into incorporating face detection and recognition methods into UAVs. |
| Drone Tracking [157] | Clips of a flying UAV being recorded using many commercial cameras and highly precise 3D UAV trajectory classification algorithm recorded by Fixposition’s exact real-time RTK system. Ground truth time synchronization and ground truth camera positions are also included in several clips. |
| Amateur UAV Detection [158] | Non-drone, UAV-like “negative” entities are included in the dataset. Yolov2-tiny and Yolov3-voc versions were utilized with this dataset. Working with Yolo design and the darknet platform is usually recommended. |
| Phantom III drone imagery [159] | The imagery in this collection was captured using a Phantom III drone. A DJI FC300S visible light camera as well as a Senterra 1.2MP GS-0002 6.05 mm near-infrared camera placed on the UAV produced two sets of images. It gives you an image log with the GPS location of the collection points. |
| Notations | Full Name |
|---|---|
| ADS-B | Automatic Dependent Surveillance-Broadcast |
| BLOS | Beyond Line-Of-Sight |
| EXIF | Exchangeable Image Format |
| FCB | Flight Control Board |
| GCS | Ground Control System |
| GSC | Ground Station Controller |
| GPS | Global Positioning System |
| JTAG | Joint Test Action Group |
| LOS | Line-Of-Sight |
| MITM | Man in the Middle |
| PII | Personal Identifiable Information |
| PMS | Power Management System |
| UAV | Unmanned Aerial Vehicle |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sihag, V.; Choudhary, G.; Choudhary, P.; Dragoni, N. Cyber4Drone: A Systematic Review of Cyber Security and Forensics in Next-Generation Drones. Drones 2023, 7, 430. https://doi.org/10.3390/drones7070430
Sihag V, Choudhary G, Choudhary P, Dragoni N. Cyber4Drone: A Systematic Review of Cyber Security and Forensics in Next-Generation Drones. Drones. 2023; 7(7):430. https://doi.org/10.3390/drones7070430
Chicago/Turabian StyleSihag, Vikas, Gaurav Choudhary, Pankaj Choudhary, and Nicola Dragoni. 2023. "Cyber4Drone: A Systematic Review of Cyber Security and Forensics in Next-Generation Drones" Drones 7, no. 7: 430. https://doi.org/10.3390/drones7070430








