A Framework for Synthetic Agetech Attack Data Generation
Abstract
:1. Introduction
2. Related Work
3. Threat Model
4. Datasets and Data Analysis
4.1. Agetech Attack Data
- Data from smart device used for aging in place (AIP).
- Data for sensor recordings not network traffic.
- Anomaly sensor recordings data caused by security attacks and not severe health conditions or faulty devices.
4.2. TON_IoT Data
4.2.1. Dataset Overview
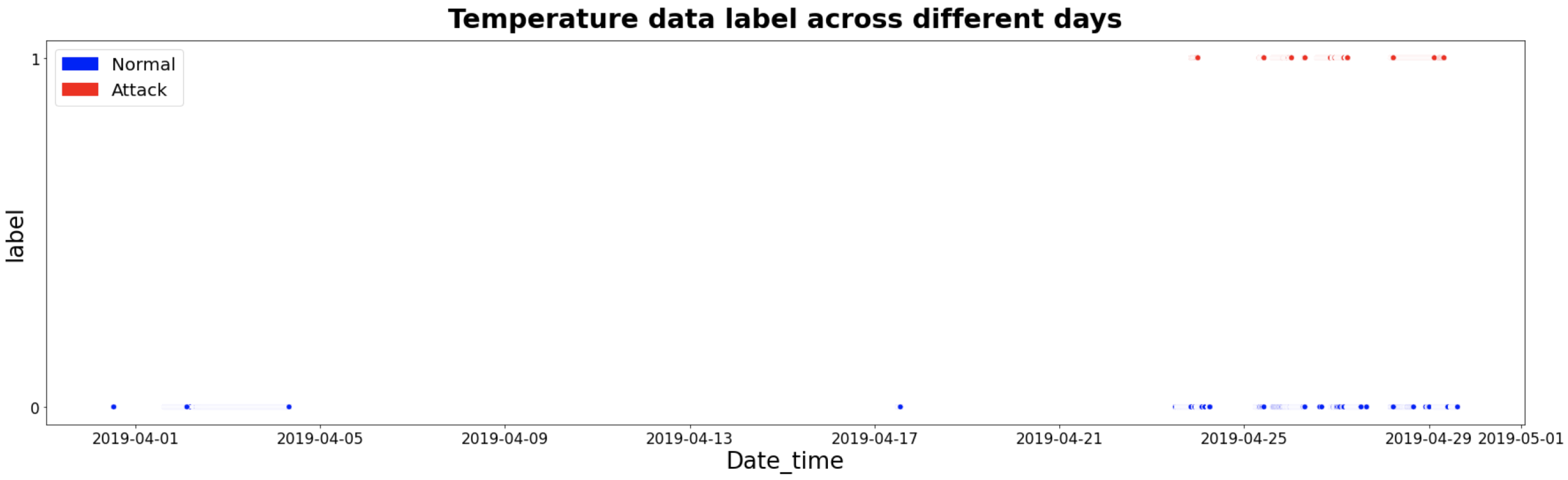
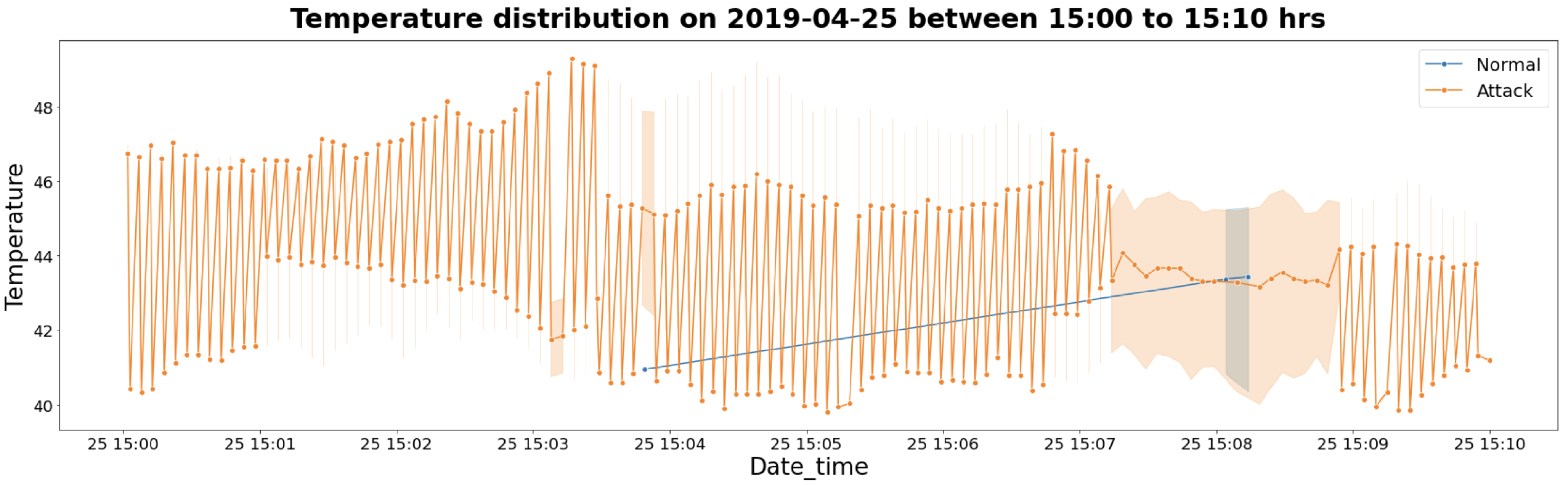
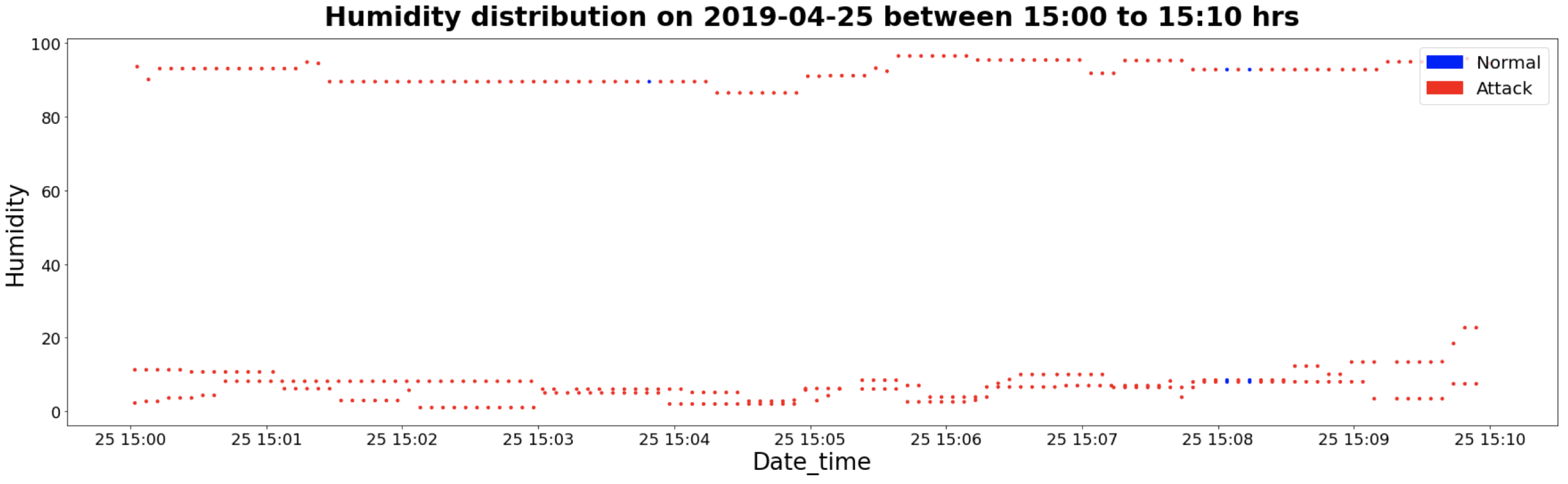
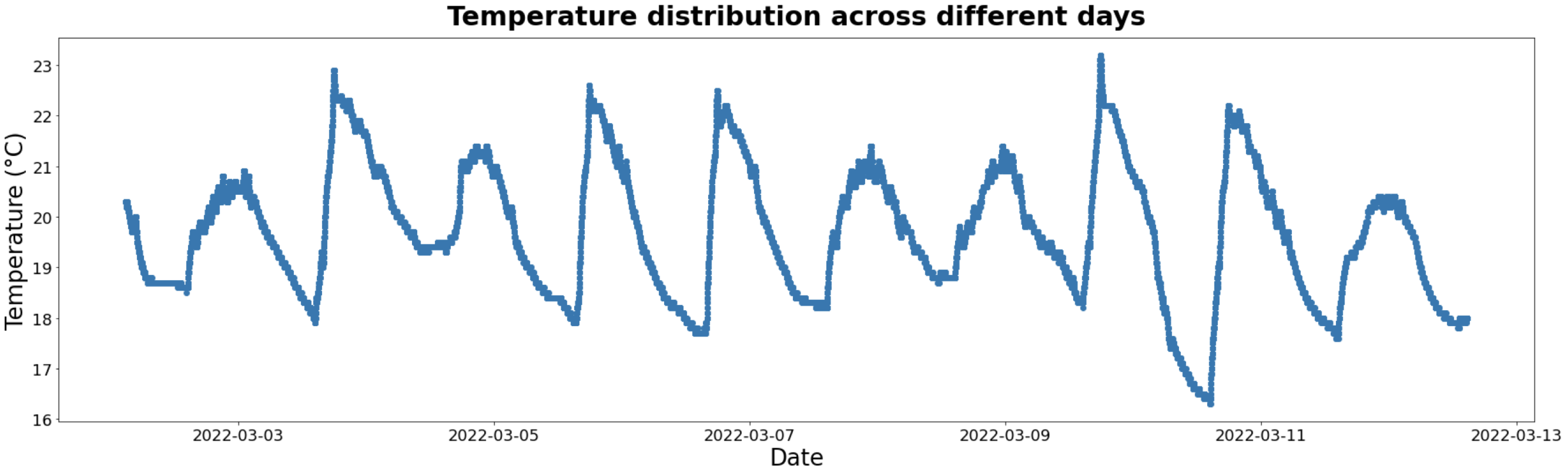
4.2.2. TON_IoT Weather Data—Temperature
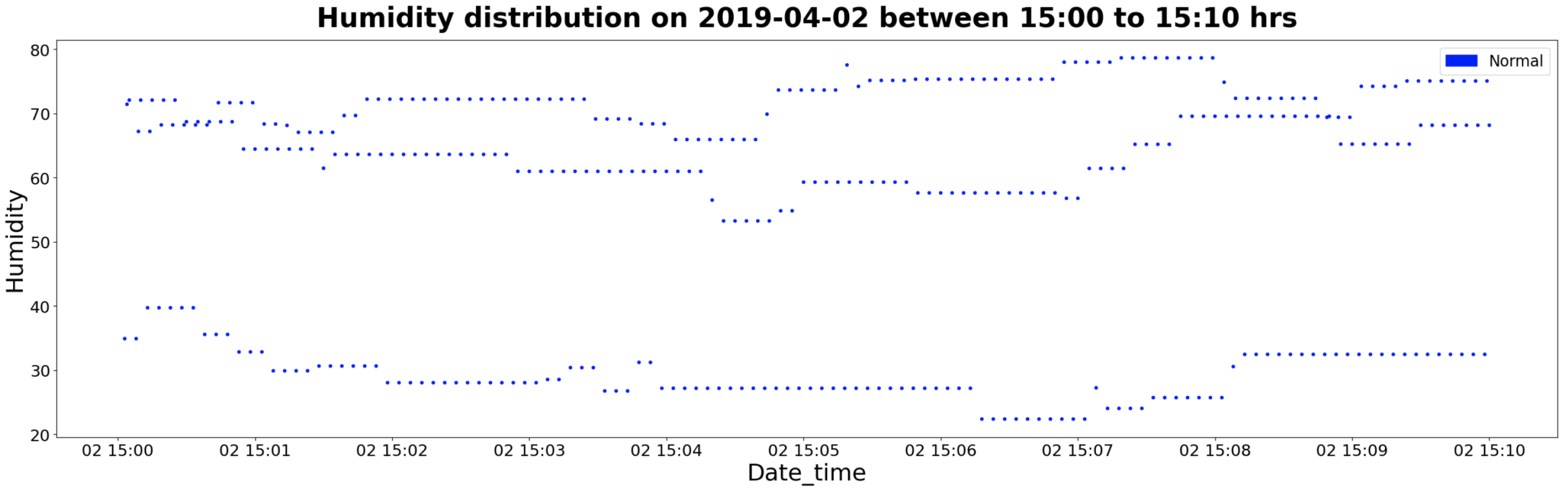
4.3. Normal Agetech Data from ISOT Lab
5. Proposed Data Generation Methods
5.1. Proposed Methods
5.1.1. Method 1: Changing the Pattern of Every Three Elements
5.1.2. Method 2: Using the Difference Borrowed from TON_IoT Data
- 1.
- From TON_IoT data:
- 2.
- On agetech data:
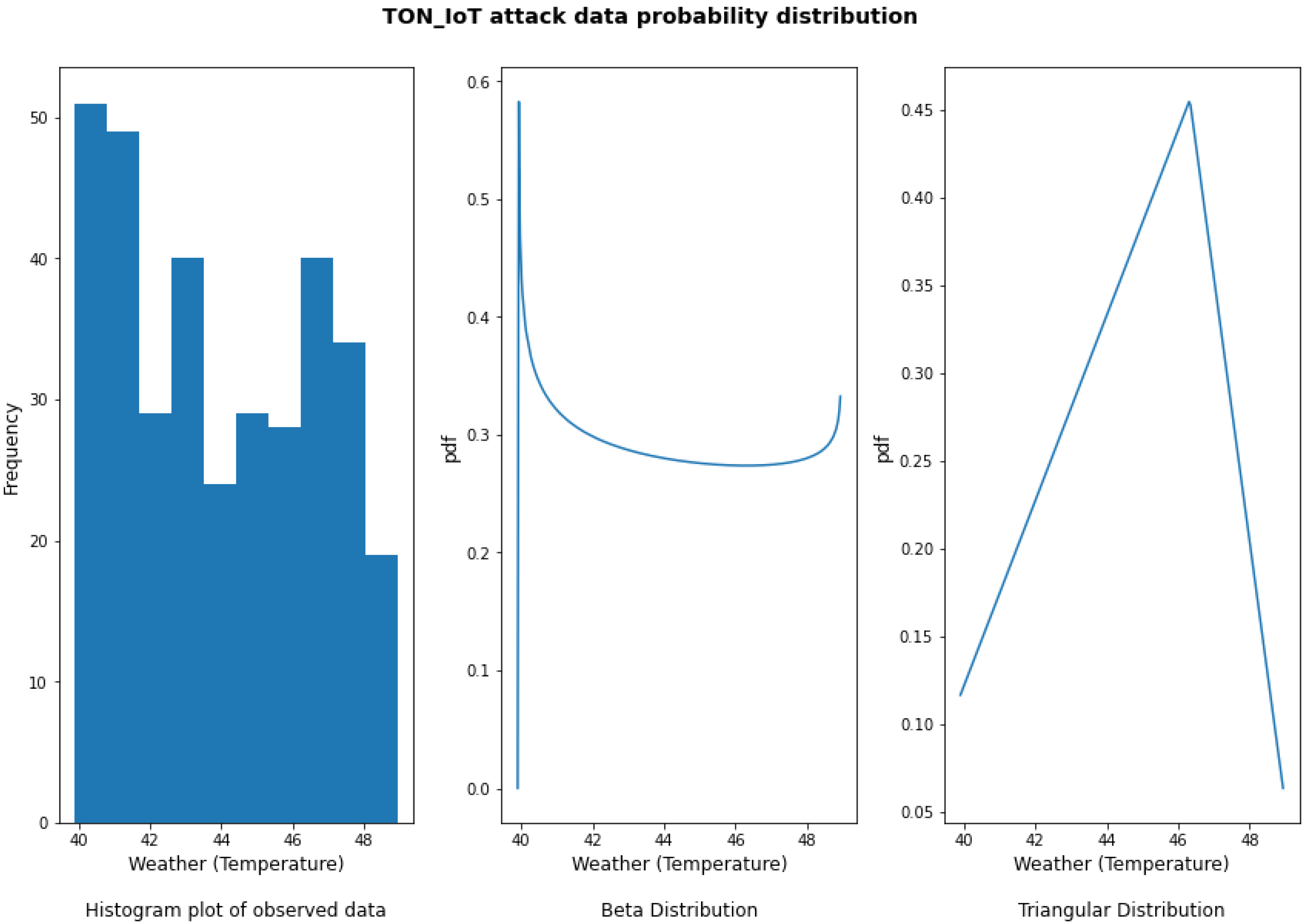
5.1.3. Method 3: Using Probability Distribution
5.1.4. Method 4: Using the Probabilistic AutoRegressive (PAR) Model
5.2. Data Validation
5.3. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- World Health Organization. Ageing and Health; World Health Organization: Geneva, Switzerland, 2022; Available online: https://www.who.int/news-room/fact-sheets/detail/ageing-and-health (accessed on 5 January 2023).
- Yamauchi, M.; Ohsita, Y.; Murata, M.; Ueda, K.; Kato, Y. Anomaly detection for smart home based on user behavior. In Proceedings of the 2019 IEEE International Conference On Consumer Electronics (ICCE), Las Vegas, NV, USA, 11–13 January 2019; pp. 1–6. [Google Scholar]
- Chimamiwa, G.; Alirezaie, M.; Pecora, F.; Loutfi, A. Multi-sensor dataset of human activities in a smart home environment. Data Brief 2021, 34, 106632. [Google Scholar] [CrossRef] [PubMed]
- Carnemolla, P. Ageing in place and the internet of things—How smart home technologies, the built environment and caregiving intersect. Vis. Eng. 2018, 6, 7. [Google Scholar] [CrossRef]
- Khaemba, N.; Traoré, I.; Mamun, M. Security and Privacy of IoT Devices for Aging in Place. In Artificial Intelligence for Cyber-Physical Systems Hardening; Springer International Publishing: Cham, Switzerland, 2023; pp. 181–201. [Google Scholar]
- Zhou, W.; Cao, X.; Li, X.; Sha, Y.; Chen, J.; Yan, Y.; Liu, X.; Kong, X. Attack sample generation algorithm based on dual discriminant model in industrial control system. J. Phys. Conf. Ser. 2021, 1828, 012123. [Google Scholar] [CrossRef]
- Pham, T.; Nguyen, Q.; Nguyen, X. Generating artificial attack data for intrusion detection using machine learning. In Proceedings of the Fifth Symposium On Information And Communication Technology, Hanoi, Vietnam, 4–5 December 2014; pp. 286–291. [Google Scholar]
- Belenko, V.; Krundyshev, V.; Kalinin, M. Synthetic datasets generation for intrusion detection in VANET. In Proceedings of the 11th International Conference On Security Of Information And Networks, Cardiff, United Kingdom, 10–12 September 2018; pp. 1–6. [Google Scholar]
- Sourav, S.; Chen, B. Distort to Detect, not Affect: Detecting Stealthy Sensor Attacks with Micro-distortion. In Proceedings of the 2021 IEEE International Conference On Communications, Control, And Computing Technologies For Smart Grids (SmartGridComm), Control, Aachen, Germany, 25–28 October 2021; pp. 412–418. [Google Scholar]
- Mahak, M.; Singh, Y. Threat modelling and risk assessment in internet of things: A review. In Proceedings of the Second International Conference On Computing, Communications, and Cyber-Security: IC4S 2020, Ghaziabad, India, 3–4 October 2020; pp. 293–305. [Google Scholar]
- What Is an IoT Device Vulnerability? Available online: https://www.fortinet.com/resources/cyberglossary/iot-device-vulnerabilities (accessed on 5 January 2023).
- Srihith, I.; Donald, A.; Srinivas, T.; Anjali, D.; Chandana, A. Firmware Attacks: The Silent Threat to Your IoT Connected Devices. Int. J. Adv. Res. Sci. Commun. Technol. (IJARSCT) 2023, 3, 145–154. [Google Scholar] [CrossRef]
- Rizvi, S.; Kurtz, A.; Pfeffer, J.; Rizvi, M. Securing the internet of things (IoT): A security taxonomy for IoT. In Proceedings of the 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 163–168. [Google Scholar]
- Kröger, J. Unexpected inferences from sensor data: A hidden privacy threat in the internet of things. In Internet Of Things. Information Processing in An Increasingly Connected World: First IFIP International Cross-Domain Conference, IFIPIoT 2018, Held at The 24th IFIP World Computer Congress, WCC 2018, Poznan, Poland, 18–19 September 2018; Revised Selected Papers 1; Springer: Cham, Switzerland, 2019; pp. 147–159. [Google Scholar]
- Gangolli, A.; Mahmoud, Q.; Azim, A. A systematic review of fault injection attacks on IOT systems. Electronics 2022, 11, 2023. [Google Scholar] [CrossRef]
- Zahra, S.; Chishti, M. Ransomware and internet of things: A new security nightmare. In Proceedings of the 2019 9th International Conference On Cloud Computing, Data Science & Engineering (Confluence), Uttar Pradesh, India, 10–11 January 2019; pp. 551–555. [Google Scholar]
- Moustafa, N. The TON_IoT Datasets|UNSW Research. 2019. Available online: https://research.unsw.edu.au/projects/toniot-datasets (accessed on 5 January 2023).
- Gulrajani, I.; Ahmed, F.; Arjovsky, M.; Dumoulin, V.; Courville, A. Improved training of wasserstein gans. In Proceedings of the Advances In Neural Information Processing Systems, Long Beach, CA, USA, 4–9 December 2017; Volume 30. [Google Scholar]
- Hu, W.; Tan, Y. Generating adversarial malware examples for black-box attacks based on GAN. arXiv 2017, arXiv:1702.05983. [Google Scholar]
- PAR Model. 2018. Available online: https://sdv.dev/SDV/user_guides/timeseries/par.html (accessed on 5 January 2023).











| Vulnerability | Possible Attack | Exploit | Impact | Mitigation |
|---|---|---|---|---|
| Weaknesses in services and protocols running on IoT device, faulty secure sockets layer (SSL) configuration | Man-in-the-middle (MITM) attack/Eavesdropping attack | Hacker intercepts and sends data or modifies previously sent data | Incorrect sensor records, disrupt normal function, spy or cause harm to the user | Strong encryption of communication |
| Default or easy passwords | Password attack (Brute force attack) | Attackers can guess passwords and gain access to device | Modify the device to whatever they want or destroy it | Use strong passwords especially passphrases |
| Insecure default settings and update mechanisms [11] | Firmware attack | Hacker cracks encryption keys or passwords used to secure firmware, Corrupt updates to compromise device | Loss of data, Device control, Malware installation, Physical damage of device, Attacker can maintain access to device for long because they are difficult to detect, Connected devices turned into bots [12] | Monitor the network for any suspicious activity, use strong passwords and keep firmware up to date |
| Insufficient sanitization of data input in the web interface | Cross-site scripting (XSS) attack | Executing of a malicious script through the web browser of the user | Attacker can hijack the user’s session and cause distributed denial of service (DDoS) [13] | Data validation of all input |
| Hidden sensors encapsulated in smart devices that do not need access permission unlike cameras, microphones and Global Positioning System (GPS), and these allow for covert surveillance of the person using the device [14] | Keystroke inference | Determine keyboard and touchscreen inputs based on accelerometer data, gyroscope data, micro-motions and ambient-light sensors | Compromise entire technological ecosystem of the user when sensitive information like location, activities or passwords are leaked through embedded sensors | Classify disregarded types of sensor data like data about motion and light as sensitive by default so that it can be properly protected |
| Logic blocks weaknesses that can be tampered with, secure boot and flash encryption that can be bypassed | Fault injection attack | Introduces glitches like electromagnetic injection, clock glitching and voltage glitching into the device hardware, causing abnormal behavior of the software [15] | Can disrupt the functioning of the system, negatively affect device drivers, change the behavior of application software and access control software | Make use of software vulnerability detection tools and employ multi-layer protection |
| Unsecured query entry field | Structured Query Language (SQL) injection | Attacker inputs an SQL query that consists of a valid request and malicious request that are also executed [13] | Can lead to privilege escalations and access to what they are not authorized to | Input validation and sanitization of code |
| Misconfigured IoT devices | Denial of Service (DoS) and Distributed Denial-of-Service (DDoS) | Use of a botnet to send many requests that overwhelms the device such that it can’t perform its normal functions | The device jams and becomes unusable or gets damaged | Have systems in place for automatic detection and filtering of malicious activity |
| Poorly designed or older software without proper validation of the size or format of the input it receives | Buffer overflow attack | Attacker sends an amount of data that is larger than the temporary data storage area causing the excess data to overwrite other parts of the program’s memory | Attacker can execute malicious code or take control of the system | Ensure there is proper input validation |
| Device lacks capability to check and verify what is being executed, device not secured with efficient security protocols | Ransomware attack | Malware can be stored in for example the wallpapers of a thermostat and once the user clicks on it, the attacker gains control of the system and tricks customer to send them money or gift card [16] | Attacker can control the operation of the device. Also they could gain access to other IoT devices connected to the same network | Avoid clicking on suspicious links, always update device firmware, restrict permissions on IoT device, employ multi-layer protection |
| Model | Accuracy | F-Beta Score |
|---|---|---|
| Random Forest | 0.9860 | 0.7593 |
| KNN | 0.9820 | 0.9402 |
| XGBoost | 0.9340 | 0.7593 |
| LightGBM | 0.9840 | 0.8824 |
| CatBoost | 0.9520 | 0.8286 |
| Model | Accuracy | F-Beta Score |
|---|---|---|
| Random Forest | 0.9860 | 0.9357 |
| KNN | 0.9760 | 0.8754 |
| XGBoost | 0.9860 | 0.9357 |
| LightGBM | 0.9940 | 0.9738 |
| CatBoost | 0.9940 | 0.9855 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khaemba, N.; Traoré, I.; Mamun, M. A Framework for Synthetic Agetech Attack Data Generation. J. Cybersecur. Priv. 2023, 3, 744-757. https://doi.org/10.3390/jcp3040033
Khaemba N, Traoré I, Mamun M. A Framework for Synthetic Agetech Attack Data Generation. Journal of Cybersecurity and Privacy. 2023; 3(4):744-757. https://doi.org/10.3390/jcp3040033
Chicago/Turabian StyleKhaemba, Noel, Issa Traoré, and Mohammad Mamun. 2023. "A Framework for Synthetic Agetech Attack Data Generation" Journal of Cybersecurity and Privacy 3, no. 4: 744-757. https://doi.org/10.3390/jcp3040033
APA StyleKhaemba, N., Traoré, I., & Mamun, M. (2023). A Framework for Synthetic Agetech Attack Data Generation. Journal of Cybersecurity and Privacy, 3(4), 744-757. https://doi.org/10.3390/jcp3040033





