Abstract
IoT security, also known as Internet of Things security, is an innovation component that focuses on protecting connected devices and systems on the Internet of Things (IoT). There are several fields which relate to the IoT framework such as computers, mechanical and computerized machines, objects, creatures, and people. Each thing has a unique identifier and the ability to transfer data across an organization. The Internet of Things organizations help to obtain a practical advantage by taking care of the hardships of consolidating wearables, sensors, associations, cloud, and applications without choosing security. Development is stressed over partner contraptions with each other to work with the correspondence between them. The devices that are related will really need to share the information that can be used as a commitment by any contraption that is dependent upon various contraptions for input. It is known as the Trap of Things, like the Internet. This development requires certifications to sort out among contraptions. Different industry-unequivocal data and IoT development expertise cover firmware improvement, transportability, conveyed registering, and data assessment, for making the market space an impressive range for end clients. The end clients receive soft assembled decisions concerning solid data assessment in IoT organizations. Nowadays, many IoT applications, computations, and organizations are utilizing services over the Internet. These are the most important applications that need security from the cyber web. If cyberattacks are going on in IoT devices, security is a must for the end users.
1. Introduction
The new exploration towards the IoT is an organization of gadgets that are associated with the web for moving and detecting the information absent from a lot of human intercession.; since the IoT should make the gadget savvy, this innovation is utilized by different businesses and spaces to seek administrations like clinical treatment, controllers, improving light insight, the auto industry, a combination of man-made intelligence application, to obtain a superior customized insight, and so on. These administrations are named as IoT administrations in the IoT environment [1]. The IoT administrations which utilize different layered IoT models are characterized in a safe way. The primary layer is shown in Figure 1 for IoT gadgets and involves interfacing them to the organization. The subsequent layer fabricates a decentralized organization to keep information handling near where it starts, which takes into consideration quick neighborhood choices. In the third layer, an information handling climate for heterogeneous IoT information is demonstrated, applying AI and information science calculations to recognize examples and patterns required for the arrangement of the required issues. The fourth layer makes various sorts of applications to serve the envisioned information experiences [2]. The fifth layer makes web and portable applications empowering the controller of IoT gadgets. IoT application of the board is for reasonable activity like speedy recognizable proof of information quality, application accessibility, and utilization issues [3].
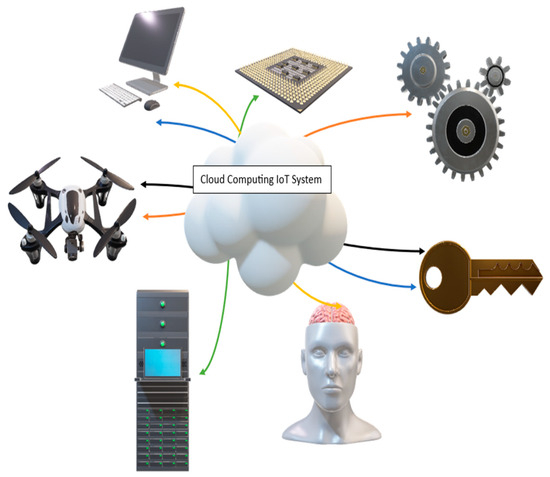
Figure 1.
Basic structure of IoT system.
The social affair of the IoT and useful improvement contraptions have detonated as of late. In any case, while coordinated gadgets can expand the effectiveness and perceptible quality into an alliance’s endeavors, they likewise go with essential security wagers that widen an association’s assault surface [4]. The IoT and composed useful improvement contraptions have changed into a fundamental piece of many affiliations’ endeavors and key positions. In any case, as these contraptions become more implanted inside an affiliation, they address a making bet to the security of a connection’s information and different gadgets on its affiliation. There have, as of late, been many events of IoT gadgets being hacked when criminals have looked for IoT security weaknesses and been convincing. Several affiliations have even had their state-of-the-art robots and materials connected with them hacked. The explanation is that designers can change control-circle limits, play with creation thinking, change the robot’s state, and essentially more. A party of specialists chose to show how much damage a hacked robot can truly do. IoT security is gathering systems, procedures, and instruments to protect these contraptions from becoming compromised. Amusingly, the receptiveness typical for the IoT makes these devices continuously frail against cyberattacks [5].
2. IoT Services
The Internet of Things should make gadgets savvy by upgrading their effectiveness. Different enterprises and spaces have utilized this innovation to make the errand more straightforward [6]. Figure 2 deals with the issues of the IoT services within the computing system. The following are a portion of the significant administrations given by way of the Internet of Things [7,8].
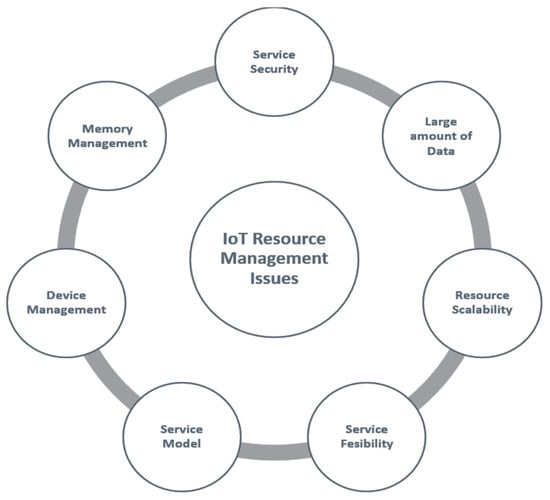
Figure 2.
IoT service management system.
- There are gadgets that have been created utilizing the IoT that help the patient during treatment. From one viewpoint, being situated in the clinic to seek the treatment is excessively costly.; then again, utilizing such IoT-empowered gadgets makes it reasonable for patients to proceed with the treatment for a minimal price. The most involved gadget in this space is utilized to battle against diabetes.
- The IoT allows us to control gadgets that are found geologically far away. It is an element of gadgets associated through the IoT that they can take input from different gadgets that are associated through the web. Generally, cell phones are being utilized regularly to remotely send guidelines to the gadget. In such cases, typically, the web is preferred, while on the off chance that the gadgets are associated with a similar organization, they can utilize Wi-Fi.
- The IoT can be customized to carry a few functionalities to make the user’s experience and cooperation with light-producing gadgets the best. We can consider making the light gleam so it truly does illuminate just when somebody is scrolling, which could prompt saving parcels to drive utilization. It may very well be accomplished by making the lighting gadgets sufficiently bright to comprehend when to sparkle and follow an example.
- The machines utilized these days are too complicated to even think about understanding. By utilizing the IoT, a framework could be fostered that can recognize disappointment in the machines. Such machines are utilized to caution the client regarding the ill-advised working of any piece of the gadget. This will be useful to guarantee the nature of the item. It can likewise prompt protection of the clients of the machine from a lethal mishap.
- Involving IoT-empowered gadgets within the climate could be extremely shrewd and ideal. Brilliant gadgets lower the utilization of assets and upgrade productivity. This could prompt a superior working setting, as the spot should be well developed by utilizing less assets, and the IoT can be demonstrated to be the most ideal choice to serve such conditions.
- Computerized reasoning is the next enormous thing, as practically all brilliant gadgets use it to upgrade productivity. The ideas and elements of the IoT could be incorporated with Artificial Intelligence-based applications to make it work much better and increment registering power. There are, as of now, gadgets out in the market that influence both the simulated intelligence applications and the IoT, and those gadgets are now working productively [9].
- In the period of web-based business, there are a great many clients reliant upon the web-based site to purchase the items they need. The web-based business sites likewise comprehend that they must treat their clients with a customized experience so they can feel open to utilizing their foundation, and here is where the IoT could be utilized in the best way. It makes the client utilize the web-based site effortlessly with the goal that they can zero in on what they need to purchase rather than zeroing in on how the site functions.
3. IoT Service Methodology
The level of difficulties and the degree of promising plans that could be sought after further addressing them are outlined below, facilitated by the following rules:
- The diverse plan of IoT security requires a base-up, ordinary cycle to guarantee that the results address all current and coherent difficulties and issues [10]. The procedure ought to be liquid in nature, portrayed, and refined through conversation with assistants.
- From one side of the planet to the other, blended specific norms are crucial for refreshing IoT security. Ultimately, they are trying to get it right and take their time. It is sensible for approaches to overseeing IoT security to begin at a public level while working with other public, normal, and general bodies.
- In view of the snappiness of the dangers and the drawn-out time of the extended length movements, for example, climbs to structure frameworks and the improvement of overall standards, it is essential to begin work on preparing clients and for the relationship to start embracing the acknowledged methods that will diminish the dangers of client IoT contraption gathering. A key enabler of transformations is a digital infrastructure that is secure, reliable, and high-performance. To accelerate the deployment of their 5G networks and cloud infrastructure, nations such as India, China, and the United States are making significant investments.
A third of the world’s population needs to be connected, and emerging markets lack digital infrastructure. Additionally, many “connected” individuals in less-developed nations are unable to take advantage of Internet connectivity due to obstacles like cost and lack of skills. At that point, as the most recent blast of simulated intelligence like ChatGPT shows, simulated intelligence runs on information, and that connection prompts a self-sustaining pattern of solidification in enterprises: your product will be better if you have more data; the more users you gain, the better your product is; you will have more data the more users you gain. While we are acutely aware of the “internet gap”, in which financial, health, and educational inclusion are limited by a lack of Internet access in emerging markets, we must immediately address the “AI gap”, in which the IoT revolution and Artificial Intelligence will widen the gap between nations. With billions of associated gadgets gathering and sending sensitive data, the commitment of the IoT is only comparable to the protection and security behind it [11,12]. Due to the proliferation of devices worldwide, the year 2023 may see an increase in automated attacks against home smart devices. Figure 3 shows multiple areas which were exploited to gain unauthorized access because the IoT combines hardware, software, data transfer and storage, network connectivity, and more. For instance, the healthcare sector might be thought to be behind this digital trend, but it requires the absolute highest level of trust and safety. Certain parts of IoT security are so deeply grounded that they were stated as gauge moves that should be initiated to upgrade IoT security, including the following steps:
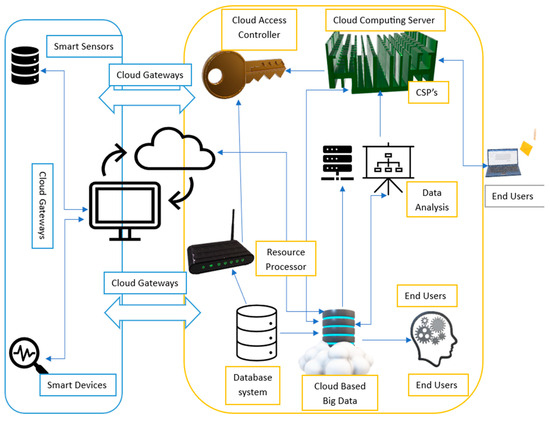
Figure 3.
Security methodology used in IoT.
- Step 1: No widespread or handily speculated pre-set passwords.
- Step 2: Information ought to be communicated and put away safely from areas of strength for utilizing.
- Step 3: Information assortment ought to be limited to just what is vital for a gadget to work.
- Step 4: Gadgets ought to be equipped for receiving security updates and fixes.
- Step 5: Gadget makers ought to tell buyers on the off chance that there is a security break.
- Step 6: Gadget makers ought to guarantee shoppers can reset a gadget to its processing plant settings in case of a deal or move of the gadget.
4. Challenges, Open Issues, and Future Research Directions
The power that IoT applications hold to help businesses become more efficient and raise the service quality cannot be denied [13,14]. Using many connected sensors and actuators, businesses can collect a lot of data for continuous improvement. They can, for example, control processes from a distance to smooth out staffing and expand yield, track the areas of resources for increment functional productivity, and expect upkeep prerequisites in far off hardware to limit downtime and use staff productively. The IoT is working in every field for smart business, smart commerce, and smart environmental management. There will be many more smart systems for the IoT in the future [15]. These several research issues demonstrate the multifaceted nature of the IoT and the need for interdisciplinary collaboration between computer scientists, engineers, data scientists, ethicists, and policymakers to address the challenges and advance the field. The Internet of Things (IoT) is a rapidly evolving field with several ongoing research issues and challenges. IoT devices are often vulnerable to security breaches, posing risks to both individual privacy and critical infrastructure. Researchers are working on developing robust security protocols, encryption methods, and authentication mechanisms to protect IoT ecosystems from cyberattacks [16,17,18]. As the number of IoT devices continues to grow, scalability becomes a significant concern. Research is needed to address the challenges of managing and maintaining large-scale IoT deployments efficiently. IoT devices and platforms from different manufacturers often use proprietary protocols and standards, making interoperability a challenge. Researchers are exploring methods to create standardized communication protocols that allow seamless device integration [19,20,21].
Processing data at the edge, closer to the IoT devices, is essential for reducing latency and improving real-time decision-making. Researchers are working on edge computing solutions and algorithms to optimize IoT data processing. Many IoT devices are battery-powered, and extending their battery life is crucial. Researchers are investigating energy-efficient communication protocols, low-power hardware design, and energy harvesting technologies. Handling the massive volume of data generated by IoT devices is a significant challenge [22,23,24]. Researchers are developing advanced data analytics techniques, machine learning models, and data storage solutions to extract valuable insights from IoT data. Maintaining QoS in IoT applications, such as healthcare or industrial automation, is essential. Researchers are working on QoS-aware resource allocation, traffic management, and adaptive algorithms. The IoT lacks comprehensive global standards and regulations, leading to issues related to security, privacy, and data ownership. Research in this area involves creating a regulatory framework and industry standards for the IoT. IoT systems should be able to withstand various forms of failures, including network disruptions and device malfunctions [19]. Researchers are exploring fault-tolerant mechanisms and self-healing algorithms. IoT technologies raise ethical concerns related to data privacy, surveillance, and consent. Research focuses on ethical frameworks, user education, and understanding the societal impact of the IoT [25,26,27,28]. These research areas represent the evolving landscape of the IoT and the need for interdisciplinary collaboration among researchers, engineers, data scientists, and policymakers to harness the full potential of IoT technologies while addressing the associated challenges.
5. Conclusions and Future Work
The Internet of Things is primarily the interconnection of the gadgets that normally look for input from different gadgets. The significant piece of involving the IoT in the gadget is that it makes things simpler to work inside lower energy utilization. To take advantage of this innovation, one should know about how it functions by keeping up with the guidelines called IoT norms. It has been exceptionally valuable for different ventures. When we discuss computerizing things so the creation framework can be improved, the Web of Things comes to the primary spot. Additionally, it is not difficult to carry out this innovation as it prompts a cost decrease in the creation climate.
Author Contributions
Conceptualization, S.P., N.K.S., N.S. and S.A.; methodology, J.P.B. and S.K.V.; validation, S.P., N.K.S., N.S. and S.A.; formal analysis, J.P.B. and S.K.V.; investigation, S.P., N.K.S., N.S. and S.A.; resources, J.P.B. and S.K.V.; data curation, J.P.B. and S.K.V.; writing—original draft preparation, S.P., N.K.S., N.S. and S.A.; validation, J.P.B. and S.K.V.; writing—review and editing, S.P., N.K.S., N.S. and S.A.; validation, J.P.B. and S.K.V.; visualization, J.P.B. and S.K.V.; supervision, S.P., N.K.S., N.S. and S.A.; All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data sharing is not applicable to this article.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Madakam, S.; Lake, V.; Lake, V.; Lake, V. Internet of Things (IoT): A literature review. J. Comput. Commun. 2015, 3, 164. [Google Scholar] [CrossRef]
- Altay, N.; Green, W.G. OR/MS research in disaster operations management. Eur. J. Oper. Res. 2006, 175, 475–493. [Google Scholar] [CrossRef]
- Pain, P.; Sadhu, A.; Das, K.; Kanjilal, M.R. Design and Implementation of Multi-Operative Reversible Gate for Even/Odd Parity Generators in Quantum Based Technologies. J. Comput. Mech. Manag. 2023, 2, 20–28. [Google Scholar] [CrossRef]
- Verma, C.P. Enhancing Parameters of LEACH Protocol for Efficient Routing in Wireless Sensor Networks. J. Comput. Mech. Manag. 2023, 2, 30–34. [Google Scholar] [CrossRef]
- Kumar Sharma, A.; Tiwari, A.; Bohra, B.; Khan, S. A Vision towards Optimization of Ontological Datacenters Computing World. Int. J. Inf. Syst. Manag. Sci. 2018, 1, 1–6. [Google Scholar]
- Tiwari, A.; Sharma, R.M. Rendering Form Ontology Methodology for IoT Services in Cloud Computing. Int. J. Adv. Stud. Sci. Res. 2018, 3, 273–278. [Google Scholar]
- Tiwari, A.; Garg, R. Eagle Techniques in Cloud Computational Formulation. Int. J. Innov. Technol. Explor. Eng. 2019, 1, 422–429. [Google Scholar]
- Tiwari, A.; Garg, R. ACCOS: A Hybrid Anomaly-Aware Cloud Computing Formulation-Based Ontology Services in Clouds. In Proceedings of the ISIC’21: International Semantic Intelligence Conference, Online, 25–27 February 2021; pp. 341–346. [Google Scholar]
- Koppaiyan, R.S.; Pallivalappil, A.S.; Singh, P.; Tabassum, H.; Tewari, P.; Sweeti, M.; Kumar, S. High-Availability Encryption-Based Cloud Resource Provisioning System. In Proceedings of the 4th International Conference on Information Management & Machine Intelligence, Jaipur, India, 23–24 December 2022; pp. 1–6. [Google Scholar]
- Tiwari, A.; Garg, R. Reservation System for Cloud Computing Resources (RSCC): Immediate Reservation of the Computing Mechanism. Int. J. Cloud Appl. Comput. (IJCAC) 2022, 12, 1–22. [Google Scholar]
- Gokhale, P.; Bhat, O.; Bhat, S. Introduction to IOT. Int. Adv. Res. J. Sci. Eng. Technol. 2018, 5, 41–44. [Google Scholar]
- Tiwari, A.; Kumar, S.; Baishwar, N.; Vishwakarma, S.K.; Singh, P. Efficient Cloud Orchestration Services in Computing. In Proceedings of the 3rd International Conference on Machine Learning, Advances in Computing, Renewable Energy and Communication, Ghaziabad, India, 10–11 December 2021; pp. 739–746. [Google Scholar]
- Rohinidevi, V.V.; Srivastava, P.K.; Dubey, N.; Tiwari, S.; Tiwari, A. A Taxonomy towards fog computing Resource Allocation. In Proceedings of the 2022 2nd International Conference on Innovative Sustainable Computational Technologies (CISCT), Dehradun, India, 23–24 December 2022; pp. 1–5. [Google Scholar]
- Singh, N.K.; Jain, A.; Arya, S.; Gonzales, W.E.G.; Flores, J.E.A.; Tiwari, A. Attack Detection Taxonomy System in cloud services. In Proceedings of the 2022 2nd International Conference on Innovative Sustainable Computational Technologies (CISCT), Dehradun, India, 23–24 December 2022; pp. 1–5. [Google Scholar]
- Rangaiah, Y.V.; Sharma, A.K.; Bhargavi, T.; Chopra, M.; Mahapatra, C.; Tiwari, A. A Taxonomy towards Blockchain based Multimedia Content Security. In Proceedings of the 2022 2nd International Conference on Innovative Sustainable Computational Technologies (CISCT), Dehradun, India, 23–24 December 2022; pp. 1–4. [Google Scholar]
- Kamble, S.; Saini, D.K.J.; Kumar, V.; Gautam, A.K.; Verma, S.; Tiwari, A.; Goyal, D. Detection and tracking of moving cloud services from video using saliency map model. J. Discret. Math. Sci. Cryptogr. 2022, 25, 1083–1092. [Google Scholar] [CrossRef]
- Tiwari, A.; Garg, R. Adaptive Ontology-Based IoT Resource Provisioning in Computing Systems. Int. J. Semant. Internet Inf. Syst. (IJSWIS) 2022, 18, 1–18. [Google Scholar] [CrossRef]
- Tiwari, A.; Garg, R. Orrs Orchestration of a Resource Reservation System Using Fuzzy Theory in High-Performance Computing: Lifeline of the Computing World. Int. J. Softw. Innov. (IJSI) 2022, 10, 1–28. [Google Scholar] [CrossRef]
- Kumar, S.; Kumar, S.; Ranjan, N.; Tiwari, S.; Kumar, T.R.; Goyal, D.; Rafsanjani, M.K. Digital watermarking-based cryptosystem for cloud resource provisioning. Int. J. Cloud Appl. Comput. (IJCAC) 2022, 12, 1–20. [Google Scholar] [CrossRef]
- Lakshmanna, K.; Kaluri, R.; Gundluru, N.; Alzamil, Z.S.; Rajput, D.S.; Khan, A.A.; Alhussen, A. A review on deep learning techniques for IoT data. Electronics 2022, 11, 1604. [Google Scholar] [CrossRef]
- Sarker, I.H.; Khan, A.I.; Abushark, Y.B.; Alsolami, F. Internet of things (iot) security intelligence: A comprehensive overview, machine learning solutions and research directions. Mob. Netw. Appl. 2022, 28, 296–312. [Google Scholar] [CrossRef]
- Goudarzi, A.; Ghayoor, F.; Waseem, M.; Fahad, S.; Traore, I. A Survey on IoT-Enabled Smart Grids: Emerging, Applications, Challenges, and Outlook. Energies 2022, 15, 6984. [Google Scholar] [CrossRef]
- Benhamaid, S.; Bouabdallah, A.; Lakhlef, H. Recent advances in energy management for Green-IoT: An up-to-date and comprehensive survey. J. Netw. Comput. Appl. 2022, 198, 103257. [Google Scholar] [CrossRef]
- Christou, I.T.; Kefalakis, N.; Soldatos, J.K.; Despotopoulou, A.M. End-to-end industrial IoT platform for Quality 4.0 applications. Comput. Ind. 2022, 137, 103591. [Google Scholar] [CrossRef]
- Ravula, A.K.; Ahmad, S.S.; Singh, A.K.; Sweeti, S.; Kaur, A.; Kumar, S. Multi-level collaborative framework decryption-based computing systems. AIP Conf. Proc. 2023, 2782, 020131. [Google Scholar]
- Dora Pravina, C.T.; Buradkar, M.U.; Jamal, M.K.; Tiwari, A.; Mamodiya, U.; Goyal, D. A Sustainable and Secure Cloud resource provisioning system in Industrial Internet of Things (IIoT) based on Image Encryption. In Proceedings of the 4th International Conference on Information Management & Machine Intelligence, Jaipur, India, 23–24 December 2022; pp. 1–5. [Google Scholar]
- Manikandan, R.; Maurya, R.K.; Rasheed, T.; Bose, S.C.; Arias-Gonzáles, J.L.; Mamodiya, U.; Tiwari, A. Adaptive cloud orchestration resource selection using rough set theory. J. Interdiscip. Math. 2023, 26, 311–320. [Google Scholar] [CrossRef]
- Srivastava, P.K.; Kumar, S.; Tiwari, A.; Goyal, D.; Mamodiya, U. Internet of thing uses in materialistic ameliorate farming through AI. AIP Conf. Proc. 2023, 2782, 020133. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).