A Comparative Study of Coverage Hole Detection Techniques in Wireless Sensor Networks †
Abstract
:1. Introduction
2. Methodology
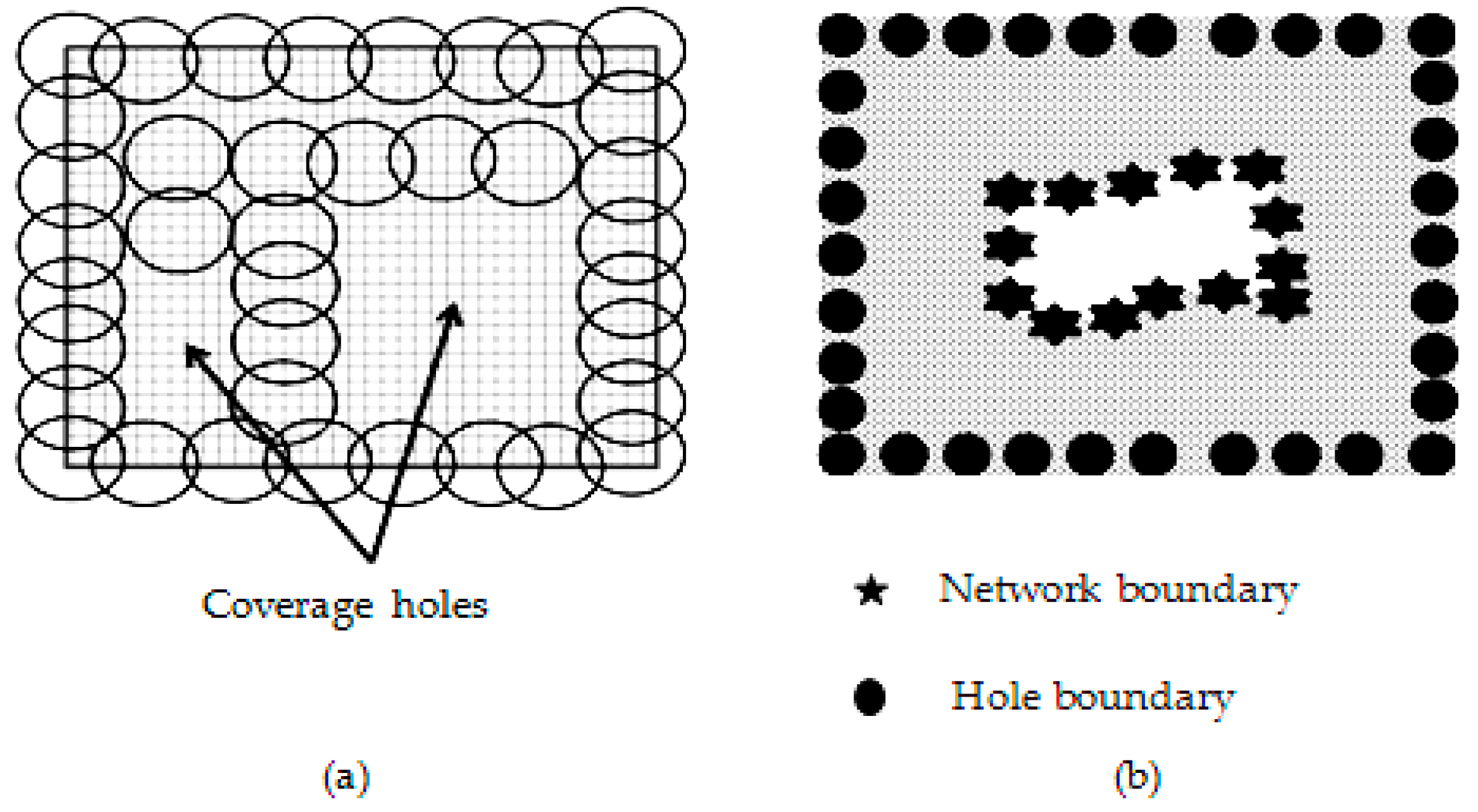
- The nonfunctional nodes can be accurately identified by the hole boundary;
- By identifying hole borders, effective routing can stop data from being lost in the network;
- Detecting the hole boundary precisely determines the hole region;
- Geographic multicasting is enhanced by the introduction of a hole restriction;
- The number of additional nodes required for hole correction may be determined with proper hole boundary detection.
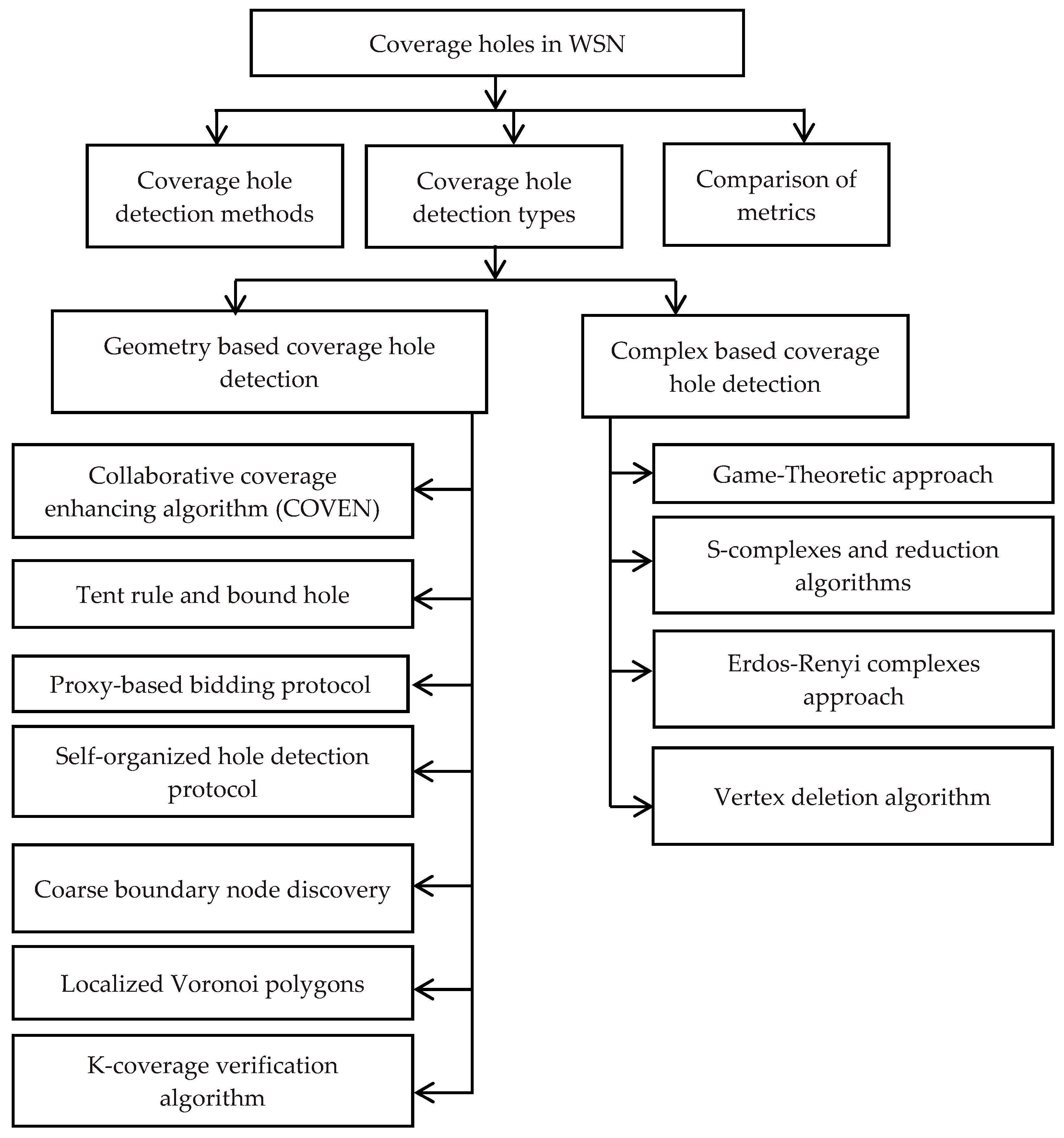
2.1. Techniques for Detecting Coverage Holes
2.2. Algorithm for Detecting Coverage Holes Based on Simplified Rips Complex
| function detectCoverageHoles(): initializeGrid()//Create a grid over the network area markGridCellsAsCovered()//Mark grid cells with sensor nodes for each grid cell: if isEmpty(grid cell) or isLowDensity(grid cell): markAsPotentialHole(grid cell) identifyConnectedComponents()//Analyze connectivity among grid cells for each potential hole: if isConnectedToBoundary(potential hole): markAsCoverageHole(potential hole) function initializeGrid(): //Divide the network area into grid cells function markGridCellsAsCovered(): for each sensor node: calculateGridCell(node position) markGridCellAsOccupied(grid cell) function isEmpty(grid cell): //Check if a grid cell has no sensors function isLowDensity(grid cell): //Check if the sensor density in a grid cell is below a threshold function markAsPotentialHole(grid cell): //Mark a grid cell as a potential coverage hole function identifyConnectedComponents(): //Use graph traversal algorithms (e.g., Depth-First Search or Breadth-First Search) //to find connected components of grid cells function isConnectedToBoundary(potential hole): //Check if a potential hole is connected to the network boundary function markAsCoverageHole(potential hole): //Mark a potential hole as a coverage hole |
2.3. Coverage Hole Detection Technique with Low Energy Consumption
2.4. Sensing Coverage Hole Detection and Repair Algorithms for WSNs
2.5. Reinforcement-Learning-Based Distributed Coverage Hole Recovery Approach
2.6. List of Coverage Holes Found in WSN
3. Experimental Setup
4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Guleria, K.; Verma, A.K. Comprehensive review for energy efficient hierarchical routing protocols on wireless sensor networks. Wirel. Netw. 2019, 25, 1159–1183. [Google Scholar] [CrossRef]
- Bhushan, B.; Gadadhar, S. Recent advances in attacks, technical challenges, vulnerabilities and their countermeasures in wireless sensor networks. Wirel. Pers. Commun. 2018, 98, 2037–2077. [Google Scholar] [CrossRef]
- Shaikh, F.K.; Sherali, Z. Energy harvesting in wireless sensor networks: A comprehensive review. Renew. Sustain. Energy Rev. 2016, 55, 1041–1054. [Google Scholar] [CrossRef]
- Ayadi, A.; Ghorbel, O.; Obeid, A.M.; Abid, M. Outlier detection approaches for wireless sensor networks: A survey. Comput. Netw. 2019, 129, 319–333. [Google Scholar] [CrossRef]
- Das, S.; DebBarma, M.K. Hole detection in wireless sensor network: A review. In Recent Findings in Intelligent Computing Techniques: Proceedings of the 5th ICACNI 2017; Springer: Singapore, 2018; Volume 2, pp. 87–96. [Google Scholar]
- Das, S.; Debbarma, M.K. A Review on Coverage-Hole Boundary Detection Algorithms in Wireless Sensor Networks. Comput. Y Sist. 2021, 24, 121–140. [Google Scholar] [CrossRef]
- Deng, X.; Jiang, Y.; Yang, L.T.; Lin, M.; Yi, L.; Wang, M. Data fusion based coverage optimization in heterogeneous sensor networks: A survey. Inf. Fusion 2020, 52, 90–105. [Google Scholar] [CrossRef]
- Yang, H. A practical method for connectivity and coverage reliability analysis for linear wireless sensor networks. Ad Hoc Netw. 2023, 146, 103183. [Google Scholar] [CrossRef]
- Sung, T.-W.; Yang, C.-S. Voronoi-based coverage improvement approach for wireless directional sensor networks. J. Netw. Comput. Appl. 2014, 39, 202–213. [Google Scholar] [CrossRef]
- Soundarya, A.; Santhi, V. An efficient algorithm for coverage hole detection and healing in wireless sensor networks. In Proceedings of the 2017 1st International Conference on Electronics, Materials Engineering and Nano-Technology (IEMENTech), Kolkata, India, 28–29 April 2017; pp. 1–5. [Google Scholar]
- Das, S.; Debbarma, M.K. A survey on coverage problems in wireless sensor network based on the monitored region. Adv. Data Inf. Sci. 2019, 2, 349–359. [Google Scholar]
- Kröller, A.; Fekete, S.P.; Pfisterer, D.; Fischer, S. Deterministic boundary recognition and topology extraction for large sensor networks. In Proceedings of the Seventeenth Annual ACM-SIAM Symposium on Discrete Algorithm, Miami, FL, USA, 22–26 January 2006; Society for Industrial and Applied Mathematics: Philadelphia, PA, USA, 2006; pp. 1000–1009. [Google Scholar]
- Wang, Y.; Gao, J.; Mitchell, J.S. Boundary recognition in sensor networks by topological Methods. In Proceedings of the 12th Annual International Conference on Mobile Computing and Networking, Los Angeles, CA, USA, 23–29 September 2006; ACM: New York, NY, USA, 2006; pp. 122–133. [Google Scholar]
- Sharma, P.; Singh, R.P. Coverage hole identification & healing in Wireless Underground Sensor Networks. Meas. Sens. 2022, 24, 100540. [Google Scholar]
- Wang, F.; Hu, H. Coverage hole detection method of wireless sensor network based on clustering algorithm. Measurement 2021, 179, 109449. [Google Scholar] [CrossRef]
- Li, W.; Zhang, W. Coverage hole and boundary nodes detection in wireless sensor networks. J. Netw. Comput. Appl. 2015, 48, 35–43. [Google Scholar] [CrossRef]
- Zhang, J.; Chu, H.; Feng, X. Efficient Coverage Hole Detection Algorithm Based on the Simplified Rips Complex in Wireless Sensor Networks. J. Sens. 2020, 2020, 3236970. [Google Scholar] [CrossRef]
- Abdellatief, W.; Abdelkader, H.; Hadhoud, M. An energy-efficient coverage hole detection technique for randomly deployed wireless sensor networks. In Proceedings of the 2016 11th International Conference on Computer Engineering & Systems (ICCES), Cairo, Egypt, 20–21 December 2016; pp. 340–347. [Google Scholar]
- Singh, P.; Chen, Y.C. Sensing coverage hole identification and coverage hole healing methods for wireless sensor networks. Wirel. Netw. 2021, 26, 2223–2239. [Google Scholar] [CrossRef]
- Hajjej, F.; Hamdi, M.; Ejbali, R.; Zaied, M. A distributed coverage hole recovery approach based on reinforcement learning for Wireless Sensor Networks. Ad Hoc Netw. 2020, 101, 102082. [Google Scholar] [CrossRef]
| Author | Energy Consumption | Processing Time | Number of Patching Sensors | Cost | Network Lifetime |
|---|---|---|---|---|---|
| Sung et al. [9] | Less energy consumption | Decreased half of the time consumed | Reduced | Not measured | Improved |
| Das et al. [11] | Not considered | Processing time is reduced | Higher | Not measured | Increased network lifespan |
| Wang et al. [13] | Not considering the energy problem | Not considered | Higher | Not measured | Not improved |
| Singh et al. [19] | Need to increase energy efficiency | Reasonable time frame | Not considered | High | Improved |
| Hajjej et al. [20] | Not considered | Not considered | Higher | Highest cost | Not improved |
| Author | Deployment Strategy | Energy Consumption | Computational Complexity | ||||
|---|---|---|---|---|---|---|---|
| Low | Medium | High | Low | Medium | High | ||
| Guleria et al. [1] | Randomly | - | √ | - | - | √ | - |
| Deng et al. [7] | Randomly | - | - | √ | - | √ | - |
| Sung et al. [9] | Randomly | - | - | - | - | - | √ |
| Wang et al. [13] | Randomly | √ | - | - | √ | - | - |
| Fekete al. [14] | Randomly | - | - | √ | - | √ | - |
| Staddon et al. [15] | Deterministic | - | √ | - | - | - | √ |
| Das et al. [16] | Randomly | √ | - | - | - | √ | |
| Hajjej et al. [20] | Randomly | - | √ | - | - | - | √ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Angelin, A.C.; Silas, S. A Comparative Study of Coverage Hole Detection Techniques in Wireless Sensor Networks. Eng. Proc. 2023, 59, 5. https://doi.org/10.3390/engproc2023059005
Angelin AC, Silas S. A Comparative Study of Coverage Hole Detection Techniques in Wireless Sensor Networks. Engineering Proceedings. 2023; 59(1):5. https://doi.org/10.3390/engproc2023059005
Chicago/Turabian StyleAngelin, Anitha Christy, and Salaja Silas. 2023. "A Comparative Study of Coverage Hole Detection Techniques in Wireless Sensor Networks" Engineering Proceedings 59, no. 1: 5. https://doi.org/10.3390/engproc2023059005
APA StyleAngelin, A. C., & Silas, S. (2023). A Comparative Study of Coverage Hole Detection Techniques in Wireless Sensor Networks. Engineering Proceedings, 59(1), 5. https://doi.org/10.3390/engproc2023059005





