AIS for Malware Detection in a Realistic IoT System: Challenges and Opportunities
Abstract
:1. Introduction
Contribution and Paper Structure
- We use multiple state-of-the-art datasets with different types of malware attacks in the IoT to run AIS solutions for malware detection. We benchmark the results against the state-of-the-art intrusion detection methods that use the same datasets.
- We propose an AWS-enabled validation framework for the evaluation of AIS malware detection solutions, under realistic architecture and characteristics.
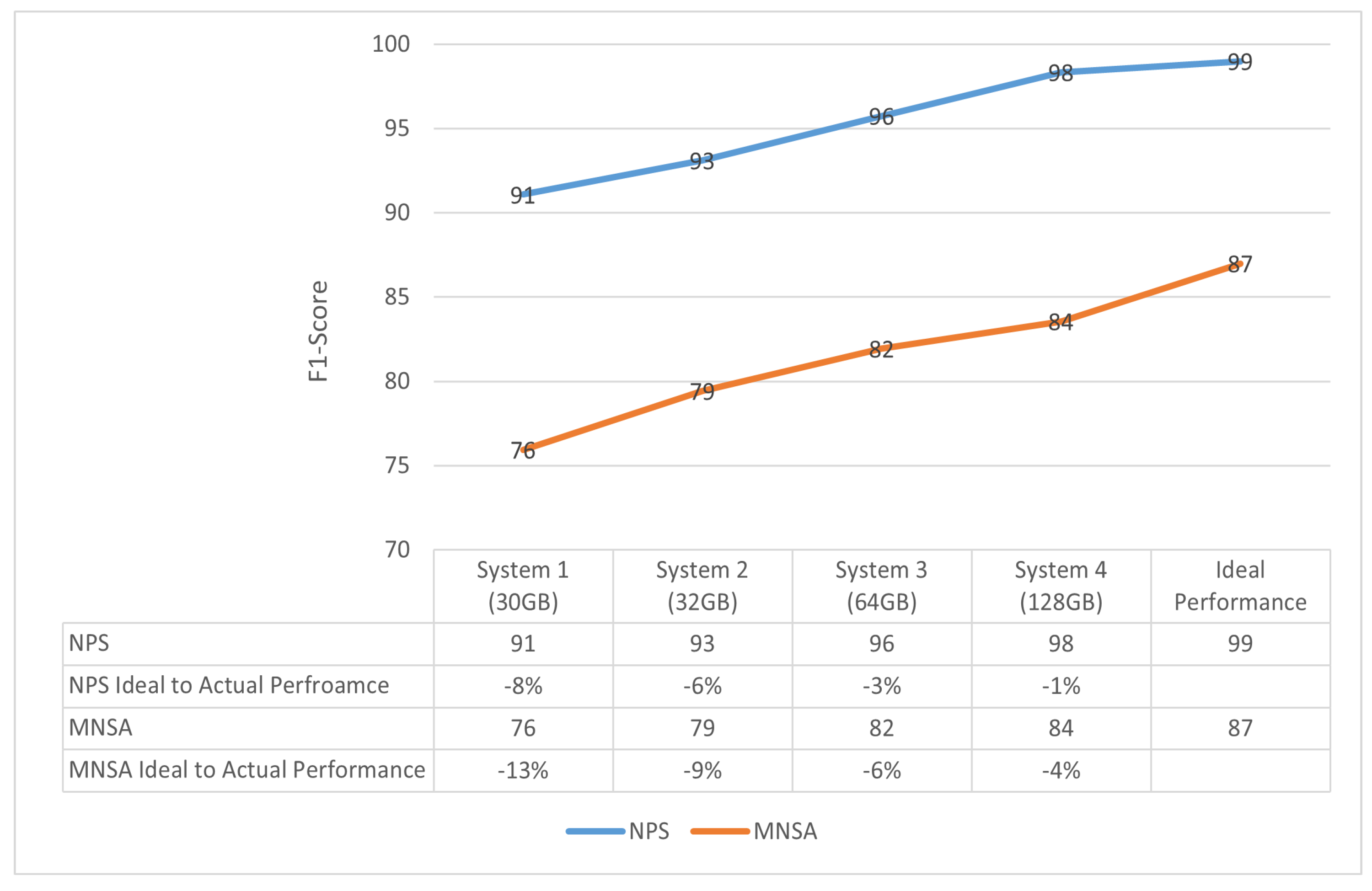
- The proposed framework is used to evaluate the performance of two leading AIS solutions under constrained systems. The memory size is found to be the most limiting factor that results in under-par performance compared to the reported simulation results for both solutions.
- We propose the first trial of transfer learning within IoT systems to combat the constrained memory in IoT devices. We demonstrate the transfer learning effectiveness of AIS solutions in securing the IoT.
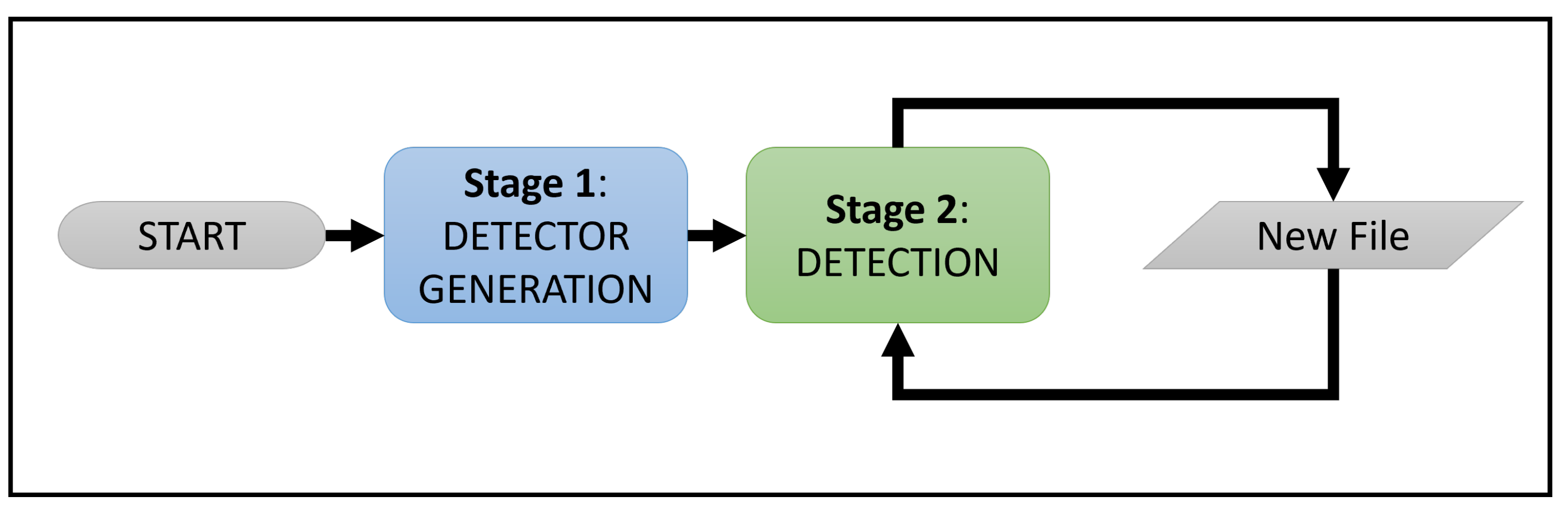
2. State-of-the-Art AIS Solutions
3. NPS Simulations and Evaluation
3.1. NSL-KDD Dataset
3.2. Bot-IoT Dataset
3.3. UNSW-NB15 Dataset
3.4. Performance Analysis of NPS
- True positive (TP): malware is detected as a malicious application;
- True negative (TN): a benign application is detected as a nonmalicious application;
- False positive (FP): a benign application is detected as a malicious application;
- False negative (FN): malware is detected as a nonmalicious application.
4. AIS Solutions’ Implementation
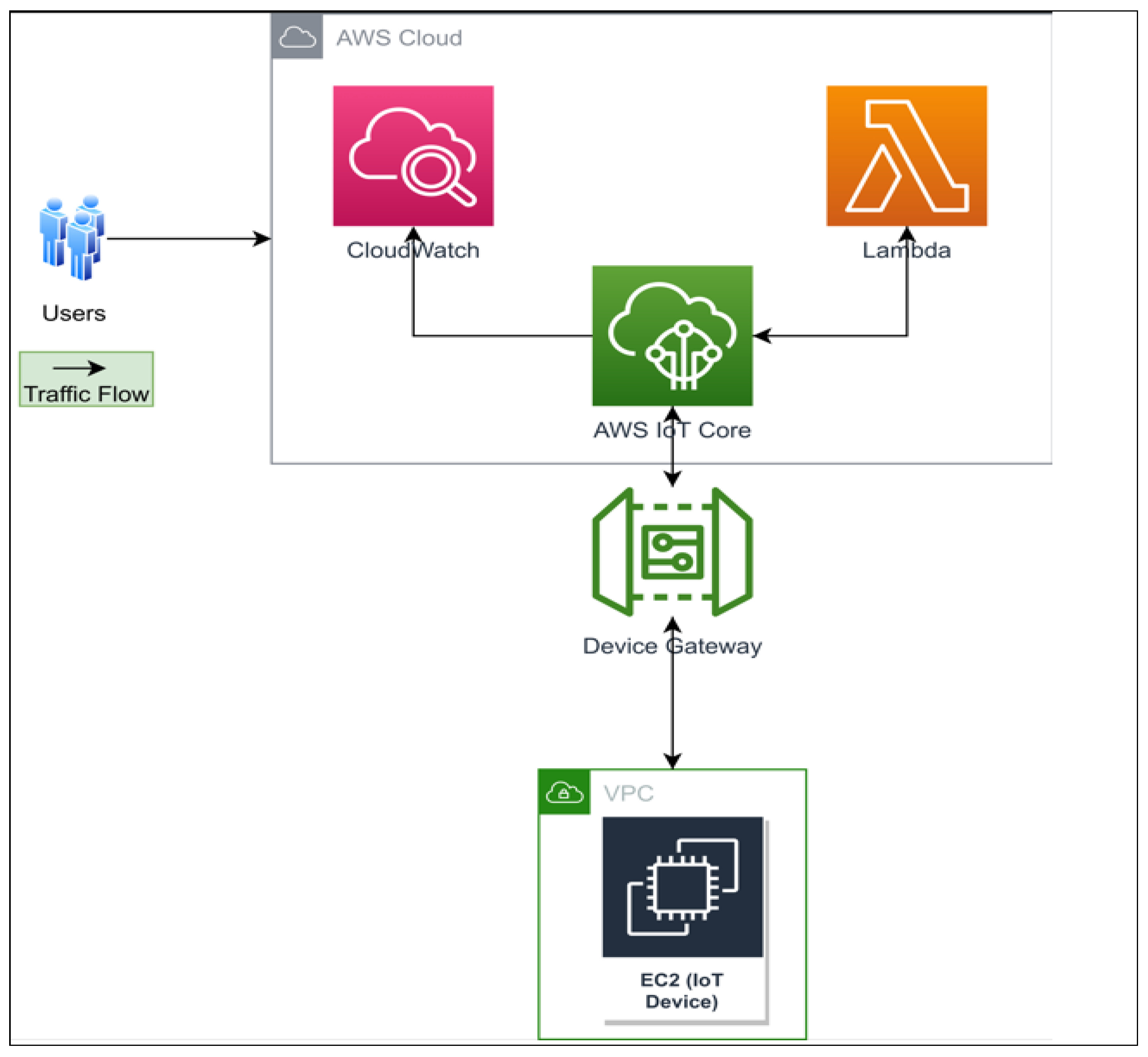
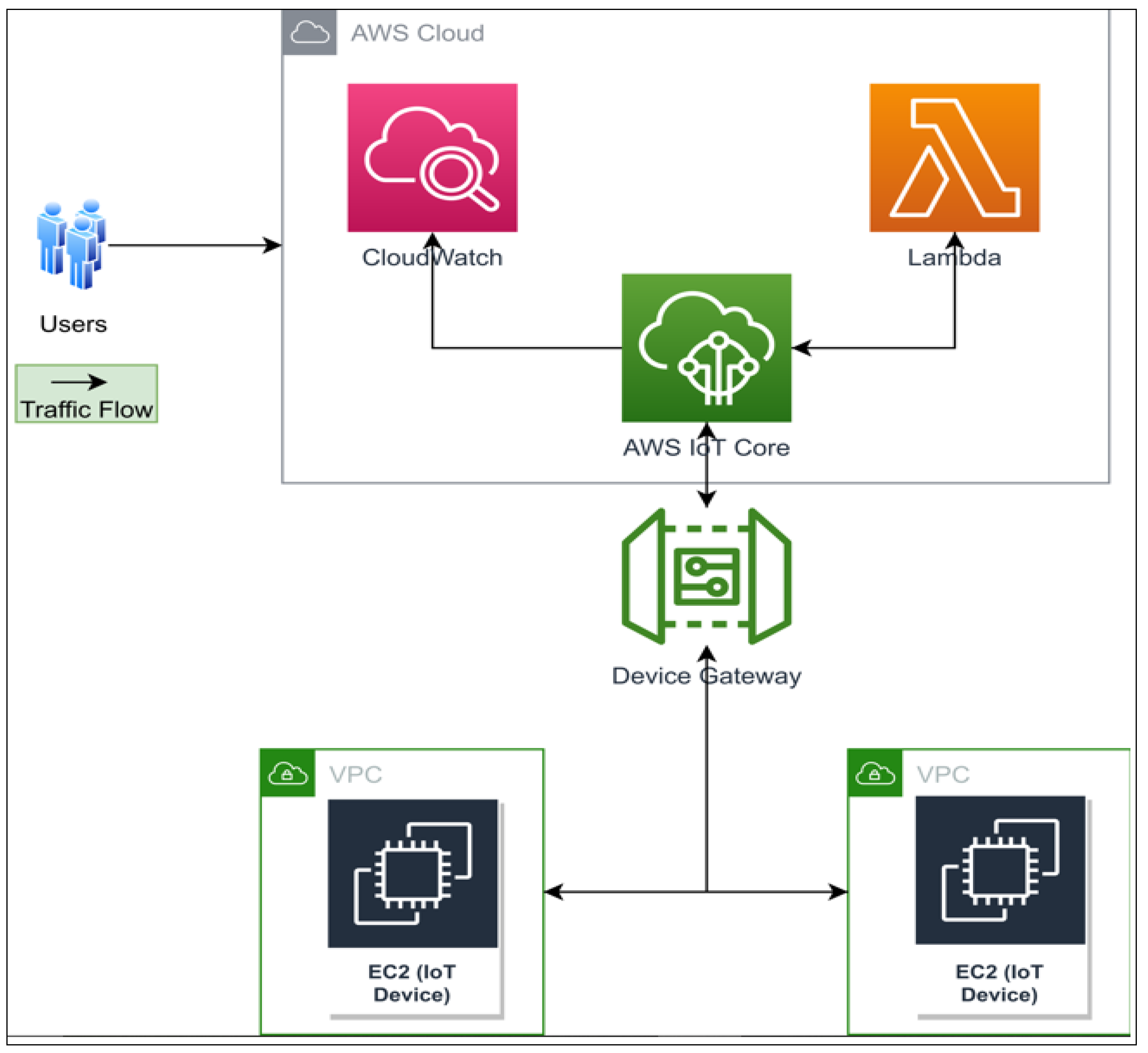
4.1. IoT System Architecture
- Amazon Elastic Compute Cloud (Amazon EC2) provides scalable computing capacity in the AWS Cloud. Users have total control over the EC2 configuration as it is not an AWS managed service.
- Virtual Private Cloud (Amazon VPC) creates a logically isolated virtual network when launching AWS resources. This service provides an extra layer of security to the implementation by using public and private subnets, and network access control list configuration.
- AWS IoT Core enables IoT devices connected to the AWS cloud. It supports a large number of devices and messages by providing reliable and secure services.
- Device Gateway: the entry point for IoT devices connected to AWS
- AWS Lambda runs programming code in a serverless computing service in response to events and automatically manages the underlying computing resources.
- Cloudwatch: monitoring and management services for AWS resources.
4.2. Problem Formulation
4.3. Implementation
5. Results and Discussion
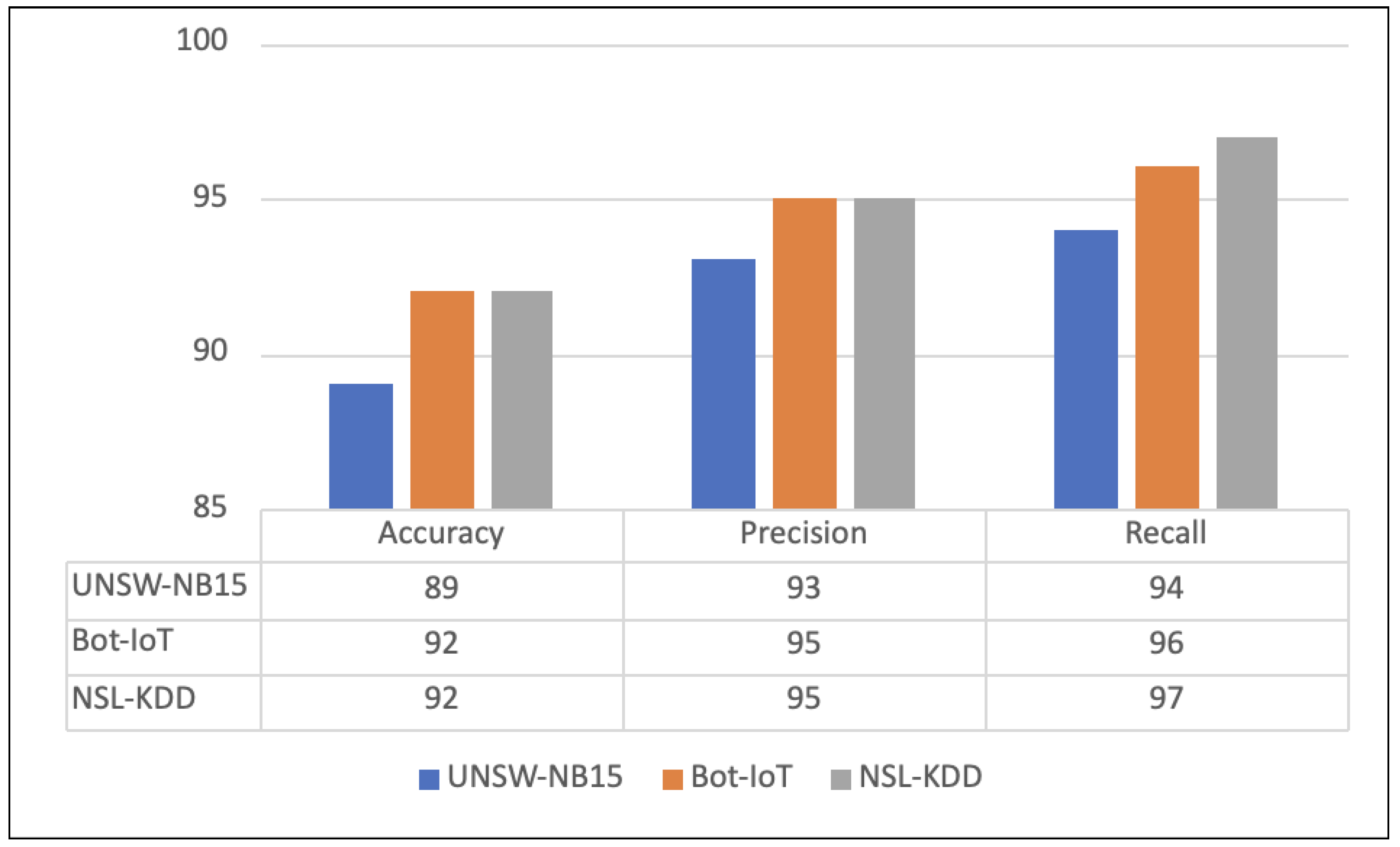
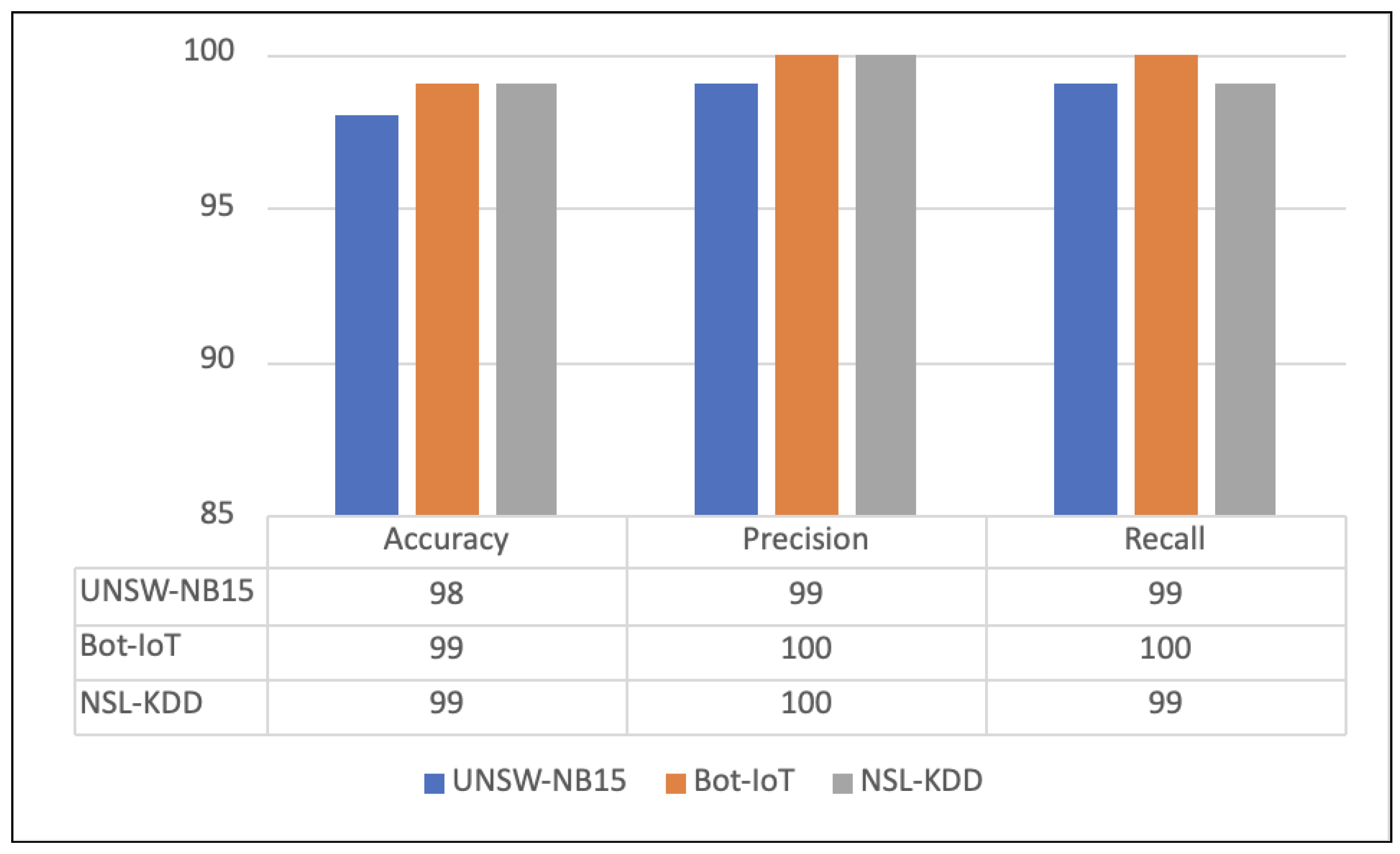
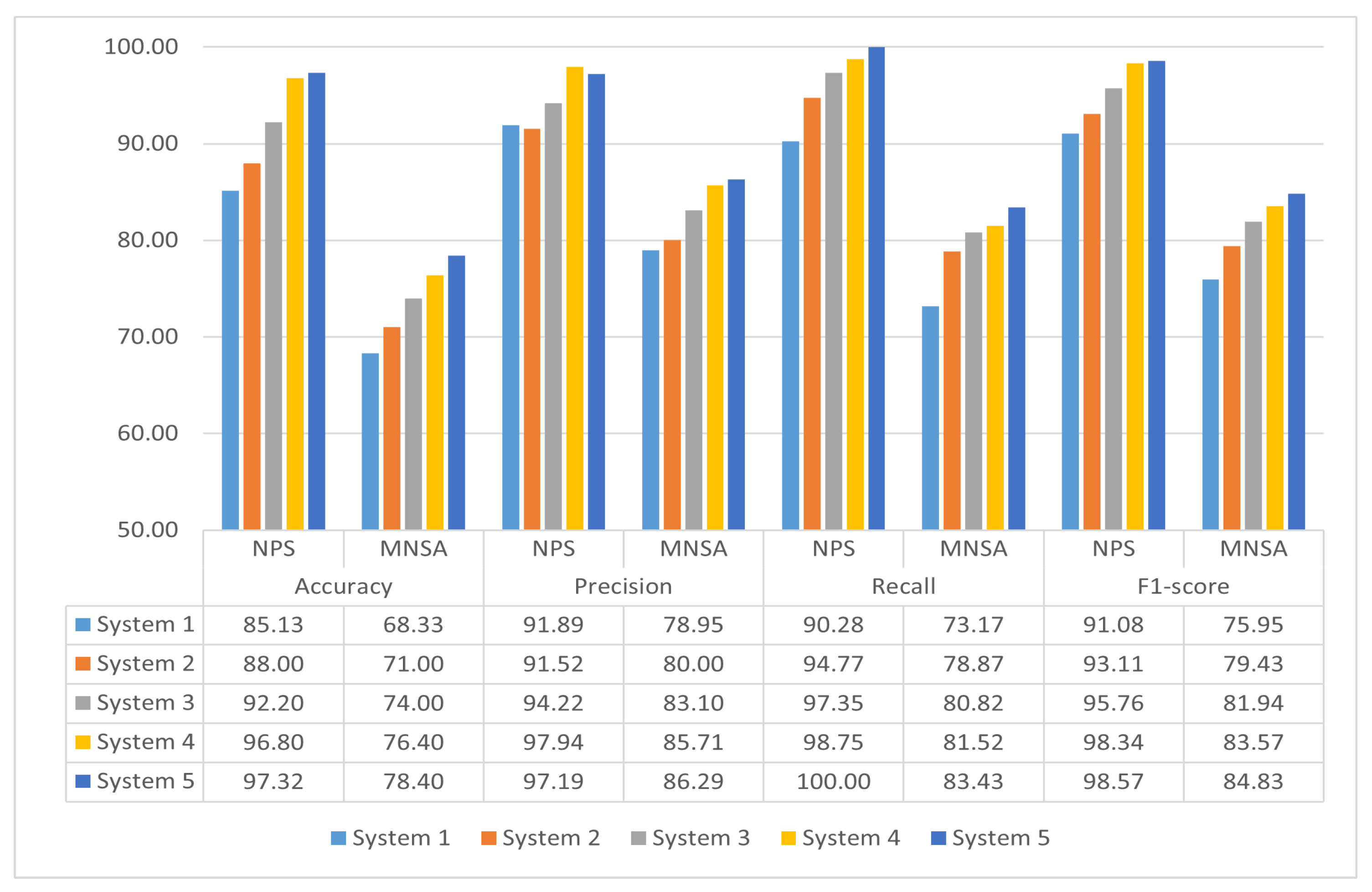
5.1. Detection Performance
5.2. CPU Utilization
5.3. Algorithm Simulation and Implementation Performance Analysis
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AIS | Artificial immune systems |
| AWS | Amazon Web Services |
| IoT | Internet of things |
| NSNN | Neural networks methods |
| OS | Operating system |
| IoMT | Internet of medical things |
References
- Wang, J.; Lim, M.K.; Wang, C.; Tseng, M.L. The evolution of the Internet of Things IoT over the past 20 years. Comput. Ind. Eng. 2021, 155, 107174. [Google Scholar] [CrossRef]
- Mazlumi, S.H.H.; Kermani, M.A.M. Investigation the structure of the Internet of things (IoT) patent network using social network analysis. IEEE Internet Things J. 2022, 9, 13458–13469. [Google Scholar]
- Alrubayyi, H.; Goteng, G.; Jaber, M.; Kelly, J. Challenges of Malware Detection in the IoT and a Review of Artificial Immune System Approaches. J. Sens. Actuator Netw. 2021, 10, 61. [Google Scholar] [CrossRef]
- The Most Vulnerable IOT Devices: Think before You Buy. Available online: https://tdwi.org/articles/2021/11/05/most-vulnerable-iot-devices.aspx (accessed on 1 June 2023).
- Asif, R. Post-Quantum Cryptosystems for Internet-of-Things: A Survey on Lattice-Based Algorithms. IoT 2021, 2, 71–91. [Google Scholar] [CrossRef]
- Summary: 9 March 9 2021 Security Incident Report. Available online: https://www.verkada.com/uk/security-update/report/ (accessed on 1 June 2023).
- Keerthi, K.; Roy, I.; Hazra, A.; Rebeiro, C. Formal Verification for Security in IoT Devices. In Security and Fault Tolerance in Internet of Things; Chakraborty, R.S., Mathew, J., Vasilakos, A.V., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 179–200. [Google Scholar] [CrossRef]
- Jim, L.E.; Islam, N.; Gregory, M.A. Enhanced MANET security using artificial immune system based danger theory to detect selfish nodes. Comput. Secur. 2022, 113, 102538. [Google Scholar] [CrossRef]
- Alrubayyi, H.; Goteng, G.; Jaber, M.; Kelly, J. A novel negative and positive selection algorithm to detect unknown malware in the IoT. In Proceedings of the IEEE INFOCOM 2021-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Virtual, 10–13 May 2021; pp. 1–6. [Google Scholar]
- Iqbal, M.; Ari Laksmono, A.M.; Prihatno, A.T.; Pratama, D.; Jeong, B.; Kim, H. Enhancing IoT Security: Integrating MQTT with ARIA Cipher 256 Algorithm Cryptography and mbedTLS. In Proceedings of the 2023 International Conference on Platform Technology and Service (PlatCon), Busan, Republic of Korea, 16–18 August 2023; pp. 91–96. [Google Scholar] [CrossRef]
- Liu, C.; Zhang, Y.; Xu, J.; Zhao, J.; Xiang, S. Ensuring the Security and Performance of IoT Communication by Improving Encryption and Decryption With the Lightweight Cipher uBlock. IEEE Syst. J. 2022, 16, 5489–5500. [Google Scholar] [CrossRef]
- Netea, M.G.; Schlitzer, A.; Placek, K.; Joosten, L.A.; Schultze, J.L. Innate and Adaptive Immune Memory: An Evolutionary Continuum in the Host’s Response to Pathogens. Cell Host Microbe 2019, 25, 13–26. [Google Scholar] [CrossRef] [PubMed]
- Pump, R.; Ahlers, V.; Koschel, A. Evaluating Artificial Immune System Algorithms for Intrusion Detection. In Proceedings of the 2020 Fourth World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, 27–28 July 2020; pp. 92–97. [Google Scholar] [CrossRef]
- Abdullahi, M.; Baashar, Y.; Alhussian, H.; Alwadain, A.; Aziz, N.; Capretz, L.F.; Abdulkadir, S.J. Detecting Cybersecurity Attacks in Internet of Things Using Artificial Intelligence Methods: A Systematic Literature Review. Electronics 2022, 11, 198. [Google Scholar] [CrossRef]
- Pamukov, M.E.; Poulkov, V.K.; Shterev, V.A. Negative Selection and Neural Network Based Algorithm for Intrusion Detection in IoT. In Proceedings of the 2018 41st International Conference on Telecommunications and Signal Processing (TSP), Athens, Greece, 4–6 July 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Pamukov, M.; Poulkov, V. Multiple negative selection algorithm: Improving detection error rates in IoT intrusion detection systems. In Proceedings of the 2017 9th IEEE International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS), Bucharest, Romania, 21–23 September 2017; Volume 1, pp. 543–547. [Google Scholar] [CrossRef]
- NSL-KDD Dataset. Available online: https://www.unb.ca/cic/datasets/nsl.html (accessed on 1 June 2023).
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, Ottawa, ON, Canada, 8–10 July 2009; pp. 1–6. [Google Scholar] [CrossRef]
- The Bot-LoT Dataset. Available online: https://research.unsw.edu.au/projects/bot-iot-dataset (accessed on 1 June 2023).
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the Internet of Things for network forensic analytics: Bot-IoT dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Slay, J. Towards Developing Network Forensic Mechanism for Botnet Activities in the IoT Based on Machine Learning Techniques. In Proceedings of the Mobile Networks and Management, Melbourne, Australia, 13–15 December 2017; pp. 30–44. [Google Scholar]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E. A new network forensic framework based on deep learning for Internet of Things networks: A particle deep framework. Future Gener. Comput. Syst. 2020, 110, 91–106. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Schiliro, F.; Gauravaram, P.; Janicke, H. A Holistic Review of Cybersecurity and Reliability Perspectives in Smart Airports. IEEE Access 2020, 8, 209802–209834. [Google Scholar] [CrossRef]
- The UNSW-NB15 Dataset. Available online: https://research.unsw.edu.au/projects/unsw-nb15-dataset (accessed on 1 June 2023).
- Moustafa, N.; Slay, J. UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In Proceedings of the 2015 Military Communications and Information Systems Conference (MilCIS), Canberra, ACT, Australia, 10–12 November 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Moustafa, N.; Slay, J. The evaluation of Network Anomaly Detection Systems: Statistical analysis of the UNSW-NB15 data set and the comparison with the KDD99 data set. Inf. Secur. J. Glob. Perspect. 2016, 25, 18–31. [Google Scholar] [CrossRef]
- Moustafa, N.; Slay, J.; Creech, G. Novel Geometric Area Analysis Technique for Anomaly Detection Using Trapezoidal Area Estimation on Large-Scale Networks. IEEE Trans. Big Data 2019, 5, 481–494. [Google Scholar] [CrossRef]
- Moustafa, N.; Creech, G.; Slay, J. Big Data Analytics for Intrusion Detection System: Statistical Decision-Making Using Finite Dirichlet Mixture Models. In Data Analytics and Decision Support for Cybersecurity: Trends, Methodologies and Applications; Palomares Carrascosa, I., Kalutarage, H.K., Huang, Y., Eds.; Springer International Publishing: Cham, Switzerland, 2017; pp. 127–156. [Google Scholar] [CrossRef]
- Sarhan, M.; Layeghy, S.; Moustafa, N.; Portmann, M. NetFlow Datasets for Machine Learning-Based Network Intrusion Detection Systems. In Big Data Technologies and Applications; Deze, Z., Huang, H., Hou, R., Rho, S., Chilamkurti, N., Eds.; Springer: Cham, Switzerland, 2021; pp. 117–135. [Google Scholar]
- Zeeshan, M.; Riaz, Q.; Bilal, M.A.; Shahzad, M.K.; Jabeen, H.; Haider, S.A.; Rahim, A. Protocol-Based Deep Intrusion Detection for DoS and DDoS Attacks Using UNSW-NB15 and Bot-IoT Data-Sets. IEEE Access 2022, 10, 2269–2283. [Google Scholar] [CrossRef]
- Larriva-Novo, X.; Villagrá, V.A.; Vega-Barbas, M.; Rivera, D.; Sanz Rodrigo, M. An IoT-Focused Intrusion Detection System Approach Based on Preprocessing Characterization for Cybersecurity Datasets. Sensors 2021, 21, 656. [Google Scholar] [CrossRef] [PubMed]
- Guizani, N.; Ghafoor, A. A Network Function Virtualization System for Detecting Malware in Large IoT Based Networks. IEEE J. Sel. Areas Commun. 2020, 38, 1218–1228. [Google Scholar] [CrossRef]
- Yang, Y.; Zheng, K.; Wu, C.; Yang, Y. Improving the Classification Effectiveness of Intrusion Detection by Using Improved Conditional Variational AutoEncoder and Deep Neural Network. Sensors 2019, 19, 2528. [Google Scholar] [CrossRef] [PubMed]
- Ibitoye, O.; Shafiq, M.O.; Matrawy, A. Analyzing Adversarial Attacks against Deep Learning for Intrusion Detection in IoT Networks. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Perlitz, L.; Elliott, S.G. The Products. 2000. Available online: https://aws.amazon.com/products/ (accessed on 1 June 2023).
- 8 of the Best Heart Rate Monitors of 2023. 2023. Available online: https://www.healthline.com/health/fitness/heart-rate-monitor (accessed on 1 June 2023).

| NSL-KDD Dataset Features | |
|---|---|
| Total number of records | over 1,074,992 |
| Attack Files | 262,178 |
| Benign files | 812,814 |
| Types of attacks | Brute-force, Heartbleed attack, botnet, |
| denial of service, distributed denial of service, Web attacks, | |
| infiltration of the network from inside | |
| Number of traffic features | 80 |
| Some of the traffic features | Destination port, flow duration, average size of |
| packet, number of forward packets per second, | |
| number of backward packets per second | |
| Bot-IoT Dataset Features | |
|---|---|
| Total number of records | over 73,000,000 |
| Attack files | 73,360,900 |
| Benign files | 9543 |
| List of attacks | DDoS, DoS, |
| operating system (OS) and service scan, | |
| keylogging and data exfiltration attacks | |
| Number of traffic features | 46 |
| Some of the traffic features | Destination port, flow duration, average size of |
| packet, number of forward packets per second, | |
| number of backward packets per second | |
| UNSW-NB15 Dataset Features | |
|---|---|
| Total number of records | over 25,000,000 |
| Attack files | 321,283 |
| Number of benign files | 2,218,761 |
| List of attacks | Fuzzers, analysis, backdoors, |
| DoS, exploits, generic, | |
| reconnaissance, shellcode and worms | |
| Number of traffic features | 49 |
| Some of the traffic features | Destination port, flow duration, average size of |
| packet, number of forward packets per second, | |
| number of backward packets per second | |
| System 1 | System 2 | System 3 | System 4 | System 5 | |
|---|---|---|---|---|---|
| Volume size | 30 GB | 32 GB | 64 GB | 128 GB | 30 GB |
| || | 12,000 | 14,000 | 28,000 | 400,000 | 24,000 |
| Number of IoT devices | One | One | One | One | Two |
| NPS | MNSA | |
|---|---|---|
| || | 30 | 20 |
| || | 30 | 150 |
| |L| | 16 | 12 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alrubayyi, H.; Goteng, G.; Jaber, M. AIS for Malware Detection in a Realistic IoT System: Challenges and Opportunities. Network 2023, 3, 522-537. https://doi.org/10.3390/network3040023
Alrubayyi H, Goteng G, Jaber M. AIS for Malware Detection in a Realistic IoT System: Challenges and Opportunities. Network. 2023; 3(4):522-537. https://doi.org/10.3390/network3040023
Chicago/Turabian StyleAlrubayyi, Hadeel, Gokop Goteng, and Mona Jaber. 2023. "AIS for Malware Detection in a Realistic IoT System: Challenges and Opportunities" Network 3, no. 4: 522-537. https://doi.org/10.3390/network3040023
APA StyleAlrubayyi, H., Goteng, G., & Jaber, M. (2023). AIS for Malware Detection in a Realistic IoT System: Challenges and Opportunities. Network, 3(4), 522-537. https://doi.org/10.3390/network3040023







