Abstract
We study a class of two-transmitter two-receiver dual-band Gaussian interference channels (GIC) which operates over the conventional microwave and the unconventional millimeter-wave (mm-wave) bands. This study is motivated by future 5G networks where additional spectrum in the mm-wave band complements transmission in the incumbent microwave band. The mm-wave band has a key modeling feature: due to severe path loss and relatively small wavelength, a transmitter must employ highly directional antenna arrays to reach its desired receiver. This feature causes the mm-wave channels to become highly directional, and thus can be used by a transmitter to transmit to its designated receiver or the other receiver. We consider two classes of such channels, where the underlying GIC in the microwave band has weak and strong interference, and obtain sufficient channel conditions under which the capacity is characterized. Moreover, we assess the impact of the additional mm-wave band spectrum on the performance, by characterizing the transmit power allocation for the direct and cross channels that maximizes the sum-rate of this dual-band channel. The solution reveals conditions under which different power allocations, such as allocating the power budget only to direct or only to cross channels, or sharing it among them, becomes optimal.
1. Introduction
Current technology such as 4G (e.g., [1]) is rapidly becoming inadequate to support the exponential growth in wireless traffic [2]. Moreover, the potential for improvement of network throughput in 4G is limited due to the shortage of spectrum in the incumbent microwave band (i.e., carrier frequencies below 6 GHz). Thus, methods to tackle the ever growing amount of mobile traffic has become a key research area (see [3] and references therein). Several new technologies are being considered, among which employing additional spectrum in the 28–300 GHz frequency range, often referred to as the millimeter wave (mm-wave) band, seems to be a promising solution to the problem of spectrum scarcity [3,4]. Specifically, integrating additional spectrum from the mm-wave band to complement transmissions in the microwave band is poised to play a central role in the functioning of 5G networks.
Transmission in the mm-wave band is distinctly different from that in the microwave band. Due to higher operating frequencies, omnidirectional transmission in the mm-wave band is subject to much higher absorption and power loss [5] compared to that in the microwave band, and thus a transmitter needs to employ beamforming with highly directional antenna arrays to counter this loss and reach its receiver [2]. However, beamforming constrains most of the transmission energy to the line-of-sight (LOS) component and very few, if any, significant non-LOS components exist [6,7]. Thus, transmission in this band is highly directional and point-to-point. Such mm-wave channels can support high data rates due to their vast bandwidth, but nevertheless are prone to blockage and absorption [8] due to their point-to-point nature. In contrast, microwave links are much more reliable due to rich scattering and diffraction, but cannot support as high rates as the mm-wave links. Thus, in a dual-band setting, conventional traffic and control information can be reliably communicated over microwave links, and high data-rate traffic can be sent through mm-wave links [2,7,9,10,11,12,13,14,15].
Most studies on microwave and mm-wave dual-band transmission have focused on how to improve network layer performance metrics of cellular access or backhaul networks by using the high-bandwidth, highly directional mm-wave links [9,13]. For example, the authors in [7] posed the problem of optimal resource allocation in a cellular setting in the dual microwave and mm-wave band, and showed that certain network level performance parameters, e.g., the number of simultaneously supported users and the link connection probability, are vastly improved with their proposed solution. Similarly, the authors in [11] study a two-tier cellular network where the 60 GHz band is used to create point-to-point directional links, and the 70 GHz band is used to establish long range connections just as the microwave band is used in our work, and propose a hybrid scheme involving both bands that improves the network throughput. In a more related article [14], the authors characterize the benefits of beamforming over a point-to-point dual band multi-antenna channel, and study the performance of a hybrid adaptive queueing scheme over both bands that maximizes the delay-constrained throughput.
Recent works on joint transmission in the microwave band and mm-wave band [14,16,17,18,19,20] indicate that it is possible to isolate the transmissions in the microwave band from that in the mm-wave band, and communicate over the two bands simultaneously. For example, the authors in [14] designed a queue-based scheme that transmits from a single transmitter to a single receiver simultaneously over the 3 GHz microwave band and the 30 GHz mm-wave band using beamforming, and conducted successful practical experiments in this dual-band setup. In addition, Intel has recently announced the production of a dual-band modem that supports both sub-6 GHz and 28 GHz bands [16]. Moreover, recent works on resource allocation in the microwave and mm-wave dual-band setting in [19,20], and their variant in [21], show that simultaneous transmission in both microwave and mm-wave bands are indeed feasible, and are gaining acceptance as an architecture for cellular access in 5G.
We study here the performance of a two-transmitter two-receiver () dual-band interference channel from an information theoretic perspective, where a transmitter communicates to its respective receiver over the microwave band and the mm-wave band simultaneously. In the microwave band, each receiver observes the superposition of signals from both transmitters as in a conventional single band Gaussian interference channel (GIC) [22]. However, as the mm-wave channels are considered to be highly directional, a transmitter in this band is well-modeled as being able to transmit towards one intended receiver, while causing negligible to no interference to the other receiver [6]. This raises the question: to which receiver should a transmitter in the mm-wave band transmit? In this GIC, the transmitters in the mm-wave band can transmit from: (a) the first transmitter () to the first receiver (), and the second transmitter () to the second receiver (); (b) to , and to ; (c) and to ; or (d) and to . We focus here on the first two cases where the transmitters in the mm-wave band either transmit (a) from to , and from to , i.e., in the direct channels; or (b) from to , and from to , i.e., in the cross channels; or (c) share the spectrum between the two modes. We denote the resulting channels by Direct-Link IC (DLIC), Cross-Link IC (CLIC) and Direct-and-Cross-Link IC (DCLIC), respectively, and study their capacity.
The capacity of the conventional single band GIC [22] has been characterized when it has strong [22] or very strong interference [23]. We know that, under strong interference, encoding the message at each transmitter with independent Gaussian distributed codewords, and decoding both the desired and the interfering messages at each receiver is the optimal strategy [22]. However, if the GIC has weak interference [24], the capacity and the optimal strategy is still unknown in general.
The parallel Gaussian IC (PGIC) consists of several orthogonal parallel channels (sub-channels) such that a conventional GIC operates in each sub-channel without interfering with that in other sub-channels [25]. The optimal strategies for the PGIC are not known in general; however, its capacity was characterized in [26] when the GIC in each sub-channel has strong interference. In a related study, the capacity of the ergodic fading GIC was characterized in [27] when each fading state has strong interference. In the dual-band GIC considered here, the number of channel uses in the microwave band and the mm-wave band may differ. We model this with a bandwidth mismatch factor (BMF) in the system model. Note that the dual-band GIC considered here is a special case of the ergodic fading GIC in [27] if one identifies each fading state as a different sub-channel. In the special case that the bandwidth mismatch factor between the microwave and mm-wave bands is 1, it is also a special case of the PGIC in [26].
Moreover, the studies in [26,27] show that if every sub-channel (or fading state) has strong interference, the capacity is achieved by encoding jointly over all sub-channels and decoding messages from both transmitters. Encoding independently over each sub-channel of a PGIC is suboptimal in general [28], except for the GIC in the very weak (noisy) interference regime [29]. In fact, joint encoding over all sub-channels generally achieves better rates as it can potentially offset the weak interference in one or more sub-channels if the other sub-channels have strong interference [28].
In this sequel, we study the capacity of the DCLIC and the CLIC. First, we present a useful result that decomposes the capacity of the DCLIC into that of the underlying CLIC and the set of direct channels. This result shows that the capacity of the DCLIC can be established if the capacity of a corresponding CLIC is known. Hence, we focus on the CLIC next. In particular, we consider two specific classes, the strong CLIC and the weak CLIC, where the underlying GIC in the microwave band has strong and weak interference, respectively, and characterize sufficient conditions on the channel parameters under which their capacity is established.
Resource allocation techniques that maximize the sum-rate or throughput of interference channels have been investigated throughly (e.g., see [25,30,31]) as they indicate how to allocate resources in practice. The DCLIC models a basic multiuser network over the microwave and mm-wave dual-band, whose performance is likely to be dominated by the mm-wave channels due to their large bandwidths [9]. Thus, it is useful to understand how to optimize the performance of the DCLIC over the parameters in the mm-wave band. Therefore, we study the power allocation in the direct and cross channels in the mm-wave band that maximizes the sum-rate of the DCLIC. We derive the optimal powers in closed form, and study how the channel parameters influence the optimal power allocation.
The contributions of this paper are summarized as follows:
- We show that the capacity region of the DCLIC can be decomposed into the capacity region of the underlying CLIC and two non-interfering direct links in the mm-wave band. This illustrates that the cross channels are actively involved in characterizing the capacity of the CLIC, whereas the direct channels improve the rates of individual users.
- We characterize the capacity of the strong CLIC, and observe that the strong interference condition in the microwave band is sufficient to characterize the capacity.
- For the weak CLIC, we characterize sufficient channel conditions under which its capacity is established. This shows that even if the GIC in the microwave band has weak interference, adequately strong cross channels in the mm-wave band are sufficient to characterize the capacity.
- We characterize the optimal power allocation in the direct and cross channels that maximizes the sum-rate of the DCLIC, and study channel conditions under which the optimal power allocation either assigns the entire power budget to a specific subset of channels, or shares the power budget among all channels. We establish a direct relation between the channel parameters and the optimal powers, from which we observe the following:
- -
- The optimal power allocation distributes the power budget among the direct and cross channels following two properties: a waterfilling-like property and a max-min property.
- -
- When the power budget is sufficiently small, the optimal allocation assigns power to either both direct channels, or both cross channels and at most one direct channel.
- -
- Due to the max-min property, the optimal allocation imposes a maximum limit on the cross-channel powers. When the power budget exceeds a certain threshold, the limit on the cross-channel powers are reached, and all additional increments to the power budget are then added only to the direct channels that do not have such limits.
- -
- If the underlying GIC in the microwave band has very strong interference, the optimal power allocation assigns the power budget entirely to the direct channels.
- -
- If the channel parameters satisfy one of the following criteria, then transmitting only in the direct channels is approximately optimal, in the sense that the difference between the sum-rates resulting from allocating to only direct channels and allocating optimally in all channels, is negligibly small: (a) the transmit powers in the underlying GIC in the microwave band is very small; or (b) the cross channel gains in the mm-wave band are very large.
The rest of the paper is organized as follows. We define the system model in Section 2. We present the decomposition result on the DCLIC and the capacity of the strong CLIC in Section 3. We present the capacity result on the weak CLIC in Section 4. In Section 5, we formulate the optimum sum-rate problem and discuss its solution, and we conclude in Section 6.
Notation: We denote sets in calligraphic (e.g., ), except the sets of reals, positive reals, and positive integers, which are denoted by , and , respectively. Vectors are in bold (e.g., ), and denotes that each element of is in , where is the zero vector. We denote by the statistical expectation of a random variable (RV) Y, and by an RV following the Gaussian distribution with mean and variance . We also denote an n-length vector by , the empty set by ∅, by , and define .
2. System Model
First, we define the discrete memoryless (DM) model of the DCLIC, and from that we define the Gaussian models. In the DCLIC, a bandwidth mismatch between the first (microwave) band and the second (mm-wave) band may exist. Thus, we assume that during n accesses of the first band, the second band is accessed times as cross channels, and times as direct channels. We model this by two bandwidth mismatch factors (BMF) . Thus, the total normalized channel uses in the second band is asymptotically , which is shared between the cross channels () and direct channels (). For ease of exposition, we denote by ,
The DM interference channel is defined by where and are the discrete input and output alphabets of user k, and is the set of channel transition probabilities [32] (Chapter 6.1). We define the DM DCLIC similarly by the tuple, , where and are the input and output alphabets of the interference channel in the first band, and are the input and output alphabets for the to direct channels in the second band, and and (respectively and ) are the input and output alphabets for the to (resp. to ) cross channel in the second band. The joint probability mass function (pmf) of the DCLIC decomposes as
We define a code for the DCLIC to consist of (a) two uniformly distributed and independent message sets, and , respectively, for and ; (b) two encoding functions, and , respectively for and such that ; and (c) two decoding functions, and , respectively, for and such that .
We define the decoding probability of error at by We say that is an achievable rate pair of the DCLIC, if there exists a sequence of codes such that and as for . The capacity region of the DCLIC is defined as the closure of the set of all achievable rate tuples.
Following the above notations, the GIC in the first band of the Gaussian DCLIC is modeled as in [22]. The signals received at and are given by
where , are coefficients of the channels from to , ( are normalized to 1 as in [22]), and are i.i.d. noise, . In addition, the codewords now satisfy the average power constraint, . The cross links in the second band of the DCLIC are point-to-point, and are modeled as
where , are coefficients of the channels from to , , and are i.i.d. noise. The codewords satisfy the average power constraint, The direct links in the second band are similarly modeled as
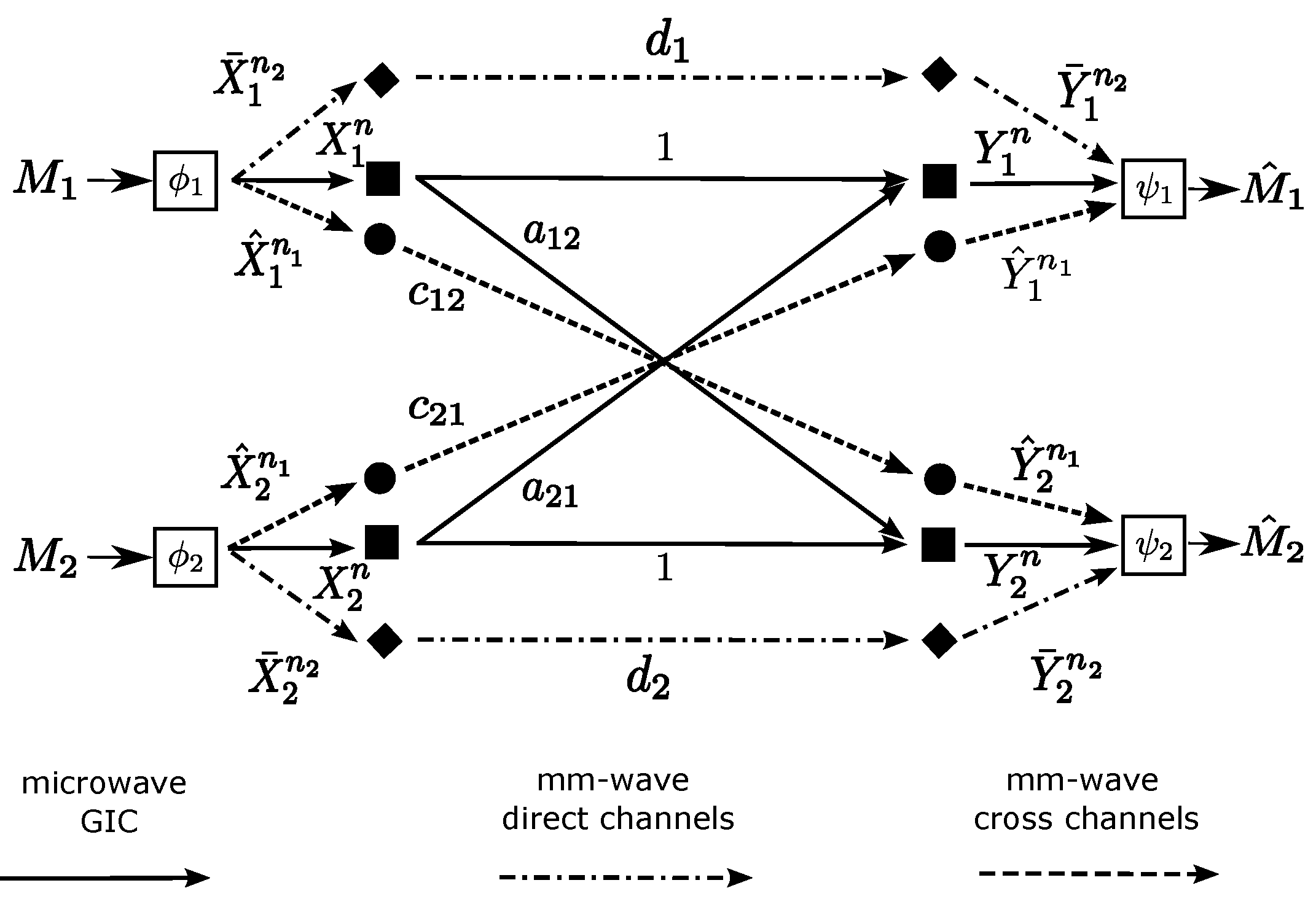
where , are the direct channel coefficients, are i.i.d. noise, , and the codewords satisfy the average power constraint, as well. We present the Gaussian DCLIC in Figure 1. We define a code for the Gaussian DCLIC from that of the DM DCLIC, by choosing all input and output variables to be in , and by imposing the average power constraints on the codewords, , and , defined above.
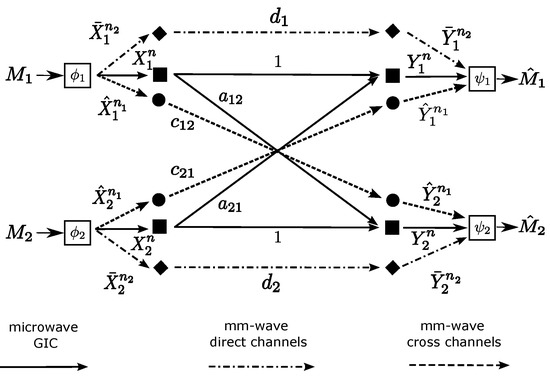
Figure 1.
System model of the Gaussian DCLIC, which consists of an underlying GIC in the microwave band and the set of direct channels and cross channels in the mm-wave band.
Next, the Gaussian CLIC is defined from the Gaussian DCLIC by imposing the restrictions, and , such that the channel outputs in the CLIC are described by (1)–(4), respectively. A code for CLIC is defined from a code of the Gaussian DCLIC with the above-mentioned restrictions.
For ease of exposition, we define two classes of the CLICs: we say that a CLIC is a strong CLIC or a weak CLIC, if the underlying GIC in the first band has strong interference (i.e., , ) or weak interference (i.e., , respectively. Moreover, a symmetric CLIC is a CLIC where , , , and . In addition, a symmetric DCLIC is a DCLIC with an underlying symmetric CLIC, and .
3. Decomposition Result on the Capacity of the DCLIC
Recall that, in the DCLIC, there are n channel uses in the first band, cross channel uses in the second band, and direct channels uses in the second band. We show below that the capacity of the DCLIC can be decomposed into the capacity of the underlying CLIC, complemented by the direct channels that are used to transmit individual user information to their respective receivers.
Theorem 1.
The capacity region of the DCLIC with BMFs and is given by the set of all nonnegative rate tuples that satisfy the decomposition
where is an achievable rate tuple in the underlying CLIC with BMF .
Proof.
The proof is relegated to Appendix A. ☐
Therefore, an achievable rate pair in the DCLIC with BMFs and consists of a rate pair achievable in the CLIC with BMF , and the rate pair achieved in the direct channels, . The capacity of the DCLIC can thus be characterized from that of the underlying CLIC. Hence, we focus on the CLIC next. In particular, we consider two specific classes of the CLIC, the strong CLIC and the weak CLIC. First, we present the capacity of the strong CLIC.
Lemma 1.
The capacity region of the strong CLIC with BMF is given by the set of all nonnegative rate tuples () that satisfy
The proof of Lemma 1 follows from that of [27] in a straightforward manner. Hence, we omit the proof here, and discuss only the key idea. In the strong CLIC, the GIC in the first band has strong interference. Additionally, in the second band, the cross-channel gains are positive and the direct-channel gains are zero, which results in a GIC with strong interference. Hence, the strong CLIC is a parallel GIC with strong interference in both bands. The capacity is thus achieved by encoding jointly over both bands and decoding messages from both transmitters as in [27].
Moreover, the capacity of the DCLIC with strong underlying CLIC, which follows from Theorem 1 and Lemma 1, is characterized below.
Corollary 1.
The capacity region of the DCLIC with BMFs and that has a strong underlying CLIC is given by the set of all nonnegative rate tuples () that satisfy
Furthermore, if the DLIC, where the second band is used as direct channels only, has strong underlying GIC, the capacity region follows from Corollary 1 with and .
4. Capacity of the Weak CLIC
Now, consider the weak CLIC where the underlying GIC has weak interference. Recall that in a conventional GIC with weak interference, decoding both messages is suboptimal in general. However, in the weak CLIC, if messages are encoded jointly over both bands and the cross channels in the second band are sufficiently strong, then decoding both messages is indeed optimal. We characterize the sufficient conditions below.
Lemma 2.
Provided the channel parameters of the CLIC with BMF satisfy , , as well as the conditions
the following inequalities hold
for all and with product distributions on , which satisfy the average power constraints, .
Proof.
We prove only (18) as (19) follows similarly. From the system model for the first band in (1) and (2), we have
where (a) follows from unconditioning, , and since ; (b) follows since , and thus , where , are i.i.d.; (c) follows since the first term in b is maximized by , i.i.d.; (d) follows from the chain rule; (e) follows since are i.i.d., and since unconditioning does not reduce entropy; (f) follows by replacing the i.i.d. RVs, and , with and respectively; (g) follows by invoking the worst additive noise result of [33] to every mutual information term inside the summation of (f), where , with , and ; (h) follows from the differential entropy of Gaussian RVs; (i) follows since the log function is concave in ; (j) follows since ; and (k) follows from condition (16). ☐
We characterize the capacity of the weak CLIC under the conditions of Lemma 2 below.
Theorem 2.
Proof.
The proof is relegated to Appendix B. ☐
The result shows that, in the weak CLIC, where sufficient interference forwarding is not possible through the underlying weak GIC, if the cross links in the second band are sufficiently strong, it is possible to forward enough interference by encoding jointly over both bands such that decoding both messages becomes optimal. Hence, these conditions can be classified as being able to push the receivers to the “strong interference regime over both bands”.
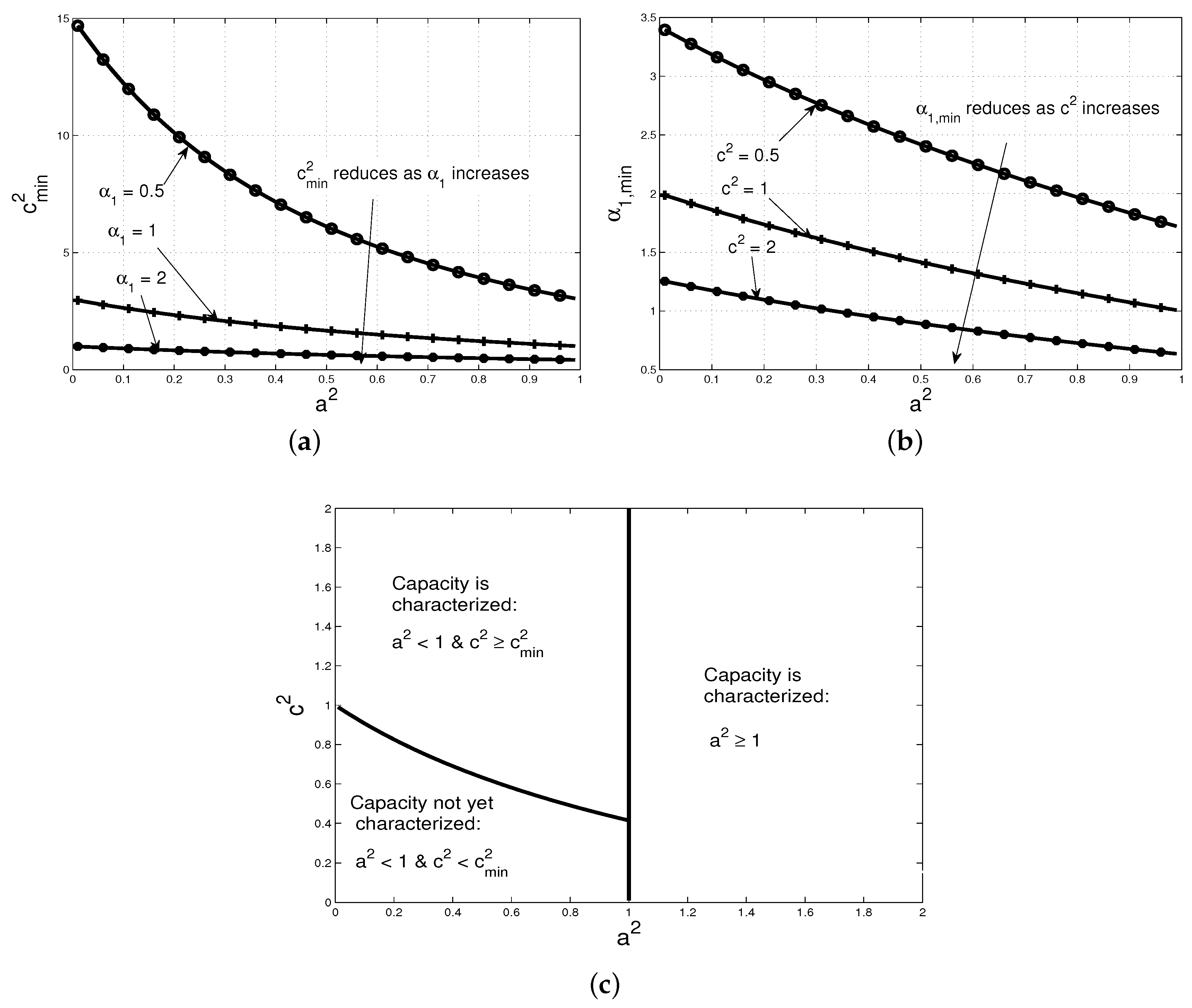
Next, we illustrate the relationship between the channel parameters in (16) and (17) with an example of a symmetric weak CLIC, where (16) and (17) imply the same condition. We denote by , and , respectively the minimum and the minimum required to achieve (16), and show the interplay between and for .
In Figure 2a, we plot against for . Note that reduces monotonically as or increases. This follows since, if increases, then the first band forwards more interference, and, if increases, then the pre-log factor of the cross-channel capacity increases. In either case, smaller is required to achieve (16). Similarly in Figure 2b, we plot against for , and note that reduces as or increases. Finally, in Figure 2c, we depict the set of cross-channel gains ( and ) of a symmetric CLIC with , and partition it depending on whether the capacity has been characterized in each set. Note that the capacity for the set where and has not been characterized yet.
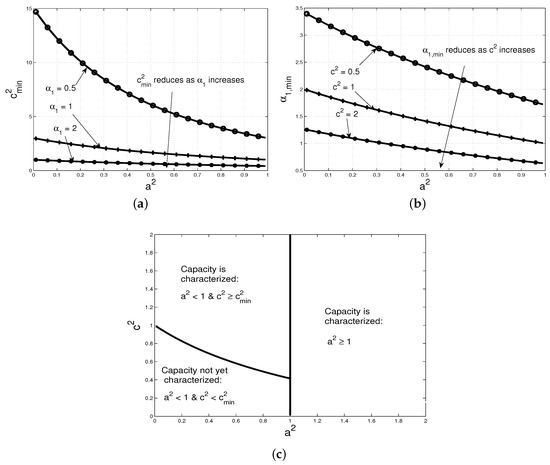
Figure 2.
In (a,b), we plot and , respectively. In (c), the channel gains of a symmetric CLIC is partitioned based on whether its capacity has been characterized in each set.
5. The Optimal Sum-Rate Problem
In this section, we study the power allocation scheme over the direct and cross channels in the DCLIC that maximizes its sum-rate. Recall from Corollary 1 that, if the underlying GIC of the DCLIC has strong interference (i.e., and ), then the sum-rate of the DCLIC is known for all values of the remaining channel parameters, and, in particular, for all transmit powers in the second band. Therefore, we pose this problem for the class of DCLICs with strong underlying GIC (see [A1] below). Also recall that the normalized bandwidth () of the second band is shared between the direct channels () and the cross channels (). We denote the fraction of alloted to the direct and cross channels by and , respectively, where and , and . Thus, provides a trade-off between the bandwidths in the direct channels () and the cross channels ().
We formulate the problem under the following assumptions:
- the underlying GIC of the DCLIC has strong interference, but not very strong interference, and ;
- the underlying GIC of the DCLIC satisfies: ;
- and are fixed a priori;
- the transmission power in the direct channel () and cross channel () from transmitter k () satisfy the constraint, , where P is the power budget.
In [A1], we assume that the underlying GIC does not have very strong interference, since the power allocation in that case is trivial (see Section 5.4). For ease of exposition, we assume in [A2] that the underlying GIC receives equal power in both its receivers. Note that the class of GICs that satisfies [A2] also contains the symmetric GICs. Moreover, the analysis under [A2] reveals enough insight such that it can be extended to the general case (see Remark 1).
In [A3], is assumed to be fixed a priori and known. This models practical constraints in many wireless networks where dynamically allocating the bandwidth may not be feasible or straightforward [34]. In [A4], we assume that power budget (P) in both transmitters are the same. There is no loss of generality in this assumption as the relative difference between the power budgets of the first and the second user can be absorbed into the channel gains.
5.1. Problem Formulation and Solution
For a fixed power allocation in the mm-wave channels, we denote the sum-rate achievable at and in (14) and (15) by and , and the interference-free sum-rate given by the sum of individual rates in (12) and (13) by , and present them below
where and . Furthermore, they satisfy due to [A2] and [A1]. Therefore, a necessary and sufficient condition for R to be an achievable sum-rate of the DCLIC is , for some power allocation (). The optimization problem that maximizes R over the transmit powers () is then
Note that is a convex optimization problem, since its objective function R is linear, the equality constraints (30) and (31) are affine, and the inequality constraints (27)–(29) are convex. Furthermore, satisfies Slater’s condition [35] (Chapter 5.2.3), and thus it can be solved using the Karush–Kuhn–Tucker (KKT) conditions [35] (Chapter 5.5.3). We relegate the details to Appendix C.
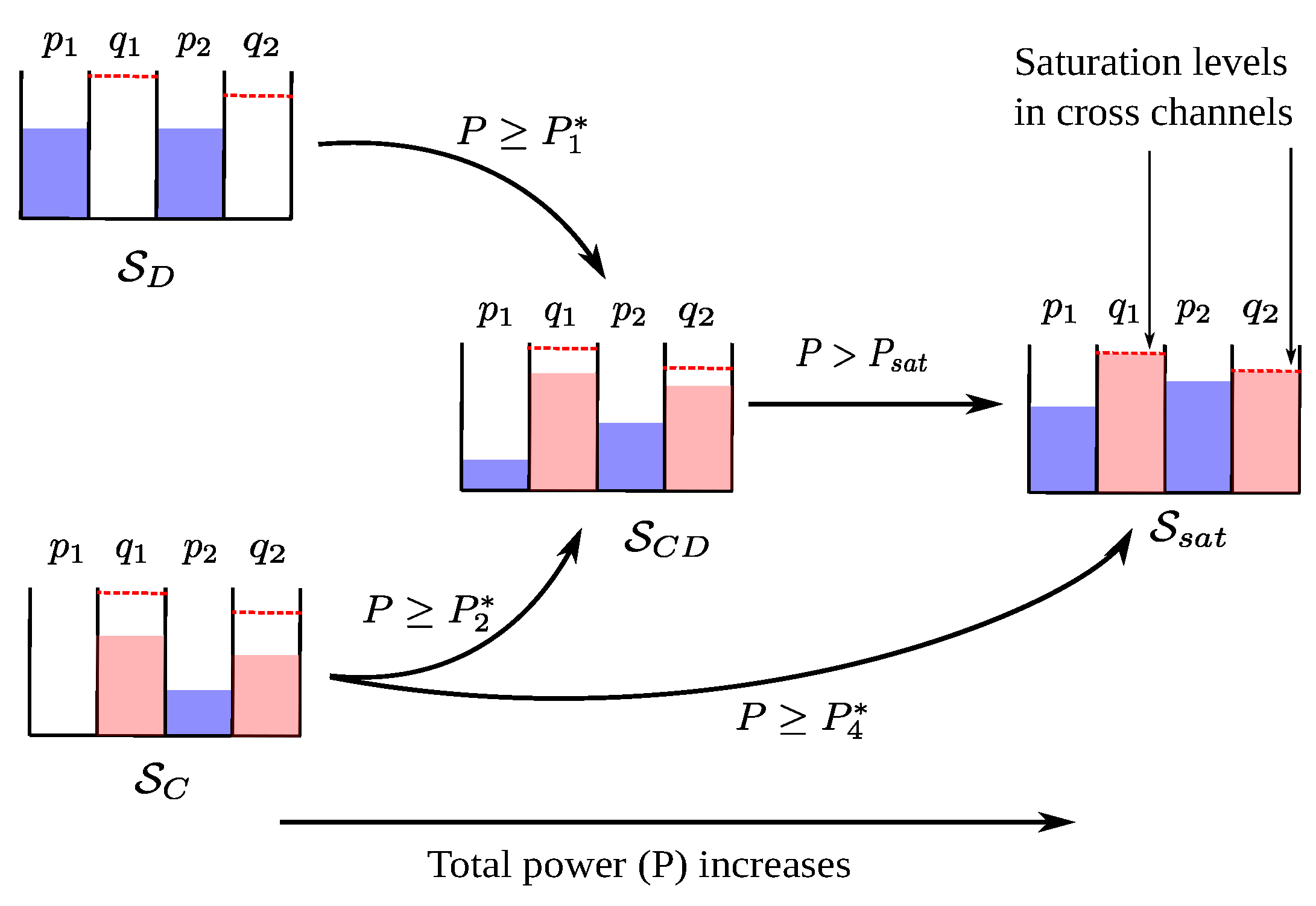
It is well known that optimal power allocation in parallel Gaussian point-to-point channels follows the Waterfilling (WF) property. Due to this, if the power budget is sufficient small, it is allocated entirely to the “strongest” sub-channel, and, as the power budget is increased, power is allocated to the other “weaker” sub-channels, in addition to the strongest one (see Chapter 3.4.3 in [32]). In the ensuing discussion, it becomes clear that the optimal power allocation in (hereby referred to as “the optimal allocation”) has two noticeable properties: a WF-like property, due to which it assigns power to the cross and direct channels following a WF-like allocation, and a max-min property, due to which it increases the minimum of the sum-rate constraints.
Due to its WF-like property, the optimal allocation assigns the entire power budget (P) to only a subset of all the direct and cross channels, depending on channel conditions that indicate whether the direct channels are stronger than the cross channels or vice versa. Moreover, if P is sufficiently increased, it becomes optimal to allocate power to the remaining set of channels. In addition, since the objective of the problem is to maximize , the optimal allocation assigns powers in such a way that minimizes or eliminates any difference between and . We observe that, due to this property (max-min property), the optimal allocation imposes a maximum limit on the cross-channel powers, which is unlike WF in [32] where no such limit exists.
We study the optimal allocation by partitioning the entire set of channel parameters and P into disjoint sets (), such that the optimal allocation can be classified according to the power levels in the direct and cross channels in each set. Without loss of generality, we present the optimal allocation under in Table 1, and study it in detail. In this case, only fours sets, , , and , are sufficient. The power allocation under can be readily obtained from Table 1 by swapping the indices 1 and 2, and the case with is briefly discussed in Section 5.3.

Table 1.
Optimal power allocation and conditions of sets in
For notational convenience, we express the optimal powers and the conditions of the sets in Table 1 in terms of the following functions:
and . We relegate the details of the derivation to Appendix C.
In the following, we use “the optimal allocation” and interchangeably to refer to the optimal power allocation for under , and discuss some interesting characteristics of .
First, the condition in implies that the direct channels are “stronger” than the cross channels, in the sense that, for sufficiently small P, the sum-rate achieved from allocating P only to both direct channels is larger than that achieved from any other subset of channels. Thus, following its WF-like property, allocates P entirely to the direct channels, i.e., , and zero power to the cross channels, i.e., . This allocation also achieves , which is consistent with the max-min property of .
Second, the condition in implies that the cross channels are “stronger” than the direct channels, in the sense that, for sufficiently small P, the sum-rate achieved from allocating P to both cross channels and a direct channel is larger than that achieved from only direct channels. Note that, unlike in , needs to allocate power to a direct channel in addition to both cross channels in , since allocating P entirely to the cross channels causes an imbalance between and () due to , which violates the max-min property. Therefore, shares P among the cross and direct channels from to preserve . Moreover, the condition ensures that power in the cross channels have not yet reached their maximum limits.
Third, as P is increased, shares P among all channels in . As P increases, the additional benefits from transmitting in a particular subset of channels (either direct channels as in , or cross and direct channels as in ) begins to diminish. Thus, following its WF-like property, starts sharing P among all channels. In addition, shares P in such a way that preserves .
Finally, if P is increased sufficiently, follows the allocation in , where the cross-channel powers have reached their maximum limits, . Therefore, as P increases further, all subsequent increments of P is allotted to only direct channels. We now say that the cross channels are saturated, in the sense that allocating more power beyond these limits does not improve the sum-rate. Such limits for the cross channels in is unlike the WF allocation in [32].
The cross channels become saturated due to the max-min property of . Recall that, in , allocates powers to all channels, which increase as P increases. The increases in and results in the increase of and by an equal margin. However, an increase in only increases , and an increase in only increases . Now, note that, due to its max-min property, preserves in , , and . However, there may exist a gap between and . As and are increased, this gap reduces and finally becomes zero in . At this point, both cross channels become saturated simultaneously. If any more power is allocated to either or , a suboptimal sum-rate will result. Therefore, maintains and diverts all additional power to the direct channels.
Note that once, in , the sum-rates achieved by joint decoding ( and ) become equal to the sum of interference-free user rates (), which is somewhat similar to the behavior of the GIC under very strong interference. At this point, all additional increments in P are allocated to the direct channels to increase the individual user rates.
In addition, note that the sets form a partition due to their construction using the optimal Lagrange multipliers (defined in Appendix C). Thus, the conditions in Table 1 are mutually exclusive.
Moreover, these conditions can be equivalently described in terms of three critical powers, , defined by where is defined in (33)–(35) for . Specifically, the conditions of , , and are given by , , and , respectively. In addition, we note that the direct channels are “stronger” than the cross channels in the sense specified above, if . Similarly, if , the cross channels are “stronger” than the direct channels. Furthermore, if , the cross channels are said to be “much stronger”, in the sense that continues allocating power to the cross channels as in until they become saturated, and only after that it assigns power to both direct channels.
We note from the mutual exclusiveness of and that, if then no exists that satisfies . This shows that, if the direct channels are stronger, the allocation in is suboptimal for any . Similarly, if then no exists such that , and thus the allocation in is suboptimal for any .
5.2. The Waterfilling-Like Nature of the Optimal Power Allocation
Now, we characterize how adapts the power allocation, as the power budget (P) increases and crosses the critical thresholds . We say that follows the sequence where , if allocates power as in for sufficiently small P, and then adapts the powers according to the allocation in and as P increases. In this regard, we note that follows one of the three sequences, as explained below and illustrated graphically in Figure 3.
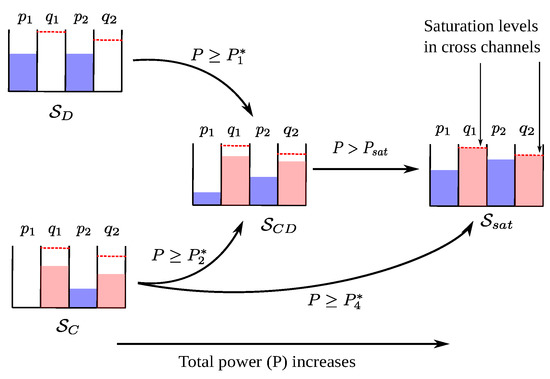
Figure 3.
Due to its WF-like property, follows one of the three sequences depending on . The saturation levels in the cross channels are due to its max-min property.
- If : follows the sequence (denoted by [S1]). Since the direct channels are stronger, allocates all of P to them as in when P is sufficiently small (i.e., ). However, as P increases, the additional benefit from transmitting only in the direct channels decreases, and thus, when , begins transmitting in both cross and direct channels as in . This allocation follows from its WF-like property, and remains optimal for all . Finally, when , the max-min property of comes into effect, and thus the cross channels become saturated and starts following the allocation in . Note that, in this case, the saturation threshold for P is .
- If but is not satisfied: follows the sequence ([S2]). This case is similar to [S1] above, except for the fact that now the cross channels are stronger. Hence, transmits in the cross channels and the direct channel with gain as in when P is sufficiently small (i.e., ). Next, following its WF-like property, starts transmitting in all the direct and cross channels as in when . Finally, when the cross channels become saturated, and follows the allocation in thereon. The saturation threshold for P in this case is .Note that, whenever , follows [S2] irrespective of how , and compare, except in two cases: (a) , where follows [S3], described next, and (b) , which is infeasible as they violate the mutual exclusiveness of and .
- If : follows the sequence ([S3]). In this case, the cross channels are much stronger than the direct channels. Hence, similar to [S2], allocates power to both cross channels and a direct channel as in when P is sufficiently small (i.e., ). As P increases and , the cross channels become saturated, and begins assigning powers to all channels as in . Interestingly, in this case, skips . This shows that, since the cross channels are much stronger, it is optimal to allocate power as in until they become saturated at , beyond which the allocation in becomes optimal.
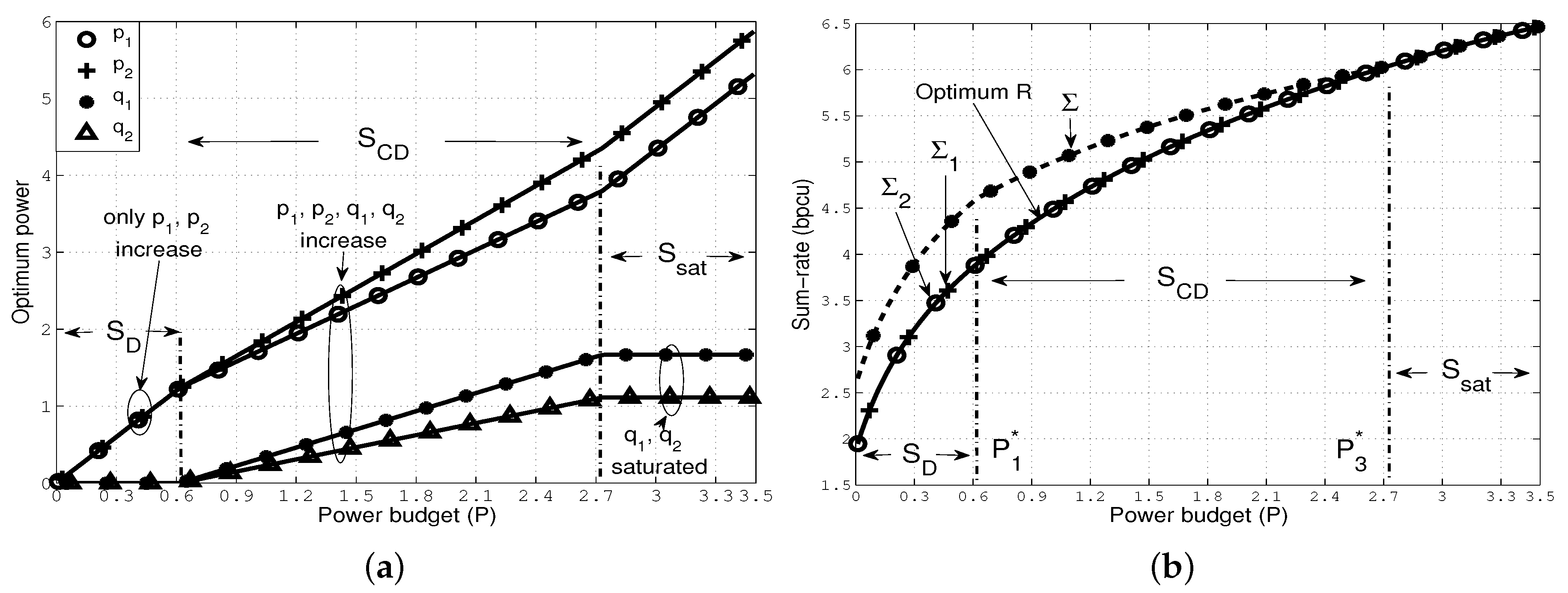
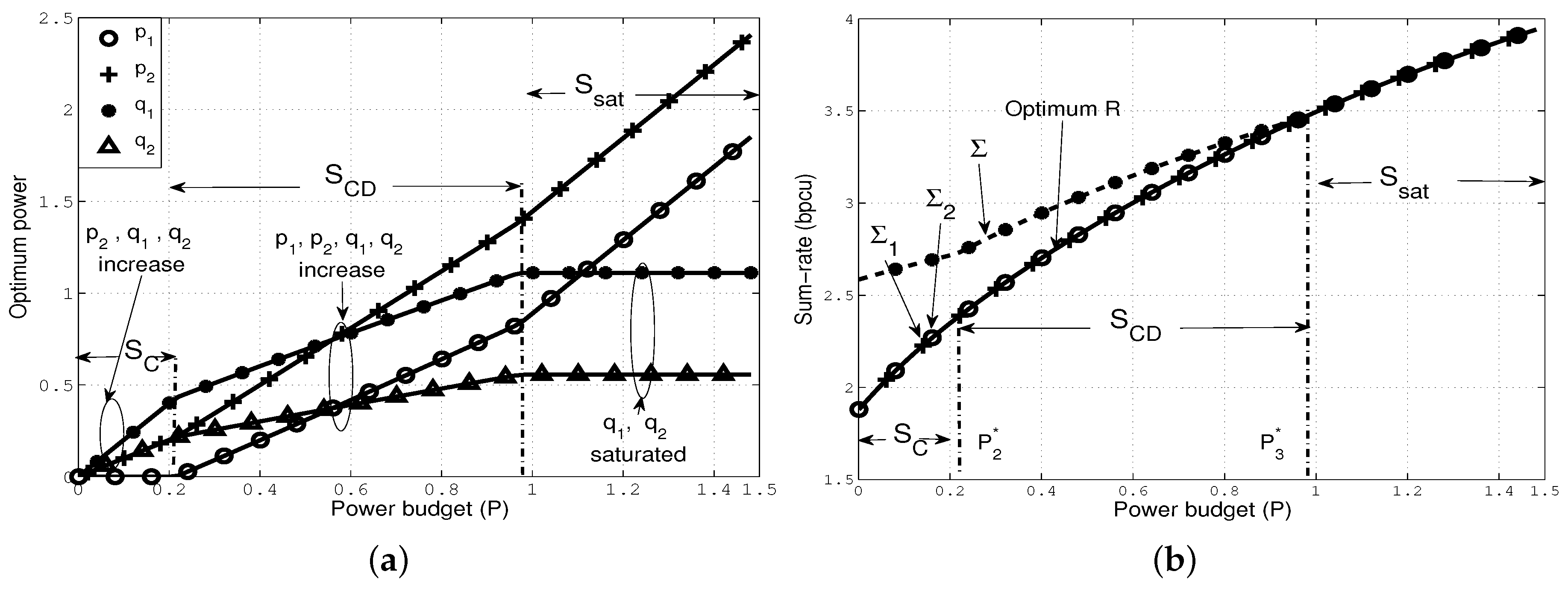
We illustrate the characteristics of with two numerical examples where we choose the following parameters, . First, we illustrate an example of [S1] by additionally choosing , such that the direct channels are stronger than the cross channels in the sense that and . In Figure 4a, we plot the optimal powers against the power budget P, and note the following: (i) when , allocates P entirely to the direct channels as in , and thus and increase with P, and ; (ii) when , allocates power to all channels as in , and thus and also increase with P; (iii) finally, when , follows where the cross channels become saturated simultaneously, and all increments of P are added to and .
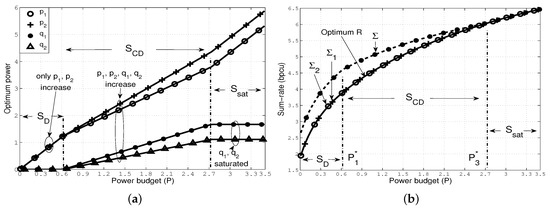
Figure 4.
Optimal power allocation that follows the sequence [S1] (a) optimal power allocation ; (b) the resulting sum-rate constraints.
We depict the resulting constraints , and in Figure 4b. First, note that preserves for all P. However, there exists a gap between and in and . Specifically, in , the gap remains constant (); in it reduces gradually as transmits in the cross channels, and, in it becomes zero as achieves , as expected.
Next, we illustrate an example of [S2] with the channel gains, such that the cross channels are stronger than the direct channels in the sense that and . In Figure 5a, we plot the optimal powers against P, and observe the following: (i) when , follows the allocation in , and thus , and increase with P, whereas ; (ii) when , allocates power to all channels as in , and thus now increases with P; (iii) finally, when , follows , and thus the cross channels become saturated simultaneously, as expected in [S2]. In Figure 5b, we plot the sum-rate constraints, and note that achieves in all the sets. In addition, the gap between and is gradually offset as transmits in the cross channels in and , and it finally becomes zero in , as expected. We omit an example of [S3] (), which is somewhat similar to [S2].
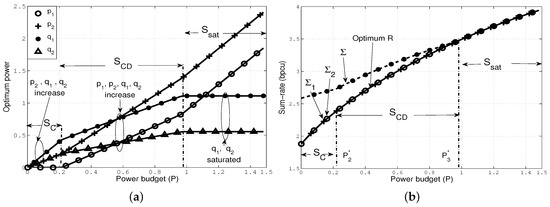
Figure 5.
Optimal power allocation that follows the sequence [S2] (a) optimal power allocation ; (b) the resulting sum-rate constraints.
Remark 1.


Recall that presents the solution for under and [A2] (implying ). If remains unchanged, and is formulated under a more general assumption [A2G]; where , then seven disjoint sets are needed to describe the optimal allocation (now denoted by ). The conditions and power allocations of these sets are found by solving the corresponding KKT conditions in a similar way to that of under [A2] in Appendix C. Hence, their explicit derivation is omitted for brevity. Of the seven sets, the first four sets, , , are counterparts of the corresponding sets in Table 1, in the sense that the power allocation in is similar to that in as discussed below. The remaining three sets are “new” in the sense that the power allocation in these sets do not resemble that in any of the sets in Table 1.
The power allocation in the first four sets are similar to that of in that (a) when the power budget (P) is sufficiently small, allocates power to only both direct channels (in ), or both cross channels and one direct channel (in ) depending on whether the direct or the cross channels are “strong” as in or before; (b) as P is increased allocates power to all channels (in ) as in ; and (c) when P is sufficiently large, both cross channels become saturated simultaneously, and allocates all additional increments of P to only the direct channels (in ) as in before. Note that the optimal powers and the critical powers of differ slightly from that of due to the general assumption [A2G]. For conciseness, we omit the conditions, and present the optimal powers in Table 2.

Table 2.
Optimal power allocation in the first four sets in
Here , and and η are defined in (39) and (40) below
with , defined in (37). Note that, under [A2] (), the powers in Table 2 simplifies to that in Table 1.
Next, we present the optimal powers and the critical powers of the three new sets in Table 3, where

Table 3.
Optimal power allocation and conditions of sets in
The power allocation for the new sets can be understood by following the WF-like and max-min properties of . For illustration, we explain the allocations in and . In , the cross channels are stronger than the direct channels. Thus, due to its WF-like property, preferably allocates as much of P to the cross channels as possible. However, under [A2G] () and , allocating power to both cross channels results in , and does not increase as much as possible. This results in a suboptimal sum-rate. Therefore, allocates , which increases only , and assigns , which represents the allocation in .
Furthermore, as P increases and , additional benefits from transmitting only in the cross channel with gain reduces, and thus starts allocating a fraction of P to the direct channel with gain , due to its WF-like property. Thus, follows the power allocation in , which remains optimal as long as . The power allocation in can be interpreted similarly.
The important insight is that can be explained with the WF-like and max-min properties as in , and it does not reveal any new fundamental properties.
5.3. Optimum Power Allocation in the Symmetric DCLIC
We briefly discuss the optimum allocation for the symmetric DCLIC, where , , , and . Due to symmetry, considering only symmetric power allocation of the form is sufficient, and does not cause loss of generality. Moreover, any feasible (symmetric) power allocation achieves , rendering the constraint in (28) redundant. The sum-rate optimization problem in this case can be formulated and solved as in , and is omitted here for brevity. In addition, we denote the optimal power allocation for this case by .
In this case, can be described by the power allocation in four disjoint sets, , which are counterparts of the sets in Table 1. The conditions and optimal powers in these sets are given in Table 4, and they can be derived following the same procedure as in Appendix C, and thus is omitted here.

Table 4.
Optimal power allocation and conditions of sets in
Moreover, the critical powers are now given by
where .
has the same WF-like and max-min properties as that of . In fact, a rudimentary inspection of the conditions reveals that follows one of the three possible sequences of sets depending on the channel gains, as before:
- If (direct channels are “stronger”): follows the sequence . It transmits only in the direct channels as in when , then transmits in all channels as in when , and finally starts following the allocation in when .
- If (cross channels are “stronger”): follows the sequence . It transmits only in the cross channels as in when , then transmits in all channels as in when , and finally follows when .
- If (cross channels are much “stronger”): follows the sequence . It follows when , and then follows when , while skipping altogether.
Thus, allocates all of P to either both direct or both cross channels if P is small, and then shares P among all channels as P increases. In addition, when P is increased beyond the saturation threshold, the cross channels become saturated. Note that, due to symmetry, needs to transmit in both cross channels only in to preserve , unlike in , where additionally transmits in a direct channel.
We note the following, which are revealed due to symmetry. First, if , the direct channels are considered to be stronger than the cross channels. Similarly, if , the cross channels are considered to be stronger. Moreover, in the special case of , neither the direct nor the cross channels are stronger than the other, and thus allocating P entirely to only direct or cross channel would be suboptimal. Therefore, transmits in all channels as in when . Finally, the condition implies that the cross channels are much stronger than the direct channels. Thus, it is optimal to transmit only in the cross channels as in until they become saturated, at which point the allocation in becomes optimal. Note that these conditions follow trivially from the corresponding conditions of [S1], [S2], and [S3] in Section 5.2 by applying symmetry.
Furthermore, due to symmetry, one can now directly observe that the conditions of the sets in Table 4 are mutually exclusive. For example, consider the conditions of , and , and note that they violate the second condition of (since ), the first condition in (since ), and the second condition in (trivially follows from ).
In Figure 6, we depict the set of cross and direct channel gains ( and ) of a symmetric DCLIC with parameters , and partition it depending on whether the direct or the cross channels are stronger.
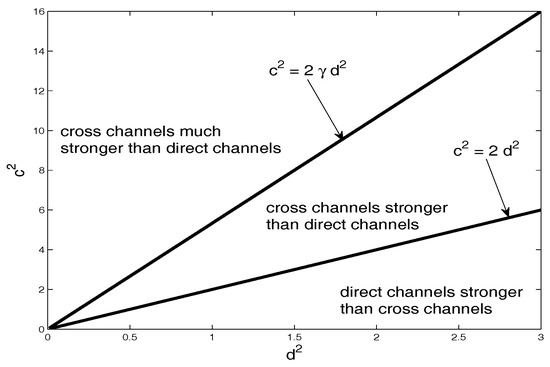
Figure 6.
The set of all and is partitioned depending on whether the cross or the direct channels are “stronger”.
5.4. Discussion and Insights
Now, we discuss some insights obtained from the power allocation in in Table 1.
First, if the underlying GIC in the first band has very strong interference, i.e., and , allocates the power budget (P) entirely to direct channels as in for all values of P. Note that, under very strong interference, we have for any feasible power allocation. Therefore, the sum-rate is maximized by maximizing , which is achieved by allocating all of P to the direct channels.
Second, if the transmit powers in the underlying GIC of the strong CLIC ( and ) are small, i.e., , then allocating P entirely to the direct channels as in , is approximately optimal for all values of P, in the sense that, the difference between the sum-rates achieved with the allocation in and that in is very small. Specifically, since , the gap between and at is very small. As P is sufficiently increased, starts transmitting in all channels as in . However, since the gap is very small, only a small fraction of P needs to be allocated to the cross channels to offset the gap, and thus almost all of P is redirected to the direct channels. The resulting allocation closely resembles that in .
We can attribute this behavior of to the fact that the GIC with strong interference () and small transmit powers () approaches the very strong interference regime (, ), where allocating P entirely to the direct channels as in is optimal for all P.
Third, if the transmit powers in the underlying GIC of the strong CLIC are large, i.e., , allocates power in all channels as in for all but a relatively small range of P. Recall that even if transmits in the direct or cross channels as in or for small P, eventually when or , allocates power in all channels as in , where the gap between and starts to reduce. However, if , this gap is very large, and thus very large P is needed to offset the gap as in . Therefore, for all moderate P, allocates power to all channels following .
Fourth, if the cross channel gains in the second band are very large, allocating P entirely to the direct channels as in is approximately optimal for all P, in the sense described in the second point above. This follows since with very large and , needs to allocate only a very small fraction of P to close the gap between and , and thus redirects the remaining of P to the direct channels. The resulting allocation thus closely resembles that in .
Finally, when , the DCLIC can be approximated by the DLIC, and thus allocating P entirely to only the direct channels is approximately optimal. On the other hand, when , the DCLIC can be approximated by the CLIC where allocating P entirely to the cross channels is approximately optimal. However, since the cross channels do not increase , the sum-rate becomes limited to when P is sufficiently large, and does not increase anymore.
6. Conclusions
Motivated by simultaneous transmission in the microwave and mm-wave bands, we considered a special class of dual band GIC. Due to their small wavelength and the use of highly directional antenna arrays, the mm-wave band can be used to form highly directional point-to-point links, allowing interference free reception at a designated receiver. For this model, we first showed that the capacity region of a DCLIC can be decomposed into the capacity of a CLIC complemented by direct channels. Moreover, we considered two specific classes of the CLIC with strong and weak underlying GIC, and obtained sufficient conditions on the channel gains under which the capacity region is characterized.
We characterized the power allocation over the mm-wave channels that maximizes the sum-rate of the DCLIC. Channel conditions have been characterized that determine how power is allocated to the channels depending on whether the direct or the cross channels are “strong”. In particular, the optimal allocation has a WF-like property due to which, when the power budget is small, it assigns the power budget entirely to either both direct channels, or both cross channels and at most one direct channel. As the power budget is increased, the optimal allocation eventually assigns power to all channels. It also has a max-min property, and, as a result, imposes a maximum limit on the cross-channel powers. This power allocation evaluates the impact of high bandwidth point-to-point mm-wave channels on the sum-rate performance, and thus can be useful in allocating resources in practice.
Potential future work includes analyzing other multi-user networks that operate with dual microwave and mm-wave bands.
Acknowledgments
Parts of this work was presented at the 2016 IEEE International Symposium on Information Theory, Barcelona, Spain, 10–15 July 2016. This work was supported by the Natural Sciences and Engineering Research Council of Canada.
Author Contributions
Both Subhajit Majhi and Patrick Mitran conceived of the idea of a dual-band GIC. Subhajit Majhi derived the results and completed writing the manuscript, with Patrick Mitran providing guidance on improving the quality of the presentation of the manuscript. All authors have read and approved the final manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| GIC | Gaussian interference channel |
| CLIC | Cross-Link interference channel |
| DLIC | Direct-Link interference channel |
| DCLIC | Direct-and-Cross-Link interference channel |
| PGIC | Parallel Gaussian interference channel |
| BMF | Bandwidth mismatch factor |
| DM | Discrete memoryless |
| RV | Random variable |
| WF | Waterfilling |
| KKT | Karush–Kuhn–Tucker |
Appendix A. Proof of Theorem 1
Proof.
Outer bound: We derive the bounds on and as follows. If transmitter transmits the message , we have from Fano’s inequality
where (a) follows from the chain rule; (b) follows since the second term of (a) is zero due to the Markov chain (MC) , and the fourth term of (a) is zero due to the MC ; (c) follows since unconditioning does not reduce entropy, and also from the memoryless Gaussian model of the direct channels; and (d) follows since , i.i.d., maximizes the mutual information. Bounding similarly, and since , we have
where , for product distribution , with .
Achievability: We will code over t blocks of symbols together. We choose , and define where , and define and choose , i.i.d., for . Suppose transmits . Thus, to encode over t blocks for the underlying CLIC, we generate i.i.d. sequences , one for each , where are distributed according to . Similarly, for the two direct channels, we generate i.i.d. sequences , distributed as where , for and .
Thus, to transmit , and are transmitted through the CLIC, and and are transmitted through the two direct channels in the second band. Upon receiving the sequences and , employs joint typical decoding to estimate the transmitted message as in [32] (Chapter 4.3). The probability of decoding error vanishes with if
which matches the upper bound on and , as , and . Finally, the capacity region of the CLIC with BMF is defined as the closure of the union of all sets of achievable rate pairs that satisfy (A2) with , where the union is taken over all product distributions, , and for all , such that . ☐
Appendix B. Proof of Theorem 2
Proof.
Outer bound: We derive the bound on first. Assuming that the transmitter transmits the message , we have from Fano’s inequality
where (a) follows since ; (b) follows from the chain rule; (c) follows from the first term in (b) due to the MCs and , and since the second term in (b) is zero due to ; (d) follows since unconditioning does not reduce entropy, and also from the memoryless Gaussian model; and (e) follows from the Gaussian system model, and by choosing i.i.d., which maximizes the mutual information. We similarly bound by, .
Next, we bound the sum-rate. We have from Fano’s inequality
where the first term in (a) follows from the steps (a)–(c) of (A3), and the second term follows similarly; (b) follows from (18) in Lemma 2; (c) follows since unconditioning does not reduce entropy, and also from the memoryless Gaussian model; and (d) follows from choosing i.i.d., which maximizes the mutual information. Hence as , and thus , we obtain the bound in (23). The other bound in (22) is found similarly. Thus, (20)–(23) provides an outer bound on the capacity region of the CLIC.
Achievability: We fix n and , and choose independent input distributions for the codewords of two users in each channel, i.e., , and . The transmitter encodes a message, into two codewords, and , generated according to the i.i.d. distributions, and . The codewords, and , are then transmitted through the IC in the first band and the cross channels in the second band, respectively. Each receiver then estimates both messages, , from the signals observed over both bands as in a multiple access channel. We use standard error analysis technique [32] (Chapter 4.5) to find that the probability of decoding error becomes arbitrarily small as , if the rates achieved in the receiver satisfies
for . Moreover, these achievable rates are maximized by using i.i.d. Gaussian inputs, and . Finally, observe that (18) and (19) in Lemma 2 are valid for the independent Gaussian inputs and with , which implies that the individual rates must satisfy, , where is the channel output with the Gaussian inputs . Hence, the individual rates are limited to , which matches the bound in (20) and (21). In addition, the sum-rate constraints in (A5) above match the sum-rate bounds in (22) and (23). Thus, the outer bound is achieved with independent Gaussian inputs. ☐
Appendix C. Derivation of the Optimal Power Allocation
The KKT Conditions: We show that is convex, and formulate its KKT conditions. Denote by a feasible point, satisfying the constraints in . Now, the objective of is equivalent to minimizing, which is linear, and the equality constraints (30) and (31) are affine. Next, we note that the constraints (27)–(29) are convex. To illustrate, we define corresponding to (27) with , and derive its Hessian, , where is a diagonal matrix with elements . Note that is positive semidefinite, and thus (27) is convex. Likewise, (28) and (29) are found to be convex. In addition, (30) and (31) and imply that the feasible set is compact for given and . Hence, is a convex problem over a compact set. Furthermore, satisfies Slater’s condition [35] (Chapter 5.2.3), since the point is strictly feasible for sufficiently small . Therefore, can be solved using the KKT conditions [35] (Chapter 5.5.3).
We define the Lagrange multipliers corresponding to (27)–(29), corresponding to (30) and (31), and corresponding to the nonnegativity constraints, . The Lagrangian is then
where and , are defined in (24)–(26) with .
With a slight abuse of notation, we denote the optimal primal variable by , and the optimal Lagrange multipliers by . The optimal variables satisfy the KKT conditions below
where we used the fact that since . Next, in order to characterize the power allocation in , where [A2] (implying ) and apply, we partition the set of optimal Lagrange multipliers.
Partitioning the Set of the Optimal Lagrange Multipliers: First, note that and do not satisfy and , as this implies , which violates (A12). Similarly, and do not satisfy and , as this violates (A13). Therefore, we partition the set of into the disjoint subsets, , , and . Similarly, we partition the set into three disjoint subsets, . Therefore, any tuple must be in one of the nine resulting cases, . For conciseness, we denote the tuples and by the vectors and , respectively.
We similarly partition the set of into 5 subsets: , , , , and . Note that when , it satisfies either (a) , or (b) . Specifically, in (a) (A14) and (A16) are tight, and thus , and in (b) only (A14) is tight, and thus . Thus, in , we have . Similarly, we note the following: in , we have ; in , we have ; in , we have , and in , we have .
Now, we characterize “rules” () that determines whether any and jointly satisfy the KKT conditions (i.e., they are compatible) or not (i.e., incompatible).
- : For any , , if then
- : For any , , if then
- : If then , .
- : If then , .
- : If then , .
- : If then , .
- : If then , .
We provide below an outline of how follow. For brevity, we indicate the compatibility (incompatibility) between and by (×) in Table A1, along with the conditions [Cm], () that make them compatible (incompatible). Note that [Cm], are given in (A25)–(A28) in the next two pages.

Table A1.
Compatibility of and .
Table A1.
Compatibility of and .
| Cond. | Cond. | Cond. | Cond. | Cond. | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| × | × | × | × | × | ||||||
| × | × | × | × | × | ||||||
| × | × | × | √ | [C1] | √ | [C3] | ||||
| × | × | × | × | × | ||||||
| × | × | × | √ | [C2] | × | |||||
| × | × | × | × | × | ||||||
| × | × | × | × | × | ||||||
| × | × | × | × | × | ||||||
| × | × | × | √ | [C4] | √ | [C3] |
follows from a specific relation between and as follows. Suppose as in . In , we have , and in we have for . Now, implies from (A9), resulting in from (A8), which contradicts in . Thus, , . follows from a similar relation between and .
Now, consider where satisfy . This results in following (A20)–(A23) and (A12) and (A13). This further implies , which contradicts the implications of . Therefore, , . follows similarly where the roles of and are exchanged with that of and , respectively.
In , satisfy , which results in from (A20)–(A23) and (A12) and (A13). Since and , we have that contradicts the implications of as in above. The assertion in follows similarly by exchanging the roles of and with and , respectively.
In , satisfy , which results in from (A20)–(A23) and (A12) and (A13). This implies , which is consistent with the implication of only.
Power Allocation in : We associate the five compatible subsets in Table A1 (denoted by √) to the four sets in Table A1 according to the resulting power allocations: channel parameters and P are in (a) if , ; (b) if , ; (c) if or , ; and (d) if , . Next, we characterize the conditions, [Cm], in terms of the channel parameters, which give the conditions of sets .
- : Since , they satisfy , which implies from (A12), (A20) and (A21), and from (A22) and (A23). In addition, implies from (A17) and (A18), which, from the expressions of and in (24) and (25) gives . Thus, we have , and therefore, from (A13). Note that and are sufficient for . Moreover, implies , resulting in , i.e., where , defined in (38), is due to assumption [A1]. Next, from and (A10) and (A11), we have . In addition, from and (A8), the condition for is . Since from (A7) we have , which subsequently gives , i.e., as in Table 1. Thus, the condition of is
- : Since , they satisfy , and imply , following (A20)–(A23) and (A12) and (A13). In addition, implies from (A17)–(A19), for which assumption [A1] is sufficient. Next, using and (A8)–(A11) the sufficient conditions for and are found to be and respectively. Since , and thus from (A7), the bounds on and are combined, which gives , i.e., as in Table 1. Finally, is sufficient for . Thus, the condition of is
- : Since , they satisfy , and imply , following (A20)–(A23). In addition, implies and from (A17)–(A19), which gives and respectively, where . Thus, we have and from (A12)–(A13). Note that the condition for is , i.e., , and it is also sufficient for due to .Now, from and (A8)–(A11), and using the expressions of above we find , and . We also note that is sufficient for . Next, to ensure , and must satisfy , which gives the condition as in in Table A1. In addition, note that is sufficient for .Finally, the case with only differ from that with in that now , and thus . We note that is sufficient for . We also note that the other condition, which follows from the conditions on and as in , is expressed by evaluating above at . Therefore, the conditions of the two cases are combined as
- : Since , they satisfy , and imply , following (A20)–(A23. In addition, imply . Next, from , (A8)–(A11), (A12) and (A13), we find , and . Also, since , we have from (24) and (25), . In addition, since we have . Combining these conditions, we get a quadratic equation of , , where , and with and as defined in (37). One of its roots, , is infeasible as it violates (A7) and the nonnegativity of , respectively, when and . Therefore, the valid solution is . Next, from (A9) and substituting in , and with some algebraic simplification, we have where , and and defined in (37). Finally, from the mutual exclusiveness of the sets , the condition of is given by
References
- LTE-A 4G Solution, Stockholm, Sweden. Available online: https://www.ramonmillan.com/documentos/bibliografia/4GEricsson.pdf (accessed on 13 September 2017).
- Pi, Z.; Khan, F. An introduction to millimeter-wave mobile broadband systems. IEEE Commun. Mag. 2011, 49, 101–107. [Google Scholar] [CrossRef]
- Rappaport, T.S.; Sun, S.; Mayzus, R.; Zhao, H.; Azar, Y.; Wang, K.; Wong, G.N.; Schulz, J.K.; Samimi, M.; Gutierrez, F. Millimeter wave mobile communications for 5G cellular: It Will Work! IEEE Access 2013, 1, 335–349. [Google Scholar] [CrossRef]
- Akdeniz, M.R.; Liu, Y.; Samimi, M.K.; Sun, S.; Rangan, S.; Rappaport, T.S.; Erkip, E. Millimeter Wave Channel Modeling and Cellular Capacity Evaluation. IEEE J. Sel. Areas Commun. 2014, 32, 1164–1179. [Google Scholar] [CrossRef]
- Qingling, Z.; Li, J. Rain Attenuation in Millimeter Wave Ranges. In Proceedings of the IEEE 7th International Symposium on Antennas, Propagation and EM Theory, Guilin, China, 26–29 October 2006; pp. 1–4. [Google Scholar]
- Singh, S.; Mudumbai, R.; Madhow, U. Interference analysis for highly directional 60-GHz mesh networks: The case for rethinking medium access control. IEEE/ACM Trans. Netw. 2011, 19, 1513–1527. [Google Scholar] [CrossRef]
- Qiao, J.; Shen, X.S.; Mark, J.W.; Shen, Q.; He, Y.; Lei, L. Enabling device-to-device communications in millimeter-wave 5G cellular networks. IEEE Commun. Mag. 2015, 53, 209–215. [Google Scholar] [CrossRef]
- Collonge, S.; Zaharia, G.; Zein, G.E. Influence of the human activity on wide-band characteristics of the 60 GHz indoor radio channel. IEEE Trans. Wirel. Commun. 2004, 3, 2396–2406. [Google Scholar] [CrossRef]
- Zheng, K.; Zhao, L.; Mei, J.; Dohler, M.; Xiang, W.; Peng, Y. 10 Gb/s Hetsnets with Millimeter-wave communications: Access and networking - challenges and protocols. IEEE Commun. Mag. 2015, 53, 222–231. [Google Scholar] [CrossRef]
- G Radio Access: Requirements, Concept and Technologies. Available online: https://gsacom.com/paper/docomo-5g-radio-access-requirements-concept-and-technologies/ (accessed on 13 September 2017).
- Mehrpouyan, H.; Matthaiou, M.; Wang, R.; Karagiannidis, G.K.; Hua, Y. Hybrid millimeter-wave systems: A novel paradigm for hetnets. IEEE Commun. Mag. 2015, 53, 216–221. [Google Scholar] [CrossRef]
- Majhi, S.; Mitran, P. On the capacity of a class of dual-band interference channels. In Proceedings of the IEEE International Symposium on Information Theory, Barcelona, Spain, 10–15 July 2016; pp. 2759–2763. [Google Scholar]
- Feng, W.; Li, Y.; Jin, D.; Su, L.; Chen, S. Millimetre-wave backhaul for 5G networks: Challenges and solutions. Sensors 2016, 16, 892. [Google Scholar] [CrossRef] [PubMed]
- Morteza, H.; Koksal, C.E.; Shroff, N.B. Dual Sub-6 GHz—Millimeter Wave Beamforming and Communications to Achieve Low Latency and High Energy Efficiency in 5G Systems. Available online: https://arxiv.org/pdf/1701.06241.pdf (accessed on 13 September 2017).
- Niu, Y.; Li, Y.; Jin, D.; Su, L.; Vasilakos, A.V. A survey of millimeter wave communications (mmWave) for 5G: Opportunities and challenges. Wirel. Netw. 2015, 21, 2657–2676. [Google Scholar] [CrossRef]
- Intel Announces World’s First Global 5G Modem. Available online: https://newsroom.intel.com/newsroom/wp-content/uploads/sites/11/2017/01/5G-modem-fact-sheet.pdf (accessed on 13 September 2017).
- Ali, A.; González-Prelcic, N.; Heath, R.W. Estimating millimeter wave channels using out-of-band measurements. In Proceedings of the 2016 Information Theory and Applications Workshop, La Jolla, CA, USA, 31 January–5 February 2016; pp. 1–6. [Google Scholar]
- Ali, A.; Prelcic, N.; Robert, W.; Heath, J. Millimeter Wave Beam-Selection Using Out-of-Band Spatial Information. Available online: https://arxiv.org/pdf/1702.08574.pdf (accessed on 13 September 2017).
- Elshaer, H.; Kulkarni, M.N.; Boccardi, F.; Andrews, J.G.; Dohler, M. Downlink and uplink cell association with traditional macrocells and millimeter wave small cells. IEEE Trans. Wirel. Commun. 2016, 15, 6244–6258. [Google Scholar] [CrossRef]
- Semiari, O.; Saad, W.; Bennis, M. Joint millimeter wave and microwave resources allocation in cellular networks with dual-mode base stations. IEEE Trans. Wirel. Commun. 2017, 16, 4802–4816. [Google Scholar] [CrossRef]
- Rebato, M.; Boccardi, F.; Mezzavilla, M.; Rangan, S.; Zorzi, M. Hybrid spectrum sharing in mmwave cellular networks. IEEE Trans. Cogn. Commun. Netw. 2017, 3, 155–168. [Google Scholar] [CrossRef]
- Sato, H. The capacity of the Gaussian interference channel under strong interference. IEEE Trans. Inf. Theory 1981, 27, 786–788. [Google Scholar] [CrossRef]
- Carleial, A. A case where interference does not reduce capacity. IEEE Trans. Inf. Theory 1975, 21, 569–570. [Google Scholar] [CrossRef]
- Kramer, G. Outer bounds on the capacity of Gaussian interference channels. IEEE Trans. Inf. Theory 2004, 50, 581–586. [Google Scholar] [CrossRef]
- Chung, S.T.; Cioffi, J. The capacity region of frequency-selective Gaussian interference channels under strong interference. IEEE Trans. Commun. 2007, 55, 1812–1821. [Google Scholar] [CrossRef]
- Choi, S.W.; Chung, S.Y. On the separability of parallel Gaussian interference channels. In Proceedings of the IEEE International Symposium on Information Theory, Seoul, South Korea, 28 June–3 July 2009; pp. 2592–2596. [Google Scholar]
- Sankar, L.; Shang, X.; Erkip, E.; Poor, H.V. Ergodic fading interference channels: Sum-capacity and separability. IEEE Trans. Inf. Theory 2011, 57, 2605–2626. [Google Scholar] [CrossRef]
- Cadambe, V.; Jafar, S. Parallel Gaussian interference channels are not always separable. IEEE Trans. Inf. Theory 2009, 55, 3983–3990. [Google Scholar] [CrossRef]
- Shang, X.; Chen, B.; Kramer, G.; Poor, H. Noisy-interference sum-rate capacity of parallel Gaussian interference channels. IEEE Trans. Inf. Theory 2011, 57, 210–226. [Google Scholar] [CrossRef]
- Yu, W.; Ginis, G.; Cioffi, J.M. Distributed multiuser power control for digital subscriber lines. IEEE J. Sel. Areas Commun. 2002, 20, 1105–1115. [Google Scholar] [CrossRef]
- Chen, H.; Ma, Y.; Lin, Z.; Li, Y.; Vucetic, B. Distributed power control in interference channels with QoS constraints and RF energy harvesting: A game-theoretic approach. IEEE Trans. Veh. Technol. 2016, 65, 10063–10069. [Google Scholar] [CrossRef]
- Gamal, A.E.; Kim, Y.H. Network Information Theory; Cambridge University Press: Cambridge, UK, 2012. [Google Scholar]
- Diggavi, S.N.; Cover, T.M. The worst additive noise under a covariance constraint. IEEE Trans. Inf. Theory 2006, 47, 3072–3081. [Google Scholar] [CrossRef]
- Sankar, L.; Liang, Y.; Mandayam, N.B.; Poor, H.V. Fading multiple access relay channels: Achievable rates and opportunistic scheduling. IEEE Trans. Inf. Theory 2011, 57, 1911–1931. [Google Scholar] [CrossRef]
- Boyd, S.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).