An Analysis of Smart Contracts Security Threats Alongside Existing Solutions
Abstract
:1. Introduction
2. Background
2.1. Distributed Ledger Technology
2.2. Smart Contracts
2.3. Solidity
- Status variables: values that are permanently stored in the contract.
- Functions: units of executable code within a contract.
- Function modifiers: used to increase functionality and functions in a simple and declarative way.
- Events: communication interface with EVM logging tools for smart contract code debugging or alerts.
- Structures: these are custom data structures that can group several variables together.
- Enumerations: can be used to create custom data types that represent a finite set of status possibilities.
| Algorithm 1 Smart contract example. |
|
3. Security in Smart Contracts
3.1. Vulnerability Classification
- Calls to the unknown: It happens that some primitives of the Solidity language used to call other functions or send ether may suffer from a side effect of calling a function defined by default that all contracts have (and whose code could be unknown to the caller), in case the called function is not found. The primitives affected by this effect are:
- −
- Call: Is a primitive used to call the functions of a smart contract (of the same or another). If the function passed to the primitive as a parameter does not exist in the contract, a default function or fallback will be executed.
- −
- Send: This primitive allows the user to send ether from the contract in execution to another addressee. Once ether’s quantity has been shipped, the default function is executed in the target contract.
- −
- DelegateCall: This primitive one is very similar to CALL except that in this one, the context of variables of the caller contract is used.
- Gasless sending: Sending ether using the primitive SEND could result in a gas exhaustion exception if the recipient is a contract has a fallback function with a lot of code.
- Exception disorder: In Solidity there are several situations that can cause an exception to be triggered during execution, namely: if the execution of the contract runs out of gas, if the call stack is exhausted, or if the exception is launched explicitly by calling the command throw. However, Solidity does not treat exceptions in the same way if they occur during a function call directly or using the primitive CALL. In the first case, the execution is stopped and any side effects are reversed, including ether transfers. However, if the exception occurred in the context of a call using CALL, the exception will propagate “up” by reversing the effects in the called contracts until the CALL call is reached, returning false and continuing the execution from there and consuming gas. This inconsistency in handling exceptions can lead to vulnerabilities.
- Type conversion: Although the Solidity compiler can detect errors with types, for example if a function waits for an integer and is called by passing it a string, in the case of contract definitions or functions with a certain structure, or in the case of calling a function in a contract, if the programmer makes a mistake and calls another contract by mistake but it contains a function with the same structure expected by the compiler, the function will be executed and if the function does not exist, the function of fallback will be called. In any case, no exception will be launched.
- Re-entrancy: This is a vulnerability well known for its impact. The programmer may think that a non-recursive function cannot be re-called while it is running, but this is not always the case, as it could be the case that within the function, an empty malicious contract is called that only contains a function of fallback that calls back the function it comes from. For example, suppose we have such a contract, as shown in Algorithm 2.The function foo receives, as a parameter, the address of a contract, and if the token is not activated, it sends 1 wei (ether’s minimum unit) to the contract c. After receiving the ether, Alice calls her fallback function, which in turn calls Bob’s foo function again and as the witness is not set to true it will transfer back to Alice ether and this will be repeated until the gas is exhausted or the call stack limit is reached. This vulnerability was used in the Decentralised Autonomous Organization (DAO) attack discussed in Section 3.3.
Algorithm 2 Re-entrancy vulnerability example. - 1:
- contract Bob {
- 2:
- bool sent = false;
- 3:
- function foo(address c) {
- 4:
- if (!sent) {
- 5:
- c.call.value(1)();
- 6:
- sent = true;
- 7:
- }
- 8:
- }
- 9:
- }
- 10:
- contract Alice {
- 11:
- function(){
- 12:
- Bob(msg.sender).foo(this);
- 13:
- }
- 14:
- }
- Secrets: Solidity allows you to define the visibility of fields in contracts as public or private. This can be useful if you need to hide certain information between contract calls. Unfortunately this system is not effective as changes in private fields have to be sent to mining nodes to be put into the blockchain, which is public.
- Unpredictable state: All smart contracts have a state determined by the value of their fields and their ether balance sheet. But you cannot guarantee that the state a contract had when we made a transaction to it will be the same as when that transaction is mined and included in the blockchain. That is to say, it could happen that before processing our transaction, other transactions have changed the status of the destination contract, and besides being fast, does not guarantee us anything because the miners can mine the transactions in the order they want. There is another problem added by the nature of the blockchain, and that is that a chain fork could occur if two miners continue to mine a valid block at the same time. This would cause some miners to try to add their block in one of the two strings and the others in the other. At some point the shorter chain would be discarded, losing the transactions contained in it and changing the state of the contracts to an indeterminate state. Another case would be contracts that use dynamic libraries (a special type of contract that cannot have mutable fields). Such contracts could maliciously change to deceive the victim who would call them without knowing that they have changed.
- Random numbers: The execution of the Ethereum virtual machine code is deterministic. This means that the code executed with the same inputs must produce the same output in all the nodes that execute it. This presents a problem when generating random numbers. To simulate randomness, many contracts use a random number generator initialized with the same seed for all miners. One option widely used by programmers is to use as seed the hash of a given block in the future. Being an unpredictable value a priori, it is a good way to initialize the generator of random numbers. However, since miners can choose which transactions to put in the new blocks, they could conspire to try to alter the operation of the random number generator.
- Time restrictions: Many applications have time restrictions to operate. Usually these restrictions use timestamps. In the case of smart contracts, the programmer can get the timestamp of when the block was mined, which is shared by all transactions in the block. The trouble is that miners in the early versions of the protocol could choose the timestamp of the block they were going to arbitrarily mine, which could be used to carry out attacks.
- Immutable bugs: Although This is not a vulnerability in itself, but the consequence of a blockchain property. All the source code of smart contracts, including those containing bugs, are immutable once they are mined and added to the blockchain, although they can be blocked by calling a destructor function.
- Loss of ether: If the programmer enters an address to send ether and that address exists but it is an orphan address that belongs to no one that ether will be lost forever.
- Stack size: Each time one contract calls another contract the associated call stack increases by one. The stack limit is 1024 and when the limit is reached an exception is launched. Until October 18, 2016 it was possible to take advantage of this to launch an attack where a malicious user increased the battery counter until almost exhausted and then called the victim’s function which launched an exception when the battery limit was exhausted. If the victim did not take this into account and does not handle the exception correctly, the attack could be successful. The impact of this vulnerability caused Ethereum to be redesigned.
3.2. Analysis Methods
- Static analysis: Static software analysis is a way of studying the behaviour of a program from its compiled binary code without executing it, looking for known patterns that often lead to vulnerabilities. There are several procedures when making a static analysis, like:
- −
- Disassembly: The process by which binary code is translated into an human-readable set of instructions.
- −
- Decompilation: The process to inversely generate from code disassembled code in a high-level language.
- −
- Symbolic execution: Symbols are used instead of using specific values for variables. Operations on these symbols lead to algebraic terms, and conditional statements give rise to propositional formulas that characterize branches. A particular part of the code is attainable if the conjunction of formulas on the way to this part is satisfactory, which can be checked by SMT solvers.
- −
- Control flow graph: The representation using a graph of the possible paths that the execution of a program can follow.
- −
- Pattern recognition: This searches for portions of bytecode known to contain potentially vulnerable code.
- −
- Rule-based analysis: A method that transforms the CFG into a representation of rules.
- Dynamic analysis: This type of analysis acts in the execution phase of the program, detecting vulnerabilities that could have gone unnoticed during the static analysis (for example due to the existence of obfuscated code or resistant packaging) at the same time that it serves to verify those found by this one.
- −
- Execution trace: As with the CFG in the static analysis, the trace of contract execution is generated by this during the execution.
- −
- Symbolic analysis: From the different traces at execution time, a symbolic execution of the contract is carried out by inserting different symbolic values in the variables and recording the different outputs produced.
- −
- Validation of false/true positives: After the symbolic analysis and once a contract has been identified as a possible vulnerable candidate, the result of the symbolic analysis is validated with concrete data.
- Formal verification: Through this type of analysis, a verification is carried out using formal mathematical methods to test the specific properties of the code, using theorems provers like SMT Z3 and Coq, among others.
3.3. Most Relevant Attacks on Smart Contracts
3.3.1. The DAO Attack
| Algorithm 3 Vulnerable Decentralised Autonomous Organization (DAO) smart contract example. |
|
| Algorithm 4 Smart contract used to attack DAO example. |
|
- Swap the lines 12 by 13 in DAOexample so that the ether balance of the attacker is first updated and in the next recursive call the condition is false as seen in Algorithm 5.
- Use the methods send() and transfer() to send money to another contract instead of call.value(). The reason is that the methods send() and transfer() have by default limited gas consumption to a very low value that would not allow the successive recursive calls needed to perform this attack.
- Use some kind of mutex object in order to protect the sensible parts.
| Algorithm 5 Non-vulnerable DAO smart contract example. |
|
3.3.2. Parity Multi-Signature Wallet (Double) Attack
| Algorithm 6 Simplified version of vulnerable Parity multi-signature wallet. |
|
4. Tools
4.1. Oyente
- Parity Multi-signature Bug.
- Callstack Depth Attack.
- Timestamp Dependency.
- Re-entracy problem.
4.2. Remix-IDE
- Online editor to write contracts in Solidity.
- Solidity Compiler Switcher and EVM Version selector.
- Solidity Static Analysis.
- Plugin Manager.
4.3. Solgraph
- Red: Send to external address.
- Blue: Constant function.
- Yellow: View.
- Green: Pure.
- Orange: Call.
- Purple: Transfer.
- Lilac: Payable.
4.4. MadMax
- The use of static EVM bytecode decompiler, mainly because of the problem with the stack-based low-level nature and the low control-flow structures (that were discussed before).
- The ability to find gas vulnerabilities.
- An abstraction to understand EVM bytecode by giving a high-level data structure to this level and making an approach between EVM low-level and high-level vulnerabilities.
- The ability to validate a huge number of contracts already deployed on the Ethereum blockchain.
| Algorithm 7 Loop smart contract. |
|
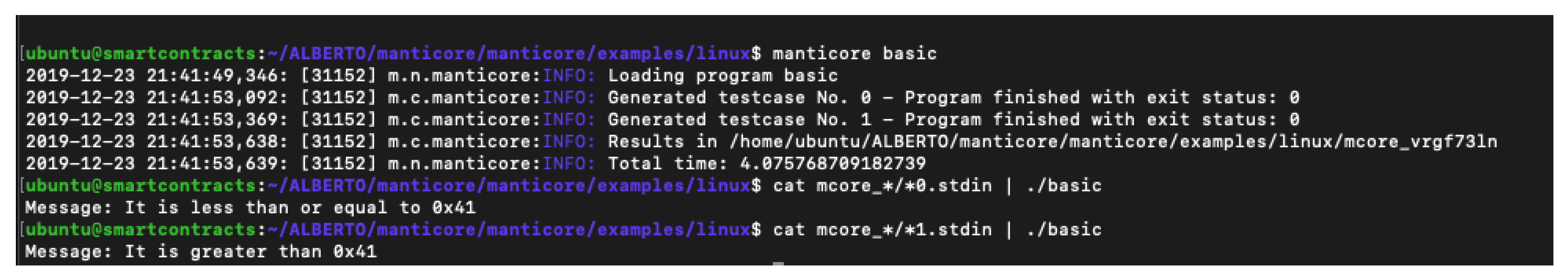
4.5. Manticore
| Algorithm 8 Manticore example C program. |
|
4.6. SmartCheck
4.7. Mythril
- Delegate Call Untrusted Contract.
- Delegate Call To Untrusted Contract.
- Dependence on Predictable Variables.
- Deprecated Opcodes.
- Ether Thief.
- Exceptions.
- External Calls.
- Integer.
- Multiple Sends.
- Suicide.
- State Change External Calls.
- Unchecked return value
- User Supplied assertion.
- Arbitrary Storage Write.
- Arbitrary Jump.
4.8. ContractLarva
- Specification: the properties to capture the events. ContractLarva allows capturing just two types: control flow events (entry and exit function points) and data flow events corresponding to changes in values of variables.
- Input: the input contract.
- Output: results of analysis.
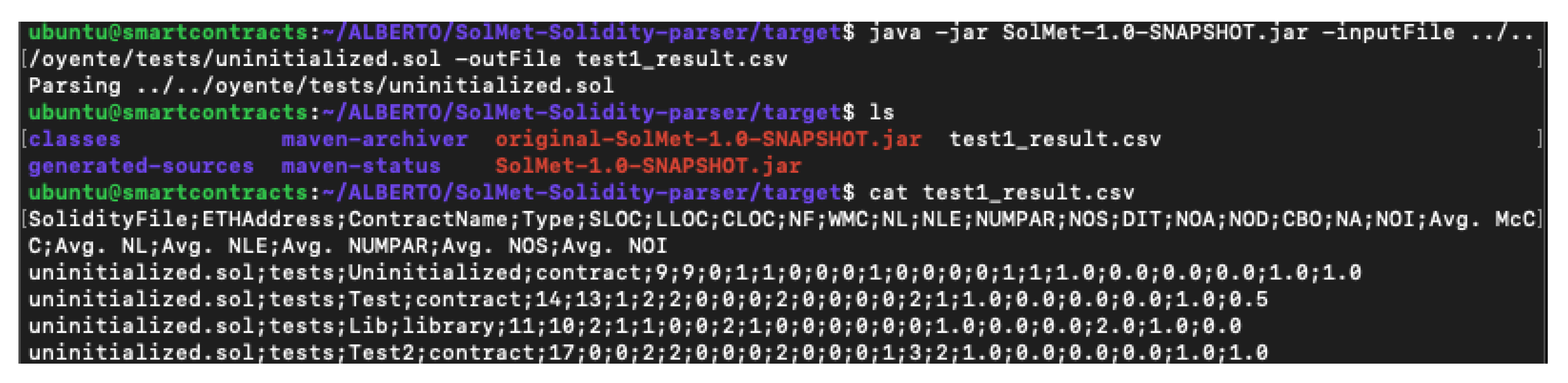
4.9. SolMet
- SLOC—number of source code lines.
- LLOC—number of logical code lines (lines without empty and comment lines).
- CLOC—number of comment lines.
- NF—number of functions.
- McCC—McCabe’s cyclomatic complexity.
- WMC—weighted sum of McCabe’s style complexity over the functions of a contract.
- NL—the deepest nesting level of control structures in functions summed for a contract.
- NLE—nesting level else-if.
- NUMPAR—number of parameters.
- NOS—number of statements.
- DIT—depth of inheritance tree.
- NOA—number of ancestors.
- NOD—number of descendants.
- CBO—coupling between object classes.
- NA—number of attributes (i.e., states).
- NOI—number of outgoing invocations (i.e., fan-out).
4.10. Vandal
- Disassembler (works with Python): Provides extra functionality compare to Ethereum one.
- Decompiler: The creators of the tool says that is the core of Vandal, converting EVM bytecode to an intermediate representation enabling the creation of a control flow diagram (just like the SolGraph program).
- Datalog: Vandal uses the Soufflé Datalog engine, detecting logic and different Solidity operation code to determine whether it is a vulnerability or not.
4.11. EthIR
4.12. MAIAN
- Prodigal: These leak funds to arbitrary users.
- Suicidal: These contracts can be killed by any user.
- Greedy: These contracts lock funds indefinitely.
4.13. Erays
4.14. Rattle
4.15. Osiris
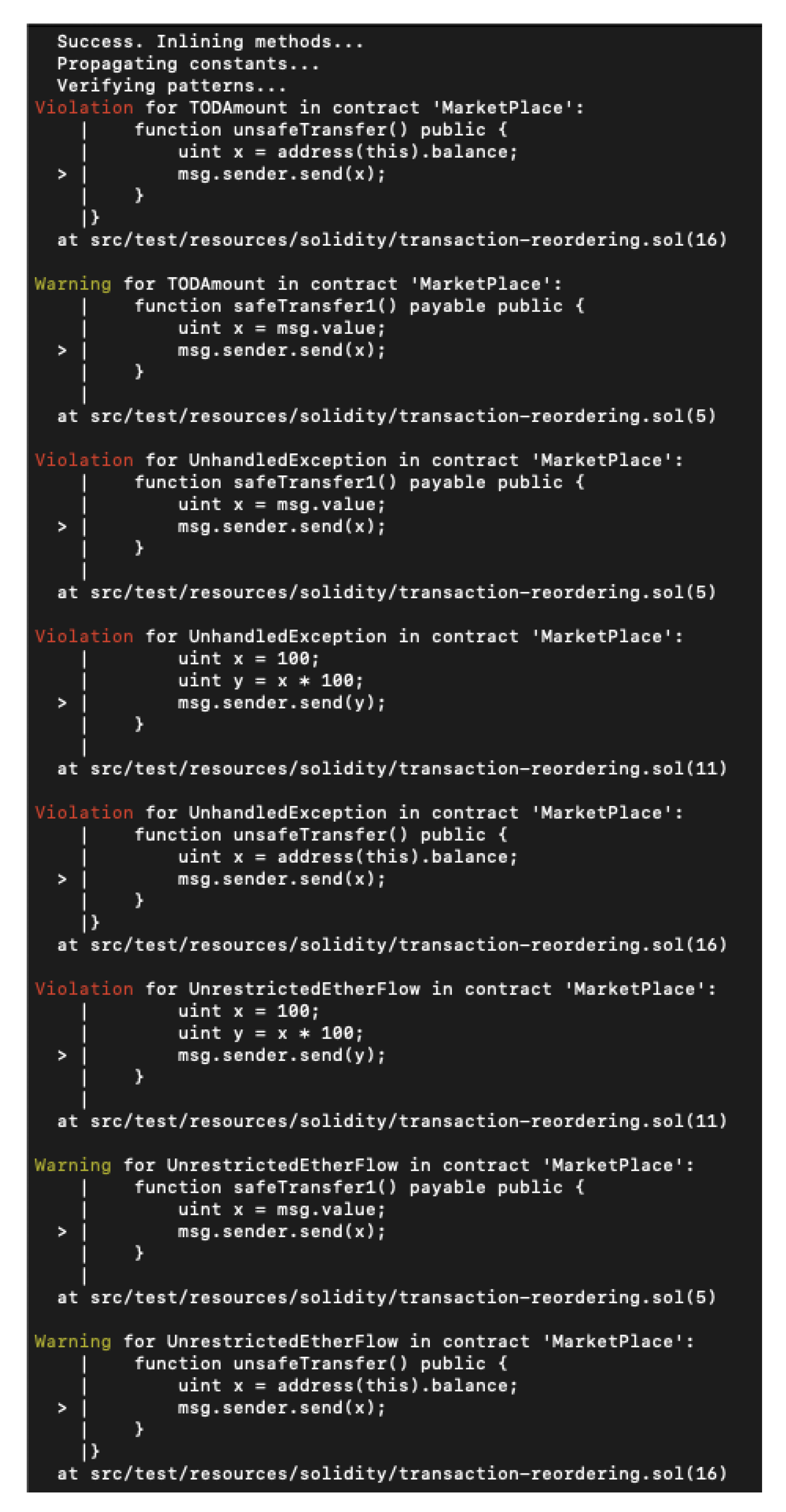
4.16. Securify
- Some forms of the DAO bug (also known as re-entrancy).
- Locked ether.
- Missing input validation.
- Transaction ordering-dependent amount, receiver, and transfer.
- Unhandled exceptions unrestricted ether flow.
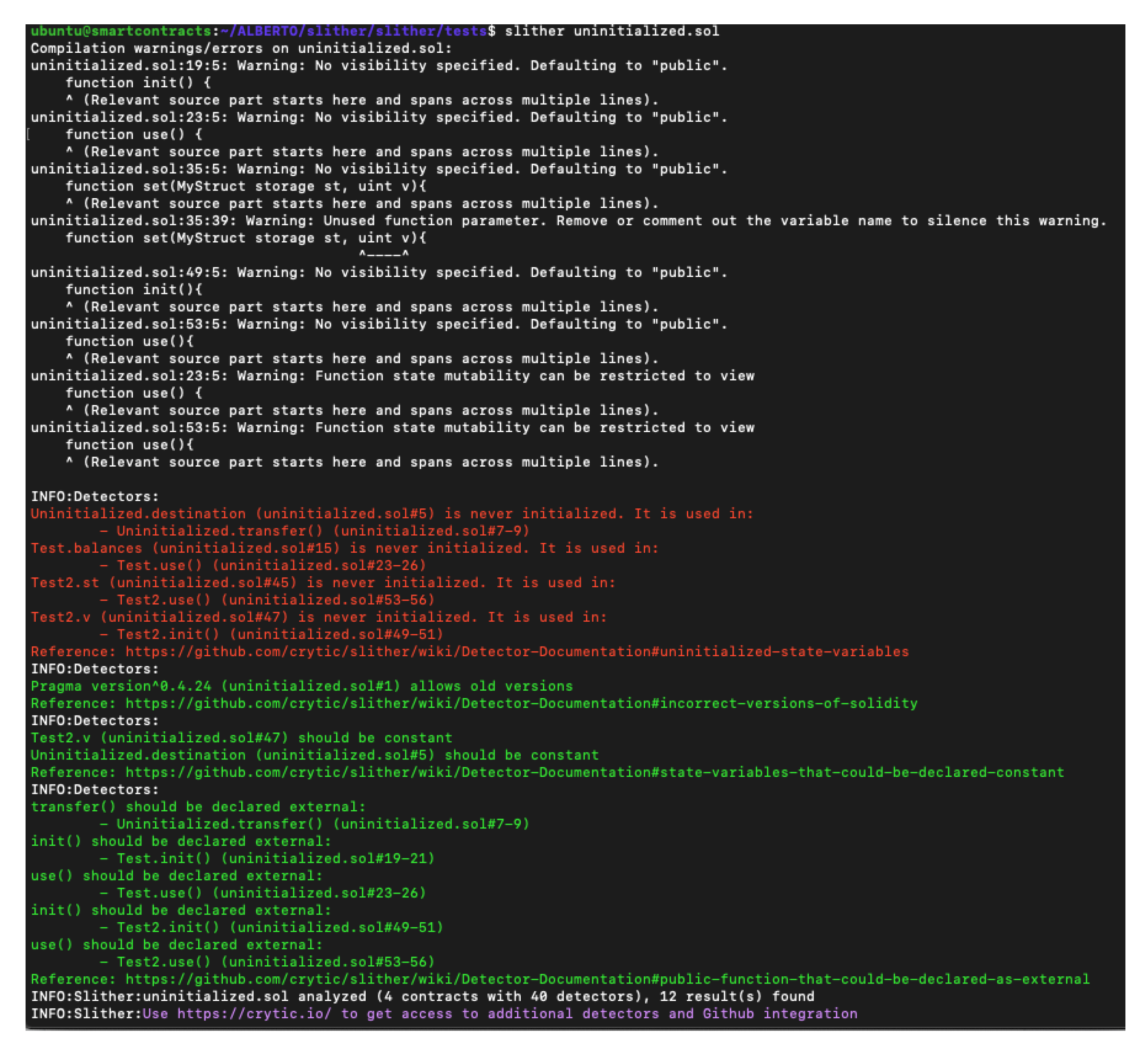
4.17. Slither
- Detection of low false-positives.
- The position of the errors in the code.
- Availability to analyse smart contracts from Solidity version 0.4.
- The partition of 99.9% public Solidity code.
- Average execution time of less than 1 second per contract.
4.18. EtherTrust
4.19. Summary
5. Conclusions
Author Contributions
Funding

Conflicts of Interest
Abbreviations
| DAO | Decentralised Autonomous Organization |
| DLT | Distributed Ledger Technology |
| ETH | Ether (Ethereum cryptocurrency) |
| EVM | Ethereum Virtual Machine |
| P2P | Peer to peer |
| TEE | Trusted Execution Environment |
References
- Szabo, N. Formalizing and securing relationships on public networks. First Monday 1997, 2, 9. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://git.dhimmel.com/bitcoin-whitepaper/ (accessed on 7 February 2020).
- Al-Bassam, M. SCPKI: A smart contract-based PKI and identity system. In Proceedings of the ACM Workshop on Blockchain, Cryptocurrencies and Contracts; ACM: New York, NY, USA, 2017; pp. 35–40. [Google Scholar]
- Dunphy, P.; Petitcolas, F.A. A first look at identity management schemes on the blockchain. IEEE Secur. Privacy 2018, 16, 20–29. [Google Scholar] [CrossRef] [Green Version]
- McCorry, P.; Shahandashti, S.F.; Hao, F. A smart contract for boardroom voting with maximum voter privacy. In International Conference on Financial Cryptography and Data Security; Springer: Berlin, Germany, 2017; pp. 357–375. [Google Scholar]
- Kshetri, N.; Voas, J. Blockchain-enabled e-voting. IEEE Softw. 2018, 35, 95–99. [Google Scholar] [CrossRef] [Green Version]
- Peters, G.W.; Panayi, E. Understanding modern banking ledgers through blockchain technologies: Future of transaction processing and smart contracts on the internet of money. In Banking Beyond Banks and Money; Springer: Berlin, Germany, 2016; pp. 239–278. [Google Scholar]
- Bocek, T.; Rodrigues, B.B.; Strasser, T.; Stiller, B. Blockchains everywhere-a use-case of blockchains in the pharma supply-chain. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; pp. 772–777. [Google Scholar]
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Yuen, H.Y.; Wu, F.; Cai, W.; Chan, H.C.; Yan, Q.; Leung, V. Proof-of-play: A novel consensus model for blockchain-based peer-to-peer gaming system. In Proceedings of the 2019 ACM International Symposium on Blockchain and Secure Critical Infrastructure; ACM: New York, NY, USA, 2019; pp. 19–28. [Google Scholar]
- Bisti, J.; Bertsche, R.; Judka, D.; Siconolfi, P. Game Data Offloading to a Blockchain. U.S. Patent Application No. 15/826,412, 2019. [Google Scholar]
- Rifi, N.; Rachkidi, E.; Agoulmine, N.; Taher, N.C. Towards using blockchain technology for eHealth data access management. In Proceedings of the 2017 Fourth International Conference on Advances in Biomedical Engineering (ICABME), Beirut, Lebanon, 19–21 October 2017; pp. 1–4. [Google Scholar]
- Buterin, V. A next-generation smart contract and decentralized application platform. White Paper 2014, 3, 37. [Google Scholar]
- Cachin, C. Architecture of the Hyperledger Blockchain Fabric. Workshop on Distributed Cryptocurrencies and Consensus Ledgers. 2016, Volume 310, p. 4. Available online: https://pdfs.semanticscholar.org/f852/c5f3fe649f8a17ded391df0796677a59927f.pdf (accessed on 7 February 2020).
- Brown, R.G.; Carlyle, J.; Grigg, I.; Hearn, M. Corda: An introduction. R3 CEV August 2016, 1, 15. [Google Scholar]
- Coinlore. Smart Contract Platforms. 2019. Available online: https://www.coinlore.com/es/smart-contract-platforms (accessed on 7 February 2020).
- El Ioini, N.; Pahl, C. A review of distributed ledger technologies. In OTM Confederated International Conferences On the Move to Meaningful Internet Systems; Springer: Berlin, Germany, 2018; pp. 277–288. [Google Scholar]
- Gervais, A.; Karame, G.O.; Wüst, K.; Glykantzis, V.; Ritzdorf, H.; Capkun, S. On the security and performance of proof of work blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer And Communications Security; ACM: New York, NY, USA, 2016; pp. 3–16. [Google Scholar]
- Bertoni, G.; Daemen, J.; Peeters, M.; Van Assche, G. Keccak. In Annual International Conference on the Theory and Applications Of Cryptographic Techniques; Springer: Berlin, Germany, 2013; pp. 313–314. [Google Scholar]
- Dannen, C. Introducing Ethereum and Solidity; Springer: Berlin, Germany, 2017. [Google Scholar]
- Atzei, N.; Bartoletti, M.; Cimoli, T. A survey of attacks on ethereum smart contracts (sok). In International Conference on Principles of Security and Trust; Springer: Berlin, Germany, 2017; pp. 164–186. [Google Scholar]
- Mehar, M.I.; Shier, C.L.; Giambattista, A.; Gong, E.; Fletcher, G.; Sanayhie, R.; Kim, H.M.; Laskowski, M. Understanding a revolutionary and flawed grand experiment in blockchain: the DAO attack. J. Cases Inf. Technol. (JCIT) 2019, 21, 19–32. [Google Scholar] [CrossRef] [Green Version]
- Palladino, S. The Parity Wallet Hack Explained. July 2017. Available online: https://blog.zeppelin.solutions/on-the-parity-wallet-multisig-hack-405a8c12e8f7 (accessed on 7 February 2020).
- Luu, L.; Chu, D.H.; Olickel, H.; Saxena, P.; Hobor, A. Making smart contracts smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer And Communications Security; ACM: New York, NY, USA, 2016; pp. 254–269. [Google Scholar]
- Melon Project. Oyente. 2016. Available online: https://github.com/melonproject/oyente (accessed on 7 February 2020).
- Go Ethereum. Go-Ethereum. 2013. Available online: https://geth.ethereum.org (accessed on 7 February 2020).
- Ethereum Foundation. Remix-IDE. 2018. Available online: https://github.com/ethereum/remix-ide (accessed on 7 February 2020).
- Revere, R. Solgraph. 2018. Available online: https://github.com/raineorshine/solgraph (accessed on 7 February 2020).
- Grech, N.; Kong, M.; Jurisevic, A.; Brent, L.; Scholz, B.; Smaragdakis, Y. Madmax: Surviving out-of-gas conditions in ethereum smart contracts. Proc. ACM Program. Lang. 2018, 2, 116. [Google Scholar] [CrossRef] [Green Version]
- Mossberg, M.; Manzano, F.; Hennenfent, E.; Groce, A.; Grieco, G.; Feist, J.; Brunson, T.; Dinaburg, A. Manticore: A User-Friendly Symbolic Execution Framework for Binaries and Smart Contracts. arXiv 2019, arXiv:1907.03890. [Google Scholar]
- De Moura, L.; Bjørner, N. Z3: An efficient SMT solver. In International Conference on Tools and Algorithms for The Construction and Analysis of Systems; Springer: Berlin, Germany, 2008; pp. 337–340. [Google Scholar]
- Of Bits, T. Manticore. Available online: https://github.com/trailofbits/manticore (accessed on 7 February 2020).
- Tikhomirov, S.; Voskresenskaya, E.; Ivanitskiy, I.; Takhaviev, R.; Marchenko, E.; Alexandrov, Y. Smartcheck: Static analysis of ethereum smart contracts. In Proceedings of the 2018 IEEE/ACM 1st International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB), New York, NY, USA, 27 May 2018; pp. 9–16. [Google Scholar]
- SmartDec. SmartCheck. 2017. Available online: https://github.com/smartdec/smartcheck (accessed on 7 February 2020).
- Mueller, B. Smashing smart contracts. In Proceedings of the 9th HITB Security Conference, Amsterdam, The Netherlands, 9–13 April 2018. [Google Scholar]
- ConsenSys. Mythril. 2017. Available online: https://github.com/ConsenSys/mythril-classic (accessed on 7 February 2020).
- Albert, E.; Gordillo, P.; Livshits, B.; Rubio, A.; Sergey, I. Ethir: A framework for high-level analysis of ethereum bytecode. In International Symposium on Automated Technology for Verification and Analysis; Springer: Berlin, Germany, 2018; pp. 513–520. [Google Scholar]
- Pace, G. contractLarva. 2017. Available online: https://github.com/gordonpace/contractLarva (accessed on 7 February 2020).
- Hegedus, P. Towards analyzing the complexity landscape of solidity based ethereum smart contracts. Technologies 2019, 7, 6. [Google Scholar] [CrossRef] [Green Version]
- Hegedus, P. SolMet. 2018. Available online: https://github.com/chicxurug/SolMet-Solidity-parser (accessed on 7 February 2020).
- Brent, L.; Jurisevic, A.; Kong, M.; Liu, E.; Gauthier, F.; Gramoli, V.; Holz, R.; Scholz, B. Vandal: A scalable security analysis framework for smart contracts. arXiv 2018, arXiv:1809.03981. [Google Scholar]
- Jordan, H.; Scholz, B.; Subotić, P. Soufflé: On synthesis of program analyzers. In International Conference on Computer Aided Verification; Springer: Berlin, Germany, 2016; pp. 422–430. [Google Scholar]
- Smart Contract Research (USYD). Vandal. 2018. Available online: https://github.com/usyd-blockchain/vandal (accessed on 7 February 2020).
- Gordillo, P. EthIR. 2018. Available online: https://github.com/costa-group/EthIR (accessed on 7 February 2020).
- Nikolić, I.; Kolluri, A.; Sergey, I.; Saxena, P.; Hobor, A. Finding the greedy, prodigal, and suicidal contracts at scale. In Proceedings of the 34th Annual Computer Security Applications Conference; ACM: New York, NY, USA, 2018; pp. 653–663. [Google Scholar]
- MAIAN-Tool. MAIAN. 2018. Available online: https://github.com/MAIAN-tool/MAIAN (accessed on 7 February 2020).
- Erays: reverse engineering ethereum’s opaque smart contracts. In Proceedings of the 27th USENIX Security Symposium, Berkeley, CA, USA, 15–17 August 2018; pp. 1371–1385.
- Teamnsrg. 2018. Available online: https://github.com/teamnsrg/erays (accessed on 7 February 2020).
- Stortz, R. Rattle—An Ethereum EVM Binary Analysis Framework. 2018. Available online: https://github.com/crytic/rattle (accessed on 7 February 2020).
- Trail of Bits. Rattle. 2018. Available online: https://github.com/trailofbits/rattle (accessed on 7 February 2020).
- Torres, C.F.; Schütte, J.; State, R. Osiris: Hunting for integer bugs in ethereum smart contracts. In Proceedings of the 34th Annual Computer Security Applications Conference; ACM: New York, NY, USA, 2018; pp. 664–676. [Google Scholar]
- Ferreira, C. Osiris. 2018. Available online: https://github.com/christoftorres/Osiris (accessed on 7 February 2020).
- Tsankov, P.; Dan, A.; Drachsler-Cohen, D.; Gervais, A.; Buenzli, F.; Vechev, M. Securify: Practical security analysis of smart contracts. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security; ACM: New York, NY, USA, 2018; pp. 67–82. [Google Scholar]
- SRI Lab. Securify. 2018. Available online: https://github.com/eth-sri/securify (accessed on 7 February 2020).
- Feist, J.; Grieco, G.; Groce, A. Slither: A static analysis framework for smart contracts. In Proceedings of the 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB), Montreal, QC, Canada, 27 May 2019; pp. 8–15. [Google Scholar]
- Crytic. Slither. 2018. Available online: https://github.com/crytic/slither (accessed on 7 February 2020).
- Grishchenko, I.; Maffei, M.; Schneidewind, C. EtherTrust: Sound Static Analysis of Ethereum Bytecode. Tech. Univ. Wien Tech. Rep. 2018. Available online: https://www.netidee.at/sites/default/files/2018-07/staticanalysis.pdf (accessed on 7 February 2020).
- SecPriv. EtherTrust. 2019. Available online: https://github.com/SecPriv/EtherTrust (accessed on 7 February 2020).











| Blockchain | Tangle | Hashgraph | |
|---|---|---|---|
| - Transparency | - No mining required | -High number of transactions | |
| Strengths | - Lots of implementation | - No transaction fee | - Scale in number of transactions |
| - In production | - Quantum security | - Fairness | |
| - Small block size | - Single organization | - Gossiping overhead | |
| - Low scalability | management | - Use coins toss to terminate | |
| Weakness | - Low processing speed | consensuns | |
| - Lack of interoperability | - Permissioned network | ||
| - Transaction fees |
| Oyente | Remix-IDE | Solgraph | MadMax | Manticore | SmartCheck | Mythril | ContractLarva | SolMet | Vandal | EthIR | MAIAN | Erays | Rattle | Osiris | Securify | Slither | EtherTrust | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Nivel | Bytecode | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Solidity | ✗ | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | |
| Dynamic analysis | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | |
| Analysis | Static analysis | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ |
| Formal verification | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | ✓ | ✗ | ✓ |
| Tool | Ease of Installation | Usefulness | Stays Up to Date | Dependencies |
|---|---|---|---|---|
| Oyente | 1/5 | 3/5 | No | Python 2 (pip2), Z3 Prover, web3 (pip3), solc, Go-Ethereum |
| Remix-IDE | 5/5 | 5/5 | Yes | nodejs, npm |
| Solgraph | 4/5 | 5/5 | No | nodejs, npm, graphviz |
| MadMax | 4/5 | 5/5 | No | Python 3 |
| Manticore | 5/5 | 5/5 | Yes | Python 3 (+3.6v), pip3, solc |
| SmartCheck | 5/5 | 5/5 | Yes | npm |
| Mythril | 5/5 | 5/5 | Yes | npm, Python 3, pip3 |
| ContractLarva | 3/3 | 3/3 | Yes | Haskell (ghc) |
| SolMet | 5/5 | 5/5 | No | Java, maven, CSV reader |
| Vandal | 4/4 | 4/4 | No | Python 3 |
| EthIR | 1/5 | 3/5 | Yes | Python 2 (pip2), Z3 Prover, web3 (pip3), solc, Go-Ethereum |
| MAIAN | 1/5 | 1/5 | No | solc, Z3, Python 3, web3 |
| Erays | 5/5 | 3/5 | No | graphviz, Python |
| Rattle | 5/5 | 5/5 | No | graphviz, solc, Python 3 |
| Osiris | 2/5 | 5/5 | No | Python 2 (pip2), Z3 Prover, web3 (pip3), solc, Go-Ethereum |
| Securify | 5/5 | 5/5 | No | soufflé, Java 8, solc |
| Slither | 5/5 | 5/5 | Yes | solc, Python 3 |
| EtherTrust | 1/5 | 2/5 | No | Z3 Prover, Python, maven |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
López Vivar, A.; Castedo, A.T.; Sandoval Orozco, A.L.; García Villalba, L.J. An Analysis of Smart Contracts Security Threats Alongside Existing Solutions. Entropy 2020, 22, 203. https://doi.org/10.3390/e22020203
López Vivar A, Castedo AT, Sandoval Orozco AL, García Villalba LJ. An Analysis of Smart Contracts Security Threats Alongside Existing Solutions. Entropy. 2020; 22(2):203. https://doi.org/10.3390/e22020203
Chicago/Turabian StyleLópez Vivar, Antonio, Alberto Turégano Castedo, Ana Lucila Sandoval Orozco, and Luis Javier García Villalba. 2020. "An Analysis of Smart Contracts Security Threats Alongside Existing Solutions" Entropy 22, no. 2: 203. https://doi.org/10.3390/e22020203
APA StyleLópez Vivar, A., Castedo, A. T., Sandoval Orozco, A. L., & García Villalba, L. J. (2020). An Analysis of Smart Contracts Security Threats Alongside Existing Solutions. Entropy, 22(2), 203. https://doi.org/10.3390/e22020203






