- Feature Paper
- Article
On Best Erasure Wiretap Codes: Equivocation Matrices and Design Principles
- Willie K. Harrison,
- Truman Welling and
- Andrew Swain
- + 1 author
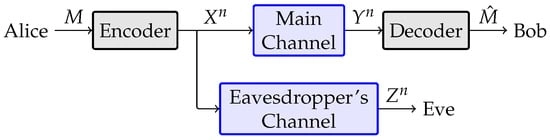
Physical-layer security can aid in establishing secure telecommunication networks including cellular, Internet of Things, and telemetry networks, among others. Channel sounding techniques and/or telemetry systems for reporting channel conditions, coupled with superior wiretap code design are necessary to implement such secure systems. In this paper, we present recent results in best wiretap coset code design for the binary erasure wiretap channel. We define equivocation matrices, and showcase their properties and utility in constructing good, and even the best, wiretap codes. We outline the notion of equivalence for wiretap coset codes, and use it to reduce the search space in exhaustive searches for best small codes. Through example, we show that the best codes do not exist for some code sizes. We also prove that simplex codes are better than codes repeating one column multiple times in their generator matrix.
9 December 2025