Visual Secure Image Encryption Scheme Based on Compressed Sensing and Regional Energy
Abstract
:1. Introduction
2. Fundamental Knowledge and Related Technologies
2.1. Compressed Sensing
2.2. Multi-Character Chaotic System
2.3. Zigzag
3. Hour Hand Printing Scrambling and Embedding Strategy Based on Regional Energy
3.1. Hhp Scrambling
- For odd circles, start from the top left position and arrange in a clockwise direction;
- For even circles, start from the bottom right position and arrange in anti-clockwise direction;
- Alternating odd and even circles until the two-dimensional matrix is filled, then the HHP is completed.
3.2. Embedding Strategy Based on Regional Energy
4. Encryption and Decryption Scheme for Visually Secure Images
4.1. Generation of Vital Values and Construction of Measurement Matrix
4.1.1. Obtaining Initial Values of Multi-Character Chaotic Systems
4.1.2. Construction and Optimization of Measurement Matrix
4.2. Visual Security Image Encryption Algorithm
4.2.1. Compressing and Encrypting Plain Image into a Secret Image
4.2.2. Embedding the Secret Image into Carrier Image
| Algorithm 1 The embedding process. |
Input: The secret image , four matrices , , and of the carrier image, embedding intensity factors a. Output: a set of mappings recording the embedding positions, four modified matrices , , and . (1): The secret image is divided into non-overlapping blocks, each block is represented by , and T is the sum of the blocks. DWT is performed on to obtain four matrices for each image block as , , and , . (2): DWT is performed again for all matrices and in (1), respectively. obtaining the matrices , , , and , , , , . (3): According to Equations 16 and 17, calculate the energy of each secret image block to generate the average sum of , , and matrices and denoted as , .
(4): The four matrices , , and are divided into non-overlapping blocks, all blocks are denoted by , and V is the sum of matrix blocks. The matrix block with belongs to , belongs to , belongs to and belongs to . (5): According to Equation (18), calculate the energy of each matrix block in (4), denoted by .
(6): After sorting the values in and in descending order, two sets of image block position indexes and (V) can be obtained. The first T indexes in are chosen to form a set of mappings with , denoted as . According to and Equation (19), the secret image block is embedded into of the carrier image.
(7): The modified matrix blocks are merged in at intervals and the merged matrices are , , , . |
4.3. Decryption Algorithm
4.3.1. Extract Secret Images from Visually Secure Cipher Images
4.3.2. Recover the Plain Image from the Secret Image
5. Simulation Results
6. Performance Analyses
6.1. Key Space Analysis
6.2. Key Sensitivity Analysis
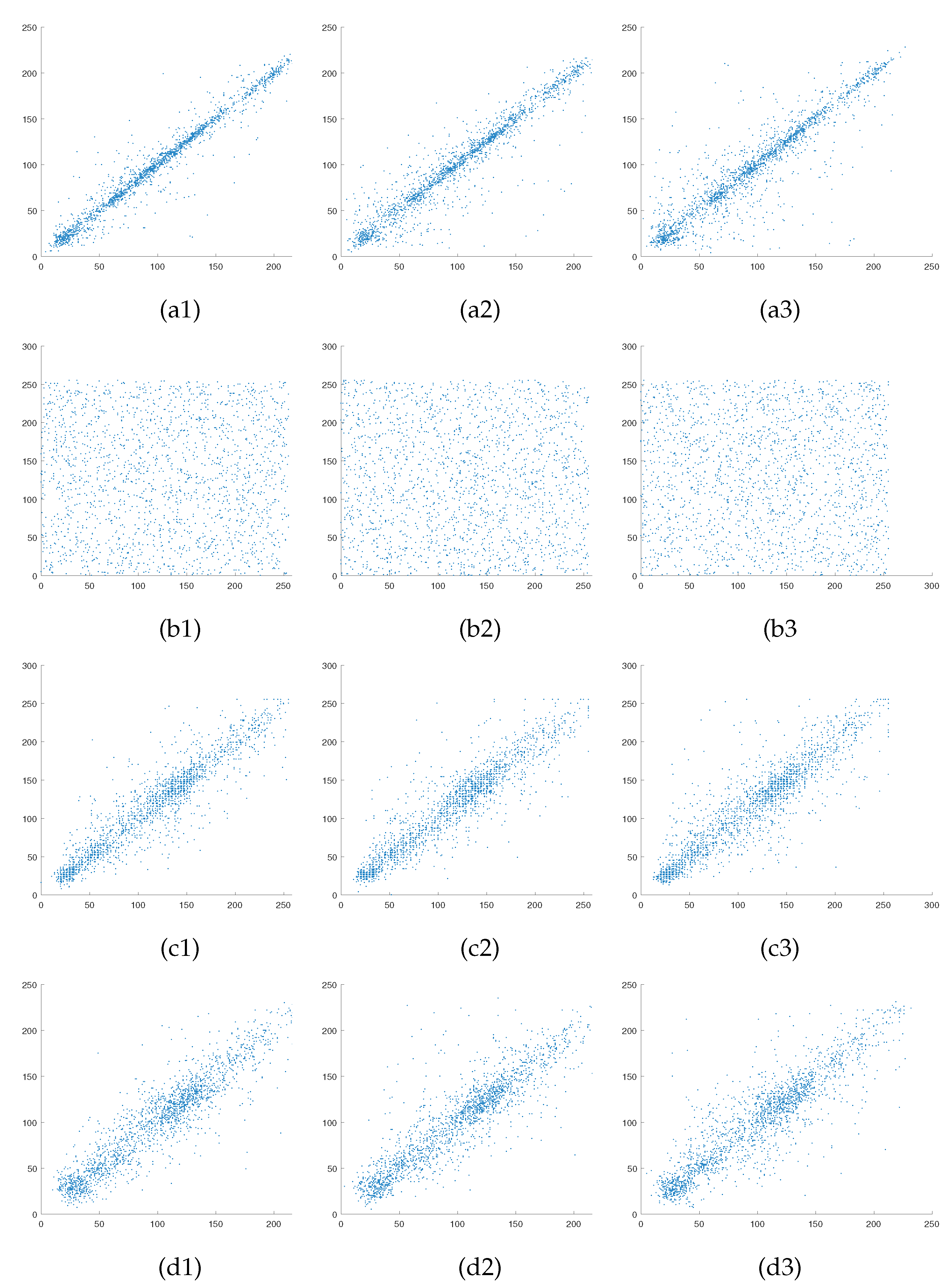
6.3. Correlation Analysis
6.4. Histogram Analysis
6.5. Information Entropy
6.6. Known Plaintext Attack and Chosen Plaintext Attack
6.7. Robustness
6.7.1. Noise Attack
6.7.2. Data Cropping Attacks Analysis
6.8. Compression Capability Analysis
6.9. Complexity
6.10. Time Efficiency Analysis
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Liu, W.H.; Sun, K.; Zhu, C. A fast image encryption algorithm based on chaotic map. Opt. Lasers Eng. 2016, 84, 26–36. [Google Scholar] [CrossRef]
- Çavuşoğlu, Ü.; Kaçar, S.; Pehlivan, I.; Zengin, A. Secure image encryption algorithm design using a novel chaos based S-Box. Chaos, Solitons Fractals 2017, 95, 92–101. [Google Scholar] [CrossRef]
- Hua, Z.; Jin, F.; Xu, B.; Huang, H. 2D Logistic-Sine-coupling map for image encryption. Signal Process. 2018, 149, 148–161. [Google Scholar] [CrossRef]
- Wang, X.Y.; Cao, S. Application of matrix semi-tensor product in chaotic image encryption. J. Frankl. Inst. 2019, 356, 11638–11667. [Google Scholar] [CrossRef]
- Huang, L.; Cai, S.; Xiong, X.; Xiao, M. On symmetric color image encryption system with permutation-diffusion simultaneous operation. Opt. Lasers Eng. 2019, 115, 7–20. [Google Scholar] [CrossRef]
- Zhang, Q.; Liu, L.; Wei, X.P. Improved algorithm for image encryption based on DNA encoding and multi-chaotic maps. AEU Int. J. Electron. Commun. 2014, 68, 186–192. [Google Scholar] [CrossRef]
- Enayatifar, R.; Abdullah, A.H.; Isnin, I.F. Chaos-based image encryption using a hybrid genetic algorithm and a DNA sequence. Opt. Lasers Eng. 2014, 56, 83–93. [Google Scholar] [CrossRef]
- Rahman, N.H.U.; Balamurugan, C.; Mariappan, R. A Novel DNA Computing Based Encryption and Decryption Algorithm. Procedia Comput. Sci. 2015, 46, 463–475. [Google Scholar]
- Sanpei, T.; Shimobaba, T.; Kakue, T.; Endo, Y.; Hirayama, R.; Hiyama, D.; Hasegawa, S.; Nagahama, Y.; Sano, M.; Oikawa, M. Optical encryption for large-sized images. Opt. Commun. 2016, 361, 138–142. [Google Scholar] [CrossRef]
- Mehra, I.; Nishchal, N.K. Optical asymmetric image encryption using gyrator wavelet transform. Opt. Commun. 2015, 354, 344–352. [Google Scholar] [CrossRef]
- Lu, D.J.; He, W.Q.; Peng, X. Enhancement of optical image encryption based on radial shearing interference. Opt. Commun. 2015, 336, 77–83. [Google Scholar] [CrossRef]
- Chen, T.; Zhang, M.; Wu, J.; Yuen, C.; Tong, Y. Image encryption and compression based on kronecker compressed sensing and elementary cellular automata scrambling. Opt. Laser Technol. 2016, 84, 118–133. [Google Scholar] [CrossRef]
- Niyat, A.Y.N.; Moattar, M.H.; Torshiz, M.N. Color image encryption based on hybrid hyper-chaotic system and cellular automata. Opt. Lasers Eng. 2017, 90, 225–237. [Google Scholar] [CrossRef]
- Kumar, M.; Iqbal, A.; Kumar, P. A new RGB image encryption algorithm based on DNA encoding and elliptic curve Diffie–Hellman cryptography. Signal Process. 2016, 125, 187–202. [Google Scholar] [CrossRef]
- Shankar, K.; Eswaran, P. RGB based multiple share creation in visual cryptography with aid of elliptic curve cryptography. China Commun. 2017, 14, 118–130. [Google Scholar] [CrossRef]
- Ratnavelu, K.; Kalpana, M.; Balasubramaniam, P.; Wong, K.; Raveendran, P. Image encryption method based on chaotic fuzzy cellular neural networks. Signal Process. 2017, 140, 87–96. [Google Scholar] [CrossRef]
- Rachlin, Y.; Baron, D. The secrecy of compressed sensing measurements. In Proceedings of the 2008 46th Annual Allerton Conference on Communication, Control and Computing, Monticello, IL, USA, 23–26 September 2008. [Google Scholar]
- Chen, J.X.; Zhang, Y.; Qi, Z. Exploiting chaos-based compressed sensing and cryptographic algorithm for image encryption and compression. Opt. Laser Technol. 2018, 99, 238–248. [Google Scholar] [CrossRef]
- Zhou, N.R.; Li, H.L.; Wang, D.; Pan, S.M.; Zhou, Z.H. Image compression and encryption scheme based on 2D compressive sensing and fractional Mellin transform. Opt. Commun. 2015, 343, 10–21. [Google Scholar] [CrossRef]
- Chai, X.L.; Zheng, X.Y.; Gan, Z.H.; Han, D.J.; Chen, Y.R. An image encryption algorithm based on chaotic system and compressive sensing. Signal Process. 2018, 148, 124–144. [Google Scholar] [CrossRef]
- Hua, Z.Y.; Zhou, Y.C.; Pun, C.M.; Chen, C.P. 2D Sine Logistic modulation map for image encryption. Inf. Sci. 2015, 297, 80–94. [Google Scholar] [CrossRef]
- Bao, L.; Zhou, Y.C. Image encryption: Generating visually meaningful encrypted images. Inf. Sci. 2015, 324, 197–207. [Google Scholar] [CrossRef]
- Yang, Y.G.; Zhang, Y.C.; Chen, X.B.; Zhou, Y.H.; Shi, W.M. Eliminating the texture features in visually meaningful cipher images. Inf. Sci. 2018, 429, 102–119. [Google Scholar] [CrossRef]
- Gong, L.H.; Qiu, K.D.; Deng, C.Z.; Zhou, N.R. An image compression and encryption algorithm based on chaotic system and compressive sensing. Opt. Laser Technol. 2019, 115, 257–267. [Google Scholar] [CrossRef]
- Zhu, L.Y.; Song, H.S.; Zhang, X.; Yan, M.D.; Zhang, T.; Wang, X.Y.; Xu, J. A robust meaningful image encryption scheme based on block compressive sensing and SVD embedding. Signal Process. 2020, 175, 107629. [Google Scholar] [CrossRef]
- Chai, X.L.; Wu, H.Y.; Gan, Z.H.; Zhang, Y.S.; Chen, Y.R.; Nixion, K.W. An efficient visually meaningful image compression and encryption scheme based on compressive sensing and dynamic LSB embedding. Opt. Lasers Eng. 2020, 124, 105837. [Google Scholar] [CrossRef]
- Chai, X.L.; Gan, Z.H.; Chen, Y.R.; Zhang, Y.S. A visually secure image encryption scheme based on compressive sensing. Signal Process. 2017, 134, 35–51. [Google Scholar] [CrossRef] [Green Version]
- Donoho, D.L. Compressed sensing. IEEE Trans. Inf. Theory 2006, 52, 1289–1306. [Google Scholar] [CrossRef]
- Candès, E.J.; Wakin, M.B. An Introduction To Compressive Sampling. IEEE Signal Process. Mag. 2008, 25, 21–30. [Google Scholar] [CrossRef]
- Tillmann, A.M.; Pfetsch, M.E. The Computational Complexity of the Restricted Isometry Property, the Nullspace Property, and Related Concepts in Compressed Sensing. IEEE Trans. Inf. Theory 2014, 60, 1248–1259. [Google Scholar]
- Wang, Z.H.; Wang, H.; Sun, G.; Xu, Y. Research on Measurement Matrix Based on Compressed Sensing Theory. In Communications, Signal Processing, and Systems; Liang, Q., Wang, W., Liu, X., Na, Z., Jia, M., Zhang, B., Eds.; Springer: Singapore, 2020; p. 571. [Google Scholar]
- Marques, E.C.; Maciel, N.; Naviner, L.; Cai, H.; Yang, J. A Review of Sparse Recovery Algorithms. IEEE Access 2019, 7, 1300–1322. [Google Scholar] [CrossRef]
- He, G.; Wu, W.; Nie, L.; Wen, J.; Yang, C.; Yu, W.X. An Improved Image Multi-Dimensional Chaos Encryption Algorithm Based on CUDA. In Proceedings of the 2019 9th International Conference on Information Science and Technology (ICIST), Hulunbuir, China, 2–5 August 2019. [Google Scholar]
- Nazarimehr, F.; Rajagopal, K.; Kengne, J.; Jafari, S.; Pham, V.T. A new four-dimensional system containing chaotic or hyper-chaotic attractors with no equilibrium, a line of equilibria and unstable equilibria. Chaos Solitons Fractals 2018, 111, 108–118. [Google Scholar] [CrossRef]
- Farrag, S.; Alexan, W.; Hussein, H.H. Triple-Layer Image Security Using a Zigzag Embedding Pattern. In Proceedings of the 2019 International Conference on Advanced Communication Technologies and Networking (CommNet), Rabat, Morocco, 12–14 April 2019. [Google Scholar]
- Sara, U.; Akter, M.; Uddin, M.S. Image Quality Assessment through FSIM, SSIM, MSE and PSNR—A Comparative Study. J. Comput. Commun. 2019, 7, 8–18. [Google Scholar] [CrossRef] [Green Version]
- Ye, G.D.; Pan, C.; Dong, Y.X.; Shi, Y.; Huang, X.L. Image encryption and hiding algorithm based on compressive sensing and random numbers insertion. Signal Process. 2020, 172, 107563. [Google Scholar] [CrossRef]
- Anwar, S.; Meghana, S. A pixel permutation based image encryption technique using chaotic map. Multimed Tools Appl. 2019, 78, 27569–27590. [Google Scholar] [CrossRef]
- Chen, X.; Hu, C.J. Adaptive medical image encryption algorithm based on multiple chaotic mapping. Acta Electron. Sin. 2017, 24, 1821–1827. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Y.Q.; He, Y.; Li, P.; Wang, X.Y. A new color image encryption scheme based on 2DNLCML system and genetic operations. Engineering 2020, 128, 106040. [Google Scholar] [CrossRef]
- Murillo-Escobar, M.A.; Meranza-Castillon, M.O.; Lopez-Gutierrez, R.M.; Cruz-Hernandez, C. Suggested Integral Analysis for Chaos-Based Image Cryptosystems. Entropy 2019, 21, 815. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Ali, T.S.; Ali, R. A new chaos based color image encryption algorithm using permutation substitution and Boolean operation. Multimed. Tools Appl. 2019, 79, 19853–19873. [Google Scholar] [CrossRef]
- Shen, Q.; Liu, W.; Lin, Y.; Zhu, Y.J. Designing an Image Encryption Scheme Based on Compressive Sensing and Non-Uniform Quantization for Wireless Visual Sensor Networks. Sensors 2019, 19, 3081. [Google Scholar] [CrossRef] [Green Version]
- Wen, W.Y.; Hong, Y.K.; Fang, Y.M.; Li, M. A visually secure image encryption scheme based on semi-tensor product compressed sensing. Signal Process. 2020, 173, 107580. [Google Scholar] [CrossRef]
- Wei, D.Y.; Jiang, M.J. A fast image encryption algorithm based on parallel compressive sensing and DNA sequence. Optik 2021, 238, 166748. [Google Scholar] [CrossRef]
- Yu, J.Y.; Li, C.; Song, X.M.; Guo, S.Y.; Wang, E.F. Parallel Mixed Image Encryption and Extraction Algorithm Based on Compressed Sensing. Entropy 2021, 23, 278. [Google Scholar] [CrossRef] [PubMed]
- Wang, X.Y.; Su, Y.N. Image encryption based on compressed sensing and DNA encoding. Signal Process. Image Commun. 2021, 95, 116246. [Google Scholar] [CrossRef]
- Pan, C.; Ye, G.D.; Huang, X.L.; Zhou, J.W. Novel Meaningful Image Encryption Based on Block Compressive Sensing. Secur. Commun. Netw. 2019, 2019, 6572105. [Google Scholar] [CrossRef] [Green Version]











| Plain Image | Carrier Images | PSNR (dB) | SSIM | ||
|---|---|---|---|---|---|
| Cipher Image | Decrypted Image | Cipher Image | Decrypted Image | ||
| Lena | Airfield | 45.9768 | 36.2680 | 0.9756 | 0.9938 |
| Pepper | Goldhill | 46.8526 | 36.5198 | 0.9748 | 0.9945 |
| House | Dollar | 51.9394 | 39.9148 | 0.9740 | 0.9969 |
| Boat | Sailboat | 44.6585 | 37.3770 | 0.9768 | 0.9951 |
| Item | Keys | ||||
|---|---|---|---|---|---|
| NPCR | 99.6872% | 99.7116% | 99.7101% | 99.6918% | 99.7131% |
| Image | Horizontal | Vertical | Diagonal |
|---|---|---|---|
| plain image (Lena) | 0.9736 | 0.9417 | 0.9178 |
| Secret image | 0.0229 | −0.0039 | −0.0106 |
| Carrier image (Airfield) | 0.9442 | 0.9176 | 0.8943 |
| Cipher image | 0.9356 | 0.9060 | 0.8762 |
| Item | Plain Image | Secret Image | ||||||
|---|---|---|---|---|---|---|---|---|
| Lena | Pepper | House | Boat | Lena | Pepper | House | Boat | |
| D | 30,666 | 36,653 | 299,789 | 102,311 | 127 | 136 | 128 | 128 |
| 175 | 191 | 548 | 320 | 11 | 12 | 11 | 11 | |
| Item | Plain Image Lena | Lena’s Secret Image | ||
|---|---|---|---|---|
| Ref. [41] | Ours | Ref. [41] | Ours | |
| D | 38,451 | 30,666 | 414 | 127 |
| 196 | 175 | 20 | 11 | |
| Plain Image | Carrier Images | Entropy | ||||
|---|---|---|---|---|---|---|
| Plain Image | Secret Image | Carrier Image | Cipher Image | Decrypted Image | ||
| Lena | Airfield | 7.5683 | 7.9873 | 7.1206 | 7.5631 | 7.5934 |
| Pepper | Goldhill | 7.5352 | 7.9863 | 7.4778 | 7.3116 | 7.5748 |
| House | Dollar | 6.4971 | 7.9860 | 6.9785 | 6.9621 | 6.5918 |
| Boat | Sailboat | 7.1456 | 7.9871 | 7.4758 | 7.3538 | 7.1870 |
| GN | Noise Intensity | ||||
|---|---|---|---|---|---|
| 0.000001% | 0.000003% | 0.000005% | 0.000007% | 0.000009% | |
| PSNR (dB) | 34.3698 | 30.5790 | 29.9235 | 29.5931 | 29.4689 |
| SPN | Noise Intensity | ||||
|---|---|---|---|---|---|
| 0.001% | 0.003% | 0.005% | 0.007% | 0.009% | |
| PSNR (dB) | 35.7661 | 35.0246 | 34.9296 | 34.5806 | 33.5185 |
| CR | Plain Image | PSNR (dB) | |||||
|---|---|---|---|---|---|---|---|
| Ref. [48] | Ref. [44] | Ref. [47] | Ref. [45] | Ref. [46] | Ours | ||
| 0.25 | Lena | - | - | 24.39 | 32.290 | ||
| House | - | - | 35.0177 | ||||
| 0.5 | Lena | 30.0233 | 23.3608 | 30.71 | 27.7247 | 36.268 | |
| House | 34.5722 | - | - | - | 39.9148 | ||
| Pepper | 29.8787 | - | 27.3366 | 36.5198 | |||
| Item | Time (s) |
|---|---|
| Compressing | 0.266066 |
| Embedding | 0.059261 |
| Total Encryption | 0.325327 |
| Extracting | 0.048770 |
| Reconstruction | 3.119658 |
| Total Decryption | 3.168428 |
| Total | 3.493755 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shi, M.; Guo, S.; Song, X.; Zhou, Y.; Wang, E. Visual Secure Image Encryption Scheme Based on Compressed Sensing and Regional Energy. Entropy 2021, 23, 570. https://doi.org/10.3390/e23050570
Shi M, Guo S, Song X, Zhou Y, Wang E. Visual Secure Image Encryption Scheme Based on Compressed Sensing and Regional Energy. Entropy. 2021; 23(5):570. https://doi.org/10.3390/e23050570
Chicago/Turabian StyleShi, Mengna, Shiyu Guo, Xiaomeng Song, Yanqi Zhou, and Erfu Wang. 2021. "Visual Secure Image Encryption Scheme Based on Compressed Sensing and Regional Energy" Entropy 23, no. 5: 570. https://doi.org/10.3390/e23050570






