In this section, we propose a quantum primal method for solving LWE, where the Unique-SVP problem is solved by VQE. Although the quantum advantage of solving classical optimization by VQE is not as obvious as it is in quantum chemistry, understanding the evolution of the algorithm process is still crucial for improving algorithms running on classical hardware. We detail the number of qubits required and estimate the quantum resources when attacking the KYBER cryptosystem. With the development of quantum computers, resource estimation can also be used as a direction for comparison with pure classical algorithms.
4.1. LWE Algorithm
Algotithm 5 shows the procedure of the LWE algorithm.
| Algorithm 5 The LWE algorithm. |
- Input:
LWE samples - Output:
secret vector - 1:
Construct a q-ary lattice , whose lattice basis is equivalent to . - 2:
Perform elementary row transformations on and obtain the lattice basis . - 3:
Using Kannan’s embedding technique, reduce BDD to Unique-SVP and obtain . - 4:
Process with VQE and derive a short vector . - 5:
return
|
Step 3 expands the q-ary basis by one dimension and embeds the target vector
and the embedding factor
M into matrix
. When
, there exists
[
26]. In this case, proposing the first
m bits of the vector recovers
. In the experiment, we generally take
.
Unique-SVP can be seen as a special case of SVP, and step 4 in Algorithm 5 solves SVP by VQE. The detailed description is shown in Algorithm 6.
| Algorithm 6 VQE solving SVP. |
- Input:
the lattice basis . - Output:
short vector . - 1:
Perform BKZ-reduction on . - 2:
The SVP problem is encoded to the ground state of the Hamiltonian operator H. - 3:
Construct parameterized quantum circuits. - 4:
Repeat preparing an ansatz state from the parameterized quantum circuit and measuring it in Pauli-Z basis. Calculate the expectation value . - 5:
Pass and parameters to a classical optimizer. Update the parameter and go to step 4 until the expectation value converges.
|
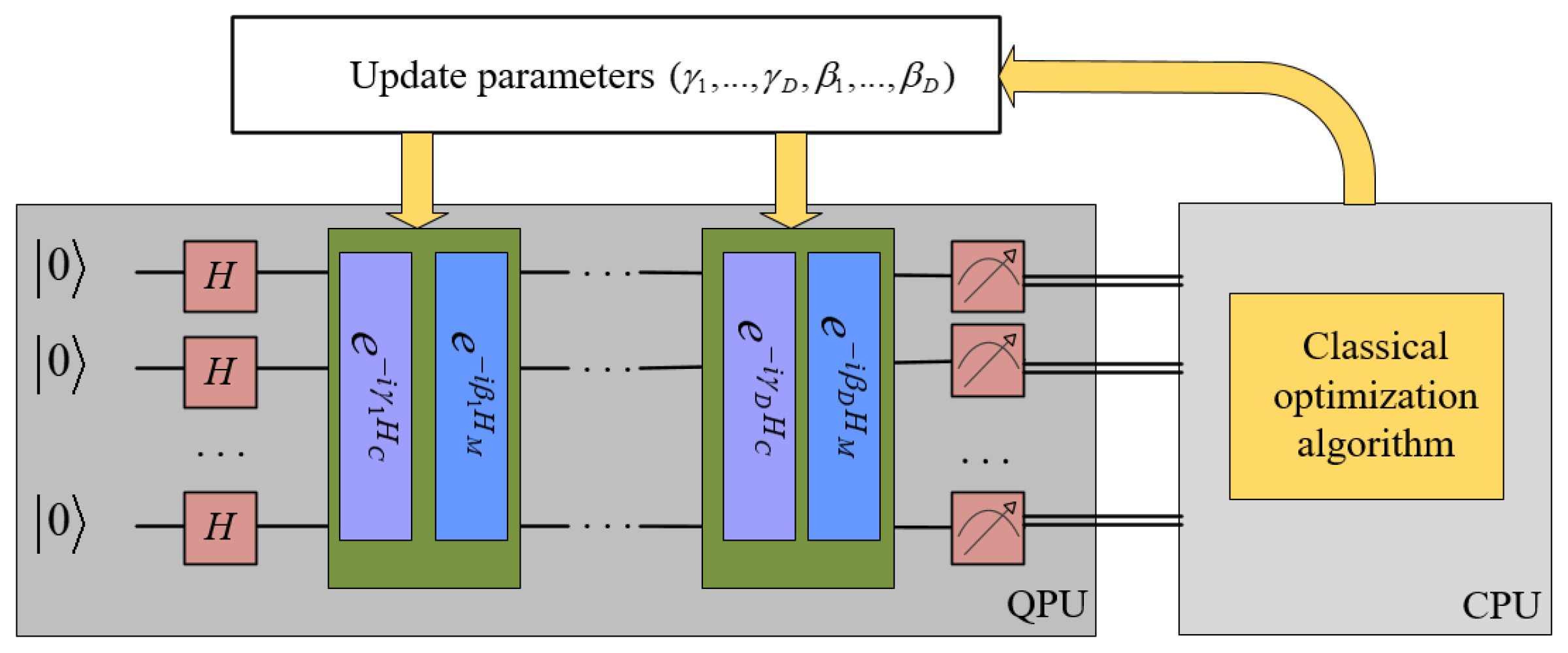
The VQE procedure is visualized in
Figure 2. Now, we explain the steps in Algorithm 6 in detail. In step 1, the larger the lattice size, the more quantum resources it occupies. In order to reduce the required qubits, a new basis matrix is first obtained by performing the BKZ reduction.
Step 2 constructs the problem Hamiltonian. For Lattice
, SVP is to find a nonzero vector
satisfying
. Let the row vector of coefficients be
and
; then, we have
. Let
; then, we have
. According to Algorithm 5, the dimension of the lattice is
. So, the SVP problem is equivalent to
Before mapping the SVP problem into a Hamiltonian, we first introduce the method of reducing numbers in the integer interval
to a Boolean variable polynomial. Let
, introducing
Boolean variables
; the number in the interval can be expressed as
. Therefore, for the coefficient vector
, if each entry satisfies
,
, it can be expressed by Boolean variables
. Substituting the Boolean variable polynomials into (3), we have
where
are calculated constants. Because
are Boolean variables, the above equation is equivalent to
In the above formula, it is required to find the parameter vector
to minimize the function
Encoding the cost function into a Hamiltonian requires a mapping
, where
. Then, substitute
and
to obtain the problem Hamiltonian
where
and
is the Pauli-Z operator acting on the
ith bit. The Hamiltonian acts on a Hilbert space spanned by
qubits, and it can also be written as a sum over many local interactions.
To find the ground state of
H, step 3 generates a hardware-efficient trial wavefunction, which is more suitable for available quantum devices [
27]. Let
and the reference state is set to
.
are a group of single-qubit rotations determined by rotation angles
.
are entangling drift operations generating sufficient entanglement.
D defines the level of the quantum circuit. Obviously, with the increase of
D, the convergence speed increases, but the fidelity decreases.
Step 4 calculates
. Each iteration requires measuring
N times and the cost obtained for the
i-th time is
. Then, the expectation value is
If the Hilbert space is too large, because the interaction is local, the Hamiltonian can be split into a summation over many terms. The expectation calculations for one term are relatively simple, and we can speed up the computation by parallelizing the quantum expectation-value estimation algorithm [
28]. After calculating the expectation of each item on the quantum processor, multiply it by the weight and sum on the classical processor to obtain the final expectation value.
However, the shortest vector is in this algorithm, so the restriction needs to be added. The idea is to increase C when appearing as . We assume that among the N measurements, there are results that are not , . Obviously, the larger the , the smaller the C.
Step 5 uses the classical optimization algorithm to update until the expectation value converges and the process is similar to QAOA.
We give a toy example to illustrate the process on the quantum processor. For a more convenient description, the LWE dimension is further limited, and the example also supports simple experiments on the IBM quantum system. Let
. The samples are
. The LLL-reduced matrix after Kannan’s embedding is
To simplify the model, suppose
, are already Boolean variables. Then, the SVP problem can be reduced into finding the minimum value of
. The problem Hamilton is
Now, construct a hardware-efficient Ansatz consisting of several parameterized single-qubit rotation operations and controlled-NOT gates. Using the parameterized circuit shown in
Figure 3, any 3-qubit quantum state
can be prepared, and different quantum states can be output by adjusting the six parameters.
After preparing the ansatz state and measuring it repeatedly, we calculate the expectation value. Then, we perform the optimization process on the classical processor. Iterate the above process, and finally, the parameters corresponding to the optimal result are and . So, , .
4.2. Algorithm Analysis
First, we analyze the range of in the restriction condition . Let ; then, there exists . Let the shortest vector ; then, . Due to the Gaussian heuristic, , we have .
For an
-dimensional matrix
, its orthogonality defect
. Obviously, for
, there exists
and
if and only if
is an orthogonal matrix. Therefore, the total number of qubits can be expressed as
where
. For a KZ-reduced matrix
, its orthogonality defect satisfies [
29]
So,
Substituting into Equation (
8), we have
Therefore, the maximum number of qubits is
. Now, we review the value of
when using VQE for enumeration. In practice, each
is represented by
qubits and the range of
is
, where
.
In Kannan’s embedding, the lattice dimension is
, where
m is the sample number. In most cases, an LWE-based scheme produces only
LWE samples (and the polynomial bound can be as small as
). In the LWE-based cryptosystem proposed in paper [
12],
and
here means the root-Hermite factor. The theoretical worst-case reduction for LWE requires
[
4], so we set
. Now, we analyze the average number of qubits required, and its LWE parameters are shown in
Table 1.
There are 4 groups of parameters in the table. For each group, 10 experiments are performed, and the average value of the cost function
C is obtained. Finally, we calculate the average number of qubits required, and the result is illustrated in
Figure 4. The four curves with different colors represent that the preprocessing method for the lattice basis is LLL, BKZ-20, BKZ-40 and BKZ-80, respectively. By the regression analysis, taking BKZ-20 as an example, we have
For example, for a 40-dimensional LWE problem, the maximum number of qubits required is 1126, which is a scale that is considered achievable in the near future. With the further development of quantum computers, LWE with larger dimensions can also be solved successively.
4.3. Attacks on Existing Cryptosystems
In this section, we calculate the number of qubits required for a VQE attack on the KYBER cryptosystem. KYBER is a key encapsulation mechanism based on the module-LWE problem, which means it is based on Ring
. KYBER has three modes to satisfy 128/192/256-bit security, respectively. The parameters are listed in
Table 2.
In the table,
represents the maximum degree of polynomial, the number of polynomials in each vector and the modulus. The most famous attack on the MLWE problem does not utilize the special structure of a lattice, so we still analyze it as an LWE problem. Paper [
7] mentioned that the number of samples is between 0 and
. To analyze the worst case, let
. Therefore, in the primal attack, the lattice dimension
. Using the conclusion in
Section 4.2, for the above three parameter settings, the required maximum qubits are 13,768, 19,538, and 25,482, respectively.
Although the quantum computers made at this stage are all NISQ devices, after IBM launched the 127-QubitEagle processor in 2021, it plans to launch the 1121-QubitCondor processor in 2023. At the same time, the IBM team also fully considered the future million-qubit system when designing the world’s largest dilution refrigerator “Goldeneye”, which is an important part of the IBM’s roadmap for scaling quantum technology.