1. Introduction
Secret image sharing (SIS) is a significant branch in multi-party security cryptosystems [
1,
2], which originates from secret sharing (SS) introduced by Shamir in 1979.
-threshold SS can process private data into
n shares managed by different members. When
k or more members provide their shares, the private data can be recovered. Otherwise, nothing will be revealed about the data. As a special format of data, images seldom raise suspicion by the attackers and can cover much information. Thus, SIS realizes information sharing based on images. In 2002, Thien and Lin realized SIS for the first time [
3]. Many researches focus on SIS with various realizations [
4,
5,
6], and continuously study the applications [
7,
8,
9] and improvements [
10,
11,
12,
13]. With the development of network technology, users are increasingly demanding the security, robustness and efficiency of secret image transmission. When plenty of secret images are delivered by SIS in cloud computing, it is difficult for users to manage and search among shadow images which are all noise-like and indistinguishable. These shadow images also suffer from the risk of being tampered with. Suppose attackers modify shadow images, secret images cannot be reconstructed correctly. However, the transmission of fake shadow images wastes lots of time and money, which results in a weak efficiency. For unpublished or confidential drawings like industrial products and instructions, it is necessary to ensure the security. There is an intensely close connection among them, but separate encryption and transmission for each drawing will raise the risk of being attacked. In addition, in police, procuratorate, court and other judicial departments, the most common evidence format is the photo or image. As the quantity of evidence is overgrowing, the staff must attach importance to their management, retrieval, storage and security. However, conventional methods like encryption and marking are incapable of balancing the effectiveness and safety and preventing malicious tampering.
The above issues can be addressed by SIS for multiple secrets (MSIS). Existent SISs mainly include polynomial-based SIS (PSIS), Chinese remainder theorem-based SIS (CRTSIS) and visual cryptography (VC). In general, the object of a traditional SIS is one secret image, while MSIS can share two secret images simultaneously. As shown in
Figure 1, both secret images are shared at the same time. We obtain
n shadow images. Any
k or more of them can recover two secret images. Compared with SIS, MSIS further reduces the risk, improves the effectiveness and saves the storage.
There are broad applications of MSIS. In 2006, Iwamoto et al. [
14] constructed a VC scheme (VCS) for multiple secret images in which each shadow image can be rotated with 180 degrees in decryption. However, the reconstructed secret images were with loss. Naidu et al. [
15] designed a secure e-voting system which provided authentication based on non-transferable personal credentials like biometric features by MSIS, but its theory presented in [
16] also led to a serious loss for recovered fingerprint images and photos. Chen et al. [
17] proposed a new boolean-based MSIS scheme (MSISS) to share different sized secret images, but its process was too complicated and the robustness was poor. Sridhar et al. [
18] proposed an enhanced
-threshold MSISS which uses circular shadow images instead of rectangular ones based on random grids; however, it took four stages to complete the scheme with high operational complexity. Prasetyo et al. [
19] focused on color secret images and introduced a
-threshold MSISS. The security of the scheme mainly relied on the randomness of generalized chaotic image scrambling. However, the scheme itself would not solid and safe. In 2020, Chen et al. [
20] studied boolean-operation for MSIS and introduced a general access structure, but the general structures of other MSIS principles do not be proposed yet. Wang et al. [
21] proposed a polynomial-based scheme to share multiple secret images both within a group and between groups for access control, but the applications of the scheme was too limited. Liu et al. [
22] introduced a
-threshold two-in-one secret image sharing scheme with PSIS and random grid-based visual cryptography scheme (RGVCS) for multiple secrets, but the payload was not ideal. In the following sections, we will compare the scheme with our proposed scheme in detailed parameters, which can prove the improved performance of our scheme. There are many issues in the above MSISSs, namely, recovered secret images distortion, the weak security and the poor ability to resist attack, high complexity (complicated steps or phases of a scheme) and the lack of general structures for other principles, and so we proposed a general and novel MSISS to improve the above issues.
In addition, in 2014, Chang et al. [
23] proposed a lossless secret sharing scheme using a steganography technique. The scheme combined SIS with steganography. From the idea, Mao et al. [
24] proposed a lossless image morphing algorithm to recover the original image from the morphed image. Indeed, the morphed image carried information of two images. However, the scheme realized by combining two independent processes, first realizing SIS and then adding steganography to SIS, which resulted in a low efficiency. For improvement, our proposed scheme is an undivided process by fusing SIS with steganography.
Thus, based on information hiding in sharing domain (IHSD), a -threshold MSISS (IHSD-MSISS) is proposed in this paper, and we provide a general construction model and algorithms. The proposed -threshold IHSD-MSISS is a general and applicable scheme with users’ inputs, which is an undivided process with a reasonable efficiency. The proposed scheme can improve the existent MSISSs, such as the recovery for original images without loss and low complexity, and it also strengthens the security and the robustness.
In practical applications, for images with a strong correlation conventional methods cannot guarantee the required security. Each separate protection and communication for images will occupy the resource and face unpredictable risk. For instance, once an undisclosed product and its instruction manual are stolen, the company will suffer huge financial and reputation losses. For another example, the police usually takes evidence for photos in the crime scene. If one of several related photos is revealed or modified, the pressure and influence will be tremendous.
The proposed scheme is precisely applicable to the above situations. The company can adopt the proposed scheme, embedding product drawings into instruction drawings. It is more safe and reliable for the company to utilize n shadow images and protect these drawings, and they can be recovered at the same time. For police, the proposed scheme can promote the protection for strong-associated evidence and prevent malicious tampering or revelation. The evidence will be divided as n shadow images and can be recovered simultaneously. From the above, we can find that the proposed scheme also saves the storage. A traditional -threshold SIS of two secret images requires shadow images for storage, while our proposed scheme occupies half of the space to share two secret images.
Moreover, we can utilize the proposed scheme to manage and identify shadow images. By embedding logo images into shadow images, the efficiency for management and identification will be improved. The proposed scheme is also applicable in covert communication where the more critical secret image can be transmitted in private by a common image.
In this paper, we propose a general
-threshold IHSD-MSISS to improve existent MSISSs, which based on IHSD [
25] is a novel and undivided MSISS. We introduce the general construction model and algorithms of the proposed scheme. Then, with concrete examples, we present sufficient theoretical analyses, experiments and comparisons which prove the effectiveness of the proposed scheme.
The rest of this paper is organized as follows. Relevant basic knowledge for the proposed scheme is presented in
Section 2.
Section 3 introduces the general and novel
-threshold IHSD-MSISS and provides the realization steps and algorithms of the proposed scheme. With concrete examples, theoretical analyses and proof are given in
Section 4.
Section 5 shows the experimental results and comparisons. Finally,
Section 6 concludes our work.
4. Theoretical Analyses and Proof
In this section, the proposed -threshold IHSD-MSISS is analyzed in theory. We apply a PSIS scheme (PSISS) to the proposed scheme, that is -threshold IHSD-PMSISS, and use the example to discuss clearly and thoroughly. In addition, evaluating metrics of the proposed scheme are discussed. Especially, the embedding rate and the quantity of available random pixels q are theoretically demonstrated for their validity and objectivity.
Analysis 1. The proposed -threshold IHSD-MSISS is undivided and perfectly feasible in theory.
Proof. -threshold IHSD-MSISS is whole and undivided based on IHSD [
25]. SIS of various principles can create random elements, and secret images by SIS will be shared into noise-like shadow images. We focus on the randomness of SIS. By the designed random elements utilization model, we control and screen among the random elements generated in the sharing phase. At the beginning, we generate
n shadow images from the primary secret image. During the sharing phase, we select
m bits from shadow pixels as the payload, and we combine them in a designed order. Then, we utilize the new combinations and try to recover a pixel of the secondary secret image. If the recovery is failed, we will adopt the random elements utilization model again to create lots of random elements for new combinations and tries, so that it is greatly possible for the new combination to recover the secondary secret pixel. Thus, the proposed scheme is perfectly feasible in theory.
In addition, the information hiding condition of IHSD must require the reversibility, while the proposed scheme utilize SIS into IHSD to fuse the sharing phase of the secondary secret image into the sharing phase of the primary secret image. SIS is reversible, so the proposed scheme can realize by IHSD.
Moreover, the sharing phase of the proposed scheme is the sharing phase of the primary secret image with other operations. After the sharing phase, n shadow images carries the information of two secret images. So the proposed scheme is an undivided scheme for sharing multiple secrets. □
Analysis 2. -threshold IHSD-MSISS is secure in theory.
Proof. -threshold IHSD-MSISS applies the idea of IHSD [
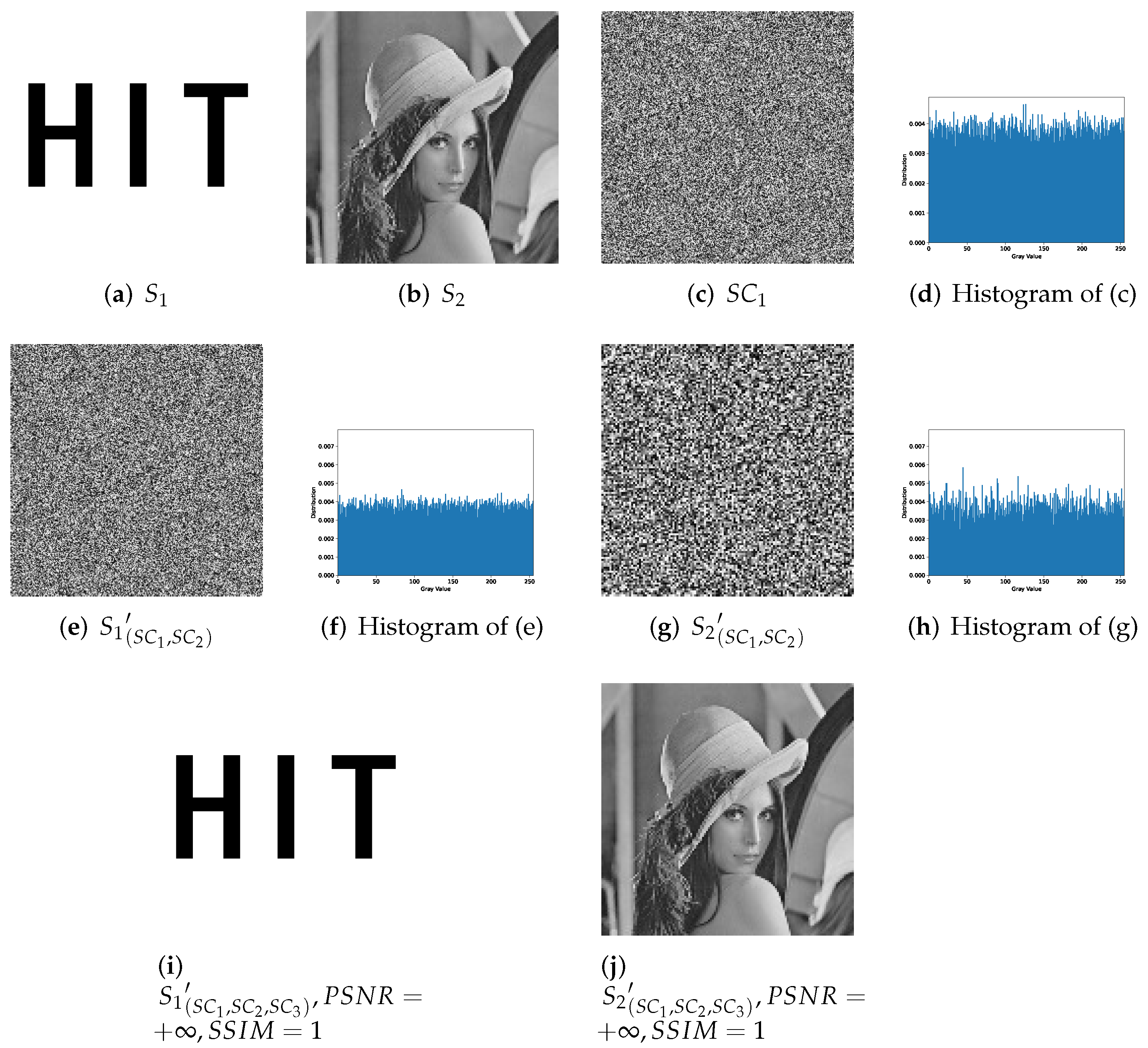
25], which describes that the sharing phase of SIS not only can protect a secret image but also can hide extra information at the same time. An SIS generates many random pixels for a secret image to confuse images’ original features. To avoid suspicion and maintain enough randomness, hidden information must be absolutely random in IHSD for promoted security. Nature images are born with texture features. By SIS, the images will be divided as noise-like shadow images. From this idea, the proposed scheme realizes by utilizing SIS in IHSD. It fuses the sharing phase of the secondary secret image into the sharing phase of the primary secret image. The shadow images of the secondary secret can be extracted from the shadow images of the primary secret, which relies on SIS. Thus, the proposed scheme is safe. Moreover, the histograms of final shadow images should be well-distributed theoretically. □
Analysis 3. -threshold IHSD-MSISS is general and applicable.
Proof. Existent popular SIS including PSIS, CRTSIS and VC can generate lots of random elements in the sharing phase. From the principle, we proposed the -threshold IHSD-MSISS. Thus, one of the above SISS with the proper images can be applied in the proposed scheme. □
Analysis 4. -threshold IHSD-MSISS shares two secret images into n shadow images. In the recovery phase, n shadow images can recover both secret images simultaneously, so that the recovery rate is . Moreover, if any shadow images are missed or damaged, neither secret image will be recovered.
Proof. -threshold IHSD-MSISS relies on -threshold SIS. When , the number of shadow images participated in the sharing and recovery phase is the same. So, in the recovery phase, by n shadow images we can obtain two secret images without loss, and the recovery rate is .
In addition, the proposed scheme realizes based on the sharing phase of the primary secret image. From n shadow images of the primary secret image, we can extract n shadow images of the secondary secret image. n shadow images generated from the proposed scheme carries the information of two secret images. Thus, any lack or modification of shadow images will fail recovery for both secret images. □
Analysis 5. Recovered secret image fidelity relies on the concrete inputs in -threshold IHSD-MSISS. By the proposed scheme, the secret images can be recovered losslessly. The fidelity is independent of the realization principle of the proposed scheme.
Proof. Recovered secret image fidelity of -threshold IHSD-MSISS relies on the user’s inputs, which is relevant with pixel values of the secret images and concrete SIS parameters.
For instance, we use PSISS with prime and share two secret images whose pixels both range from 0 to 250. The recovered images will be lossless. However, in the case of PSISS with and secret images with , we will obtain two recovered secret images with loss. □
Analysis 6. In -threshold IHSD-MSISS, the embedding rate is defined as Equation (7). Proof. In
-threshold IHSD-MSISS, we aim at two secret images in the sharing phase, each in grayscale level
with the size of
and the weight factor
. Then, we get
n shadow images of grayscale level
with the size of
. The proposed scheme protect two secret images by
n shadow images. Thus, the equation of embedding rate
, which measures the rate of each share bit carrying with secret images, can be calculated in Equation (
7). By the equation, we also know that the larger
-threshold, the less
. □
Analysis 7. The quantity of available random pixels denoted by q is the total number of qualified shadow pixels in a single sharing phase of a primary secret pixel. q has to be calculated by a concrete SISS. By -threshold IHSD-PMSISS, q will be calculated in Equation (10), where p, m and n denote prime p of PSISS, the number of payload bits and -threshold, respectively. Proof. In
-threshold IHSD-PMSISS, a primary secret pixel is shared by a random
-degree polynomial with
n coefficients denoted by
,
, ⋯,
. Except
, the other coefficients range from 0 to
. There are
p possibilities for each coefficient so that a random polynomial has
possibilities. Once the polynomial is determined,
n shadow images generated in the sharing phase will be decided. For a primary secret pixel, there are
n shadow pixels generated by a random polynomial, which has
probabilities. Users need to decide the number of payload bits, that is
m-bit payload, in
-threshold IHSD-PMSISS, where
m-bit payload means selecting
m front bits from each shadow pixel (
n shadow pixels in total) out of the primary secret pixel. Eight bits of shadow pixels are 0 or 1 in binary. So, there are two possibilities for each payload bit. Among
possibilities,
m-bit payload in
n shadow pixels should be considered together for judgment of qualified shadow pixels, which has
possibilities. Thus, the equation of
q in
-threshold IHSD-PMSISS is calculated in Equation (
10). Moreover, the quantity of available random pixels of the example in
Section 3, denoted by
, can be also proved as Equation (
9). □
Analysis 8. The sharing and recovery time of -threshold IHSD-MSISS is dependent on the embedding rate and the quantity of available random pixels, where we conclude theoretically that the higher embedding rate, the more the time, while the greater the quantity of available random pixels, the less the time.
Proof. According to Algorithm 1, m-bit payload means that we simultaneously share secret pixels. In -threshold IHSD-MSISS, the higher embedding rate implies that the payload bits are more (m is larger). It is more difficult to combine from shadow pixels of fewer secret pixels ( is fewer), which will take more time. In addition, as the quantity of available random pixels is more, the probability of combinations from qualified shadow images will be higher, so the proposed scheme will spend less time sharing multiple secrets. □
6. Conclusions
In this paper, we have proposed a novel and general
-threshold IHSD-MSISS. The proposed
-threshold scheme fuses the sharing phases of two secret images by controlling and screening among the randomness of SIS. The introduction of the proposed scheme are presented. We theoretically analyze the practicability and applicability. Through a concrete instance that a
-threshold IHSD-PMSISS in 1-bit, 2-bit and 4-bit payload, we experiment and further validate the availability and security of the proposed scheme. Comparisons with the scheme of [
22] are given for a comprehensive comment on our proposed scheme.
From the experimental and compared results, the proposed scheme can recover two secret images losslessly with
and
. In the most difficult experimental conditions,
-threshold with 4-bit payload, the average time is 9497.492 s, which is the longest but still acceptable. In addition, the embedding rate of the proposed scheme in 1-bit payload is equal to that of the scheme [
22]. In other, more complex conditions, the embedding rate of the proposed scheme is higher. Thus, the proposed scheme improves the efficiency of sharing multiple secrets.
As the payload bits are increase in number, the current average time by proposed -threshold IHSD-MSISS will ascend sharply. Thus, our future work is to improve the efficiency of our proposed scheme. Moreover, we will study IHSD-MSISS on -threshold for more applications.