Intelligent Reflecting Surface–Assisted Wireless Secret Key Generation against Multiple Eavesdroppers
Abstract
:1. Introduction
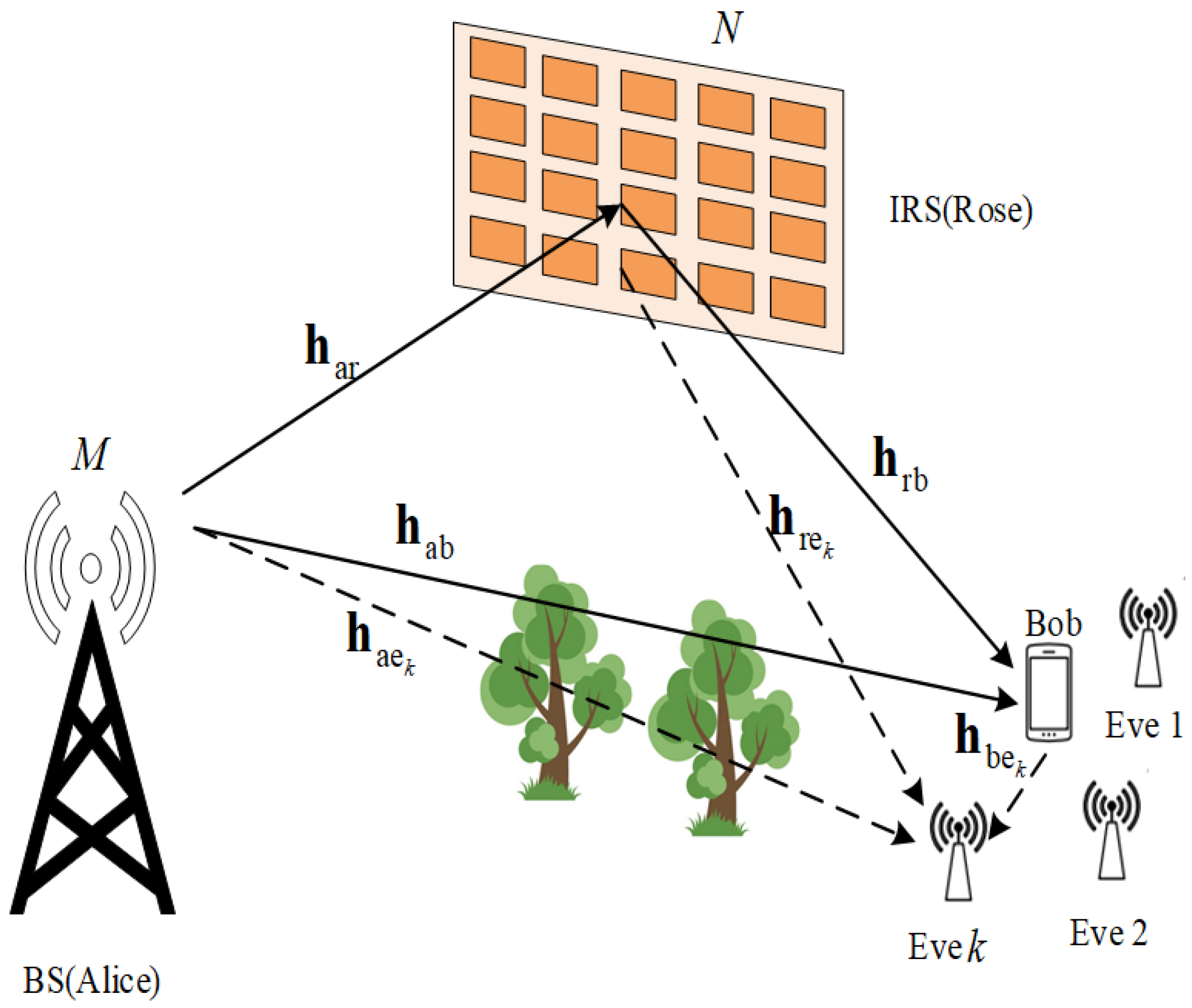
2. System Model and Signal Representation
2.1. Channel Model
2.2. Spatial Correlation
3. IRS-Assisted Secret Key Rate Analysis
4. Proposed Optimization Scheme and Solution
4.1. Optimization Analysis
| Algorithm 1 Our algorithm based on SDR and CCP |
| Input: |
| Output: , |
| 1: Initialize , and Set . |
| 2: repeat (Bisection Search for ) |
| 3: repeat (Our algorithm based on SDR and CCP) |
| 4: For given , when , initialize a positive semi-definite matrix randomly; when |
| , given , solve the above optimization problem (28) for . |
| 5: Update . |
| 6: until the optimization variable reaches convergence. |
| 7: Record of the current iteration if the above problem can be solved, then update |
| ; if is unreachable, then update |
| 8: until . |
| 9: Recover from by Gaussian randomization. |
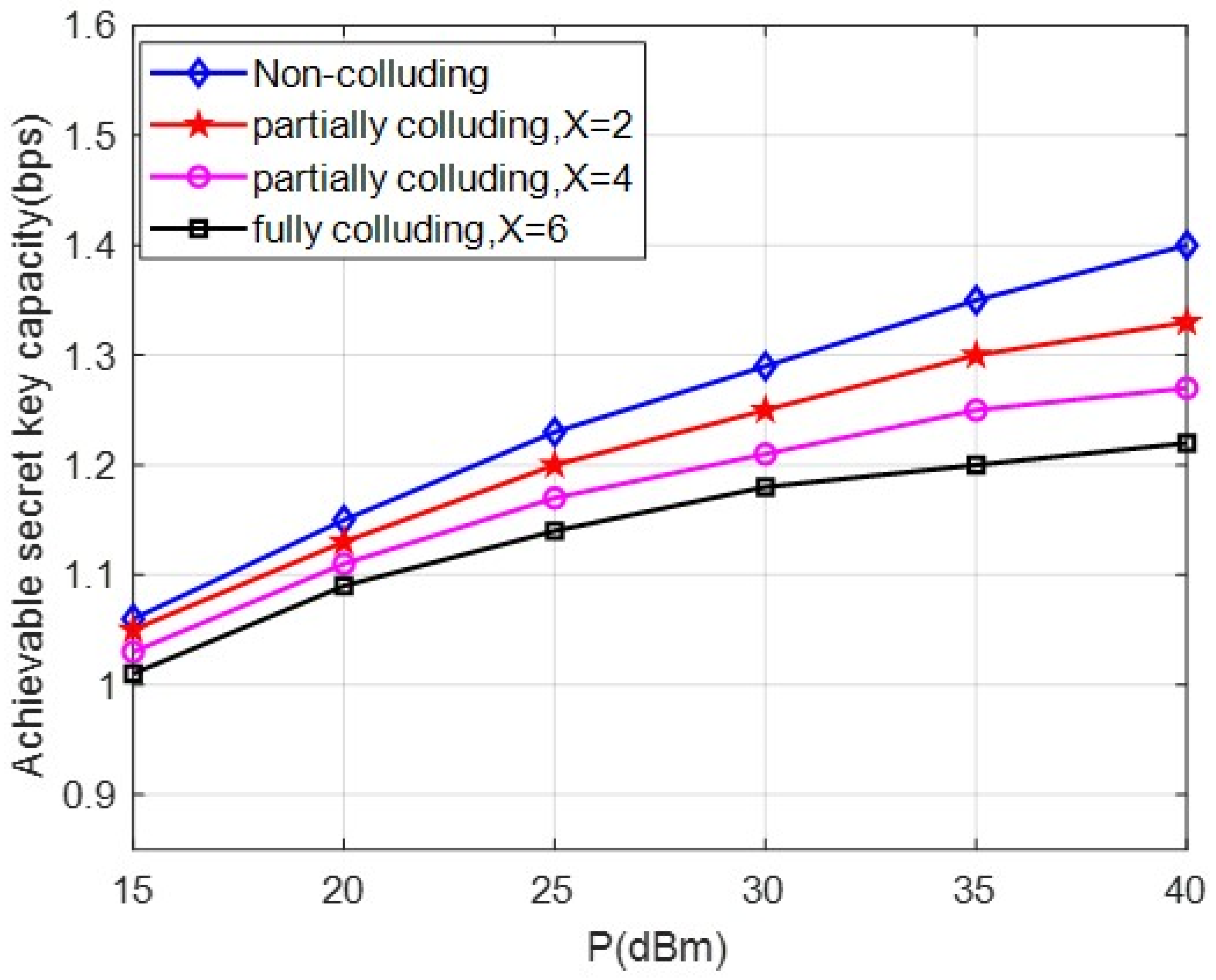
4.2. Partially Colluding and Fully Colluding Cases
4.3. Discussion on Active Pilot Attacks
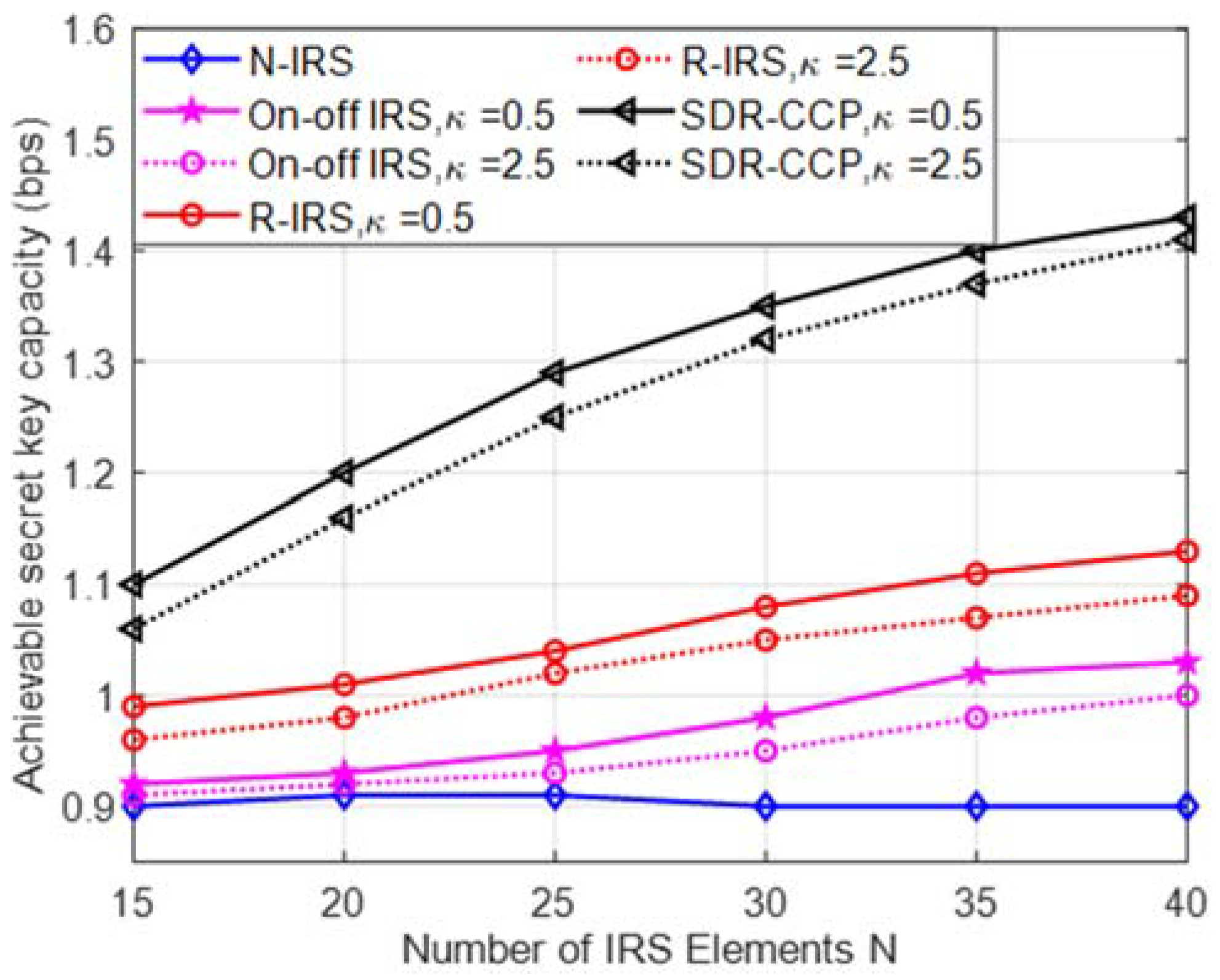
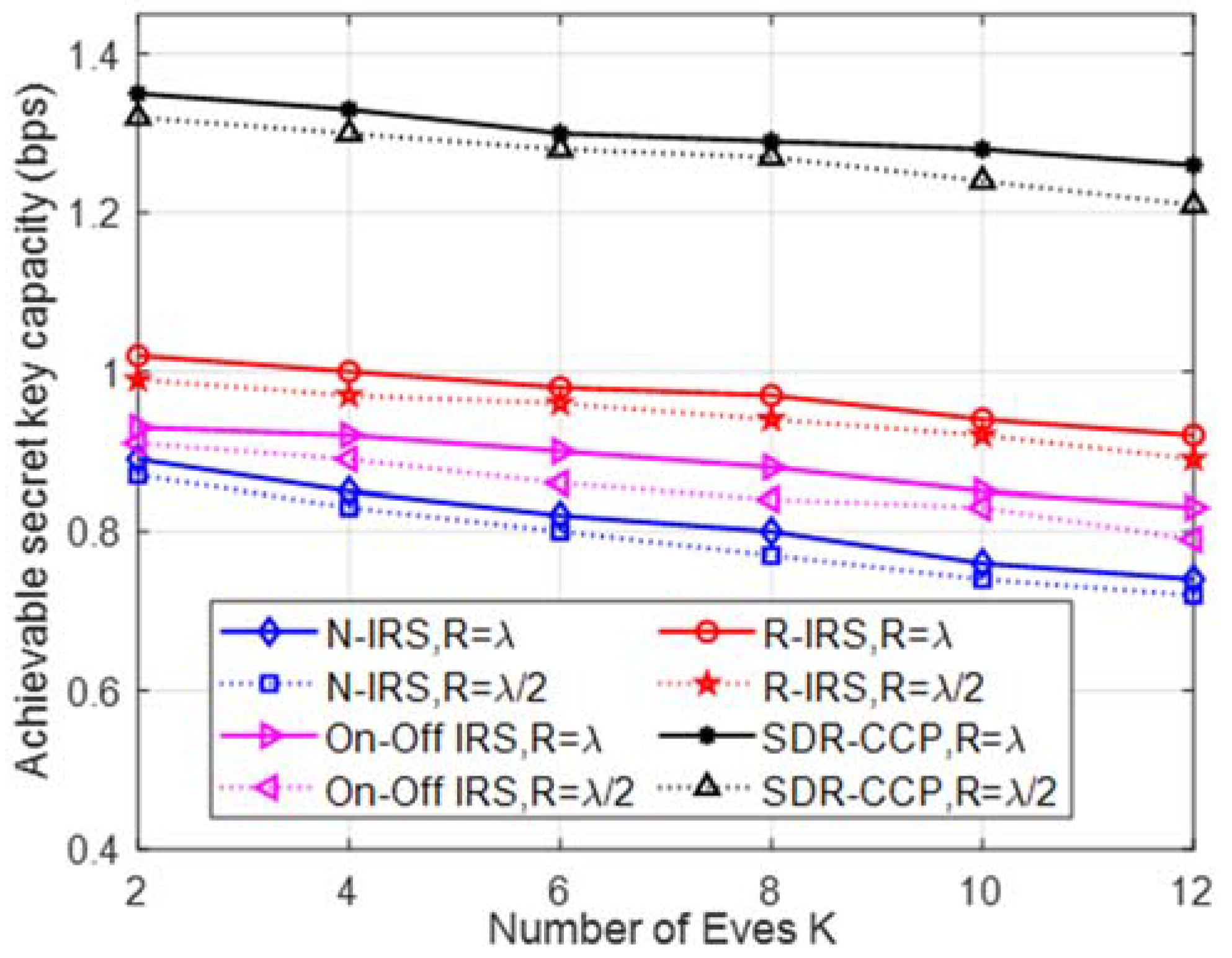
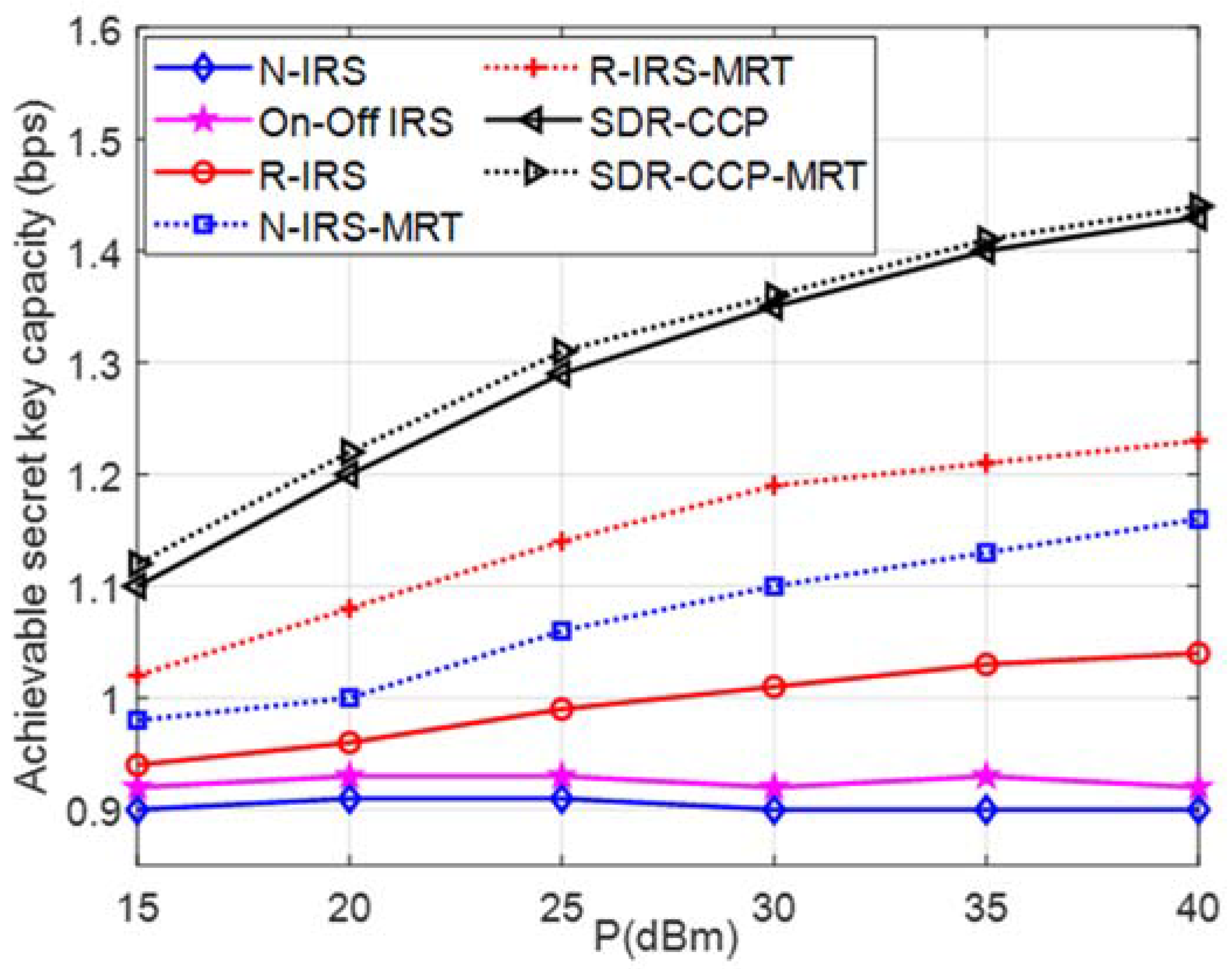
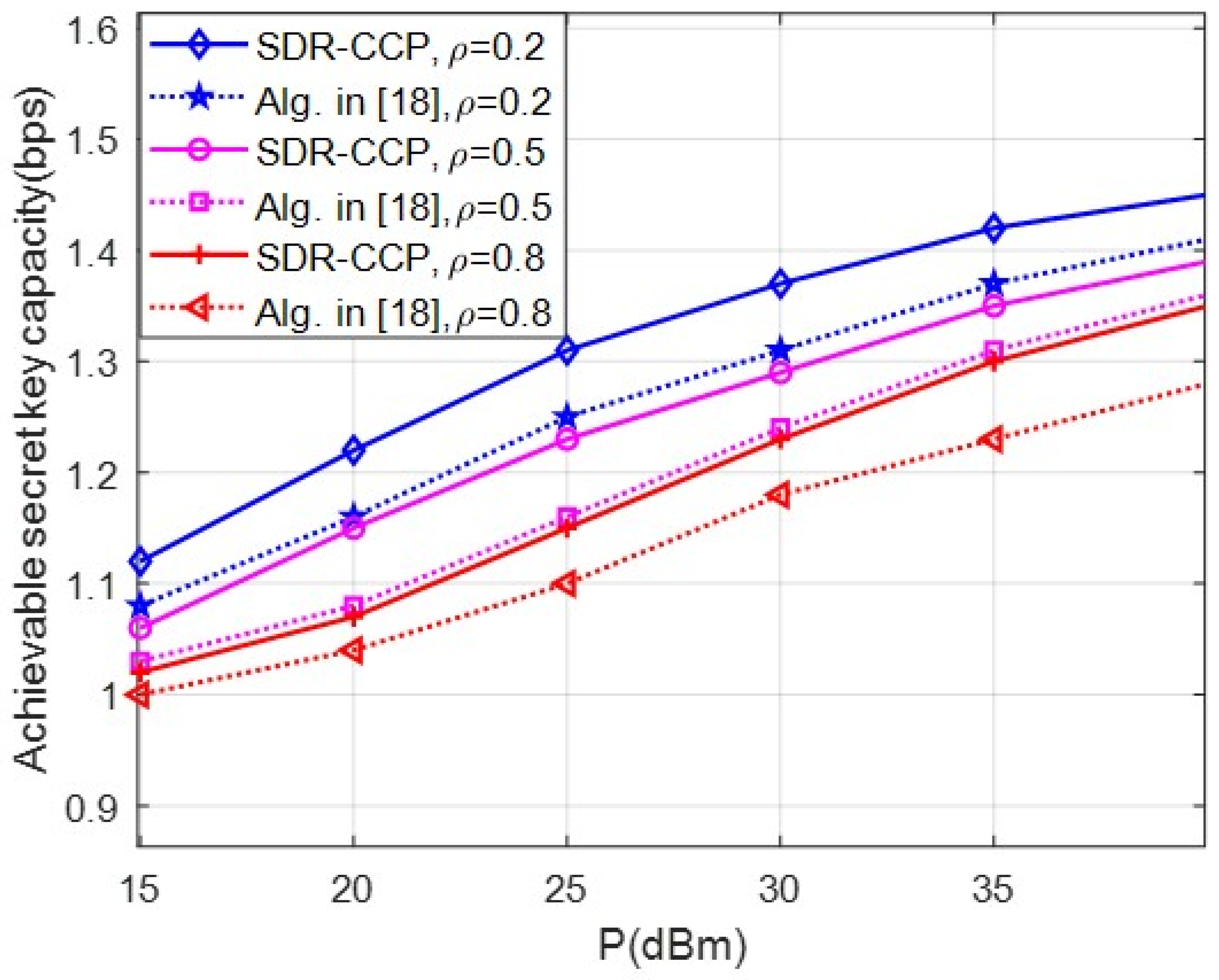
5. Simulation Analysis
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ylianttila, M.; Kantola, R.; Gurtov, A.; Mucchi, L.; Oppermann, I.; Yan, Z.; Nguyen, T.H.; Liu, F.; Hewa, T.; Liyanage, M.; et al. 6G white paper: Research challenges for trust, security and privacy. arXiv 2020, arXiv:2004.11665. [Google Scholar]
- Zhang, H.; Ji, Z.; Wang, H.; Wu, W. Survey on quantum information security. China Commun. 2019, 16, 1–36. [Google Scholar] [CrossRef]
- Maurer, U.M. Secret key agreement by public discussion from common information. IEEE Trans. Inf. Theory 1993, 39, 733–742. [Google Scholar] [CrossRef] [Green Version]
- Li, G.; Zhang, Z.; Zhang, J.; Hu, A. Encrypting Wireless Communications on the Fly Using One-Time Pad and Key Generation. IEEE Internet Things J. 2021, 8, 357–369. [Google Scholar] [CrossRef]
- Li, G.; Sun, C.; Zhang, J.; Jorswieck, E.; Xiao, B.; Hu, A. Physical layer key generation in 5G and beyond wireless commu-nications: Challenges and opportunities. Entropy 2019, 21, 497. [Google Scholar] [CrossRef] [Green Version]
- Zeng, K. Physical layer key generation in wireless networks: Challenges and opportunities. IEEE Commun. Mag. 2015, 53, 33–39. [Google Scholar] [CrossRef]
- You, X.; Wang, C.-X.; Huang, J.; Gao, X.; Zhang, Z.; Wang, M.; Huang, Y.; Zhang, C.; Jiang, Y.; Wang, J.; et al. Towards 6G wireless communication networks: Vision, enabling technologies, and new paradigm shifts. Sci. China Inf. Sci. 2021, 64, 110301. [Google Scholar] [CrossRef]
- Wallace, J. Secure Physical Layer Key Generation Schemes: Performance and Information Theoretic Limits. In Proceedings of the 2009 IEEE International Conference on Communications, Dresden, Germany, 14–18 June 2009; pp. 1–5. [Google Scholar] [CrossRef] [Green Version]
- Huth, C.; Guillaume, R.; Strohm, T.; Duplys, P.; Samuel, I.A.; Güneysu, T. Information reconciliation schemes in physical-layer security: A survey. Comput. Netw. 2016, 109, 84–104. [Google Scholar] [CrossRef]
- Bennett, C.; Brassard, G.; Crepeau, C.; Maurer, U. Generalized privacy amplification. IEEE Trans. Inf. Theory 1995, 41, 1915–1923. [Google Scholar] [CrossRef] [Green Version]
- Wang, Z.; Cao, Y.; Zhang, D.; Hua, X.; Gao, P.; Jiang, T. User Selection for MIMO Downlink With Digital and Hybrid Maximum Ratio Transmission. IEEE Trans. Veh. Technol. 2021, 70, 11101–11105. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, R. Towards Smart and Reconfigurable Environment: Intelligent Reflecting Surface Aided Wireless Network. IEEE Commun. Mag. 2020, 58, 106–112. [Google Scholar] [CrossRef] [Green Version]
- Wu, Q.; Zhang, R. Beamforming Optimization for Wireless Network Aided by Intelligent Reflecting Surface with Discrete Phase Shifts. IEEE Trans. Commun. 2020, 68, 1838–1851. [Google Scholar] [CrossRef] [Green Version]
- Abeywickrama, S.; Zhang, R.; Wu, Q.; Yuen, C. Intelligent Reflecting Surface: Practical Phase Shift Model and Beamforming Optimization. IEEE Trans. Commun. 2020, 68, 5849–5863. [Google Scholar] [CrossRef]
- Liu, F.; Tsilipakos, O.; Pitilakis, A.; Tasolamprou, A.C.; Mirmoosa, M.S.; Kantartzis, N.V.; Kwon, D.-H.; Georgiou, J.; Kossifos, K.; Antoniades, M.A.; et al. Intelligent metasurfaces with continuously tunable local surface impedance for multiple reconfigurable functions. Phys. Rev. Appl. 2019, 11, 044024. [Google Scholar] [CrossRef] [Green Version]
- Chen, L.; Hu, W.; Jamieson, K.; Chen, X.; Fang, D.; Gummeson, J. Pushing the physical limits of IoT devices with pro-grammable metasurfaces. In Proceedings of the 18th Symposium on Networked Systems Design and Implementation, Boston, MA, USA, 12–14 April 2021. [Google Scholar]
- Ji, Z.; Yeoh, P.L.; Zhang, D.; Chen, G.; Zhang, Y.; He, Z.; Yin, H.; Li, Y. Secret Key Generation for Intelligent Reflecting Surface Assisted Wireless Communication Networks. IEEE Trans. Veh. Technol. 2021, 70, 1030–1034. [Google Scholar] [CrossRef]
- Hu, X.; Jin, L.; Huang, K.; Sun, X.; Zhou, Y.; Qu, J. Intelligent Reflecting Surface-Assisted Secret Key Generation With Discrete Phase Shifts in Static Environment. IEEE Wirel. Commun. Lett. 2021, 10, 1867–1870. [Google Scholar] [CrossRef]
- Lu, X.; Lei, J.; Shi, Y.; Li, W. Intelligent Reflecting Surface Assisted Secret Key Generation. IEEE Signal Process. Lett. 2021, 28, 1036–1040. [Google Scholar] [CrossRef]
- Staat, P.; Elders-Boll, H.; Heinrichs, M.; Kronberger, R.; Zenger, C.; Paar, C. Intelligent Reflecting Surface-Assisted Wireless Key Generation for Low-Entropy Environments. In Proceedings of the 2021 IEEE 32nd Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Helsinki, Finland, 13–16 September 2021; pp. 745–751. [Google Scholar] [CrossRef]
- Hoang, T.M.; Dung, L.T.; Nguyen, B.C.; Tran, X.N.; Kim, T. Secrecy Outage Performance of FD-NOMA Relay System With Multiple Non-Colluding Eavesdroppers. IEEE Trans. Veh. Technol. 2021, 70, 12985–12997. [Google Scholar] [CrossRef]
- Wang, P.; Fang, J.; Duan, H.; Li, H. Compressed Channel Estimation for Intelligent Reflecting Surface-Assisted Millimeter Wave Systems. IEEE Signal Process. Lett. 2020, 27, 905–909. [Google Scholar] [CrossRef]
- Li, G.; Hu, A.; Zhang, J.; Peng, L.; Sun, C.; Cao, D. High-Agreement Uncorrelated Secret Key Generation Based on Principal Component Analysis Preprocessing. IEEE Trans. Commun. 2018, 66, 3022–3034. [Google Scholar] [CrossRef]
- Li, G.; Sun, C.; Xu, W.; Di Renzo, M.; Hu, A. On Maximizing the Sum Secret Key Rate for Reconfigurable Intelligent Surface-Assisted Multiuser Systems. IEEE Trans. Inf. Forensics Secur. 2022, 17, 211–225. [Google Scholar] [CrossRef]
- Thai, C.D.T.; Lee, J.; Quek, T.Q.S. Physical-Layer Secret Key Generation with Colluding Untrusted Relays. IEEE Trans. Wirel. Commun. 2016, 15, 1517–1530. [Google Scholar] [CrossRef]
- Chen, G.; Gong, Y.; Xiao, P.; Chambers, J.A. Physical Layer Network Security in the Full-Duplex Relay System. IEEE Trans. Inf. Forensics Secur. 2015, 10, 574–583. [Google Scholar] [CrossRef] [Green Version]
- Sun, C.; Li, G. Power Allocation and Beam Scheduling for Multi-User Massive MIMO Secret Key Generation. IEEE Access 2020, 8, 164580–164592. [Google Scholar] [CrossRef]
- Guan, X.; Wu, Q.; Zhang, R. Intelligent Reflecting Surface Assisted Secrecy Communication: Is Artificial Noise Helpful or Not? IEEE Wirel. Commun. Lett. 2020, 9, 778–782. [Google Scholar] [CrossRef] [Green Version]
- Zhang, J.; He, B.; Duong, T.Q.; Woods, R. On the Key Generation from Correlated Wireless Channels. IEEE Commun. Lett. 2017, 21, 961–964. [Google Scholar] [CrossRef] [Green Version]


Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, Y.; Huang, K.; Sun, X.; Yang, S.; Wang, L. Intelligent Reflecting Surface–Assisted Wireless Secret Key Generation against Multiple Eavesdroppers. Entropy 2022, 24, 446. https://doi.org/10.3390/e24040446
Liu Y, Huang K, Sun X, Yang S, Wang L. Intelligent Reflecting Surface–Assisted Wireless Secret Key Generation against Multiple Eavesdroppers. Entropy. 2022; 24(4):446. https://doi.org/10.3390/e24040446
Chicago/Turabian StyleLiu, Ya, Kaizhi Huang, Xiaoli Sun, Shaochuan Yang, and Liang Wang. 2022. "Intelligent Reflecting Surface–Assisted Wireless Secret Key Generation against Multiple Eavesdroppers" Entropy 24, no. 4: 446. https://doi.org/10.3390/e24040446





