Abstract
Image encryption based on elliptic curves (ECs) is emerging as a new trend in cryptography because it provides high security with a relatively smaller key size when compared with well-known cryptosystems. Recently, it has been shown that the cryptosystems based on ECs over finite rings may provide better security because they require the computational cost for solving the factorization problem and the discrete logarithm problem. Motivated by this fact, we proposed a novel image encryption scheme based on ECs over finite rings. There are three main steps in our scheme, where, in the first step, we mask the plain image using points of an EC over a finite ring. In step two, we create diffusion in the masked image with a mapping from the EC over the finite ring to the EC over the finite field. To create high confusion in the plain text, we generated a substitution box (S-box) based on the ordered EC, which is then used to permute the pixels of the diffused image to obtain a cipher image. With computational experiments, we showed that the proposed cryptosystem has higher security against linear, differential, and statistical attacks than the existing cryptosystems. Furthermore, the average encryption time for color images is lower than other existing schemes.
1. Introduction
In this modern era, the transmission of images over public networks is an indispensable task. Therefore, distributing secret images in a secure way is essential. Encryption schemes take plain-text data as an input and convert it into an unreadable form using secret keys. Then, an authorized person uses the secret keys to acquire the original data. Recently, S-box-based encryption algorithms have gained special attention [1]. An S-box is used to create confusion; therefore, researchers are not only trying to improve the existing S-box schemes, but are also proposing new ones. Many authors (see, for example, [2,3]) have observed that the S-box used in the well-known cryptosystem, the advanced encryption standard (AES), is vulnerable because the AES cryptosystem uses a static S-box. Furthermore, it also has low algebraic complexity.
The role of an S-box is vital in a cryptosystem. Therefore, researchers are trying to generate S-boxes which are cryptographically secure. One way is to improve the security of the AES cryptosystem. That is why Cui and Cao [4] enhanced the algebraic complexity of an AES S-box to make it secure against algebraic attacks. Similarly, Liu et al. [5] proposed an improved AES S-box that has reliable security against algebraic and differential attacks. Tran et al. [6] presented the Gray S-box for the AES, which is secure against algebraic and interpolation attacks. In addition to this, many other techniques are used to design S-boxes with the desired security. For example, Silva-Garcia et al. [7] developed a novel chaos-based cryptosystem, which generates an S-box to resist linear attacks. Ibrahim and Alhabi [1] used a Henon map to generate secure and dynamic S-boxes. Özkaynak [8] proposed robust S-boxes using different chaotic systems. Due to their higher security, EC-based cryptosystems have gained the interest of researchers. Miller [9] presented an EC-based cryptosystem with high security and a small key size. Cheon et al. [10] used hyperelliptic curves to obtain a lower bound on the nonlinearity of Boolean functions. Hayat et al. [11,12] employed ECs over finite fields and rings to design secure S-boxes. It is analyzed that the S-box generators over finite rings generate dynamic S-boxes with reasonable time complexity.
Furthermore, the pixels have high correlation and the data size is large in an image. Therefore, to develop secure cryptosystems for the delivery of secret images is a common interest of researchers. Many techniques, such as fuzzy theory [13] and chaotic maps [14,15,16,17,18,19,20,21,22,23,24,25], are used to develop encryption schemes.
Recently, chaos-based schemes have received more attention due to their easy implementation and fast execution [26]. Similarly, chaotic maps have some unique characteristics, such as ergodicity, unpredictability, random behavior, and sensitivity to initial parameters, which are required for a good cryptosystem [27]. Therefore, a number of image encryption schemes are proposed based on sine maps [28,29], cat maps [30], and some other chaotic maps [31]. Huang et al. [32] developed an encryption scheme with better confusion-creation capability using the Rivest–Shamir–Adleman (RSA) algorithm and Arnold map. Similarly, Ye et al. [33] designed an effective and secure image cryptosystem based on the RSA technique and a fractional-order chaotic system. On the other hand, there exist chaotic encryption schemes which are not secure. Chen et al. [30] developed an image encryption algorithm using a 3D chaotic cat map, which has short period and hence, is vulnerable to the chosen plain-text attack [34]. Similarly, the scheme developed by Sui et al. [31] is based on logistic maps; however, logistic maps are insecure due to the small key space [14].
Related work: Like chaotic maps, elliptic curves (ECs) are highly sensitive to the initial parameters, and a number of EC-based algorithms have been developed for cryptographic applications [9,35,36,37,38,39,40,41,42,43,44,45,46,47,48]. Zhang and Wang [40] used the group law for the generation of a public key and encrypted digital images by combining a chaotic system and elliptic curve cryptography (ECC). Abdelfatah [41] presented a digital signature scheme using the group law. Abbas et al. [42] proposed a chaotic encryption algorithm using an addition operator over the points of the EC. El-Latif et al. [49] developed an efficient encryption scheme using a cyclic EC and a generalized logistic map; basically, an EC-based sequence and a chaotic sequence are combined to generate a keystream for encryption. Toughi et al. [50] generated a sequence of numbers using ECs, which are then used in the generation of keys to propose an encryption algorithm. Hayat et al. [51] proposed a twofold image encryption scheme. Firstly, a plain image is masked by EC-based random numbers, and then permuted by an S-box generated using an EC. Reyad et al. [52] modulated random sequences using ECs and chaotic maps. It is experimentally proved that all the above schemes are highly secure. In addition, ECs provide more security to a cryptosystem than chaotic maps [53,54], but it is important to mention that the scheme in [49] first generates a sequence of scalars. Each scalar is then mapped to a scalar multiple of a point of a cyclic EC. To compute a scalar multiple of a point lying on an EC is not simple; it involves the group law, consisting of many complex calculations. Similarly, the scheme in [52] also uses group operations to generate random numbers from the points of ECs. Thus, the schemes of [4041,42,44,49,52] are time-consuming due to the use of the group law. The scheme in [51] avoids the group law to generate ECs, but each plain image requires the generation of two ECs. Moreover, trials are required for the generation of ECs to ensure the encryption of an image because the said scheme does not output an S-box for all parameters. These facts slow the execution time of the scheme. The algorithm in [37] does not generate triads for all images of the same size, but generates an EC for each image, which enhances the execution time.
In all the above-discussed EC-based schemes, finite fields are used to obtain the desired security. The security of such cryptosystems based on ECs over finite fields essentially depends on the computational cost for solving the discrete logarithm problem [55]. Recently, Diaz et al. [55] pointed out that the cryptosystems based on ECs over finite rings are more secure as compared to the cryptosystems based on ECs over finite fields. Their claim follows from the fact that the computational cost of breaking such cryptosystems based on ECs over finite rings depends on solving the factorization problem [56] and the discrete logarithm problem. Our research contribution aims to develop a cryptosystem that is based on a ring of integers and that has higher resistance against modern attacks than the existing schemes of ECs over finite fields. In this work, we propose:
- A new S-box generator that can generate a good S-box based on an EC over a finite ring of integers;
- An image encryption algorithm using the aforementioned S-box generator.
The current work is novel in the sense that:
- It is based on a ring of integers rather than on a finite field;
- It avoids the traditional way (group law) of generating an EC. Furthermore, it imposes a bound on the y-coordinate of the EC, which is not the case in [12,51], and one does not have to check all the possible values over the underlying structure. So, the current S-box generator is comparatively efficient for a possible S-box;
- It generates cryptographically strong S-boxes;
- The time complexity of the proposed scheme is dependent on the chosen bound on the y-coordinate of the EC;
- Unlike the case in [37,51,57], each input image does not need the computation of a new EC for the confusion phase;
- It can encrypt a number of images with better security against differential, statistical, key and plain-text attacks;
- The run-time of the proposed scheme to encrypt color images is very low.
The rest of the paper is organized as follows: Section 2 contains the related notions of ECs. In Section 3, the proposed S-box algorithm and its analysis is described. In Section 4, the proposed image encryption scheme is presented. In Section 5, the decryption of the proposed scheme is reported. The security analysis is conducted in Section 6. An application of the proposed scheme to color images is shown in Section 7. Lastly, the conclusion is drawn in Section 8.
2. Related Notions of ECs
Let be a set of primes for any indexing set . Then, for , is a composite integer and, hence, is a ring. As for each prime p, represents a finite field. Thus, for primes , we say that is a finite field related to the ring . For any two integers, , with the condition that , the EC represents the set of points , where ∞ is the neutral point lying at each vertical line passing through the EC, and is the discriminant of . The condition on the discriminant is imposed so that the EC has no singular point. The integers and b are known as the parameters of . For , the ECs are known as Mordell elliptic curves (MECs); we denote them by , and denotes the number of points on the MEC . There is a bijection [56] between and , which maps to Consequently, an EC may be deduced from by mapping to and, hence, for each we have a surjective map from to . Let and represent the former bijective and surjective maps, respectively; then, mathematically, f and g are given by:
The MECs play an important role in cryptography. Azam et al. [58] defined different total orders, named as natural ordering () and diffusion ordering (), on the points of MECs. For details, the readers are referred to [58].
3. The Proposed S-Box and Its Analysis
The proposed encryption scheme in Section 4 requires an S-box generator to obtain the desired level of confusion. For the construction of an S-box, we need the parameters , and t. It is mentioned that , where each is a prime and k is a positive integer. In principle, n may be assigned any value. We choose n as a product of primes because, in the masking phase for each prime , we need the EC over the related prime field . The parameters are used to generate the EC over the ring of integers , where t is used as an upper bound on the y-coordinate of the EC . Here, upper bound t means that we compute such for which . The y-coordinate is kept bounded, so that we compute for all and particular values of y instead of all . This is conducted in order to reduce the time of execution. After the generation of the EC , the points of need to be arranged by some ordering. The points may be arranged according to any ordering, but the ordering is capable of generating S-boxes with high cryptographic properties. Therefore, we use to sort the points of . Then, we construct an S-box by extracting the first different values of the y-coordinate of the ordered . Mathematically, the S-box is generated according to the following function:
defined by:
where for some and for . The S-box construction is clearly described in the following steps: stepsenumerate1
- Step 1.
- To generate an S-box, select three integers , and t such that and ;
- Step 2.
- Choose primes for a finite in such a way that ;
- Step 3.
- For each and , compute all the points such that ; i.e., compute ;
- Step 1.
- If the set is contained in the y-coordinates of the points , then proceed to Step 5. Otherwise, change for some i and repeat Steps 1–3;
- Step 5.
- Arrange the points of by applying the ordering ;
- Step 6.
- Construct the S-box , such that , where for some with the constraint that and for .
For parameters , and , an S-box generated by the proposed method on an EC is shown in Table 1.

Table 1.
The S-box generated by the proposed algorithm.
3.1. Analysis of the Proposed S-Box
The cryptographic strength of the proposed S-box is analyzed by well-known tests, which are described as follows.
3.1.1. Linear Attacks
A cryptosystem is secure if it can strongly resist attackers to exploit the linear relations of inputs and outputs. The immunity of an S-box S against linear attacks is evaluated by its non-linearity NL(S) [59], linear approximation probability LAP(S) [60], and algebraic complexity AC(S) [61].
For a chosen n, the NL(S) represents the minimum Hamming distances between the S-box S and all the corresponding affine functions. Similarly, the LAP(S) is the approximation of the relation lying between the inputs and outputs, and the AC(S) represents the number of non-zero terms in the polynomial representation of the S-box S. Mathematically, the NL(S) and LAP(S) are computed by Equations (1) and (2), respectively:
where , and “· ”denotes the dot product. The resistance to linear attacks is greater if the NL(S) is close to , the LAP(S) is low, and the AC(S) tends to . The values of the NL, LAP, and AC for the S-box shown in Table 1 are , and 254, respectively. Moreover, from Table 2, it follows that the NL of the proposed S-box is greater than those of [51,62,63,64,65,66] and equal to NL of the S-boxes in [8,12,37,48,58]. Similarly, the LAP of the new S-box is less than the LAP of the S-boxes in [8,12,37,48,51,58,62,63,64,65,66]. The AC of the presented S-box is greater than the AC of the S-boxes proposed in [51,58,64,65] and equal to that of the S-boxes [37,62,63,66]. From the above discussion, it is obvious that the proposed S-box is highly secure against linear attacks, compared to the S-boxes in [37,51,58,62,63,64,65,66], while the security of the proposed S-box against linear attacks is comparable with the S-boxes in [8,12,48].

Table 2.
Comparison of the S-boxes generated by the proposed algorithm and some recent algorithms.
3.1.2. Differential Attacks
Differential attacks are used to study the differences of outputs for the corresponding differences of inputs to obtain useful information. For an S-box S, the differential approximation probability DAP(S) [67] measures the strength of S to thwart the differential attackers. The mathematical representation of DAP is given by:
where , and “⊕” stands for the bit-wise addition in . Thus, the S-box S possesses higher security if the DAP(S) is close to . The DAP value of the S-box depicted in Table 1 is . From Table 2, it is also evident that the DAP value of the proposed S-box is equal to the DAP values of the S-boxes displayed in [12,65,66], and comparable to the DAP of the S-boxes in [8,37,48,51,58,62,63,64]. Thus, the strength of the presented S-box against differential attacks is comparable to strength of the S-boxes in [8,12,37,48,51,58,62,63,64,65,66].
3.1.3. Analysis of Boolean Functions
The Boolean functions of an S-box are used to create confusion/diffusion in a cryptosystem. Two approaches, strict avalanche criterion (SAC) [68] and bit independence criterion (BIC) [68], are used to analyze the Boolean functions. The SAC calculates the change that occurred in the output bits due to the inversion of one bit in a set of input bits. The BIC determines the dependence level of a pair of output bits on inverting an input bit. For an S-box S, two matrices, and , compute the SAC(S) and the BIC(S), respectively:
where represents the number of non-zero symbols in y, with , and denotes the i-th Boolean function of the S-box S. An S-box creates enough confusion/diffusion if all off-diagonal entries of and are close to . The minimum (SAC (min)) and maximum (SAC (max)) of the off-diagonal values of for the S displayed in Table 1 are and , respectively. Furthermore, it follows from Table 2 that the SAC (min) value of the designed S-box is greater than the SAC (min) values of the S-boxes designed in [8,37,58], and that the SAC (max) value of the new S-box is less than or equal to that of the S-boxes in [8,12,37,58]. So, the confusion-creation capability of the S-box in Table 1 is greater than that of the S-boxes in [8,37,58]. The SAC (min) value of the presented S-box is equal to the SAC (min) values of the S-boxes in [12,62,65], and the SAC (max) value is less than that of the S-boxes in [12,62,65]. This reveals that the proposed scheme generates S-boxes with higher confusion than the schemes in [12,62,65]. The SAC values indicate that the confusion-creation capability of the new S-box is equal to the S-box in [51] and comparable to that of [48,66]. Now, the minimum (BIC (min)) and maximum (BIC (max)) of the off-diagonal values of for S in Table 1 are and , respectively. Table 2 reveals that the BIC (min) of the proposed S-box is comparable with that of the S-boxes in [8,12,37,48,51,58,62,63,64,65,66], and the BIC (max) value of the current S-box is less than that of the S-boxes in [8,12,48,51,64,65,66]. Thus, the proposed scheme generates S-boxes with diffusion-creation capabilities comparable to the S-boxes in [8,12,37,48,51,58,62,63,64,65,66].
4. The Proposed Encryption Scheme
Suppose we want to encrypt an image I of size over the symbol set , and represents the pixel lying at the intersection of the i-th row and the j-th column. Furthermore, let denote the sum of all pixel values of I. Then, the proposed encryption scheme consists of the following steps.
4.1. Generation of Keys
To encrypt an image of size , we need to generate an EC , over a ring , for . For the sake of convenience, we take and , so that we choose primes and integers to generate . Thus, and t are chosen in such a way that there exists at least points , where y is attaining each value in the interval . This condition is imposed to ensure the generation of an S-box using points of the EC . We further choose an integer value as a key. The use of the key is explained in Section 4.4(i). The parameters , and are all secret keys.
4.2. Masking Phase
Before masking an image I, we first arrange the points of the EC according to the ordering . After ordering, we assume that stands for the i-th point of the EC . The reason for this is that the diffuses the y-coordinates of the points lying on an EC, because, over a ring of integers , if , then, for such an x, there are at least two values of y in , such that . The masking phase of an image I takes place as follows:
- (i)
- Generate a row matrix M from of length such that, for , we have:The purpose of constructing matrix M is to design a sequence from both coordinates of . The elements of the said sequence are used to hide the pixel values of an image I;
- (ii)
- Choose a submatrix N, which consists of the first entries of the matrix M because only the values are needed to hide the pixel values. The chosen n should not be less than ; otherwise, in Section 4.3(i), the construction of with size will not be possible;
- (iii)
- The sensitivity to the plain image is necessary for a secure cryptosystem. For this purpose, transform the entries of N by the pixel value to obtain the matrix B, given by:There is no restrictions on pixel or the number of pixels. Any number of arbitrary pixels may be used for transformation. For the sake of convenience, only one pixel value is fixed;
- (iv)
- For the sake of simplicity, reshape the matrix B to construct a matrix with u rows and v columns. By reshaping B, we mean that B is divided into v blocks such that each block contains u entries and the i-th block represents the i-th column of the matrix B, so that the corresponding values of both B and I are combined to hide the pixel values of the image I;
- (v)
Since there is a one–one correspondence between and , may be mapped onto and , respectively, via the following maps:
These two ECs, and , are used to alter the pixels of an image. The S-box generated on is used to create the confusion in the encrypted image. The steps of the said procedure are explained in the following phase.
4.3. Diffusion Phase
The steps of this phase are explained as follows:
- (i)
- For , construct two row matrices, , due to the all points for both primes , respectively, such that:and:In fact, we want to generate two sequences using ECs and . Both sequences consist of integer values, which are further used to alter the pixel values of the masked image in Section 4.3(v) and to permute the image P in Section 4.4(iii), respectively;
- (ii)
- Take submatrices containing the first entries of , respectively, so as to choose the sequences of length that are equal to that of the number of pixels in the image I;
- (iii)
- Modify the sizes of above constructed matrices, so that has u rows and v columns. The reason for generating such matrices has been explained previously;
- (iv)
- Apply the modulo operator to to generate the matrices , consisting of m-bit integers. Since for encrypting m-bit images, m-bit sequences are needed;
- (v)
- Convert the elements of and into the binary format and generate the image by diffusing the pixels of by the following equation:where ⊕ is a logical operator (XOR operation by binary bit) known as exclusive disjunction.
4.4. Confusion Phase
For a secure cryptographic algorithm, it is necessary to have a desired level of confusion. For the current cryptosystem, the confusion phase consists of the following steps:
- (i)
- Choose a secret key to construct a shifting parameter , such that ; then, give a circular shift to the S-box to design a new S-box . The shifting parameter, the secret key , and are linked in order to enhance the sensitivity to the plain image I;
- (ii)
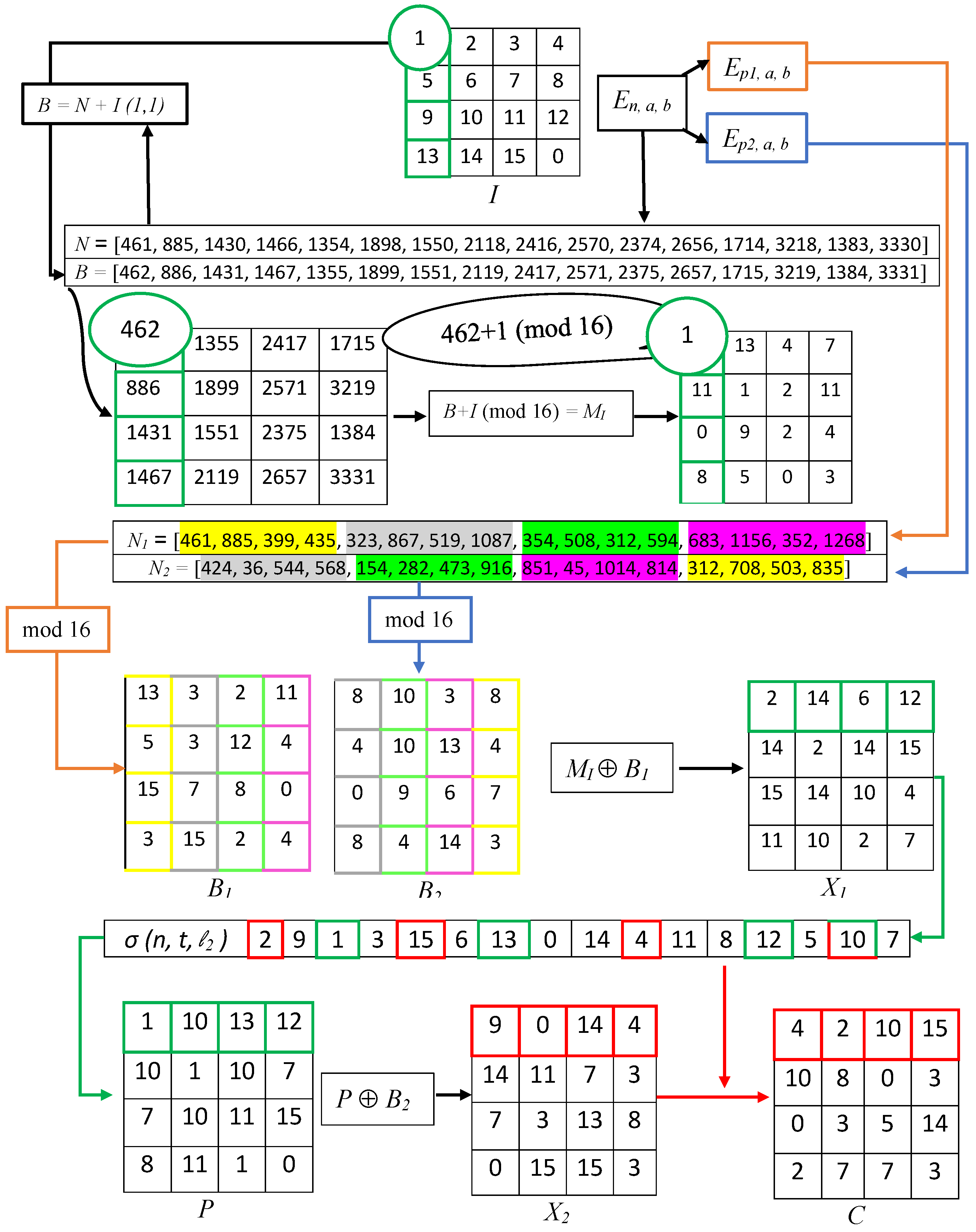
- Permute the pixels of the image using the S-box as follows:In the coming encryption of a hypothetical image, the first entry of is 2. Then, represents the third entry of the S-box , which is 1. That is, stands for the -th element of the S-box ;
- (iii)
- In order to obtain the scrambled image , repeat Section 4.3(v) using P in place of , and replacing with , such that:
- (iv)
- Finally, to obtain the encrypted image C with the desired level of confusion, permute the image as follows:
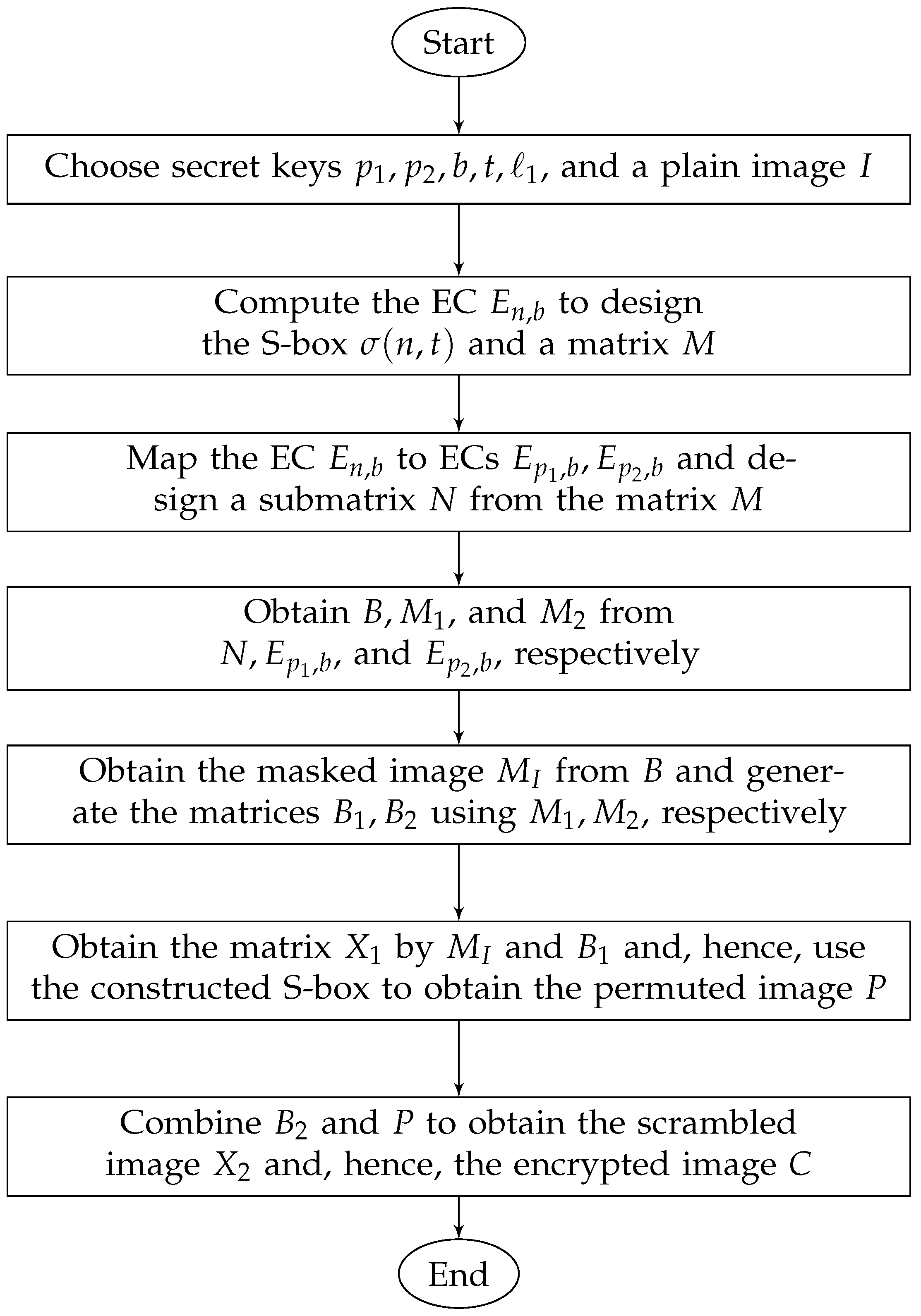
The flowchart of the proposed encryption scheme is shown in Figure 1.
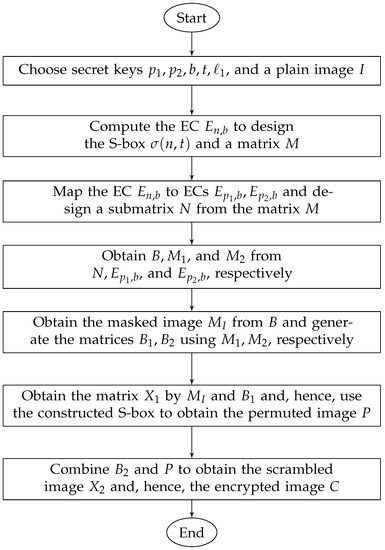
Figure 1.
Flowchart of the encryption scheme.
We theoretically derive the time complexity of the proposed scheme in Theorem 1.
Theorem 1.
Let I be a plain image of size , and let be a positive integer; then, the time complexity of the proposed scheme is , where is an integer such that is computed for all and .
Proof.
In the key generation phase (Section 4.1), to compute all , we need to check for each , t values of , such that . Thus, the computation of takes time. Further, the ordering of the points of the EC needs time. In Section 4.2(i), we can see that ; therefore, M can be constructed in time. As , we can design by a for loop, executing times. Furthermore, B can be reshaped by two nested loops, such that one loop executes u times, while the other executes v times. In a similar way, we can add two matrices of the same order by two nested loops. Thus, the time complexity of Section 4.2(ii)–(v) is . From the chosen keys, we have and , so that the complexity of the masking phase is
Now, we can map the EC on the ECs in time. In the diffusion phase (Section 4.3(i)), and for . Therefore, Section 4.3(i)–(v) takes and time, respectively.
In the confusion phase (Section 4.4(i)), the time required to compute is and can be computed in constant time. Since has entries, we can implement Section 4.4(ii)–(iv) in time, using two nested loops executing u and v times, respectively.
Clearly, and ; thus, the above discussion implies that the time complexity for the presented scheme is . □
As the time complexity is dependent on the parameter t, that is, the time is controllable with t, the current scheme is effective, particularly when a large dataset of images is to be encrypted.
The whole process is illustrated by the encryption of a 4-bit hypothetical image, as shown in Figure 2.
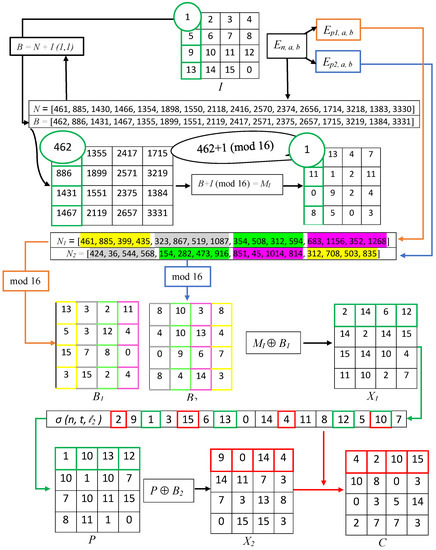
Figure 2.
Encryption of a image by the proposed scheme.
5. Decryption
6. Security Analysis
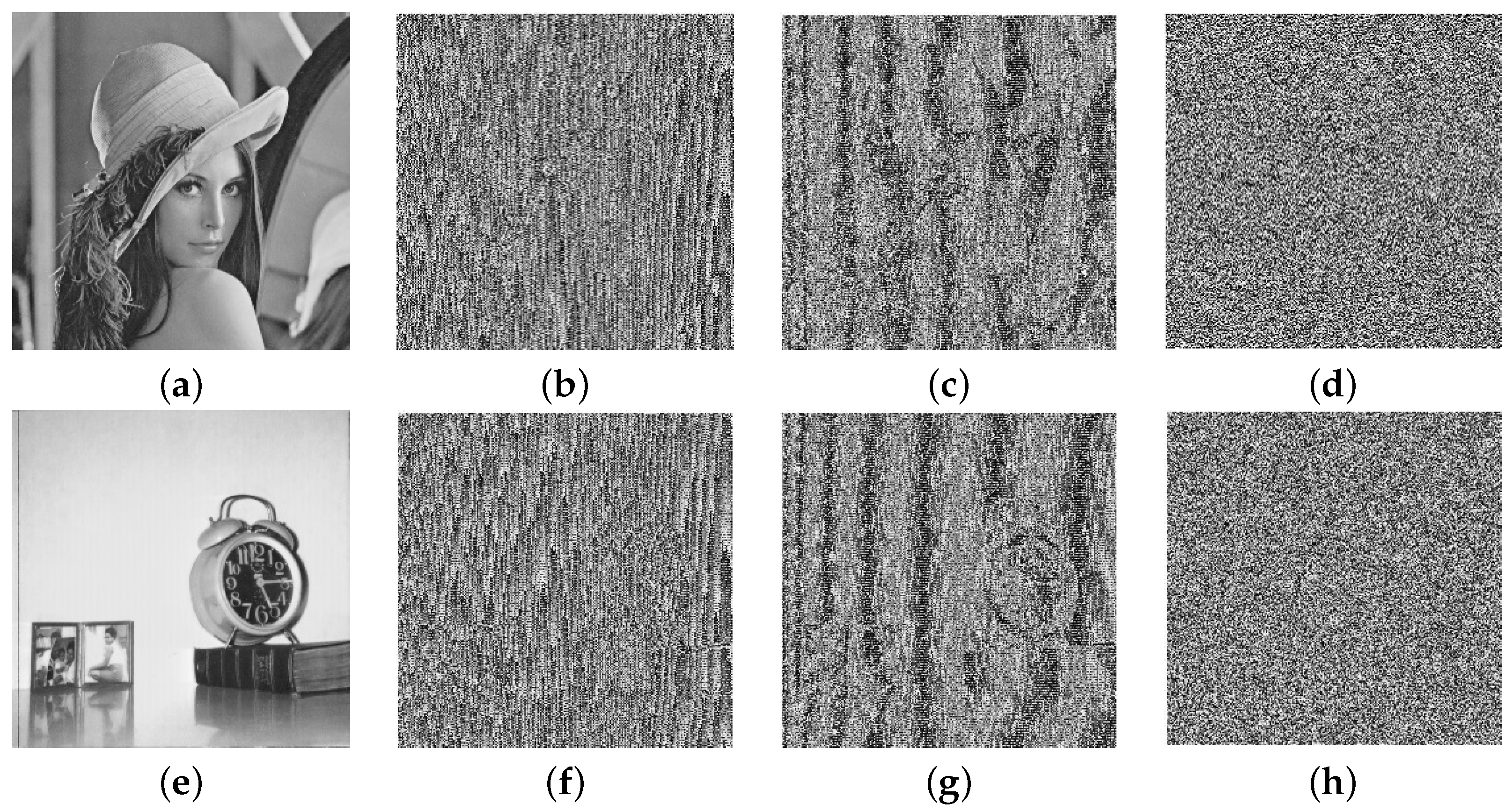
In this section, some well-known metrics are described, which are generally used to measure the security level of new algorithms. The security of the proposed encryption scheme is evaluated by performing experiments on all-gray images of different sizes, taken from the USC-SIPI database [69]. The database consists of square images of size , The plain images of Lena and Clock, along with their encrypted images, are shown in Figure 3. The experiments are performed by taking the parameters and , using MATLAB 2016a on a personnel machine equipped with a GHz processor, 6 GB RAM, and Windows 10 operating system. The security strength of the encryption algorithm is analyzed in the following subsections.
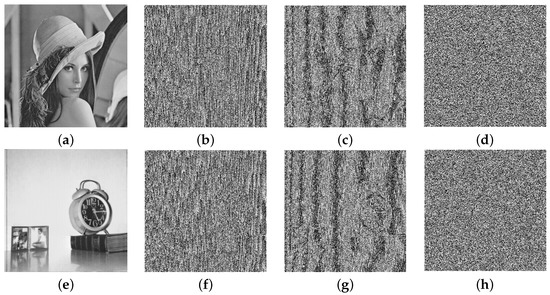
Figure 3.
(a,e) Plain images; (b,f) masked images; (c,g) diffused images; (d,h) encrypted images of Lena and Clock, respectively.
6.1. Differential Attacks Analysis
The cryptographic strength of an encryption scheme against differential attacks is analyzed by two measures: the number of pixels’ change rate (NPCR) and the unified average changing intensity (UACI). In an encryption algorithm, the change of one pixel of a plain image has an influence on the encrypted image. The NPCR is a criterion used to measure the influence of a change in a plain image on the ciphers. The UACI criterion measures the average intensity difference between two different images. If I and are any two plain images of the same dimension , and and are the respective cipher images of I and , then NPCR and UACI are calculated by Equations (14) and (15), as given by:
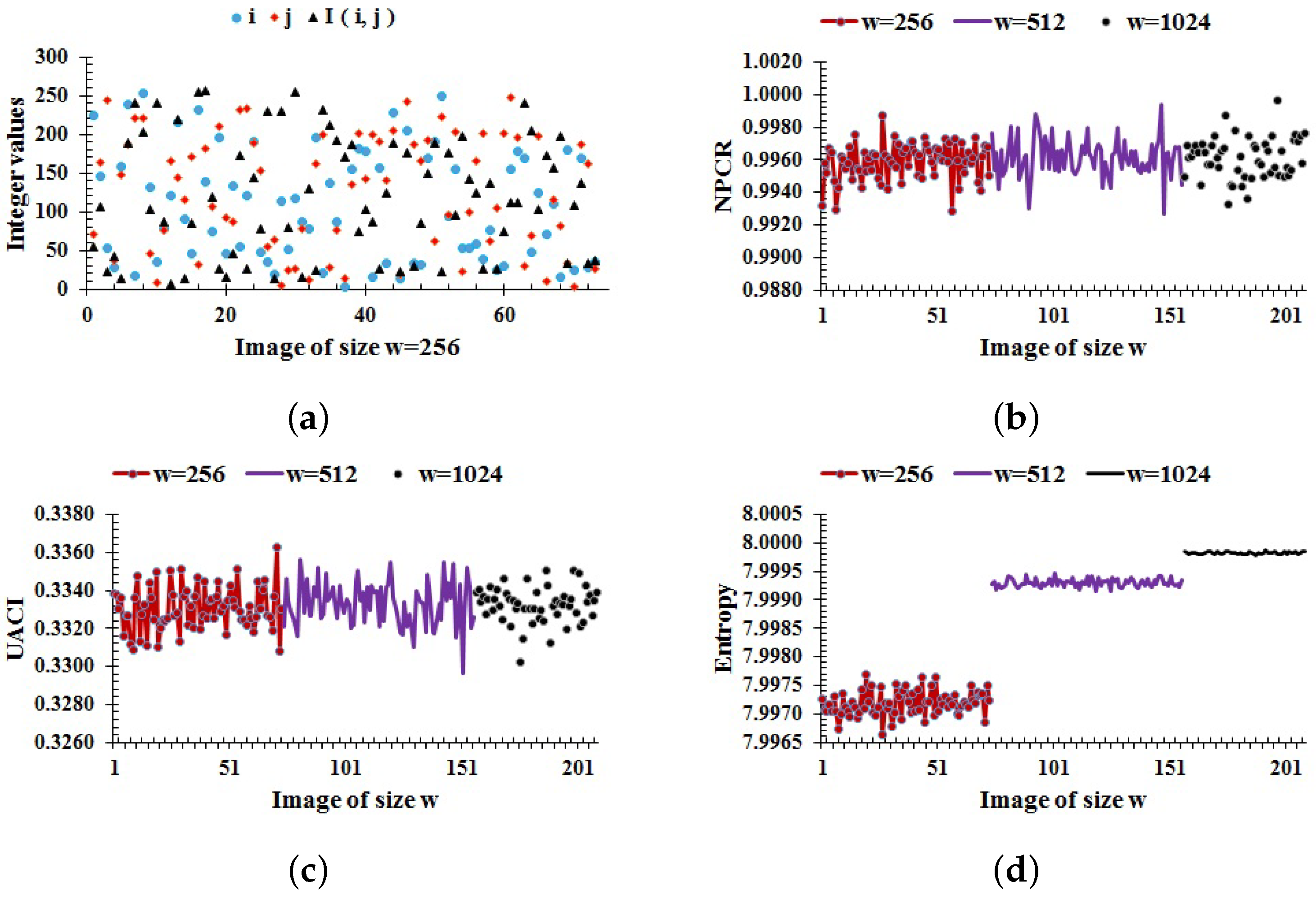
where if , and otherwise. For 8-bit images with , the theoretical values of NPCR are , respectively. Unlike NPCR, the expected ranges of UACI are , , , and , respectively [18]. We randomly choose i and j, and a random value is assigned to the pixel for each image I of the database. The random values of and for images of size are shown in Figure 4a. Then, the NPCR and UACI results for the current scheme are computed for each image of the database for a randomly chosen pixel value ; the graphical results are shown in Figure 4b,c, where the average values of NPCR and UACI are and , respectively, which are close enough to the expected values.
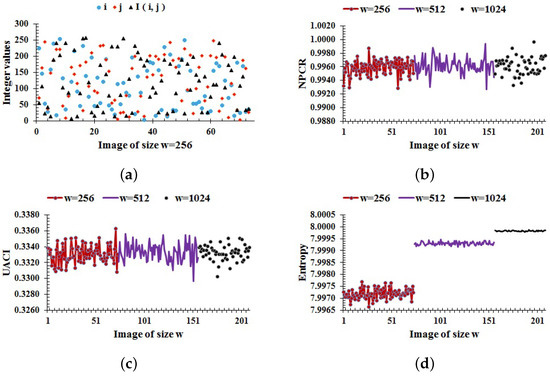
Figure 4.
(a) Random values of and ; (b–d) NPCR, UACI, and entropy results, respectively, for the whole image database.
Moreover, we randomly changed one pixel value of some images, and compared the results of the NPCR and UACI tests with the results of the recent schemes in [14,15,16,17,18,28,51,57,70,71], as shown in Table 3 and Table 4, respectively. The pass ratio for the proposed scheme in Table 3 is higher than that of the schemes in [14,15,17,28,51], and equal to that of the schemes in [16,18,57,70,71]. Similarly, the pass ratio for the proposed scheme in Table 4 is higher than that of the schemes in [15,16,17,51,57,70] and equal to that of the schemes in [14,18,28,71]. It follows that the proposed scheme has better performance against differential attacks than the schemes in [14,15,16,17,28,51,57], and has comparable performance to the schemes in [18,71].

Table 3.
Comparison of NPCR results due to the proposed algorithm and some other schemes, where the bold value shows that the corresponding image passed the test.

Table 4.
Comparison of UACI results due to the proposed algorithm and some other schemes, where the bold value shows that the corresponding image passed the test.
6.2. Information Entropy
Information entropy is used to measure disorder in an image. Equation (16) is used to determine the randomness of an image I:
where represents the probability of a pixel value , and k is the total number of gray values in an image I. For an 8-bit encrypted image, the ideal value of entropy is 8, which corresponds to the highest level of uncertainity. Thus, for a cryptographically strong encryption scheme, the value of should be close to 8. The entropy results for the current scheme are computed for each image of the database as shown in Figure 4d. The entropy for images of size are lying in the ranges [], [], and [], respectively. In all cases, the entropy approaches the optimal value. Consequently, the proposed encryption scheme is capable of providing high randomness in a cipher.
The comparison of the entropy results is carried out in Table 5. It is clear from Table 5 that the information entropy for the presented scheme is higher than that of [15,16,17,19,20,28,46,51,57] and comparable to that of the schemes in [14,18,41,72]. Thus, our scheme generates encrypted images having more randomness than the techniques in [15,16,17,19,20,28,46,51,57.

Table 5.
Comparison of entropy results due to the proposed algorithm and some other schemes.
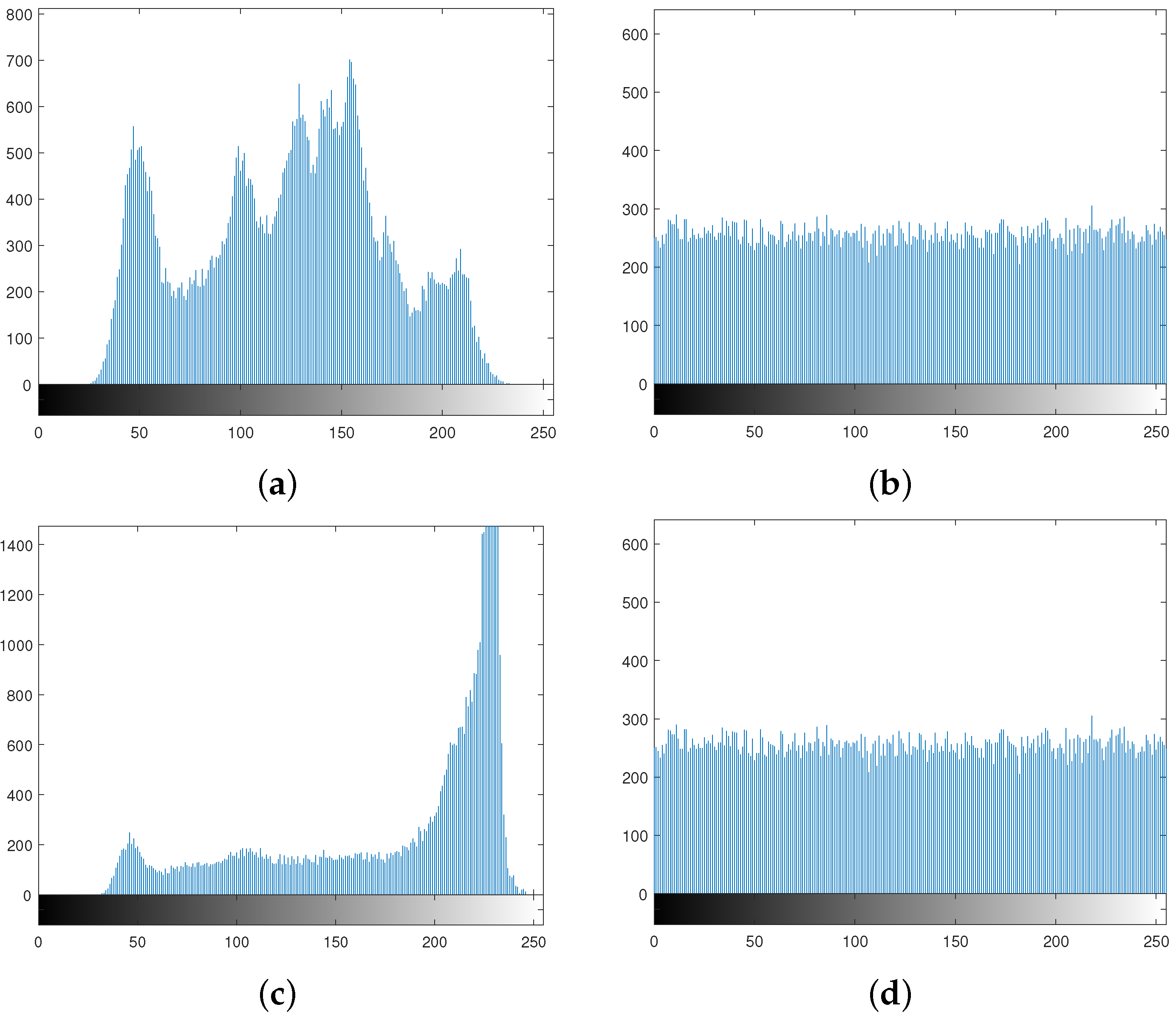
6.3. Histogram
A histogram of an image represents the frequency distribution of the gray values. If each pixel value occurs with almost equal frequency in an image, then the histogram of that image is said to be uniform. The histogram of an ordinary image is always highly nonuniform, while a properly encrypted image has a uniform histogram. Figure 5a,c depicts the histograms of the plain images in Figure 3a,e, repectively, and Figure 5b,d shows the histograms of the cipher images in Figure 3d,h, respectively.
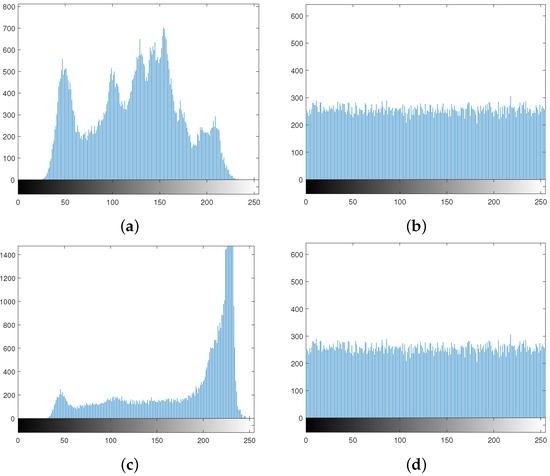
It is evident from the histograms that the proposed scheme encrypts an image in such a way that it does not reveal any secret information of the former.
6.4. Correlation
A pixel of an ordinary image has high correlation with adjacent pixels. A good encryption scheme breaks the correlation among the pixels of an encrypted image. The correlation coefficient between datasets x and y of the same size M is determined by:
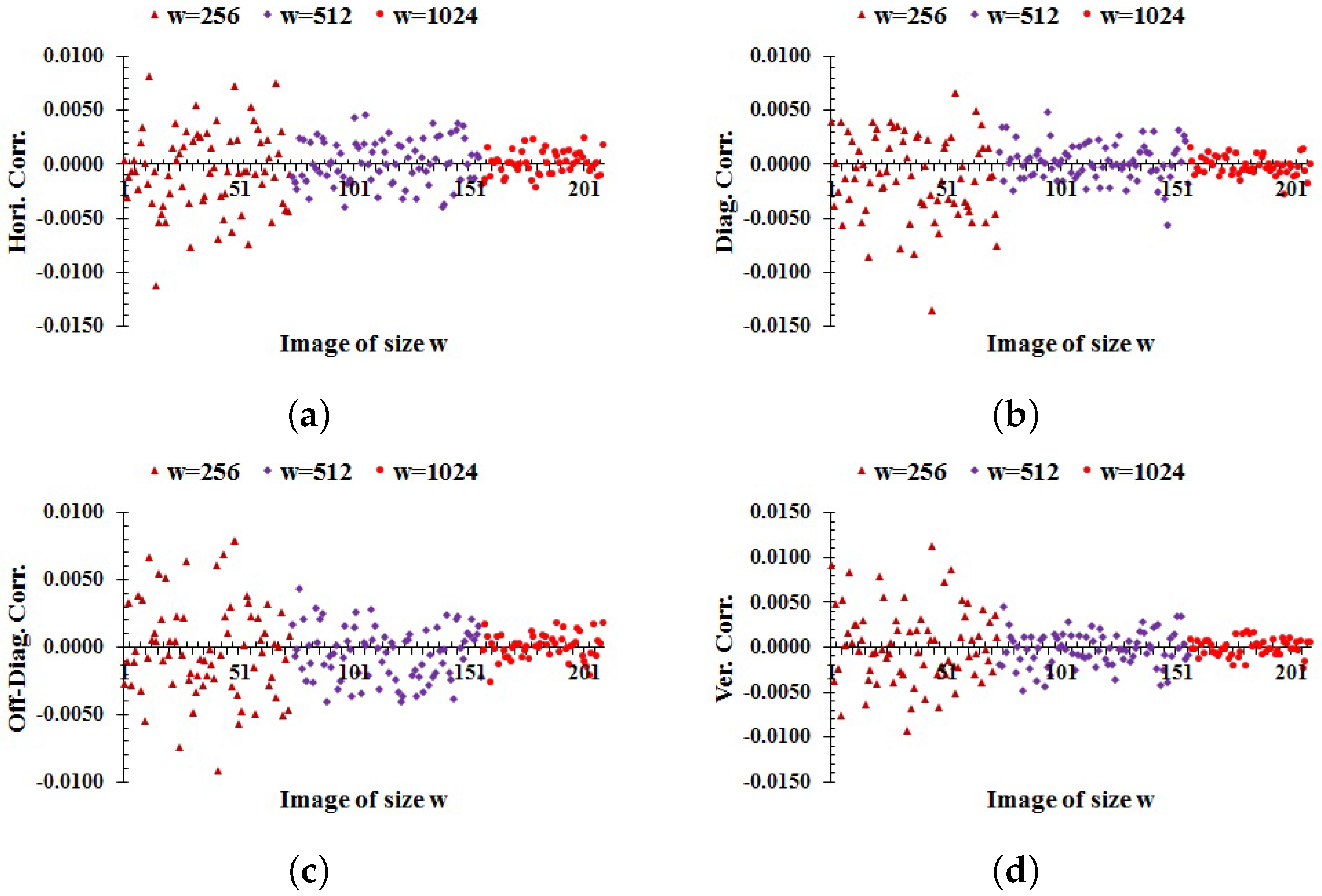
where and and . The horizontal, diagonal, off-diagonal, and vertical correlation coefficients among the pixels of each image in the database encrypted by the proposed scheme are computed as shown in Figure 6. The average values of correlation in Figure 6a–d are , and , respectively. From these results, it follows that the proposed scheme makes the correlation close to zero in all directions. So, the proposed method is capable of disrupting the correlation of pixels in ciphers.
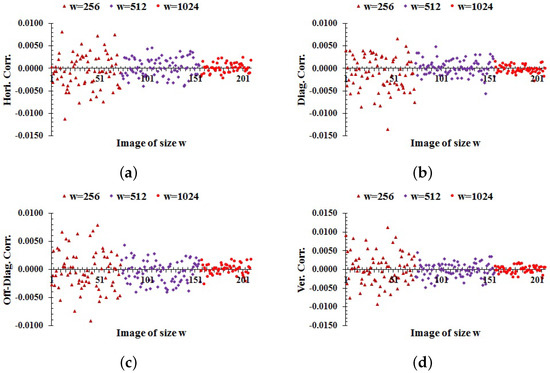
Figure 6.
Correlation among the adjacent pixels of each encrypted image in the databases: (a) horizontal; (b) diagonal; (c) off-diagonal; (d) vertical correlation.
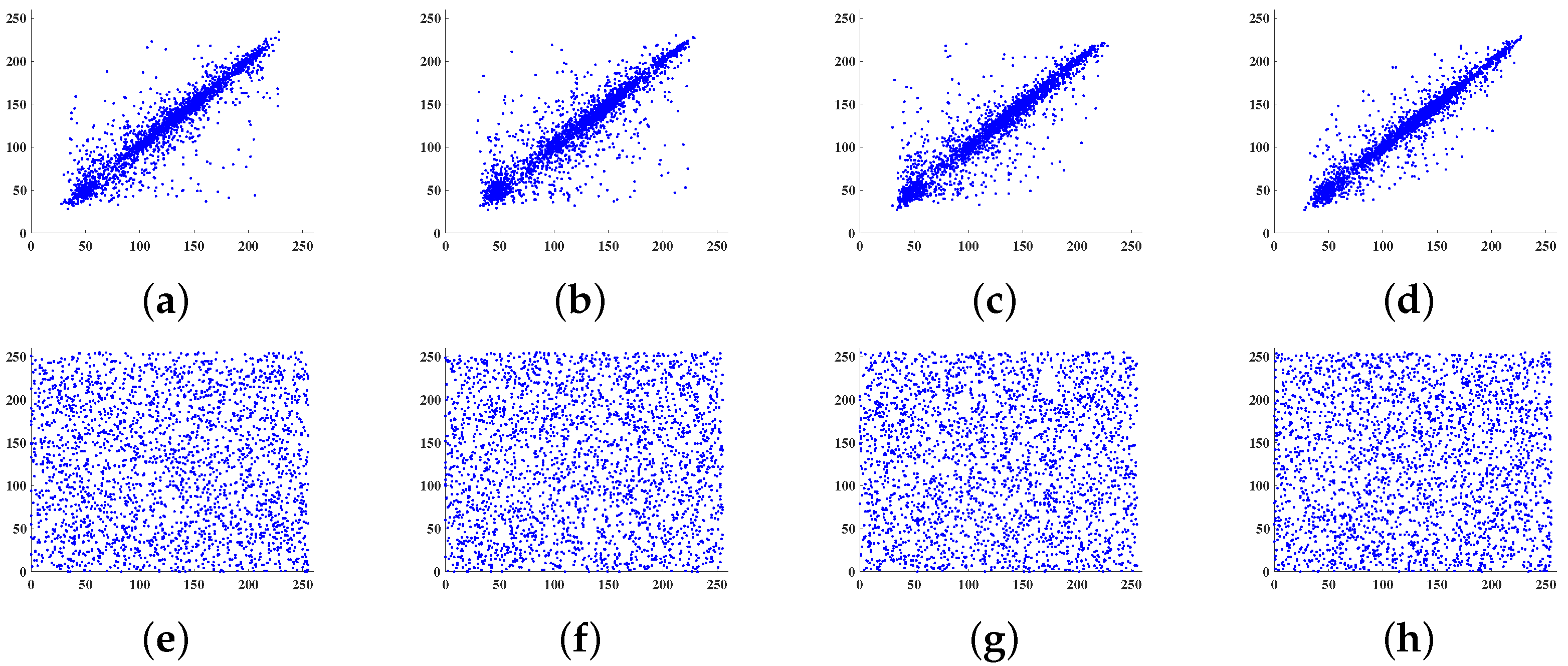
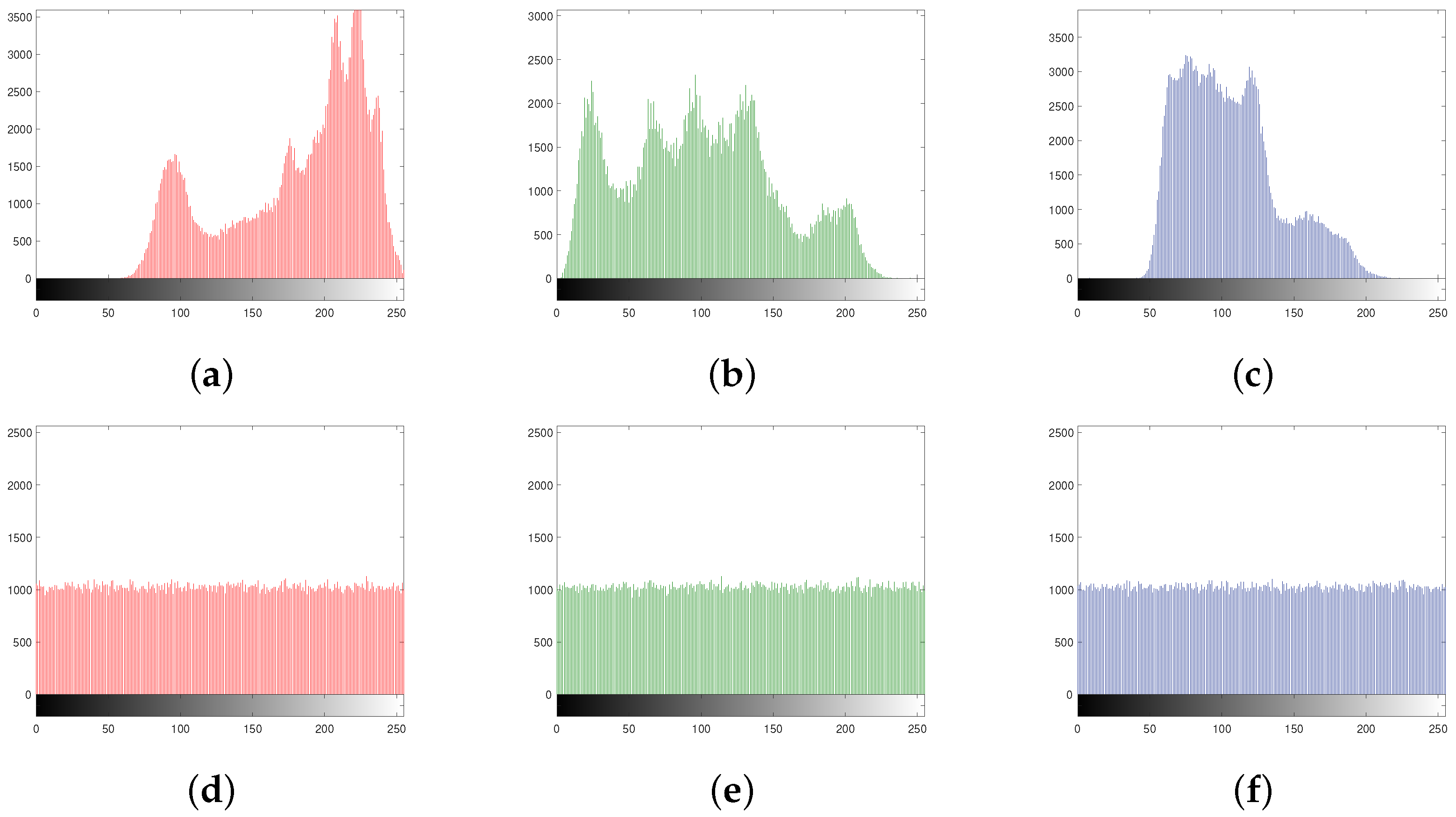
In addition, a random sample of 2560 pairs of pixels is selected along the horizontal, diagonal, off-diagonal, and vertical directions from both the plain image and the cipher image of Lena. The correlation distribution between the adjacent gray values before and after encryption is shown in Figure 7.
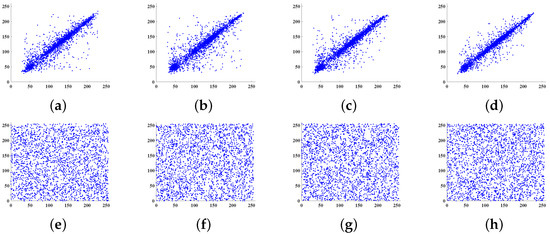
Figure 7.
Correlation distribution of adjacent pixels of plain image along the (a) horizontal, (b) diagonal, (c) off-diagonal, and (d) vertical directions, respectively; correlation distribution of adjacent pixels of cipher image along the (e) horizontal, (f) diagonal, (g) off-diagonal, and (h) vertical directions, respectively.
It follows From Figure 7a–d that adjacent pixels of the plain image are in high correlation, but Figure 7e–h indicates that the proposed scheme successfully weakens the correlation of the pixels.
The correlation results for encrypted image of Lena and Barbara are compared with other schemes in Table 6. It can be observed that the results for the Lena image of the current scheme are better than all the compared schemes. Similarly, the results for the Barbara image encrypted by the proposed scheme are better than that of the schemes in [19,41,51,72], and comparable to the results of [16,57]. Thus, our scheme generates encrypted images with more randomness than the other techniques listed in Table 6.

Table 6.
Comparison of correlation results along all the three directions for the Lena and Barbara images, due to the proposed algorithm and some other schemes.
6.5. Key Space
Key space is a set consisting of the all possible secret keys for a cryptosystem. Generally, for a good cryptosystem, the size of a key space should be at least The five keys , and are introduced by the proposed scheme. The least number of bits to store a key required by the proposed algorithm is 29. Thus, the size of our key space is , which is much larger than . Hence, the described scheme has the capability to resist brute-force attacks in an efficient way.
6.6. Key Sensitivity
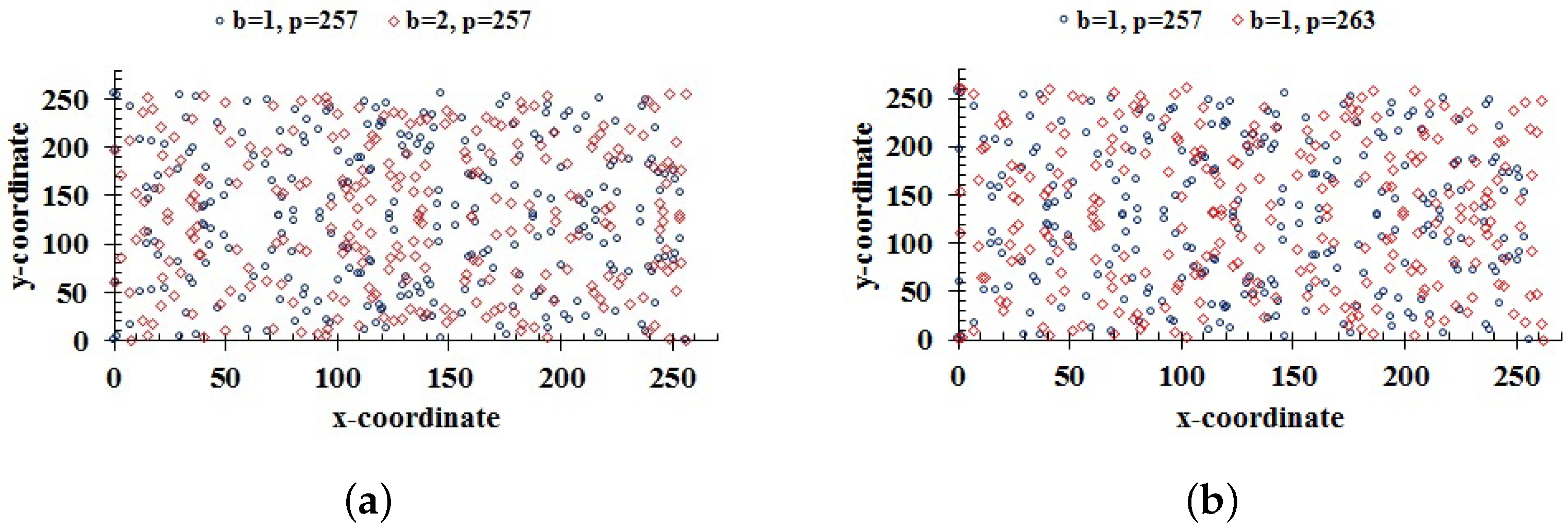
This is an important feature of a cryptographically strong cryptosystem. Key sensitivity is also necessary to resist brute-force attacks. If a small change in a key leads to a significant change in the cipher, then the cryptosystem is said to be sensitive to the keys. For this purpose, we decrypted the Lena image by changing a single key; the results are shown in Figure 8b–d.
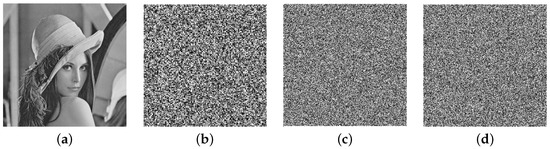
Figure 8.
Decrypted image with (a) actual keys; (b) ; (c) b = 8; (d) .
Moreover, slightly changing the keys b and p change the coordinates of the ECs , and ; these are shown in Figure 9a,b, respectively.
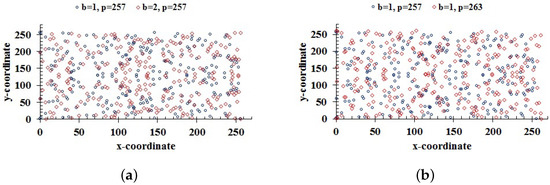
Figure 9.
(a) Two ECs generated for a small change in the key b; (b) points of ECs for two different primes.
6.7. Plain-Text Attacks
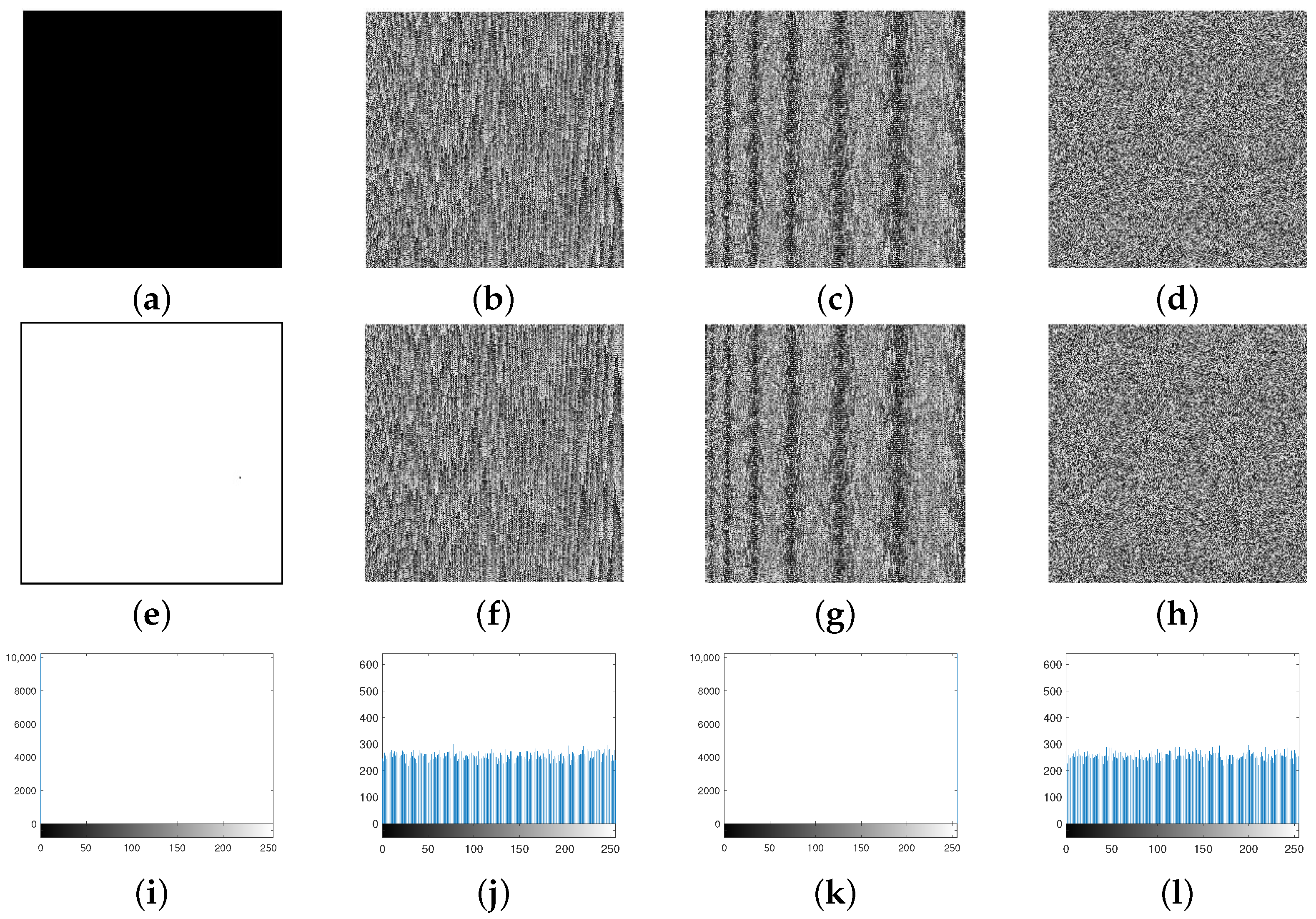
There are two types of plain-text attacks, i.e., known plain-text attacks and chosen plain-text attacks. In known plain-text attacks, the attacker knows about a string of the plain text, along with the relevant string of the cipher text. In chosen plain-text attacks, the adversary has a partial access to the encryption scheme. That is, the adversary can obtain the ciphered string for a chosen plain-text string. For this purpose, attackers use all-black or all-white images to obtain information about the encryption scheme [50], so that a secure encryption scheme encrypts all-black and all-white images with optimal results. The efficiency of the current scheme is visible from Table 7 and Figure 10.

Table 7.
Analysis of the proposed encryption technique against plain-text attacks.
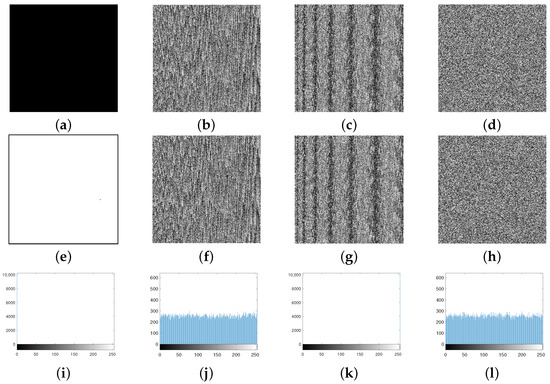
Figure 10.
(a,e) Plain images; (b,f) masked images; (c,g) diffused images; (d,h) encrypted images of all-black and all-white images, respectively; (i,k) histograms of (a,e), respectively; (j,l) histograms of (d,h), respectively.
Table 7 and Figure 10 indicate that the current scheme not only randomizes the all-white and all-black images, but also weakens the pixels’ correlation and makes the pixels’ distribution uniform in the encrypted images. Thus, the proposed scheme is highly secure against both kinds of plain-text attacks.
7. An Application to Encryption of Color Images
In this section, we apply the proposed scheme to the color images. We encrypted images of Female, Lena, and San Francisco using the parameters , and , where I stands for the R (Red), G (Green), and B (Blue) components of an image, respectively. The plain and encrypted images of Female, Lena, and San Francisco are shown in Figure 11.

Figure 11.
(a–c) Plain images; (d–f) encrypted images of Female, Lena, and San Francisco, respectively.
The NPCR and UACI results are computed by randomly changing a pixel value in each channel. It can be observed from Table 8 that the NPCR and UACI results of each channel for the tested color images lie in the expected range. Similarly, the entropy results of the R, G, and B components also belong to the expected ranges for each of the color images.

Table 8.
The NPCR, UACI and entropy results of the encrypted color images.
The experimental results of the color Lena are compared with the results of the schemes in [7,28,29,73,74,75,76,77,78], as shown in Table 9 and Table 10.

Table 9.
Comparison of NPCR and UACI results for the color image of Lena.

Table 10.
Comparison of the Entropy results for the color image of Lena.
The results in Table 9 reveal that the NPCR values for the R, G, and B components of Lena are greater than the theoretical value (). Apart from this, the R component’s NPCR value is greater than the values of the schemes in [29,75], equal to that of [7,77], and comparable with [28,74,76]. The NPCR value of the G plane is greater than all the NPCR results of to the schemes in [7,28,29,73,74,75,76,77]. Similarly, the NPCR results of the B component is better than the results of [7,28,29,74,75,76,77,78]. In addition, the average NPCR value resulting from the current scheme is greater than the NPCR results of all the listed schemes in Table 9. The UACI results of the R, G, and B components of the current scheme lie in the expected range. Furthermore, the UACI results of the new scheme for all the three components are better than the results of the schemes in [7,73,75,78] and comparable to that of the schemes in [28,29,74,76,77]. It follows that the proposed scheme is better in performance against the differential attacks than the schemes in [7,28,70,73,74,75,76,77,78].
Table 10 reveals that the entropy value of the R component is greater than that in [74,75,77] and equal to the values of [76,78]. The entropy value of the G component is also greater than that in [74,75,77] and equal to the value of [29]. Similarly, the entropy result of the B component is greater than the results of [28,29,43,73,74,75,77,78] and equal to that of [7,76]. In addition, the average entropy value resulting from the current scheme is better than that of the schemes in [73,74,75,77] and equal to that of the results of [28,29,43,76,78]. This discussion indicates that the current scheme generates encrypted color images with higher randomness than the schemes in [74,75,77], and the randomness of the encrypted images in current scheme and the schemes in [29,78] is comparable.
The histograms of the channels of the plain Lena and the encrypted Lena are shown in Figure 12a–f, respectively.
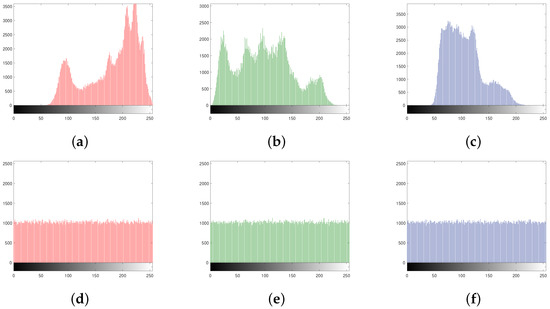
Figure 12.
(a–c) Histogram of the plain R, G, and B channels of the color Lena, respectively; (d–f) histogram of the encrypted R, G, and B channels of the color Lena, respectively.
Figure 12 confirms that the histograms of the encrypted channels are uniform and, hence, the presented scheme encrypts color images having high resistance against the statistical attacks.
In Table 11, the correlation of the adjacent pixels of three different encrypted images with different sizes is shown. It is evident that the proposed scheme encrypts any image in such a way that it weakens the correlation between two adjacent pixels of any channel.

Table 11.
Correlation coefficients of two adjacent pixels in encrypted color images.
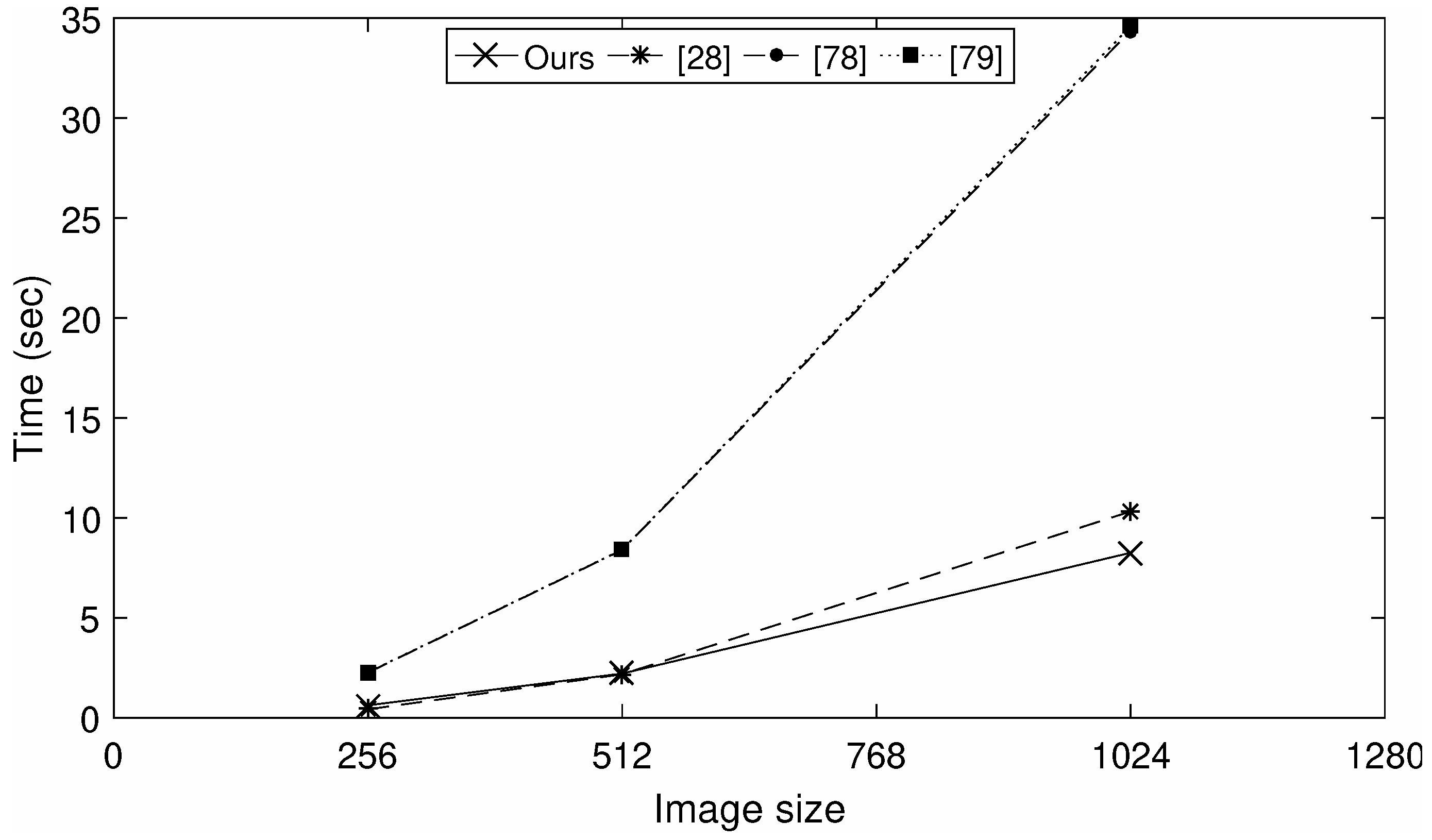
Along with other properties, a good encryption scheme should be highly efficient. Different color images with different sizes are encrypted using the current scheme. To demonstrate the efficiency of the current scheme, the encryption times (sec) for the said three images are computed, since we use a pre-computed EC over the ring of integers as an input for all input images. While computing the encryption time, the time taken by the inputs is not taken under the consideration. The encryption time of the current scheme is compared with the time of some recent schemes [28,78,79], as shown in Figure 13. The results for the schemes in [28,78,79] are available in Table 3 of [80].
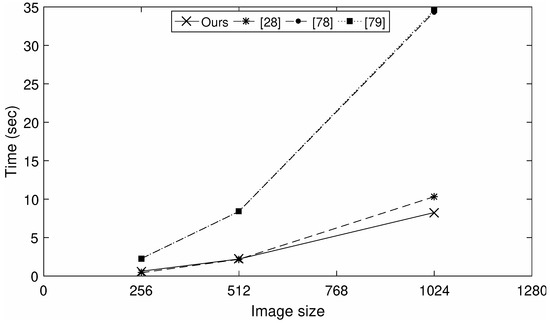
Figure 13.
Encryption time for color images according to different encryption schemes.
For images of size w = 256,512, the performance of our scheme is comparable with that of [28], and for , the new scheme is highly efficient, compared to the scheme of [28]. Similarly, in Figure 13, the plots of [78,79] are overlapping, but our scheme is more efficient than [78,79] for images of all sizes.
Thus, the presented scheme is capable of efficiently encrypting color images as well, and can be used for the good encryption of color images.
8. Conclusions
We proposed a new S-box generator and an image encryption algorithm. We employed an EC over a ring of integers instead of a finite field. The presented S-box is highly resistive against linear attacks when compared to the S-boxes generated by the ECs over finite fields in [37,51,58] and the S-boxes of [62,63,64,65,66]. The confusion-creation capability of the proposed S-box is higher than that of the S-boxes in [8,37,58].
Furthermore, our encryption scheme has better performance against differential attacks than that of the EC-based schemes [51,57] and the schemes in [14,15,16,17,28], and provides encrypted images with higher randomness than the schemes in [15,16,17,19,20,28,51,57]. The current scheme is also used for different color images. The presented scheme is able to encrypt color images with low run-times and higher security when compared with [78,79], while the scheme in [51] discusses the novelty regarding only gray images. Furthermore, for relatively large images, the run-time of the current scheme is very low, compared to the schemes in [28,78,79]. The future directions consist of the following works:
(i) To improve the current scheme for the simultaneous encryption of all channels of a color image; (ii) To optimize the current scheme for a text-encryption algorithm; (iii) To generate random numbers based on ECs over rings and employ the sequence of random numbers in text encryption; (iv) To generate random binary sequences using ECs over a ring of integers and experimentally prove their cryptographic strength.
Author Contributions
Conceptualization, U.H. and N.A.A.; Funding acquisition, N.A.A. and S.A.; Methodology, U.H., I.U., N.A.A. and S.A.; Software, U.H., I.U., N.A.A. and S.A.; Supervision, U.H. and N.A.A.; Writing—original draft, I.U. and S.A.; Writing—review & editing, U.H. and N.A.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research is funded by the HEC project NRPU-7433 and the QAU project URF-2015.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| ECs | Elliptic curves |
| S-box | Substitution box |
References
- Ibrahim, S.; Alharbi, A. Efficient image encryption scheme using Henon map, dynamic S-boxes and elliptic curve cryptography. IEEE Access 2020, 8, 194289–194302. [Google Scholar] [CrossRef]
- Murphy, S.; Robshaw, M.J. Essential algebraic structure within the AES. In Proceedings of the 22nd Annual International Cryptology Conference on Advances in Cryptology, Berlin/Heidelberg, Germany, 18–22 August 2002; pp. 1–16. [Google Scholar]
- Rosenthal, J. A polynomial description of the Rijndael Advanced Encryption Standard. J. Algebra Its Appl. 2003, 2, 223–236. [Google Scholar] [CrossRef] [Green Version]
- Cui, L.; Cao, Y. A new S-box structure named Affine-Power-Affine. Int. J. Innov. Comput. Inf. Control 2007, 3, 751–759. [Google Scholar]
- Liu, J.; Wei, B.; Cheng, X.; Wang, X. An AES S-box to increase complexity and cryptographic analysis. In Proceedings of the 19th International Conference on Advanced Information Networking and Applications (AINA’05) Volume 1 (AINA Papers), Taipei, Taiwan, 25–30 March 2005; Volume 1, pp. 724–728. [Google Scholar]
- Tran, M.T.; Bui, D.K.; Duong, A.D. Gray S-box for advanced encryption standard. In Proceedings of the 2008 International Conference on Computational Intelligence and Security, Suzhou, China, 13–17 December 2008; Volume 1, pp. 253–258. [Google Scholar]
- Silva-Garcia, V.M.; Flores-Carapia, R.; González-Ramírez, M.D.; Vega-Alvarado, E.; Villarreal-Cervantes, M.G. Cryptosystem Based on the Elliptic Curve With a High Degree of Resistance to Damage on the Encrypted Images. IEEE Access 2020, 8, 218777–218792. [Google Scholar] [CrossRef]
- Özkaynak, F. Construction of robust substitution boxes based on chaotic systems. Neural Comput. Appl. 2019, 31, 3317–3326. [Google Scholar] [CrossRef]
- Miller, V.S. Use of elliptic curves in cryptography. In Proceedings of the Conference on the Theory and Application of Cryptographic Technique, Linz, Austria, 9–11 April 1985; pp. 417–426. [Google Scholar]
- Cheon, J.H.; Chee, S.; Park, C. S-boxes with controllable nonlinearity. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; pp. 286–294. [Google Scholar]
- Hayat, U.; Azam, N.A.; Asif, M. A method of generating 8 × 8 substitution boxes based on elliptic curves. Wirel. Pers. Commun. 2018, 101, 439–451. [Google Scholar] [CrossRef]
- Hayat, U.; Azam, N.A.; Gallegos-Ruiz, H.R.; Naz, S.; Batool, L. A Truly Dynamic Substitution Box Generator for Block Ciphers Based on Elliptic Curves Over Finite Rings. Arab. J. Sci. Eng. 2021, 46, 8887–8899. [Google Scholar] [CrossRef]
- Azam, N.A. A novel fuzzy encryption technique based on multiple right translated AES gray S-boxes and phase embedding. Secur. Commun. Netw. 2017, 2017, 5790189. [Google Scholar] [CrossRef] [Green Version]
- Liu, L.; Miao, S. A new simple one-dimensional chaotic map and its application for image encryption. Multimed. Tools Appl. 2018, 77, 21445–21462. [Google Scholar] [CrossRef]
- Liu, L.; Miao, S.; Hu, H.; Cheng, M. N-phase logistic chaotic sequence and its application for image encryption. IET Signal Process. 2016, 10, 1096–1104. [Google Scholar] [CrossRef]
- Wang, X.; Feng, L.; Li, R.; Zhang, F. A fast image encryption algorithm based on non-adjacent dynamically coupled map lattice model. Nonlinear Dyn. 2019, 95, 2797–2824. [Google Scholar] [CrossRef]
- Tang, J.; Yu, Z.; Liu, L. A delay coupling method to reduce the dynamical degradation of digital chaotic maps and its application for image encryption. Multimed. Tools Appl. 2019, 78, 24765–24788. [Google Scholar] [CrossRef]
- Talhaoui, M.Z.; Wang, X.; Midoun, M.A. Fast image encryption algorithm with high security level using the Bülban chaotic map. J. Real-Time Image Process. 2020, 18, 85–98. [Google Scholar] [CrossRef]
- Ismail, S.M.; Said, L.A.; Radwan, A.G.; Madian, A.H.; Abu-Elyazeed, M.F. Generalized double-humped logistic map-based medical image encryption. J. Adv. Res. 2018, 10, 85–98. [Google Scholar] [CrossRef] [PubMed]
- Wang, M.; Wang, X.; Zhao, T.; Zhang, C.; Xia, Z.; Yao, N. Spatiotemporal Chaos in Improved Cross Coupled Map Lattice and Its Application in a Bit-level Image Encryption Scheme. Inf. Sci. 2020, 544, 1–24. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Huang, H. Cosine-transform-based chaotic system for image encryption. Inf. Sci. 2019, 480, 403–419. [Google Scholar] [CrossRef]
- Lambić, D.; Janković, A.; Ahmad, M. Security analysis of the efficient chaos pseudo-random number generator applied to video encryption. J. Electron. Test. 2018, 34, 709–715. [Google Scholar] [CrossRef]
- Ahmad, M.; Alam, M.Z.; Umayya, Z.; Khan, S.; Ahmad, F. An image encryption approach using particle swarm optimization and chaotic map. Int. J. Inf. Technol. 2018, 10, 247–255. [Google Scholar] [CrossRef]
- Zhang, Y. A new unified image encryption algorithm based on a lifting transformation and chaos. Inf. Sci. 2020, 547, 307–327. [Google Scholar] [CrossRef]
- Zhang, Y. The fast image encryption algorithm based on lifting scheme and chaos. Inf. Sci. 2020, 520, 177–194. [Google Scholar] [CrossRef]
- Tong, X.J.; Wang, Z.; Zhang, M.; Liu, Y.; Xu, H.; Ma, J. An image encryption algorithm based on the perturbed high-dimensional chaotic map. Nonlinear Dyn. 2015, 80, 1493–1508. [Google Scholar] [CrossRef]
- Wang, X.; Zhao, J.; Zhang, Z. A chaotic cryptosystem based on multi-one-dimensional maps. Mod. Phys. Lett. B 2009, 23, 183–189. [Google Scholar] [CrossRef]
- Hua, Z.; Jin, F.; Xu, B.; Huang, H. 2D Logistic-Sine-coupling map for image encryption. Signal Process. 2018, 149, 148–161. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Pun, C.M.; Chen, C.P. 2D Sine Logistic modulation map for image encryption. Inf. Sci. 2015, 297, 80–94. [Google Scholar] [CrossRef]
- Chen, G.; Mao, Y.; Chui, C.K. A symmetric image encryption scheme based on 3D chaotic Cat maps. Chaos Solitons Fractals 2004, 21, 749–761. [Google Scholar] [CrossRef]
- Sui, L.; Duan, K.; Liang, J.; Hei, X. Asymmetric double-image encryption based on cascaded discrete fractional random transform and logistic maps. Opt. Express 2014, 22, 10605–10621. [Google Scholar] [CrossRef] [PubMed]
- Huang, X.l.; Dong, Y.x.; Jiao, K.x.; Ye, G.d. Asymmetric pixel confusion algorithm for images based on RSA and Arnold transform. Front. Inf. Technol. Electron. Eng. 2020, 21, 1783–1794. [Google Scholar] [CrossRef]
- Ye, G.; Jiao, K.; Wu, H.; Pan, C.; Huang, X. An asymmetric image encryption algorithm based on a fractional-order chaotic system and the RSA public-key cryptosystem. Int. J. Bifurc. Chaos 2020, 30, 2050233. [Google Scholar] [CrossRef]
- Wang, X.; Liu, L.; Zhang, Y. A novel chaotic block image encryption algorithm based on dynamic random growth technique. Opt. Lasers Eng. 2015, 66, 10–18. [Google Scholar] [CrossRef]
- Amara, M.; Siad, A. Elliptic curve cryptography and its applications. In Proceedings of the International Workshop on Systems, Signal Processing and Their Applications, WOSSPA, Tipaza, Algeria, 9–11 May 2011; pp. 247–250. [Google Scholar]
- Azam, N.A.; Hayat, U.; Ullah, I. An Injective S-Box Design Scheme over an Ordered Isomorphic Elliptic Curve and Its Characterization. Secur. Commun. Netw. 2018, 2018, 3421725. [Google Scholar] [CrossRef]
- Ullah, I.; Hayat, U.; Bustamante, M.D. Image Encryption Using Elliptic Curves and Rossby/Drift Wave Triads. Entropy 2020, 22, 454. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Sadkhan, S.B.; Hameed, N.F. Proposed Developments of Elliptic Curves Cryptosystem. J. Qadisiyah Pure Sci. 2019, 15, 79–86. [Google Scholar]
- Obaid, Z.K.; Al Saffar, N.F.H. Image Encryption Based on Menezes Vanstone Elliptic Curve Cryptosystem. Solid State Technol. 2020, 63, 5256–5265. [Google Scholar]
- Zhang, X.; Wang, X. Digital image encryption algorithm based on elliptic curve public cryptosystem. IEEE Access 2018, 6, 70025–70034. [Google Scholar] [CrossRef]
- Abdelfatah, R.I. Secure image transmission using chaotic-enhanced elliptic curve cryptography. IEEE Access 2019, 8, 3875–3890. [Google Scholar] [CrossRef]
- Abbas, A.M.; Alharbi, A.A.; Ibrahim, S. A Novel Parallelizable Chaotic Image Encryption Scheme Based on Elliptic Curves. IEEE Access 2021, 9, 54978–54991. [Google Scholar] [CrossRef]
- Díaz, E.A.H.; Meana, H.M.P.; García, V.M.S. Encryption of RGB images by means of a novel cryptosystem using elliptic curves and chaos. IEEE Lat. Am. Trans. 2020, 18, 1407–1415. [Google Scholar] [CrossRef]
- Ali, T.S.; Ali, R. A novel medical image signcryption scheme using TLTS and Henon chaotic map. IEEE Access 2020, 8, 71974–71992. [Google Scholar] [CrossRef]
- Shafique, A.; Ahmed, J.; Rehman, M.U.; Hazzazi, M.M. Noise-Resistant Image Encryption Scheme for Medical Images in the Chaos and Wavelet Domain. IEEE Access 2021, 9, 59108–59130. [Google Scholar] [CrossRef]
- Li, X.; Xiao, D.; Mou, H.; Lu, D.; Peng, M. A Compressive Sensing Based Image Encryption and Compression Algorithm With Identity Authentication and Blind Signcryption. IEEE Access 2020, 8, 211676–211690. [Google Scholar] [CrossRef]
- Azhar, S.; Azam, N.A.; Hayat, U. Text Encryption Using Pell Sequence and Elliptic Curves with Provable Security. Comput. Contin. 2022, 71, 4972–4989. [Google Scholar] [CrossRef]
- Murtaza, G.; Azam, N.A.; Hayat, U. Designing an Efficient and Highly Dynamic Substitution-Box Generator for Block Ciphers Based on Finite Elliptic Curves. Secur. Commun. Netw. 2021, 2021, 3367521. [Google Scholar] [CrossRef]
- Abd El-Latif, A.A.; Niu, X. A hybrid chaotic system and cyclic elliptic curve for image encryption. AEU-Int. J. Electron. Commun. 2013, 67, 136–143. [Google Scholar] [CrossRef]
- Toughi, S.; Fathi, M.H.; Sekhavat, Y.A. An image encryption scheme based on elliptic curve pseudo random and advanced encryption system. Signal Process. 2017, 141, 217–227. [Google Scholar] [CrossRef]
- Hayat, U.; Azam, N.A. A novel image encryption scheme based on an elliptic curve. Signal Process. 2019, 155, 391–402. [Google Scholar] [CrossRef]
- Reyad, O.; Kotulski, Z.; Abd-Elhafiez, W. Image encryption using chaos-driven elliptic curve pseudo-random number generators. Appl. Math. Inf. Sci 2016, 10, 1283–1292. [Google Scholar] [CrossRef]
- Cover, T.M.; Thomas, J.A. Elements of Information Theory; Wiley: Hoboken, NJ, USA, 2012. [Google Scholar]
- Jia, N.; Liu, S.; Ding, Q.; Wu, S.; Pan, X. A New Method of Encryption Algorithm Based on Chaos and ECC. J. Inf. Hiding Multimed. Signal Process. 2016, 7, 637–643. [Google Scholar]
- Duran Diaz, R.; Hernandez Encinas, L.; Munoz Masque, J. A group law on the projective plane with applications in Public Key Cryptography. Mathematics 2020, 8, 734. [Google Scholar] [CrossRef]
- Meyer, B.; Müller, V. A public key cryptosystem based on elliptic curves over Z/nZ equivalent to factoring. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Saragossa, Spain, 12–16 May 1996; pp. 49–59. [Google Scholar]
- Azam, N.A.; Ullah, I.; Hayat, U. A Fast and Secure Public-key Image Encryption Scheme Based on Mordell Elliptic Curves. Opt. Lasers Eng. 2020, 137, 106371. [Google Scholar] [CrossRef]
- Azam, N.A.; Hayat, U.; Ullah, I. Efficient construction of a substitution box based on a Mordell elliptic curve over a finite field. Front. Inf. Technol. Electron. Eng. 2019, 20, 1378–1389. [Google Scholar] [CrossRef] [Green Version]
- Adams, C.; Tavares, S. The structured design of cryptographically good S-boxes. J. Cryptol. 1990, 3, 27–41. [Google Scholar] [CrossRef]
- Matsui, M. Linear cryptanalysis method for DES cipher. In Workshop on the Theory and Application of of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1993; pp. 386–397. [Google Scholar]
- Sakallı, M.T.; Aslan, B.; Buluş, E.; Mesut, A.Ş.; Büyüksaraçoğlu, F.; Karaahmetoğlu, O. On the algebraic expression of the AES S-Box like S-Boxes. In Proceedings of the International Conference on Networked Digital Technologies, Prague, Czech Republic, 7–9 July 2010; pp. 213–227. [Google Scholar]
- Ye, T.; Zhimao, L. Chaotic S-box: Six-dimensional fractional Lorenz–Duffing chaotic system and O-shaped path scrambling. Nonlinear Dyn. 2018, 94, 2115–2126. [Google Scholar] [CrossRef]
- Özkaynak, F.; Çelik, V.; Özer, A.B. A new S-box construction method based on the fractional-order chaotic Chen system. Signal, Image Video Process. 2017, 11, 659–664. [Google Scholar] [CrossRef]
- Çavuşoğlu, Ü.; Zengin, A.; Pehlivan, I.; Kaçar, S. A novel approach for strong S-Box generation algorithm design based on chaotic scaled Zhongtang system. Nonlinear Dyn. 2017, 87, 1081–1094. [Google Scholar] [CrossRef]
- Belazi, A.; Abd El-Latif, A.A. A simple yet efficient S-box method based on chaotic sine map. Optik 2017, 130, 1438–1444. [Google Scholar] [CrossRef]
- Liu, L.; Zhang, Y.; Wang, X. A novel method for constructing the S-box based on spatiotemporal chaotic dynamics. Appl. Sci. 2018, 8, 2650. [Google Scholar] [CrossRef] [Green Version]
- Biham, E.; Shamir, A. Differential cryptanalysis of DES-like cryptosystems. J. Cryptol. 1991, 4, 3–72. [Google Scholar] [CrossRef]
- Webster, A.; Tavares, S.E. On the design of S-boxes. In Proceedings of the Conference on the Theory and Application of Cryptographic Techniques, Linz, Austria, 9–11 April 1985; pp. 523–534. [Google Scholar]
- USC-SIPI Image Database. Available online: http://sipi.usc.edu/database/database.php (accessed on 29 December 2020).
- Zhou, Y.; Bao, L.; Chen, C.P. Image encryption using a new parametric switching chaotic system. Signal Process. 2013, 93, 3039–3052. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X. Fractal sorting matrix and its application on chaotic image encryption. Inf. Sci. 2021, 547, 1154–1169. [Google Scholar] [CrossRef]
- Luo, Y.; Ouyang, X.; Liu, J.; Cao, L. An image encryption method based on elliptic curve elgamal encryption and chaotic systems. IEEE Access 2019, 7, 38507–38522. [Google Scholar] [CrossRef]
- Patro, K.A.K.; Acharya, B. An efficient colour image encryption scheme based on 1D chaotic maps. J. Inf. Secur. Appl. 2019, 46, 23–41. [Google Scholar]
- Kumar, M.; Sathish, G.; Alphonse, M.; Lahcen, R.A.M. A new RGB image encryption using generalized heat equation associated with generalized Vigenere-type table over symmetric group. Multimed. Tools Appl. 2019, 78, 28025–28061. [Google Scholar] [CrossRef]
- Kadir, A.; Hamdulla, A.; Guo, W.Q. Color image encryption using skew tent map and hyper chaotic system of 6th-order CNN. Optik 2014, 125, 1671–1675. [Google Scholar] [CrossRef]
- Li, S.; Ding, W.; Yin, B.; Zhang, T.; Ma, Y. A novel delay linear coupling logistics map model for color image encryption. Entropy 2018, 20, 463. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Wu, X.; Kurths, J.; Kan, H. A robust and lossless DNA encryption scheme for color images. Multimed. Tools Appl. 2018, 77, 12349–12376. [Google Scholar] [CrossRef]
- Zhou, Y.; Bao, L.; Chen, C.P. A new 1D chaotic system for image encryption. Signal Process. 2014, 97, 172–182. [Google Scholar] [CrossRef]
- Chai, X.; Chen, Y.; Broyde, L. A novel chaos-based image encryption algorithm using DNA sequence operations. Opt. Lasers Eng. 2017, 88, 197–213. [Google Scholar] [CrossRef]
- Hua, Z.; Zhu, Z.; Yi, S.; Zhang, Z.; Huang, H. Cross-plane colour image encryption using a two-dimensional logistic tent modular map. Inf. Sci. 2021, 546, 1063–1083. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).