Abstract
Fifth generation mobile communication systems (5G) have to accommodate both Ultra-Reliable Low-Latency Communication (URLLC) and enhanced Mobile Broadband (eMBB) services. While eMBB applications support high data rates, URLLC services aim at guaranteeing low-latencies and high-reliabilities. eMBB and URLLC services are scheduled on the same frequency band, where the different latency requirements of the communications render their coexistence challenging. In this survey, we review, from an information theoretic perspective, coding schemes that simultaneously accommodate URLLC and eMBB transmissions and show that they outperform traditional scheduling approaches. Various communication scenarios are considered, including point-to-point channels, broadcast channels, interference networks, cellular models, and cloud radio access networks (C-RANs). The main focus is on the set of rate pairs that can simultaneously be achieved for URLLC and eMBB messages, which captures well the tension between the two types of communications. We also discuss finite-blocklength results where the measure of interest is the set of error probability pairs that can simultaneously be achieved in the two communication regimes.
1. Introduction
Modern communication networks serve a range of applications with heterogenous characteristics. Indeed, 5G and proposed 6G wireless mobile cellular networks are expected to serve a diverse set of applications including telephony, video-streaming, online gaming, time-critical control for transportation or remote surgery, or massive machine-type applications for sensor networks in the Internet of Things (IoT) [1]. These applications differ in terms of both reliability and latency requirements. A key example is when Ultra-Reliable Low-Latency Communication (URLLC) and enhanced Mobile Broadband (eMBB) [2] applications utilize the same time-frequency resource blocks.
URLLC is designed to ensure 99.99% reliability at a maximum end-to-end delay of no more than one millisecond [3,4,5,6,7,8,9,10]. It is thus suited for delay- and mission-critical applications such as remote surgery, control of manufacturing sites, or communication to and from autonomous vehicles. On the other hand, eMBB is most prominently used for video streaming and other applications with less stringent delay tolerances [2].
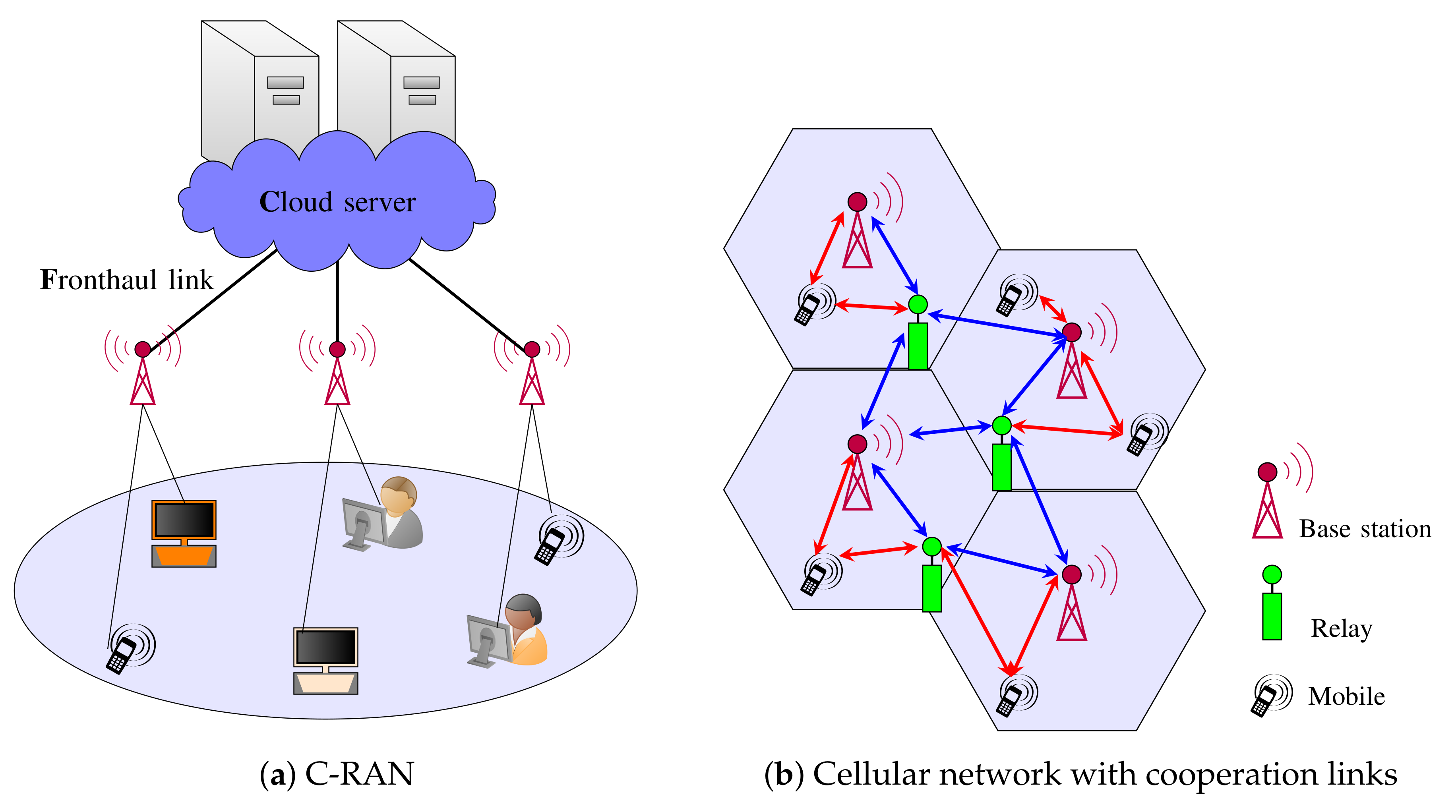
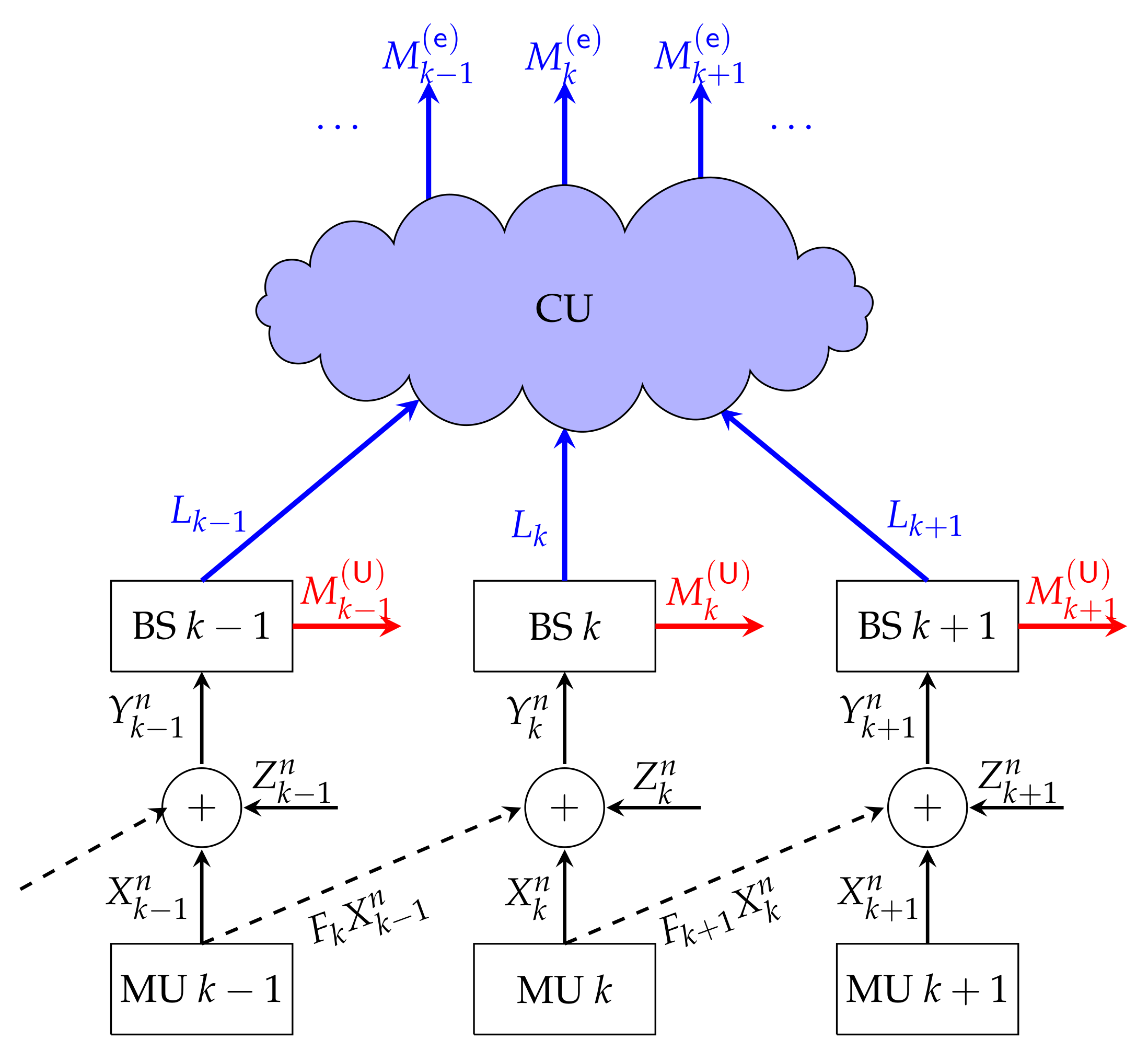
In 5G and proposed 6G systems, URLLC and eMBB users are allocated network slices, which correspond to resources within the radio access network. A key challenge is how to design resource allocation and coding schemes given that URLLC and eMBB slices have very different delay requirements. As such, the network must support mixed delay traffic. This challenge is further complicated when the radio access network exploits advanced architectures, such as cloud radio access networks (C-RANs) [11,12] (illustrated in Figure 1a) or cooperative networks (illustrated in Figure 1b).
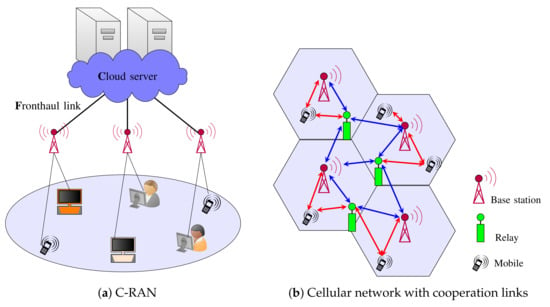
Figure 1.
Infrastructures that allow the mitigation of interference.
One standard approach is to use smart scheduling and resource allocation algorithms, which interrupt eMBB transmissions to send URLLC data. Various scheduling algorithms have been proposed, which exploit machine learning techniques [13,14,15,16] (including deep learning [17,18]) and intelligent reflective surfaces [19] to improve performance.
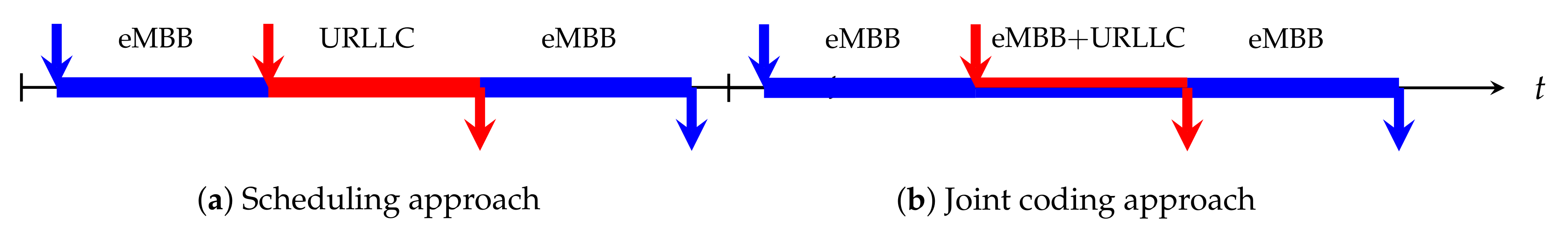
Nevertheless, an information theoretic perspective suggests that performance can be further improved via advanced joint coding schemes, which account for the mixed delay requirements of URLLC and eMBB slices. Indeed, by introducing joint coding schemes, data from both URLLC and eMBB slices can be simultaneously transmitted in the same resource block, as illustrated in Figure 2. A key issue is that interference is introduced not only by multiple users within the same time-frequency resource, but also from data from each slice transmitted by the same user. Nevertheless, as we show in this survey, by using appropriate joint coding techniques, the presence of interference does not necessarily lead to reductions in performance.
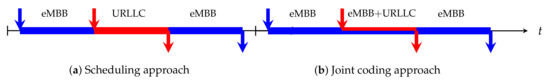
Figure 2.
URLLC and eMBB transmissions: (a) Scheduling approach, (b) Joint coding approach.
In this survey, we overview recent work on joint coding with mixed delay traffic arising from URLLC and eMBB slices in network architectures ranging from point-to-point to C-RANs.
1.1. Related Works
While in this survey we focus on communication scenarios with different network slices that have different delay constraints, information-theorists have also studied related scenarios with other types of heterogeneous communication requirements. The works most closely related to mixed-delay are [20,21,22]. Specifically, [20] studies a scenario where two messages are transmitted over a broadcast channel, but only one of them can profit from the cooperation link between the two receivers. The other message has to be decoded directly based on the legitimate receiver’s channel outputs, without cooperation from the other receiver. The motivation in [20] to study such a system was to design a robust communication scheme where the receivers can reliably decode two messages when the cooperation link between the receivers is present, while still being able to reliably decode a single message in case the cooperation link fails. A different interpretation, but with the same mathematical model, is to say that one of the messages needs to be decoded immediately without waiting for the cooperation message from the other receiver, while the other message can tolerate more delay and therefore be decoded also based on the cooperation message. In this sense, the model [20] well suits also a mixed-delay communication scenario with URLLC and eMBB slices as considered in this survey. The works in [21,22] study a scenario with different reliability criteria of two slices, as also characteristic for URLLC and eMBB slices. In particular, [21] imposes the constraint that the data from one slice has to be decoded even under an adversarial attack model (the arbitrarily varying channel [23,24,25]) whereas the data from the other slice only has to be decoded in the likely event that the channel exhibits an expected behavior.
1.2. Related Surveys and Contributions
A number of surveys, summarized in Table 1, have recently appeared covering varying aspects of coding, resource allocation, and architecture design in 5G and beyond. The surveys in [11,26,27] have focused on system level approaches in order to support network slicing, but do not consider aspects related to coding.

Table 1.
Related Surveys.
On the other hand, the surveys in [2,28,29,30,32,33,34,35,36] focus on communication theoretic aspects of 5G and future 6G systems. In particular, [2,28,29,32] consider various resource allocation techniques and specifically [2] treates resource allocation for eMBB and URLLC slices. The surveys in [33,34,35,36] focus on non-orthogonal multiple access (NOMA) schemes based on successive interference cancellation for multiple access networks, while the survey [30] overviews the benefits of rate-splitting techniques on the multiple-access channel.
Despite the importance of joint coding schemes with mixed delay traffic, there has not been a comprehensive survey on this topic. This survey aims to fill this gap by highlighting how joint coding can improve performance of standard scheduling schemes, drawing on fundamental insights from an information theoretic analysis of the network.
The main contributions in this survey are summarized as follows:
- (i)
- An overview of interference mitigation techniques drawn from information theory, with a focus on superposition coding, dirty paper coding, and coordinated multi point transmission and reception.
- (ii)
- A summary of joint coding schemes and recent results on their performance for mixed delay traffic in
- (a)
- point-to-point networks;
- (b)
- broadcast networks;
- (c)
- cooperative networks;
- (d)
- C-RANs.
- (iii)
- A discussion of open problems in the design of joint coding schemes for mixed delay traffic.
1.3. Outline of the Survey
This survey article is organized as follows. In Section 2 we review known interference mitigation techniques such as superposition coding, dirty-paper coding, and Coordinated Multi-Point (CoMP) transmission and reception. For a more thorough discussion of these tools, we refer to the original articles or standard textbooks [37,38]. We then continue in Section 3 to discuss integrated transmission of URLLC and eMBB messages on P2P channels with a single transmitter and a single receiver, followed by Section 4 which discusses extensions to multi-receiver broadcast channels (BC). Section 5 and Section 6 consider mixed-delay transmissions over cooperative cellular interference networks and C-RANs. The survey is concluded with a summary and outlook section in Section 7.
Notation: Throughout the survey, we abbreviate transmitter and receiver by Tx and Rx. For independent and identically distributed we use i.i.d. Random variables are denoted using upper case letters, and realizations thereof by lower case letter, e.g., X and x. Random vectors are denoted with uppercase bold symbols. Fixed constants are often written with sans-serif font, for example or using Greek letters, for example and . To follow standard notation we however use n to denote the blocklength of transmission. For any positive integer we use the short-hand notation . Channels are assumed to be real-valued, extensions to complex channels with independent real and complex components are straightforward. In this sense, denotes the real centered Gaussian distribution of variance . We also use the usual shorthand notation .
2. Mixed Delay Traffic and Interference Mitigation
2.1. Coding and Delay
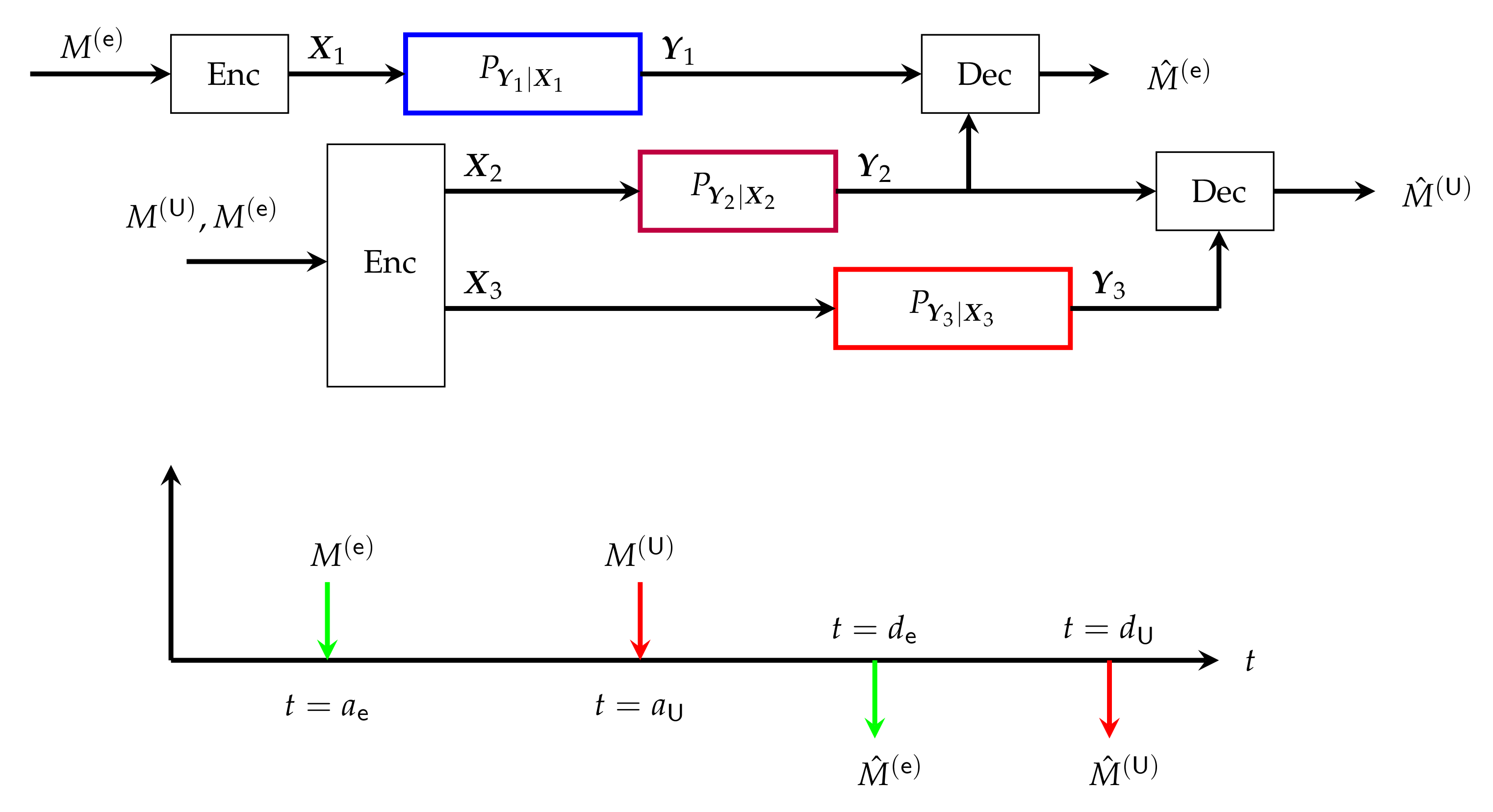
The primary goal of a communications network is to reliably send one or more messages from one or more Txs to one or more Rxs. To do so, each Tx encodes the different messages it wishes to send into a waveform , which corresponds to the physical signal sent over the network. In a scenario with homogeneous delay constraints i.e., where all messages are sent over the same blocklength n, a Tx k encodes its messages , where collects the indices of all messages sent by Tx k, into the codeword using a joint encoding function . After receiving the corresponding output symbols , Rx k produces a guess for each of its desired messages , where collects the indices of the messages intended for Rx k, by applying a decoding function to its observed outputs .
A more complicated scenario typically arises in the mixed-delay scenarios we consider in this survey, because the various messages are created at different times and have different decoding delays. In this case, each message is assigned a creation time and a latest possible decoding time . As a consequence, a Tx k produces its inputs using per-symbol encoding functions , where at time-t the function maps all its previously created messages to an input symbol:
Rx k decodes any of its intended messages by applying the decoding function to the first channel outputs . The decoding function that produces the message guess is thus of the form .
Associated with the described mixed-delay encodings are two key parameters:
- (i)
- the length of each codeword, ;
- (ii)
- and the rate, defined by
In multi-hop scenarios such as experienced in C-RANs or cooperative networks, transmission delay not only depends on the blocklength of communication, but also on the delay introduced from the communication over the addition hops. For example, in the uplink of C-RANs, the total delay experienced for the transmission of a messages is formed by:
- the communication delay over the network from the mobile users to the BSs;
- the processing time of the compression at the BSs as well as the communication delay over the fronthaul links to the cloud processor;
- the decoding processing time at the cloud processor.
In mixed-delay networks, the additional delay introduced by the compression at the BSs and the fronthaul communication might exceed the latest allowed decoding time for certain messages , which thus have to be directly decoded at the BSs. A similar situation is also encountered in the downlink of C-RANs, where URLLC messages should directly be encoded at the BSs and not at the cloud processor so as to avoid the delay introduced by the additional communication hop over the fronthaul link. In the same way, URLLC messages transmitted in cooperative interference networks cannot support the additional communication hops required to establish cooperation between Txs or Rxs. In these networks, the cooperative communication at the Tx side thus can only depend on eMBB messages and the cooperative communication at the Rx side can only serve decoding of eMBB messages. We will provide a more detailed model for the encoding and decoding of mixed-delay messages in Section 5 ahead. A main assumption in our model will be that the communication over the interference network is sufficiently short so that also URLLC messages can tolerate the introduced delay.
As we will overview in this survey, mixed delay constraints require careful design of the joint coding schemes, in particular to mitigate the interference caused by the different slices. In the remainder of this section, we summarize key information-theoretic interference mitigation techniques.
2.2. Superposition Coding
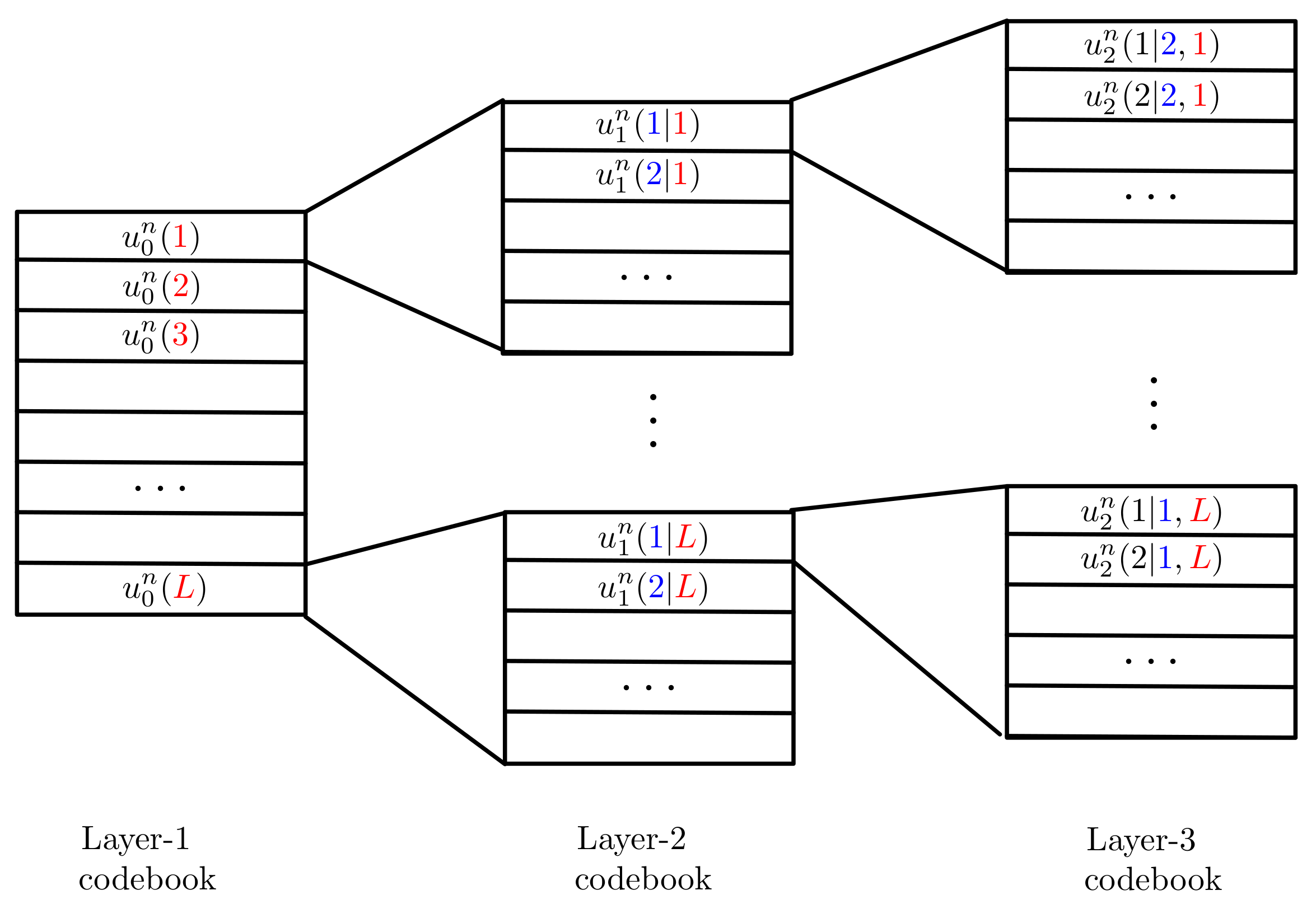
Superposition coding [37,39] was first proposed in the context of broadcast communication. It can be used to send multiple messages to one or more receivers. The main technical feature is that the different messages are encoded into the different layers of a so called superposition code, illustrated in Figure 3 for a code example with three layers. The entries of the layer-1 code are drawn i.i.d. according to a chosen distribution . For each layer-1 codeword a new layer-2 codebook is chosen. The entries of the layer-2 codewords are drawn independent of each other and the i-th entry follows a conditional distribution given the i-th entry of codeword . For each layer-2 codeword, a new layer-3 codebook is chosen. Entries of this codebook are again independently of each other and drawn according to a conditional distribution given the entries in the corresponding layer-2 codeword.
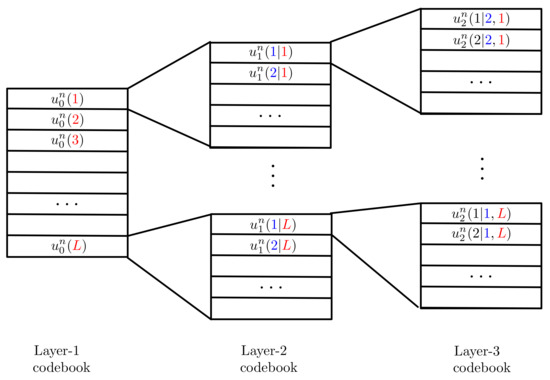
Figure 3.
Superposition code with 3 layers.
In a superposition code, each message is not only protected by its corresponding layer, but also by all underlying layers. Given the structure of the code, any receiver that is interested in decoding a given layer also has to decode all previous layers, typically in a joint manner. Upper layers are not decoded and cause additional disturbance (noise) on the decoding of lower layers.
Given the described decoding order, in the context of mixed-delay traffic it is possible to send URLLC data on lower layers and eMBB on upper layers but not the other way around, because URLLC messages have to be decoded first, prior to decoding eMBB messages.
A simpler alternative to superposition coding is to encode each message using an independent codebook and to combine the chosen codewords, by means of a predefined mapping, to form the sequence of channel inputs. In particular, for Gaussian channels, messages are encoded into Gaussian codewords and the sum of these codewords is transmitted over the channel. The advantage of this method is that no layering-order of the codewords has to be established a priori. This is particularly convenient in fading channels where the exact channel statistics are not known at time of encoding, and the receiver can decide on the layers to decode after having estimated the realization of the channel. In this sense, the simpler alternative can allow for increased expected rates over slowly fading channels where the channel variations are limited over the duration of a single codeword. As we shall see, this approach is also highly beneficial for joint transmission of URLLC and eMBB messages where the fading is almost constant over the duration of an URLLC communication but varies significantly during the transmission of eMBB messages.
2.3. Dirty-Paper Coding (DPC)
If interference is known at a Tx before communication starts, the Tx can mitigate this interference through Dirty Paper Coding [40,41,42] and achieve the full capacity of the channel without interference. To illustrate, consider the Gaussian interference channel
where is an i.i.d. standard Gaussian noise sequence and is memoryless interference sequence, with each component zero-mean Gaussian of power . If is unknown to both the Tx and the Rx, the interference simply acts as additional noise, and the capacity of the channel equals . If the Rx knows , then it can subtract this interference from the outputs and as a consequence the capacity of the channel is the same as without interference, i.e., . Costa [40] showed that when is unknown to the Rx but known to the Tx even before the communication starts, then the capacity of the channel is also equal to the interference-free capacity . The coding scheme achieving this performance was termed dirty-paper coding (DPC) and is described in the following. (For an analysis see [37,40]).
Define the parameter and the random variable where and independent of each other. It can be verified that
Fix arbitrary small. For each generate a bin with codewords by picking each component of each codeword i.i.d. according to . Reveal the codebook consisting of all bins to the Rx and the Tx.
Encoding: To encode a message , the encoder looks for a codeword in bin m that is jointly typical [37] (i.e., has approximately the correct joint empirical distribution) with the interference sequence . The Tx then forms , where indicates the chosen index, and send this sequence over the channel. Note that the Tx declares an error if no codeword in bin m is jointly typical with the interference .
Decoding: After observing the sequence , the Rx looks for a codeword that is jointly typical with . If a single such codeword exists, the Rx declares , otherwise it declares an error.
It can be shown that with probability tending to 1 as the blocklength , the only codeword that is jointly typical with is codeword which was selected at the transmitter. The Rx thus not only recovers the correct message with high probability, but can also reconstruct the transmitted codeword with high probability.
2.4. Coordinated Multi Point (CoMP)
Coordinated multi-point (CoMP) refers to a wide set of techniques that enable either a set of distributed Txs to jointly encode messages or a set of distributed Rxs to jointly decode messages. We will be particularly interested in scenarios where CoMP is facilitated through cooperative communication over dedicated links between transmitters or between receivers.
In the case of CoMP transmission [43,44,45,46], we consider a set of distributed Txs, each having one message to send, and with cooperation links between neighbouring Txs. Before communicating to the Rxs, all Txs convey their messages to a dedicated Tx, called the master Tx, which then jointly designs input signals for all Txs (also exploiting its available state-information) and conveys rate-distortion compressed (lossy) versions of these signals to each of the Txs. The Txs reconstruct the compressed signals and send these signals over the channel to the Rxs. If cooperation links are of sufficiently high rates, then the loss of the compression can be maintained at noise-level and does not decrease the degrees of freedom (DoF), i.e., the factor in front of the logarithmic expansion of the asymptotic high-SNR sum-capacity. In this case, the interference channel is intuitively transformed into a multi-antenna single-Tx BC and the DoF is given by the minimum number of Tx and Rx antennas.
In case of CoMP reception [47,48,49,50], consider a set of distributed Rxs, each wishing to decode one message, and with cooperation links between neighbouring Rxs. Each Rx applies a lossy compression algorithm to its observed output signal and describes the compressed signal over the cooperation links to a dedicated Rx, called master Rx. This master Rx reconstructs all the compressed signals and jointly decodes all the messages, which it then sends to their intended Rxs over the cooperation links. If cooperation links are of sufficiently large rates, then lossy compression of the receive signals can be performed so that the loss is maintained at noise-level, which again has no influence on the DoF of the channel, and corresponds to the DoF of a single-Rx multi-access channel which equals the minimum number of Tx and Rx antennas.
CoMP transmission and reception can only be used to encode and decode eMBB messages, because the communication over the cooperation links induces significant delay. The delay is in fact given by twice the number of hops required on the cooperation links to reach the master Tx/Rx from any other Tx/Rx in the network times the communication duration on a single cooperation hop. Since in practical networks also eMBB communication is delay-limited, CoMP transmission and reception can be performed only on small subsets of Txs and Rxs, where the size depends on the maximum allowed number of communication hops.
3. Point-to-Point Communications
3.1. Introduction
This section focuses on P2P channels with a single Tx and a single Rx. Section 3.2 reviews the superposition coding approach over fading channels in [51,52]. This approach manages to send URLLC messages over single coherence blocks of the fading channel without suffering from a degradation due to the lack of state knowledge at the Tx, and simultaneously also sends eMBB messages over multiple coherence blocks, thus exploiting the ergodic behaviour of the channel. This approach is also known as broadcast approach and has been studied for a wide field of applications, see the recent survey paper [53].
Section 3.3 summarizes the results in [54,55], which analyze a similar superposition coding approach but for Gaussian channels and in the finite-blocklength regime. The analysis is based on the concept of “parallel channels” introduced in [56].
3.2. The Broadcast Approach over Fading Channels without Transmitter Channel State Information
This section is based on the results in [51,52,53]. Consider a P2P channel where a single Tx wishes to send both URLLC and eMBB messages over a fading channel to a single Rx. Latency requirements impose that transmission of URLLC messages spans only a single coherence time of the fading channel, but transmission of eMBB can span multiple coherence blocks and thus profit from channel diversity. In a single-antenna setup, a simple channel model capturing these constraints is as follows:
where denotes the number of blocks, the channel coherence time, describe the fading power in the various coherence blocks and are assumed i.i.d. with probability distribution function (pdf) and variance 1, and is a sequence of i.i.d. standard Gaussian noises. The fading power is assumed to be perfectly known at the Rx (e.g., by transmitting pilot signals at the beginning of each block based on which the Rx can estimate the fading power), but not at the Tx. Since each URLLC message can be transmitted only over a single coherence block, the channel inputs are formed as
for some appropriate encoding functions satisfying the power constraint
and where indicates the URLLC message sent in block b and the single eMBB message sent over the entire B blocks.
In the following, messages are assumed independent of each other and uniform over message sets and . In this subsection, and , where and denote the URLLC and eMBB rates of transmission.
After each block b, the Rx decodes the URLLC message sent in this block:
and at the end of the entire communication it also decodes the eMBB message:
for decoding functions and on appropriate domains.
In [51,52], the authors propose to encode the two message streams using simplified superposition coding where both streams are encoded into independent Gaussian codewords, which are then added up for transmission. More precisely, the URLLC message in each block is encoded into multiple layers so that the Rx can decode as many layers as the actual instantaneous fading power permits. (This implies also that depending on the fading realization, certain URLLC messages are not decoded and in practice have to be retransmitted in the next block.) To allow for closed-form expressions, an infinite layering approach is employed with layers that are of infinitesimally small power.
The Tx allocates total power to the transmission of the URLLC messages and power to transmit the eMBB messages. The power distribution to the different URLLC layers is described by a power density satisfying , where indicates the (infinitesimally small) power that is assigned to a given layer that is decoded whenever the fading . The interference power stemming from non-decoded URLLC messages under state is then given by where
Since URLLC messages are decoded after each block, and eMBB messages only at the end of the last block B, decoding of URLLC messages not only suffers from the interference of non-decoded URLLC messages, but also from the interference of eMBB messages. The power of this latter interference is equal to independent of the block (since the Tx has no knowledge about it cannot adapt the power).
To decode the eMBB message at the end of the last block , the Rx first subtracts the contributions of the codewords corresponding to the decoded URLLC messages and then decodes the eMBB message based on this difference while accounting for the interference power created by all non-decoded URLLC messages, which in block b is given by .
A careful analysis of the infinite-layering approach, see [52], reveals that the expected rate of the reliably decoded messages (i.e., messages decoded with error probability tending to 0 as the blocklength ) can be as high as
where denotes the cumulative distribution function (cdf) associated with the pdf . In the denominator of (13), the term indicates the interference power experienced during the decoding of URLLC messages stemming from the eMBB transmission and the non-decoded URLLC messages.
For a sufficiently large number of blocks , the following rate is achievable for the eMBB messages:
Here we find in the denominator which describes the interference power of the non-decoded URLLC messages.
Equations (13) and (14) thus determine the maximum achievable (expected) sum-rate in function of the URLLC interference power (notice that ), which is a design parameter of the scheme and can be optimized. It is shown in [52] that the optimal interference power function among all continuously differentiable functions satisfying the boundary conditions and is given by:
for , , and .
Figure 4 compares the sum-rate achieved for this optimal interference power for different power allocation parameters to a simple outage-based approach where is chosen as a dirac-function at threshold , i.e., when the interference power is given by the step function
Here, the optimal value for the threshold can be derived analytically and is given by the solution to the following equation
From Figure 4, we observe that for small URLLC rates , the penalty in eMBB rates is small when using the suboptimal power allocation corresponding to instead of the optimal allocation corresponding to . For larger URLLC rates, this penalty increases.
We further observe that the maximum sum-rate achieved by both power allocations decreases with increasing URLLC rates. The sum-rate for both approaches is more than 5 when . For it is around 4 under the optimal power allocation and even vanishes completely under outage power allocation leading to (16). In this high-URLLC-rate regime, the gap to the outer bound is also significant, leaving open the possibility of finding better coding schemes.
The described broadcast approach can further be improved by applying a multi-layering approach also for the transmitted eMBB message. In this approach, different eMBB layers are decoded successively, and after each eMBB decoding step, the Tx decodes further URLLC layers so as to remove their interference for the decoding of subsequent eMBB layers. This additional decoding of URLLC messages at the end of block cannot be used to improve performance of the URLLC communication, because the admissible delay is exceeded. However, it enables an improvement in the decoding performance of eMBB messages.
Another way to improve this broadcast approach is to combine it with adaptive causal network coding. For example, the work in [57] proposes a novel layering scheme consisting of a base layer and an enhancement layer for data streaming under mixed-delay constraints. The base layer contains URLLC data and the enhancement layer contains eMBB data. In the proposed scheme, the base layer is encoded using a broadcast approach, which allows the Rx to decode the base layer (i.e., URLLC data) with minimum delay required. The enhancement layer is encoded using a priori and posteriori forward error correction so as to be able to control the throughput-delay trade-off of this communication.
3.3. Finite Block-Length Analysis over Gaussian Channels
This section is based on the results in [54,55]. We again consider a P2P scenario, but where communication is over a non-fading Gaussian channel
for an i.i.d. standard Gaussian noise sequence.
The Tx has a single URLLC message and a single eMBB message to send to the Rx, where both messages are assumed to have strict creation times and fixed decoding deadlines. Specifically, transmission of eMBB message commences at time and decoding has to be performed at time , while the URLLC message can be transmitted starting at time and has to be decoded at time . We thus parametrize the message sets as and . We also denote the transmission window of the eMBB message by and the transmission window of the URLLC messages by :
Since the URLLC delay is assumed shorter than the eMBB delay , the following three situations can occur:
- Case 1: URLLC and eMBB transmissions do not overlap. i.e., .
- Case 2: The eMBB transmission interval includes the URLLC transmission interval, i.e., .
- Case 3: URLLC and eMBB transmissions overlap, but URLLC transmission is not included in eMBB transmission, i.e., and .
In Case 1 where the two messages are transmitted during independent time intervals, URLLC and eMBB transmissions can be analyzed independently based on the achievability and converse bounds in [58]. Cases 2 and 3 can be treated similarly. Here, we focus on a subcase of Case 3 where encoding starts with the eMBB message at time and terminates at time with the decoding of the URLLC message, see Figure 5. The Tx thus produces channel inputs at times as follows:
where are appropriate encoding functions. Note that the Tx does not know the URLLC message before time and therefore channel inputs prior to time cannot depend on . It can also be assumed that channel inputs after the eMBB decoding time de not depend on the eMBB message . One can therefore think of the transmission taking place over three parallel channels, with respective blocklengths
where the first channel consists of channel uses and incorporates only eMBB transmission; the second channel consists of channel uses and incorporates joint transmission of URLLC and eMBB messages; and the third channel consists of channel uses and incorporates only URLLC transmission. We denote the inputs and outputs of the three parallel channels by
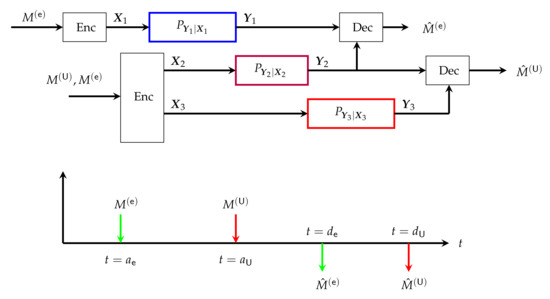
Figure 5.
System model for transmission of URLLC and eMBB messgaes in the finite blocklength regime and under heterogeneous decoding deadline.
For the i-th channel with , the encoding functions satisfy the average block power constraint
almost surely. The resulting system model is illustrated in Figure 5, where notice that the three channels , and are additive, memoryless, stationary, and Gaussian of variances 1.
The scheme further proposes to combine the eMBB and URLLC transmission over the second channel by means of the simple superposition coding approach described at the end of Section 3.2, for which the block-2 power is split into power for the eMBB transmission and power for the URLLC transmission, for some . In particular, the channel inputs are formed as
where is a codeword encoding of average power , and is a codeword encoding of average power .
The Rx first decodes the eMBB message based on the outputs of the first and second channels where it treats the transmission of the URLLC message over the second channel as interference. Subsequently, it decodes the URLLC message based on the outputs of the second and third channel, conditioning on the already decoded eMBB message.
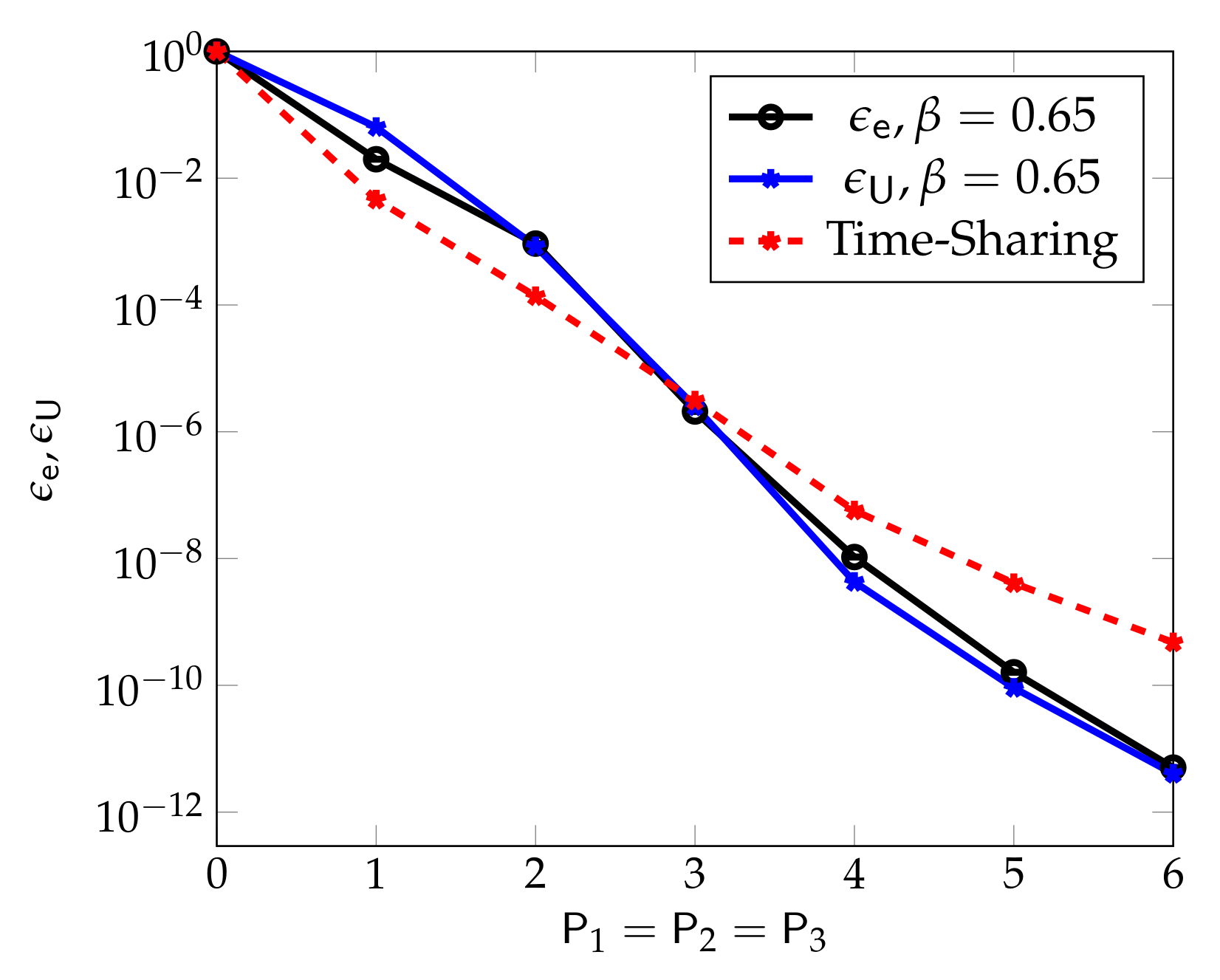
The error probabilities of the described scheme can be analyzed and compared to fundamental lower bounds on the error probabilities, obtained via meta-converse arguments [58] with an extension to parallel channels [56]. As shown in [54], the converse and achievability bounds match in specific cases.
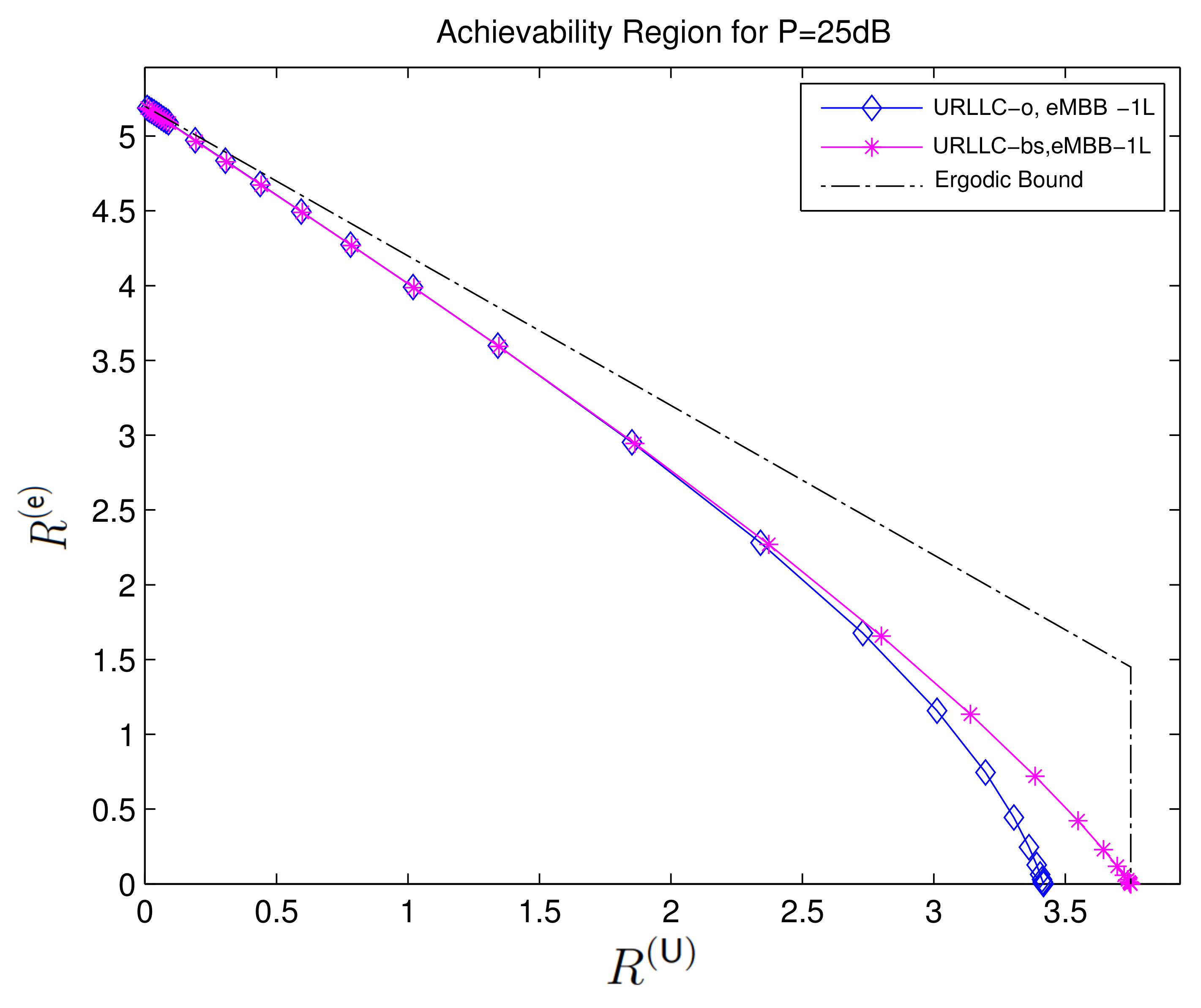
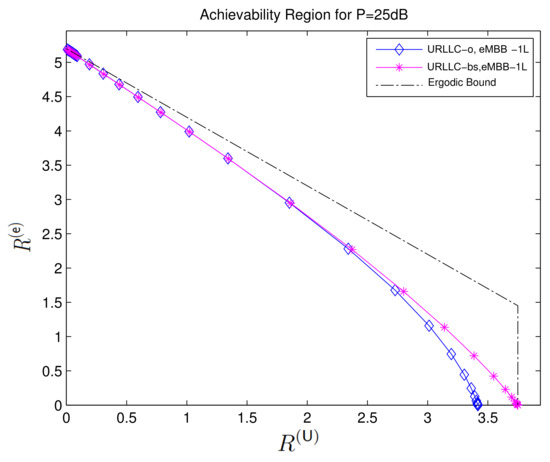
Figure 6, from [54], compares the performance of the described superposition coding scheme with a standard scheduling scheme that allocates the first half of the channel uses to eMBB transmission and the second half to URLLC transmission. (Under this scheduling approach .) One observes that for the chosen set of parameters, , , and , the superposition coding approach results in almost identical URLLC and eMBB error probabilities and . Moreover, at medium and high powers , the superposition coding approach significantly outperforms the scheduling approach.
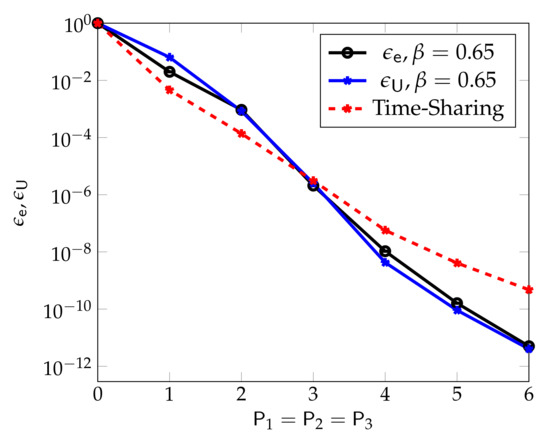
Figure 6.
The figure illustrates the average error probabilities of the eMBB and URLLC messages denoted by and in function of the block transmit powers and for blocklengths , URLLC rate , and power split .
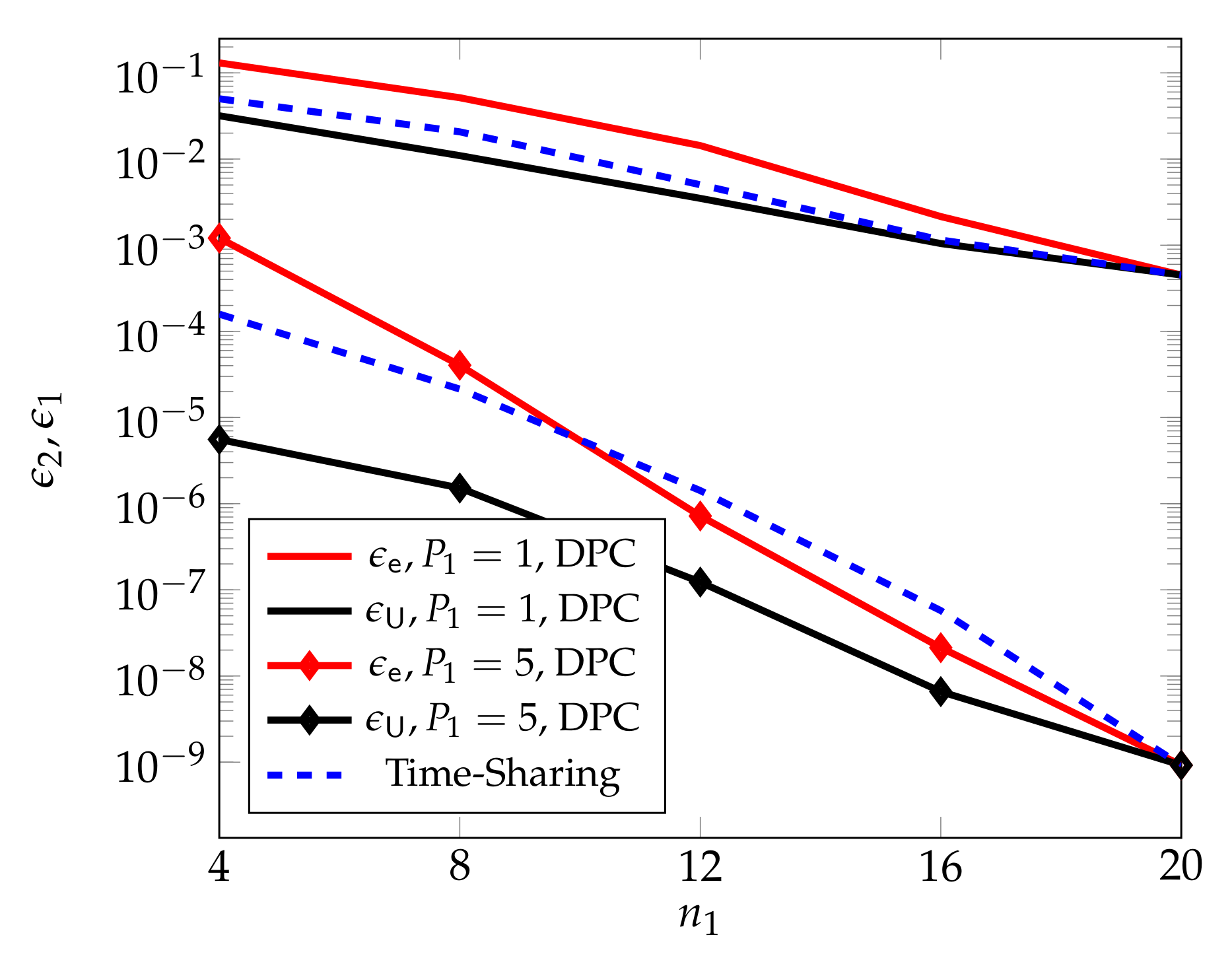
In [55], the authors extend above coding scheme by using the finite-blocklength dirty paper coding (DPC) scheme in [59] to precancel the interference of the eMBB message on the URLLC transmission. Notice that in finite-blocklength DPC, the joint-typicality check is replaced by a norm condition on the input signal, and the Tx has to sacrifice few channel uses to approximately describes the norm of the interference sequence to the Rx. The error probabilities of this DPC based scheme are analyzed in [55] based on the DPC analysis technique in [59] and the parallel channel extension analysis in [56].
Figure 7, from [55], compares the performances of the proposed DPC based scheme with standard scheduling, and shows that for large transmit powers , the DPC based scheme outperforms scheduling over a wide range of blocklengths .
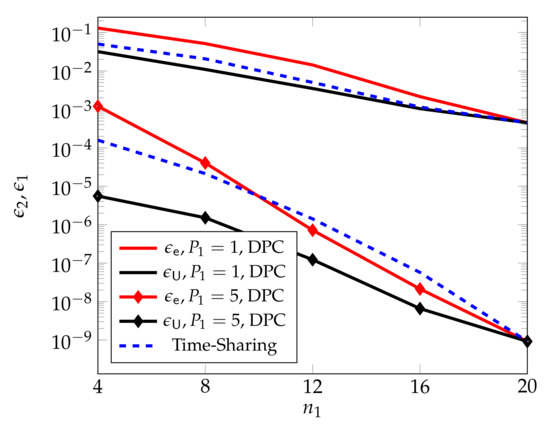
Figure 7.
DPC based upper bounds on and in function of the blocklength and for average block-powers .
3.4. Summary
This section considered a P2P channel with a single Tx that sends an URLLC message and an eMBB message, where the two types of messages have different decoding delays. In Section 3.2, transmission is over fading channels and URLLC messages have to be transmitted within a single coherence block, whereas eMBB messages can be sent over multiple blocks and thus profit from channel diversity. To compensate for the missing channel state-information at the Tx, an infinite-layer broadcast approach is employed. A closed-form solution for the sum-rate achieved by this broadcast approach was presented, and based on numerical simulations it was observed its maximum sum-rate decreases with increasing URLLC rates. Furthermore, a simplified single-layer power allocation was shown to perform close to the optimal power allocation in the broadcast approach at low URLLC rates.
Section 3.3 studies a related simplified superposition coding or dirty-paper coding schemes but over static Gaussian channels and with fixed creation and decoding times. For this setup, upper and lower bounds on the set of achievable error probability pairs that can simultaneously be achieved for URLLC and eMBB messages was derived in [54]. The obtained results show a performance improvement under these schemes compared to the standard scheduling scheme.
4. Broadcast Channels with Mixed-Delay Traffic
4.1. Introduction
This section focuses on multi-receiver broadcast channels (BC). The results of this section are based on [60] where similarly to Section 3.2, URLLC messages have to be decoded within a single coherence block but eMBB messages can be transmitted over multiple blocks. In contrast to Section 3.2, the fading powers of the various blocks are known to the various Rxs and the Tx in advance.
4.2. Broadcast Approach over Fading Channels
In the setup proposed in [60] each Rx might demand a URLLC message, an eMBB message or both. We thus define the two sets and indicating the sets of users requesting URLLC and eMBB messages, respectively. Notice that the two sets can overlap. The mixed-delay constraint is captured by imposing a fixed rate on all transmitted URLLC messages, whereas eMBB messages can be either of larger or smaller rates. This rate-adaption on eMBB messages depending on the encountered fading powers enables an increase in the system’s sum-rate. The corresponding optimization problem can be expressed as
where the maximization is only over rate-tuples such that URLLC rates are achievable on each block and eMBB rates are simultaneously achievable over the entire transmission, all using dirty-paper coding with an optimal precoding order and under an average block power constraint .
The optimization problem in (24) is cumbersome to solve, and instead [60] proposes the following suboptimal algorithm. Fix the dirty-paper precoding order to first precode the eMBB messages followed by the URLLC messages. This implies that eMBB transmissions act as noise on the URLLC communication but not vice versa. Then choose a target URLLC rate and find the minimum required average block-power , for , that ensures achievability of the per-block and per-user URLLC rate . Identify finally the maximum sum-rate achievable on the eMBB transmission with average power .
Though optimal, dirty-paper coding is difficult to implement in practical systems and is often replaced by the simpler zero-force beamforming. In the context of our multi-user and mixed-delay communication scenario, under zero-force beamforming, it remains to determine the assignment of beams to users and the two communication types. The work in [60] proposes a sophisticated beam assignement algorithm, which assigns stronger sub-channels (beams) to URLLC messages, and weaker channels to eMBB messages. The idea being that eMBB communication can profit from channel diversity over multiple coherence blocks.
Numerical simulations in [60] compare the sum-rate in (24) achieved with dirty-paper coding and with a precoding order and power allocation established according to the suboptimal algorithm described above, with the sum-rate achieved with a beamforming alternative. For both schemes the maximum sum-rate increases with small values of and reaches a peak when the URLLC rate contributes approximately a third of the sum-rate. Beyond, the sum-rate decays rapidly because the delay constraint on the URLLC message becomes too stringent and limits the overall performance.
4.3. Summary
This section extended the superposition coding approach to fading BCs with multiple Rxs where certain Rxs demand URLLC messages and other eMBB messages. Assuming perfect channel state information, [60] proposes precoding orders or beam assignments for URLLC and eMBB messages, that take into account that URLLC messages have to achieve their desired rates in a single coherence block and therefore cannot exploit the channel diversity offered over multiple blocks. The results in [60] show that for small requested URLLC rates, the sum-rate of the system is not limited by the stringent delay constraint of URLLC messages. For larger URLLC rates this is however the case and URLLC delay constraints limit the overall performance.
5. Cooperative Interference Networks
5.1. Introduction
In this section we consider interference networks where Txs and/or Rxs can cooperate over dedicated cooperation links. This models for example cellular networks where BSs can cooperate over high-rate fiber-optic links, and neighbouring mobiles can cooperate using bluetooth or millimeter wave communication, which take place on different frequency bands than the standard radio communication between mobiles and BSs, and cause no interference.
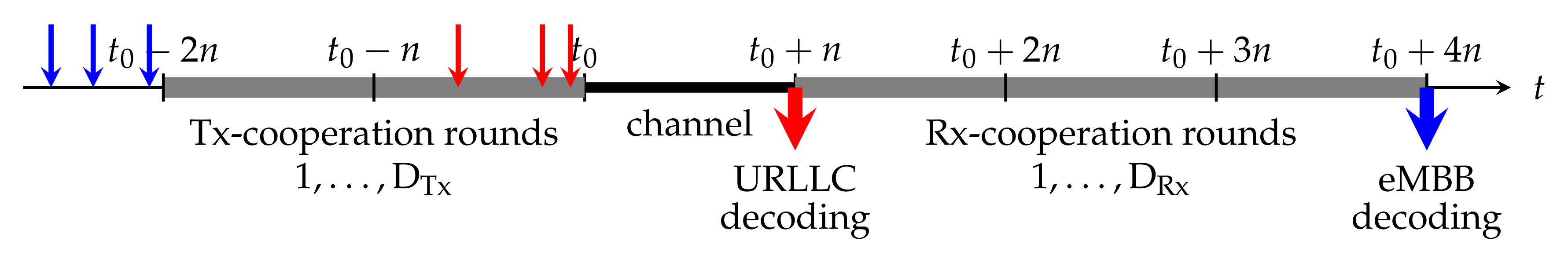
Cooperation links between Txs are beneficial for eMBB transmissions, because they allow Txs to exchange parts of their messages or their signals so as to enable cooperative signaling over the channel. Cooperation links between Rxs can be used to exchange information about receive signals or decoded messages, allowing the Rxs to better mitigate interference. URLLC transmissions however have to start immediately after the creation of the messages and the additional delays caused by exchanging (parts of) URLLC messages between Txs cannot be tolerated. In the same sense, URLLC messages have to be decoded before Rxs can learn information about other Rxs’ decoded messages or receive signals. Figure 8 illustrates a typical timeline in our model. The actual communication time over the interference network is from time to time and corresponds to the blocklength of communication. Here denotes an arbitrary starting time of a block and n refers to the block length. It is dedicated to the transmission of URLLC messages generated just prior to and of eMBB messages generated prior to , so as to allow the eMBB messages to profit from rounds of Tx-cooperation. (For simplicity it is assumed that n represents also the length of a cooperation round. The results also extend to scenarios where this is not the case.) Rxs decode the URLLC messages transmitted in this block as soon as the block is terminated, each Rx simply based on its receive signal. Decoding of eMBB messages can be delayed to time , until the termination of Rx-cooperation rounds.
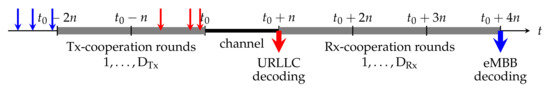
Figure 8.
Timeline of cooperation and transmission over the interference network for URLLC and eMBB messages associated to the block from time to time .
Consider a scenario where each Tx sends an URLLC message and an eMBB message to its corresponding Rx. The focus is on the set of degrees of freedom (DoF) pairs that are simultaneously achievable for URLLC and eMBB messages, and in particular on how the sum-DoF decreases with increasing URLLC DoFs. This decrease describes the degradation of the overall system performance caused by the stringent delay constraints on URLLC messages, as a function of the URLLC rates. Somehow surprisingly, it can be shown that such a degradation does not exist in a variety of networks even with moderate or large URLLC DoFs.
In the following Section 5.2 we describe the problem setup. In Section 5.3, we present the integrated scheduling and coding scheme for URLLC and eMBB messages in [61], and in Section 5.4 we show that this scheme achieves maximum sum-rate even for moderate or large URLLC rates on a variety of network topologies, thus limiting the degradation of the overall system performance. In Section 5.5 we discuss a random-arrival model for URLLC and eMBB messages, where URLLC and eMBB messages are assigned to users according to some random arrival process. Again based on the coding scheme in [61], it can be shown that even under random arrival messages, the overall system performance is hardly degraded by the strict URLLC delay constraints [62,63].
5.2. Problem Description
Throughout this section, we consider a cellular network, but assume that users of the same cell are scheduled in different frequency bands. Interference thus occurs only from the mobile users in neighbouring cells that are scheduled on the same frequency band. The system therefore decomposes into subsystems with only a single mobile in each cell.
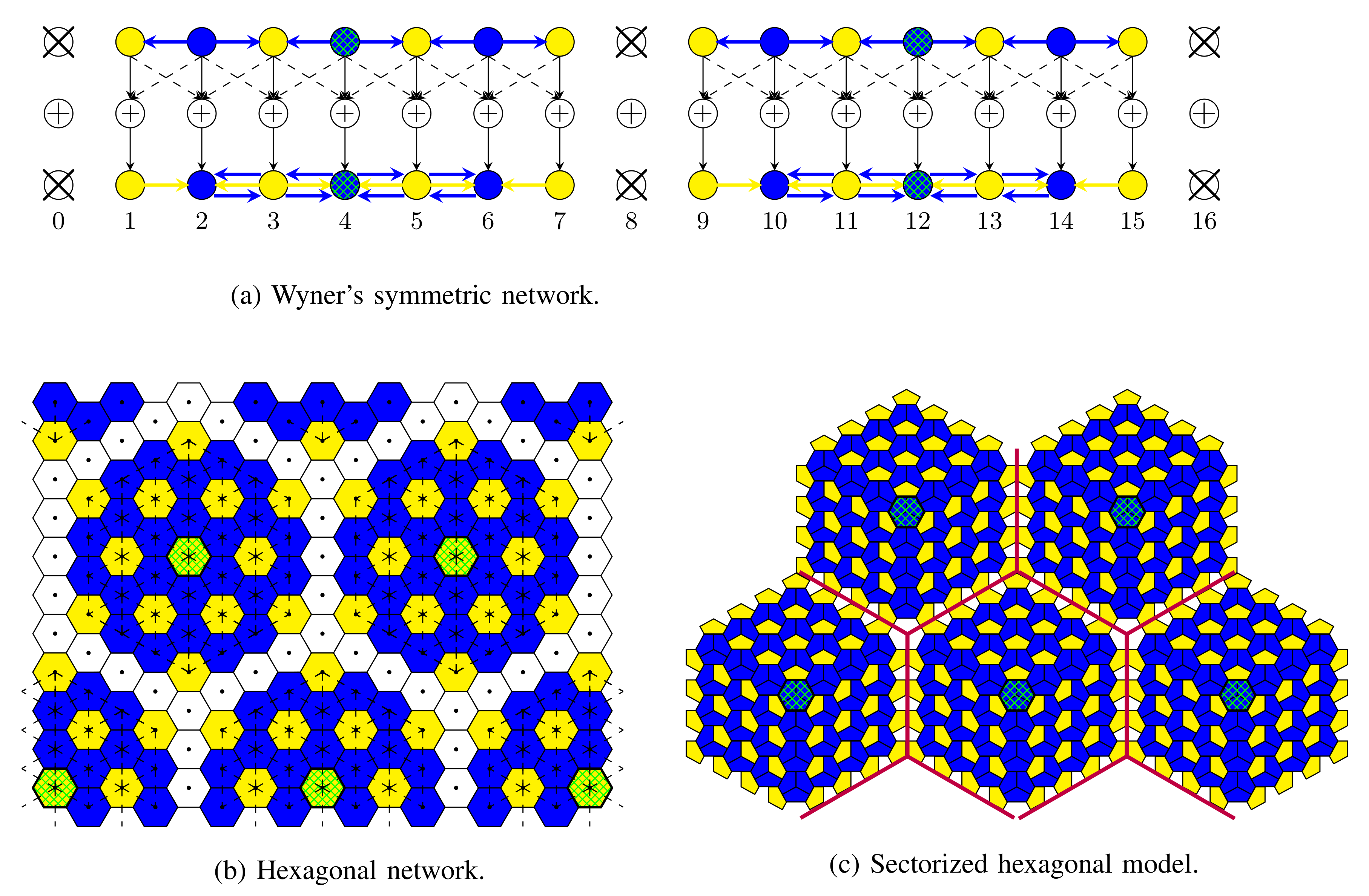
Consider thus an interference network with cells, each consisting of a single Tx/Rx pair (i.e., a single mobile/BS pair). Networks have a regular interference pattern except at the network borders, with a focus on three different network topologies with short-range interference:
- Wyner’s linear symmetric model in Figure 9a, where Txs and Rxs are aligned on two parallel lines and interference is only from the two Txs on the left and the right of any given Tx/Rx pair. This topology models for example situations in a corridor or along a railway line or highway where BSs are aligned. Cooperation links are present between neighbouring Txs and between neighbouring Rxs.
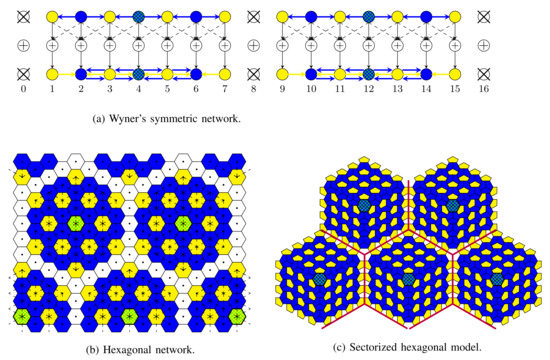 Figure 9. Message assignment for the various network models. White is used for , yellow for , and blue for . Master Txs (Rxs) are in green pattern. Maximum number of allowed cooperation rounds .
Figure 9. Message assignment for the various network models. White is used for , yellow for , and blue for . Master Txs (Rxs) are in green pattern. Maximum number of allowed cooperation rounds . - Wyner’s hexagonal model in Figure 9b, where cells are assumed of hexagonal shape. Interference is from the six neighbouring cells. Cooperation links are present between BSs and between mobiles of neighbouring cells.
- Sectorized hexagonal model in Figure 9c, where cells are again of hexagonal shape. In this model, Txs and Rxs use directed antennas, allowing us to divide each cell into three sectors with non-interfering communications, and interference is only from the neighbouring sectors in neighbouring cells, but not from sectors within the same cell. Here, a single mobile user is assumed in each sector, and thus three mobiles in each cell. Cooperation links are present between BSs of neighbouring cells and between mobiles in neighbouring sectors that are not in the same cell.
Each Tx wishes to convey a pair of independent URLLC and eMBB messages and to its corresponding Rx . URLLC Message is of rate and eMBB message of rate . The focus is on the average URLLC and eMBB rates
Consider a cooperation scenario where neighbouring Txs cooperate during rounds and neighbouring Rxs during rounds. The total cooperation delay is constrained as
where is a given parameter of the system and the values of and are design parameters and can be chosen arbitrary such that (27) is satisfied. During the Tx-cooperation rounds, each Tx can send arbitrary messages to its neighbours depending on the cooperation messages it received in previous rounds and on its eMBB Message . In contrast, Tx-cooperation messages cannot depend on URLLC messages, as they are created only shortly before their transmission over the channel. The cooperative communication is assumed noise-free and the total cooperation load over all Tx-cooperation rounds on each link is limited to bits. Each Tx forms then its channel inputs as a function of all its received cooperation messages and both its URLLC message and eMBB message :
Channel inputs at each Tx are subject to an average block-power constraint .
After receiving its channel outputs
where is i.i.d. standard Gaussian noise, matrix models the channel from Tx to Rx k, which is assumed to be constant during the duration of communication and known by all terminals, each Rx k immediately decodes its intended URLLC message:
using some decoding function on appropriate domains. Following this first decoding step, neighbouring Rxs communicate with each other during Rx-cooperation rounds. In each round, each Rx can send arbitrary messages to its neighbours that depend both on the previously received cooperation messages as well as on its output signals. The cooperative communication is assumed noise-free, but its total communication load over all Rx-cooperation rounds on each link is restricted to bits. At the end of these Rx-cooperation rounds, each Rx k decodes its desired eMBB message as
where denotes all the Rx-cooperation messages received at Rx k and is an appropriate decoding function.
The focus of this section is on the Degrees of Freedom (DoF) region of the described model, i.e., on the set of possible pre-log factors of URLLC and eMBB rates that are simultaneously achievable in the limit of infinite powers :
where the pairs need to be simultaneously achievable for given power .
5.3. Coding Schemes
The following coding scheme was presented in [61]. All Txs in the network are scheduled to either send their URLLC message, their eMBB message, or no message at all. The scheduled eMBB and URLLC messages are then jointly transmitted using an integrated URLLC/eMBB coding scheme. Different schedulings can be envisioned to achieve fairness and send all the required messages. Scheduling is described by three sets , , and , where
- Txs in are silenced and Rxs in do not take any action.
- Txs in send only URLLC messages. Tx/Rx pairs in are called URLLC Txs/Rxs.
- Txs in send only eMBB messages. Tx/Rx pairs in are called eMBB Txs/Rxs.
Figure 9 illustrates the choices of the , , and proposed in [61] for Wyner’s linear symmetric network, the hexagonal model, and the sectorized hexagonal model when the maximum number of allowed cooperation rounds is either or . White colour is used for Tx/Rx pairs in , yellow colour for pairs in , and blue colour for pairs in . The set is chosen as large as possible so that URLLC transmissions are interfered only by eMBB transmissions and not by other URLLC transmissions.
Consider the following joint coding scheme, which integrates both eMBB and URLLC messages. eMBB Txs describe quantized versions of their channel input signals during the Tx-conferencing phase to their neighbouring URLLC Txs, which then precancel the interference on their transmissions. URLLC Rxs can thus decode based on interference-free channels. After decoding, URLLC Rxs describe their decoded messages during the Rx-conferencing phase to the adjacent eMBB Rxs, so as to allow them to pre-subtract the interference from URLLC messages before decoding their intended eMBB messages. As a result, with the proposed scheduling and coding, URLLC messages can be decoded based on interference-free outputs and do not disturb the transmission of eMBB messages. For the transmission of eMBB messages, either CoMP transmission or CoMP reception is used, see Section 2.4, but only on subnets. In fact, with the choice of in Figure 9, the networks decompose into small subnets so that each subnet contains a master Tx/Rx that can be reached by any other Tx/Rx in the subnet with no more than hops over the cooperation links. This ensures that CoMP transmission or reception in each subnet is possible with only cooperation rounds. Since a single cooperation round is used to describe eMBB transmit signals to URLLC Txs and a single round is used to describe the decoded URLLC messages to eMBB Rxs, the scheme respects the maximum number D of total cooperation rounds.
The coding scheme described above transmits both URLLC and eMBB messages. Variants thereof can be used to transmit only eMBB messages or only URLLC messages. More precisely, since any eMBB message can also be treated as a URLLC message (this would mean imposing stringent delay constraints also on some eMBB messages), the same scheme can also be used to send only eMBB messages. An alternative for sending only eMBB messages, is to silence again a set of Tx/Rx pairs and then directly employ CoMP transmission or CoMP reception on the set of non-silenced Txs/Rxs. Both schemes achieve the same DoF, but depending on the specific network they require larger or smaller cooperation rates and .
A simple way to send only URLLC messages is to choose a largest possible set of non-interfering Tx/Rx pairs and to silence all other Tx/Rx pairs. For Wyner’s linear symmetric network this is optimal. For the two hexagonal models, and for certain channel coefficients, better performance is possible using the interference alignment techniques in [64].
5.4. Results on the Joint eMBB/URLLC DoF Region
This subsection presents the achievable eMBB/URLLC DoF region achieved by the schemes in the previous subsection on the three network topologies in Figure 9, and compares them to the outer bounds derived in [61].
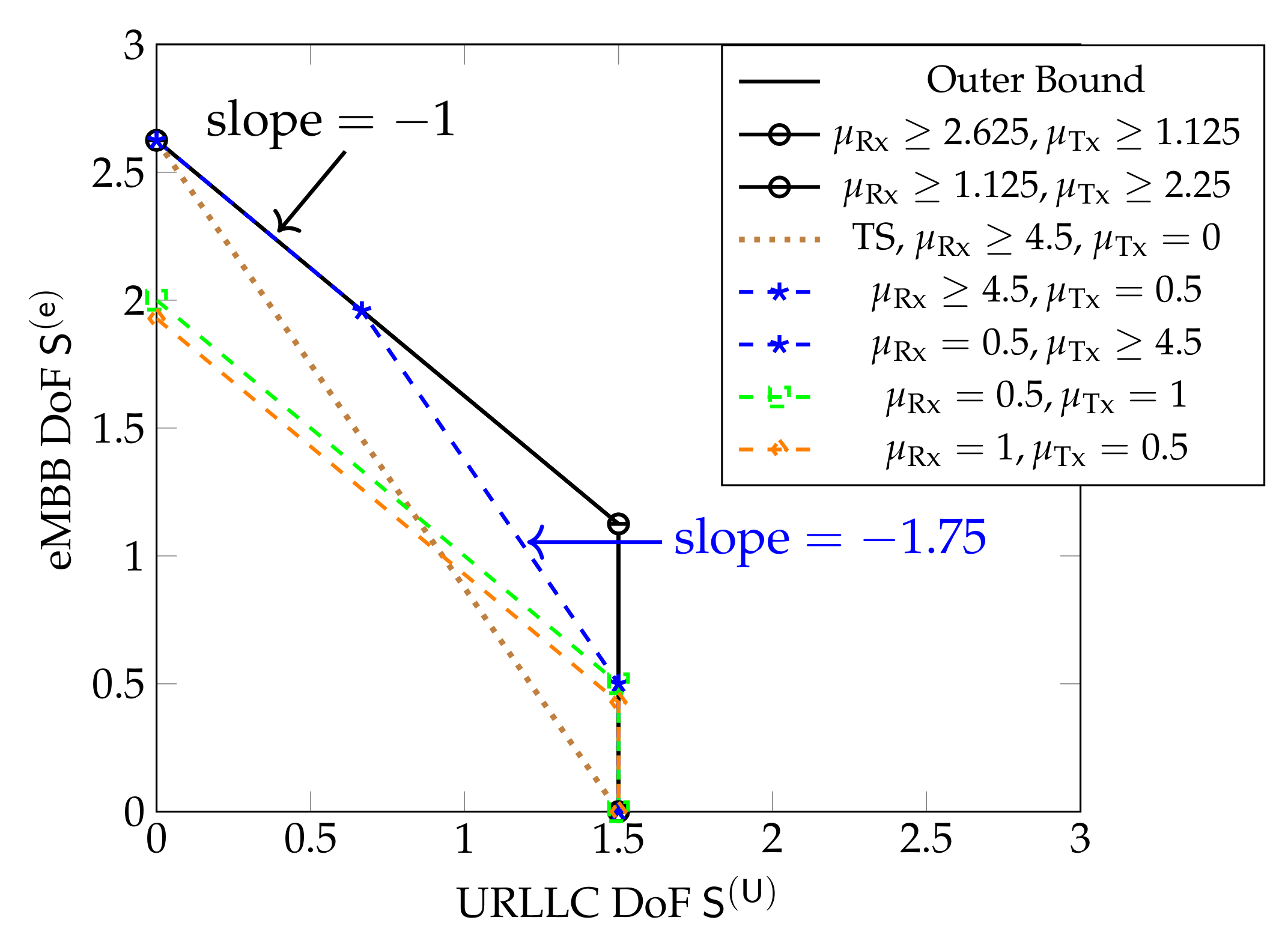
First consider Wyner’s linear symmetric network. For this network and for sufficiently large cooperation prelog factors and , all DoF pairs in the DoF region are achieved by the schemes described in the previous subsection or by time-sharing different versions thereof. The DoF region is given by the set of all DoF pairs that satisfy
One notices that the sum-DoF of the system is limited by the maximum number of allowed cooperation rounds D. Moreover, the stringent delay constraint on URLLC messages does not penalize the maximum achievable sum-DoF, which is equal to , irrespective of .
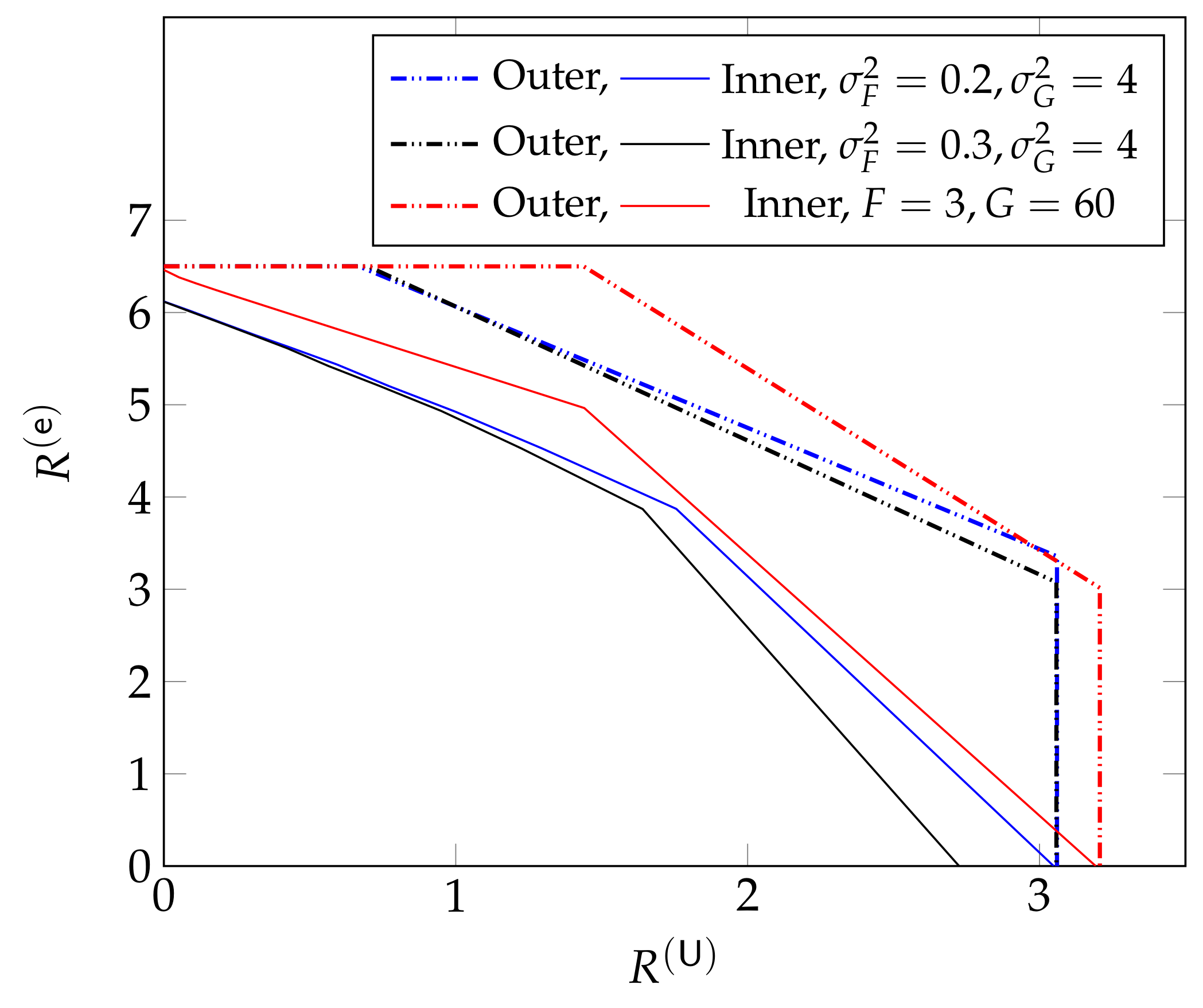
For smaller cooperation prelog factors this is not the case, as can be seen in Figure 10, which shows inner and outer bounds on the DoF region derived in [61]. The inner bound is achieved by time-sharing the coding schemes in Section 5.3, and significantly improves over a pure scheduling approach that time-shares between a system sending only URLLC messages or only eMBB messages. We notice that for and the inner and outer bounds match. The inner bound is achieved by the schemes in Section 5.3 employing CoMP reception for eMBB messages. For and the inner and outer bounds also match, and are achieved by the same schemes, but employing CoMP transmission. When only one of the two cooperation prelogs or is large and the other small (e.g., and ; or and ) the inner bound matches the outer bound only for below a given threshold. For URLLC DoFs exceeding this threshold, the maximum eMBB DoF achieved by the schemes in Section 5.3 decreases linearly with . For example, for and or , beyond this threshold, when one increases the URLLC DoF by , then the eMBB DoF decreases by approximately and the sum DoF by . Yet another behavior is observed when both and are moderate or small, e.g., and or and . In this case, the sum DoF achieved by the inner bound is not at its maximum value, but constant over all regimes of . The overall performance of the system is thus again not limited by the stringent delay constraints on URLLC messages, but simply by the available cooperation rates.
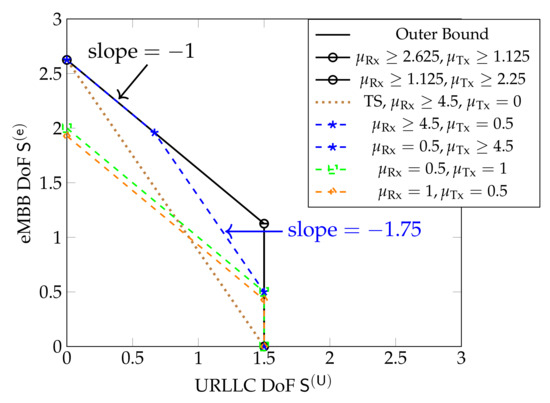
Figure 10.
Bounds on DoF region for Wyner’s symmetric model for different values of and , and . The brown dotted line represents the pure scheduling performance.
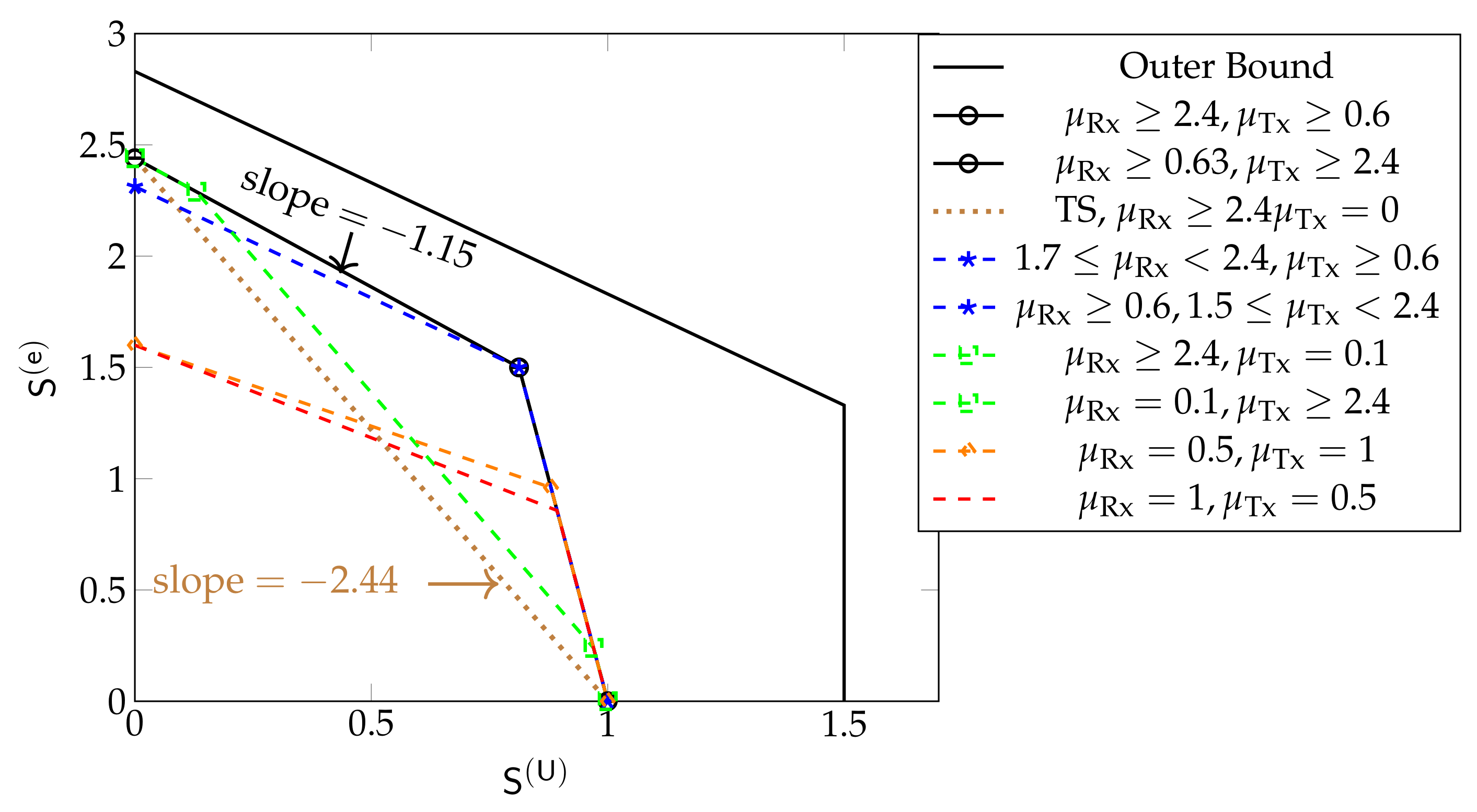
Figure 11 shows the inner and outer bounds on the DoF region proposed in [61] for the hexagonal model when and for different values of and . Unlike in Wyner’s symmetric model, the sum DoF achieved by the schemes in Section 5.3 always decreases as increases, irrespective of the cooperation prelogs . Moreover, the maximum is only achieved for .
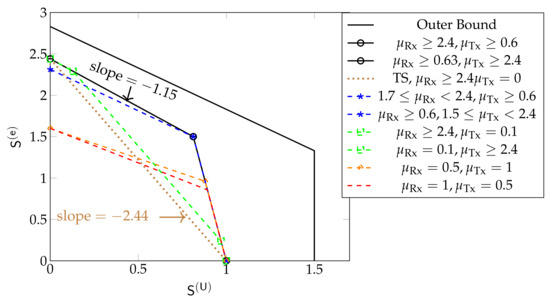
Figure 11.
Inner and outer bounds on the DoF region for the hexagonal model for and different values of and . The brown dotted line shows the pure time-sharing region.
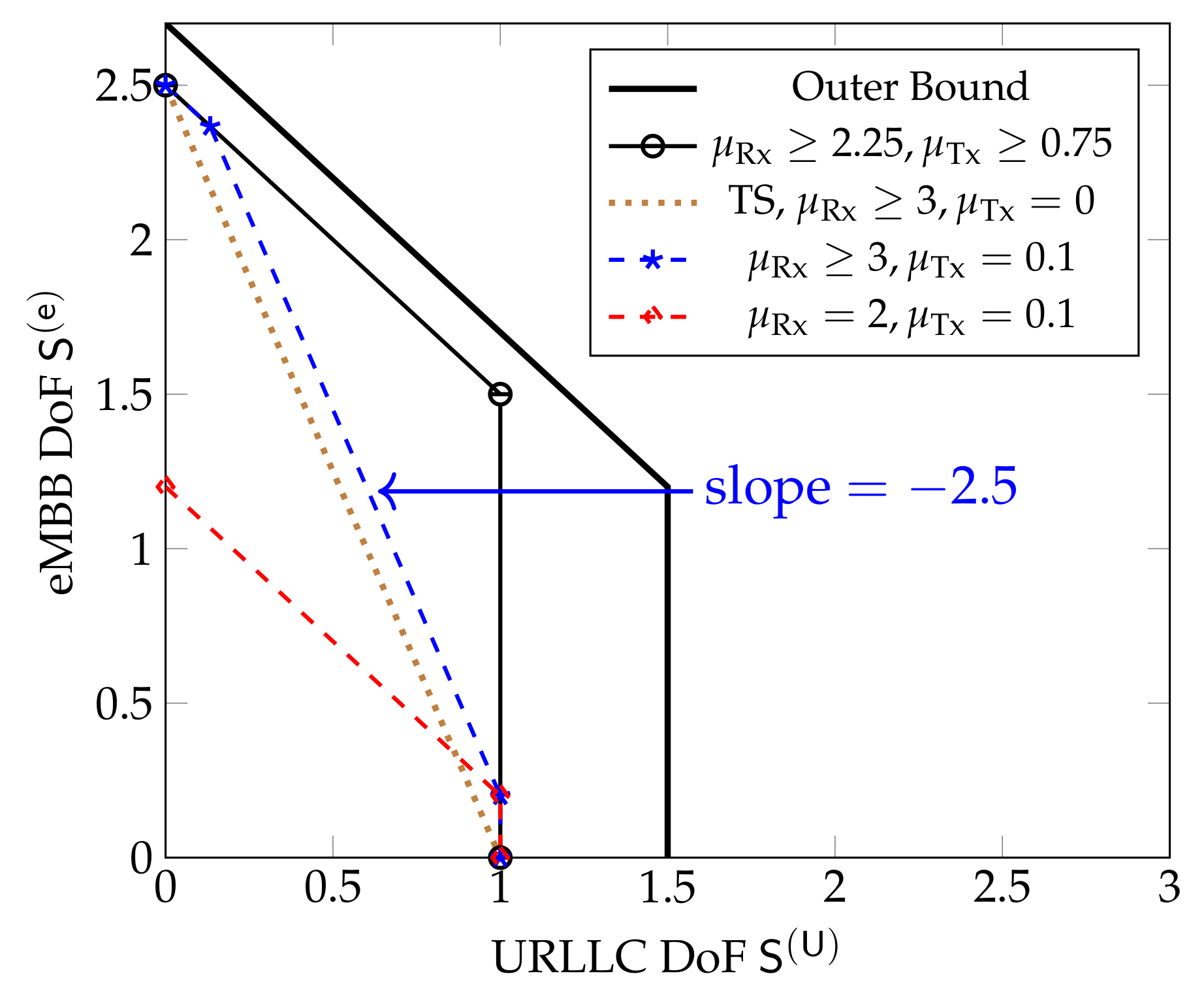
Figure 12 shows inner and outer bounds on the DoF region for the sectorized hexagonal model when . We notice that when both and are above given thresholds, , then the combined scheme integrating both URLLC and eMBB messages in Section 5.3 simultaneously achieves maximum URLLC DoF and maximum sum-DoF. If only one of the two cooperation prelogs is very high but the other one small, the scheme achieves maximum sum-DoF only for small URLLC DoFs. The reason is that the integrated scheme in Section 5.3 that jointly sends URLLC and eMBB messages inherently requires both Tx- and Rx-cooperation of sufficiently high cooperation prelogs, whereas Tx- or Rx-cooperation are sufficient for the scheme that sends only eMBB messages.
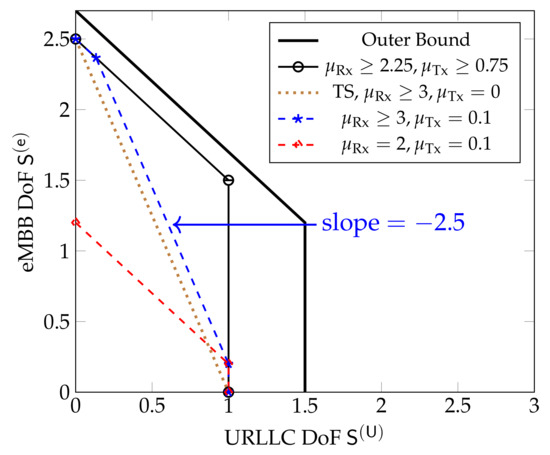
Figure 12.
Inner and outer bounds on the DoF region for the sectorized hexagonal model for and different values of and . The brown dotted line indicates the pure scheduling performance.
To summarize, for all three considered network models the joint scheme in Section 5.3 that integrates both URLLC and eMBB messages achieves maximum sum-DoF at high (or maximum) URLLC DoFs whenever the cooperation rates are sufficiently large. In this case, the stringent delay constraints on the URLLC messages do not harm the overall system performance. For smaller cooperation rates either the maximum sum-DoF is decreased or it is the same as with high cooperation prelogs but can only be achieved for small URLLC DoFs.
The described integrated coding scheme inherently requires at least a single cooperation round both at the Tx-side as well as at the Rx-side. The work in [65] also considered a scenario with only Rx- or only Tx-cooperation. It was shown that when only Rxs or only Txs can cooperate, then the ideal performance in (34) is not possible. Instead for sufficiently large cooperation rates the DoF region is given by the set of all rate-pairs satisfying [65]
The maximum sum-DoF is thus not decreased compared to a scenario with Tx- and Rx-cooperation. However, this maximum sum-DoF is only achievable for URLLC DoF . We conclude that the stringent delay constraint inherently limits the overall system performance for moderate or large URLLC DoFs when only Rxs can cooperate. In fact, in this regime, increasing the URLLC DoF by requires decreasing the eMBB DoF by and the sum-DoF by . Similar conclusions also hold for smaller cooperation prelogs and even in the non-asymptotic regime of finite powers [65].
5.5. Random User Activities
In practical systems, URLLC messages (and sometimes even eMBB messages) arrive in a random and bursty fashion and consequently in any given block, some Txs do not have an URLLC message to transmit. We consider the random user-activity and random arrival model proposed in [62], where each Tx is active with probability , independent of all other Txs. If a Tx is active, it sends an eMBB message to its corresponding Rx, and moreover, with probability , it also sends an additional URLLC message. Both the activity and arrival realizations are assumed to be known to all terminals in the network.
The DoF of all URLLC messages in the system is fixed and given by , whereas the eMBB DoF can vary over the variuos eMBB messages, and the quantity of interest is the expected average DoF over all eMBB messages. (Similarly to the BC scenario in Section 4, the expected average eMBB DoF accounts for the possibility that eMBB messages are sent over multiple URLLC arrival blocks.) The same random-user activity model (but without mixed delays and random message arrivals) was already considered in [66,67,68], where it was observed that under this model the networks considered in Figure 9 decomposes into non-interfering subnets.
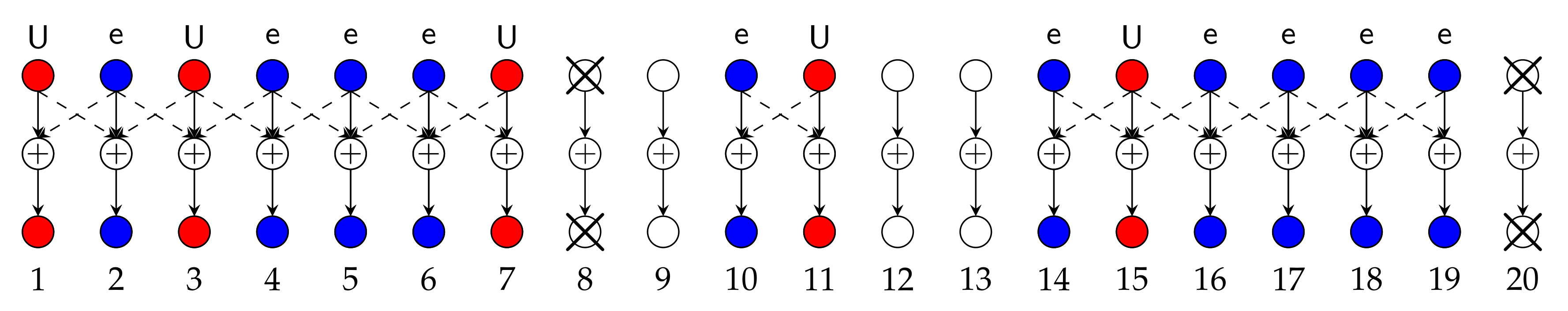
The same decomposition happens in the mixed-delay and random message arrivals model. As a consequence, an independent instance of the schemes in Section 5.3 should be applied to each subnet, where the schemes however have to be further adapted to the random URLLC message arrival situation. In particular, the scheduling (choices of sets ) needs to be adapted to the actual URLLC messages present in a subnet. The work in [62] proposes such a new scheduling approach, which on Wyner’s linear symmetric network time-shares between a scheduling that sends URLLC messages at odd Txs and a second scheduling that sends URLLC messages at even Txs. (This allows us to achieve a symmetric URLLC DoF over all users having a URLLC message to send.) The scheduling for odd URLLC Txs is illustrated in Figure 13 for Wyner’s linear symmetric model and specific realizations of the user activities and URLLC message arrivals. In the presented example, Txs 9, 12, 13 are inactive and Txs 1, 3, 7, 11, and 15 have an URLLC message to send. The network thus decomposes into three subnets: the first includes Tx/Rx pairs 1–8, the second includes Tx/Rx pairs 10–11, and the third includes Tx/Rx pairs 14–20. In each subnet, an independent instance of the integrated scheme of Section 5.3 is applied, but where the eMBB message at Tx 19 is treated as URLLC messages to comply with the scheme. In particular, Txs 8 and 20 are silenced because the maximum allowed cooperation delay equals , and Txs/Rxs 4 and 16 act as master Txs/Rxs in the CoMP scheme.
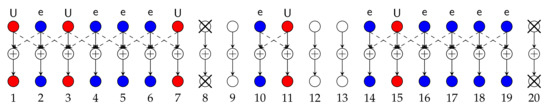
Figure 13.
Wyner’s symmetric linear network with random user activity and random arrival. .
For sufficiently large cooperation rates, the approach in [62] achieves all DoF pairs satisfying
where
By means of an information-theoretic converse, it can be shown that all DoF pairs not satisfying (36) and
cannot lie in the DoF region. Constraints (36) and (39) thus provide an outer bound on the DoF region. Notice that this outer bound and the inner bound given by (36) and (37) only differ in the factors, or 1, preceding the URLLC DoF in the bounds (37) and (39), respectively. These factors are close whenever , and as a consequence also the presented inner and outer bounds are close. For small values of the factors are already close for . Moreover, for small values of and , the right-hand sides of (37) and (39), are approximately equal to , irrespective of D. This indicates that for small values of , increasing the number of cooperation rounds D beyond 4 (and thus further increasing the delay of eMBB messages) does not improve the DoF region of the system. The reason behind this phenomenon is that a large number of cooperation rounds D is only useful in subnets with a large number of consecutive active Txs, and such subnets are very rare when the random user-activity probability is small.
Notice further that by (36), the maximum URLLC DoF both in the inner and outer bounds is , because each Tx sends an URLLC message with probability and in the deterministic setup of Section 5.4, the maximum URLLC DoF is . Notice also that all bounds (36)–(39) increase with the activity parameter . The maximum eMBB DoF in the inner and outer bounds is . In the limit as , it is thus given by , and simply represents the expected fraction of active users. For finite D, the eMBB DoF decreases because to avoid interference to propagate, some of the Txs have to be silenced as in the scheme of Section 5.3. The term thus describes the expected fraction of active but silenced Txs.
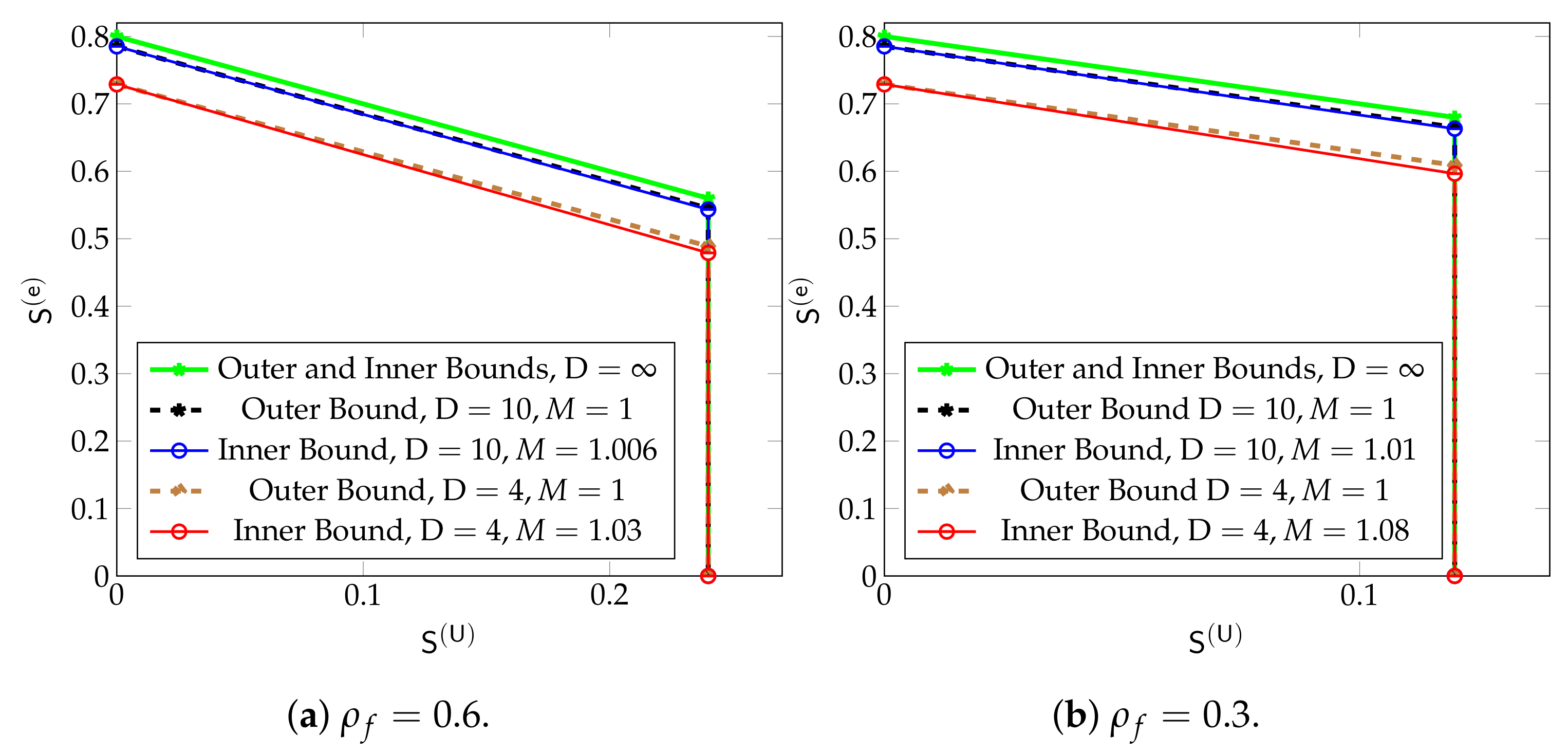
Figure 14, illustrate the inner and outer bounds in (36)–(39) for different values of , and D. The most interesting part of the plots is the upper side of the trapezoids (the side lying opposite the two right angles). The slope of this line, which is for the outer bounds and for the inner bounds, describes the penalty in maximum eMBB DoF incurred when one increases the URLLC Dof . Thus, on the outer bounds, increasing by decreases the maximum by and thus the sum DoF stays constant for all values of . On the inner bounds, the maximum eMBB DoF is decreased by when is increased by and the sum DoF thus decreases by .
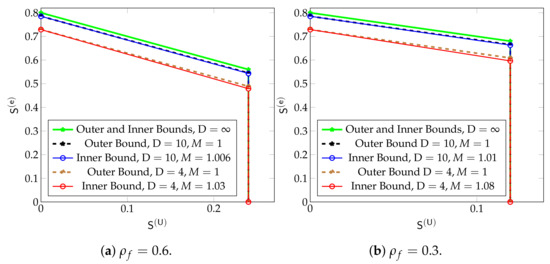
Figure 14.
Inner and outer bounds on the DoF region for and different values of D.
A similar model, but with only Rx-cooperation was studied in [63] for Wyner’s soft-handoff model, Wyner’s linear symmetric model, and the hexagonal model. Similarly to the setup with deterministic user activities and arrivals, with only Rx-cooperation but no Tx-cooperation the stringent delay requirement on URLLC messages harm the overall performance of the system and maximum sum DoF is only achieved when transmitting only eMBB messages. For networks with regular interference structures as in Figure 9 and when , e.g., because URLLC messages are rare, it was shown in [63] that DoF pairs satisfying the following equality are achievable
for and ℓ denoting the number of interference signals experienced at each Rx. (For example, for Wyner’s linear symmetric network and for the hexagonal model ).
5.6. Summary
This section considered cooperative interference networks where only eMBB messages can profit from these cooperation links, but not URLLC messages because they have to be transmitted and decoded without further due. A general coding scheme was presented that manages to exploit the cooperation links for the transmission of eMBB messages in a way that allows us to attain the optimal overall performance (sum DoF) of the system despite the transmission of URLLC messages. Achieving this performance requires cooperation both at the Tx and Rx side, one of the two is not sufficient. Moreover, a careful scheduling of URLLC and eMBB messages to users had to be performed. In practice this scheduling is performed at a system level in the sense that applications randomly generate URLLC messages. The proposed scheme in [62] was adapted to such random and bursty arrivals of the URLLC messages, with only a small penalty in overall system performance.
6. Cloud Radio Access Networks (C-RANs)
6.1. Introduction
In this section we consider cloud radio access networks (C-RANs) where BSs are connected to a cloud processor via high-rate fronthaul links and in the uplink communication all transmitted messages are jointly decoded at the central processor so as to be able to alleviate the effect of interference [12]. URLLC messages are however not compatible with this new architecture as they have to be decoded directly at the BSs because communication over an additional hop to the cloud processor would violate their stringent delay constraints. As in the previous sections, we wish to investigate how this restriction affects the overall performance of the systems, and more specifically the sum-rates and rate pairs can simultaneously be achieved for URLLC and eMBB transmissions.
This section reviews two pieces of work on C-RAN with mixed-delay traffic. The work in [69], discussed in Section 6.2 considers a fading network and focuses on an information-theoretic discussion of the problem comparing inner and outer bounds on the fundamental performance limits of such systems. The work in [70,71], discussed in Section 6.3, takes a communication-theoretic approach. It decomposes communication in minislots and then compares performance of different communication strategies. In this latter work, the network is assumed static.
6.2. Fading C-RAN Model
The work in [69] considers the uplink of a C-RAN, and models the network from the mobile users to the BSs by an i.i.d. fading Wyner soft-handoff model, see Figure 15. That means, BSs are aligned on a line and each cell contains a single mobile user. This latter assumption stems again from the orthogonal frequency access applied by various mobile users in a cell. In Wyner’s soft-handoff model, mobile users are assumed to be located on cell borders and thus interfere only on the communication in this neighbouring and closeby cell. At a given time , the signal received at any BS is thus described as
where and are the signals sent by mobile users k and at time t; are i.i.d standard Gaussian noise; and the sequence of channel coefficients
is i.i.d. over time and distributed according to a given -tuple distribution . This -tuple distribution is the marginal distribution of a given stationary and ergodic process satisfying and . The fading coefficients are known perfectly at BS k but not at the mobile users.
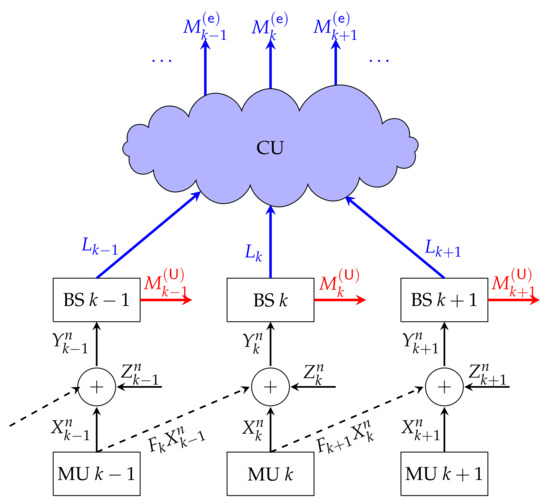
Figure 15.
C-RAN with URLLC and eMBB transmissions and the mobile-to-BS network modeled by Wyner’s soft-handoff model.
Each mobile user k sends both an URLLC message and an eMBB message . It thus produces its channel inputs as , and so that they satisfy an average block-power constraint . URLLC messages are directly decoded at the BSs based on the observed signals in (41). eMBB messages are decoded at the cloud processor, which perfectly observes the symbols sent over the fronthaul links by the BSs, where each BS k generates its symbols by employing a compression function to its observed outputs . The compression has to account for the capacity of the fronthaul links, which is assumed to be for each link, where is termed the fronthaul prelog.
For the described model, ref. [69] characterizes the set of all achievable average expected URLLC and eMBB DoFs (across users and fadings) as
The entire DoF region can be achieved by a resource scheduling approach that time-shares URLLC and eMBB transmissions. Notice that the eMBB DoF is limited by the fronthaul prelog because all eMBB messages have to be decoded at the cloud center. For small fronthaul prelogs this restriction limits the DoF of the system, which can be improved by allowing BSs to also decode part of the eMBB messages.
As can be inferred from (43), the DoF region of the described C-RAN does not depend on the fading processes and . This contrasts the behaviour at finite powers where the set of achievable average URLLC and eMBB rates depends on the law of this fading process, as can be seen in Figure 16. The performance described in this Figure 16 is attained by a superposition coding scheme, and significantly improves over a pure scheduling scheme. We further notice from the figure that for small values of URLLC rates , when increases by , then the maximum eMBB rate decreases approximately by the same amount , and thus the sum-rate remains constant. For larger values of , the maximum decreases approximately by if is increased by . Thereby the loss is larger for random than for static fading coefficients.
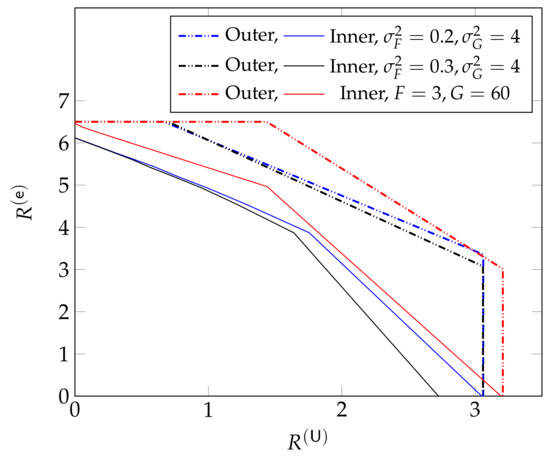
Figure 16.
Inner and outer bounds on the achievable and rate region presented in [69] for , , Gaussian i.i.d. fadings of variances and or for constant non-time varying fadings and .
6.3. Static CRAN Model with Slotted Communication
Mixed delay constraints in C-RANs were also studied in [70], where on a system-wide level communication is divided into minislots. In each minislot, each mobile user generates an URLLC message with probability q and attempts to send it over the network during the next minislot that is dedicated to URLLC communication. If a user generates multiple URLLC messages before the next URLLC minislot, it drops all but one URLLC message, which is then sent in this minislot. eMBB messages are sent over multiple minislots and share the available resources in eMBB slots. Moreover, in [70], URLLC communication is assumed to be from mobile users close to the BSs, and their communication does not suffer from intercell-interference. eMBB users are assumed on the network border as in [69] and communication suffers from intercell interference as described by Wyner’s symmetric model.
The performances of different coding schemes are compared in [70]. In all the schemes, eMBB messages are transmitted using standard multi-access codes, since they are jointly decoded at the cloud processor. URLLC messages are transmitted using standard Gaussian codebooks. If eMBB and URLLC messages are sent in the same slots, then eMBB communication (which lasts several minislots) is considered as noise in the decoding of URLLC messages.
- OMA: URLLC and eMBB messages are sent using orthogonal multiaccess (OMA), i.e., a pure scheduling approach where the minislots dedicated for URLLC and eMBB communications are disjoint. Specifically, here every -th minislot is dedicated for URLLC transmission and the other minislots for eMBB transmissions.
- NOMA–puncturing: eMBB and URLLC messages are sent using non-orthogonal multiaccess (NOMA), i.e., eMBB and URLLC are sent over the same minislots. In particular, URLLC messages are transmitted in the minislot following their generation. To avoid this URLLC communication interfering with eMBB communication, BSs compress only the signals they receive in minislots where no URLLC communication is taking place from their corresponding mobile user.
- NOMA–treating URLLC as noise: eMBB and URLLC messages are sent using NOMA. URLLC communication is treated as noise for eMBB decoding. Therefore, BSs compress all their output signals, and send all this compression information to the cloud processor.
- NOMA–SIC: As in the previous item, except that BSs perform successive interference cancellation (SIC) on their decoded URLLC messages. That means, if URLLC decoding is successful, they subtract the URLLC signal from their outputs before compressing it for transmission to the cloud processor.
The performance of eMBB transmissions is measured by the information-theoretic rate that is achievable in the asymptotic regime of large blocklengths. URLLC transmissions are performed over single minislots and thus of much smaller blocklength. Their performances are measured using a finite blocklength rate-expression [58]
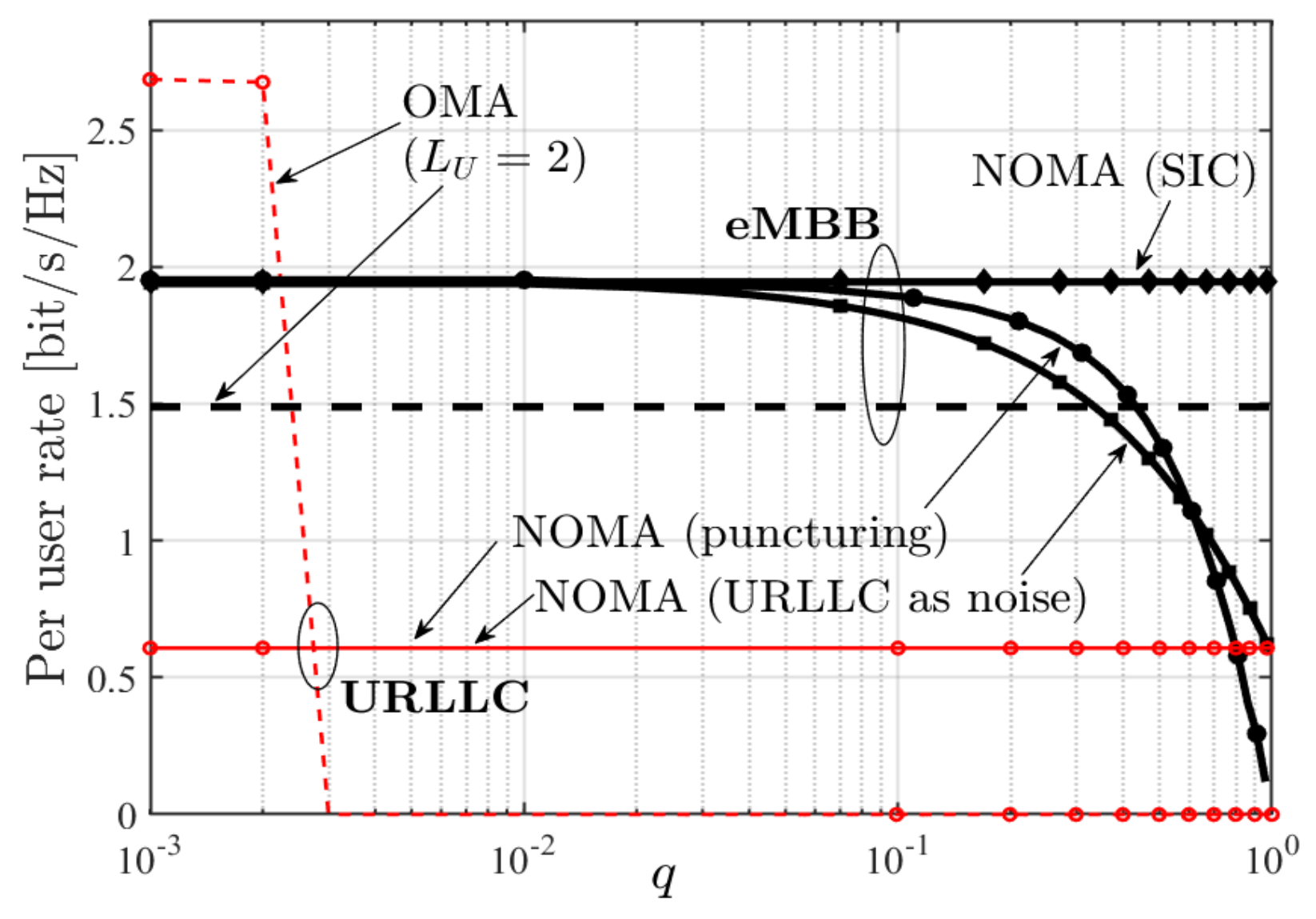
where denotes the interference power at a BS and has to be chosen sufficiently small so that the overall error probability (including the packet drops in case of OMA) does not exceed a desired threshold. Figure 17 compares the performances of these schemes in function of the URLLC message generation probability q. We observe that for the OMA approach performance degenerates quickly even for because the probability of URLLC message drop is too large. The URLLC performance is identical for all three NOMA approaches. The NOMA SIC approach achieves the best performance for the eMBB message.
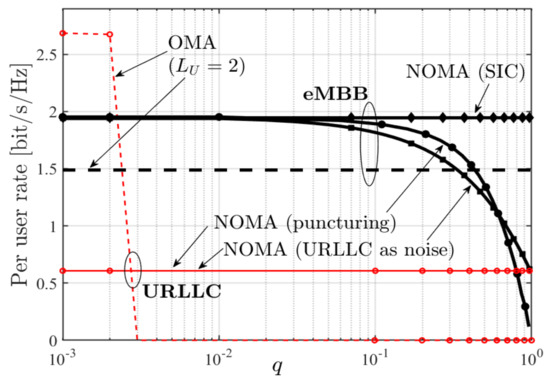
Figure 17.
eMBB and URLLC per-user rates under OMA with and NOMA for different decoding strategies as function of q in C-RAN [70].
In [71], these results are also extended to the downlink scenario. In this case, eMBB messages are created at the cloud processor and can profit from joint encoding to mitigate interference. URLLC messages are created directly at the BSs and their communications thus suffer from interference.
6.4. Summary
The last setup considered in this paper are C-RAN architectures where eMBB messages are jointly decoded at the cloud processor, whereas URLLC messages have to be decoded immediately at the BSs. Similarly to the P2P, BC, and cooperative network scenarios, for moderate powers, the overall system performance of the C-RAN with mixed-delay traffic in Section 6.2 decreases for large URLLC rates. This degradation seems to be more pronounced in fading environments than in static Gaussian environments. In the asymptotic high-power regime, however such a degradation is not observed, and at small URLLC DoFs , the sum-DoF is even increasing in . In certain scenarios it is thus possible to improve overall system performance by decoding part of the eMBB messages directly at the BSs and not at the cloud processor. Section 6.3 considers a non-fading environment and random generation of URLLC messages, for which it applies finite-blocklength performance measures. It is shown that for moderate or high URLLC generation rates, a NOMA scheme that first subtracts the contribution of the URLLC communication from the receive signals at the BSs, and then compresses and sends these differences over the fronhaul links, outperforms similar OMA and NOMA schemes.
7. Conclusions and Outlook
In this survey, we have reviewed joint coding schemes that integrate transmissions of URLLC and eMBB traffic and compared them to pure scheduling schemes in terms of rate, error probability and degree of freedom pairs that the schemes simultaneously achieve for URLLC and eMBB messages. A wide range of communication scenarios including P2P channels, BCs, cooperative interference networks, and C-RANs have been considered. The results have shown that joint coding schemes can significantly outperform the standard scheduling approach. As we have seen, in certain scenarios optimal system performance can be achieved under any URLLC rate. For other scenarios however, a large URLLC rate penalizes the overall system performance, showing that in these situations the stringent URLLC decoding constraint degrades system performance.
We conclude this survey with some lines of potential future research.
- The presented works have considered perfect channel state information (CSI) at the Rxs, and sometimes even at the Txs, where naturally CSI is more difficult to obtain. An interesting model for mixed-delay traffic is where CSI can be used for encoding and decoding of eMBB messages but not of URLLC messages [72,73]. The motivation behind such a model is that the processing of pilot and feedback signals required to gather CSI at the Rxs and Txs introduces inadmissibly large delays for URLLC communication.
- So far, firm finite-blocklength results for mixed-delay traffic have been mostly limited to the P2P case; see [74] for an exception. Extensions to multi-user network scenarios is an important future research direction.
- In practical scenarios, both URLLC and eMBB messages are randomly generated by higher layer applications. This naturally leads to potential bottlenecks where not-yet-transmitted messages have to be buffered, similar to [75]. In this context, a thorough analysis of the behavior of the buffered contents and the required size of these buffers, is of significant practical interest.
- Other heterogeneous requirements on URLLC and eMBB traffic could be introduced in the study of mixed-delay traffic. For example, different security requirements as in [76] or different reliability constraints as in [21].
- Langberg and Effros [77] introduced the notion of time-rate region which describes the fraction of the blocklengths required for the transmissions of the various messages to the different Rxs in a network scenario under given message communication rates. A natural question is whether the interference mitigation techniques discussed in this survey can improve the inner bound on the time-rate region for general networks obtained in [77], which is obtained through a reduction to standard network information theory problems.
- Finally, mixed-delay traffic where different messages are transmitted over different blocklengths is inherently also connected to variable-rate and variable-length coding [20,77,78,79]. For example, the variable-rate channel coding framework of [78] includes the variable-to-variable scenario where depending on the specific system configuration and channel state realization, a receiver can decode a message of variable-size (similarly to the broadcast approaches in Sections III-B and IV) and decoding is performed after a variable number of channel uses. An interesting line of future research is to extend this scenario to multiple messages and mixed-delay traffic where URLLC and eMBB messages are decoded with different delays, and to study the four-dimensional tradeoff between URLLC and eMBB variable-rates and variable-delays.
Author Contributions
The authors contributed equally to this work. All authors have read and agreed to the published version of the manuscript.
Funding
This research is supported by INRIA Nokia Bell Labs ADR “Network Information Theory”, the French National Agency for Research (ANR) under grant ANR-16-CE25-0001-ARBURST, the European Union’s Horizon 2020 Research And Innovation Program, grant agreements no. 715111, the US-Israel Binational Science Foundation (BSF) under grant BSF-2018710, and the U.S. National Science Foundation (NSF) within the Israel-US Binational program under grant CCF-1908308.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The works of H.N., M.E. and J.-M.G. have been supported by INRIA Nokia Bell Labs ADR “Network Information Theory” and by the French National Agency for Research (ANR) under grant ANR-16-CE25-0001-ARBURST. The work of M.W. has been supported by the European Union’s Horizon 2020 Research And Innovation Program, grant agreements no. 715111. The work of S.S. (Shitz) has been supported by the US-Israel Binational Science Foundation (BSF) under grant BSF-2018710. The work of H.V.P. has been supported by the U.S. National Science Foundation (NSF) within the Israel-US Binational program under grant CCF-1908308.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Tataria, H.; Shafi, M.; Molisch, A.F.; Dohler, M.; Sjöland, H.; Tufvesson, F. 6G wireless systems: Vision, requirements, challenges, insights, and opportunities. Proc. IEEE 2021, 109, 1166–1199. [Google Scholar] [CrossRef]
- Popovski, P.; Trillingsgaard, K.F.; Simeone, O.; Durisi, G. 5G wireless network slicing for eMBB, URLLC, and mMTC: A communication-theoretic view. IEEE Access 2018, 6, 55765–55779. [Google Scholar] [CrossRef]
- Popovski, P.; Stefanović, Č.; Nielsen, J.J.; de Carvalho, E.; Angjelichinoski, M.; Trillingsgaard, K.F.; Bana, A. Wireless access in ultra-reliable low-latency communication (URLLC). IEEE Trans. Commun. 2019, 67, 5783–5801. [Google Scholar] [CrossRef]
- Ge, X. Ultra-reliable low-latency communications in autonomous vehicular networks. IEEE Trans. Veh. Technol. 2019, 68, 5005–5016. [Google Scholar] [CrossRef]
- Shirvanimoghaddam, M.; Mohamadi, M.S.; Abbas, R.; Minja, A.; Yue, C.; Matuz, B.; Han, G.; Lin, Z.; Li, Y.; Johnson, S.; et al. Short block-length codes for ultra-reliable low latency communications. IEEE Commun. Mag. 2019, 57, 130–137. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, J.; Poor, H.V. Statistical QoS-driven energy-efficiency optimization for URLLC over 5G mobile wireless networks in the finite blocklength regime. In Proceedings of the Conference on Information Sciences and Systems, Baltimore, MD, USA, 20–22 March 2019; pp. 1–6. [Google Scholar]
- Bairagi, A.K.; Munir, M.S.; Alsenwi, M.; Tran, N.H.; Alshamrani, S.S.; Masud, M.; Han, Z.; Hong, C.S. Coexistence mechanism between eMBB and URLLC in 5G wireless networks. IEEE Trans. Commun. 2021, 69, 1736–1749. [Google Scholar] [CrossRef]
- Xiao, K.; Liu, X.; Han, X.H.; Hao, P.; Zhang, J.; Zhou, D.; Wei, X. Flexible multiplexing mechanism for coexistence of URLLC and eMBB services in 5G networks. ZTE Commun. 2021, 19, 82–90. [Google Scholar]
- Bennis, M.; Debbah, M.; Poor, H.V. Ultrareliable and low-latency wireless communication: Tail, risk, and scale. Proc. IEEE 2018, 106, 1834–1853. [Google Scholar] [CrossRef]
- Aleksandra, C.; Lehrmann, C.H.; Ying, Y.; Lara, S.; Georgios, K.; Stübert, B.M.; Lars, D. 6G wireless networks: Vision, requirements, architecture, and key technologies. IEEE Veh. Technol. Mag. 2019, 14, 28–41. [Google Scholar]
- Aleksandra, C.; Lehrmann, C.H.; Ying, Y.; Lara, S.; Georgios, K.; Stübert, B.M.; Lars, D. Cloud RAN for mobile networks—A technology overview. IEEE Commun. Surv. Tutor. 2015, 17, 405–426. [Google Scholar]
- Peng, M.; Li, Y.; Zhao, Z.; Wang, C. System architecture and key technologies for 5G heterogeneous cloud radio access networks. IEEE Netw. 2015, 29, 6–14. [Google Scholar] [CrossRef]
- Zhang, J.; Xu, X.; Zhang, K.; Zhang, B.; Tao, X.; Zhang, P. Machine learning based flexible transmission time interval scheduling for eMBB and uRLLC coexistence scenario. IEEE Access 2019, 7, 65811–65820. [Google Scholar] [CrossRef]
- Bairagi, A.K.; Munir, M.S.; Alsenwi, M.; Tran, N.H.; Hong, C.S. A matching based coexistence mechanism between eMBB and URLLC in 5G wireless networks. In Proceedings of the 34th ACM/SIGAPP Symposium on Applied Computing, New York, NY, USA, 8–12 April 2019. [Google Scholar]
- Elsayed, M.; Erol-Kantarci, M. AI-enabled radio resource allocation in 5G for URLLC and eMBB users. In Proceedings of the IEEE 2nd 5G World Forum (5GWF), Dresden, Germany, 30 September–2 October 2019; pp. 590–595. [Google Scholar]
- Alsenwi, M.; Tran, N.H.; Bennis, M.; Pandey, S.R.; Bairagi, A.K.; Hong, C.S. Intelligent resource slicing for eMBB and URLLC coexistence in 5G and beyond: A deep reinforcement learning based approach. IEEE Trans. Wirel. Commun. 2021, 20, 4585–4600. [Google Scholar] [CrossRef]
- Khan, H.; Butt, M.M.; Samarakoon, S.; Sehier, P.; Bennis, M. Deep learning assisted CSI estimation for joint URLLC and eMBB resource allocation. In Proceedings of the IEEE International Conference on Communications Workshops (ICC Workshops), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Li, J.; Zhang, X. Deep reinforcement learning-based joint scheduling of eMBB and URLLC in 5G networks. IEEE Wirel. Commun. Lett. 2020, 9, 1543–1546. [Google Scholar] [CrossRef]
- Almekhlafi, M.; Arfaoui, M.A.; Elhattab, M.; Assi, C.; Ghrayeb, A. Joint scheduling of eMBB and URLLC services in RIS-aided downlink cellular networks. In Proceedings of the International Conference on Computer Communications and Networks (ICCCN), Athens, Greece, 19–22 July 2021; pp. 1–9. [Google Scholar]
- Huleihel, W.; Steinberg, Y. Channels with cooperation links that may be absent. IEEE Trans. Inf. Theory 2017, 63, 5886–5906. [Google Scholar] [CrossRef]
- Keresztfalvi, T.; Lapidoth, A. Semi-robust communications over a broadcast channel. IEEE Trans. Inf. Theory 2019, 65, 5043–5049. [Google Scholar] [CrossRef]
- Keresztfalvi, T.; Lapidoth, A. Multiplexing zero-error and rare-error communications over a noisy channel. IEEE Trans. Inf. Theory 2019, 65, 2824–2837. [Google Scholar] [CrossRef]
- Blackwell, D.; Breiman, L.; Thomasian, A.J. The capacities of certain channel classes under random coding. Ann. Math. Stat. 1960, 31, 558–567. [Google Scholar] [CrossRef]
- Csiszár, I.; Narayan, P. Capacity and decoding rules for classes of arbitrarily varying channels. IEEE Trans. Inf. Theory 1989, 35, 752–769. [Google Scholar] [CrossRef]
- Lapidoth, A.; Narayan, P. Reliable communication under channel uncertainty. IEEE Trans. Inf. Theory 1998, 44, 2148–2177. [Google Scholar] [CrossRef]
- Morais, F.Z.; da Costa, C.A.; Alberti, A.M.; Both, C.B.; Righi, R.R. When SDN meets C-RAN: A survey exploring multi-point coordination, interference, and performance. J. Netw. Comput. Appl. 2020, 162, 102655. [Google Scholar] [CrossRef]
- Zhang, S. An overview of network slicing for 5G. IEEE Wirel. Commun. 2019, 26, 111–117. [Google Scholar] [CrossRef]
- Hossain, E.; Hasan, M. 5G cellular: Key enabling technologies and research challenges. IEEE Instrum. Meas. Mag. 2015, 18, 11–21. [Google Scholar] [CrossRef]
- Sun, Y.; Peng, M.; Zhou, Y.; Huang, Y.; Mao, S. Application of machine learning in wireless networks: Key techniques and open issues. IEEE Commun. Surv. Tutor. 2019, 21, 3072–3108. [Google Scholar] [CrossRef]
- Mao, Y.; Dizdar, O.; Clerckx, B.; Schober, R.; Popovski, P.; Poor, H.V. Rate-splitting multiple access: Fundamentals, survey, and future research trends. arXiv 2022, arXiv:2201.03192. [Google Scholar]
- Shariatmadari, H.; Iraji, S.; Jantti, R.; Popovski, P.; Li, Z.; Uusitalo, M.A. Fifth-generation control channel design: Achieving ultra reliable low-latency communications. IEEE Veh. Technol. Mag. 2018, 13, 84–93. [Google Scholar] [CrossRef]
- Vaezi, M.; Azari, A.; Khosravirad, S.R.; Shirvanimoghaddam, M.; Azari, M.M.; Chasaki, D.; Popovski, P. Cellular, wide-area, and non-terrestrial IoT: A survey on 5G advances and the road towards 6G. arXiv 2021, arXiv:2107.03059. [Google Scholar] [CrossRef]
- Makki, B.; Chitti, K.; Behravan, A.; Alouini, M.S. A survey of NOMA: Current status and open research challenges. IEEE Open J. Commun. Soc. 2020, 1, 179–189. [Google Scholar] [CrossRef]
- Vaezi, M.; Amarasuriya, G.; Liu, Y.; Arafa, A.; Fang, F.; Ding, Z. Interplay between NOMA and other emerging technologies: A survey. IEEE Trans. Cogn. Commun. Netw. 2019, 5, 900–919. [Google Scholar] [CrossRef]
- Dai, L.; Wang, B.; Ding, Z.; Wang, Z.; Chen, S.; Hanzo, L. A survey of non-orthogonal multiple access for 5G. IEEE Commun. Surv. Tutor. 2018, 20, 2294–2323. [Google Scholar] [CrossRef]
- Islam, S.M.R.; Avazov, N.; Dobre, O.A.; Kwak, K. Power-domain non-orthogonal multiple access (NOMA) in 5G systems: Potentials and challenges. IEEE Commun. Surv. Tutor. 2017, 19, 721–742. [Google Scholar] [CrossRef]
- Veeravalli, V.V.; Gamal, A.E. Interference Management in Wireless Networks: Fundamental Bounds and the Role of Cooperation; Cambridge University Press: Cambridge, UK, 2018. [Google Scholar]
- Cover, T.M.; Tomas, J.A. Elements of Information Theory; John Wiley & Sons: Hoboken, NJ, USA, 2012. [Google Scholar]
- Cover, T. Broadcast channels. IEEE Trans. Inf. Theory 1972, 18, 2–14. [Google Scholar] [CrossRef]
- Costa, M. Writing on dirty paper (Corresp.). IEEE Trans. Inf. Theory 1983, 29, 439–441. [Google Scholar] [CrossRef]
- Erez, U.; Brink, S.t. A close-to-capacity dirty paper coding scheme. IEEE Trans. Inf. Theory 2005, 51, 3417–3432. [Google Scholar] [CrossRef]
- Cohen, A.S.; Lapidoth, A. Generalized writing on dirty paper. In Proceedings of the IEEE International Symposium on Information Theory, Lausanne, Switzerland, 30 June–5 July 2002; p. 227. [Google Scholar]
- Yu, W.; Kwon, T.; Shin, C. Multicell coordination via joint scheduling, beamforming, and power spectrum adaptation. IEEE Trans. Wirel. Commun. 2013, 12, 1–14. [Google Scholar] [CrossRef]
- Chen, J.; Mitra, U.; Gesbert, D. Optimal UAV relay placement for single user capacity maximization over terrain with obstacles. In Proceedings of the IEEE International Workshop on Signal Processing Advances in Wireless Communications, Cannes, France, 2–5 July 2019; pp. 1–5. [Google Scholar]
- Nikbakht, H.; Wigger, M.; Shamai, S. Multiplexing gain region of sectorized cellular networks with mixed delay constraints. In Proceedings of the IEEE International Workshop on Signal Processing Advances in Wireless Communications, Cannes, France, 2–5 July 2019. [Google Scholar]
- Levy, N.; Shamai, S. Clustered local decoding for Wyner-type cellular models. IEEE Trans. Inf. Theory 2009, 55, 4976–4985. [Google Scholar] [CrossRef]
- Zhou, L.; Yu, W. Uplink multicell processing with limited backhaul via per-base-station successive interference cancellation. IEEE J. Sel. Areas Commun. 2013, 31, 1981–1993. [Google Scholar] [CrossRef]
- Simeone, O.; Somekh, O.; Poor, H.V.; Shamai, S. Local base station cooperation via finite-capacity links for the uplink of linear cellular networks. IEEE Trans. Inf. Theory 2009, 55, 190–204. [Google Scholar] [CrossRef]
- Simeone, O.; Levy, N.; Sanderovich, A.; Somekh, O.; Zaidel, B.M.; Poor, H.V.; Shamai, S. Cooperative wireless cellular systems: An information-theoretic view. In Foundations and Trends in Communications and Information Theory; Now Publishers Inc.: Hanover, MA, USA, 2012; Volume 8, pp. 1–177. [Google Scholar]
- Egan, M.; Collings, I.B. Low complexity quantization codebooks for CoMP. In Proceedings of the IEEE International Symposium on Personal, Indoor, and Mobile Radio Communications, London, UK, 8–11 September 2013; pp. 1024–1028. [Google Scholar]
- Cohen, K.M.; Steiner, A.; Shamai, S. The broadcast approach under mixed delay constraints. In Proceedings of the IEEE International Symposium on Information Theory, Cambridge, MA, USA, 1–6 July 2012; pp. 209–213. [Google Scholar]
- Cohen, K.M.; Steiner, A.; Shamai, S. Broadcasting with mixed delay demands. In Proceedings of the IEEE 27th Convention of Electrical and Electronics Engineers in Israel, Eilat, Israel, 14–17 November 2012; pp. 1–5. [Google Scholar]
- Tajer, A.; Steiner, A.; Shamai, S. The broadcast approach in communication networks. Entropy 2021, 23, 120. [Google Scholar] [CrossRef]
- Nikbakht, H.; Egan, M.; Gorce, J.-M. Joint channel coding of consecutive messages with heterogeneous decoding deadlines in the finite blocklength regime. In Proceedings of the IEEE Wireless Communications and Networking Conference, Austin, TX, USA, 10–13 April 2022. [Google Scholar]
- Nikbakht, H.; Egan, M.; Gorce, J.-M. Dirty Paper Coding for Consecutive Messages with Heterogeneous Decoding Deadlines in the Finite Blocklength Regime. [Research Report] Inria—Research Centre Grenoble—Rhône-Alpes. Available online: https://hal.inria.fr/hal-03556888 (accessed on 1 February 2022).
- Erseghe, T. Coding in the finite-blocklength regime: Bounds based on Laplace integrals and their asymptotic approximations. IEEE Trans. Inf. Theory 2016, 62, 6854–6883. [Google Scholar] [CrossRef]
- Cohen, A.; Médard, M.; Shamai, S. Broadcast approach meets network coding for data streaming. arXiv 2022, arXiv:2202.03018v1. [Google Scholar]
- Polyanskiy, Y.; Poor, H.V.; Verdu, S. Channel coding rate in the finite blocklength regime. IEEE Trans. Inf. Theory 2010, 56, 2307–2359. [Google Scholar] [CrossRef]
- Scarlett, J. On the dispersions of the Gel’fand—Pinsker channel and dirty paper coding. IEEE Trans. Inf. Theory 2015, 61, 4569–4586. [Google Scholar] [CrossRef]
- Lin, P.H.; Lin, S.C.; Jorswieck, E.A. Early decoding for Gaussian broadcast channels with heterogeneous blocklength constraints. In Proceedings of the IEEE International Symposium on Information Theory, Melbourne, Australia, 12–20 July 2021; pp. 3243–3248. [Google Scholar]
- Nikbakht, H.; Wigger, M.; Shamai, S. Coordinated multi point transmission and reception for mixed delay traffic. IEEE Trans. Commun. 2021, 69, 8116–8131. [Google Scholar] [CrossRef]
- Nikbakht, H.; Wigger, M.; Shamai, S.; Gorce, J.-M. Cooperative encoding and decoding of mixed delay traffic under random-user activity. In Proceedings of the IEEE Information Theory Workshop, Kanazawa, Japan, 17–21 October 2021; pp. 1–6. [Google Scholar]
- Nikbakht, H.; Wigger, M.; Shamai, S. Random user activity with mixed delay traffic. In Proceedings of the IEEE Information Theory Workshop, Riva del Garda, Italy, 11–14 April 2021. [Google Scholar]
- Jafar, S.A. Interference Alignment: A New Look at Signal Dimensions in a Communication Network; Now Publishers Inc.: Hanover, MA, USA, 2011; Volume 7, pp. 1–134. [Google Scholar]
- Nikbakht, H.; Wigger, M.; Shamai, S. Multiplexing gains under mixed-delay constraints on Wyner’s soft-handoff model. Entropy 2020, 22, 182. [Google Scholar] [CrossRef]
- Somekh, O.; Simeone, O.; Poor, H.V.; Shamai, S. The two-tap input-erasure Gaussian channel and its application to cellular communications. In Proceedings of the Allerton Conference on Communication, Control, and Computing, Monticello, IL, USA, 23–26 September 2008. [Google Scholar]
- Levy, N.; Shamai, S. ‘Information theoretic aspects of users’ activity in a Wyner-like cellular model. IEEE Trans. Inf. Theory 2010, 56, 2241–2248. [Google Scholar] [CrossRef]
- Somekh, O.; Simeone, O.; Poor, H.V.; Shamai, S. Throughput of cellular uplink with dynamic user activity and cooperative base-stations. In Proceedings of the IEEE Information Theory Workshop, Taormina, Italy, 11–16 October 2009. [Google Scholar]
- Nikbakht, H.; Wigger, M.; Hachem, W.; Shamai, S. Mixed delay constraints on a fading C-RAN uplink. In Proceedings of the IEEE Information Theory Workshop, Visby, Sweden, 25–28 August 2019. [Google Scholar]
- Kassab, R.; Simeone, O.; Popovski, P. Coexistence of URLLC and eMBB services in the C-RAN uplink: An information-theoretic study. In Proceedings of the IEEE Global Communications Conference, Abu Dhabi, United Arab Emirates, 9–13 December 2018. [Google Scholar]
- Kassab, R.; Simeone, O.; Popovski, P.; Islam, T. Non-orthogonal multiplexing of ultra-reliable and broadband services in fog-radio architectures. IEEE Access 2019, 7, 13035–13049. [Google Scholar] [CrossRef]
- Wang, J.; Yuan, B.; Huang, L.; Jafar, S.A. GDoF of interference channel with limited cooperation under finite precision CSIT. arXiv 2019, arXiv:1908.00703. [Google Scholar]
- Chan, Y.; Wang, J.; Jafar, S.A. Towards an extremal network theory–robust GDoF gain of transmitter cooperation over TIN. IEEE Trans. Inf. Theory 2020, 66, 3827–3845. [Google Scholar] [CrossRef]
- Mary, P.; Gorce, J.; Unsal, A.; Poor, H.V. Finite blocklength information theory: What is the practical impact on wireless communications? In Proceedings of the IEEE Global Communications Conference, Washington, DC, USA, 4–8 December 2016. [Google Scholar]
- Steiner, A.; Shamai, S. On queuing and multilayer coding. IEEE Trans. Inf. Theory 2010, 56, 2392–2415. [Google Scholar] [CrossRef]
- Zou, S.; Liang, Y.; Lai, L.; Poor, H.V.; Shamai, S. Degraded broadcast channel with secrecy outside a bounded range. IEEE Trans. Inf. Theory 2018, 64, 2104–2120. [Google Scholar] [CrossRef]
- Langberg, M.; Effros, M. Beyond capacity: The joint time-rate region. arXiv 2021, arXiv:2101.12236v1. [Google Scholar]
- Verdu, S.; Shamai, S. Variable-rate channel capacity. IEEE Trans. Inf. Theory 2010, 56, 2651–2667. [Google Scholar] [CrossRef]
- Shulman, N.; Feder, M. Static broadcasting. In Proceedings of the IEEE International Symposium on Information Theory, Sorrento, Italy, 25–30 June 2000. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).