Abstract
Under the framework of computational integral imaging, a multi-image encryption scheme based on the DNA-chaos algorithm is proposed. In this scheme, multiple images are merged to one image by a computational integral imaging algorithm, which significantly improves the efficiency of image encryption. Meanwhile, the computational integral imaging algorithm can merge images at different depth distances, thereby the different depth distances of multiple images can also be used as keys to increase the security of the encryption method. In addition, the high randomness of the chaos algorithm is combined to address the outline effect caused by the DNA encryption algorithm. We have experimentally verified the proposed multi-image encryption scheme. The entropy value of the encrypted image is , whereas the entropy value of the merge image with two input images is , which greatly reduces the relevance of the image. The simulation results also confirm that the proposed encryption scheme has high key security and can protect against various attacks.
1. Introduction
As a basic way of carrying data, the importance of images in the information industry is self-evident. However, there is no doubt that this will raise a lot of privacy concerns if the image information owned by an individual or team is accessed by others. Image encryption is a proven means of solving image security problems [1,2,3,4,5,6]. Encrypted images lack intuitive information about the original image, in other words, the thief cannot obtain any valuable information from the encrypted image, thereby achieving the privacy protection of the image owner. At present, researchers have proposed many methods of image encryption, and optical encryption has attracted much attention in the study of image encryption because of its unique multi-dimensional capabilities, high parallelism and high-speed processing power [7,8,9,10,11,12].
Since Javidi and Refregier proposed the classic optical Dual Random Phase Encoding (DRPE) system in 1995 [13], optical encryption technology began to enter a period of rapid development. Researchers have found that the encryption system based on DRPE technology has some security problems due to its own linear factors [14]; it is vulnerable to selective plaintext attacks. In order to enhance the security of the encryption system, researchers have proposed a series of feasible optical encryption improvement schemes based on DRPE. The improvements are mainly made from the following four aspects: (1) Expansion of optical transformations; (2) Pre-process according to the characteristics of the encrypted image and the purpose of encryption; (3) Improvements of the random phase mask; (4) Non-linear operation. On this basis, more encryption algorithms have been proposed [15,16,17,18,19,20]. It is worth noting that these proposed methods of encrypting objects are all for a single image. Compared with single image encryption, multi-image encryption can process multiple images at a time, which can greatly improve encryption efficiency on the basis of ensuring encryption security.
Computational Integral Imaging (CII), as a well-performing optical imaging system, can achieve a full-color, wide-angle 3D light field display [21,22,23,24,25,26,27]. Integral imaging technology can record image information from multiple perspectives of a scene, which can provide more robustness in the recovery process of image encryption. Researchers have proposed many image encryption methods based on the CII framework, and confirmed that these algorithms have strong robustness [28,29,30]. In addition, computational integral imaging technology can also record scene information at different depths; at the same time [31,32,33], it is possible to achieve the synthesis of multiple images, which provides a new idea for multi-image encryption.
DNA algorithm with vast parallelism, large-scale storage and extraordinary information density is often applied in the study of data encoding, and some DNA-based encoding algorithms were proposed and showed a better performance [34,35,36,37,38,39]. The proposed DNA-based encryption algorithms have two main ideas—one is to explore the impact of different DNA rules on encryption performance, and the other is to improve the performance of DNA encryption by combining other encryption algorithms [40]. There will be an outline effect when DNA encryption algorithm is used, which causes the saliency boundaries of the original image to be seen from the encrypted image clearly. The chaos system possesses a variety of characteristics, such as strong confidentiality, good randomness, a large amount of keys and so on [41,42,43]. In addition, recently, elliptic curves-based image encryption schemes have been considered an alternative to the chaos-based schemes [44,45,46,47]. Therefore, they are widely used in combination with DNA algorithms to improve the performance of encryption systems.
In this paper, a multi-image encryption scheme based on CII using a DNA-chaos encryption algorithm is proposed. Two or more images are merged in different depths using the CII algorithm, which will obtain an Element Image Array (EIA) image, and then the EIA image is encrypted by the DNA-chaos encryption algorithm. Finally, the decrypted image can be reconstructed at different depths to restore the original image. Based on the high security of the DNA-chaos encryption algorithm, EIA data recorded by computational integral imaging technology to ensure the strong robustness and the multi-image merge scheme of different depths further improves the key space by using depth information as the key.
The paper is arranged as follows. In Section 2, we briefly introduce a theoretical analysis of our method, including the CII pickup process, DNA sequence operations, chaos theory, the CII Reconstruction (CIIR) algorithm and entropy analysis theory. A multi-image encryption scheme is proposed in Section 3. In Section 4, we analyze the performance of the proposed multi-image encryption scheme in terms of key security, statistical results, robustness and time analysis. The conclusions reached in this article are presented in Section 5.
2. Previous Theoretical Analysis
2.1. Pickup Original Scene by CII
CII [22] is an advanced optical imaging solution, which is the most promising commercial 3D display technology, and has important research significance in the field of 3D image processing. The modulation of optical information from CII mainly includes two processes—one is the pickup of the original scene, which can obtain the EIA, and the other is the reconstruction of the original scene through EIA. In the pickup of the original scene, an EIA is recorded, and the EIA contains a lot of redundant information about the scene, which can improve the robustness of the encryption scheme for image encryption.
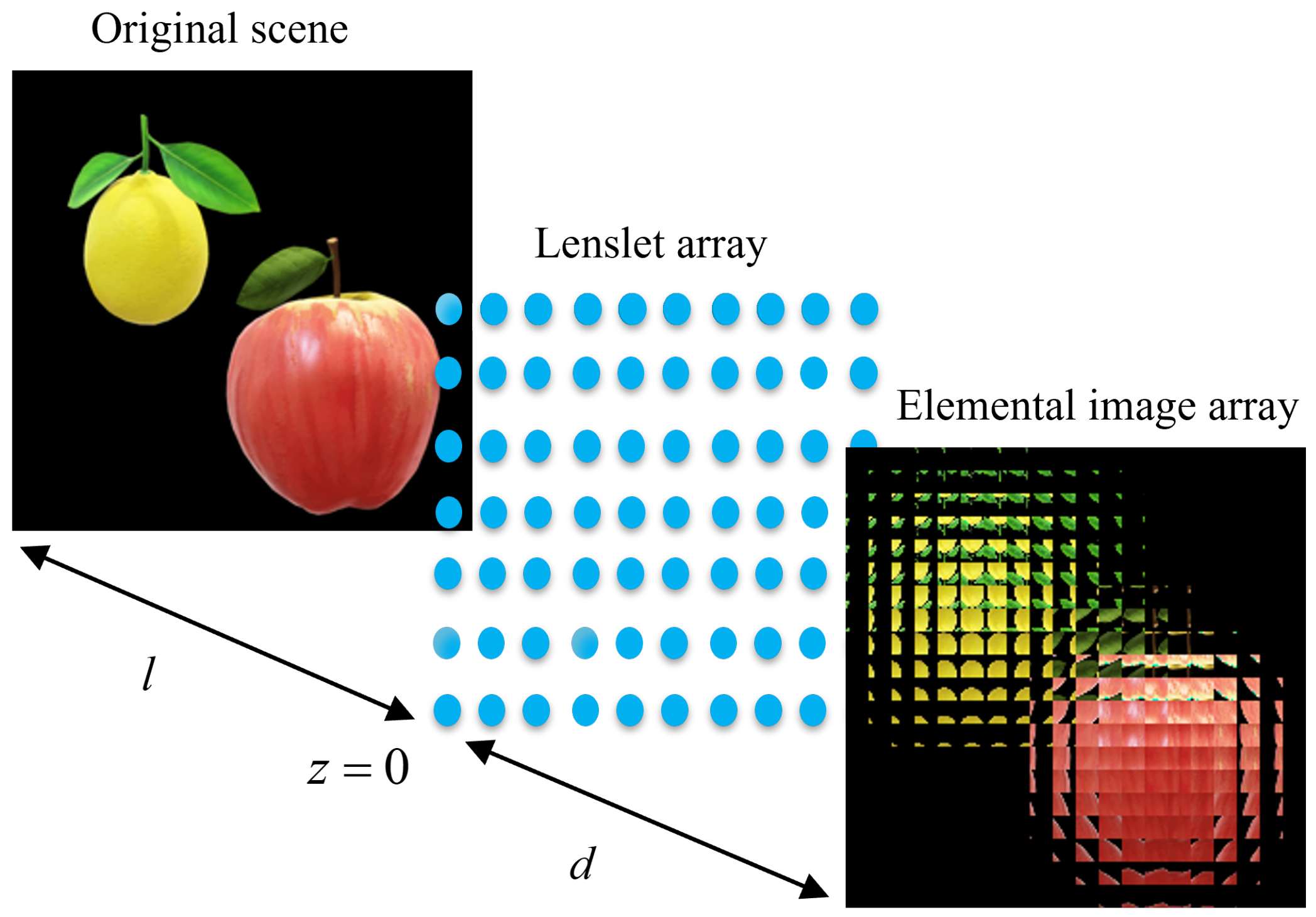
Figure 1 shows the pickup of the original scene by CII algorithm. The original scene is recorded by the sensor as EIA through a lenslet array, and the EIA contains many EIs; each EI represents the encrypted information converted by part of the original scene. Each EI is calculated by [22]:
where x, y and z represent the spatial coordinates of the lenslet array, and the size of the lenslet array determines the number of EIs. represents the size of lens, and the distance from image to lenslet array is l.
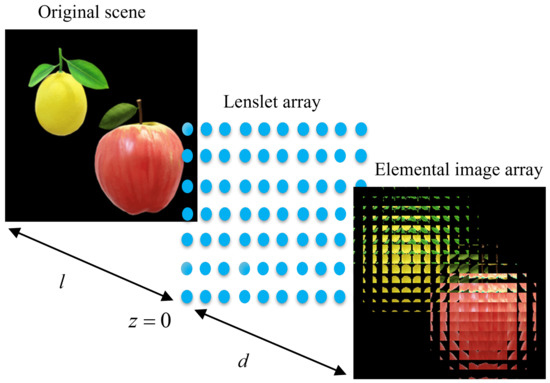
Figure 1.
The pickup of the original scene by CII.
2.2. DNA Sequence Operations
A Deoxyribo Nucleic Acid (DNA) sequence consists of four different basic nucleotides: adenine (A), guanine (G), thymine (T) and cytosine (C). These four nucleotides can be combined to form a long sequence, and T is paired with A,G is paired with C. We will obtain 24 different encoding schemes if A,C,G and T are encoded as binary numbers with two bits, respectively, but only eight encoding schemes suit the Watson–Crick rule, and they are shown in Table 1. Assuming that A-10, T-01, C-11, G-00, such as the binary sequence 10110100, the DNA sequence can be written as ACTG.

Table 1.
DNA coding rules.
DNA computing has received a lot of attention from researchers, so it has developed rapidly. Some researchers have proposed certain algebraic operations for DNA sequences, such as addition operations, subtraction operations and Ex-OR operations. Corresponding to the eight DNA coding schemes there are also eight DNA addition, subtraction and Ex-OR operations. Table 2 lists one of the arithmetic rules which, according to DNA encoding rule one, are listed in Table 1 [34].

Table 2.
DNA addition, subtraction and XOR operations.
For DNA recovery operations, the corresponding DNA sequences must meet the conditions specified by [36]:
where denotes one of the four different basic nucleotides, and is the base pair of .
2.3. Chaos Theory
Chaos as a nonlinear dynamic process that is highly sensitive to initial states and is unpredictable becomes a natural physical code. It widely applies in the fields of cryptography, random number generation, confidential communication and image encryption. In this paper, two chaos functions containing SLMM and a logistic map are selected to improve the performance of DNA encryption.
2D-SLMM is defined as [48]:
where and are control parameters, and , . It should be noted that if we want SLMM to work in a chaotic state, the should close to 3 [48].
There will be a 1D chaos function to describe the logistic map, which is defined as [49]:
where is the logistic map parameter, and . Only when , does the logistic map exhibit a state of chaos [49].
2.4. CIIR Algorithm
In the multi-image encryption scheme we proposed, the CIIR algorithm is used to recover different image scenes. However, traditional CIIR algorithms easily cause some pixels to coincide, resulting in a decrease in the intelligibility quality of the recovered scene. To improve the effects of pixel coincidence, we apply a modified reconstruction algorithm [50] so that every reconstructed scene pixel can be calculated. The calculation of the original scene uses the following formula:
where denotes the number of overlaps at the reconstruction distance z, M and N determine the number of EIs, m and n represent the size of the imaging sensor, p represents the pitch between each pinhole, and u is the magnification parameter.
2.5. Entropy Analysis Theory
To illustrate the performance of our proposed encryption scheme quantitatively, we introduce an entropy analysis method. Image entropy describes the average amount of information in an image, representing the aggregation characteristics of the image pixel distribution [51]. For image encryption, the original image contains more spatial features, the pixel distribution is more dispersed, the entropy value is small. While the encrypted image should contain the original image information as less as possible, the pixel distribution is relatively concentrated, so the entropy value is larger than in the original image. Therefore, the size of the entropy value can be analyzed to judge the performance of the encryption scheme.
The entropy of image I can be obtained by the following formula:
where denotes the probability of occurrence of pixel with value of in image I with and .
3. Multi-Image Encryption Scheme Based on CII
3.1. Framework of Multi-Image Encryption Scheme
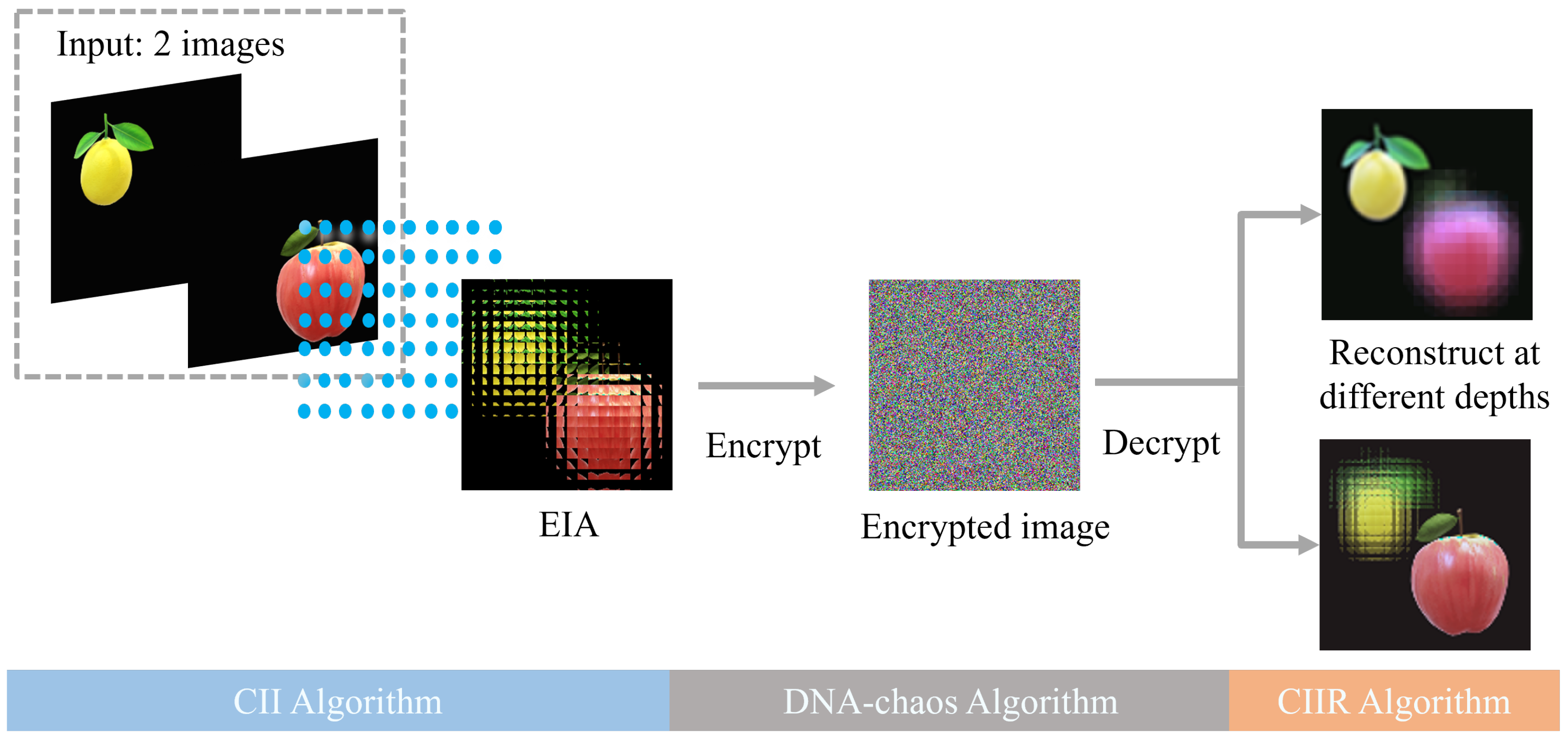
In this paper, a multi-image encryption scheme is proposed based the principle of CII, and the overall framework of the scheme is shown in Figure 2.
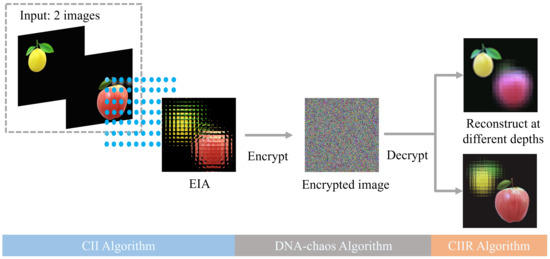
Figure 2.
Framework of multi-image encryption scheme.
In the multi-image encryption scheme we proposed, the input can be two or more images (two images are shown in Figure 2, and the following is also described in two images). Firstly, the two input images are placed on different position planes, then it is recorded on an EIA by a microlens array. The EIA merges information from two original images. It is worth noting that the different distances between two images and the microlens array can be used as keys. After that, the EIA is encrypted by the DNA-chaos encryption. Finally, the CIIR is used to reconstruct different original images with different depths. The detailed encryption and decryption procedure is described in Section 3.2.
3.2. Encryption and Decryption Procedure
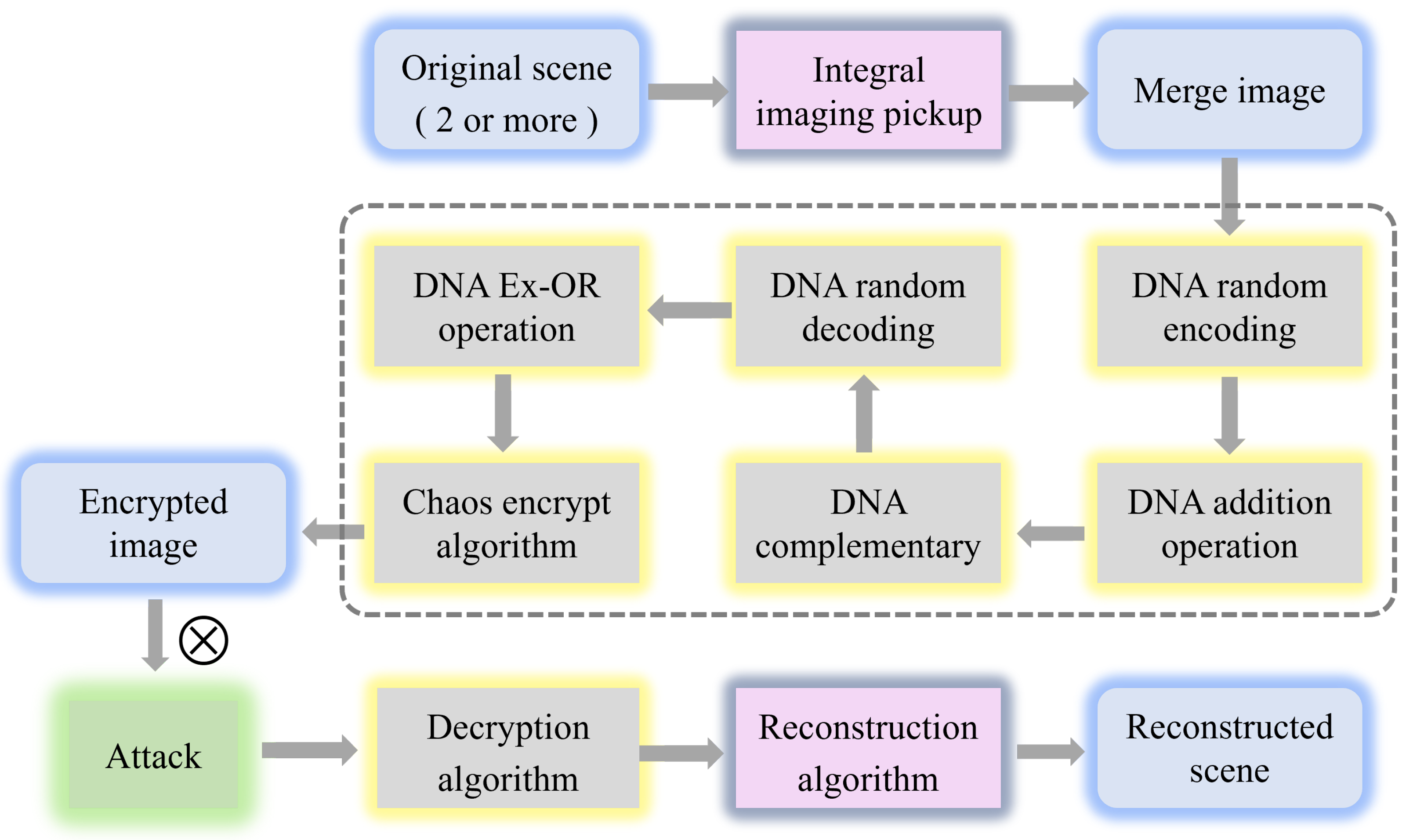
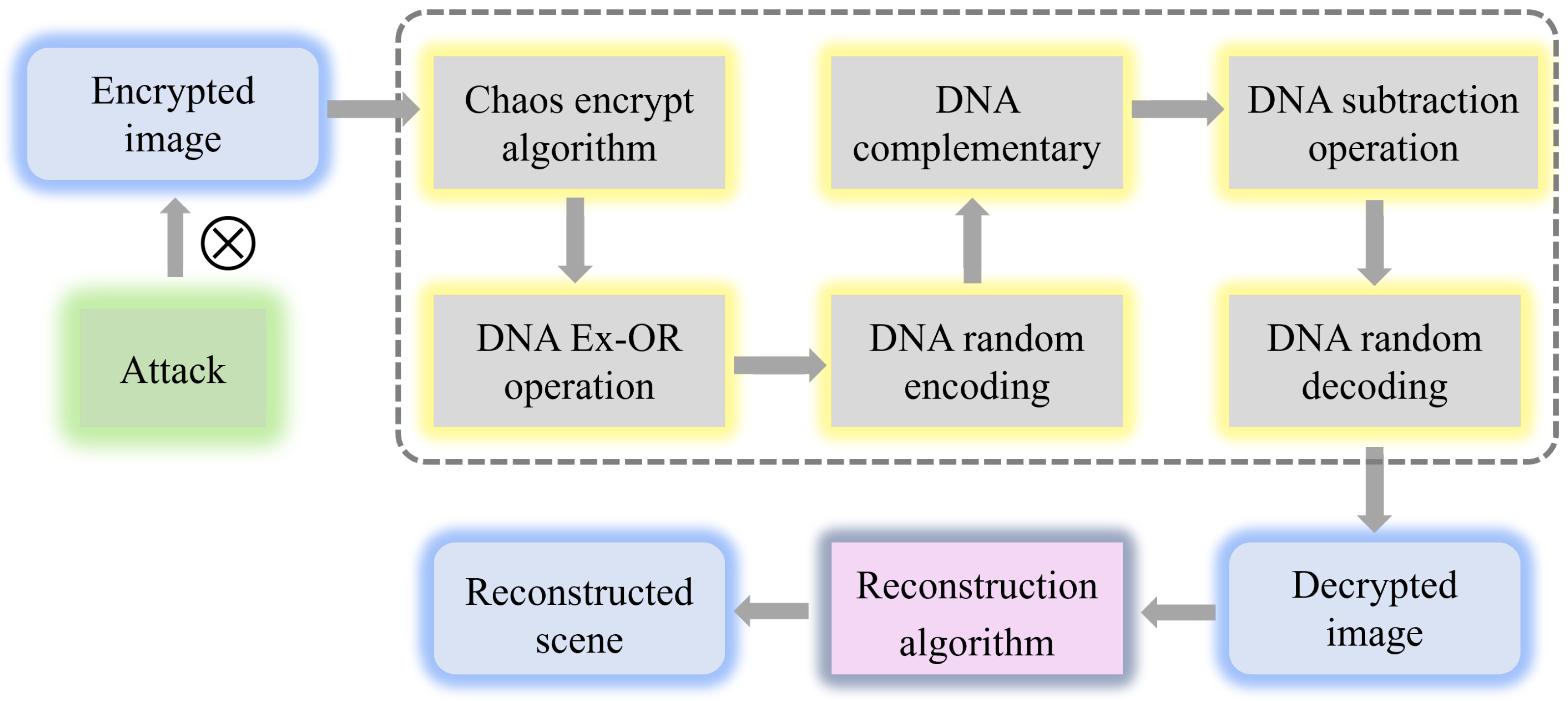
Figure 3 shows the detailed steps of the encryption algorithm we proposed. It is worth noting that we introduce the chaos algorithm to solve the outline effect caused by the DNA algorithm. The proposed multi-image encryption scheme is a symmetric process, so the decryption process of the image can be achieved by reversing the encryption process. The steps of the decryption process are shown in Figure 4, we only introduce the encryption procedure of the multi-image encryption scheme in detail.
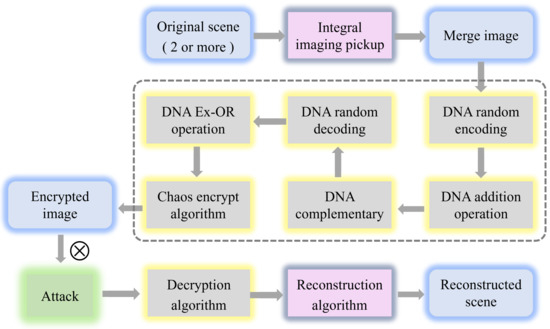
Figure 3.
The encryption procedure of multi-image encryption scheme.
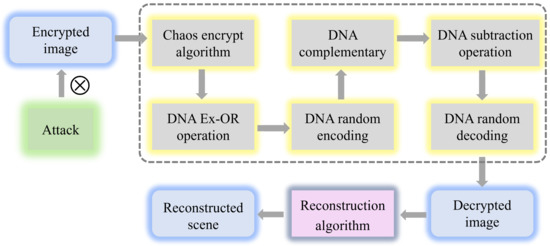
Figure 4.
The decryption procedure of multi-image encryption scheme.
The encryption procedure of the multi-image encryption scheme is introduced as follows:
Step 1: Convert the original scene into the form of merge image with size using the integral imaging pickup algorithm.
Step 2: Generate two high-quality pseudo-random sequences and with size by cellular automata with two different initial states.
Step 3: Decompose the merge image to three binary matrices , and with the size of . Then transform the three binary matrices into three DNA sequence matrices , and with the size of based on the DNA coding rules defined in Table 1 and the random encoding sequence generated from pseudo-random sequences . The random coding sequence can be obtained by:
Step 4: Perform the diffusion operations by DNA addition to get three DNA diffused matrices , and with the size of .
Step 5: Select the rule from four complementary rules according to pseudo-random sequence . Based on and the selected complementary rule, perform the DNA complementary operation on DNA diffused matrices and obtain three DNA complementary matrices , and . The pseudo-random sequence is described as:
Step 6: Decode three DNA matrices , and using DNA random decoding sequence generated form pseudo-random sequences and the DNA encoding rules. The random decoding sequence is described as:
Step 7: Perform the DNA Ex-OR operations and then convert them into the decimal matrices , and with the size of . Perform scrambling operations on the decimal three matrices with three pseudo-random sequences , and , respectively and obtained decimal three matrices , and with the size of .
Step 8: Perform chaos encryption algorithm on the decimal three matrices , and and combine them into an encrypted image.
4. Experiment Results and Performance Analysis
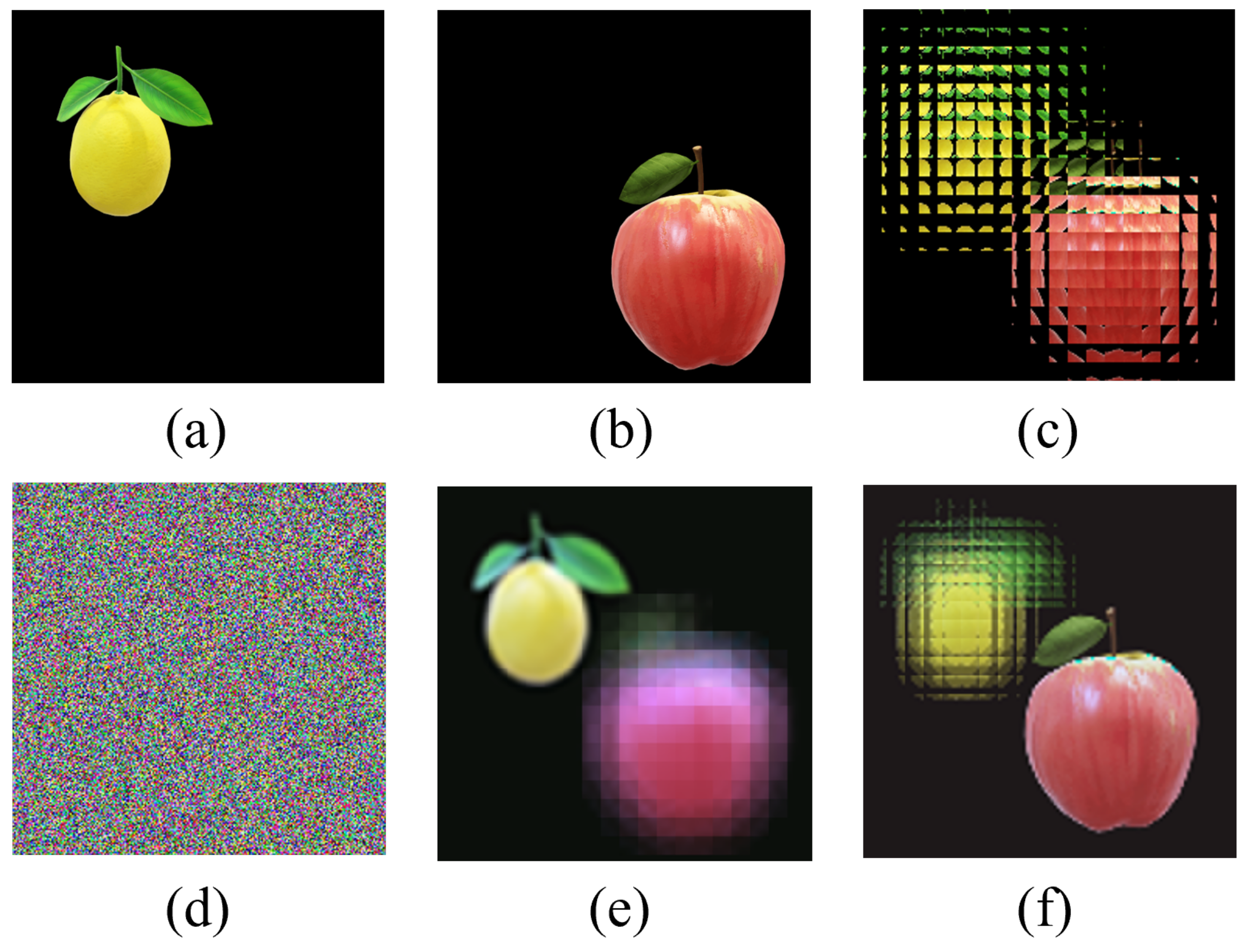
In this section, the EIA is calculated by the CII algorithm from two images, “lemon” and “apple”. Figure 5 shows the experiment results of the multi-image encryption scheme we proposed. Figure 5a,b shows the original images “lemon” and “apple” with a size of , and Figure 5c shows the EIA of original images “lemon” and “apple” generated by the CII algorithm. Figure 5d shows the encrypted image using the DNA-chaos algorithm. Figure 5e,f shows images reconstructed by the CIIR algorithm, and the reconstruction depths are 15 mm and 6 mm, respectively.
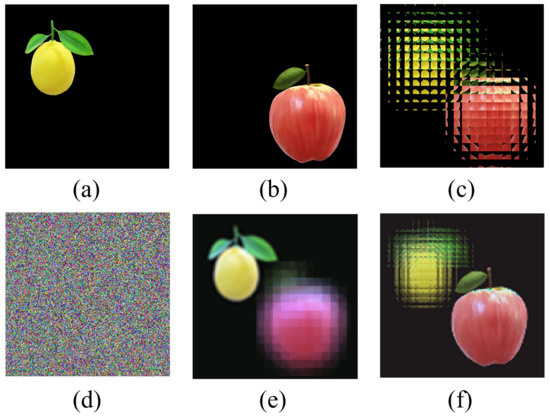
Figure 5.
The experiment results of multi-image encryption scheme (). (a) Original image “lemon”. (b) Original image “apple”. (c) EIA of image “lemon” and “apple”. (d) Encrypted image. (e) Reconstructed image (d = 15 mm). (f) Reconstructed image (d = 6 mm).
From Figure 5, we can qualitatively see that the multi-image encryption scheme we proposed has an excellent encryption and decryption performance. In order to illustrate that the multi-image encryption scheme we proposed can be applied to different scenarios, we select original images of different sizes and numbers for testing. The experimental results are shown in Figure 6 and Figure 7.
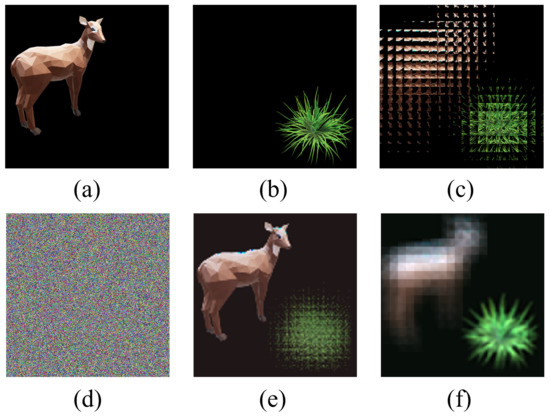
Figure 6.
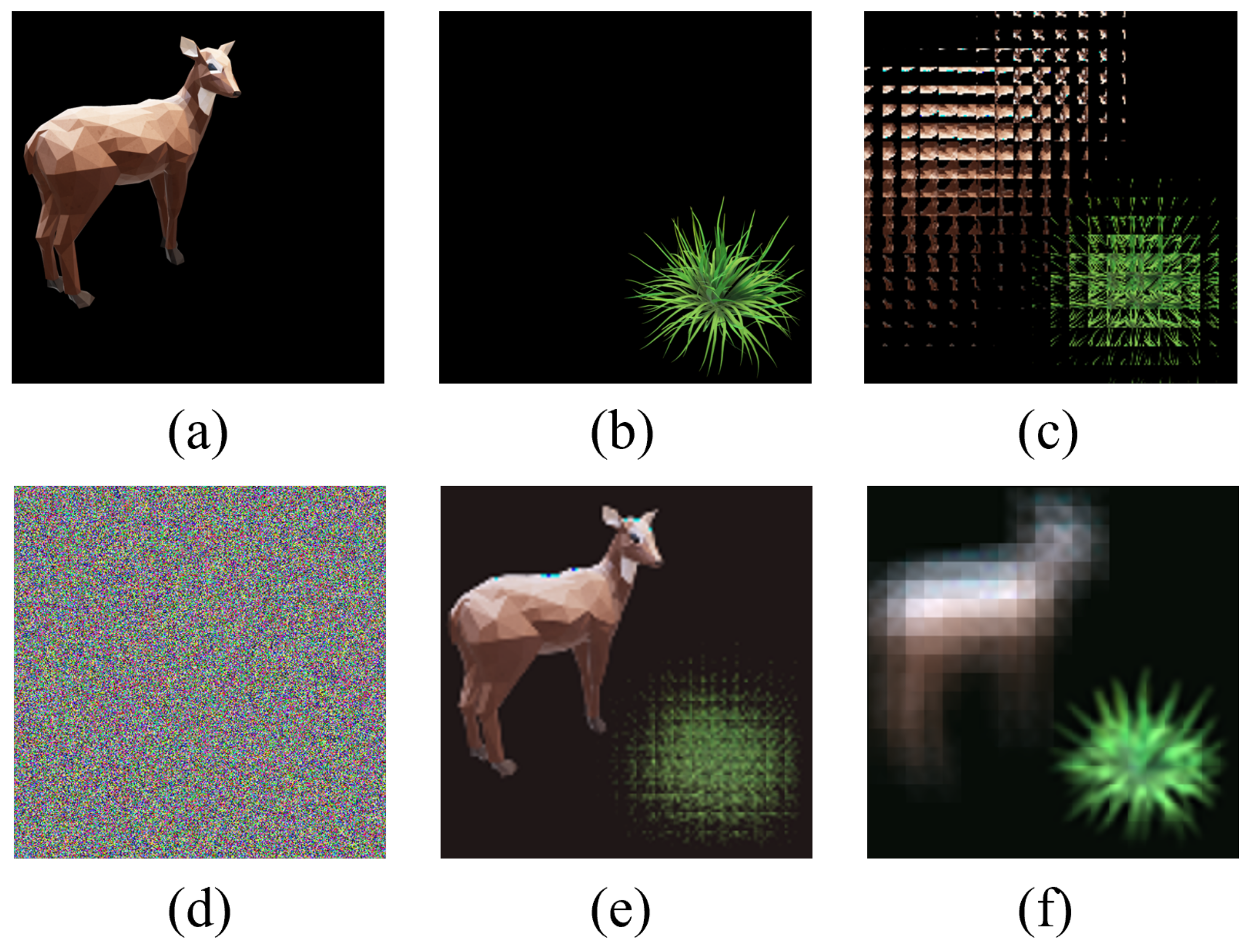
The experiment results of multi-image encryption scheme (). (a) Original image “sheep”. (b) Original image “grass”. (c) EIA of image “sheep” and “grass”. (d) Encrypted image. (e) Reconstructed image (d = 15 mm). (f) Reconstructed image (d = 6 mm).
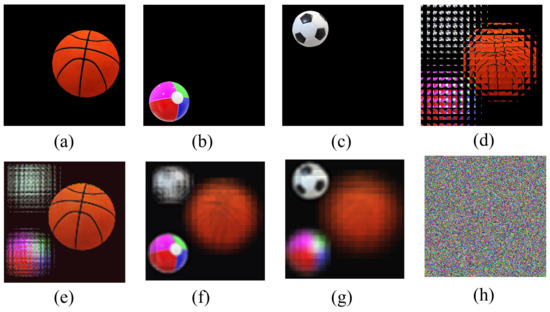
Figure 7.
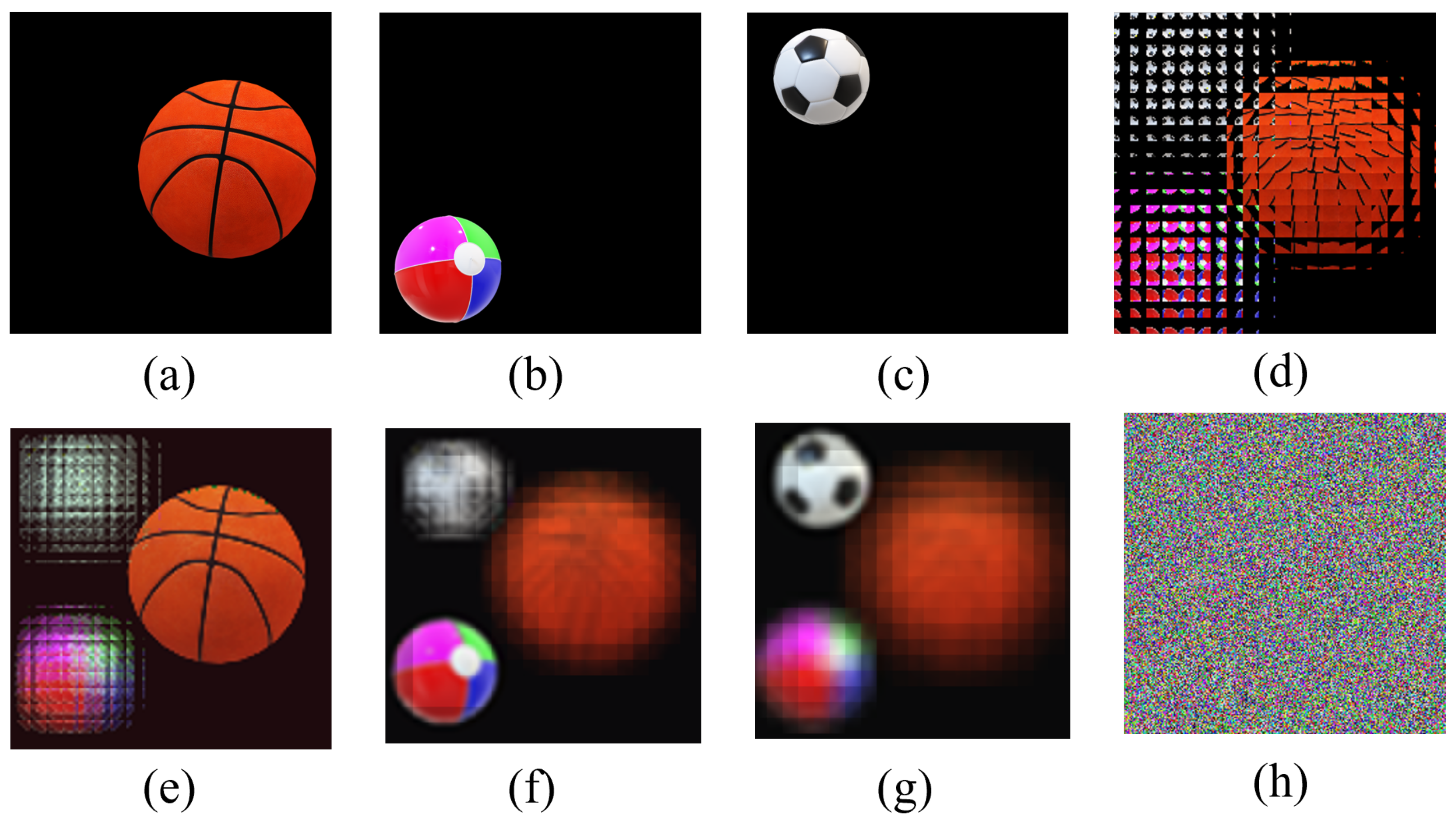
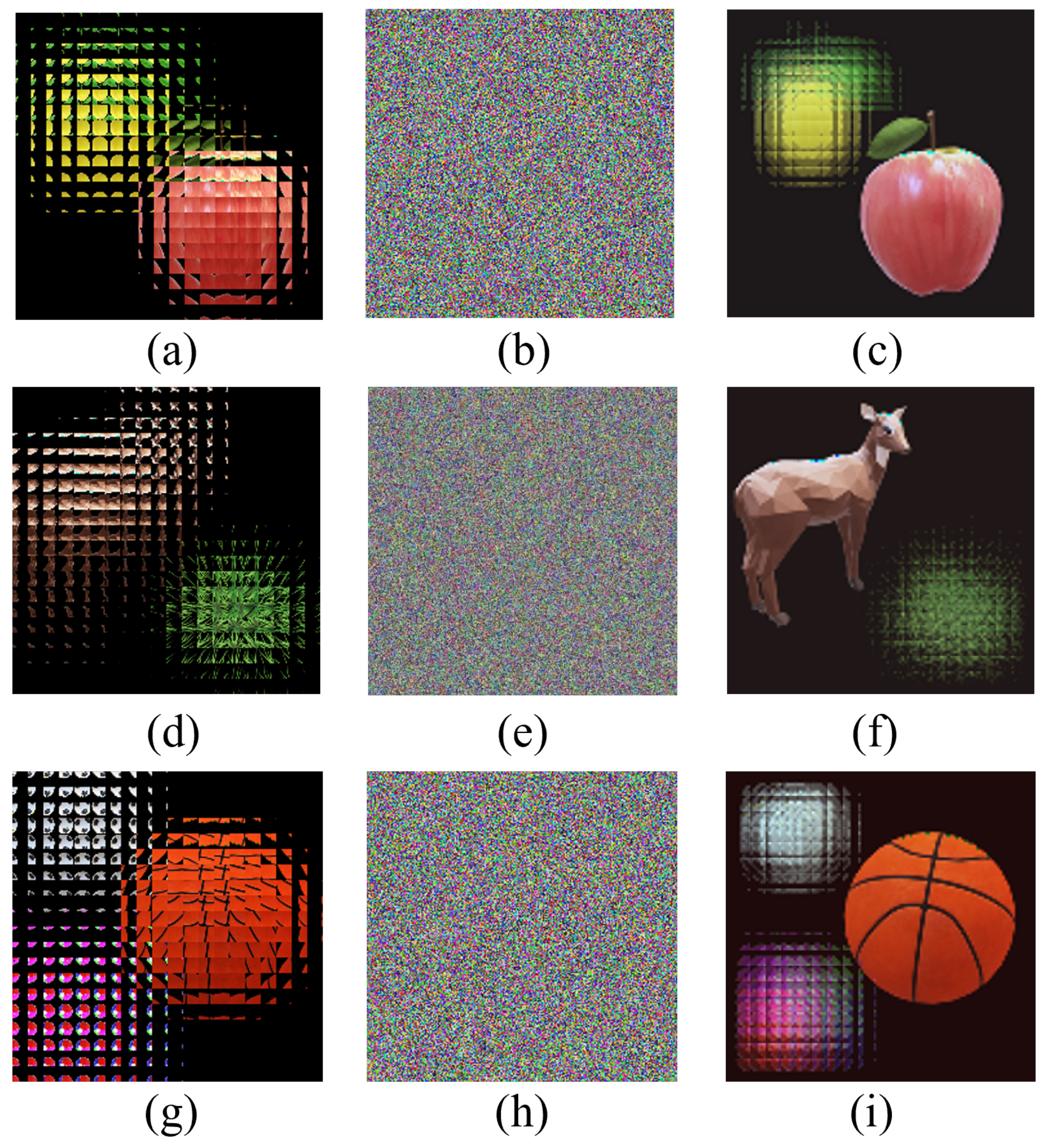
The experiment results with three original images of multi-image encryption scheme (). (a) Original image “basketball”. (b) Original image “ball”. (c) Original image “football”. (d) EIA of image “basketball”, “ball” and “football”. (e) Reconstructed image (d = 6 mm). (f) Reconstructed image (d = 15 mm). (g) Reconstructed image (d = 21 mm). (h) Encrypted image.
In Figure 6, two original images with a size of as the encryption images are different from Figure 5 with a size of . From Figure 6, we can also qualitatively see that the multi-image encryption scheme we proposed has an excellent encryption and decryption performance.
In Figure 7, three original images with a size of () are the encryption images. For obvious comparison, we put the encrypted image in the last position. From Figure 7h, we cannot observe any information about the original images. As can be seen from the first three columns in Figure 7, the reconstructed image can clearly restore the information of the original images.
The experimental results in Figure 5, Figure 6 and Figure 7 fully indicate that the multi-image encryption scheme we proposed can be applied to different scenarios, such as original images of different sizes ( in Figure 5 and in Figure 6) and different numbers (three original images in Figure 7). Following this section, we will analyze the multi-image encryption scheme we proposed quantitatively by taking two original images as examples.
4.1. Key Security Analysis
The encryption scheme must consider the security of the key, that is, the original image cannot be decrypted with the wrong key. Figure 8 shows the results of the key security analysis of our proposed multi-image encryption scheme.
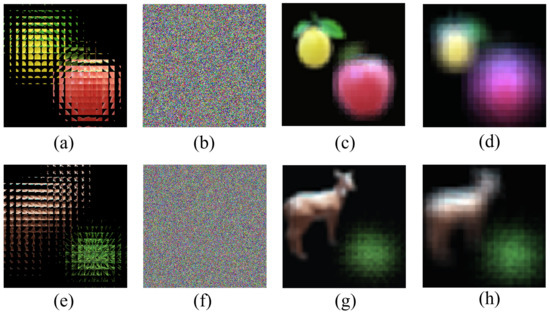
Figure 8.
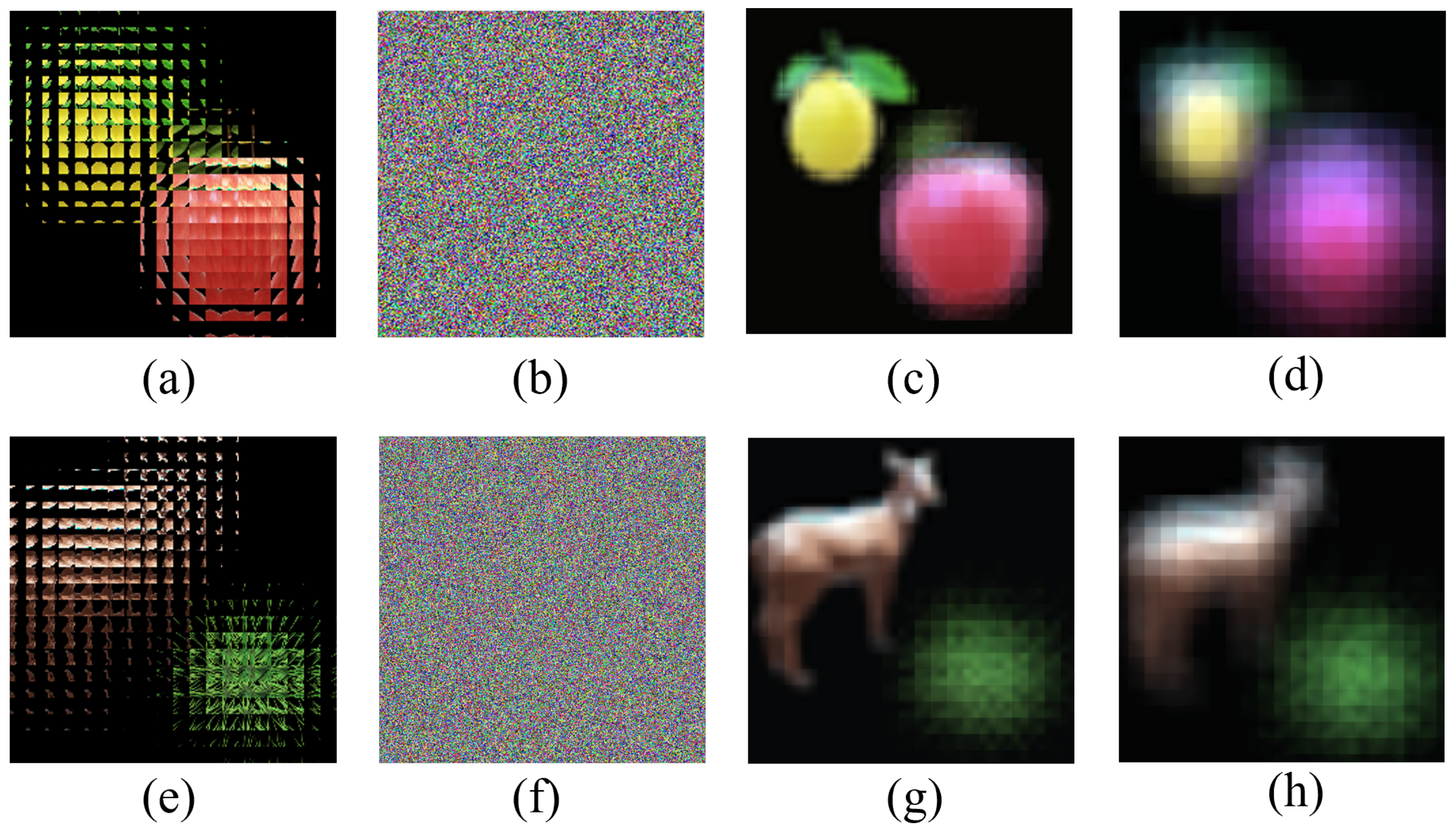
The results of key security analysis. (a) The decrypted image of Figure 5d using right key. (b) The decrypted image of Figure 5d using wrong key. (c) The reconstructed image of Figure 7a with wrong depths (d = 18 mm). (d) The reconstructed image of Figure 7a with wrong depths (d = 24 mm). (e) The decrypted image of Figure 6d using right key. (f) The decrypted image of Figure 6d using wrong key. (g) The reconstructed image of Figure 7e with wrong depths (d = 18 mm). (h) The reconstructed image of Figure 7e with wrong depths (d = 24 mm).
Figure 8 shows the results of key security analysis; the encrypted images corresponding to the first and second columns are Figure 5d and Figure 6d respectively. Figure 8a,e shows the decrypted image with the right key and Figure 8b,f shows the decrypted image with the wrong key; we cannot obtain any useful information about the original image. Figure 8c,d,g,h separately shows the reconstructed image with wrong depths; when the reconstruction depth is wrong, we cannot obtain a clear image relative to the correct reconstruction depth, such as in Figure 5d,h. This shows that the multi-image encryption scheme we proposed has high key security.
4.2. Statistical Analysis
In order to quantitatively illustrate the performance of our proposed multi-image encryption scheme, we performed a statistical analysis of the experimental results, which is shown in Figure 9.
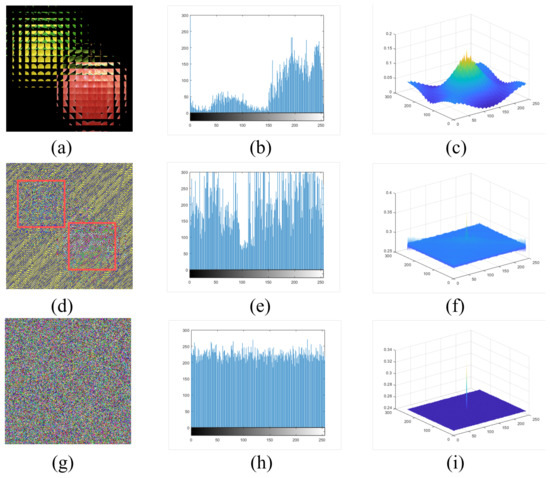
Figure 9.
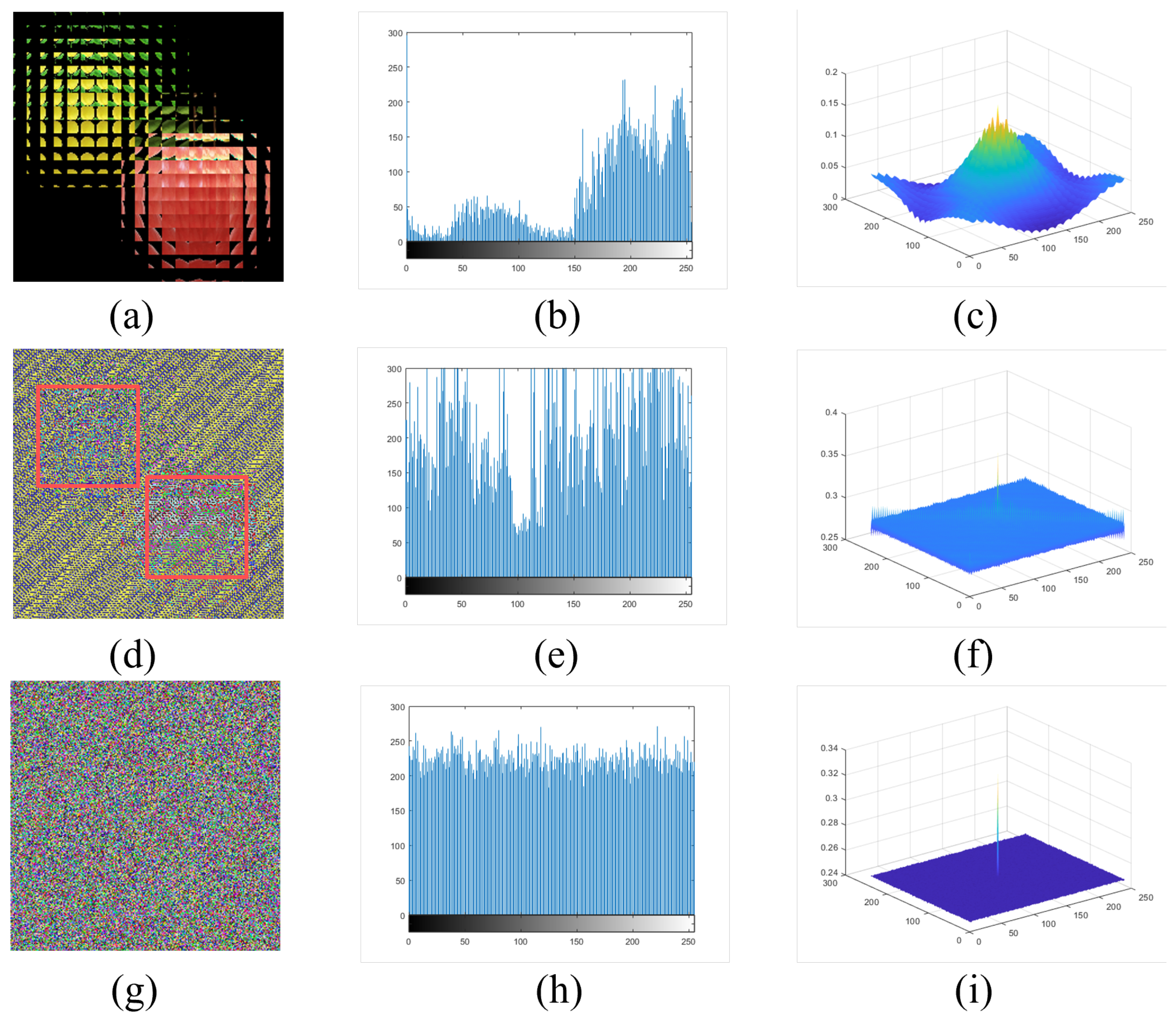
The results of statistical analysis. (a) The EIA of two original images. (d) The encrypted image only by DNA. (g) The encrypted image by DNA-chaos. (b,e,h) represent histogram (R channel) of (a,d,g) respectively. (c,f,i) show autocorrelation results (R channel) of (a,d,g) respectively.
Figure 9a is the EIA of two original images, “lemon” and “apple”, and Figure 9d shows the encrypted image only by DNA algorithm. We can see the outline of two saliency objects in the EIA clearly from the result. Figure 9g represents the image encrypted by the DNA-chaos algorithm, and we cannot see any information about the original image. Figure 9b,e,h represents a histogram (R channel) of Figure 9a,d,g separately. The results of the histogram indicate that the distribution of the image encrypted by DNA-chaos is very flat. Figure 9c,f,i represents the autocorrelation (R channel) of Figure 9a,d,g separately, and we can also find that the autocorrelation is very weak for the image encrypted by DNA-chaos. So the multi-image encryption scheme we proposed has an excellent performance according to the statistical analysis results.
In addition, we calculated the entropy value of Figure 9a,d,g from the RGB channel separately, then took the average of them, and the results are , and . The entropy value of the encrypted image is significantly larger than the entropy value of the EIA image, which shows that the encryption scheme we proposed performs well.
4.3. Robustness Analysis
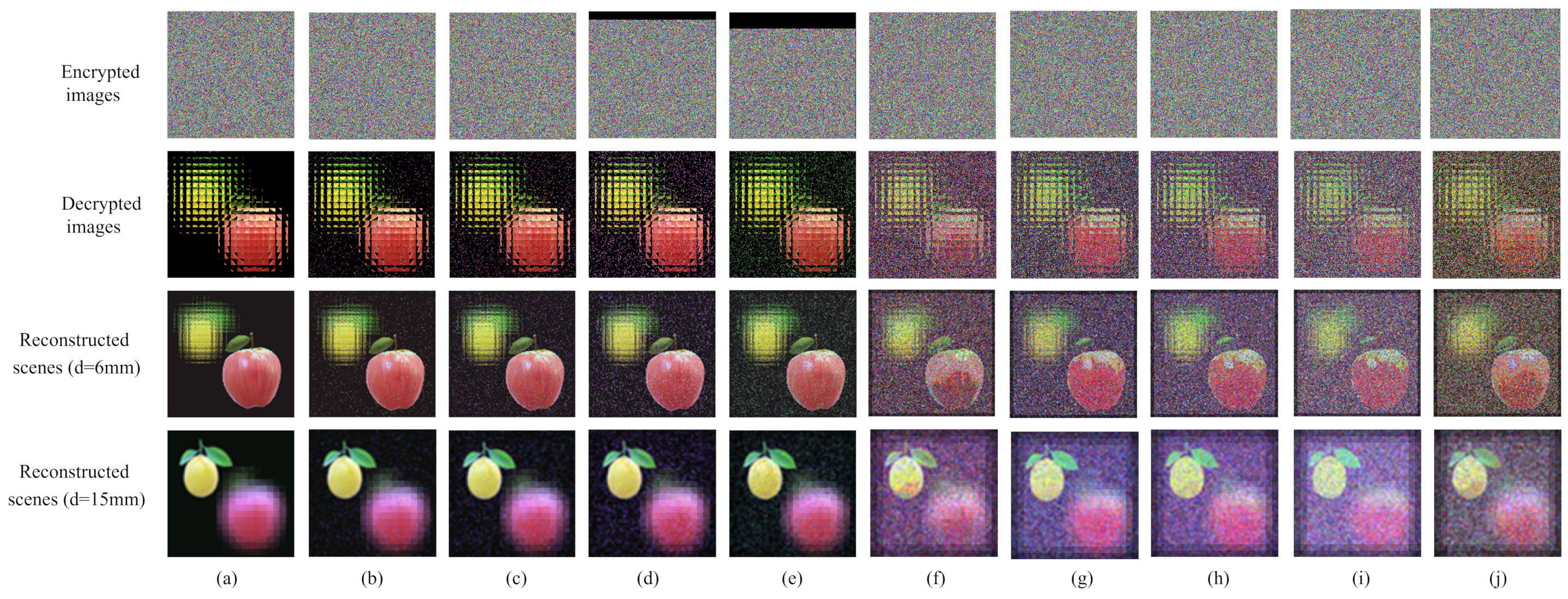
In order to verify the reliability of the multi-image encryption scheme we proposed in the noisy environment, we designed simulation experiments to analyze the robustness. We simulated Gaussian noise, Speckle noise, Poisson noise, Salt and Pepper noise and Clip attack channel environments to test the robustness of the scheme. The simulation experiment results are shown in Figure 10.
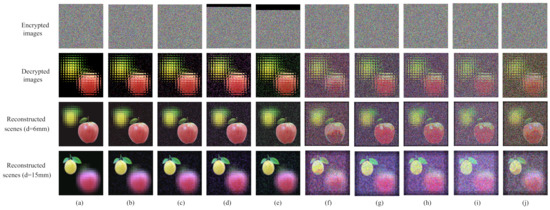
Figure 10.
The results of robustness analysis. (a) No noise. (b) Salt & Pepper noise (0.01). (c) Salt & Pepper noise (0.02). (d) Clip attack (). (e) Clip attack (). (f) Speckle noise (0.01). (g) Speckle noise (0.02). (h) Gaussian noise (0.01). (i) Gaussian noise (0.02). (j) Possion noise.
From Figure 10, we can intuitively see that the multi-image encryption scheme we proposed can reconstruct the original scene correctly in a variety of noise environments.
In order to qualitatively illustrate the visual quality the recovered scene, we use the peak signal-to-noise ratio (PSNR) image quality evaluation index that is widely recognized by researchers. The PSNR value of an image can be obtained by the formula [39]:
where M and N indicate the width and height of the image, respectively, E is the original scenes, and is the recovered scenes.
The PSNR values of the decrypted images with the the Gaussian noise, Speckle noise, Poisson noise, Salt and Pepper noise and Clip attack channel environments are shown in the Table 3.

Table 3.
PSNRs of Decrypted Scenes Against Attacks With Different Schemes.
It can be clearly seen from the Table 3 that the multi-image encryption scheme we proposed has a strong robustness in various noise environments.
There are two indexes to qualitatively illustrate the key sensitivity and plaintext sensitivity encryption scheme, namely number of pixels change rate (NPCR) and unified average changing intensity (UACI) [52]. NPCR indicates the number of pixels that change between two images and UACI represents the average number of changes in intensity between two images. The calculation formula of NPCR and UACI is as follows:
where is defined as:
where W and H denote the width and height of the image. and are two images.
That the plaintext images are sensitive is a basic requirement of a good image cryptosystem. Only those image cryptosystems with plaintext sensitivity can resist the chosen/known plaintext attacks. For any given key, if the plain image is changed slightly, its encrypted image will be changed dramatically, and this image cryptosystem is plaintext sensitive.
Key sensitivity analysis includes three aspects: (1) When encrypting a plaintext image, if the key changes slightly, the encryption system will produce two completely different encrypted images, which means that the key is sensitive in the encryption process. Meanwhile, such a key is an effective encryption key; (2) When encrypting a plaintext image, if the key changes slightly, the encryption system will produce two completely different encrypted images, which means that the key is sensitive in the encryption process. Meanwhile, such a key is an effective encryption key; (3) When decrypting a cipher image using an illegal key, if the key changes slightly, the decryption system will produce two completely different images, both totally different from the original plaintext image. This means that the illegal key is sensitive in the decryption process. Such an illegal key is effective.
We use NPCR and UACI to qualitatively illustrate the key sensitivity and plaintext sensitivity of the multi-image encryption scheme we proposed. We still use Figure 5c as our test image; the results are shown in Table 4.

Table 4.
The analysis of key sensitivity and plaintext sensitivity using NPCR and UACI.
The theoretical value of NPCR is and UACI is . From the Table 4, we can find that the NPCR and UACI are very close to the theoretical value, Which indicates the multi-image encryption scheme we proposed has excellent key sensitivity and plaintext sensitivity.
4.4. Time Analysis
Encryption time is very important for an encryption scheme. An image encryption scheme with good performance should use as little time as possible in the process of image encryption and decryption. In this section, we select different sizes of images and more than two images as input to test the multi-image encryption scheme we proposed. The results of the encryption and decryption analysis of different images are shown in Figure 11.
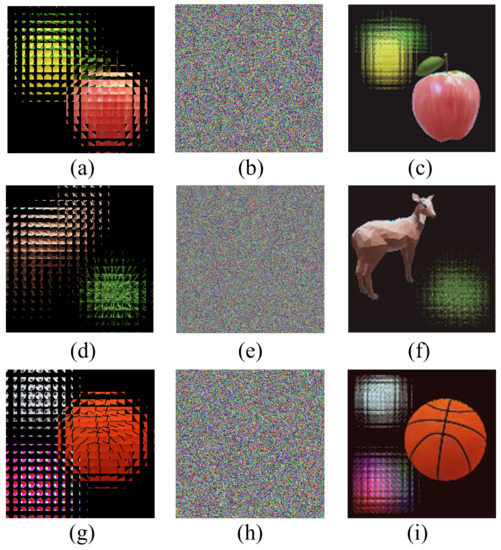
Figure 11.
Encryption and decryption analysis of different images. (a) The EIA of two input images (). (d) The EIA of two input images (). (g) The EIA of three input images (). (b,e,h) represent encrypted image of (a,d,g) separately. (c,f,i) show decryption results of (a,d,g) separately.
Figure 11a is the EIA of two input images with the size of , Figure 11d is the EIA of two input images with the size of , and Figure 11g is the EIA of three input images with the size of . We analysis the encryption and decryption time of these different images. For Figure 11a, the encryption and decryption time is s, Figure 11d is s and Figure 11d is s.
5. Conclusions
In conclusion, we apply the CII algorithm to achieve multi-image encryption, which significantly improves the efficiency of image encryption, meanwhile combining the chaos algorithm to address the outline effect caused by the DNA encryption algorithm. In the proposed multi-image encryption scheme, the different depth distances of multiple images can also be used as keys, which can improve the security of the encryption method significantly. We also analyze the robustness of this scheme against a variety of attacks. The experiment results confirm the excellent performance of our proposed multi-image encryption scheme.
Author Contributions
Conceptualization, X.L., C.Y. and J.G.; methodology, X.L. and J.G.; formal analysis, X.L. and J.G.; writing—original draft preparation, X.L. and J.G.; writing—review and editing, C.Y. and J.G. All the authors made comments on the final version before the submission. All authors have read and agreed to the published version of the manuscript.
Funding
Natural Science Foundation of Guangdong Province (2018A0303070009, 2021A1515011091); Educational Commission of Guangdong Province (2018KTSCX143, 2020ZDZX3056).
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Chen, W.; Javidi, B.; Chen, X. Advances in optical security systems. Adv. Opt. Photonics 2014, 6, 120–155. [Google Scholar] [CrossRef]
- Wang, X.; Zhu, X.; Wu, X.; Zhang, Y. Image encryption algorithm based on multiple mixed hash functions and cyclic shift. Opt. Lasers Eng. 2018, 107, 370–379. [Google Scholar] [CrossRef]
- Shi, Y.; Li, T.; Wang, Y.; Gao, Q.; Zhang, S.; Li, H. Optical image encryption via ptychography. Opt. Lett. 2013, 38, 1425–1427. [Google Scholar] [CrossRef] [PubMed]
- Li, X.; Meng, X.; Yang, X.; Yin, Y.; Wang, Y.; Peng, X.; Chen, H. Multiple-image encryption based on compressive ghost imaging and coordinate sampling. IEEE Photonics J. 2016, 8, 1–11. [Google Scholar]
- Li, X.; Xiao, D.; Wang, Q.H. Error-free holographic frames encryption with CA pixel-permutation encoding algorithm. Opt. Lasers Eng. 2018, 100, 200–207. [Google Scholar] [CrossRef]
- Zhao, R.; Zhang, Y.; Xiao, X.; Ye, X.; Lan, R. TPE2: Three-pixel exact thumbnail-preserving image encryption. Signal Process. 2021, 183, 108019. [Google Scholar] [CrossRef]
- Gong, L.; Qiu, K.; Deng, C.; Zhou, N. An optical image compression and encryption scheme based on compressive sensing and RSA algorithm. Opt. Lasers Eng. 2019, 121, 169–180. [Google Scholar] [CrossRef]
- Qu, G.; Yang, W.; Song, Q.; Liu, Y.; Qiu, C.W.; Han, J.; Xiao, S. Reprogrammable metahologram for optical encryption. Nat. Commun. 2014, 11, 5484. [Google Scholar]
- Pan, A.; Wen, K.; Yao, B. Linear space-variant optical cryptosystem via Fourier ptychography. Opt. Lett. 2019, 44, 2032–2035. [Google Scholar] [CrossRef]
- Chen, W.; Situ, G.; Chen, X. High-flexibility optical encryption via aperture movement. Opt. Express 2013, 21, 24680–24691. [Google Scholar] [CrossRef]
- Liu, Z.; Xu, L.; Lin, C.; Liu, S. Image encryption by encoding with a nonuniform optical beam in gyrator transform domains. Appl. Opt. 2010, 49, 563–5637. [Google Scholar] [CrossRef]
- Yang, B.; Liu, Z.; Wang, B.; Zhang, Y.; Liu, S. Optical stream-cipher-like system for image encryption based on Michelson interferometer. Opt. Express 2011, 19, 2634–2642. [Google Scholar] [CrossRef]
- Refregier, P.; Javidi, B. Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 1995, 20, 767–769. [Google Scholar] [CrossRef]
- Peng, X.; Zhang, P.; Wei, H.; Yu, B. Known-plaintext attack on optical encryption based on double random phase keys. Opt. Lett. 2006, 31, 1044–1046. [Google Scholar] [CrossRef]
- Unnikrishnan, G.; Joseph, J.; Singh, K. Optical Encryption by Double-random Phase Encoding in the Fractional Fourier Domain. Opt. Lett. 2000, 25, 887–889. [Google Scholar] [CrossRef]
- Situ, G.H.; Zhang, J. Double random-phase encoding in the Fresnel domain. Opt. Lett. 2004, 29, 1584–1586. [Google Scholar] [CrossRef]
- Liu, Z.J.; Xu, L.; Lin, C. Image encryption scheme by using iterative random phase encoding in gyrator transform domains. Opt. Lasers Eng. 2011, 49, 542–546. [Google Scholar] [CrossRef]
- Kumar, R.; Bhaduri, B. Optical image encryption in Fresnel domain using spiral phase transform. J. Opt. 2017, 19, 095771. [Google Scholar] [CrossRef]
- Sui, L.S.; Xu, M.J.; Tian, A.L. Optical noise-free image encryption based on quick response code and high dimension chaotic system in gyrator transform domain. Opt. Lasers Eng. 2017, 91, 106–114. [Google Scholar] [CrossRef]
- Zhao, D.M.; Li, X.; Chen, L.F. Optical image encryption with redefined fractional Hartley transform. Opt. Commun. 2008, 281, 5326–5329. [Google Scholar] [CrossRef]
- Hong, S.H.; Jang, J.S.; Javidi, B. Three-dimensional volumetric object reconstruction using computational integral imaging. Opt. Express 2004, 12, 483–491. [Google Scholar] [CrossRef] [PubMed]
- Shin, D.H.; Yoo, H. Image quality enhancement in 3D computational integral imaging by use of interpolation methods. Opt. Express 2007, 15, 12039–12049. [Google Scholar] [CrossRef]
- Chen, Y.; Wang, X.; Zhang, J.; Yu, S.; Zhang, Q.; Guo, B. Resolution improvement of integral imaging based on time multiplexing sub-pixel coding method on common display panel. Opt. Express 2014, 22, 17897–17907. [Google Scholar] [CrossRef]
- Wang, Y.J.; Shen, X.; Lin, Y.H.; Javidi, B. Extended depth-of-field 3D endoscopy with synthetic aperture integral imaging using an electrically tunable focal-length liquid-crystal lens. Opt. Lett. 2015, 40, 3564–3567. [Google Scholar] [CrossRef]
- Stern, A.; Javidi, B. Three-dimensional image sensing and reconstruction with time-division multiplexed computational integral imaging. Appl. Opt. 2003, 42, 7036–7042. [Google Scholar] [CrossRef] [Green Version]
- Adleman, L.M. Molecular computation of solutions to combinatorial problems. Science 1994, 266, 1021–1024. [Google Scholar] [CrossRef] [Green Version]
- Xiao, X.; Javidi, B.; Martinez-Corral, M.; Stern, A. Advances in three-dimensional integral imaging: Sensing, display, and applications. Appl. Opt. 2013, 52, 546–560. [Google Scholar] [CrossRef]
- Li, X.; Zhao, M.; Xing, Y.; Zhang, H.L.; Li, L.; Kim, S.T.; Wang, Q.H. Designing optical 3D images encryption and reconstruction using monospectral synthetic aperture integral imaging. Optics Express 2018, 26, 11084–11099. [Google Scholar] [CrossRef]
- Li, X.; Zhao, M.; Xing, Y.; Li, L.; Kim, S.T.; Zhou, X.; Wang, Q.H. Optical encryption via monospectral integral imaging. Opt. Express 2017, 25, 31516–31527. [Google Scholar] [CrossRef]
- Markman, A.; Wang, J.; Javidi, B. Three-dimensional integral imaging displays using a quick-response encoded elemental image array. Optica 2014, 1, 332–335. [Google Scholar] [CrossRef]
- Park, G.; Jung, J.H.; Hong, K.; Kim, Y.; Kim, Y.H.; Min, S.W.; Lee, B. Multi-viewer tracking integral imaging system and its viewing zone analysis. Opt. Express 2009, 17, 17895–17908. [Google Scholar] [CrossRef] [PubMed]
- Xing, S.; Sang, X.; Yu, X.; Duo, C.; Pang, B.; Gao, X.; Wang, K. High-efficient computer-generated integral imaging based on the backward ray-tracing technique and optical reconstruction. Opt. Express 2017, 25, 330–338. [Google Scholar] [CrossRef] [PubMed]
- Wang, Y.; Ren, Z.; Zhang, L.; Li, D.; Li, X. 3D image hiding using deep demosaicking and computational integral imaging. Opt. Lasers Eng. 2022, 148, 106772. [Google Scholar] [CrossRef]
- Watson, J.D.; Crick, F.H. Molecular structure of nucleic acids: A structure for deoxyribose nucleic acid. Nature 1953, 171, 737–738. [Google Scholar] [CrossRef]
- Sun, S. A novel hyperchaotic image encryption scheme based on DNA encoding, pixel-level scrambling and bit-level scrambling. IEEE Photonics J. 2018, 10, 1–14. [Google Scholar] [CrossRef]
- Liu, H.; Wang, X. Image encryption using DNA complementary rule and chaotic maps. Appl. Soft Comput. 2012, 12, 1457–1466. [Google Scholar] [CrossRef]
- Guesmi, R.; Farah, M.A.B.; Kachouri, A.; Samet, M. A novel chaos-based image encryption using DNA sequence operation and Secure Hash Algorithm SHA-2. Nonlinear Dyn. 2016, 83, 1123–1136. [Google Scholar] [CrossRef]
- Fu, X.Q.; Liu, B.C.; Xie, Y.Y.; Li, W.; Liu, Y. Image encryption-then-transmission using DNA encryption algorithm and the double chaos. IEEE Photonics J. 2018, 10, 1–15. [Google Scholar] [CrossRef]
- Wang, Y.; Li, X.W.; Wang, Q.H. Integral imaging based optical image encryption using CA-DNA algorithm. IEEE Photonics J. 2021, 13, 1–12. [Google Scholar] [CrossRef]
- Zhang, Y.Q.; Wang, X.Y.; Liu, J.; Chi, Z.L. An image encryption scheme based on the MLNCML system using DNA sequences. Adv. Opt. Photonics 2016, 82, 95–103. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, P.; Huang, H.; Zhu, Y.; Xiao, D.; Xiang, Y. Privacy-assured FogCS: Chaotic compressive sensing for secure industrial big image data processing in fog computing. IEEE Trans. Ind. Inform. 2020, 17, 3401–3411. [Google Scholar] [CrossRef]
- Head, T.; Rozenberg, G.; Bladergroen, R.S.; Breek, C.K.D.; Lommerse, P.H.M.; Spaink, H.P. Computing with DNA by operating on plasmids. BioSystems 2000, 57, 87–93. [Google Scholar] [CrossRef]
- Zheng, X.; Xu, J.; Li, W. Parallel DNA arithmetic operation based on n-moduli set. Appl. Math. Comput. 2015, 297, 80–94. [Google Scholar] [CrossRef]
- Hayat, U.; Azam, N.A. A novel image encryption scheme based on an elliptic curve. Signal Process. 2019, 155, 391–402. [Google Scholar] [CrossRef]
- Azam, N.A.; Ullah, I.; Hayat, U. A fast and secure public-key image encryption scheme based on Mordell elliptic curves. Opt. Lasers Eng. 2021, 137, 106371. [Google Scholar] [CrossRef]
- Jia, N.; Liu, S.; Ding, Q.; Wu, S.; Pan, X. A New Method of Encryption Algorithm Based on Chaos and ECC. J. Inf. Hiding Multim. Signal Process. 2016, 7, 637–644. [Google Scholar]
- Zhang, F.; Zhang, Z.; Guan, P. ECC2: Error correcting code and elliptic curve based cryptosystem. Inf. Sci. 2020, 526, 301–320. [Google Scholar] [CrossRef]
- Hua, Z.Y.; Zhou, Y.C.; Pun, C.M.; Chen, C.L.P. 2D Sine Logistic modulation map for image encryption. Inf. Sci. 2014, 6, 120–155. [Google Scholar] [CrossRef]
- Singh, N.; Sinha, A. Optical image encryption using Hartley transform and logistic map. Opt. Commun. 2009, 282, 1104–1109. [Google Scholar] [CrossRef]
- Niyat, A.Y.; Moattar, M.H.; Torshiz, M.N. Color image encryption based on hybrid hyper-chaotic system and cellular automata. Opt. Lasers Eng. 2017, 90, 225–237. [Google Scholar] [CrossRef]
- Tsai, D.Y.; Lee, Y.; Matsuyama, E. Information entropy measure for evaluation of image quality. J. Digit. Imaging 2008, 21, 338–347. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Chai, X.; Gan, Z.; Yuan, K.; Chen, Y.; Liu, X. A novel image encryption scheme based on DNA sequence operations and chaotic systems. Neural Comput. Appl. 2019, 31, 219–237. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).