Novel Noise Injection Scheme to Guarantee Zero Secrecy Outage under Imperfect CSI
Abstract
:1. Introduction
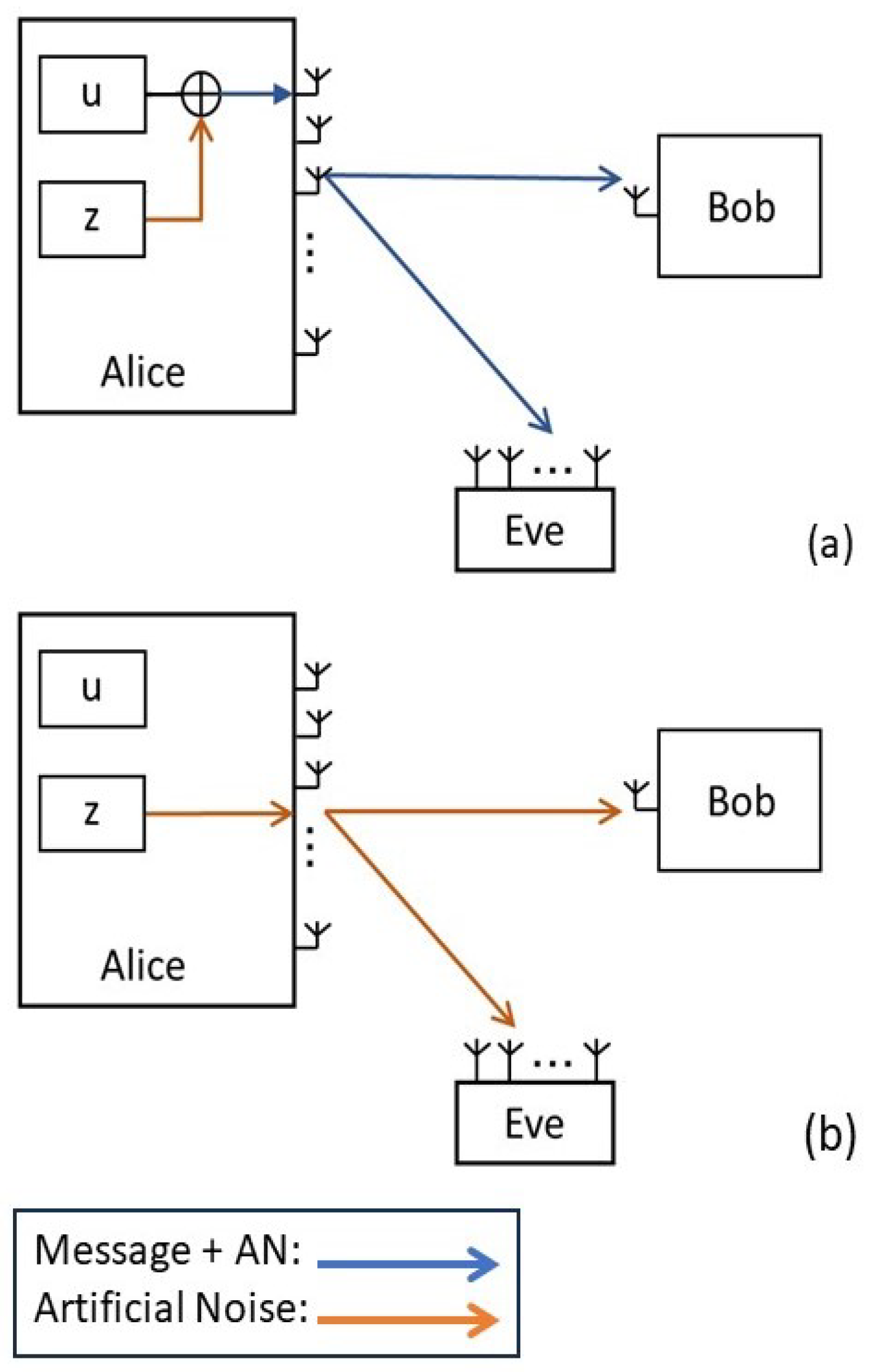
- Different from conventional schemes, in which AN is transmitted in the null space of the secure signal, the proposed artificial noise injection scheme transmits AN in the same space as the secure signal and uses an extra time slot for only transmitting AN with aid reverse pilot training to achieve noise cancellation capability at legitimate receivers and not at an eavesdropper.
- Although the proposed strategy wastes one extra time slot, it reduces complexity at the transmitter, which requires one AN vector compared to an AN matrix as in the conventional strategy. This simple strategy can also be extended to apply to many other system networks to efficiently achieve zero secrecy outage.
- The closed-form formula of the secrecy rate subject to zero secrecy outage is determined. Then, the resulting zero-outage secrecy throughput can always be achieved regardless of how powerful the eavesdropper is, e.g., if it has an infinite number of antennas.
2. System Model
2.1. Phase 1
2.2. Phase 2
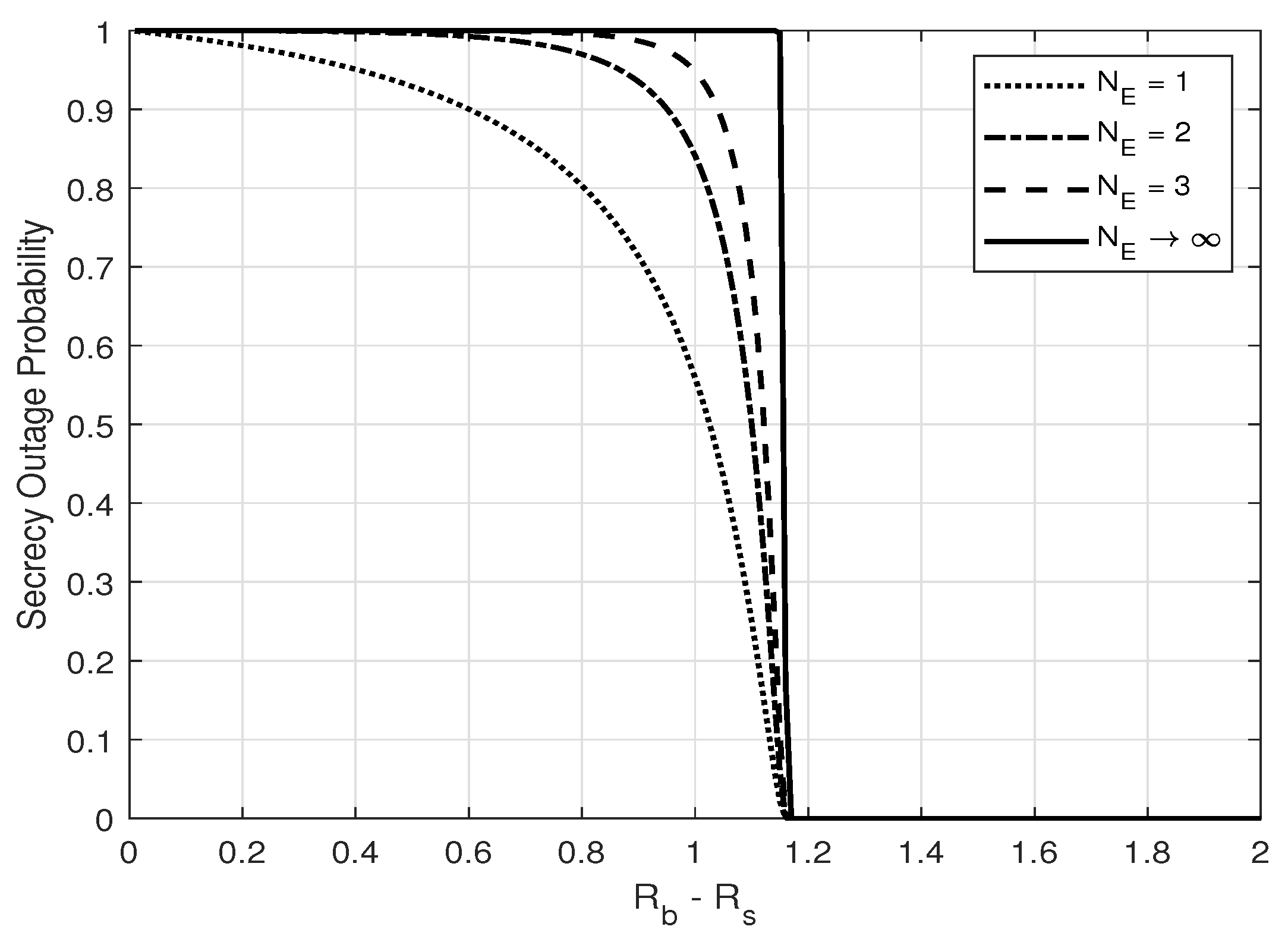
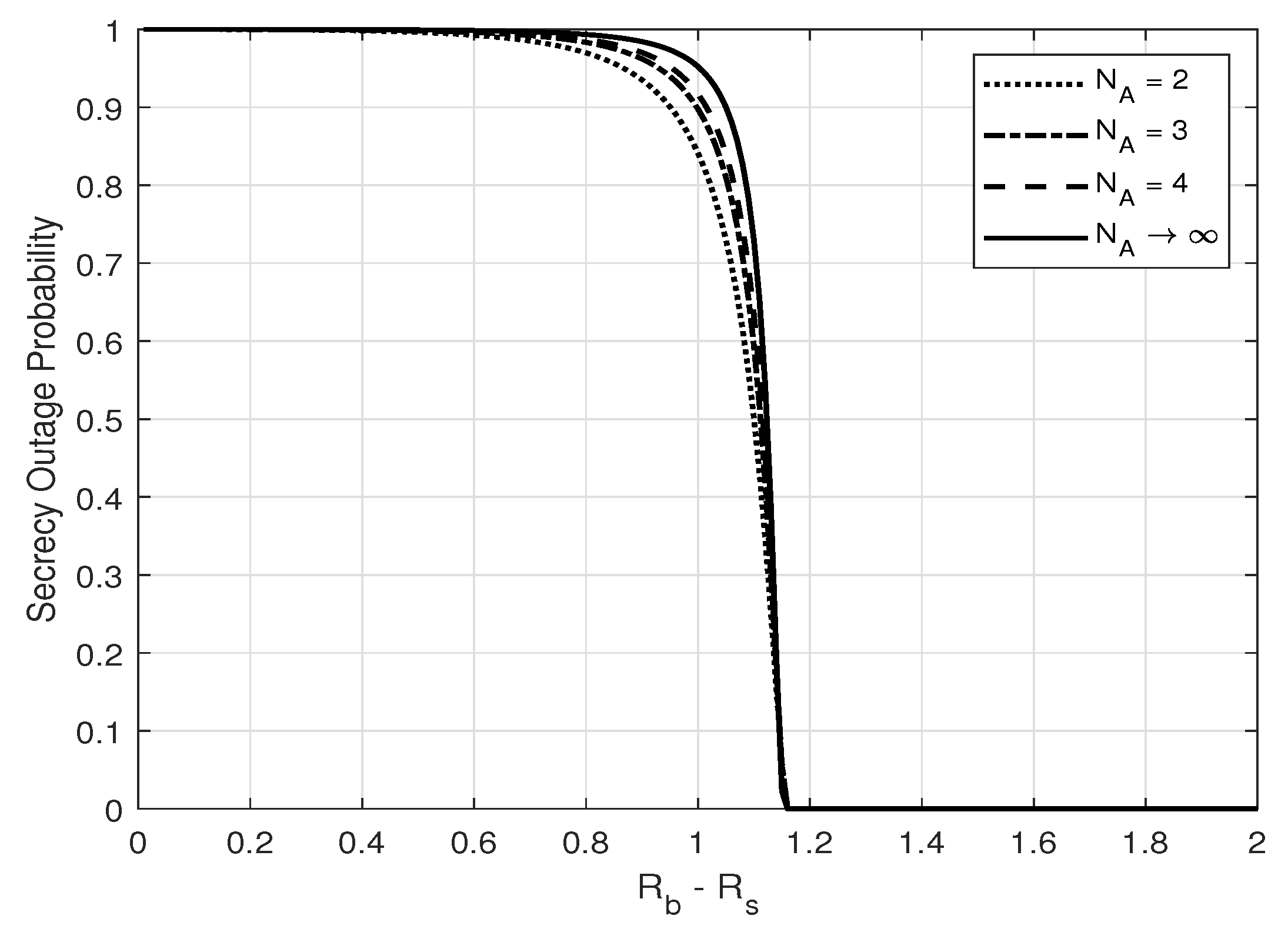
3. Secrecy Outage Probability
4. Connection Outage Probability
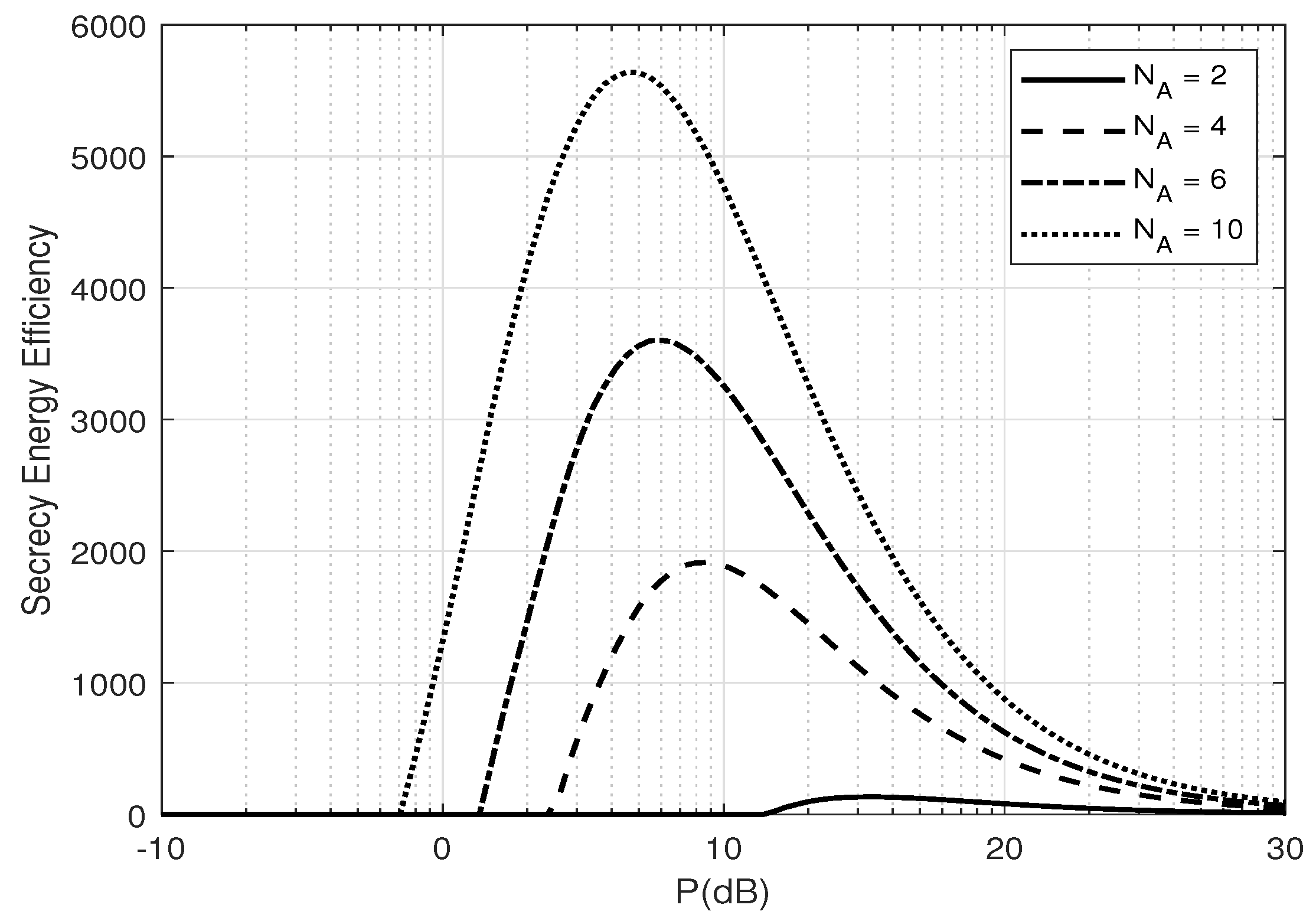
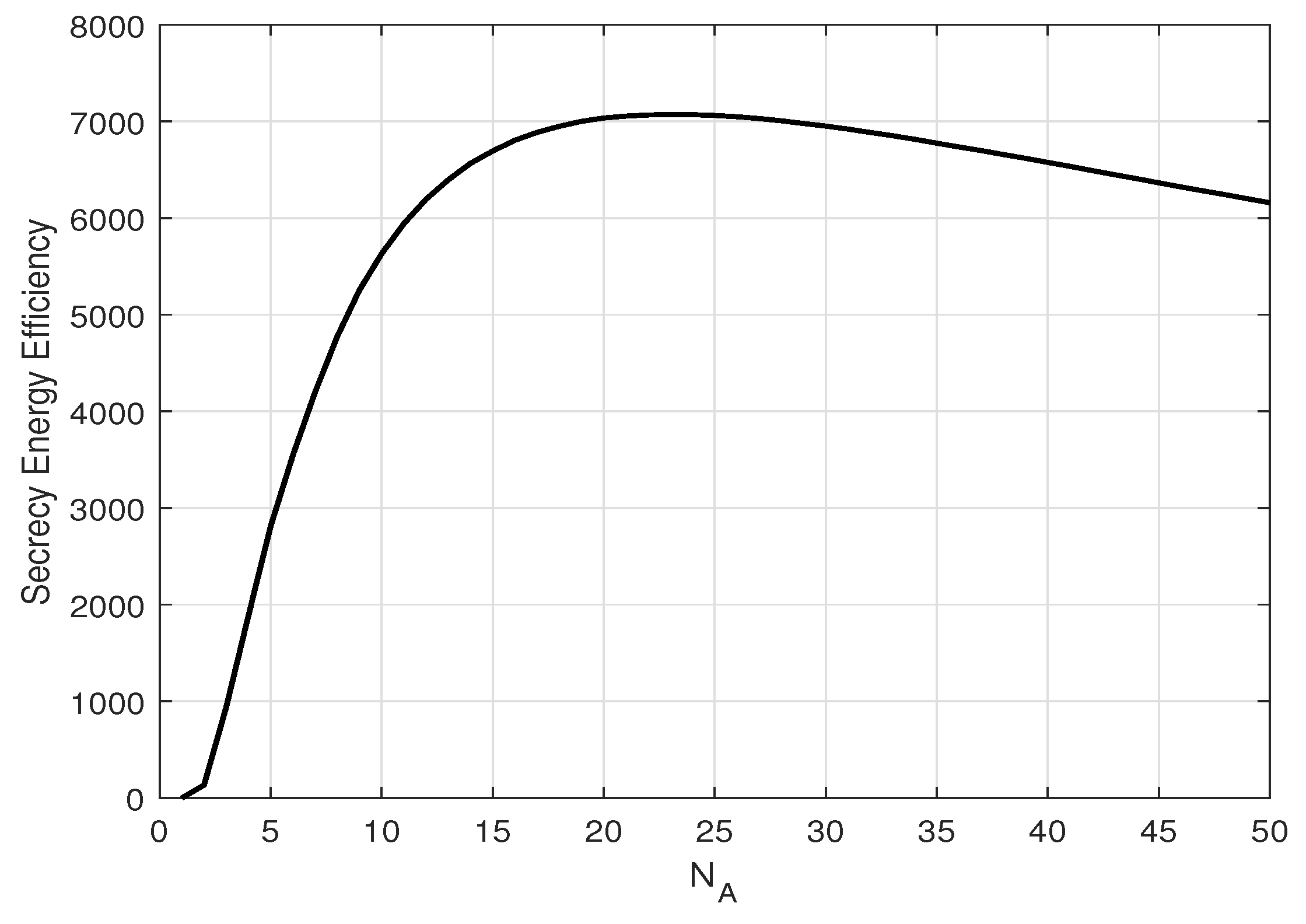
5. Zero-Outage Secrecy Throughput and Energy Efficiency
6. Numerical Results and Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
References
- Heron, S. Advanced encryption standard (AES). Netw. Secur. 2009, 2009, 8–12. [Google Scholar] [CrossRef]
- Milanov, E. The RSA Algorithm; RSA Laboratories: Bedford, MA, USA, 2009; pp. 1–11. [Google Scholar]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Barros, J.; Rodrigues, M.R.D. Secrecy Capacity of Wireless Channels. In Proceedings of the 2006 IEEE International Symposium on Information Theory, Seattle, WA, USA, 9–14 July 2006; pp. 356–360. [Google Scholar] [CrossRef]
- Wang, H.M.; Xia, X.G. Enhancing wireless secrecy via cooperation: Signal design and optimization. IEEE Commun. Mag. 2015, 53, 47–53. [Google Scholar] [CrossRef]
- Goel, S.; Negi, R. Guaranteeing Secrecy using Artificial Noise. IEEE Trans. Wirel. Commun. 2008, 7, 2180–2189. [Google Scholar] [CrossRef]
- He, B.; She, Y.; Lau, V.K. Artificial noise injection for securing single-antenna systems. IEEE Trans. Veh. Technol. 2017, 66, 9577–9581. [Google Scholar] [CrossRef]
- Zheng, G.; Krikidis, I.; Li, J.; Petropulu, A.P.; Ottersten, B. Improving physical layer secrecy using full-duplex jamming receivers. IEEE Trans. Signal Process. 2013, 61, 4962–4974. [Google Scholar] [CrossRef]
- Zheng, T.X.; Wang, H.M.; Yuan, J.; Han, Z.; Lee, M.H. Physical layer security in wireless ad hoc networks under a hybrid full-/half-duplex receiver deployment strategy. IEEE Trans. Wirel. Commun. 2017, 16, 3827–3839. [Google Scholar] [CrossRef]
- Zheng, T.X.; Wang, H.M.; Yang, Q.; Lee, M.H. Safeguarding Decentralized Wireless Networks Using Full-Duplex Jamming Receivers. IEEE Trans. Wirel. Commun. 2017, 16, 278–292. [Google Scholar] [CrossRef]
- Wang, H.M.; Zhao, B.Q.; Zheng, T.X. Adaptive Full-Duplex Jamming Receiver for Secure D2D Links in Random Networks. IEEE Trans. Commun. 2019, 67, 1254–1267. [Google Scholar] [CrossRef]
- Guo, Y. Application of full duplex guarantees secure wireless communication. J. Commun. Networks 2017, 19, 105–113. [Google Scholar] [CrossRef]
- Cao, Z.; Ji, X.; Wang, J.; Zhang, S.; Ji, Y.; Li, Y.; Wang, J. Security-Reliability Trade-Off Analysis of AN-Aided Relay Selection for Full-Duplex Relay Networks. IEEE Trans. Veh. Technol. 2021, 70, 2362–2377. [Google Scholar] [CrossRef]
- Li, B.; Zhang, M.; Rong, Y.; Han, Z. Artificial Noise-Aided Secure Relay Communication With Unknown Channel Knowledge of Eavesdropper. IEEE Trans. Wirel. Commun. 2021, 20, 3168–3179. [Google Scholar] [CrossRef]
- Liu, T.Y.; Lin, P.H.; Lin, S.C.; Hong, Y.W.P.; Jorswieck, E.A. To avoid or not to avoid CSI leakage in physical layer secret communication systems. IEEE Commun. Mag. 2015, 53, 19–25. [Google Scholar] [CrossRef]
- Zhou, X.; Lamahewa, T.A.; Sadeghi, P.; Durrani, S. Two-way training: Optimal power allocation for pilot and data transmission. IEEE Trans. Wirel. Commun. 2010, 9, 564–569. [Google Scholar] [CrossRef]
- Hassibi, B.; Hochwald, B.M. How much training is needed in multiple-antenna wireless links? IEEE Trans. Inf. Theory 2003, 49, 951–963. [Google Scholar] [CrossRef]
- Goldsmith, A. Wireless Communications; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar]
- Zhou, X.; McKay, M.R.; Maham, B.; Hjorungnes, A. Rethinking the Secrecy Outage Formulation: A Secure Transmission Design Perspective. IEEE Commun. Lett. 2011, 15, 302–304. [Google Scholar] [CrossRef]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products, 7th ed.; Elsevier/Academic Press: Amsterdam, The Netherlands, 2007. [Google Scholar]
- Ta, H.Q.; Kim, S.W. Adapting rate and power for maximizing secrecy energy efficiency. IEEE Commun. Lett. 2017, 21, 2049–2052. [Google Scholar] [CrossRef]
- Wang, A.Y.; Sodini, C.G. On the energy efficiency of wireless transceivers. In Proceedings of the 2006 IEEE International Conference on Communications, Istanbul, Turkey, 25–28 June 2006; Volume 8, pp. 3783–3788. [Google Scholar]




Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ta, H.Q.; Cao, L.; Oh, H. Novel Noise Injection Scheme to Guarantee Zero Secrecy Outage under Imperfect CSI. Entropy 2023, 25, 1594. https://doi.org/10.3390/e25121594
Ta HQ, Cao L, Oh H. Novel Noise Injection Scheme to Guarantee Zero Secrecy Outage under Imperfect CSI. Entropy. 2023; 25(12):1594. https://doi.org/10.3390/e25121594
Chicago/Turabian StyleTa, Hien Q., Lam Cao, and Hoon Oh. 2023. "Novel Noise Injection Scheme to Guarantee Zero Secrecy Outage under Imperfect CSI" Entropy 25, no. 12: 1594. https://doi.org/10.3390/e25121594
APA StyleTa, H. Q., Cao, L., & Oh, H. (2023). Novel Noise Injection Scheme to Guarantee Zero Secrecy Outage under Imperfect CSI. Entropy, 25(12), 1594. https://doi.org/10.3390/e25121594





