Cryptanalysis of an Image Encryption Algorithm Based on Two-Dimensional Hyperchaotic Map
Abstract
1. Introduction
2. Description of Original Image Encryption Algorithm
2.1. Two-Dimensional Hyperchaotic System
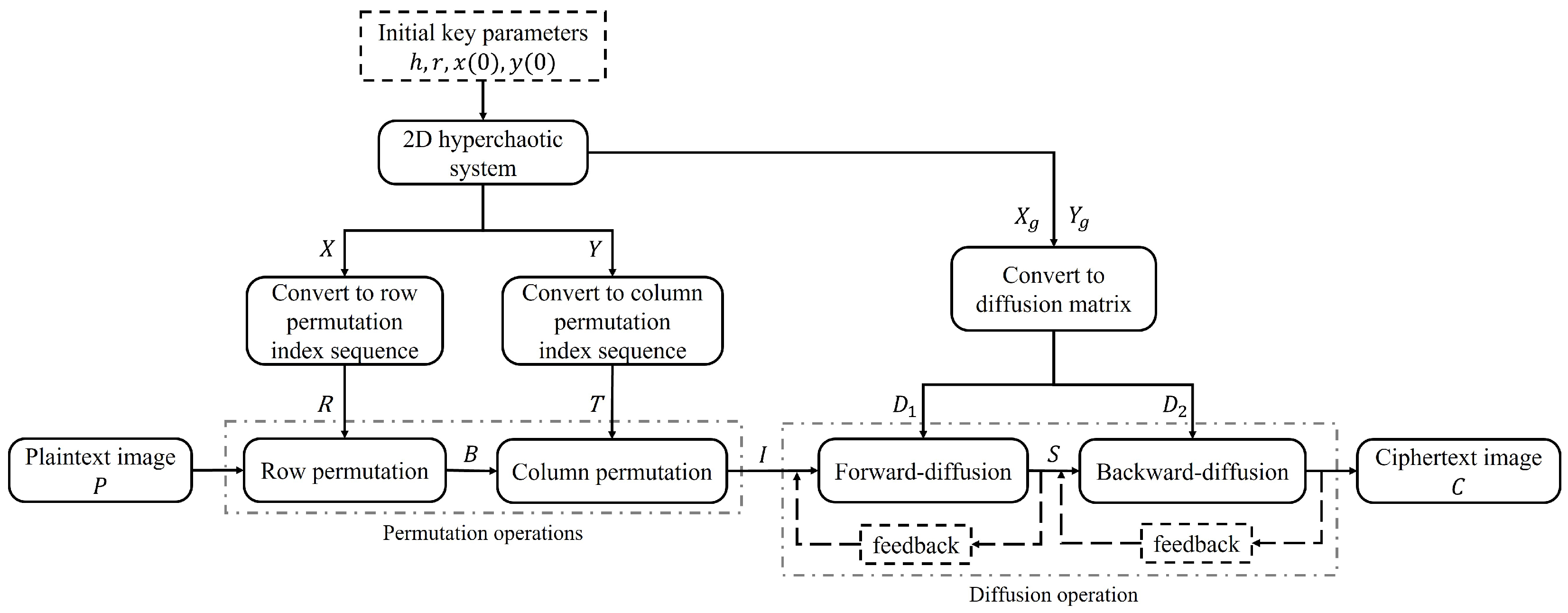
2.2. Description of the Original Encryption Algorithm
- (1)
- Selection of initial key parameters:
- (2)
- Generation of permutation index sequences:
- (3)
- Generation of diffusion matrix:
- (4)
- Encryption process:
3. Security Analysis of the Original Encryption Algorithm
3.1. Overall Analysis
3.2. Analysis of the Two-Round Diffusion Process of the Original Encryption Algorithm
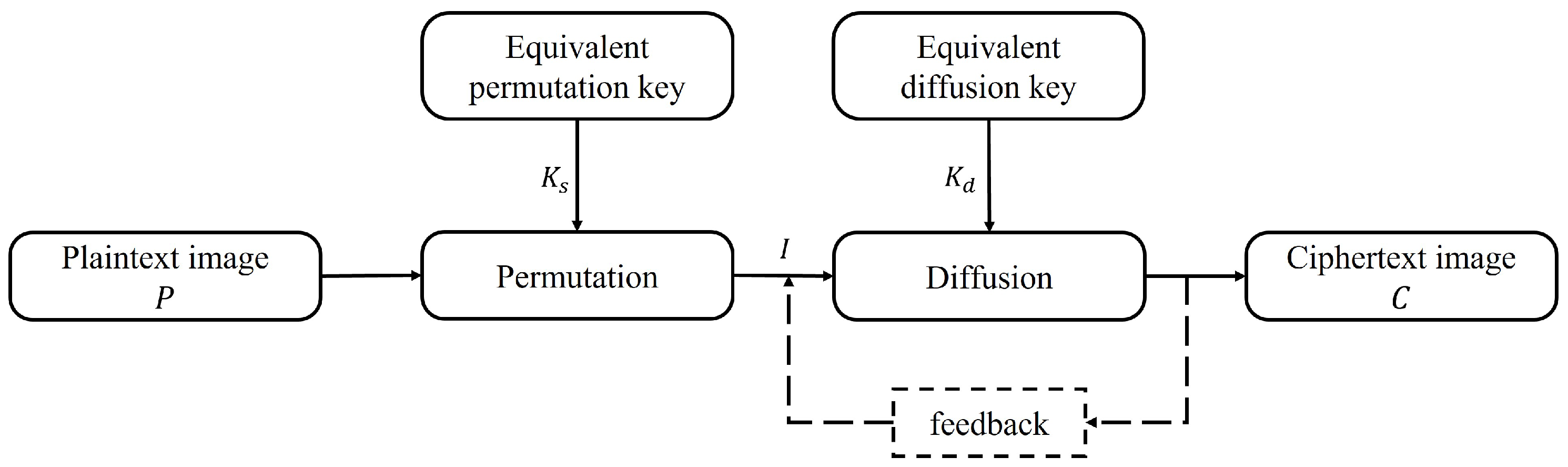
3.2.1. Pre-Analysis of Diffusion Process
3.2.2. The Equivalent Diffusion Key
| Algorithm 1 The procedure of cracking the equivalent diffusion key . |
|
3.2.3. Cracking Diffusion Encryption Process Using Equivalent Diffusion Key
| Algorithm 2 The procedure of cracking the diffusion process. |
|
3.3. Cracking the Permutation Process
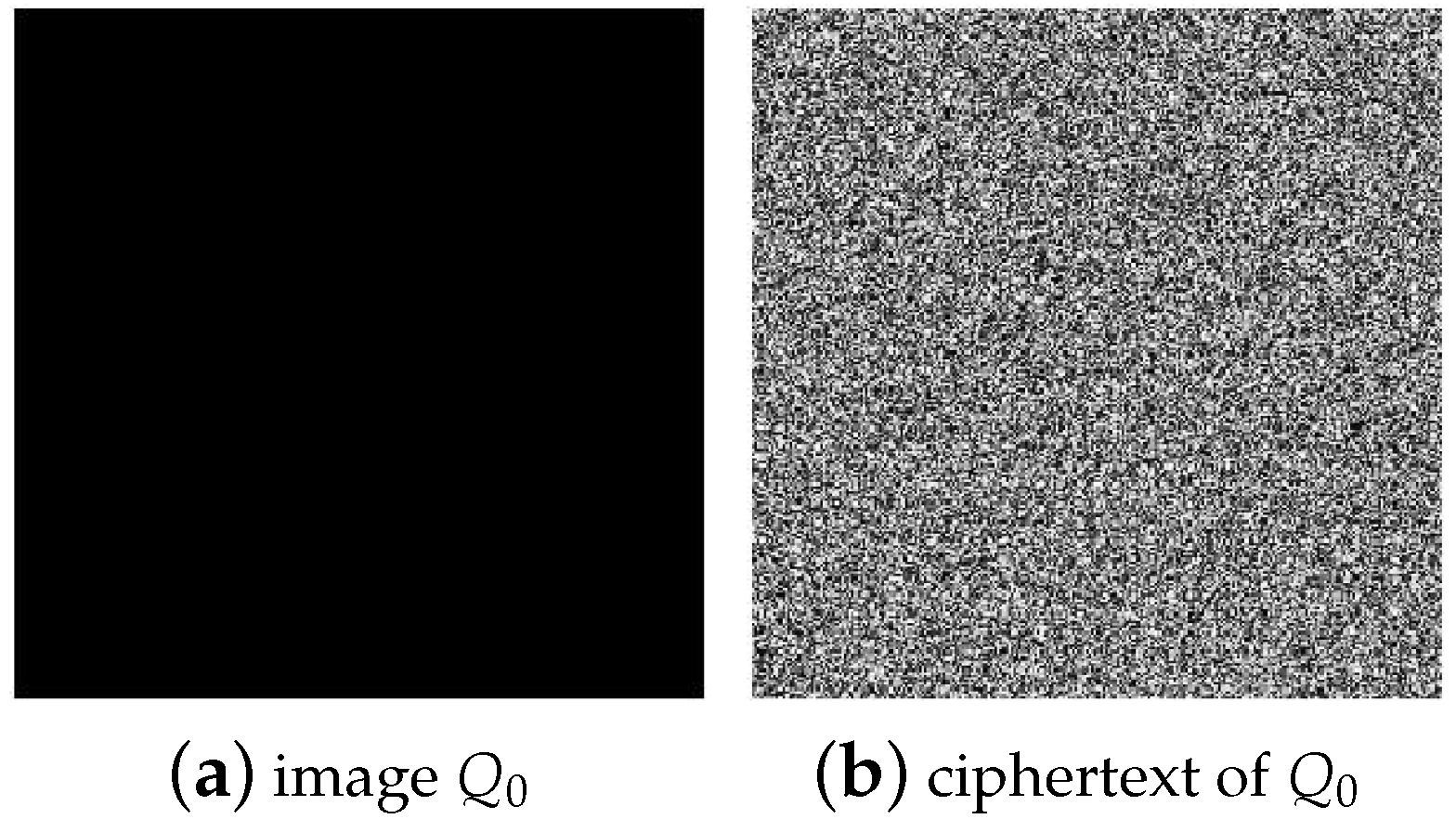
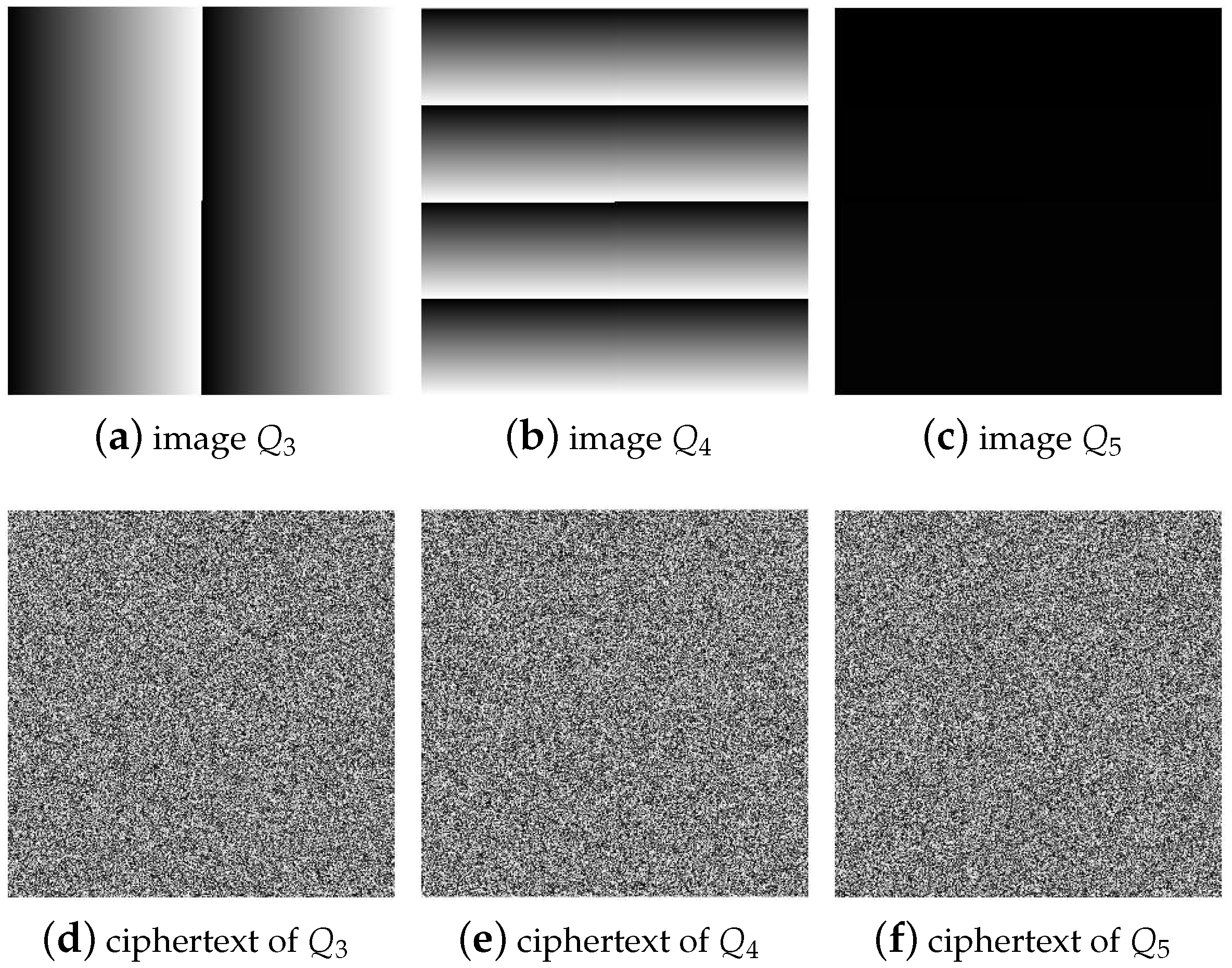
3.3.1. The Construction Method of Plaintext Images
3.3.2. The Equivalent Permutation Key
| Algorithm 3 The procedure of cracking the equivalent permutation key . |
|
3.3.3. Cracking Permutation Encryption Process by Using Equivalent Permutation Key
| Algorithm 4 The procedure of cracking the permutation process by using equivalent permutation key . |
|
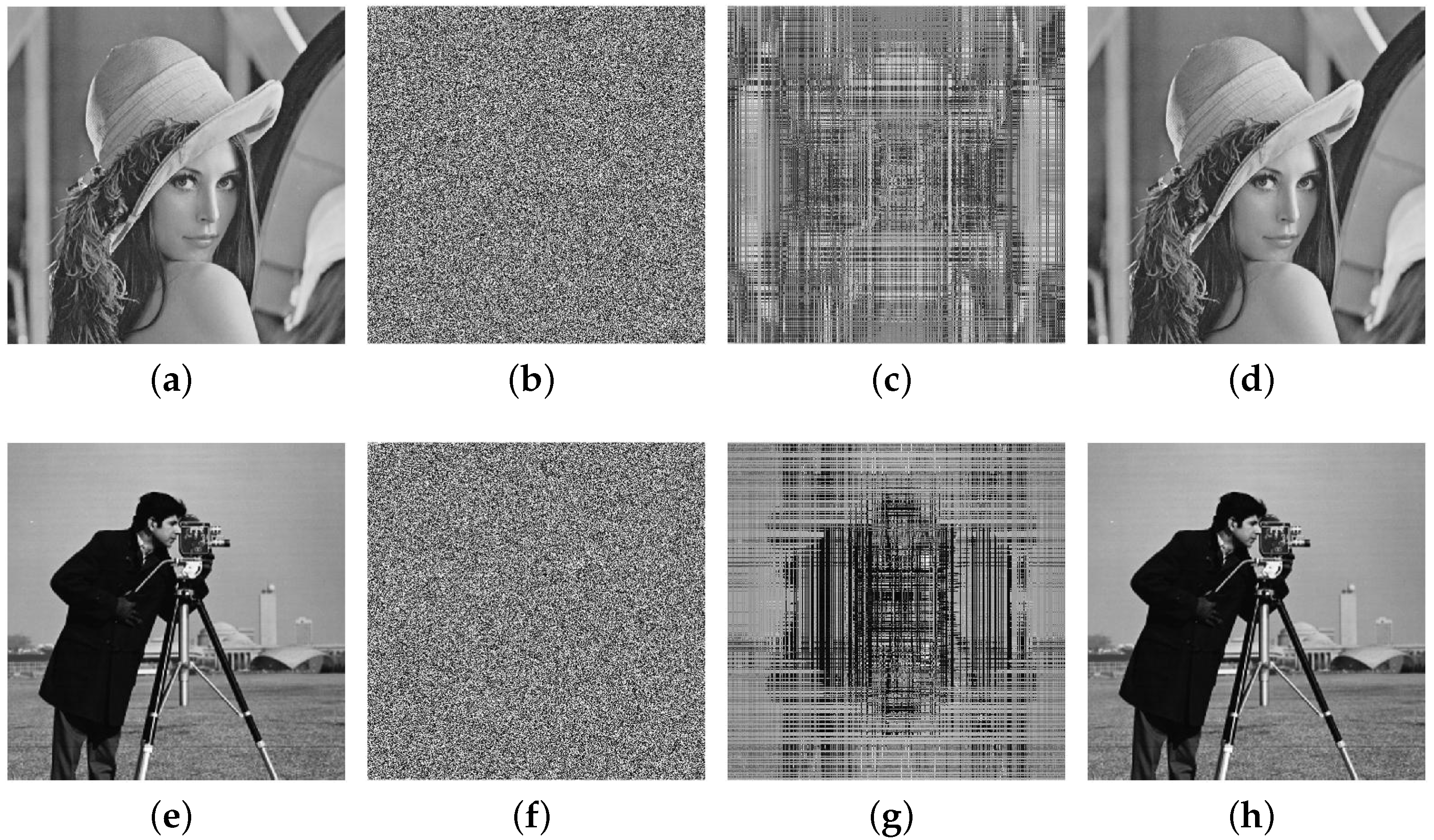
4. Experimental Results
4.1. Experimental Results of Cracking Image by Chosen Plaintext Attack
4.2. Suggestions for Improvement
5. Comparison and Performance Analysis of Cracking Algorithms
5.1. Comparison of Cracking Diffusion Processes
5.2. Comparison of Cracking Permutation Process
5.3. Comparison of Attack Complexity
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Yu, S.; Lü, J.; Li, C. Some progresses of chaotic cipher and its applications in multimedia secure communications. J. Electron. Inf. Technol. 2016, 38, 735–752. [Google Scholar] [CrossRef]
- Li, C.; Luo, G.; Qin, K.; Li, C. An image encryption scheme based on chaotic tent map. Nonlinear Dyn. 2017, 87, 127–133. [Google Scholar] [CrossRef]
- ul Haq, T.; Shah, T. 4D mixed chaotic system and its application to RGB image encryption using substitution-diffusion. J. Inf. Secur. Appl. 2021, 61, 102931. [Google Scholar] [CrossRef]
- Wang, Q.; Yu, S.; Guyeux, C.; Wang, W. Constructing Higher-Dimensional Digital Chaotic Systems via Loop-State Contraction Algorithm. IEEE Trans. Circuits Syst. Regul. Pap. 2021, 68, 3794–3807. [Google Scholar] [CrossRef]
- Fridrich, J. Symmetric ciphers based on two-dimensional chaotic maps. Int. J. Bifurc. Chaos 1998, 8, 1259–1284. [Google Scholar] [CrossRef]
- Geetha, S.; Punithavathi, P.; Infanteena, A.M.; Sindhu, S.S.S. A literature review on image encryption techniques. Int. J. Inf. Secur. Priv. (IJISP) 2018, 12, 42–83. [Google Scholar] [CrossRef]
- Chai, X.; Gan, Z.; Yuan, K.; Chen, Y.; Liu, X. A novel image encryption scheme based on DNA sequence operations and chaotic systems. Neural Comput. Appl. 2019, 31, 219–237. [Google Scholar] [CrossRef]
- Chai, X.; Gan, Z.; Yang, K.; Chen, Y.; Liu, X. An image encryption algorithm based on the memristive hyperchaotic system, cellular automata and DNA sequence operations. Signal Process. Image Commun. 2017, 52, 6–19. [Google Scholar] [CrossRef]
- Zhu, S.; Zhu, C. Secure image encryption algorithm based on hyperchaos and dynamic DNA coding. Entropy 2022, 22, 772. [Google Scholar] [CrossRef]
- Wang, X.; Li, Y. Chaotic image encryption algorithm based on hybrid multi-objective particle swarm optimization and DNA sequence. Opt. Lasers Eng. 2021, 137, 106393. [Google Scholar] [CrossRef]
- Belazi, A.; Khan, M.; El-Latif, A.A.A.; Belghith, S. Efficient cryptosystem approaches: S-boxes and permutation–substitution-based encryption. Nonlinear Dyn. 2017, 87, 337–361. [Google Scholar] [CrossRef]
- Zhu, S.; Wang, G.; Zhu, C. A secure and fast image encryption scheme based on double chaotic S-boxes. Entropy 2019, 21, 790. [Google Scholar] [CrossRef]
- Farah, M.A.; Farah, A.; Farah, T. An image encryption scheme based on a new hybrid chaotic map and optimized substitution box. Nonlinear Dyn. 2020, 99, 3041–3064. [Google Scholar] [CrossRef]
- Wang, X.Y.; Sun, H.H.; Gao, H. An image encryption algorithm based on improved baker transformation and chaotic S-box. Chin. Phys. B 2021, 30, 060507. [Google Scholar] [CrossRef]
- Zhou, N.; Li, H.; Wang, D.; Pan, S.; Zhou, Z. Image compression and encryption scheme based on 2D compressive sensing and fractional Mellin transform. Opt. Commun. 2015, 343, 10–21. [Google Scholar] [CrossRef]
- Zhou, N.; Pan, S.; Cheng, S.; Zhou, Z. Image compression–encryption scheme based on hyper-chaotic system and 2D compressive sensing. Opt. Laser Technol. 2016, 82, 121–133. [Google Scholar] [CrossRef]
- Gong, L.; Qiu, K.; Deng, C.; Zhou, N. An image compression and encryption algorithm based on chaotic system and compressive sensing. Opt. Laser Technol. 2019, 115, 257–267. [Google Scholar] [CrossRef]
- Cheng, G.; Wang, C.; Xu, C. A novel hyper-chaotic image encryption scheme based on quantum genetic algorithm and compressive sensing. Multimed. Tools Appl. 2020, 79, 29243–29263. [Google Scholar] [CrossRef]
- Xu, C.; Sun, J.; Wang, C. A novel image encryption algorithm based on bit-plane matrix rotation and hyper chaotic systems. Multimed. Tools Appl. 2020, 79, 5573–5593. [Google Scholar] [CrossRef]
- Gan, Z.; Chai, X.; Han, D.; Chen, Y. A chaotic image encryption algorithm based on 3-D bit-plane permutation. Neural Comput. Appl. 2019, 31, 7111–7130. [Google Scholar] [CrossRef]
- Wang, S.C.; Wang, C.H.; Xu, C. An image encryption algorithm based on a hidden attractor chaos system and the Knuth–Durstenfeld algorithm. Opt. Lasers Eng. 2020, 128, 105995. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X.; Yan, X.; Li, Q.; Wang, X. Image encryption based on chaotic sub-block scrambling and chaotic digit selection diffusion. Opt. Lasers Eng. 2020, 134, 106202. [Google Scholar] [CrossRef]
- Wu, Z.; Pan, P.; Sun, C.; Zhao, B. Plaintext-related dynamic key chaotic image encryption algorithm. Entropy 2021, 23, 1159. [Google Scholar] [CrossRef] [PubMed]
- Tian, J.; Lu, Y.; Zuo, X.; Liu, Y.; Qiao, B.; Fan, M.; Ge, Q.; Fan, S. A novel image encryption algorithm using PWLCM map-based CML chaotic system and dynamic DNA encryption. Multimed. Tools Appl. 2021, 80, 32841–32861. [Google Scholar] [CrossRef]
- Jiao, K.; Ye, G.; Dong, Y.; Huang, X.; He, J. Image encryption scheme based on a generalized arnold map and RSA algorithm. Secur. Commun. Netw. 2020, 2020, 9721675. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Xu, C.; Zhang, X.; Iu, H.H. A memristive synapse control method to generate diversified multi-structure chaotic attractors. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2022. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Sun, Y.; Wang, T. Generating n-Scroll Chaotic Attractors From A Memristor-based Magnetized Hopfield Neural Network. IEEE Trans. Circuits Syst. II Express Briefs 2022, 70, 311–315. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Cui, L.; Sun, Y.; Xu, C.; Yu, F. Brain-like initial-boosted hyperchaos and application in biomedical image encryption. IEEE Trans. Ind. Inform. 2022, 18, 8839–8850. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Cui, L.; Sun, Y.; Zhang, X.; Yao, W. Hyperchaotic memristive ring neural network and application in medical image encryption. Nonlinear Dyn. 2022, 110, 841–855. [Google Scholar] [CrossRef]
- Wen, H.; Yu, S. Cryptanalysis of an image encryption cryptosystem based on binary bit planes extraction and multiple chaotic maps. Eur. Phys. J. Plus 2019, 134, 337. [Google Scholar] [CrossRef]
- Hu, Y.; Yu, S.; Zhang, Z. On the Cryptanalysis of a Bit-Level Image Chaotic Encryption Algorithm. Math. Probl. Eng. 2020, 2020. [Google Scholar] [CrossRef]
- Hu, G.; Xiao, D.; Wang, Y.; Li, X. Cryptanalysis of a chaotic image cipher using Latin square-based confusion and diffusion. Nonlinear Dyn. 2017, 88, 1305–1316. [Google Scholar] [CrossRef]
- Wu, J.; Liao, X.; Yang, B. Cryptanalysis and enhancements of image encryption based on three-dimensional bit matrix permutation. Signal Process. 2018, 142, 292–300. [Google Scholar] [CrossRef]
- Fan, H.; Lu, H.; Zhang, C.; Li, M.; Liu, Y. Cryptanalysis of an Image Encryption Algorithm Based on Random Walk and Hyperchaotic Systems. Entropy 2021, 24, 40. [Google Scholar] [CrossRef]
- Wen, H.; Yu, S.; Lü, J. Breaking an image encryption algorithm based on DNA encoding and spatiotemporal chaos. Entropy 2019, 21, 246. [Google Scholar] [CrossRef]
- Li, C.; Lin, D.; Feng, B.; Lü, J.; Hao, F. Cryptanalysis of a chaotic image encryption algorithm based on information entropy. IEEE Access 2018, 6, 75834–75842. [Google Scholar] [CrossRef]
- Ma, Y.; Li, C.; Ou, B. Cryptanalysis of an image block encryption algorithm based on chaotic maps. J. Inf. Secur. Appl. 2020, 54, 102566. [Google Scholar] [CrossRef]
- Chen, L.; Li, C.; Li, C. Security measurement of a medical communication scheme based on chaos and DNA coding. J. Vis. Commun. Image Represent. 2022, 83, 103424. [Google Scholar] [CrossRef]
- Gao, X. Image encryption algorithm based on 2D hyperchaotic map. Opt. Laser Technol. 2021, 142, 107252. [Google Scholar] [CrossRef]
- Zhang, C.; Chen, J.; Chen, D. Cryptanalysis of An Image Encryption Algorithm Based on a 2D Hyperchaotic Map. Entropy 2022, 24, 1551. [Google Scholar] [CrossRef]






| Image Size | 32 × 32 | 64 × 64 | 128 × 128 | 256 × 256 | 512 × 512 |
|---|---|---|---|---|---|
| Running time in [40]/s | 8 | 50 | 540 | 7200 | 72,000 |
| Running time in this paper/s | 0.08396 | 0.09188 | 0.13891 | 0.63178 | 8.03338 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, Q.; Yu, S.; Wang, Q. Cryptanalysis of an Image Encryption Algorithm Based on Two-Dimensional Hyperchaotic Map. Entropy 2023, 25, 395. https://doi.org/10.3390/e25030395
Jiang Q, Yu S, Wang Q. Cryptanalysis of an Image Encryption Algorithm Based on Two-Dimensional Hyperchaotic Map. Entropy. 2023; 25(3):395. https://doi.org/10.3390/e25030395
Chicago/Turabian StyleJiang, Qinmao, Simin Yu, and Qianxue Wang. 2023. "Cryptanalysis of an Image Encryption Algorithm Based on Two-Dimensional Hyperchaotic Map" Entropy 25, no. 3: 395. https://doi.org/10.3390/e25030395
APA StyleJiang, Q., Yu, S., & Wang, Q. (2023). Cryptanalysis of an Image Encryption Algorithm Based on Two-Dimensional Hyperchaotic Map. Entropy, 25(3), 395. https://doi.org/10.3390/e25030395






