Cryptographically Secure PseudoRandom Bit Generator for Wearable Technology
Abstract
1. Introduction
1.1. Reducing Dependence on Externally Downloaded Entropy Sources
1.2. Reducing Vulnerability to Single Sensor Attacks
2. Random Generator Security
- True Random Bit Generators (TRBG) produce random sequences based on direct observation of a physical phenomenon.
- Pseudo-Random Bit Generators (PRBG) produce random sequences based on a deterministic algorithm initiated by an entropy source.
- Cryptographically Secure Pseudo-Random Bit Generators (CSPRBG) produce random sequences based on a strong cryptographic algorithm and a protected entropy source.
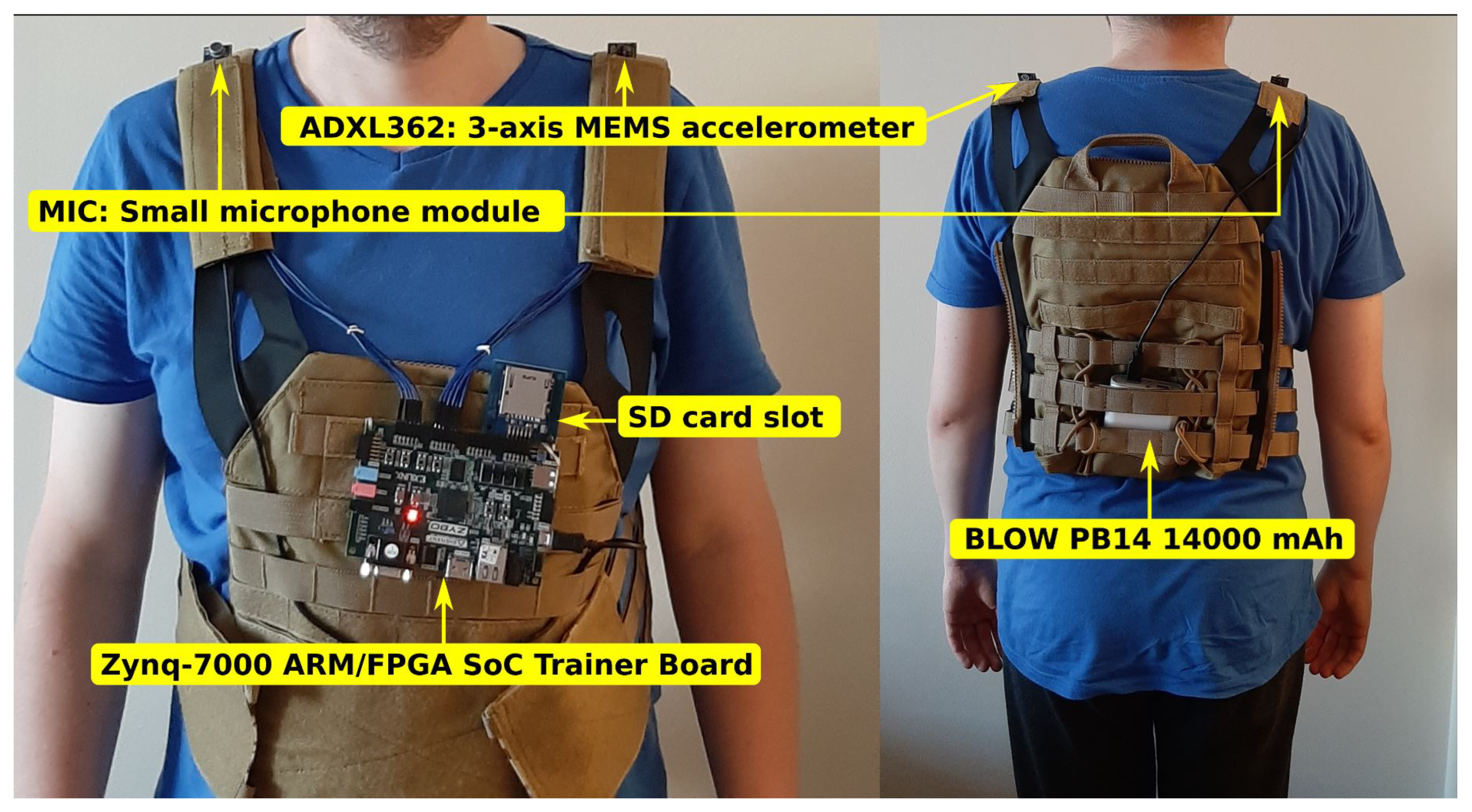
3. Hardware Layer
4. Wearable CSPRBG Performance
5. Randomness of Wearable CSPRBG
6. Future Development of Wearable CSPRBG Platform
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AES | Advanced Encryption Standard |
| AMV | Arithmetic Mean Value |
| ASIC | Application Specific Integrated Circuit |
| BRAM | Block Random Access Memory |
| BUFG | Global clock buffer |
| Comp | Compression Ratio |
| CSPRBG | Cryptographically Secure Pseudo-Random Bit Generator |
| DRBG | Deterministic Random Bit Generator |
| DRNG | Deterministic Random Number Generators |
| DSP | Digital Signal Processing |
| EaaS | Entropy as a Service |
| FF | Flip Flop |
| FPGA | Field Programmable Gate Array |
| GPU | Graphics Processing Unit |
| IO | Input Output |
| IoT | Internet of Things |
| LUT | LookUp Table |
| LUTRAM | LookUp Table Random Access Memory |
| NIST | National Institute of Standards and Technology |
| MC | Monte Carlo Value for |
| MMCM | Mixed-Mode Clock Manager |
| PDK | Process Design Kit |
| PRBG | Pseudo-Random Bit Generator |
| RAM | Random Access Memory |
| RISC | Reduced Instruction Set Computer |
| RISC-V | Reduced Instruction Set Computer-five |
| ROM | Read-Only Memory |
| SCC | Serial Correlation Coefficient |
| SHA | Secure Hash Algorithm |
| SoC | System on Chip |
| SPI | Serial Peripheral Interface |
| SRAM | Static Random-Access Memory |
| TRBG | True Random Bit Generator |
| UART | Universal Asynchronous Receiver-Transmitter |
| USB | Universal Serial Bus |
| VHDL | Very High-Speed Integrated Circuit Hardware Description Language |
| VHDL-AMS | VHDL for Analog and Mixed Signals |
| ZYBO | ZYnq BOard |
References
- Corrigan-Gibbs, H.; Mu, W.; Boneh, D.; Ford, B. Ensuring high-quality randomness in cryptographic key generation. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 685–696. [Google Scholar]
- Dodis, Y.; Guo, S.; Stephens-Davidowitz, N.; Xie, Z. No time to hash: On super-efficient entropy accumulation. In Proceedings of the Advances in Cryptology–CRYPTO 2021: 41st Annual International Cryptology Conference, CRYPTO 2021, Virtual Event, 16–20 August 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 548–576. [Google Scholar]
- Gutterman, Z.; Pinkas, B.; Reinman, T. Analysis of the Linux random number generator. In Proceedings of the 2006 IEEE Symposium on Security and Privacy (S&P’06), Berkeley/Oakland, CA, USA, 21–24 May 2006; pp. 15–385. [Google Scholar] [CrossRef]
- Zhang, C.; Shahriar, H.; Riad, A.K. Security and Privacy Analysis of Wearable Health Device. In Proceedings of the 2020 IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC), Madrid, Spain, 13–17 July 2020; pp. 1767–1772. [Google Scholar]
- Awotunde, J.B.; Jimoh, R.G.; Folorunso, S.O.; Adeniyi, E.A.; Abiodun, K.M.; Banjo, O.O. Privacy and security concerns in IoT-based healthcare systems. In The Fusion of Internet of Things, Artificial Intelligence, and Cloud Computing in Health Care; Springer: Berlin/Heidelberg, Germany, 2021; pp. 105–134. [Google Scholar]
- Arias, O.; Wurm, J.; Hoang, K.; Jin, Y. Privacy and security in internet of things and wearable devices. IEEE Trans. Multi-Scale Comput. Syst. 2015, 1, 99–109. [Google Scholar] [CrossRef]
- Datta, P.; Namin, A.S.; Chatterjee, M. A survey of privacy concerns in wearable devices. In Proceedings of the 2018 IEEE International Conference on Big Data (Big Data), Seattle, WA, USA, 10–13 December 2018; pp. 4549–4553. [Google Scholar]
- Psychoula, I.; Chen, L.; Amft, O. Privacy risk awareness in wearables and the internet of things. IEEE Pervasive Comput. 2020, 19, 60–66. [Google Scholar] [CrossRef]
- Barker, E.B.; Kelsey, J.M. Recommendation for Random Number Generation Using Deterministic Random Bit Generators (Revised); US Department of Commerce, Technology Administration, National Institute of Standards and Technology: Gaithersburg, MD, USA, 2007. [Google Scholar]
- Kelsey, J.; Schneier, B.; Wagner, D.; Hall, C. Cryptanalytic attacks on pseudorandom number generators. In Proceedings of the International Workshop on Fast Software Encryption, Paris, France, 23–25 March 1998; Springer: Berlin/Heidelberg, Germany, 1998; pp. 168–188. [Google Scholar]
- Koyen, Y.; Peetermans, A.; Rozic, V.; Verbauwhede, I. Attacking Hardware Random Number Generators in a Multi-Tenant Scenario. In Proceedings of the 2020 Workshop on Fault Detection and Tolerance in Cryptography (FDTC), Milan, Italy, 13 September 2020; pp. 18–25. [Google Scholar]
- Corrigan-Gibbs, H.; Jana, S. Recommendations for randomness in the operating system, or how to keep evil children out of your pool and other random facts. In Proceedings of the 15th Workshop on Hot Topics in Operating Systems (HotOS {XV}), Kartause Ittingen, Switzerland, 18–20 May 2015. [Google Scholar]
- Kumari, R.; Alimomeni, M.; Safavi-Naini, R. Performance analysis of linux rng in virtualized environments. In Proceedings of the 2015 ACM Workshop on Cloud Computing Security Workshop, Denver, CO, USA, 16 October 2015; pp. 29–39. [Google Scholar]
- Wang, J.; Pan, J.; Wu, X. The entropy source of pseudo random number generators: From low entropy to high entropy. In Proceedings of the 2019 IEEE International Conference on Intelligence and Security Informatics (ISI), Shenzhen, China, 1–3 July 2019; pp. 161–163. [Google Scholar] [CrossRef]
- Coppolino, L.; D’Antonio, S.; Mazzeo, G.; Romano, L. A comprehensive survey of hardware-assisted security: From the edge to the cloud. Internet Things 2019, 6, 100055. [Google Scholar] [CrossRef]
- Cohney, S.; Kwong, A.; Paz, S.; Genkin, D.; Heninger, N.; Ronen, E.; Yarom, Y. Pseudorandom black swans: Cache attacks on CTR_DRBG. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 18–21 May 2020; pp. 1241–1258. [Google Scholar]
- Melosik, M.; Marszalek, W. Trojan attack on the initialization of pseudo-random bit generators using synchronization of chaotic input sources. IEEE Access 2021, 9, 161846–161853. [Google Scholar] [CrossRef]
- Melosik, M.; Sniatala, P.; Marszalek, W. Hardware Trojans detection in chaos-based cryptography. Bull. Pol. Acad. Sci. Tech. Sci. 2017, 65, 725–732. [Google Scholar] [CrossRef][Green Version]
- Vassilev, A.; Staples, R. Entropy as a service: Unlocking cryptography’s full potential. Computer 2016, 49, 98–102. [Google Scholar] [CrossRef][Green Version]
- Bhunia, S.; Tehranipoor, M. The Hardware TrojanWar-Attacks, Myths, and Defenses; Springer: Berlin/Heidelberg, Germany, 2018. [Google Scholar] [CrossRef]
- Paar, C.; Pelzl, J. Understanding Cryptography: A Textbook for Students and Practitioners; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- Nannipieri, P.; Bertolucci, M.; Baldanzi, L.; Crocetti, L.; Di Matteo, S.; Falaschi, F.; Fanucci, L.; Saponara, S. SHA2 and SHA-3 Accelerator Design in a 7 nm Technology within the European Processor Initiative. Microprocess. Microsyst. 2021, 87, 103444. [Google Scholar] [CrossRef]
- McEvoy, R.; Curran, J.; Cotter, P.; Murphy, C. Fortuna: Cryptographically secure pseudo-random number generation in software and hardware. In Proceedings of the 2006 IET Irish Signals and Systems Conference. IET, Dublin, Ireland, 28–30 June 2006; pp. 457–462. [Google Scholar]
- Handkiewicz, A.; Szczęsny, S.; Naumowicz, M.; Katarzyński, P.; Melosik, M.; Śniatała, P.; Kropidłowski, M. SI-Studio, a layout generator of current mode circuits. Expert Syst. Appl. 2015, 42, 3205–3218. [Google Scholar] [CrossRef]
- Hasler, J. The Rise of SoC FPAA Devices. In Proceedings of the 2022 IEEE Custom Integrated Circuits Conference (CICC), Newport Beach, CA, USA, 24–27 April 2022; pp. 1–8. [Google Scholar] [CrossRef]
- Hasler, J. Large-Scale Field-Programmable Analog Arrays. Proc. IEEE 2020, 108, 1283–1302. [Google Scholar] [CrossRef]
- Koziol, S.; Schlottmann, C.; Basu, A.; Brink, S.; Petre, C.; Degnan, B.; Ramakrishnan, S.; Hasler, P.; Balavoine, A. Hardware and software infrastructure for a family of floating-gate based FPAAs. In Proceedings of the 2010 IEEE International Symposium on Circuits and Systems, Paris, France, 30 May–2 June 2010; pp. 2794–2797. [Google Scholar] [CrossRef]
- Marr, B.; Brink, S.; Hasler, P.; Anderson, D.V. A reconfigurable, analog system for efficient stochastic biological computation. In Proceedings of the 2008 IEEE Biomedical Circuits and Systems Conference, Baltimore, MD, USA, 20–22 November 2008; pp. 293–296. [Google Scholar] [CrossRef]
- Ghosh, R.; Tamil, L.S. Computation-efficient and compact FPGA design for a real-time wearable arrhythmia-detector. Biomed. Eng. Adv. 2021, 2, 100019. [Google Scholar] [CrossRef]
- Armato, A.; Nardini, E.; Lanatà, A.; Valenza, G.; Mancuso, C.; Scilingo, E.; De Rossi, D. An FPGA Based Arrhythmia Recognition System for Wearable Applications. In Proceedings of the 2009 Ninth International Conference on Intelligent Systems Design and Applications, Pisa, Italy, 30 November–2 December 2009; pp. 660–664. [Google Scholar] [CrossRef]
- Chen, X.; Sun, L. Campus football application based on FPGA system and GPS wearable electronic equipment. Microprocess. Microsyst. 2021, 81, 103784. [Google Scholar] [CrossRef]
- Pêcheux, F.; Lallement, C.; Vachoux, A. VHDL-AMS and Verilog-AMS as alternative hardware description languages for efficient modeling of multidiscipline systems. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2005, 24, 204–225. [Google Scholar] [CrossRef]
- Melosik, M.; Marszalek, W. A hybrid chaos-based pseudo-random bit generator in VHDL-AMS. In Proceedings of the 2014 IEEE 57th International Midwest Symposium on Circuits and Systems (MWSCAS), College Station, TX, USA, 3–6 August 2014; pp. 435–438. [Google Scholar]
- de la Piedra, A. AES Cores (Compact). 2018. Available online: https://opencores.org/projects/threeaesc (accessed on 15 May 2018).
- Dsocek. 3DES (Triple DES)/DES (VHDL). 2018. Available online: https://opencores.org/projects/3des_vhdl (accessed on 15 May 2018).
- Ninos, S. Twofish 128/192/256. 2018. Available online: https://opencores.org/projects/twofish (accessed on 15 May 2018).
- Digilent. PmodMIC Example Code. 2023. Available online: https://digilent.com/reference/pmod/pmod/mic/example_code (accessed on 15 May 2018).
- Doin, J. SPI Master/Slave Interface. 2018. Available online: https://opencores.org/projects/spi_master_slave (accessed on 15 May 2018).
- Merrifield, S. SD. Available online: https://goo.gl/UPjji5 (accessed on 15 May 2018).
- Bertoni, G.; Daemen, J.; Hoffert, S.; Peeters, M.; Van Assche, G.; Van Keer, R. Keccak in VHDL. Available online: https://keccak.team/hardware.html. (accessed on 15 May 2018).
- Bernmark, E.; Wiktorin, C. A triaxial accelerometer for measuring arm movements. Appl. Ergon. 2002, 33, 541–547. [Google Scholar] [CrossRef]
- Magno, M.; Brunelli, D.; Sigrist, L.; Andri, R.; Cavigelli, L.; Gomez, A.; Benini, L. InfiniTime: Multi-sensor wearable bracelet with human body harvesting. Sustain. Comput. Inform. Syst. 2016, 11, 38–49. [Google Scholar] [CrossRef]
- Rukhin, A.; Soto, J.; Nechvatal, J.; Barker, E.; Leigh, S.; Levenson, M.; Banks, D.; Heckert, A.; Dray, J.; Vo, S.; et al. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; NIST Special Publication 800-22 (revised May 15); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2002. [Google Scholar]
- Dodis, Y.; Pointcheval, D.; Ruhault, S.; Vergniaud, D.; Wichs, D. Security Analysis of Pseudo-Random Number Generators with Input: /Dev/Random is Not Robust. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 647–658. [Google Scholar] [CrossRef]
- Barker, E.; Roginsky, A. Transitioning the Use of Cryptographic Algorithms and Key Lengths; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018. [Google Scholar]
- Walker, J. ENT: A Pseudorandom Number Sequence Test Program–Fourmilab. 2008. Available online: http://www.fourmilab.ch/random/ (accessed on 25 May 2023).
- Yu, W.K.; Li, S.; Yao, X.R.; Liu, X.F.; Wu, L.A.; Zhai, G.J. Protocol based on compressed sensing for high-speed authentication and cryptographic key distribution over a multiparty optical network. Appl. Opt. 2013, 52, 7882–7888. [Google Scholar] [CrossRef]
- SkyWater Open Source PDK. Available online: https://github.com/google/skywater-pdk (accessed on 1 May 2023).
- Caravel. Available online: https://github.com/antmicro/caravel (accessed on 1 May 2023).
- Designing a Chip with an OpenRAM (sky130). Available online: https://openlane.readthedocs.io/en/latest/tutorials/openram.html (accessed on 1 May 2023).
- Shalan, M.; Edwards, T. Building OpenLANE: A 130nm openroad-based tapeout-proven flow. In Proceedings of the 39th International Conference on Computer-Aided Design, Virtual, 2–5 November 2020; pp. 1–6. [Google Scholar]
- Hesham, S.; Shalan, M.; El-Kharashi, M.W.; Dessouky, M. Digital ASIC Implementation of RISC-V: OpenLane and Commercial Approaches in Comparison. In Proceedings of the 2021 IEEE International Midwest Symposium on Circuits and Systems (MWSCAS), Lansing, MI, USA, 9–11 August 2021; pp. 498–502. [Google Scholar]
- Crocetti, L.; Di Matteo, S.; Nannipieri, P.; Fanucci, L.; Saponara, S. Design and test of an integrated random number generator with all-digital entropy source. Entropy 2022, 24, 139. [Google Scholar] [CrossRef]
- Della Sala, R.; Bellizia, D.; Scotti, G. High-Throughput FPGA-Compatible TRNG Architecture Exploiting Multistimuli Metastable Cells. IEEE Trans. Circuits Syst. I Regul. Pap. 2022, 69, 4886–4897. [Google Scholar] [CrossRef]
- Xue, M.; Gu, C.; Liu, W.; Yu, S.; O’Neill, M. Ten years of hardware Trojans: A survey from the attacker’s perspective. IET Comput. Digit. Tech. 2020, 14, 231–246. [Google Scholar] [CrossRef]
- Yu, F.; Kong, X.; Mokbel, A.A.M.; Yao, W.; Cai, S. Complex Dynamics, Hardware Implementation and Image Encryption Application of Multiscroll Memeristive Hopfield Neural Network with a Novel Local Active Memeristor. IEEE Trans. Circuits Syst. II Express Briefs 2022, 70, 326–330. [Google Scholar] [CrossRef]
- Yu, F.; Zhang, Z.; Shen, H.; Huang, Y.; Cai, S.; Jin, J.; Du, S. Design and FPGA implementation of a pseudo-random number generator based on a Hopfield neural network under electromagnetic radiation. Front. Phys. 2021, 9, 690651. [Google Scholar] [CrossRef]
- Tirdad, K.; Sadeghian, A. Hopfield neural networks as pseudo random number generators. In Proceedings of the 2010 Annual Meeting of the North American Fuzzy Information Processing Society, Toronto, ON, Canada, 12–14 July 2010; pp. 1–6. [Google Scholar]
- Fiori, S. Neural systems with numerically-matched input–output statistic: Variate generation. Neural Process. Lett. 2006, 23, 143–170. [Google Scholar] [CrossRef]
- Alcin, M.; Koyuncu, İ.; Tuna, M.; Varan, M.; Pehlivan, İ. A novel high speed artificial neural network–based chaotic true random number generator on field programmable gate array. Int. J. Circuit Theory Appl. 2019, 47, 365–378. [Google Scholar] [CrossRef]



| License | Repository | Reference | |
|---|---|---|---|
| AES | GPL | opencores.org | [34] |
| 3DES | CoreTex Systems | opencores.org | [35] |
| TWOFISH | GPL | opencores.org | [36] |
| PmodMICRefComp | Digilent Ro. | reference.digilentinc.com | [37] |
| SPI | LGPL | opencores.org | [38] |
| SD | Steven J. Merrifield | stevenmerrifield.com | [39] |
| SHA-3 | Team Keccak | keccak.team | [40] |
| Symbol on Figure 2 | Tag on ZYBO Device | Function |
|---|---|---|
| sw(0) | SW0 | System reset; |
| active with high state | ||
| sw(1) | SW1 | System start-up; |
| active with high state | ||
| sw(2) | SW2 | not connected |
| sw(3) | SW3 | enable/disable the |
| random data recording |
| # of Resources Used | Utilization Percent | ||||||
|---|---|---|---|---|---|---|---|
| FPGA Resource * | AES | 3DES | TWOFISH | AES | 3DES | TWOFISH | Max |
| (# Available) | diff | ||||||
| LUT (17600) | 7576 | 7594 | 8554 | 43.0% | 43.1% | 48.6% | 5.6% |
| LUTRAM (6000) | 66 | 192 | 66 | 1.1% | 3.2% | 1.1% | 2.1% |
| FF (35200) | 5511 | 5632 | 5621 | 15.7% | 16.0% | 16.0% | 0.3% |
| BRAM (60) | 11 | 2 | 6 | 18.3% | 3.3% | 10.0% | 15.0% |
| DSP (80) | 48 | 48 | 48 | 60.0% | 60.0% | 60.0% | 0.0% |
| IO (100) | 19 | 19 | 19 | 19.0% | 19.0% | 19.0% | 0.0% |
| BUFG (32) | 5 | 5 | 6 | 15.6% | 15.6% | 18.8% | 3.1% |
| MMCM (2) | 1 | 1 | 1 | 50.0% | 50.0% | 50.0% | 0.0% |
| Test Name | |||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Algorithm Name | Entropy Source | Frequency | Ferequency within a Block | Runs | Longest Run of Ones | Rank | Spectral | Non- Overlapping | Overlapping | Maurer’s Universal | Serial | Approximate Entropy | Cumulative Sums | Random Excursions | Random Excursions Variant | Linear Complexity | Failed Tests |
| AES | e1 | 0 | 0 | 0 | 0 | 0 | 0 | 1/148 | 0 | 0 | 0/2 | 0 | 0/2 | 0/8 | 0/18 | 0 | 1/188 |
| e2 | 0 | 0 | 0 | 0 | 0 | 0 | 1/148 | 0 | 0 | 0/2 | 0 | 0/2 | 0/8 | 0/18 | 0 | 1/188 | |
| e3 | 0 | 0 | 0 | 0 | 0 | 0 | 1/148 | 0 | 0 | 0/2 | 0 | 0/2 | 1/8 | 0/18 | 0 | 2/188 | |
| e4 | 0 | 0 | 0 | 0 | 0 | 0 | 0/148 | 0 | 0 | 0/2 | 0 | 0/2 | 0/8 | 1/18 | 0 | 1/188 | |
| e5 | 0 | 0 | 0 | 0 | 0 | 0 | 0/148 | 0 | 0 | 0/2 | 0 | 0/2 | 0/8 | 0/18 | 0 | 0/188 | |
| e6 | 0 | 0 | 0 | 0 | 0 | 0 | 0/148 | 0 | 0 | 0/2 | 0 | 0/2 | 0/8 | 0/18 | 0 | 0/188 | |
| 3DES | e1 | 0 | 1 | 0 | 0 | 1 | 0 | 0/148 | 0 | 1 | 2/2 | 1 | 0/2 | 0/8 | 0/18 | 0 | 5/188 |
| e2 | 0 | 1 | 0 | 0 | 0 | 0 | 1/148 | 0 | 1 | 2/2 | 1 | 0/2 | 0/8 | 0/18 | 0 | 4/188 | |
| e3 | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | |
| e4 | 0 | 1 | 0 | 0 | 1 | 1 | 3/148 | 0 | 1 | 0/2 | 1 | 0/2 | 0/8 | 0/18 | 0 | 8/188 | |
| e5 | 0 | 1 | 0 | 0 | 1 | 0 | 1/148 | 0 | 1 | 0/2 | 1 | 0/2 | 0/8 | 0/18 | 0 | 5/188 | |
| e6 | 1 | 1 | 0 | 0 | 1 | 0 | 5/148 | 0 | 1 | 2/2 | 1 | 1/2 | 0/8 | 0/18 | 0 | 11/188 | |
| TWOFISH | e1 | 1 | 0 | 0 | 0 | 0 | 0 | 20/148 | 0 | 0 | 1/2 | 1 | 2/2 | 0/8 | 0/18 | 0 | 25/188 |
| e2 | 1 | 1 | 1 | 0 | 0 | 0 | 36/148 | 0 | 0 | 1/2 | 1 | 2/2 | 0/8 | 0/18 | 0 | 43/188 | |
| e3 | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | - | |
| e4 | 0 | 0 | 0 | 0 | 0 | 0 | 0/148 | 0 | 0 | 0/2 | 0 | 0/2 | 0/8 | 0/18 | 0 | 0/188 | |
| e5 | 0 | 0 | 0 | 0 | 0 | 0 | 0/148 | 0 | 0 | 0/2 | 0 | 0/2 | 0/8 | 0/18 | 0 | 0/188 | |
| e6 | 0 | 0 | 0 | 0 | 0 | 0 | 0/148 | 0 | 0 | 0/2 | 0 | 0/2 | 0/8 | 0/18 | 0 | 0/188 | |
| Algorithm Name | Entropy Sources | Entropy | Comp % | ; % | AMV | MC % | SCC |
|---|---|---|---|---|---|---|---|
| AES | e1 | 7.999999 | 0 | 215.84; 90 | 127.5081 | 0 | 0.000169 |
| e2 | 7.999999 | 0 | 219.26; 90 | 127.5009 | 0.01 | −0.000011 | |
| e3 | 7.999999 | 0 | 273.84; 25 | 127.5055 | 0.01 | 0.00001 | |
| e4 | 7.999999 | 0 | 248.23; 50 | 127.508 | 0.01 | −0.000118 | |
| e5 | 7.999999 | 0 | 256.58; 50 | 127.5026 | 0.02 | 0.000004 | |
| e6 | 7.999999 | 0 | 254.27; 50 | 127.5068 | 0.01 | 0.000179 | |
| 3DES | e1 | 7.999999 | 0 | 371.06; 0.01 | 127.5076 | 0.13 | 0.015556 |
| e2 | 7.999998 | 0 | 285.66; 10 | 127.505 | 0.12 | 0.015738 | |
| e3 | - | - | - | - | - | - | |
| e4 | 7.999998 | 0 | 312.24; 1 | 127.5025 | 0.11 | 0.015595 | |
| e5 | 7.999998 | 0 | 296.90; 5 | 127.5068 | 0.11 | 0.015703 | |
| e6 | 7.999998 | 0 | 281.63; 25 | 127.4937 | 0.12 | 0.015712 | |
| Twofish | e1 | 7.998618 | 0 | 256004.59; 0.01 | 127.7015 | 0.23 | 0.000408 |
| e2 | 7.999877 | 0 | 21359.31; 0.01 | 126.7808 | 0.34 | −0.018447 | |
| e3 | 6.598928 | 17 | 554932457.50; 0.01 | 124.6524 | 7.93 | −0.098951 | |
| e4 | 7.999999 | 0 | 225.75; 90 | 127.4936 | 0 | −0.000138 | |
| e5 | 7.999999 | 0 | 259.01; 50 | 127.5029 | 0.01 | −0.00013 | |
| e6 | 7.999999 | 0 | 239.56; 50 | 127.5027 | 0 | −0.000148 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Melosik, M.; Galan, M.; Naumowicz, M.; Tylczyński, P.; Koziol, S. Cryptographically Secure PseudoRandom Bit Generator for Wearable Technology. Entropy 2023, 25, 976. https://doi.org/10.3390/e25070976
Melosik M, Galan M, Naumowicz M, Tylczyński P, Koziol S. Cryptographically Secure PseudoRandom Bit Generator for Wearable Technology. Entropy. 2023; 25(7):976. https://doi.org/10.3390/e25070976
Chicago/Turabian StyleMelosik, Michał, Mariusz Galan, Mariusz Naumowicz, Piotr Tylczyński, and Scott Koziol. 2023. "Cryptographically Secure PseudoRandom Bit Generator for Wearable Technology" Entropy 25, no. 7: 976. https://doi.org/10.3390/e25070976
APA StyleMelosik, M., Galan, M., Naumowicz, M., Tylczyński, P., & Koziol, S. (2023). Cryptographically Secure PseudoRandom Bit Generator for Wearable Technology. Entropy, 25(7), 976. https://doi.org/10.3390/e25070976






