4.4.1. The First Stage Detection Method Based on Entropy
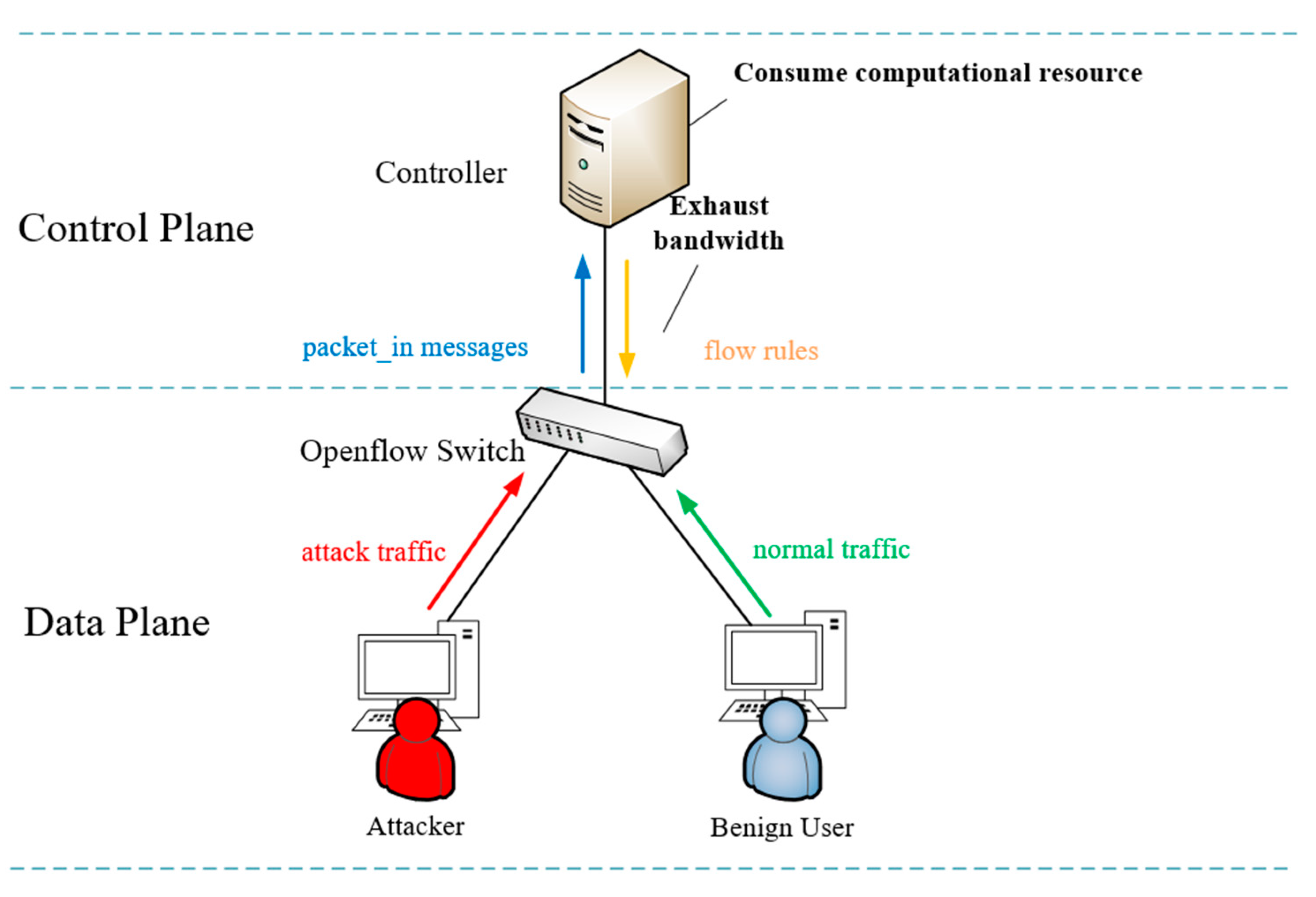
Both high-speed DDoS attacks and flash events will generate a large number of data packets in a short time, and these data packets cannot match the flow rules in the switch, so a large number of packet_in messages will be generated and sent to the controller, causing the controller service interruption. Therefore, the traffic characteristics of flash events are similar to high-speed DDoS attack flows, so it is difficult to distinguish them from DDoS flows. So, in the early stage of detection, we use the method of information entropy to preliminarily judge the abnormal flow and exclude the false detection caused by flash events.
Based on the above discussion, we propose to calculate the entropy of the source IP and destination IP in the packet_in message to determine whether an anomaly occurs. The entropy value calculation is shown in Equation (10), and the source IP entropy and destination IP entropy calculations are shown in Equations (11) and (12), respectively. If the above two indicators do not satisfy
, the preliminary detection will judge that there is a suspicious flow; otherwise, the judgment will be for a flash flow.
In Equation (10), is the probability of samples per unit of time. The data sample indicates that the sample occurred times per unit time . denotes the total number of samples per unit time . When the sample values are most concentrated, the entropy is 0, and all of the sample values are the same. Entropy is highest when the distribution of samples is most spread out, at which point all sample values are different. This method does not need to train the model and has low computational complexity and a short detection time.
- 1.
Entropy of the source IP
When a DDoS attack occurs, attackers usually randomly generate many false source IP packets, causing an increase in the source IP address and an increase in the source IP entropy. When a flash event occurs, thousands of legitimate users accessing a specific host or server can also cause the source IP entropy to increase.
In Equation (11), denotes the frequency of occurrence of the source IP entropy value in packet_in messages per unit time t.
- 2.
Entropy of the destination IP
When a DDoS attack occurs, as the attack target is an SDN controller, the attacker can widely send the attack stream to the target host, resulting in a high entropy value for the destination IP of the attack stream. However, the characteristic of flash events is that different source IP addresses flow into a small number of target hosts, resulting in a smaller entropy value for the destination IP. Therefore, the IP entropy serves as one of the important criteria for distinguishing abnormal flows.
In Equation (12), denotes the frequency of occurrence of the destination IP entropy value in packet_in messages per unit time t.
To effectively distinguish abnormal flow, the threshold setting is important. The setting of the threshold follows the hypothesis testing method in statistics. Confidence intervals for entropy are calculated from the number of samples
N, the mean value
µ of the samples, and the standard deviation σ of the samples. Then, the detection threshold is determined based on the average of the confidence intervals. The confidence interval
is calculated as shown in Equation (13).
In Equation (13),
stands for the confidence level, which is a predetermined standard used in hypothesis testing to evaluate events with low likelihood. According to the standard normal distribution table, when the
is 5%, the
is 1.96 [
25].
4.4.2. The Second-Stage Detection Method Based on CNN-GRU-Attention
Through the first stage of coarse-grained detection, it was preliminarily determined whether there were suspicious flows in the SDN network. In order to improve the detection accuracy, the deep learning hybrid model CNN-GRU-Attention is used for fine-grained detection in the second stage. The specific process is described as follows.
- 1.
Feature selection
In machine learning, feature selection directly affects the performance of the overall algorithm. Selecting good features will improve the accuracy of the algorithm, but selecting too many irrelevant features will increase the complexity of the algorithm and affect its accuracy. To better validate the superiority of the proposed anomaly detection model, we selected 19 commonly used fields from the switch flow table as feature inputs. Among them, there were 12 matching domain fields (i.e., fields in the packet header), two counter fields, two timeout fields, one priority field, one action field, and one cookie field in the flow table entries that could reflect the characteristics of DDoS attack flows. In addition, according to the nature of the flow features, we manually constructed five statistical features as another part of the feature input to improve the accuracy of the CNN-GRU-Attention anomaly detection model. The statistical features are described as follows. The input features of the CNN-GRU-Attention model are shown in
Table 2.
- (1)
Average value of packets in the flow rule (Avg_packets)
DDoS attacks typically forge a large number of source IP address packets to attack the target to prevent the defender from tracking the source. Therefore, the number of packets under each flow rule in the flow table will decrease sharply. Conversely, using a fixed source IP address for DDoS attacks can significantly increase the number of packets under each flow rule.
In Equation (14), denotes the average of the number of packets per unit time in flow rule , and duration denotes the duration of flow rule .
- (2)
Average of packet sizes in the flow rule (Avg_bytes)
DDoS attacks usually send a large number of packets in a short period of time, but the size of the packets is much smaller than normal packets, so the size of the packets can be one of the important criteria to distinguish whether an attack has occurred or not.
In Equation (15), denotes the average value of packet size per unit time in flow rule , and denotes the duration of flow rule .
- (3)
Average survival time of the flow rule (Avg_duration)
DDoS attacks usually send a large number of fake IP packets in a short period of time, with the aim of taking up the target’s resources. The duration of these fake packets surviving under the flow rules is short compared to normal packets. Conversely, with fixed source IP addresses for DDoS attacks, the flow rule survival time increases significantly. Flow rule survival time can, therefore, be used as one of the important criteria to distinguish whether an attack has occurred or not.
In Equation (16), denotes the average duration of each flow rule, denotes the duration of flow rule , and is the number of samples.
- (4)
Survival degree of the flow rule (survival_degree)
Similarly, flow rules generated under DDoS attacks are less survivable than normal flow rules.
In Equation (17), is the duration of flow rule , and is the idle time of flow rule .
- (5)
Upper and lower flow ratio (Ratio_packets)
When a DDoS attack occurs, a huge amount of traffic flows to the victim, and the victim cannot respond properly. As a result, the ratio of upstream to downstream flow during DDoS is abnormal. Here, we define the packets from the switch to the terminal as the uplink flow and the packets from the terminal to the switch as the downlink flow. In the case of a DDoS attack, the ratio will be less than 1.
In Equation (18), denotes the packets sent from the switch viewpoint per unit time , and denotes the number of packets received from the switch viewpoint per unit time .
- 2.
CNN-GRU-Attention detection model
Deep learning has achieved success in the field of intrusion detection research because of its powerful feature extraction ability. CNN [
26] abstracts local features of data through convolution operations to realize data feature extraction in the spatial dimension. GRU preserves the historical information of data through the connection of neurons in the hidden layer and realizes the data features extracted in the time dimension. The self-attention mechanism [
27] can capture relevant spatiotemporal features more accurately, to reduce the negative impact caused by error or redundant feature information and improve classification performance. In this paper, CNN and GRU are used to extract the spatial and temporal features of network flow, respectively, and the self-attention mechanism is introduced into the CNN-GRU model to improve the classification accuracy of the detection algorithm. The CNN-GRU-Attention model structure is shown in
Figure 5, and the structural parameters are shown in
Table 3.
Due to significant differences in the numerical values of the collected network flow data, to improve the accuracy of training, the sample data is normalized and then divided into the training set and test set according to 8:2. The sample labels are converted into binary (0 and 1) representation using one-hot encoding. In the CNN-GRU-Attention model structure, the convolution kernel size in the convolutional layer is 3, the step size is 1, and the RELU activation function is used to prevent the gradient from disappearing, increase the nonlinearity of the network, and make the network training faster. The pooling layer uses Maxpooling, and the kernel size is 2. The Maxpooling layer has the characteristics of translation invariance, which can reduce the parameters to reduce the dimension and prevent overfitting while retaining the main features. The activation function of the GRU layer uses the hyperbolic tangent function Tanh, and the output mapping is between [−1, 1], with a limited output range and stable optimization. Finally, the softmax function is used to classify the network flow.
- A.
CNN layer
The convolutional neural network, as a feedforward neural network, uses the idea of local correlation and weight sharing to reduce neural network parameters and achieve higher training efficiency. CNN is mainly composed of three parts: convolutional layer, pooling layer, and fully connected layer. The convolution layer extracts the feature information of the data by performing correlation operations on the matrix of each channel through the convolution kernel and increases the expression ability of the model through the non-activation function. The convolutional layer Equation is as follows:
In Equation (19), is the ith feature in the output of layer ; is the network nonlinear function RELU; is the weight of the th convolution kernel in the th layer; denotes the convolution operation; is the input of layer . is the bias of the kernel of the th convolution kernel in the th layer.
The role of the pooling layer is to reduce the size of the feature map and simplify the complexity of network calculation. At the same time, the features are compressed to retain salient features and prevent overfitting. Pooling layers are usually sandwiched between successive convolutional layers. The function of the fully connected layer is to integrate the features calculated by the convolutional layer and the pooling layer into the sample space. Fully connected layers are usually placed at the end of the convolutional neural network architecture.
- B.
GRU layer
After multiple convolutions and pooling to extract more accurate frequency and spatial domain features, the GRU layer is used as the input data of the GRU network. Among them, the update gate of GRU is close to 0, which means that some information about the hidden state of the previous layer is forgotten in this hidden layer. The update gate is close to 1, indicating that this hidden layer continues to be retained. When the reset gate of GRU is close to 0, it means that some information at the previous time is forgotten in the current memory content. The reset gate is close to 1, indicating continued retention in the current memory content. Then, the two pieces of information are added and passed through the tanh activation function to normalize the result to between [−1, 1]. Therefore, the memory content of this moment is composed of two parts: one is the reset gate to store the important information related to the past, and the other is the important information input at the current moment. These two parts compose all of the memory content of the current moment to extract the stream feature. The structural diagram of the GRU unit is shown in
Figure 6.
Two gates are obtained by the last transmission state
and the input
of the current node, the update gate
and reset gate
are represented as follows:
In Equations (20)–(23), and are the weight and bias of the update gate, respectively; and are the weight and bias of the reset gate, respectively; is the candidate state at time ; is the sigmoid function.
- C.
Self-attention layer
For each flow, not all bytes are equally important for classification. To make the relatively important information in the stream have a strong influence on the classification results, this paper introduces the attention mechanism. In the attention mechanism, the core operation is the calculation of the weight of each element. In this paper, the feature vector
output by the feature extraction layer is used as the input of the attention layer, and the flow feature vector
is obtained by weighted summation of the hidden states at each time step.
In Equations (24)–(26), is the weight coefficient of ; is the hidden layer generated by through a feedforward neural network layer; and are the weight matrix and bias, respectively.