New Quantum Private Comparison Using Four-Particle Cluster State
Abstract
1. Introduction
2. Quantum Private Comparison Protocol
2.1. Preliminaries
2.2. Protocol Description
3. Correctness
3.1. An Example of the Proposed Protocol
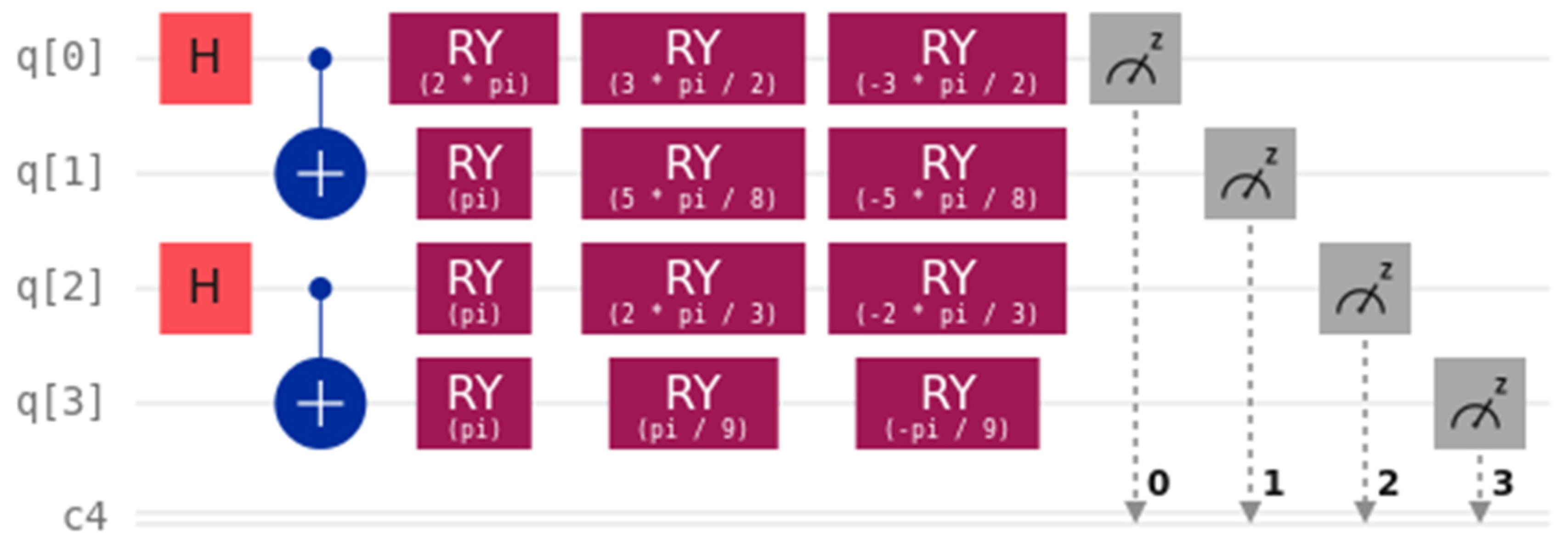
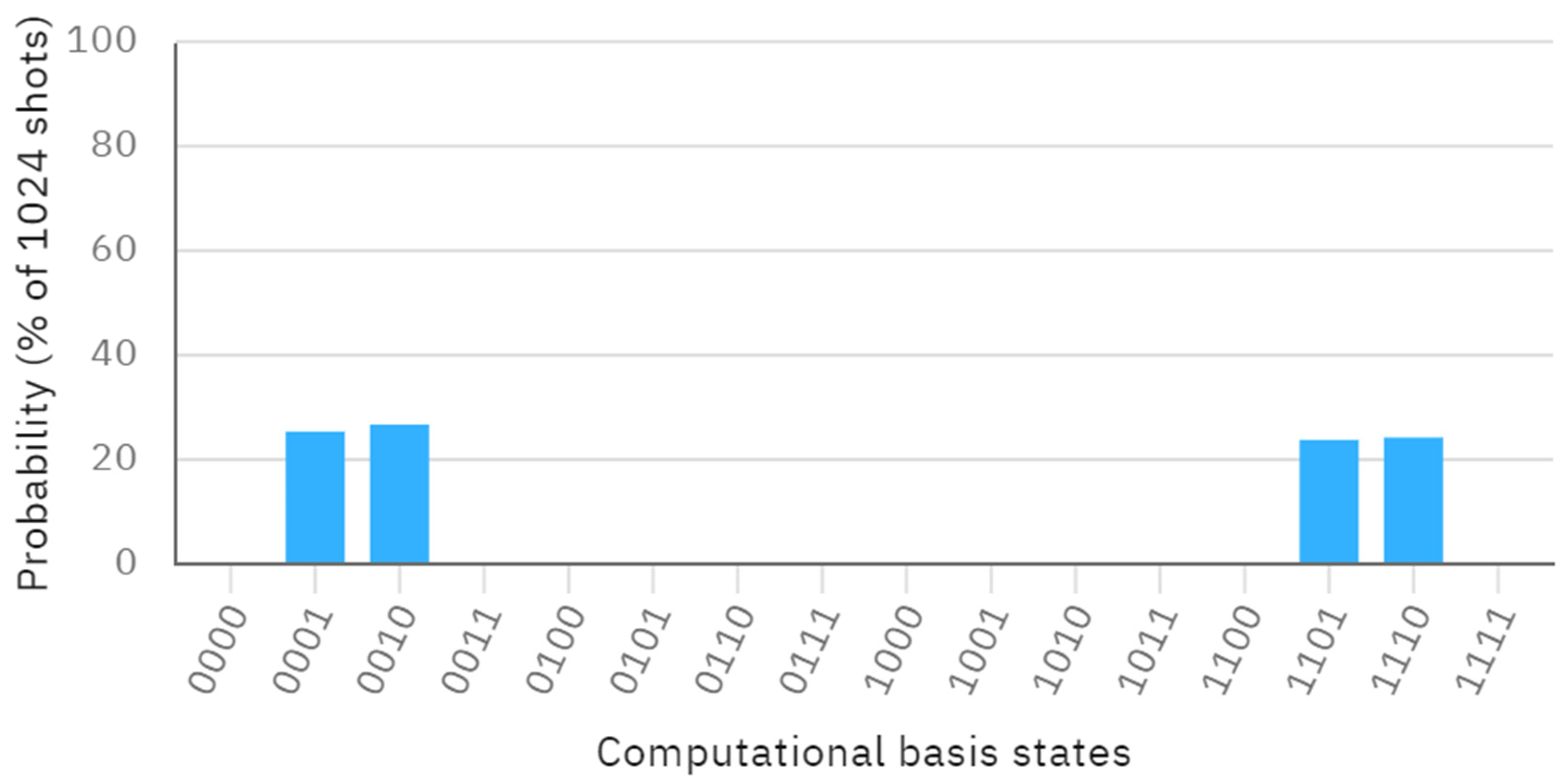
3.2. Quantum Circuit Simulation
4. Security Analysis
4.1. External Attacks
4.1.1. Intercept-Measure-Resend Attack
4.1.2. Entangle-Measure Attack
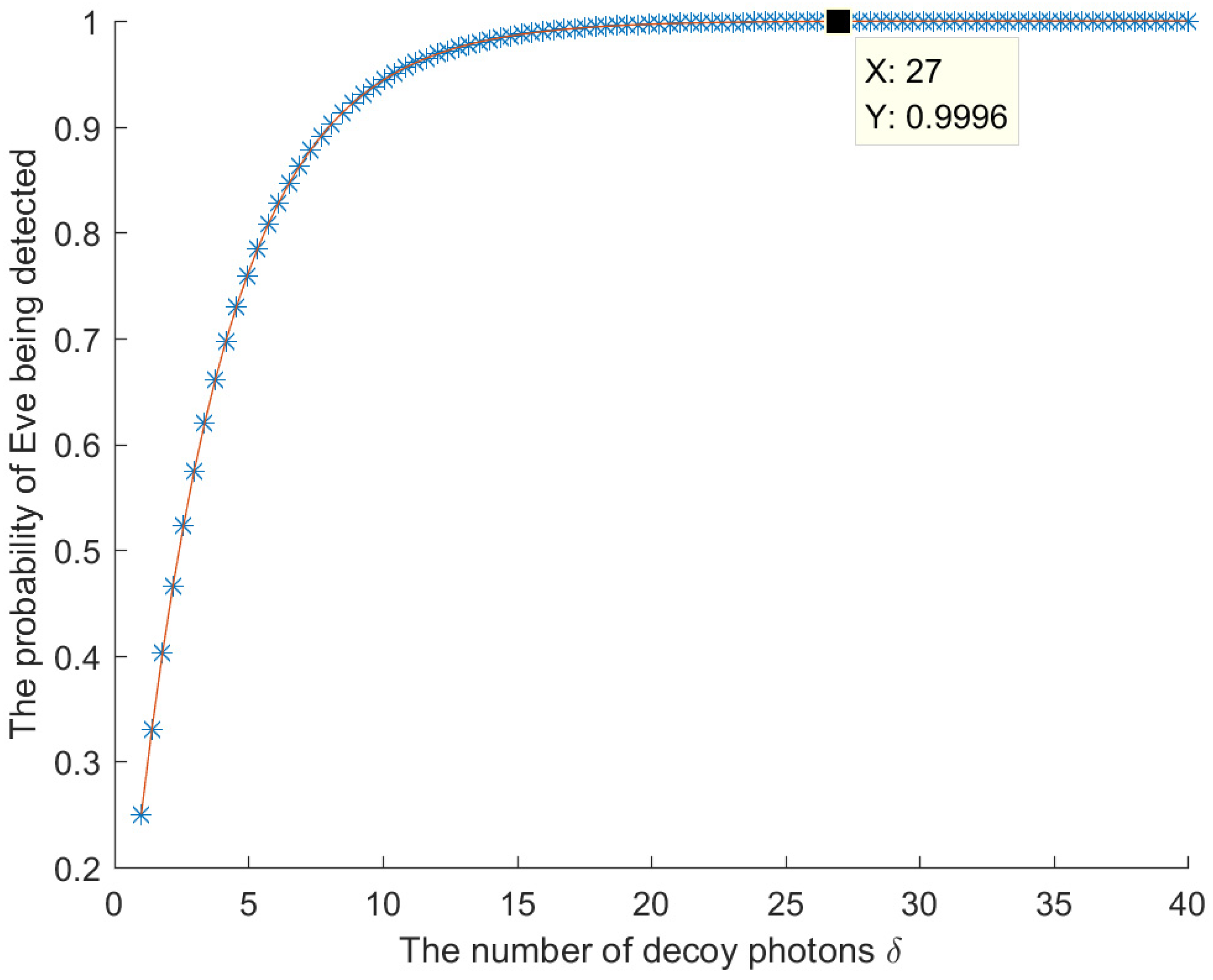
4.1.3. Trojan Horse Attack
4.2. Participant Attacks
4.2.1. Attack from TP
4.2.2. Attack from Alice or Bob (Charlie or Dove)
4.2.3. Attack from Conspiring Participants
5. Efficiency Analysis and Comparison
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM Rev. 1999, 41, 303–332. [Google Scholar] [CrossRef]
- Grover, L.K. Quantum mechanics helps in searching for a needle in a haystack. Phys. Rev. Lett. 1997, 79, 325. [Google Scholar] [CrossRef]
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers Systems and Signal Processing, Bangalore, India, 10–12 December 1984; pp. 175–179. [Google Scholar]
- Zhang, W.; van Leent, T.; Redeker, K.; Garthoff, R.; Schwonnek, R.; Fertig, F.; Eppelt, S.; Rosenfeld, W.; Scarani, V.; Lim, C.C.-W.; et al. A device-independent quantum key distribution system for distant users. Nature 2022, 607, 687–691. [Google Scholar] [CrossRef] [PubMed]
- Fang, X.T.; Zeng, P.; Liu, H.; Zou, M.; Wu, W.; Tang, Y.L.; Sheng, Y.J.; Xiang, Y.; Zhang, W.; Li, H.; et al. Implementation of quantum key distribution surpassing the linear rate-transmittance bound. Nat. Photonics 2020, 14, 422–425. [Google Scholar] [CrossRef]
- Sun, S.; Huang, A. A review of security evaluation of practical quantum key distribution system. Entropy 2022, 24, 260. [Google Scholar] [CrossRef] [PubMed]
- Huang, X.; Zhang, S.B.; Chang, Y.; Qiu, C.; Liu, D.-M.; Hou, M. Quantum key agreement protocol based on quantum search algorithm. Int. J. Theor. Phys. 2021, 60, 838–847. [Google Scholar] [CrossRef]
- Zhou, N.R.; Zhu, K.N.; Wang, Y.Q. Three-party semi-quantum key agreement protocol. Int. J. Theor. Phys. 2020, 59, 663–676. [Google Scholar] [CrossRef]
- Sheng, Y.B.; Zhou, L.; Long, G.L. One-step quantum secure direct communication. Sci. Bull. 2022, 67, 367–374. [Google Scholar] [CrossRef] [PubMed]
- Huang, X.; Zhang, S.; Chang, Y.; Yang, F.; Hou, M.; Cheng, W. Quantum secure direct communication based on quantum homomorphic encryption. Mod. Phys. Lett. A 2021, 36, 2150263. [Google Scholar] [CrossRef]
- Yang, C.W.; Lin, J.; Wang, K.L.; Tsai, C.W. Cryptanalysis and improvement of a controlled quantum secure direct communication with authentication protocol based on five-particle cluster state. Quantum Inf. Process. 2023, 22, 196. [Google Scholar] [CrossRef]
- Yao, A.C. Protocols for secure computations. In Proceedings of the 23rd IEEE Symposium on Foundations of Computer Science (FOCS’ 82), Washington, DC, USA, 3–5 November 1982; p. 160. [Google Scholar]
- Lo, H.K. Insecurity of quantum secure computations. Phys. Rev. A 1997, 56, 1154–1162. [Google Scholar] [CrossRef]
- Yang, Y.G.; Wen, Q.Y. An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A Math. Theor. 2009, 42, 055305. [Google Scholar] [CrossRef]
- Chen, X.B.; Xu, G.; Niu, X.X.; Wen, Q.Y.; Yang, Y.X. An efficient protocol for the private comparison of equal information based on the triplet entangled state and single-particle measurement. Opt. Commun. 2010, 283, 1561–1565. [Google Scholar] [CrossRef]
- Lin, P.H.; Hwang, T.; Tsai, C.W. Efficient semi-quantum private comparison using single photons. Quantum Inf. Process. 2019, 18, 207. [Google Scholar] [CrossRef]
- Yan-Feng, L. Semi-quantum private comparison using single photons. Int. J. Theor. Phys. 2018, 57, 3048–3055. [Google Scholar] [CrossRef]
- Pan, H.M. Two-party quantum private comparison using single photons. Int. J. Theor. Phys. 2018, 57, 3389–3395. [Google Scholar] [CrossRef]
- Huang, X.; Chang, Y.; Cheng, W.; Hou, M.; Zhang, S.B. Quantum private comparison of arbitrary single qubit states based on swap test. Chin. Phys. B 2022, 31, 040303. [Google Scholar] [CrossRef]
- Sun, Z.; Yu, J.; Wang, P.; Xu, L.; Wu, C. Quantum private comparison with a malicious third party. Quantum Inf. Process. 2015, 14, 2125–2133. [Google Scholar] [CrossRef]
- Kou, T.Y.; Che, B.C.; Dou, Z.; Chen, X.B.; Lai, Y.P.; Li, J. Efficient quantum private comparison protocol utilizing single photons and rotational encryption. Chin. Phys. B 2022, 31, 060307. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, W.F.; Zhang, S.B. Efficient multiparty quantum private comparison protocol based on single photons and rotation encryption. Quantum Inf. Process. 2023, 22, 272. [Google Scholar] [CrossRef]
- Liu, B.; Xiao, D.; Huang, W.; Jia, H.-Y.; Song, T.-T. Quantum private comparison employing single-photon interference. Quantum Inf. Process. 2017, 16, 180. [Google Scholar] [CrossRef]
- Tseng, H.Y.; Lin, J.; Hwang, T. New quantum private comparison protocol using EPR pairs. Quantum Inf. Process. 2012, 11, 373–384. [Google Scholar] [CrossRef]
- Lang, Y.F. Quantum private comparison using single bell state. Int. J. Theor. Phys. 2021, 60, 4030–4036. [Google Scholar] [CrossRef]
- Jiang, L.Z. Semi-quantum private comparison based on Bell states. Quantum Inf. Process. 2020, 19, 180. [Google Scholar] [CrossRef]
- Geng, M.J.; Chen, Y.; Xu, T.J.; Ye, T.Y. Single-state semiquantum private comparison based on Bell states. EPJ Quantum Technol. 2022, 9, 36. [Google Scholar] [CrossRef]
- Gong, L.H.; Li, M.L.; Cao, H.; Wang, B. Novel semi-quantum private comparison protocol with Bell states. Laser Phys. Lett. 2024, 21, 055209. [Google Scholar] [CrossRef]
- Wu, W.; Wu, J.; Guo, L. Multi-Party Quantum Private Comparison Based on Bell States. Entropy 2023, 25, 1156. [Google Scholar] [CrossRef] [PubMed]
- Xie, L.; Li, Q.; Yu, F.; Lou, X.; Zhang, C. Cryptanalysis and improvement of a semi-quantum private comparison protocol based on Bell states. Quantum Inf. Process. 2021, 20, 244. [Google Scholar] [CrossRef]
- Ye, C.Q.; Li, J.; Chen, X.B.; Hou, Y. A feasible semi-quantum private comparison based on entanglement swapping of Bell states. Phys. A Stat. Mech. Its Appl. 2023, 625, 129023. [Google Scholar] [CrossRef]
- Tsai, C.W.; Lin, J.; Yang, C.W. Cryptanalysis and improvement in semi-quantum private comparison based on Bell states. Quantum Inf. Process. 2021, 20, 1–14. [Google Scholar] [CrossRef]
- Sun, Y.; Yan, L.; Sun, Z.; Zhang, S. A novel semi-quantum private comparison scheme using bell entangle states. Comput. Mater. Contin. 2021, 66, 2385–2395. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y.; Zhang, S. Efficient Quantum Private Comparison Based on GHZ States. Entropy 2024, 26, 413. [Google Scholar] [CrossRef]
- Ji, Z.X.; Zhang, H.G.; Fan, P.R. Two-party quantum private comparison protocol with maximally entangled seven-qubit state. Mod. Phys. Lett. A 2019, 34, 1950229. [Google Scholar] [CrossRef]
- Ji, Z.; Zhang, H.; Wang, H. Quantum private comparison protocols with a number of multi-particle entangled states. IEEE Access 2019, 7, 44613–44621. [Google Scholar] [CrossRef]
- Ji, Z.X.; Ye, T.Y. Quantum private comparison of equal information based on highly entangled six-qubit genuine state. Commun. Theor. Phys. 2016, 65, 711. [Google Scholar] [CrossRef]
- Hong-Ming, P. Quantum private comparison based on χ-type entangled states. Int. J. Theor. Phys. 2017, 56, 3340–3347. [Google Scholar] [CrossRef]
- Li, J.; Che, F.; Wang, Z.; Fu, A. Efficient Quantum Private Comparison without Sharing a Key. Entropy 2023, 25, 1552. [Google Scholar] [CrossRef] [PubMed]
- Li, C.; Chen, X.; Li, H.; Yang, Y.; Li, J. Efficient quantum private comparison protocol based on the entanglement swapping between four-qubit cluster state and extended Bell state. Quantum Inf. Process. 2019, 18, 158. [Google Scholar] [CrossRef]
- Xu, G.A.; Chen, X.B.; Wei, Z.H.; Li, M.J.; Yang, Y.X. An efficient protocol for the quantum private comparison of equality with a four-qubit cluster state. Int. J. Quantum Inf. 2012, 10, 1250045. [Google Scholar] [CrossRef]
- Sun, Z.; Long, D. Quantum private comparison protocol based on cluster states. Int. J. Theor. Phys. 2013, 52, 212–218. [Google Scholar] [CrossRef]
- Chang, Y.; Zhang, W.B.; Zhang, S.B.; Wang, H.C.; Yan, L.L.; Han, G.H.; Sheng, Z.W.; Huang, Y.Y.; Suo, W.; Xiong, J.X. Quantum private comparison of equality based on five-particle cluster state. Commun. Theor. Phys. 2016, 66, 621. [Google Scholar] [CrossRef]
- Zhou, M.K. Improvements of quantum private comparison protocol based on cluster states. Int. J. Theor. Phys. 2018, 57, 42–47. [Google Scholar] [CrossRef]
- Zha, X.W.; Yu, X.Y.; Cao, Y.; Wang, S.K. Quantum private comparison protocol with five-particle cluster states. Int. J. Theor. Phys. 2018, 57, 3874–3881. [Google Scholar] [CrossRef]
- Ye, T.Y.; Hu, J.L. Multi-party quantum private comparison based on entanglement swapping of Bell entangled states within d-level quantum system. Int. J. Theor. Phys. 2021, 60, 1471–1480. [Google Scholar] [CrossRef]
- Cao, H.; Ma, W.; Lü, L.; He, Y.; Liu, G. Multi-party quantum privacy comparison of size based on d-level GHZ states. Quantum Inf. Process. 2019, 18, 287. [Google Scholar] [CrossRef]
- Wu, W.Q.; Zhao, Y.X. Quantum private comparison of size using d-level Bell states with a semi-honest third party. Quantum Inf. Process. 2021, 20, 155. [Google Scholar] [CrossRef]
- Zhao-Xu, J.; Tian-Yu, Y. Multi-party quantum private comparison based on the entanglement swapping of d-level cat states and d-level Bell states. Quantum Inf. Process. 2017, 16, 177. [Google Scholar] [CrossRef]
- Lang, Y.F. Quantum gate-based quantum private comparison. Int. J. Theor. Phys. 2020, 59, 833–840. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, S.B.; Chang, Y.; Hou, M.; Cheng, W. Efficient quantum private comparison based on entanglement swapping of bell states. Int. J. Theor. Phys. 2021, 60, 3783–3796. [Google Scholar] [CrossRef]
- Fan, P.; Rahman, A.U.; Ji, Z.; Ji, X.; Hao, Z.; Zhang, H. Two-party quantum private comparison based on eight-qubit entangled state. Mod. Phys. Lett. A 2022, 37, 2250026. [Google Scholar] [CrossRef]
- Liu, C.; Zhou, S.; Gong, L.H.; Chen, H.Y. Quantum private comparison protocol based on 4D GHZ-like states. Quantum Inf. Process. 2023, 22, 255. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y. Single-photon-based quantum secure protocol for the socialist millionaires’ problem. Front. Phys. 2024, 12, 1364140. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, W.; Zhang, S. Practical quantum protocols for blind millionaires’ problem based on rotation encryption and swap test. Phys. A Stat. Mech. Its Appl. 2024, 637, 129614. [Google Scholar] [CrossRef]
- Lucamarini, M.; Choi, I.; Ward, M.B.; Dynes, J.F.; Yuan, Z.L.; Shields, A.J. Practical security bounds against the trojan-horse attack in quantum key distribution. Phys. Rev. X 2015, 5, 031030. [Google Scholar] [CrossRef]
| State of a Decoy Photon | |||||
| Guesses measurement basis from Eve | Z-basis | X-basis | |||
| Measurement result for Eve | |||||
| The fake state that Eve prepares | |||||
| Measurement basis from the receiver | Z-basis | Z-basis | |||
| Measurement result of the receiver | |||||
| Does it introduce an error? | No | Yes | No | Yes | No |
| Ref. [40] | Ref. [41] | Ref. [42] | Ref. [43] | Ref. [51] | Ours | |
|---|---|---|---|---|---|---|
| Quantum resource | Four-qubit cluster state and extended Bell state | Four-qubit cluster state | Four-particle cluster state | Five-particle cluster state | Bell states | Four-particle cluster state |
| Unitary operation | No | Yes | Yes | Yes | No | Yes |
| Entanglement swapping | Yes | No | No | No | Yes | No |
| the pairs of private information compared | 1 | 1 | 1 | 2 | 1 | 2 |
| Quantum measurement | Bell-basis and extend Bell basis | single-particle | Single-particle | single-particle | GHZ-basis | Single-particle |
| Qubit efficiency | 50% | 50% | 25% | 40% | 50% | 50% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hou, M.; Wu, Y.; Zhang, S. New Quantum Private Comparison Using Four-Particle Cluster State. Entropy 2024, 26, 512. https://doi.org/10.3390/e26060512
Hou M, Wu Y, Zhang S. New Quantum Private Comparison Using Four-Particle Cluster State. Entropy. 2024; 26(6):512. https://doi.org/10.3390/e26060512
Chicago/Turabian StyleHou, Min, Yue Wu, and Shibin Zhang. 2024. "New Quantum Private Comparison Using Four-Particle Cluster State" Entropy 26, no. 6: 512. https://doi.org/10.3390/e26060512
APA StyleHou, M., Wu, Y., & Zhang, S. (2024). New Quantum Private Comparison Using Four-Particle Cluster State. Entropy, 26(6), 512. https://doi.org/10.3390/e26060512






