Abstract
To construct a chaotic system with complex characteristics and to improve the security of image data, a five-dimensional tri-valued memristor chaotic system with high complexity is innovatively constructed. Firstly, a pressure-controlled tri-valued memristor on Liu’s pseudo-four-wing chaotic system is introduced. Through analytical methods, such as Lyapunov exponential map, bifurcation map and attractor phase diagram, it is demonstrated that the new system has rich dynamical behaviors with periodic limit rings varying with the coupling parameter of the system, variable airfoil phenomenon as well as transient chaotic phenomenon of chaos-periodic depending on the system parameter and chaos-quasi-periodic depending on the memristor parameter. The system is simulated with dynamic circuits based on Simulink. Secondly, the differently structured synchronous controls of chaotic systems are realized using a nonlinear feedback control method. Finally, based on the newly constructed five-dimensional chaotic system, a variable parameter color image encryption scheme is proposed to iteratively generate varying chaotic pseudo-random sequences by varying the system parameters, which will be used for repetition-free disambiguation, additive modulo left-shift diffusion and DNA encryption for the three components of RGB of the color image after chunking. The simulation results are analyzed by histogram, information entropy, adjacent pixel correlation, etc., and the images are tested using differential attack, noise attack and geometric attack, as well as analyzing the PSNR and SSIM of the decrypted image quality. The results show that the encryption method has a certain degree of security and can be applied to medical, military and financial fields with more complex environmental requirements.
1. Introduction
With the continuous development of information technology, ensuring information security has become an important issue, and images, as the most frequently used multimedia tools, are widely used in medical, military, education, finance and other fields, often facing the risk of leakage, resulting in incalculable losses. Images are characterized by large amounts of data, redundancy and high correlation, so traditional encryption algorithms are not suitable for image encryption [1], and it is crucial to design an effective encryption algorithm to protect the relevant information of images. Chaotic systems are suitable for image encryption due to their properties such as ergodicity, initial value sensitivity and non-periodicity, which are similar to cryptography. The common chaotic systems are logistic mapping, Henon mapping, Lorenz chaotic system, etc. The research history of chaos theory can be traced back to the late 19th century at the earliest, but it is only in recent decades that it has begun to be applied to image encryption. Previous studies have shown that applying chaos to encryption algorithms can effectively improve the security of encryption algorithms.
In recent years, an in-depth study of the electrical characteristics of memristors and their application to chaotic systems has become one of the important research directions, and most of the studies on memristor chaotic systems are centered around magnetically controlled memristors and charge-controlled memristors. In 2024, Li Ping et al. proposed an image encryption algorithm combining the disruption–diffusion algorithm by constructing a five-dimensional memristor chaotic system using a magnetically controlled memristor [2]. In 2023, Liu Ni constructed a four-dimensional fractional-order chaotic system using magnetically controlled memristors, designed a diffusion algorithm encryption scheme based on heteroscedasticity and applied it to a power system, and the experiment proved that the encryption scheme has good security performance [3]. In 2023, Du Chuanhong designed a conservative system using a charge-controlled memristor to make a pseudo-random signal generator and used it for image encryption work [4]. In summary, the sequences generated by the chaotic system based on magnetically controlled memristors and charge-controlled memristors have strong pseudo-randomness and can be well applied in image encryption.
A number of scholars have begun to study other types of memristors. In 2020, Wang Xiaoyuan et al. first proposed the concept and mathematical model of a multi-valued memristor, deeply analyzed the mathematical model of a tri-valued memristor [5] and constructed a new four-dimensional tri-valued memristor chaotic system in the same year, which was proved experimentally to have a complex dynamical behavior [6]. With the continuous efforts of the team, in 2023, two four-dimensional memristor chaotic systems were constructed by introducing two-valued and tri-valued memristors into Chen’s system, respectively, and the differences between the two chaotic systems were compared from several angles, proving that the chaotic system constructed by tri-valued memristors could produce more complex dynamics [7]. In summary, a tri-valued memristor not only enriches the types of nonlinear systems compared to a two-valued and continuous memristor, but also broadens the design of chaotic systems, increases the stability and robustness of the system and produces rich and diverse dynamic behaviors. At this stage, the research on tri-valued memristor chaos is relatively small and limited to the basis of four-dimensional chaotic systems, and the constructed four-dimensional chaotic systems have the problems of simple structure and low sequence randomness, whereas the high-dimensional chaotic systems have more complex dynamical behaviors and a richer class of stochastic phenomena in comparison with the four-dimensional chaotic systems [8,9,10,11]. Therefore, it is challenging research to introduce tri-valued memristors into high-dimensional chaotic systems, and in this paper, we address the above problems by constructing high-dimensional chaotic systems using tri-valued memristors to produce richer dynamical behaviors and more stochastic sequences.
Synchronous control is the key to achieving confidential communication and has important applications in the fields of communication, secure transmission and information processing [12,13,14]. In 2019, Yu Fei et al. achieved synchronization between five-dimensional memristor hyperchaotic systems with different structures by actively controlling the synchronization and successfully applied it in the field of confidential communication [15]. In 2021, Liu Li combined a newly constructed five-dimensional memristor hyperchaotic system with a chaotic system of the same number of dimensions to achieve different structures’ synchronous control of the two systems [16]. In 2023, Dong Wu et al. designed a combinatorial synchronization scheme for differently structured hyperchaotic systems based on finite time theory using the backstepping method to improve the security of the secure communication system and verified the effectiveness of the scheme through experimental simulation [17]. In summary, the synchronous control of chaotic systems lays the foundation for the development of the communication field. Although some progress has been made in the research on the synchronous control of differently structured chaotic systems, the theoretical research on the synchronization of the high-dimensional differently structured chaotic systems containing different memristors is still insufficient. In this paper, we design a new synchronous controller to achieve the synchronous control of the newly constructed tri-valued memristor chaotic system and the magnetically controlled memristor chaotic system of the five-dimensional differently structured chaotic system synchronization control.
Chaotic systems have the properties of initial value sensitivity, boundedness, ergodicity and randomness [18], which can produce rich dynamical behaviors and have important applications in the fields of image encryption, neural networks and confidential communications. Chaotic encryption has the advantages of larger key space and faster encryption speed compared to traditional image encryption methods, which has become one of the important topics in the field of nonlinear research [19,20,21]. In 2022, Wang Simiao et al. proposed a chaotic encryption scheme combining three-dimensional logical mapping and Secure Hash Algorithm-3 to improve encryption effectiveness [22]. In 2023, Li Jian et al. proposed a semiconductor 32 image encryption method based on a smooth memristor with a conservative memristor chaotic system, which provided a reference for further research on the application of conservative memristor chaotic systems in the field of image encryption [23]. In 2023, Wang Yiming et al. designed a fast image encryption algorithm with an adaptive mechanism based on a 3D chaotic system [24]. The above research is limited to the encryption of a chaotic system with fixed parameters, the key space is insufficient, the complexity is low, it is easy to be affected by the short period and chaotic degradation and the security is poor as the same key flow is used for each image. Therefore, it is necessary to improve the current encryption method of the chaotic image to enhance its security and reliability. In this paper, we will focus on the above problems, and based on the principle of one-key-at-a-time, we will design a variable parameter encryption scheme, which can solve the above problems well.
Based on the above research, this paper further enriches the type of chaotic system based on a tri-valued memristor and proposes a more effective secrecy scheme based on this system. The remainder of this study is structured as follows. Section 2 constructs a five-dimensional tri-valued memristor system, which is verified as a chaotic system without equilibrium using a combination of theory and experiments. Section 3 explores the effects of the system parameters and the memristor parameters on the dynamical properties of the system and demonstrates that the system parameters are highly sensitive and can be better applied in image encryption. Section 4 uses the Simulink circuit implementation to simulate the chaotic system and verifies the correctness of the chaotic system. Section 5 uses a nonlinear feedback synchronization method to design a nonlinear feedback controller to synchronize a chaotic system containing two different memristors, which lays the foundation for the field of confidential communication applications. Section 6 summarizes the work of this paper and provides a future outlook.
2. Construction of a Five-Dimensional Tri-Valued Memristor Chaotic System
2.1. Voltage-Controlled Tri-Valued Memristor Model
In 2020, Wang Xiaoyuan et al. [5] proposed a voltage-controlled tri-valued memristor, which describes the adopted tri-valued memristor model relation in terms of an asymmetric segmented linear function, as shown in Equation (1):
where the parameters , , , and are non-zero constants and is positive (Equation (1)). Both sides of the equation are simultaneously derived for the flux to obtain the relation for this tri-valued memristor model as a segmented functional relation, as shown in Equation (2):
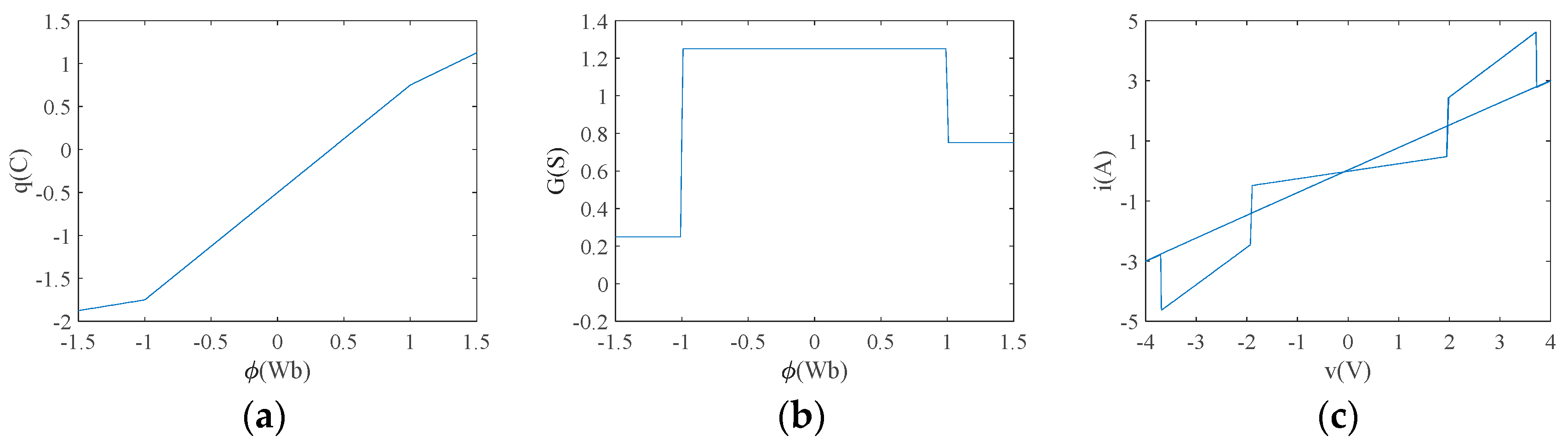
where is the memristor conductance of the memristor in Siemens (S), and denotes the sign function. Let , , , and , and the corresponding curves and are shown in Figure 1a,b. From Figure 1, the memristor is modeled as a three-part line segment passing through the origin, exhibiting three stable memristor values of S, S and S. Figure 1b shows more intuitively the effect of the change in magnetic flux on the tri-valued memristor value of the voltage-controlled tri-valued memristor. When , S; when , S; and when , S. Applying an excitation voltage with a sinusoidal signal of to this tri-valued memristor model, taking V, Hz and an initial value of , the characteristic curve can be obtained, as shown in Figure 1c. The plane shows a tight “8” contraction hysteresis curve over the origin, which satisfies the non-volatile nature of the memristor and proves that the voltage-controlled tri-valued memristor is effective.

Figure 1.
Characteristic curves of tri-valued memristor: (a) curve; (b) curve; (c) characteristic curve.
2.2. Construction of the System
Liu’s pseudo-quadruple chaotic system [25] to be improved is shown in Equation (3).
In Equation (3), , and are the state variables of the system; , , and are the system parameters. On this basis, a tri-valued memristor is added to the second equation to form a state feedback, a state variable is added to the third equation, the sum of state variables and are used as the fourth equation and the sum of state variables and are used as the fifth equation, thus obtaining a new five-dimensional tri-valued memristor chaotic system with the following mathematical model:
In Equation (4), , , , and are the state variables of the system; , , and are the system parameters.
2.3. Validation of the System
Simulation software MATLAB 2018a is used to verify whether the newly constructed five-dimensional memristor system is chaotic, and the system is analyzed by the 0–1 test, time-domain waveform map and attractor phase diagram, as follows:
The 0–1 test [8], which determines whether the sequences generated by the system exhibit chaotic behavior, shows an interesting feature: it provides a simple and intuitive test for the trajectory of the system in the plane, regardless of whether the dynamical system is chaotic. Let the discrete time series at sampling time , with chosen as a random constant in the interval , define the functions and as follows:
where is the observable data set and parameter , .
Based on the functions and , the mean square displacement is as follows:
Included among these,
If the trajectories of the functions and appear to be in irregular Brownian motion, the system is in a chaotic state; if the trajectories of and are bounded, the system is in a periodic state.
The asymptotic growth rate of the mean square displacement is defined to be
The test method can determine the chaotic properties of a time series of finite length simply based on whether the asymptotic growth rate is closer to 0 or 1, as shown in Table 1.

Table 1.
State of the system corresponding to the 0–1 test value .
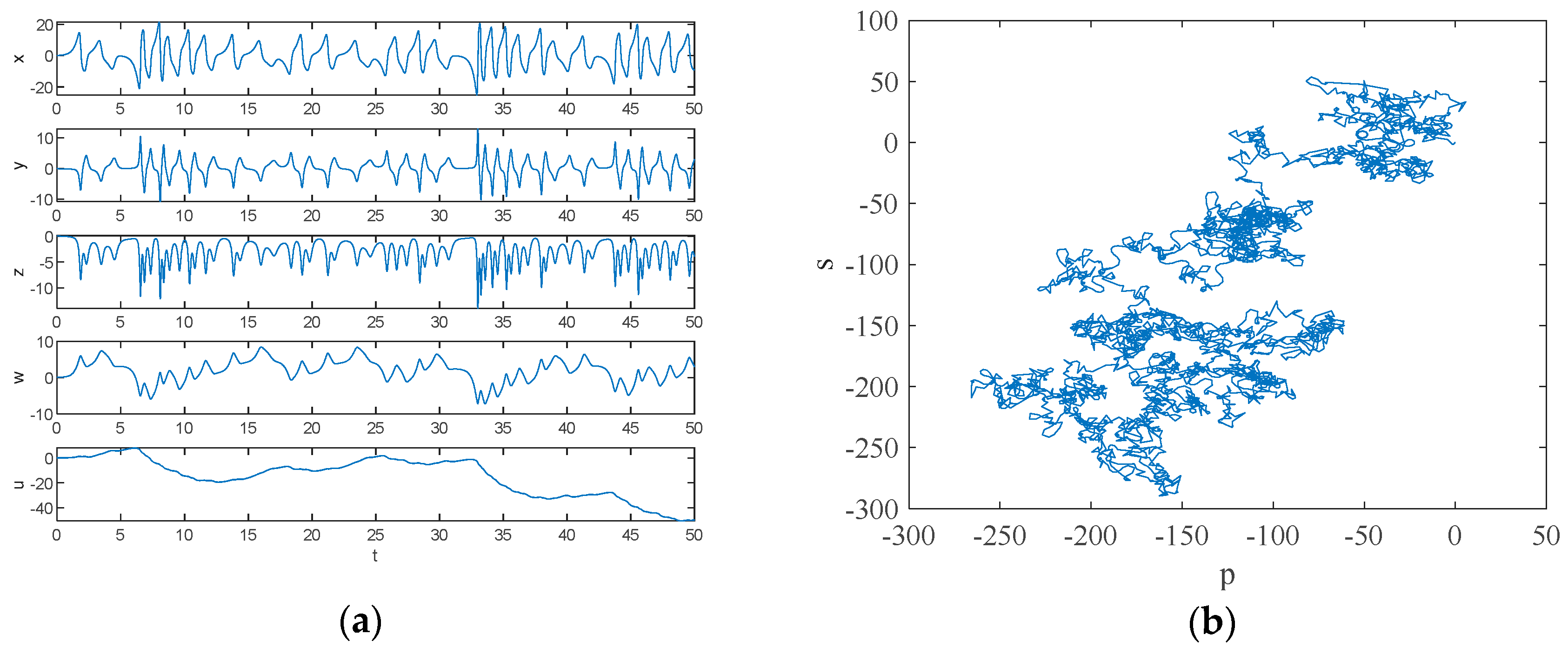
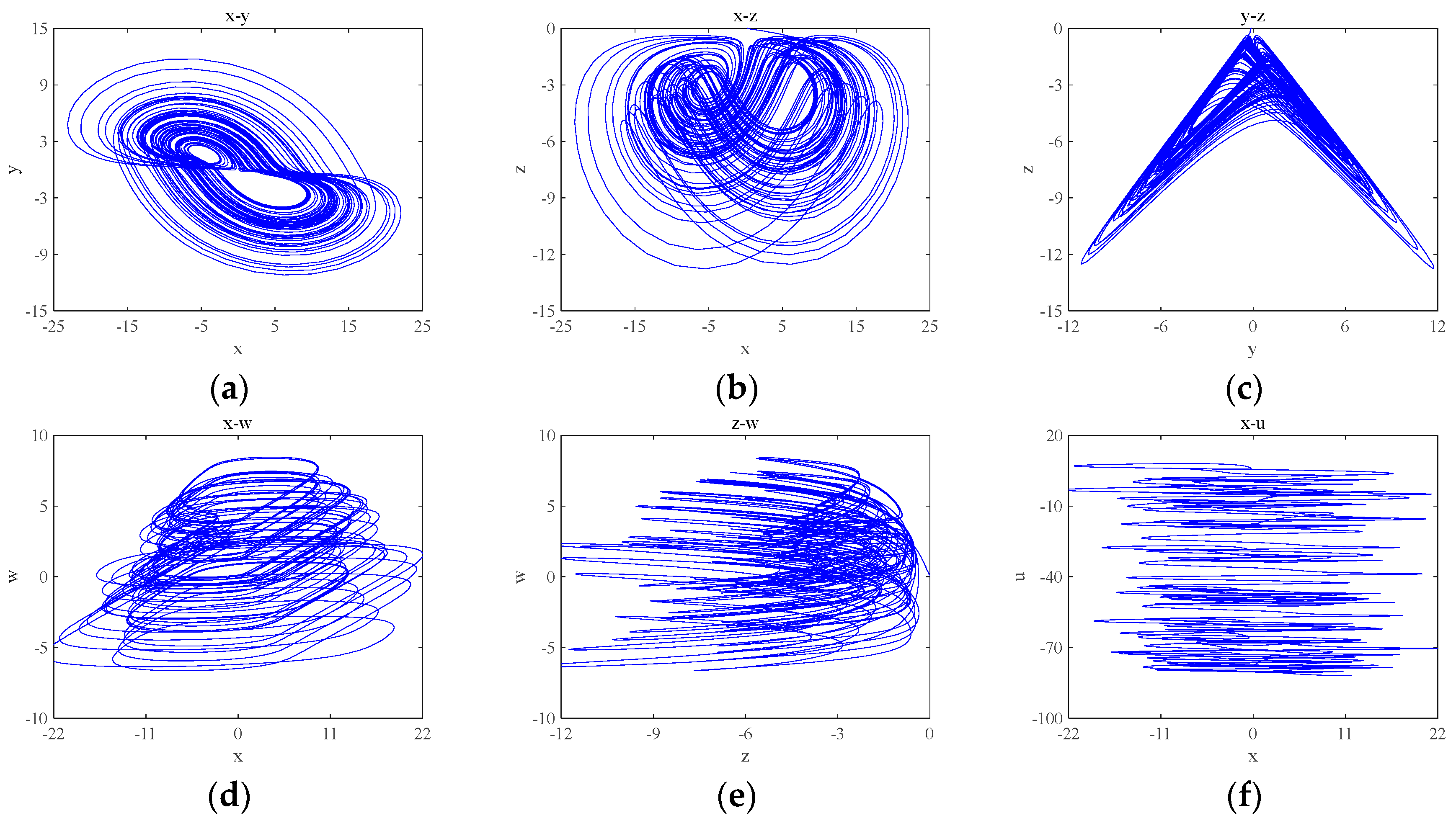
According to the 0–1 test method, the dynamic system will provide a simple visual test in the plane of . The trajectory within provides a judgement on the state that the dynamic system is in. Let , , and , and the initial condition is . Numerical simulation using MATLAB 2018a yields the time-domain waveform and 0–1 test plot of the system, which are shown in Figure 2, and the attractor phase diagrams of the , , , , and planes obtained by numerical simulation using MATLAB 2018a are shown in Figure 3. As can be seen from Figure 2, the 0–1 test plot is an irregular Brownian motion, and the value of is 1. The time-domain waveform trajectory of the system is always an irregular clutter wave.

Figure 2.
Time-domain waveform and 0–1 test plot with parameters , , and : (a) time-domain waveform; (b) 0–1 test plot.

Figure 3.
Basic phase diagrams of the system: (a) the plane; (b) the plane; (c) the plane; (d) the plane; (e) the plane; and (f) the plane.
In summary, the time-domain waveform map of the system is non-periodic and the 0–1 test map shows Brownian motion, so the newly constructed system is chaotic.
2.4. Equilibrium Stability and Dissipative Analysis
Let the right-hand side of the system (4) be zero, and the condition that the system has an equilibrium point can be obtained as and . From the defined tri-valued memristor model, it can be seen that the tri-valued memristor exhibits only three stable memristor conductance values of 0.25 S, 1.25 S and 0.75 S. The absence of indicates that the above condition for the existence of equilibrium points does not hold and, therefore, the chaotic system has no equilibrium points and the attractors produced are all hidden attractors.
In order to obtain the dissipation of the system, Equation (11) is used for calculation:
When , , and , the initial condition is , respectively, is calculated, which indicates that the system is dissipative, the volume of the phase space will be contracted exponentially to and all the trajectories of the system are compressed to 0, which is one of the most important bases for the existence of chaotic phenomena in the system.
3. Analysis of the Dynamical Behavior of the System
Chaotic properties are to some extent susceptible to the influence of system parameters, i.e., small perturbations in the system parameters are prone to cause changes in the dynamical behavior of the system, and this sensitivity can limit the application of chaotic systems in practice, so it is crucial to explore the influence of system parameters on the dynamics of chaotic systems [26]. The Lyapunov exponential and bifurcation diagrams are classical methods for analyzing the behavior of nonlinear dynamics.
The Lyapunov exponent is a numerical feature of the average exponential divergence rate of neighboring trajectories in phase space and is one of several numerical features used to identify chaotic motion. Whether a particular system is chaotic or not can be visualized by the image of the Lyapunov exponential spectrum, where only one positive Lyapunov exponent implies chaos, and two or more positive Lyapunov exponents imply hyperchaotic and the trajectory will exhibit greater complexity and unpredictability. The equation for the Lyapunov exponent [27] is as follows:
where is the Lyapunov index, is the state vector at time and is the initial state vector.
The bifurcation diagram of the chaotic system is a tool for visualizing stability and periodicity in the evolution of a system, usually using the system parameters as horizontal coordinates and the values of the system state, stability points or periodic orbits as vertical coordinates. In chaotic systems, small parameter changes may lead to significant changes in the behavior of the system, resulting in bifurcation. The different attractor states of the system can be observed from it, and if the bifurcation diagram appears as one or more straight lines consisting of dots, it indicates that the system is in a periodic or multiply-periodic state. If the bifurcation diagram appears with patches of dots, it indicates that the system is in a chaotic state.
Therefore, by fixing the other parameters, the data variations in Lyapunov exponent spectrum and bifurcation diagram in different ranges of the system coupling parameters , and memristor parameter , respectively, are observed to understand the complex dynamic properties of the system.
3.1. Dependent on the Dynamics of Parameter
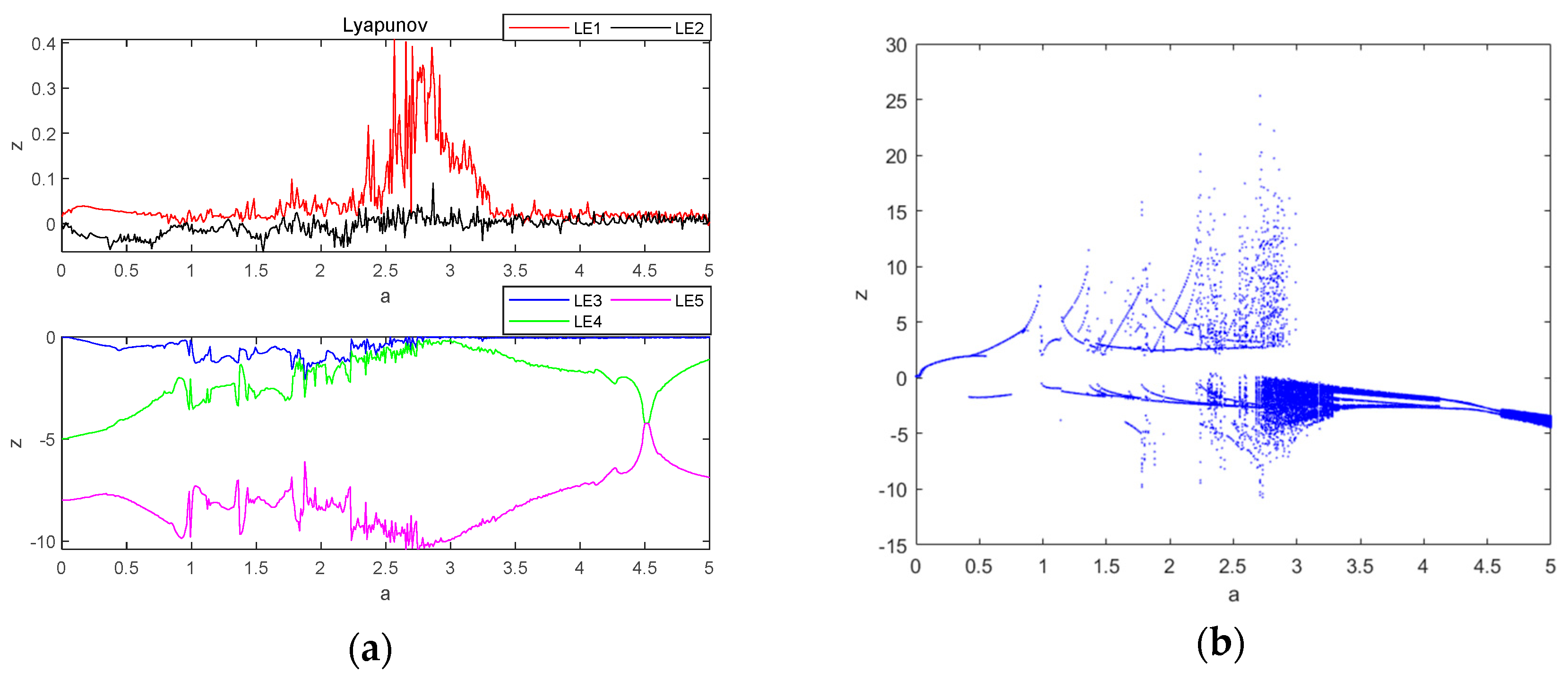
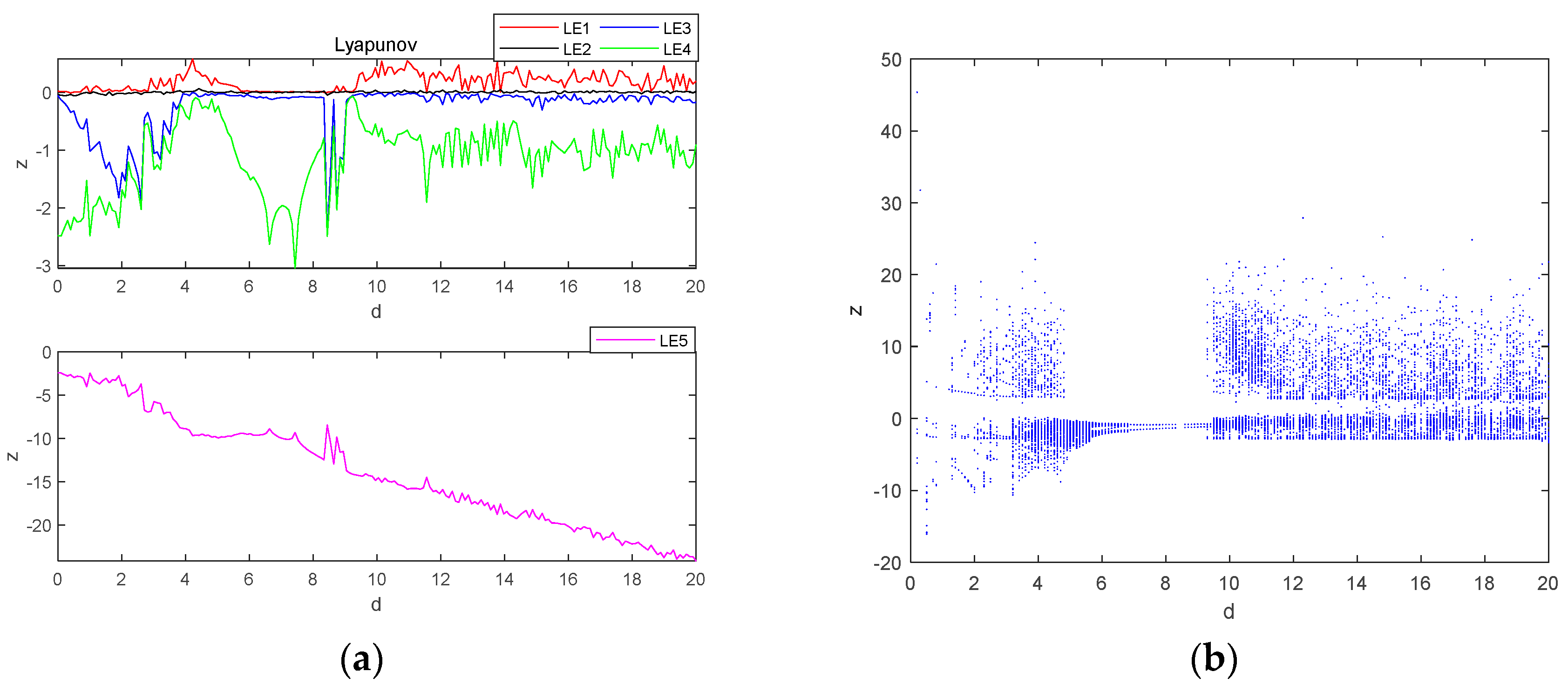
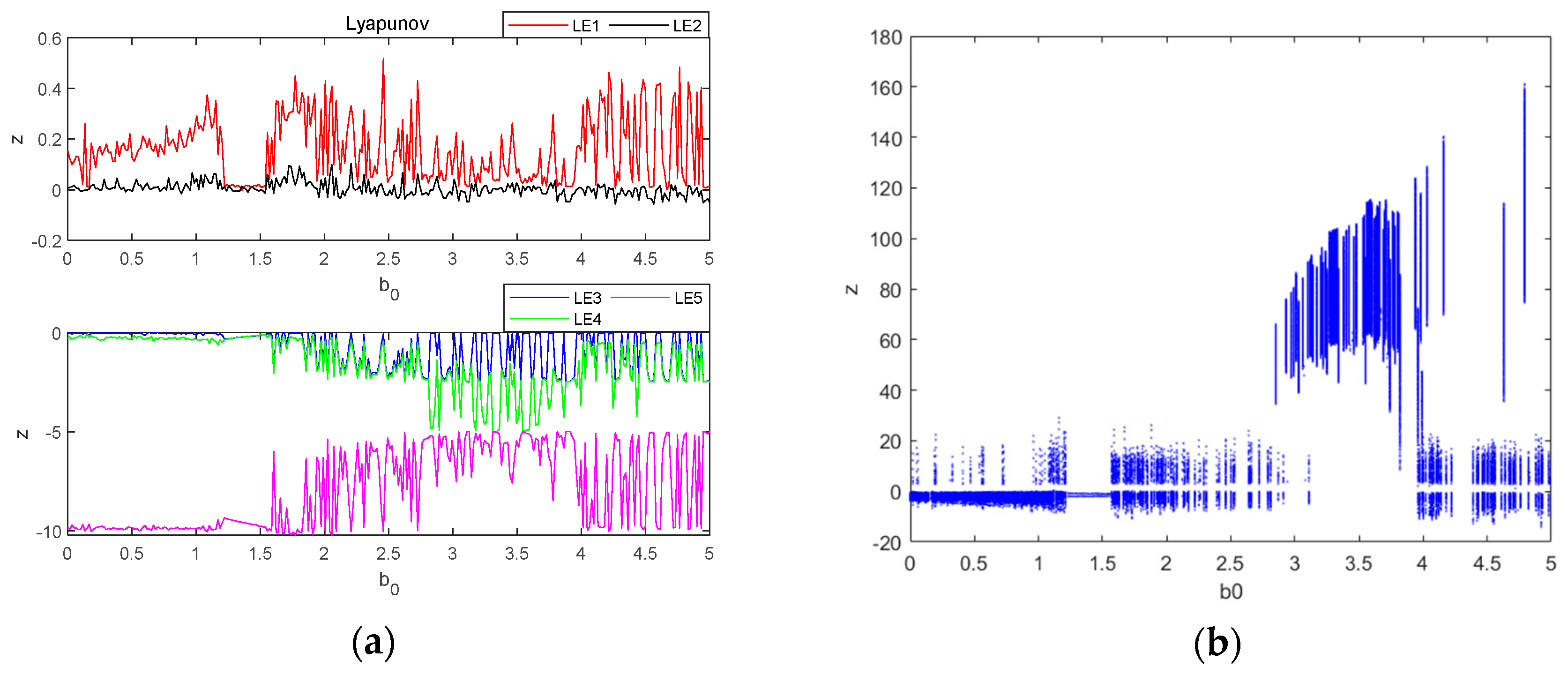
Let parameter be a variable control parameter, when , and , the initial condition is , the fixed step time is 0.01 s and the total duration is s. The fourth-order Runge–Kutta method and wolf algorithm are used to simulate the Lyapunov exponent spectrum and bifurcation diagrams for the evolution of the system variable within the parameter . The size of the value obtained from different sampling points when experimenting is not the same, which also depends on the performance of the computer, in the case of ensuring that the computer can run, as many as possible to obtain the sampling points, to improve the accuracy of the value, in which the Lyapunov exponential spectrum of 500 sampling points, bifurcation diagram sampling points of 500, the obtained image is shown in Figure 4. The principle adhered to is to take the second Lyapunov exponent value close to 0 as 0, and the value with a large difference from 0 is taken by the normal value, using this way of taking the value, which will result in a certain degree of error, so the attractor phase diagrams and the time-domain waveform diagrams are re-simulated at the special point and the critical point, to re-verify the data correctness as well as the correctness of the system state in the interval and the accuracy of the data as well as the state of the system are greatly improved correctness of the data and the system state. It can be seen that the system goes through three different states, first changing from periodic to chaotic and then to quasi-periodic: when , the system is in a periodic state; when , the system is in a chaotic state; and when , the system is in a quasi-periodic state.

Figure 4.
Lyapunov exponent spectrum and bifurcation diagram of chaotic system with : (a) Lyapunov exponent spectrum; (b) bifurcation diagram.
From Figure 4, the values of Lyapunov exponents of the system are , , , and . Based on the above values of Lyapunov exponents, the following can be obtained:
The fractional dimension of the system is calculated using the wolf algorithm [28], as shown in Equation (15):
where is to ensure that and , and thus one obtains the following:
It shows that the Lyapunov exponential dimension of the system is fractional dimensional, further verifying that the system is chaotic at this point.
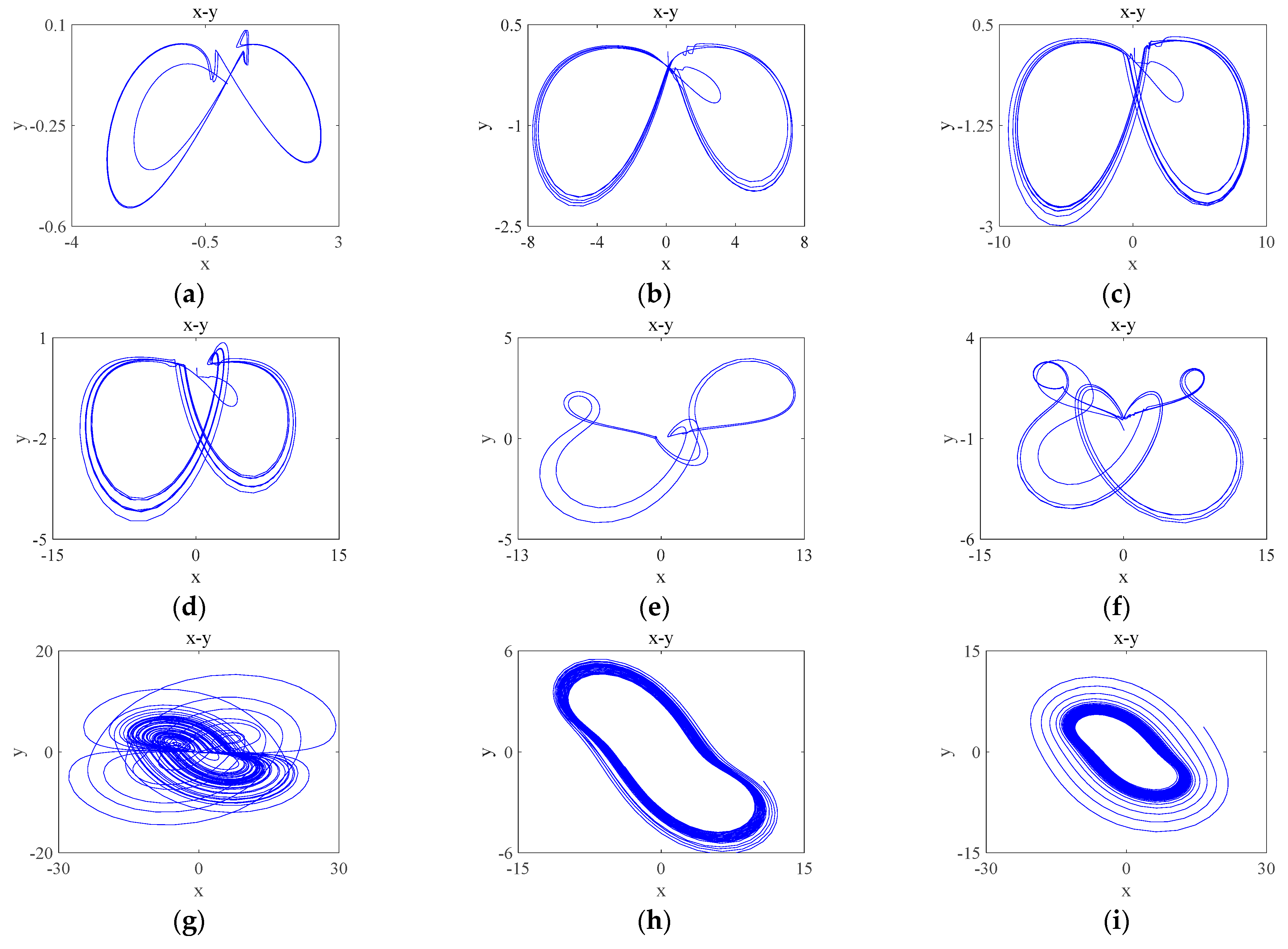
To investigate the periodic limit ring of the system, a number of parameter values are selected, as shown in Table 2, and their attractor phase diagrams are shown in Figure 5, where Table 2 corresponds to the attractor phase diagrams of Figure 5. It can be seen that the system has a periodic limit ring and chaotic attractor dependent on the different parameters .

Table 2.
Attractor categories and numbers corresponding to different values of parameter .

Figure 5.
Phase portraits of the system with different parameter (Table 2) on plane: (a) ; (b) ; (c) ; (d) ; (e) ; (f) ; (g) ; (h) ; (i) .
3.2. Dependent on the Dynamics of Parameter
Let parameter be a variable control parameter, when , and , the initial condition is , the fixed step time is 0.01 s and the total duration is s. The fourth-order Runge–Kutta method and wolf algorithm are used to simulate the Lyapunov exponent spectrum and bifurcation diagrams for the evolution of the system variable within the parameter . The Lyapunov exponent spectrum is sampled at 600 points and the bifurcation diagram at 600 points, and the obtained images are shown in Figure 6.

Figure 6.
Lyapunov exponent spectrum and bifurcation diagram of chaotic system with : (a) Lyapunov exponent spectrum; (b) bifurcation diagram.
As can be seen in Figure 6, when parameter is used as a variable control parameter, the system varies between three states: periodic, chaotic and quasi-periodic. In system it is in a periodic state; in systems and , it is in a chaotic state; and in system , it is in a quasi-periodic state.
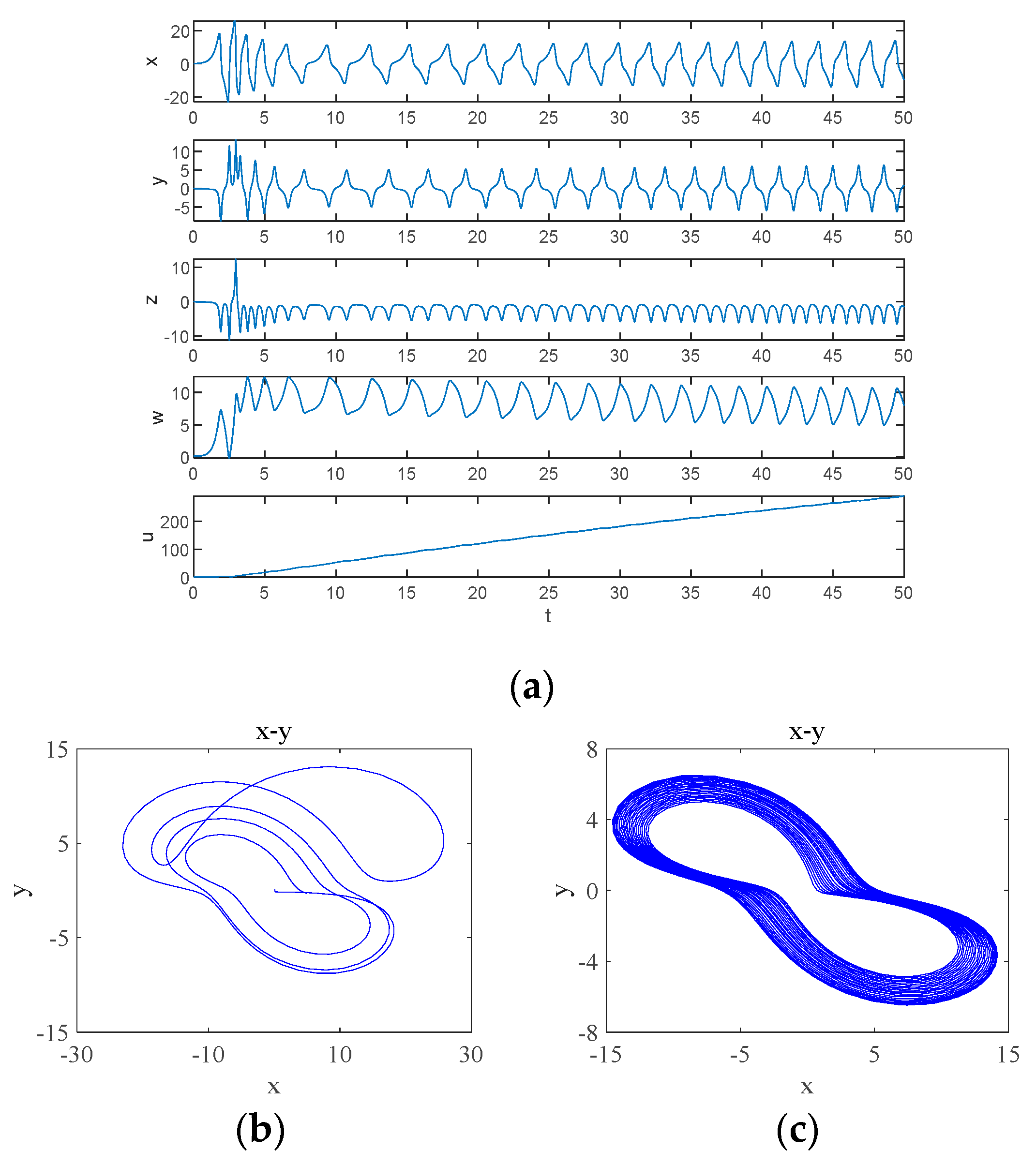
When , the system undergoes a transition from a quasi-periodic state to a chaotic state, and the simulation obtains the time-domain waveform of the system as shown in Figure 7a, where the system behaves chaotically for a shorter period and enters into a periodic behavior after a certain period, which is referred to as transient chaos, which is due to the presence of non-attractive saddle points in the phase space [29]. At , the system is in a chaotic state and its attractor phase diagram is shown in Figure 7b, and at , the system is in a periodic state and its attractor phase diagram is shown in Figure 7c.

Figure 7.
Transient chaos phenomenon of the system from chaos-period when : (a) time-domain waveform; (b) transient chaos at ; (c) steady state period at .
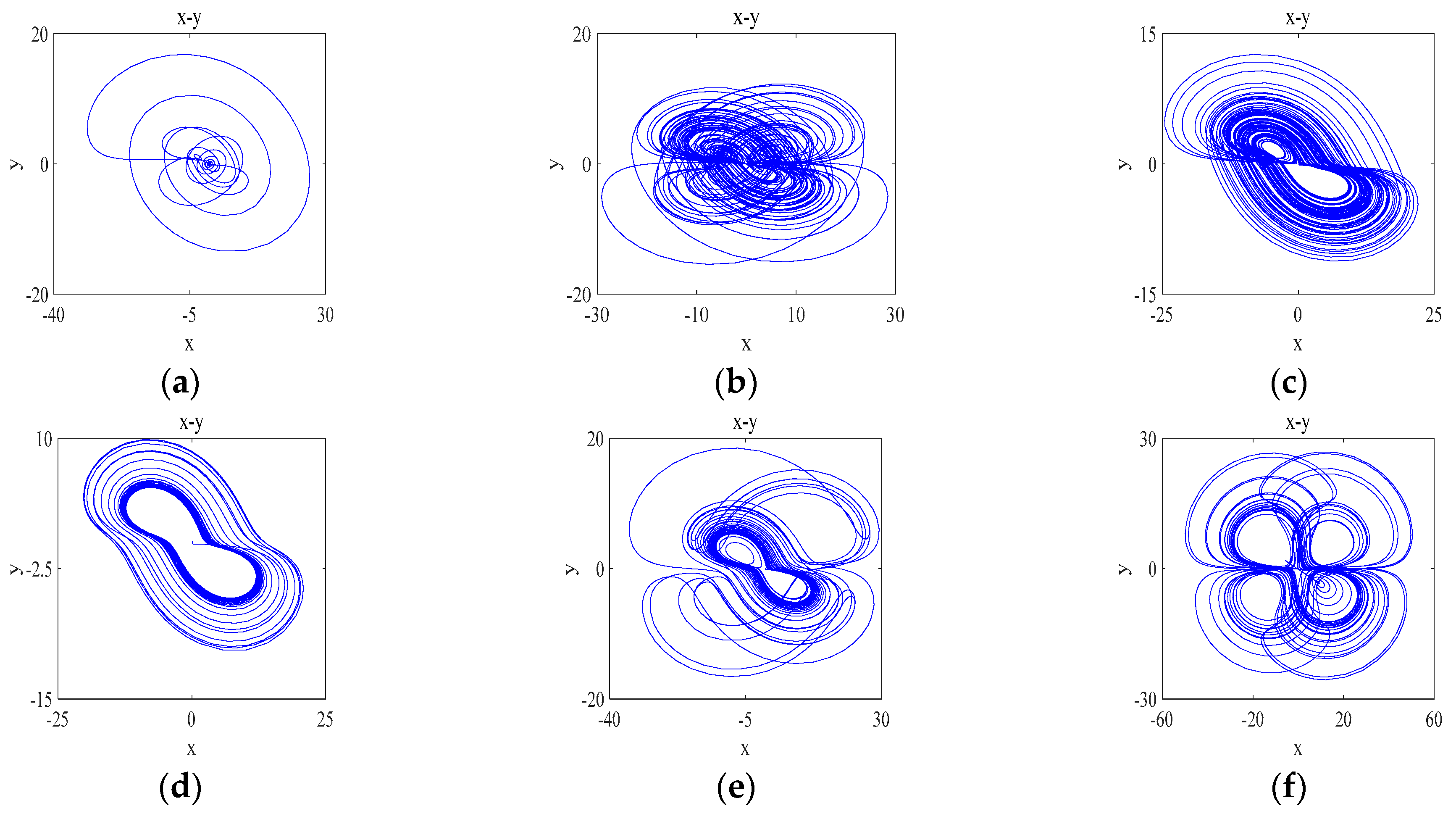
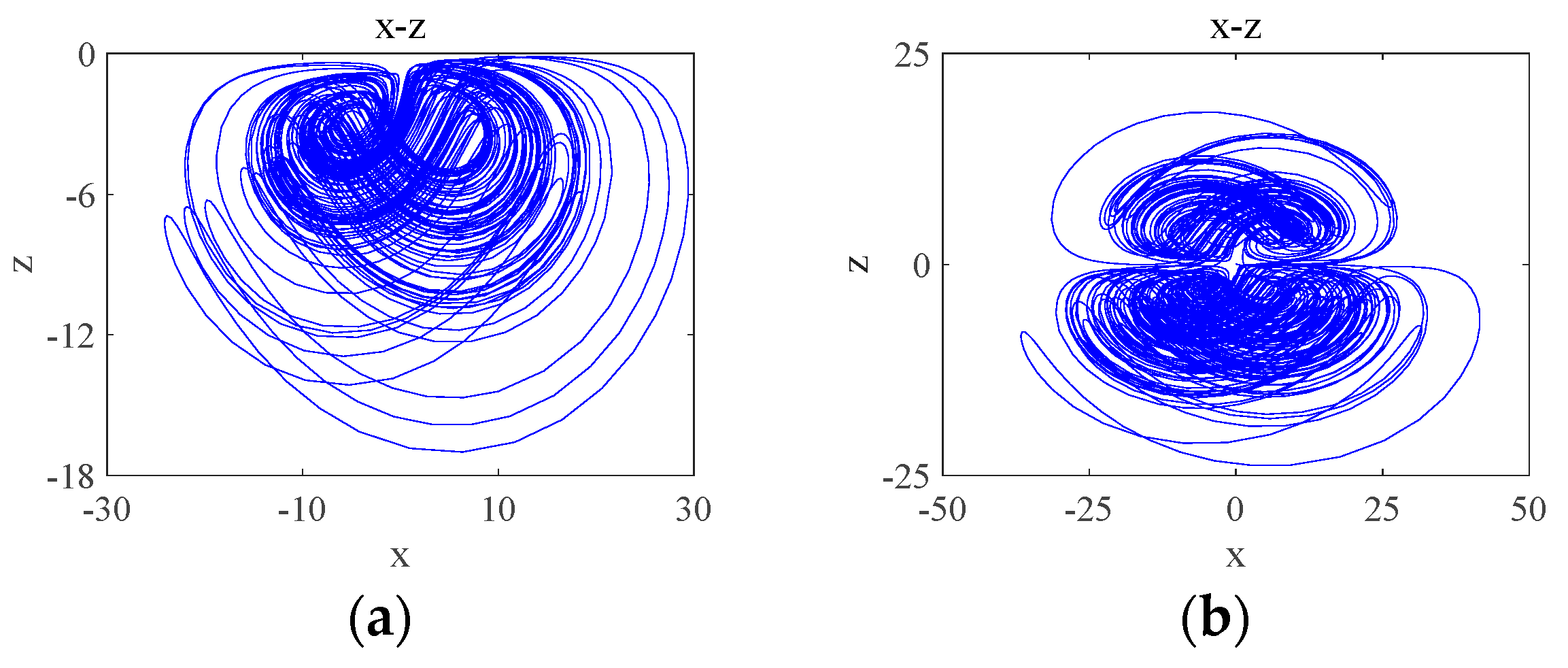
The different types of attractors that the system will produce when the parameter is varied: when the periodic state attractor of the system is shown in Figure 8a; when the system has two positive values of the Lyapunov exponent and the system has significant quadruple-winged hyperchaos in the phase plane, such that , whose attractor phase diagram is shown in Figure 8b; when the system has significant two-wing hyperchaos in the phase plane, let and its attractor phase diagram is shown in Figure 8c; when the quasi-periodic state attractor of the system is shown in Figure 8d; when the system is in a weakly chaotic state and its attractor phase diagram is shown in Figure 8e; and when , the system is in a chaotic state and its attractor still presents a quadruple-winged state, but its quadruple-winged attractor is more regular compared to . Let and its attractor phase diagram is shown in Figure 8f. Thus, the system has a large adjustable space for the parameter and has a variable wing phenomenon dependent on the parameter .

Figure 8.
Attractor phase diagrams for variable wings dependent on parameter : (a) ; (b) ; (c) ; (d) ; (e) ; (f) .
3.3. Dependence on the Kinetic Properties of the Memristor Parameter
Let parameter be a variable control parameter, when , , and , the initial condition is , the fixed step time is 0.01 s and the total duration is s. The fourth-order Runge–Kutta method and wolf algorithm are used to simulate the Lyapunov exponent spectrum and bifurcation diagrams for the evolution of the system variable within the parameter . The Lyapunov exponent spectrum is sampled at 500 points and the bifurcation diagram at 500 points, and the obtained images are shown in Figure 9.

Figure 9.
Lyapunov exponent spectrum and bifurcation diagram of chaotic system with : (a) Lyapunov exponent spectrum; (b) bifurcation diagram.
From Figure 9, it can be seen that when parameter is used as a variable control parameter, the system is in the three states of periodic, chaotic and quasi-periodic and constantly switches between the two states of periodic and chaotic, as shown in Table 3.

Table 3.
System states corresponding to different values of parameter .
The different types of attractors that the system will produce when the parameter is varied are as follows: when , the attractors of the system present a chaotic state, as shown in Figure 10a, at which time the system (4) has two positive Lyapunov exponent values and the system has significant biplane hyperchaos in the phase plane; when , the phase diagram of the attractor obtained from the simulation is shown in Figure 10b and the chaotic attractor presents a four-winged state. Thus, the memristor parameter of the system likewise has a large adjustable space, and the system has a variable wing phenomenon that depends on the memristor parameter .

Figure 10.
Attractor phase diagrams for variable wings dependent on parameter : (a) ; (b) .
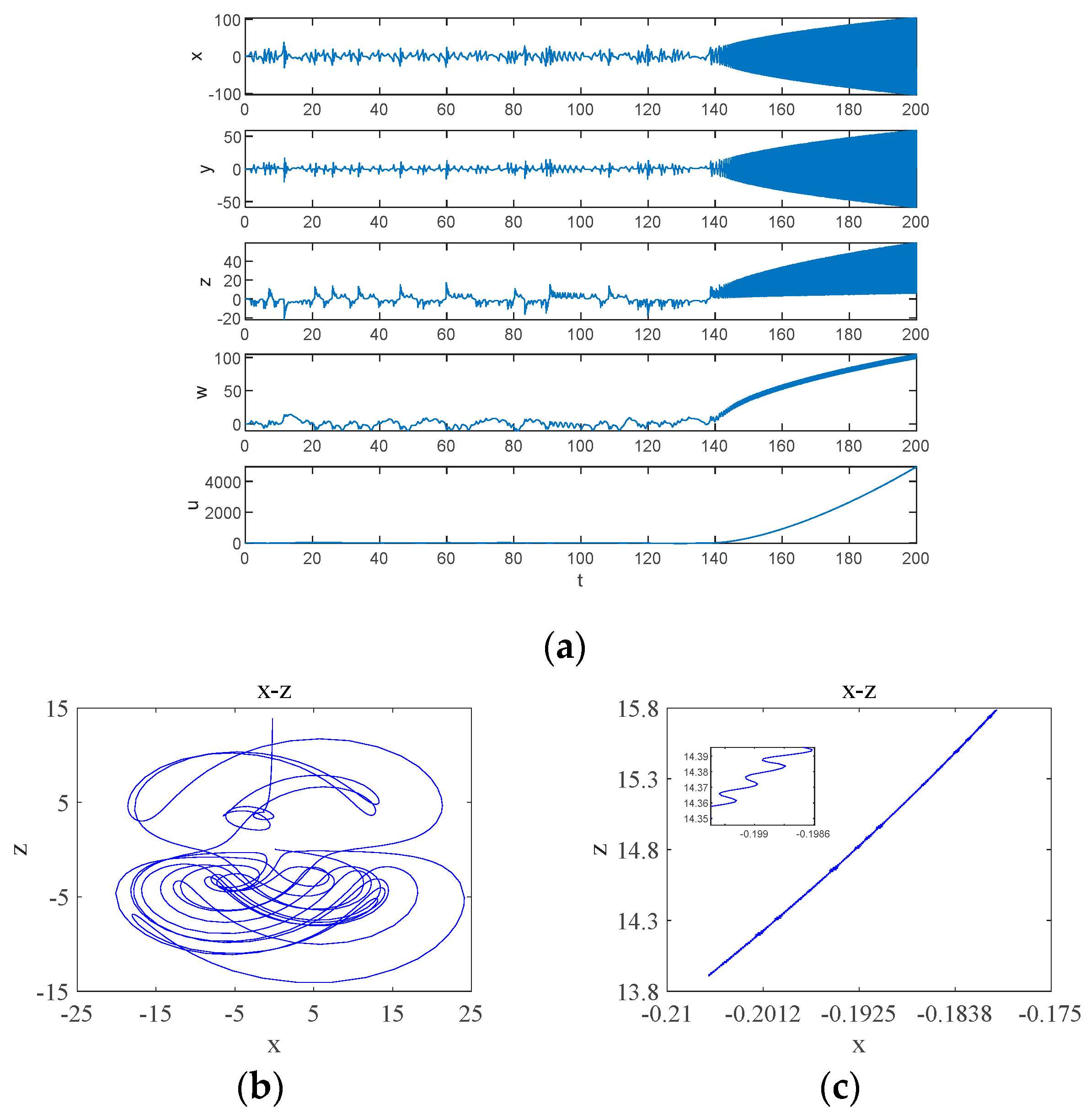
When parameter is in the quasi-periodic state interval, the system will have transient chaos phenomenon, which is different from the transient chaos phenomenon depending on the coupling parameter in Figure 7, and this time, the transient chaos phenomenon is a transition from chaotic to quasi-periodic state. is taken randomly in the quasi-periodic interval, and the simulation yields the time-domain waveform as shown in Figure 11a. The system exhibits chaotic behavior on a finite time scale, transforming to a quasi-periodic state after a period of time: inside , the system is in a chaotic state and its attractor phase diagram is shown in Figure 11b; inside , the system is in a quasi-periodic state and its attractor phase diagram is shown in Figure 11c.

Figure 11.
Time-domain waveform and attractor phase diagrams: (a) time-domain waveforms; (b) transient chaos at ; (c) steady state period at .
3.4. Complexity Analysis
The spectral entropy value of a chaotic system (SE) [30] is an important index for evaluating the complexity and stochasticity of chaotic sequences, which as an optimization algorithm of approximate entropy approximation can measure the complexity of chaotic sequences and can reflect the structural complexity of chaotic systems. In the field of communication, the system complexity is closely related to the communication security. The specific spectral entropy complexity calculation process is as follows:
Step 1: Remove the direct current (DC). For a chaotic pseudo-random sequence of length , the following equation is used to remove the DC part, so that the spectrum can reflect the signal energy information more effectively, i.e.,
where .
Step 2: Fourier transform. Perform a discrete Fourier transform on the sequence .
where .
Step 3: Calculate the relative power spectrum. For the transformed sequence, take the first half for calculation, according to Paserval’s theorem, and calculate the power spectrum value of a certain frequency point as
where , and the total power of the sequence can be defined as
Then, the relative power spectrum probability of the sequence is :
Easy to know .
Step 4: Calculate the spectral entropy. Using the relative power spectral density , combined with the Shannon concept, the spectral entropy se of the signal is obtained as
where is defined to be 0 if is 0. It can be proved that the magnitude of the spectral entropy converges to . In order to facilitate the comparative analysis, the spectral entropy is normalized, and the normalized spectral entropy (SE) is obtained as
It can be seen that when the sequence power spectrum distribution is more unbalanced, the simpler the sequence spectral entropy structure is, the more obvious oscillation laws are in the signal, and the smaller the value of SE measure obtained, i.e., the smaller the complexity is, otherwise the greater the complexity is. For spatial spectral entropy complexity maps, the darker the image color, the greater the complexity of the system, the better the pseudo-randomness of the resulting sequence and the better it can be applied in the field of encryption [31].
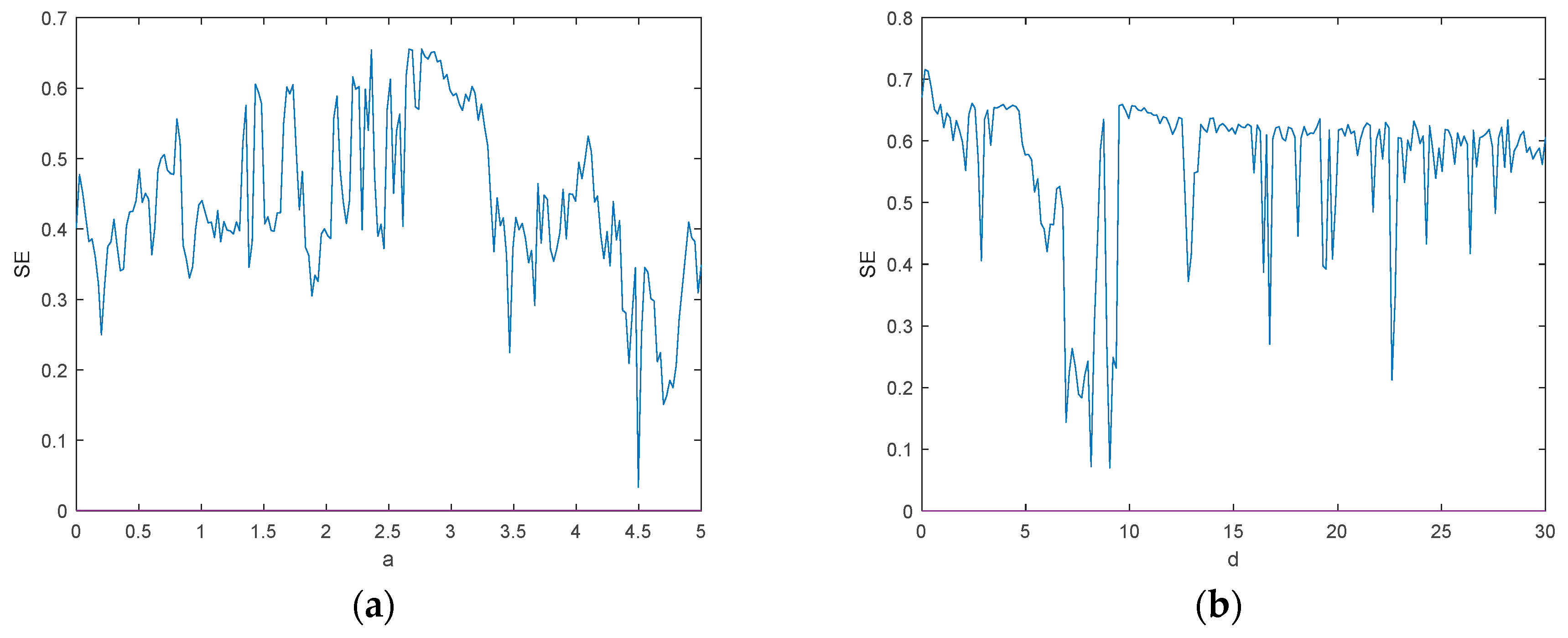
To better analyze the dynamic behavior and complexity characteristics of the chaotic system, the spectral entropy complexity SE cure of the chaotic system at , as shown in Figure 12a, and at , as shown in Figure 12b, are plotted by MATLAB 2018a. From Figure 12a,b, it can be seen that the maximum value of SE is about 0.65, which corresponds to the maximum Lyapunov exponential map, and the complexity of the system appears to have a higher value at . However, at this time, the system is in a cyclic state, and this phenomenon may be because the system has a high degree of sensitivity and small parameter variations can cause the system to be in a different state of the limit loop.

Figure 12.
SE complexity analysis: (a) The spectral entropy complexity SE of ; (b) the spectral entropy complexity SE of .
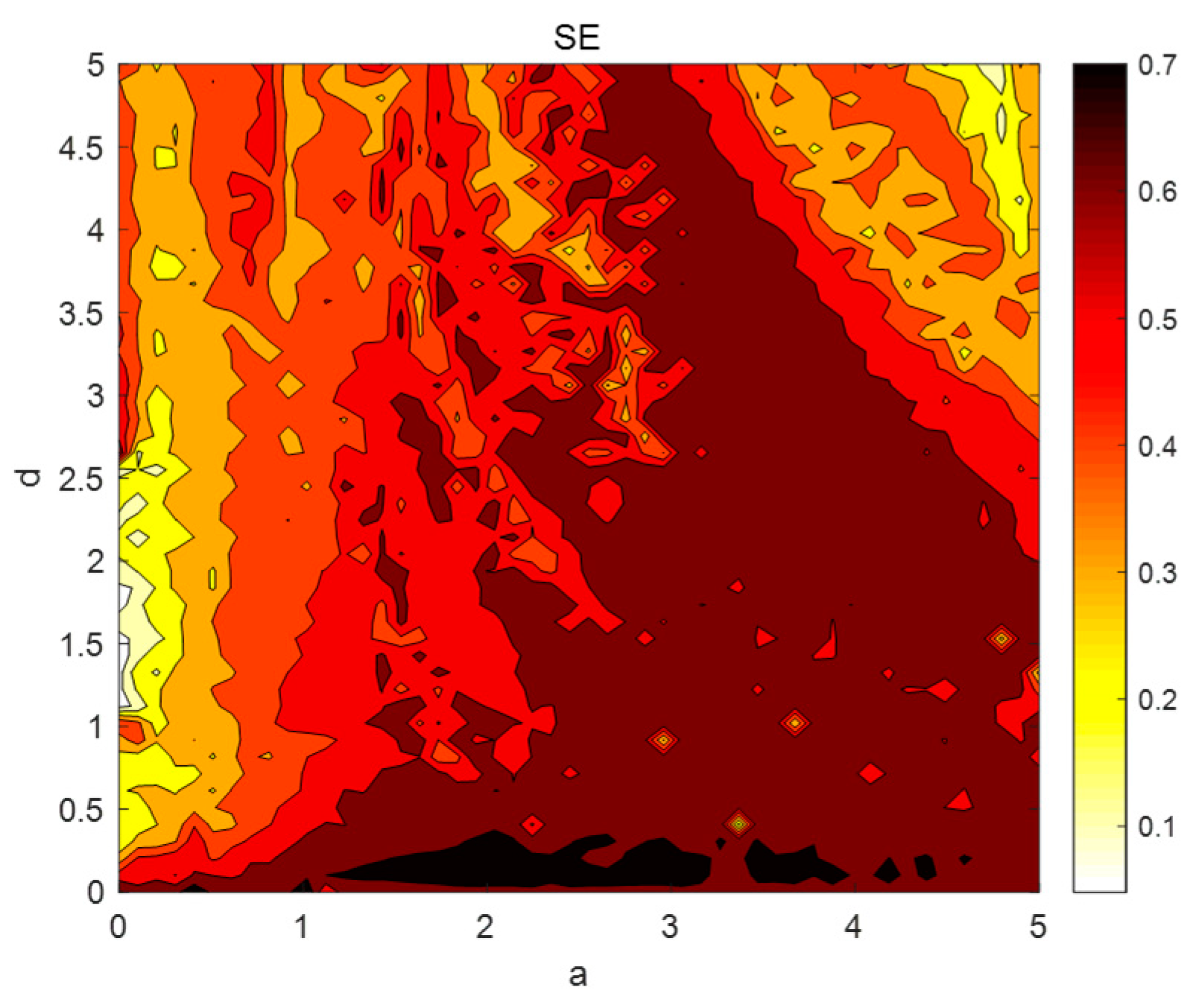
The system parameters and are divided into parts, where and . The spectral entropy complexity of each point in the parameter space is obtained by simulation, as shown in Figure 13. As can be seen from Figure 13, the complexity is mainly concentrated between and .

Figure 13.
The spectral entropy complexity of and .
The complexity of the system proposed in this study is compared with the literature [32,33,34,35], and the results are shown in Table 4. Therefore, the four-dimensional chaotic system of system four has the highest complexity and has a greater advantage in practical more complex encryption environments.

Table 4.
Comparison of SE complexity of this paper with the other literature.
4. Circuit Simulation
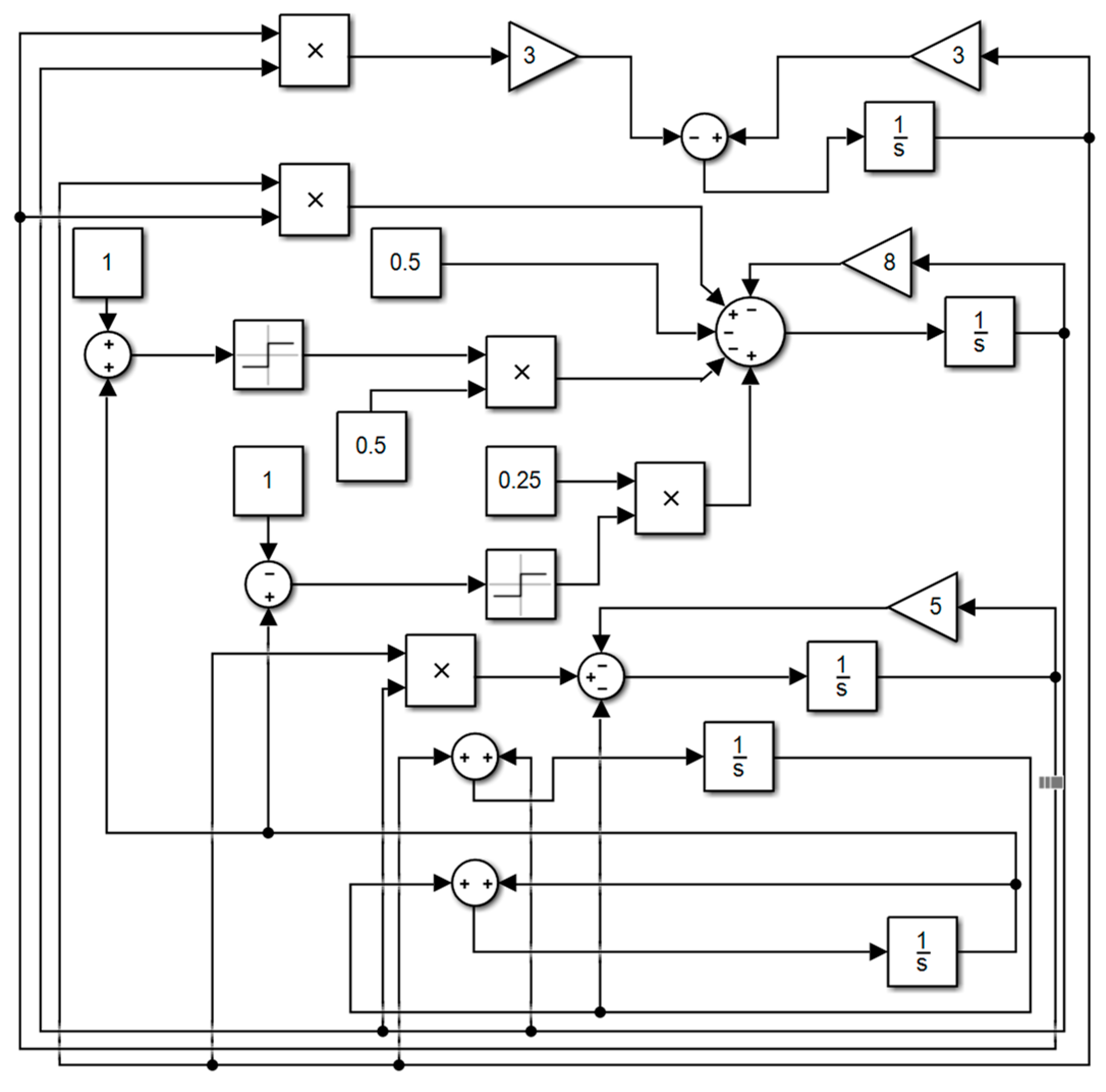
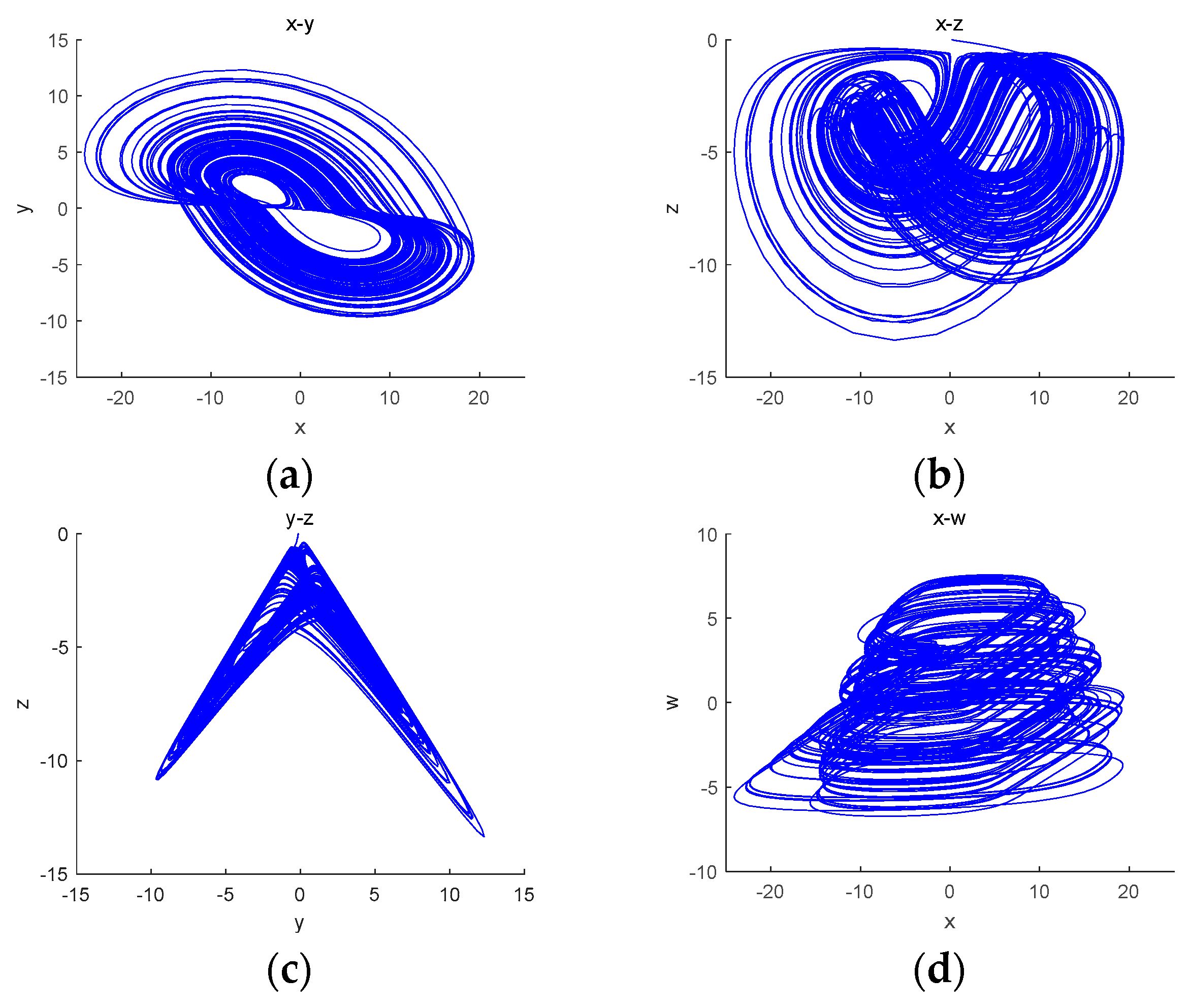
Based on the obtained model of the tri-valued memristor chaotic system, the circuit is built using the DSP Builder element in MATLAB/Simulink library [36], as shown in Figure 14, and the attractor phase diagram of the system is obtained using an oscilloscope, as shown in Figure 15. The chaotic attractor trajectories in the , , and planes obtained through numerical experiments are almost the same as the attractor phase diagrams obtained through Simulink, which verifies the correctness of this chaotic system.

Figure 14.
Simulink circuit diagram.

Figure 15.
Attractor phase diagrams: (a) the plane; (b) the plane; (c) the plane; (d) the plane.
5. Synchronized Control of Differently Structured Five-Dimensional Memristor Chaotic Systems
There are relatively few studies on the synchronization of differently structured chaotic systems based on different memristors. When high-dimensional chaotic systems containing different memristors are synchronized, it is almost impossible to predict the synchronized chaotic system at the receiver due to the different system structures at the sender and the receiver, so the synchronization of differently structured chaotic systems improves the confidentiality and security of information transmission. In this paper, we use the nonlinear feedback synchronous control method to synchronize the new fifth-order third-valued memristor chaotic system and the five-dimensional magnetically controlled memristor hyperchaotic system of the literature [37] by designing a feedback controller, which is rewritten as a five-dimensional tri-valued memristor chaotic system as the main system:
The five-dimensional magnetically controlled memristor chaotic system of the literature [37] is rewritten as a slave system as
In Equation (25), , , , and are synchronization controllers.
The total slave system is realized to be synchronized in different initial states, defining the error between the two systems as
Bringing Equations (24) and (25) into Equation (26), the error system equation is obtained as
Designed synchronous controllers are as follows:
The controller (28) is brought into the error system (27) to obtain a linear error system written as
Construct the Lyapunov function as
Derivation of Equation (28) and combining Equation (30) gives
When , , , the error system (27) converges exponentially to the global equilibrium point and the error system tends to zero, i.e., the two differently structured systems are synchronized.
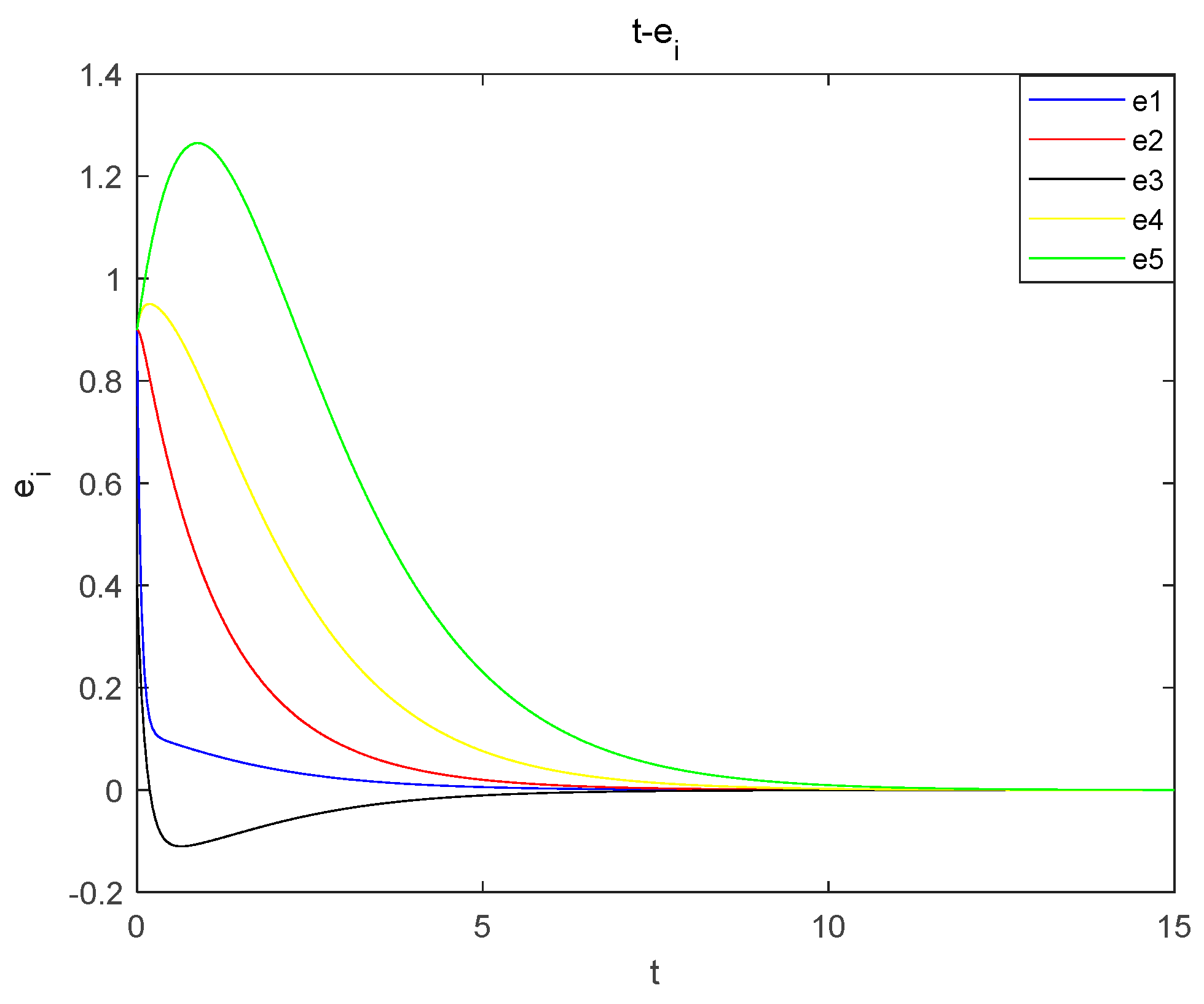
Experimental simulation of the proposed nonlinear feedback synchronous control is carried out, the initial value of the master system is and the initial value of the slave system is . Taking the , of the controller, the error curves are obtained as shown in Figure 16, from which it can be seen that the master and slave systems are synchronized at . This verifies the correctness and validity of the design of the controller and proves that the newly proposed chaotic system can be applied in the field of encryption.

Figure 16.
Nonlinear feedback synchronization error plot.
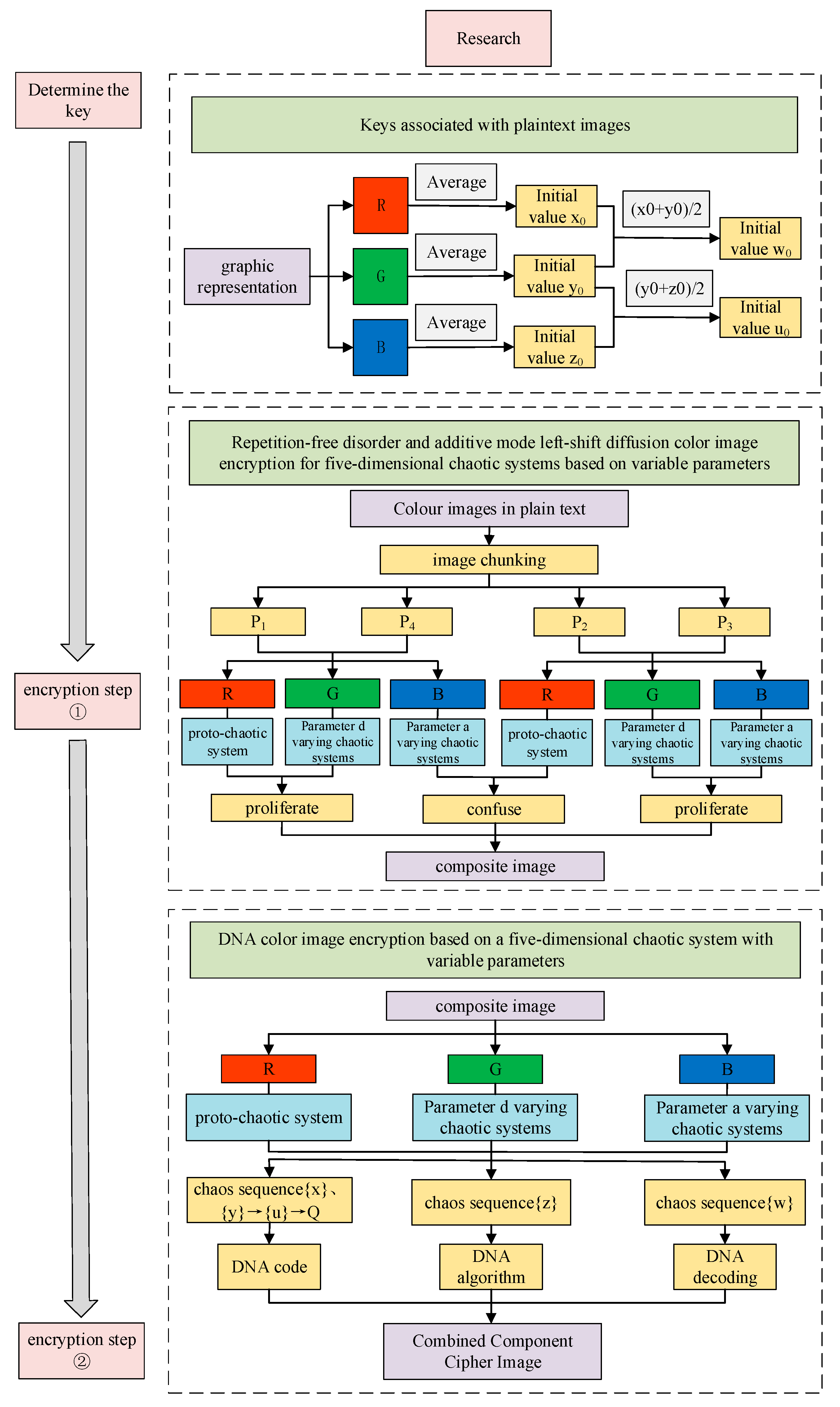
6. Variable Parameter Color Image Encryption Scheme
6.1. Encryption and Decryption Program
Traditional chaos-based encryption regimes generally use fixed parameters, and the analysis and deciphering of system tracks make the algorithms less secure. Therefore, a dynamic parameter encryption scheme is proposed based on the framework system of diffusion, disruption and DNA encryption algorithms by taking advantage of the parameter tunability of five-dimensional tri-valued memristor chaotic systems. The process is described below:
Step 1: Determining the key. The three color components of the plaintext color image are transformed into one-dimensional vectors , and . The pixel averages of their components are found separately and combined as the key and as the initial value of the chaotic system, as shown in Equations (32) and (33) below.
Step 2: Chunking. chunking operation is performed on the color image of size , which is uniformly divided into images of size . The chunked images are transformed into one-dimensional vectors, denoted as , , and , respectively.
Step 3: Diagonal block encryption methods and .
- 1.
- Generate a chaotic pseudo-random sequence of length using chaotic system, discard the first 1500 points of the transition state and perform additive modulo left-shift diffusion operation on a component of the image obtained from the chunking. Convert the component into a gray-scale image with eight bits for each pixel point. The lower three bits of any data range from zero to seven as the effective range of cyclic shifting of a pixel point’s data, then the plaintext after the cyclic left shift of the data and the chaotic sequence are added and each byte is summed and modeled to obtain the encrypted sequence . The computation is shown in Equation (34).where is a ciphertext sequence, is a chaotic sequence, is a plaintext vector and is a cyclic left shift to the lowest three bits of the data.
- 2.
- From the dynamical behavior of the new system, it can be seen that the complexity of the system is higher when parameter . Take this time to generate a pseudo-random sequence of length . Perform a modulo left-shift diffusion operation on the component of image obtained from the chunking to obtain the encrypted sequence .
- 3.
- When parameter , the complexity of the system is the highest. Take this time to produce a pseudo-random sequence of length . The repeated pseudo-random numbers in are eliminated and only the first occurrence of the value is retained, and then the elements in the set that do not appear in are ranked from smallest to largest. Then, is swapped with to change the position and component of image obtained from the chunking is dislocated without repetition to obtain the encrypted sequence .
Similarly, the , and of the chunked are encrypted in the same way as .
Step 4: Diagonal block encryption methods and .
- 1.
- Keeping the system parameters unchanged and making the system parameters , the components and of are encrypted without repetitive disruption, respectively, in the same way as in Step 3 of 3.
- 2.
- Let parameter , generate a pseudo-random sequence and perform a modulo left-shift diffusion operation on the component of , encrypted in the same way as in Step 3 of 1.
Similarly, the , and of the chunked are encrypted in the same way as .
Step 5: Combining the images. The sub-blocks that have been diffused and encrypted are recombined to obtain image .
Step 6: DNA encryption.
- 1.
- Separate the components , and of image .
- 2.
- Keeping the parameters unchanged, sequences , , , and of length are generated and sequence is transformed into a two-dimensional matrix , which is used for DNA operations with component of image .
- 3.
- Sequence determines the encoding mode of the DNA of each component of image , and sequence determines the DNA encoding mode of matrix . There are a total of eight modes of DNA encoding and decoding, which need to be transformed into and . After the transformation, the value of each sequence is a random integer from one to eight, and the transformation equation is shown in Equation (36):
- 4.
- The decoding of DNA is determined by sequence . DNA decoding is the inverse process of DNA coding, and there are eight ways of decoding, i.e., decoding , , and into specific binary values.
- 5.
- There are three algorithms for defining DNA, and the DNA algorithm is determined by the system-generated sequence . If , additive, if , subtractive and if , different-or. Sequence is transformed according to Equation (38) into integers ranging from zero to three.
Similarly, make and repeat Step 6 for DNA encryption of component ; make and repeat Step 6 for DNA encryption of component .
Step 7: Combining the three 2D matrices encrypted by DNA into a 3D matrix to obtain the encrypted image.
The encryption flowchart is shown in Figure 17.

Figure 17.
Encryption flowchart.
The encryption algorithms used are all reversible, so the decryption process is the inverse of the encryption process. The encrypted image is subjected to DNA encoding, DNA inverse operation, DNA decoding, inverse scrambling and inverse diffusion in order to obtain the decrypted image. The decrypted image can be obtained. The specific decryption steps are as follows:
Step 1: Determining the key. Same as the first step of the encryption process.
Step 2: DNA decoding. The reverse process of DNA coding is known as DNA decoding.
- 1.
- Separate the components , and of ciphertext image .
- 2.
- Keeping the parameters unchanged, sequences , , , and of length are generated, and sequence is transformed into a two-dimensional matrix , which is used for DNA operations with component of image .
- 3.
- Sequence determines the decoding method of DNA for each component of image , and sequence determines the decoding method of DNA for matrix . There are eight ways to encode and decode DNA, which need to transform and . The value of each sequence after transformation is a random integer from one to eight, and transformation Equation (40) is as follows:
- 4.
- Sequence determines how the DNA is encoded, and there are eight ways to decode it, i.e., , , and are encoded into specific binary values.
- 5.
- There are three algorithms for defining DNA, and the DNA algorithm is determined by the system-generated sequence . If , subtraction is used; if , addition is used; and if , inverse heteroscedasticity is used. Sequence is transformed into an integer in the range zero to three by the transformation of Equation (42).
Similarly, let , repeat Step 6 for DNA decryption of component ; let , repeat Step 6 for DNA decryption of component .
Step 3: Combining the 2D vectors of the three-component RGB after performing DNA decryption to obtain color cipher image .
Step 4: Chunking. The chunking operation is performed on the color ciphertext image of size , which is uniformly divided into images of size . The chunked image is converted into one-dimensional vectors, denoted as , , and , respectively.
Step 5: Diagonal block decryption method and .
- 1.
- Using the chaotic system to generate a chaotic pseudo-random sequence of length , discard the first 1500 points of the transition state, carry out the reverse additive modulo left-shift diffusion operation on a certain component of the ciphertext image obtained from the chunking and transform the component into a gray-scale image with eight bits for each pixel point. The low three bits of any piece of data are taken as the value range of 0~7 as the effective range of cyclic shifting of a pixel point’s data, and then after the cyclic right shift the plaintext data and the chaotic sequence for the addition operation, each byte is added and modulo to obtain the decrypted sequence . Equation (43) is as follows:where is a ciphertext sequence, is a chaotic sequence, is a plaintext vector and is a cyclic right shift of the lowest three bits of the data.
- 2.
- From the dynamical behavior of the new system, it can be seen that the complexity of the system is higher when parameter . Taking this time, a pseudo-random sequence of length is generated and an inverse modulo left-shift diffusion operation is performed on the component of image obtained from the chunking to obtain decrypted sequence .
- 3.
- When parameter , the complexity of the system is the highest. Take this time to produce a pseudo-random sequence of length . The repeated pseudo-random numbers in are eliminated and only the first occurrence of the value is retained, and then the elements in the set that do not appear in are ranked from smallest to largest. Then, and are swapped for the position of components of image obtained from the chunking to perform a repetition-free disarray and to obtain the decrypted sequence .
Similarly, the , and of the chunked are decrypted in the same way as image .
Step 6: Decrypting the diagonal blocks way and .
- 1.
- Keeping the system parameters unchanged and letting system parameters , the inverse non-repetitive disambiguation operation is performed on component and component of , respectively, decrypted in the same way as in the third step (3).
Let parameter , generate a pseudo-random sequence and perform a reverse modulo left-shift diffusion operation on component of . The decryption in the same way as in Step 5 of 3.
Step 7: Combining the images. The sub-blocks that have been diffused and decrypted are recombined to obtain original image .
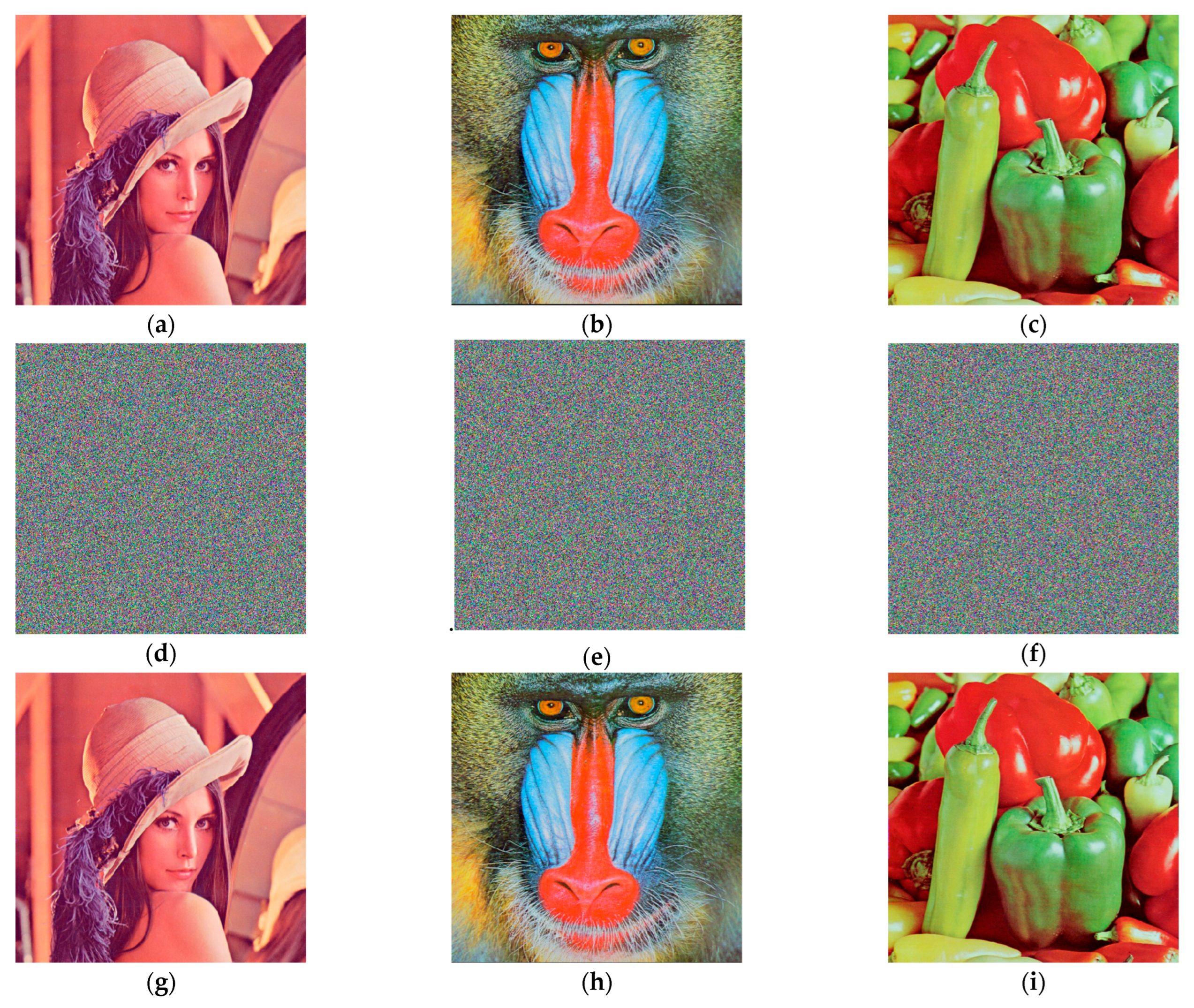
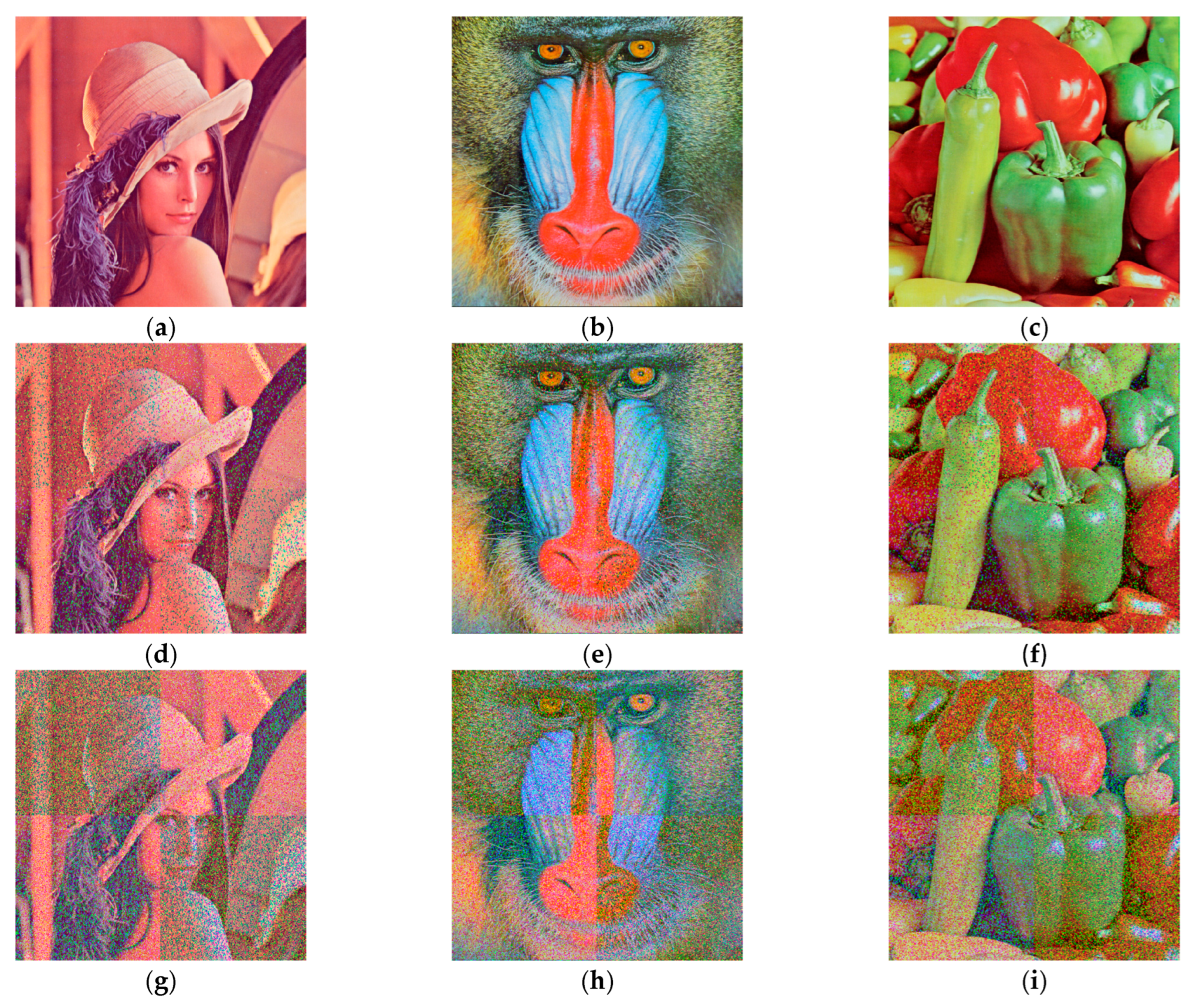
Using the above proposed variable parameter encryption and decryption scheme, the encryption and decryption operations are carried out on RGB color Lena, Baboon and Peppers images of size pixels using MATLAB 2018a, and the encryption results are shown in Figure 18. It is difficult to see the information of the original image from the encrypted images, and the decrypted images do not differ much from the original images, which proves that the encryption and decryption algorithm is feasible.

Figure 18.
Original images, encrypted images and decrypted images: (a) the Lena original image; (b) the Baboon original image; (c) the Peppers original image; (d) the Lena encrypted image; (e) the Baboon encrypted image; (f) the Peppers encrypted image; (g) the Lena decrypted image; (h) the Baboon decrypted image; (i) the Peppers decrypted image.
6.2. Performance Analysis
6.2.1. Histogram Tests
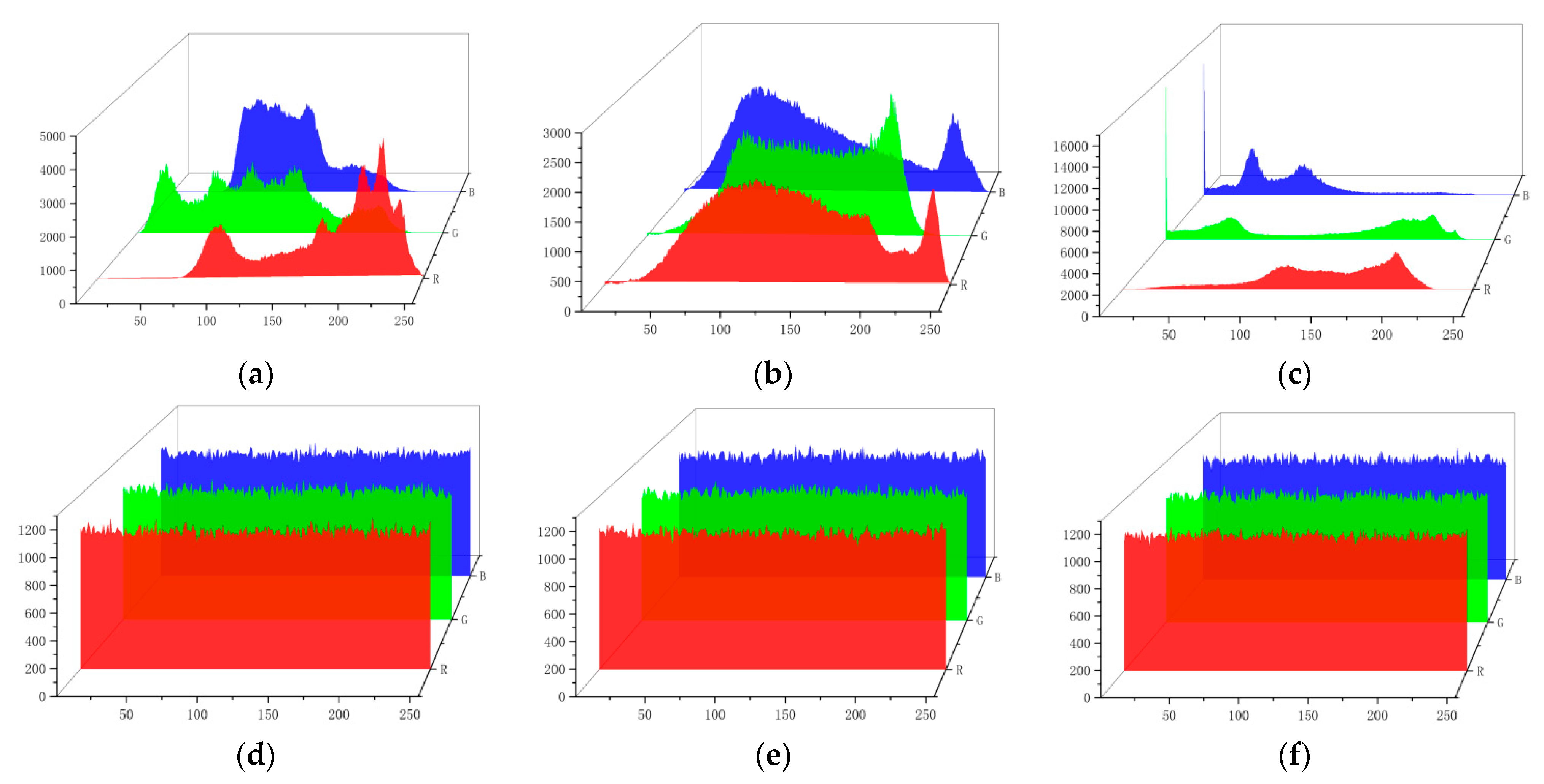
The distribution of the number of pixel points can be seen from the histograms. The histograms of the RGB components of the color Lena image, Baboon image and Peppers image are shown in Figure 19. The histogram of the plaintext image falls and falls, while the encrypted images have a uniform distribution, based on which the encryption algorithm effectively hides the statistical features of the original image, and it is difficult for the attacker to predict the original image using statistical analysis.

Figure 19.
Histogram tests: (a) the Lena plaintext image; (b) the Baboon plaintext image; (c) the Peppers plaintext image; (d) the Lena encrypted image; (e) the Baboon encrypted image; (f) the Peppers encrypted image.
6.2.2. Pixel Distributions
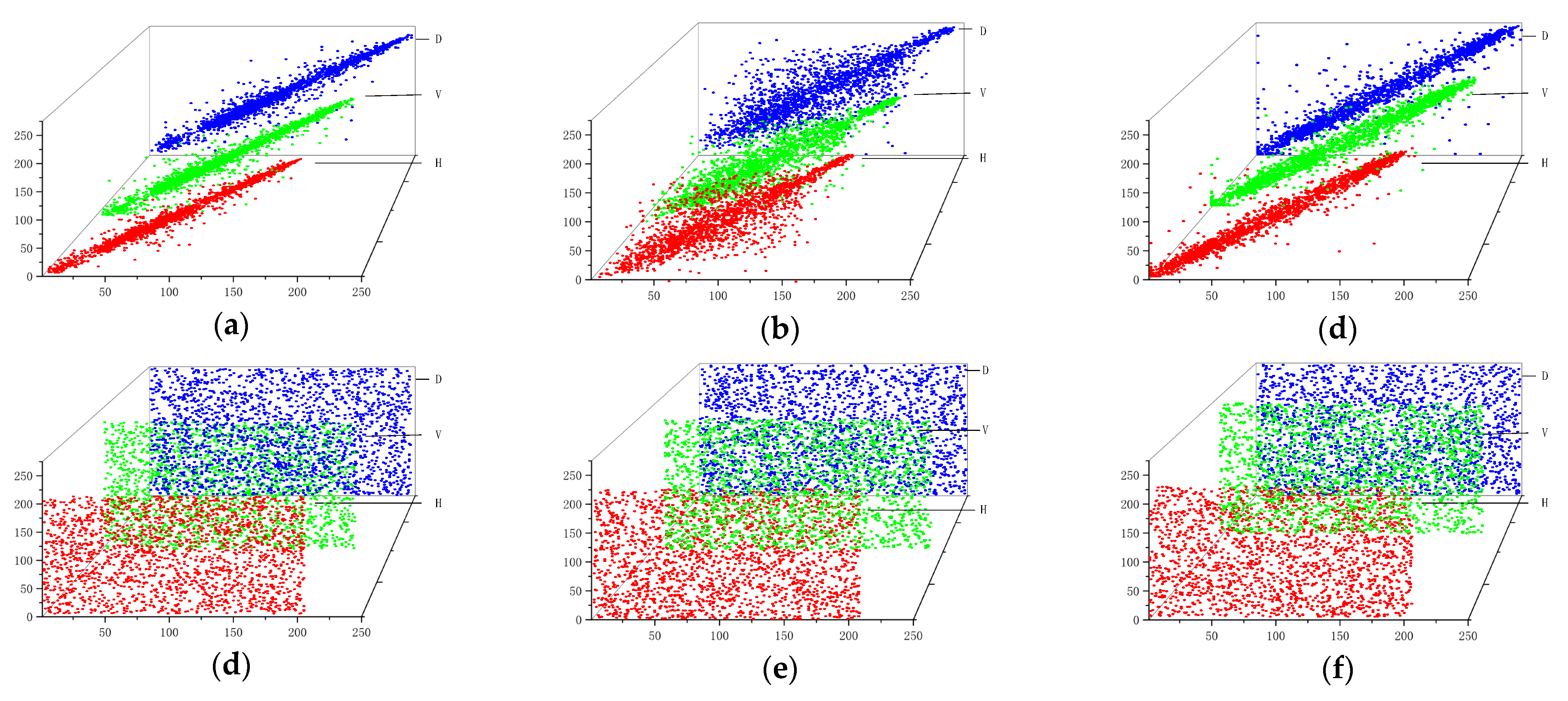
The correlation coefficient is a quantitative expression of the image pixel correlation, and to prevent statistical attacks, the correlation needs to be reduced to hide the statistical information of the plaintext. The distributions of neighboring pixels in the horizontal, vertical and diagonal directions for the Lena, Baboon and Peppers plaintext images and the encrypted images are shown in Figure 20. Taking Lena image as an example, the correlation coefficients of this paper’s algorithm are compared with those of the algorithms in the literature [38,39,40], and the results are shown in Table 5. The correlation of neighboring pixel points of plaintext images is stronger and the pixel points are concentrated in the nearby distribution, while the correlation of encrypted images encrypted by the encryption algorithm is close to zero and the distribution of pixel points is more randomized and close to a uniform distribution, which is more conducive to hide the plaintext information.

Figure 20.
Pixel distributions: (a) the Lena plaintext image; (b) the Baboon plaintext image; (c) the Peppers plaintext image; (d) the Lena encrypted image; (e) the Baboon encrypted image; (f) the Peppers encrypted image.

Table 5.
Relevance of the adjacent pixels of the Lena image.
6.2.3. Information Entropy
The information entropy reflects the uncertainty of the image information, the greater the entropy (close to eight), the greater the uncertainty and the less the visible information, calculated as
where , denote the gray value of the image, and denote the probability of occurrence of the gray values.
The distribution of gray values of the three channels RGB of the color image is counted using the above equation, and the percentage of gray values of the component RGB, i.e., the probability of each gray value, is calculated. The final information entropy of the color image is calculated by calculating the average of the three channels as the information entropy of the color image and will be compared with the literature [41,42,43], as shown in Table 6. In this paper, the information entropy is closer to eight, so the algorithm can be more resistant to entropy attacks.

Table 6.
Comparison of Lena’s information entropy.
6.2.4. Differential Attack
Differential attack is a powerful crypt analysis method that focuses on inferring the key by using the difference information between plaintext and ciphertext pairs. The number of pixels change rate (NPCR) and Unified Average Changing Intensity (UACI) are usually used to evaluate whether an algorithm can resist differential attacks. In general, the closer the NPCR is to 99.6094% and the UACI is to 33.4635% [44], the better the performance of the encryption algorithm.
A pixel is randomly selected from the original image, and one of the pixel values is modified according to Equation (45) to acquire image . The original image and modified image are encrypted using the algorithm proposed in this paper to obtain cipher images and . The difference between and is quantified by NPCR and UACI, and the NPCR and UACI values are computed as shown in Equations (46)–(48).
where is the original cipher image, is the cipher image with one pixel point changed, is any position of the image, is any position of the image, and are the image size, when is equal to , the value of is 0 and when is not equal to , the value of is 1.
The values of NPCR and UACI of Lena image are calculated using the above equation and compared with the literature [45,46] methods. The specific results are shown in Table 7, and the encryption algorithm in this paper is closer to the ideal values compared to the other literature. The difference in NPCR is 0.0009, while the difference in the literature [45] is 0.001, the difference in the literature [46] is 0.0013 and the difference between this paper and the ideal value of NPCR is the smallest; the difference in UACI is 0.0057, while the difference in the literature [45] is 0.0122, the difference in the literature [46] is 0.0157 and the difference between this paper and the ideal value of UACI is the smallest. It is proved that the encryption scheme has good sensitivity and high resistance to differential attacks. The algorithm proposed in this paper is parametrically dynamic compared to the literature [45,46], and the proposed DNA encryption scheme is parametrically dynamic, which greatly improves the ability to be deciphered.

Table 7.
The NPCR and UACI results compared with the other referenced literature.
In this paper, we propose a dynamic variable parameter encryption scheme based on more complex new five-dimensional tri-valued memristor chaotic systems, combining repeat-free disruption and additive mode left-shift diffusion methods, as well as DNA encryption methods. A differential attack is one of the more difficult attacks to resist among all the attacks, and the algorithm proposed in this paper can resist differential attacks better as compared to other encryption methods. This result is mainly because the parameters chosen for the encryption scheme in this paper are dynamically changing, and the attacker cannot simply perform a differential attack by analyzing a fixed parameter, which greatly increases the difficulty of deciphering and thus improves the security of the crypto system. This is the biggest advantage and difference in the dynamic variable parameter encryption scheme proposed in this paper over other advanced encryption methods.
6.2.5. Noise Attack
Strong encryption algorithms are tolerant to noise attacks to protect the image. To test the noise immunity of the encryption scheme, the encryption performance is tested in this paper by adding salt-and-pepper noise (SPN) and Gaussian noise (GN). The peak signal-to-noise ratio (PSNR) is used to measure the ability to resist noise attacks; in general, the larger the PSNR, the stronger the noise resistance of the encryption algorithm.
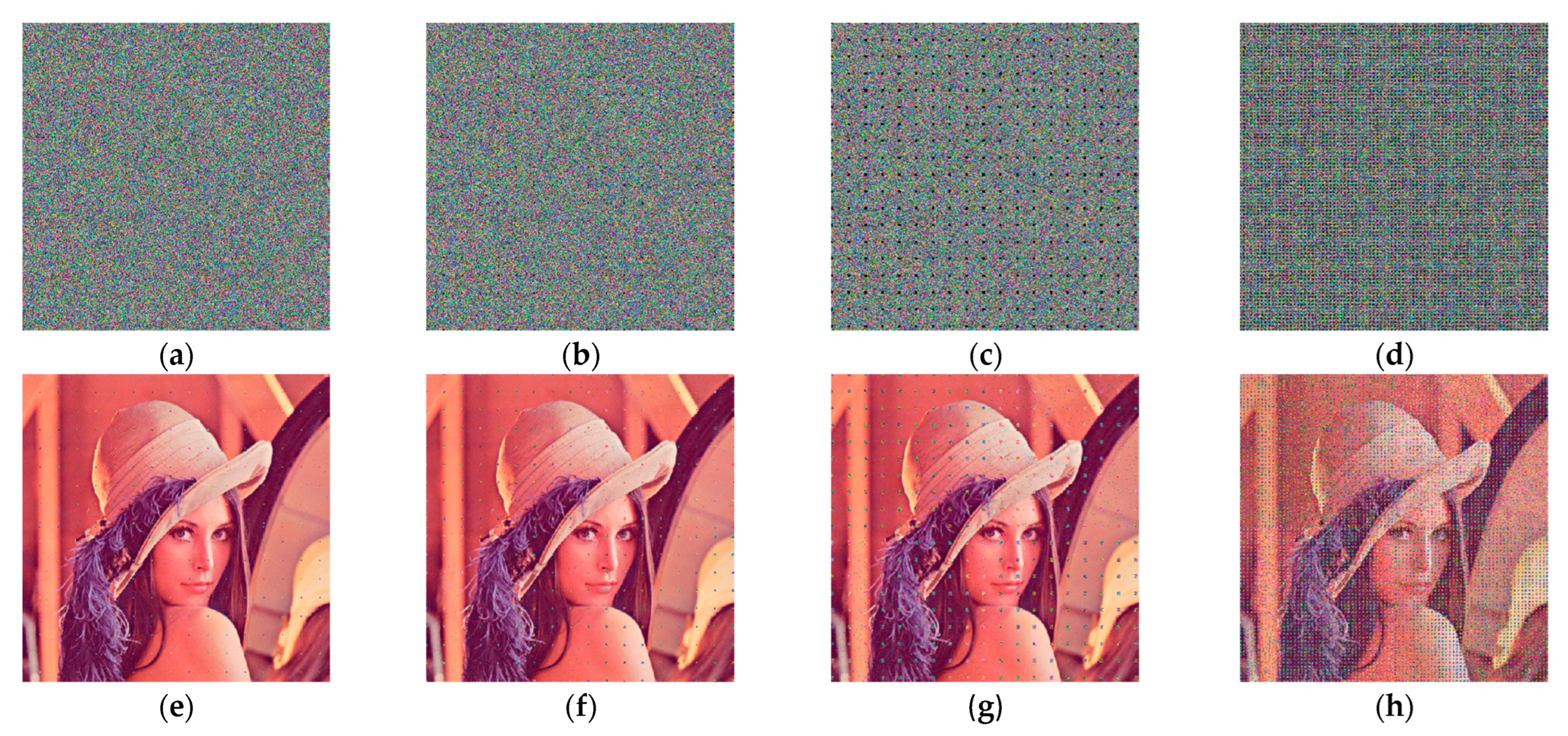
Salt-and-pepper noise is a common type of noise caused by variations in the intensity of signal pulses. When salt-and-pepper noise with densities of 0.01%, 0.1% and 1% is added to the Lena image, Baboon image and Peppers image for testing, the decrypted images obtained are shown in Figure 21. The PSNR values of the decrypted images containing densities of 0.01%, 0.1% and 1% salt-and-pepper noise obtained by numerical computation using MATLAB 2018a are shown in Table 8. When affected by salt-and-pepper noise with a density of 0.01%, the PSNR value of the decrypted images is greater than 31 dB, indicating that the quality of the decrypted images is better, even if there are distortions that cannot be detected by the naked eye. The PSNR value of the decrypted images is greater than 25 dB when affected by salt-and-pepper noise with a density of 0.1%, indicating that the decrypted images are of average quality with distortion. When subjected to salt-and-pepper noise with a density of 1%, the PSNR value of the decrypted images is greater than 16 dB and the presence of variability from the original images are already evident. Thus, it is proved that the algorithm can resist a certain degree of noise attack with high robustness.

Figure 21.
Decrypted images with different levels of salt-and-pepper noise added: (a) the Lena image with 0.01% salt-and-pepper noise; (b) the Baboon image with 0.01% salt-and-pepper noise; (c) the Peppers image with 0.01% salt-and-pepper noise; (d) the Lena image with 0.1% salt-and-pepper noise; (e) the Baboon image with 0.1% salt-and-pepper noise; (f) the Peppers image with 0.1% salt-and-pepper noise; (g) the Lena image with 1% salt-and-pepper noise; (h) the Baboon image with 1% salt-and-pepper noise; (i) the Peppers image with 1% salt-and-pepper noise.

Table 8.
Adding varying degrees of salt-and-pepper noise to the PSNR of the decrypted images.
Gaussian noise is a class of noise whose probability of occurrence obeys a Gaussian distribution and noise with a random depth of noise occurs at each pixel point of an image affected by Gaussian noise. Keeping the mean value as 0, when Gaussian noises with variance , variance and variance are added to Lena image, Baboon image and Peppers image for testing, the decrypted images obtained are shown in Figure 22. The PSNR values of the decrypted images obtained for Gaussian noise with different variances and means are shown in Table 9. When the effect of Gaussian noise with variance is added, the PSNR values of the decrypted images are greater than 33 dB, the quality of the decrypted images are better and the distortion is not detectable by the naked eye. When the effect of Gaussian noise with variance is added, the PSNR values of the decrypted images are greater than 10 dB, indicating that the decrypted images are already distorted. When the effect of Gaussian noise with variance is added, the PSNR values of the decrypted images are greater than 6.9 dB, which can largely reveal the outline of the images and the general information of the subject, but the encryption algorithm is not as good at resisting Gaussian noise as it is at resisting salt-and-pepper noise.

Figure 22.
Decrypted images with different levels of Gaussian noise added: (a) the Lena decrypted image of Gaussian noise with variance ; (b) the Baboon decrypted image of Gaussian noise with variance ; (c) the Peppers decrypted image of Gaussian noise with variance ; (d) the Lena decrypted image of Gaussian noise with variance ; (e) the Baboon decrypted image of Gaussian noise with variance ; (f) the Peppers decrypted image of Gaussian noise with variance ; (g) the Lena decrypted image of Gaussian noise with variance ; (h) the Baboon decrypted image of Gaussian noise with variance ; (i) the Peppers decrypted image of Gaussian noise with variance .

Table 9.
Adding varying degrees of noise to the PSNR of the decrypted images.
In summary, the increase in the intensity of salt-and-pepper noise and Gaussian noise gradually affects the quality of the decrypted image, but the main features of the image are still recognizable. This indicates that the proposed dynamic encryption scheme can resist the attack of salt-and-pepper noise and Gaussian noise to a certain extent with high robustness.
6.2.6. Geometric Attack
The Lena image is used as an experimental object to verify the resistance of this encryption algorithm to geometric attacks. The most common attack means of geometric attacks is the cropping attack, so the cropping attack is used as an example to decrypt the cipher image that has been missing information blocks with the same and correct key as the encryption process. The encrypted images are cropped uniformly, and the cropping sizes are 0.0976%, 0.391%, 1.56% and 6.25% of the original images, respectively. The resulting cropped encrypted images as well as decrypted images are shown in Figure 23. The main information of the decrypted images can still be recognized, and the recovery of the decrypted images becomes weaker as the clipped area increases. Therefore, the algorithm is resistant to cropping.

Figure 23.
Lena encrypted and decrypted images under cropping attack: (a) Cropping 0.0976% of Lena encrypted image; (b) cropping 0.391% of Lena encrypted image; (c) cropping 1.56% of Lena encrypted image; (d) cropping 6.25% of Lena encrypted image; (e) cropping 0.0976% of Lena decrypted image; (f) cropping 0.391% of Lena decrypted image; (g) cropping 1.56% of Lena decrypted image; (h) cropping 6.25% of Lena decrypted image.
6.2.7. Image Quality Analysis
To test and measure the quality of encrypted and decrypted images, PSNR and Structural Similarity (SSIM) are quantitatively analyzed, in which the higher the value of PSNR, the better the quality of the reconstructed image and the higher the degree of restoration of the image information. The closer the value of SSIM is to one means the more similar the two images are. Lena image, Baboon image and Pepper image are selected and analyzed to calculate the PSNR value and SSIM value of the encrypted and decrypted images, as shown in Table 10. The PSNR values of all three groups of encrypted images are less than 4.1 dB and the SSIM values are less than 0.0094, which indicate that the encrypted images are so different from the original images that the useful information of the original image can not be directly observed and the encryption effect is better. The PSNR values of the three groups of decrypted images are all greater than 33 dB and the SSIM values are greater than 0.9993, indicating that the decrypted images are very similar to the original images, visually close to the plaintext images and the quality of the decrypted images are more satisfactory.

Table 10.
Decrypting PSNR and SSIM of images.
6.2.8. Key Space
This algorithm takes the pixel average of the plaintext image as the initial value of the new chaotic system and also as the key for encryption, and the accuracy of the initial value can reach . Therefore, the size of the key space is . The value is much larger than . It can be regarded that the key space is a secure key space, which is able to resist the exhaustive attack. When any one of the fifteen-bit error keys are changed for decryption, the decrypted image obtained is shown in Figure 24, which shows that the key based on the dynamic parameter encryption scheme has a certain degree of sensitivity.

Figure 24.
Error key decryption diagram.
6.3. Analysis of Application Scenarios
For the current more complex encryption environment, the encryption performance, key management and encryption quality and other requirements are higher, such as military, medical, financial and other fields, which often need to use very strong encryption algorithms. The dynamic encryption algorithm can resist statistical attacks, differential attacks, noise attacks and shear attacks, the ciphertext information of the neighboring pixel points are more uniformly distributed, from which the original plaintext information can not be observed. The image quality is higher and the key space is larger, which can well ensure the confidentiality, integrity and availability of information. Therefore, it can be applied to military, medical, financial and other fields.
Encryption of medical data in healthcare organizations to protect patient privacy and data confidentiality from unauthorized access and leakage, where medical images, medical records, prescriptions, etc., can be stored or transmitted, can be encrypted using this encryption technology. In military institutions where the security of sensitive data such as operational plans, intelligence information, map data, etc., needs to be protected, the encryption scheme can be used by military command, control and intelligence departments to protect the confidentiality of sensitive information against eavesdropping and theft by hostile forces. The encryption technology can help financial institutions protect the confidentiality of large amounts of sensitive customer information and financial data, including personal identification information, account balances, transaction records, etc., against data leakage and illegal access.
7. Summary and Outlook
In this paper, a new five-dimensional memristor chaotic system with rich dynamical behavior is firstly constructed by using a tri-valued memristor. Compared with the previous chaotic systems, the new system improves the complexity and exhibits strong sensitivity to parameter variations, with the existence of not only the periodic limit ring and chaotic attractor depending on the system coupling parameter, but also the variable wing phenomenon depending on the system parameter and the memristor parameter. In addition to this, the system has two different types of transient chaotic phenomena, chaos-periodic and chaos-quasi-periodic depending on the coupling parameter of the system and the memristor parameter. Secondly, the circuits of the new five-dimensional memristor chaotic system are constructed by using the simulation devices in the Simulink platform, which are consistent with the numerical simulation results and verify the correctness of the new system. Finally, a variable parameter color image encryption method is proposed based on this chaotic system, which associates the values of the three component pixel points of the color image with the key according to the principle of one image, one key, to enhance the sensitivity and security of the plaintext and the key. The sequence generated by the parametric dynamic characteristics of the new system is used to encrypt the three color components of the RGB of the color image after chunking by combining additive mode left-shift diffusion and no-repeat disambiguation. DNA encoding and operations are performed on the 2D matrix of the combined color image, and the three channels are finally combined to obtain the encrypted image. In addition, the security analysis of the encrypted image shows that the algorithm can effectively counter the statistical analysis attack, differential attack, noise attack and cropping attack, the information entropy of the encrypted image is close to eight, the correlation coefficient is close to zero, the PSNR values of the decrypted image quality are all greater than 33 dB and the SSIM values are all greater than 0.9990, which verify the security and effectiveness of the algorithm. However, the algorithm is weak against filtering attacks and image compression attacks, and the algorithm will be optimized for these two parts subsequently. In the future, hardware implementations based on this encryption scheme could be considered for implementation in areas such as medical imaging, military encryption and financial data protection.
Author Contributions
L.D. gave some theoretical guidance. P.W. conceived and wrote the paper. All authors have read and agreed to the published version of the manuscript.
Funding
This work is supported by scientific project under Grant NO. HKD202212, the name of the project is the Introduction of High Level Talents Research Initiation Fund Project of Heilongjiang University of Science and Technology. This work is also supported by scientific project under Grant NO. 2023-KYYWF-0537, the name of the project is the High Level Cultivation Project for Basic Research Business Expenses of Provincial Undergraduate Universities in Heilongjiang Province 2023.
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Acknowledgments
The author would like to thank the anonymous reviewers and editors for their comments that improved the quality of this paper.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Yang, Y.; Wang, J. Quantum logistic map image encryption algorithm based on SHA-256 and Arnold map. J. Anhui Univ. Nat. Sci. Ed. 2024, 48, 35–42. [Google Scholar]
- Li, P.; Xia, L.; Fan, Y.; Qian, J. Five-dimensional magnetically controlled memristor chaotic system and its applicationto image encryption. Complex Syst. Complex. Sci. 2024, 1–8. Available online: http://kns.cnki.net/kcms/detail/37.1402.N.20240116.1629.004.html (accessed on 24 April 2024).
- Liu, N. Dynamic Behavior Analysis of Fractional Memristive Chaotic Circuits and Its Application in Power System Image Encryption. Master’s Thesis, Xi’an University of Technology, Xi’an, China, 2024. [Google Scholar] [CrossRef]
- Du, Z. Analysis of the Dynamic Behavior of Amnesia Coupled Systems and Its Applications. Master’s Thesis, Guizhou Universitym, Guiyang, China, 2023. [Google Scholar] [CrossRef]
- Wang, X.; Zhou, P.; Jin, C.; Wang, G.; Lu, H. Mathematic modeling and circuit implementation on multi valued memristor. IEEE Int. Symp. Circuits Syst. (ISCAS) 2020, 1–5. [Google Scholar] [CrossRef]
- Wang, X.; Zhang, X.; Gao, M. A novel voltage-controlled tri-valued memristor and its application in chaotic system. Complexity 2020, 1–8. [Google Scholar] [CrossRef]
- Wang, X.; Tian, Y.; Cheng, Z. Characteristic Analysis of Chaotic System Based on Binary-valued and Tri-valued MemristorModels. J. Electron. Inf. Technol. 2023, 45, 4556–4565. [Google Scholar]
- Yan, M.; Zhu, J. Coexistence of attractors in four-dimensional chaotic system with a wide range of parameters. J. Shenzhen Univ. Sci. Eng. 2024, 41, 108–117. [Google Scholar] [CrossRef]
- Zang, H.; Liu, J.; Li, J. Construction of a Class of High-Dimensional Discrete Chaotic Systems. Mathematics 2021, 9, 365. [Google Scholar] [CrossRef]
- Wormell, C. Non-hyperbolicity at large scales of a high-dimensional chaotic system. Proc. R. Soc. A 2022, 478, 20210808. [Google Scholar] [CrossRef]
- Guo, D.; Bai, C. Synchronization for a Hyper-chaotic Lǔ System and lts Application. Comput. Meas. Control 2022, 30, 103–110. [Google Scholar] [CrossRef]
- Birs, I.; Muresan, C.; Nascu, I.; Ionescu, C. A survey of recent advances in fractional order control for time delay systems. IEEE Access 2019, 7, 30951–30965. [Google Scholar] [CrossRef]
- Fu, Q.; Xu, X.; Chu, W. LQR Chaos Synchronization for a Novel Memristor-Based Hyperchaotic Oscillator. Mathematics 2022, 11, 11. [Google Scholar] [CrossRef]
- Mao, B.; Wang, D. Self-Adaptive Sliding Mode Synchronization of Uncertain Fractional-Order High-DimensionChaotic Systems. Acta Electron. Sin. 2021, 49, 775–780. [Google Scholar]
- Yu, F.; Liu, L.; He, B.; Huang, Y.; Chang, Q.; Cai, S.; Song, Y.; Du, S.; Wan, Q. Analysis and FPGA Realization of a Novel 5D Hyperchaotic Four-Wing Memristive System, Active Control Synchronization, and Secure Communication Application. Complexity 2019, 2019, 4047957. [Google Scholar] [CrossRef]
- Liu, L. Design and FPGA Implementation of Five-Dimensional Hyperchaotic System Based on Emristor. Master’s Thesis, Changsha University of Technology, Changsha, China, 2021. [Google Scholar] [CrossRef]
- Dong, W.; Wang, C.; Zhang, H.; Ma, P. Finite-time Combination-Combination Synchronization of Hyperchaotic Systems with Different Structures and lts Application. J. Syst. Simul. 2023, 35, 1590–1601. [Google Scholar] [CrossRef]
- Du, P.; Cui, Q.; Wang, S.; Dong, Y.; Li, H. Privacy lmage Encryption Algorithm Based on Novel Spatiotemporal Chaotic System. Comput. Eng. 2024, 50, 140–153. [Google Scholar] [CrossRef]
- Yang, F.; Mou, J.; Sun, K.; Cao, Y.; Jin, J. Color Image Compression-Encryption Algorithm Based on Fractional-Order Memristor Chaotic Circuit. IEEE Access 2019, 7, 58751–58763. [Google Scholar] [CrossRef]
- Lai, Q.; Wang, Z.; Kamdem, P. Dynamical analysis, FPGA implementation and synchronization for secure communication of new chaotic system with hidden and coexisting attractors. Mod. Phys. Lett. B 2022, 36, 2150538. [Google Scholar] [CrossRef]
- Yan, M.; Zhang, P. Coexistence analysis and image encryption of chaos-like attractors in conservative systems. J. Lanzhou Univ. Technol. 2023, 49, 102–111. [Google Scholar]
- Wang, S.; Peng, Q.; Du, B. Chaotic color image encryption based on 4D chaotic maps and DNA sequence. Opt. Laser Technol. 2022, 148, 107753. [Google Scholar] [CrossRef]
- Li, J.; Liang, B.; Zhang, X.; Yu, Z. A Conservative Memristive Chaotic System with Extreme Multistability and Its Application in Image Encryption. Entropy 2023, 25, 1656. [Google Scholar] [CrossRef]
- Wang, Y.; Leng, X.; Zhang, C.; Du, B. Adaptive Fast Image Encryption Algorithm Based on Three-Dimensional Chaotic System. Entropy 2023, 25, 1399. [Google Scholar] [CrossRef] [PubMed]
- Yao, W. Research on Extreme ulti-stability ofFour-dimensional Chaotic System with DiscreteBifurcation Diagrams. Master’s Thesis, Harbin Engineering University, Harbin, China, 2022. [Google Scholar] [CrossRef]
- Wang, Q.; Hu, C.; Tian, Z.; Wu, X.; Sang, H.; Cui, Z. A 3D memristor-based chaotic system with transition behaviors of coexisting attractors between equilibrium points. Results Phys. 2024, 56, 107201. [Google Scholar] [CrossRef]
- Yuan, T.; Qu, Q.; Jiang, Q. An Encrypted DNA Encoding Method Based on Chaotic System and Fountain Code. J. Integr. Technol. 2024, 13, 4–24. [Google Scholar]
- Leutcho, G.; Wang, H.; Fozin, T.; Sun, K.; Njitacke, Z.; Kengne, J. Dynamics of a new multistable 4D hyperchaotic Lorenz system and its applications. Int. J. Bifurc. Chaos 2022, 32, 2250001. [Google Scholar] [CrossRef]
- Yan, S.; Song, J.; Sun, X.; Wang, E.; Zhang, Y. A non-autonomous chaotic system and its application in weak signal detection. J. Shenzhen Univ. Sci. Eng. 2023, 40, 227–235. [Google Scholar] [CrossRef]
- Niu, S.; Xue, R.; Ding, C. A color image encryption method based on improved 3D _Henon chaos mapping. Comput. Eng. Sci. 2024, 46, 657–666. [Google Scholar]
- Lei, T.; Zhou, Y.; Fu, H.; Huang, L.; Zang, H. Multistability Dynamics Analysis and Digital Circuit Implementation of Entanglement-Chaos Symmetrical Memristive System. Symmetry 2022, 14, 2586. [Google Scholar] [CrossRef]
- Liu, X.; Liu, J. Five-dimensional Lorentz chaotic system and its circuit implementation. J. Dalian Polytech. Univ. 2024, 41, 220–227. [Google Scholar] [CrossRef]
- Yan, S.; Shi, W.; Song, Z.; Wang, E.; Sun, X.; Huang, Y. A new 3D chaotic circuit design and its synchronous control. Comput. Eng. Sci. 2022, 44, 1409–1417. [Google Scholar]
- Hu, G.; Wang, K.; Liu, L. Detection line spectrum of ship radiated noise based on a new 3D chaotic system. Sensors 2021, 21, 1610. [Google Scholar] [CrossRef]
- Zhang, J.; Hou, J.; Xu, L.; Zhu, X.; Xie, Q. Dynamical analysis, circuit implementation, and simultaneous application of a novel four-dimensional hyperchaotic system based on cosine functions. Microelectron. Eng. 2023, 271, 111939. [Google Scholar] [CrossRef]
- Zhao, H.; Yan, S.; Yu, Q. Simulation experiment of linear state feedback control with hyperchaotic Bao system. J. Mach. Des. 2020, 37, 9–12. [Google Scholar] [CrossRef]
- Ding, L.; Wang, P.; Ma, L.; Wu, Z. Study On Five—Dimensional Chaotic System Based On Flux-controlled Memristor. In Proceedings of the International Conference on Blockchain Technology and Information Security (ICBCTIS), Xi’an, China, 26–28 May 2023; pp. 138–143. [Google Scholar]
- Xie, D.; Chen, F.; Luo, Y.; Li, L. One-to-many image encryption with privacy-preserving homomorphicoutsourced decryptionbased on compressed sensing. Digit. Signal Process. 2019, 95, 102587. [Google Scholar] [CrossRef]
- Ma, C.; Li, G. Color bit-level image encryption algorithm based on L-K double chaotic system. Comput. Appl. Softw. 2020, 37, 321–326. [Google Scholar]
- Ravichandran, D.; Praveenkumar, P.; Balaguru Rayappan, J.; Amirtharajan, R. Chaos based crossover and mutation for securing DICOM image. Comput. Biol. Med. 2016, 72, 170–184. [Google Scholar] [CrossRef] [PubMed]
- Zhang, R.; Yu, L.; Jiang, D.; Ding, W.; Ding, Q. A novel plaintext-related color image encryption scheme based on cellular neural network and Chen’s chaotic system. Symmetry 2021, 13, 393. [Google Scholar] [CrossRef]
- Cheng, G.; Wang, C.; Chen, H. A novel color image encryption algorithm based on hyperchaotic system and permutation-diffusion architecture. Int. J. Bifurc. Chaos 2019, 29, 1950115. [Google Scholar] [CrossRef]
- Mollaeefar, M.; Sharif, A.; Nazari, M. A novel encryption scheme for colored image based on high level chaotic maps. Multimed. Tools Appl. 2017, 76, 607–629. [Google Scholar] [CrossRef]
- Li, N.; Xie, S.; Zhang, J. A color image encryption algorithm based on double fractional order chaotic neural network and convolution operation. Entropy 2022, 24, 933. [Google Scholar] [CrossRef]
- Li, X.; Zeng, J.; Ding, Q.; Fan, C. A novel color image encryption algorithm based on 5-D hyperchaotic system and DNA sequence. Entropy 2022, 24, 1270. [Google Scholar] [CrossRef]
- Wu, Y.; Zeng, J.; Dong, W.; Li, X.; Qin, D.; Ding, Q. A novel color image encryption scheme based on hyperchaos and Hopfield chaotic neural network. Entropy 2022, 24, 1474. [Google Scholar] [CrossRef] [PubMed]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).