Secure Patient Data Transfer Using Information Embedding and Hyperchaos
Abstract
1. Introduction
2. Related Work
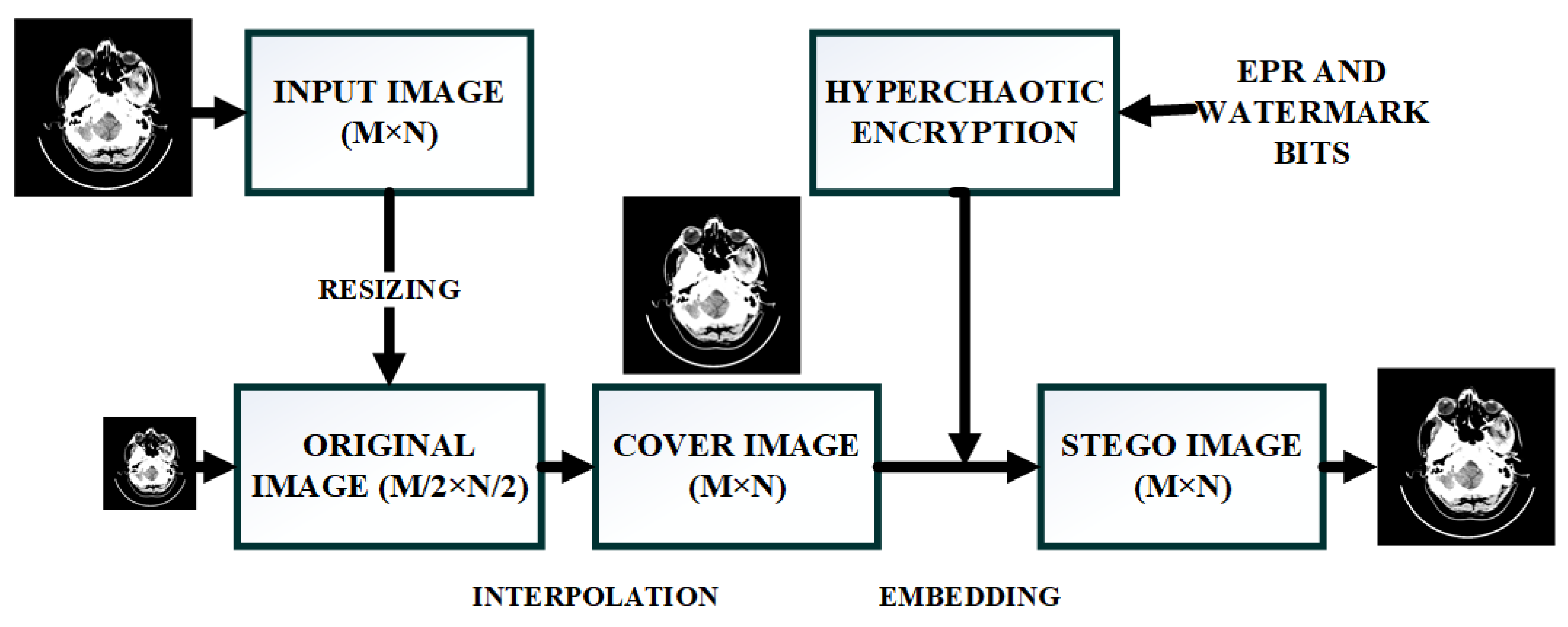
3. Proposed Technique
3.1. Improved IP Scheme
- One-pixel I1(k, l) of the CI is equivalent to I(k, l) of the ORG image (I).
- We calculate the pixel values I1(k, l + 1), I1 (k + 1, l), and I1 (k + 1, l + 1) by making use of Equations (1)–(4).
3.2. Hypechaotic (HC) Encryption
3.3. Data Embedding
| Algorithm 1. Image IP, EHR, and WM Encryption using HC, and LSB embedding of data bits in DCP |
| Input: Grayscale M × N Secret Image, a hyperchaotic map with the initial values and control parameters a, b, e, t, l1, l2, l3. |
| Output: Stego Image (SI) of size M × N |
BEGIN
|
3.4. Data Extraction
| Algorithm 2. CI generation, WM, and EHR data extraction and decryption |
| Input: Stego Image (SI) M × N, keys as initial conditions and control variables |
| Output: Cover Image (CI) of size M × N, WM, EHR |
BEGIN
|
4. Experimental Results
4.1. Imperceptibility Analysis
4.2. Computational Complexity Analysis
4.3. Payload and Reversibility Analysis
4.4. Fragility Analysis for Noise Attacks, Filtering Attacks, and Compression Attacks
4.5. Comparison of Proposed Scheme with Contemporary Methods
4.6. Key-Space and Statistical Analysis
4.7. Encryption Speed
4.8. Histogram Analysis
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Herman, M.; Pentek, T.; Otto, B. Design principles for Industrie 4.0 scenarios. In Proceedings of the 2016 49th Hawaii International Conference on System Sciences (HICSS), Koloa, HI, USA, 5–8 January 2016; pp. 3928–3937. [Google Scholar] [CrossRef]
- Thuemmler, C.; Bai, C. Health 4.0: Application of Industry 4.0: Design Principles in Future Asthma Management. In Health 4.0: How Virtualization and Big Data are Revolutionizing Healthcare; Springer: Cham, Switzerland, 2017; pp. 23–37. [Google Scholar]
- Fatima, I.; Malik, S.U.R.; Anjum, A.; Ahmad, N. Cyber-Physical Systems and IoT: Architectural Practices, Interoperability, and Transformation. IT Prof. 2020, 22, 46–54. [Google Scholar] [CrossRef]
- Kim, N.Y.; Rathore, S.; Ryu, J.H.; Park, J.H. A Survey on Cyber-Physical System Security for IoT: Issues, Challenges, Threats, Solutions. J. Inf. Process. Syst. 2018, 14, 1361–1384. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A Survey of Machine and Deep Learning Methods for Internet of Things (IoT) Security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef]
- Al-Turjman, F.; Alturjman, S. 5G/IoT-enabled UAVs for multimedia delivery in industry-oriented applications. Multimed. Tools Appl. 2020, 79, 8627–8648. [Google Scholar] [CrossRef]
- Mohamed, N.; Al-Jaroodi, J. The Impact of Industry 4.0 on Healthcare System Engineering. In Proceedings of the 2019 IEEE International Systems Conference (SysCon), Orlando, FL, USA, 8–11 April 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Lopes, J.M.; Marrone, P.; Pereira, S.L.; Dias, E.M. Health 4.0: Challenges for an Orderly and Inclusive Innovation. IEEE Technol. Soc. Mag. 2019, 38, 17–19. [Google Scholar] [CrossRef]
- Sudana, D.; Emanuel, A.W.R. How Big Data in Health 4.0 Helps Prevent the Spread of Tuberculosis. In Proceedings of the 2019 2nd International Conference on Bioinformatics, Biotechnology and Biomedical Engineering (BioMIC)-Bioinformatics and Biomedical Engineering, Yogyakarta, Indonesia, 12–13 September 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Sayilgan, E.; İşler, Y. Medical devices sector in medical industry 4.0. In Proceedings of the 2017 Medical Technologies National Congress (TIPTEKNO), Trabzon, Turkey, 12–14 October 2017; pp. 1–4. [Google Scholar] [CrossRef]
- Parah, S.A.; Ahad, F.; Sheikh, J.A.; Bhat, G.M. Hiding clinical information in medical images: A new high capacity and reversible data hiding technique. J. Biomed. Inform. 2017. [Google Scholar] [CrossRef]
- Parah, S.A.; Ahad, F.; Sheikh, J.A.; Bhat, G.M. Reversible and high capacity data hiding technique for E-healthcare applications. Multimed. Tools Appl. 2017, 76, 3943–3975. [Google Scholar] [CrossRef]
- Loan, N.A.; Parah, S.A.; Sheikh, J.A.; Akhoon, J.A.; Bhat, G.M. Hiding Electronic Patient Record (EPR) in medical images: A high capacity and computationally efficient technique for e-health care applications. J. Biomed. Inform. 2017, 73, 125–136. [Google Scholar] [CrossRef]
- Parah, S.A.; Sheikh, J.A.; Akhoon, J.A.; Loan, N.A.; Bhat, G.M. Information hiding in edges: A high capacity information hiding technique using hybrid edge detection. Multimed. Tools Appl. 2017. [Google Scholar] [CrossRef]
- Parah, S.A.; Ahad, F.; Sheikh, J.A.; Loan, N.A.; Bhat, G.M. Information Hiding in Medical Images: A Robust Medical Image Watermarking System for E-Healthcare. Multimed. Tools Appl. 2017, 76, 10599–10633. [Google Scholar] [CrossRef]
- Qiu, H.; Qiu, M.; Memmi, G.; Liu, M. Secure Health Data Sharing for Medical Cyber-Physical Systems for the Healthcare 4.0. IEEE J. Biomed. Health Inform. 2020. [Google Scholar] [CrossRef] [PubMed]
- Jamai, I.; Ben Azzouz, L.; Saïdane, L.A. Security issues in Industry 4.0. In Proceedings of the 2020 International Wireless Communications and Mobile Computing (IWCMC), Limassol, Cyprus, 15–19 June 2020; pp. 481–488. [Google Scholar] [CrossRef]
- Carracedo, J.M.; Milliken, M.; Chouhan, P.K.; Scotney, B.; Lin, Z.; Sajjad, A.; Shackleton, M. Cryptography for Security in IoT. In Proceedings of the 2018 Fifth International Conference on Internet of Things: Systems, Management, and Security, Valencia, Spain, 15–18 October 2018; pp. 23–30. [Google Scholar] [CrossRef]
- Sarmila, K.B.; Manisekaran, S.V. A Study on Security Considerations in IoT Environment and Data Protection Methodologies for Communication in Cloud Computing. In Proceedings of the 2019 International Carnahan Conference on Security Technology (ICCST), Chennai, India, 1–3 October 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Sadhukhan, S.; Singh, M.; Majumder, K.; Chatterjee, S.; Sarkar, S. A Survey on Security on Medical Data and Images in Healthcare. In Proceedings of International Conference on Recent Trends in Machine Learning, IOT Smart Cities and Applications; ICMISC-2020; Springer: Singapore, 2020. [Google Scholar] [CrossRef]
- Sharma, S.; Singh, S. An Analysis of Reversible Data Hiding Algorithms for Encrypted Domain. In Proceedings of the 2019 Third International conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 12–14 December 2019; pp. 644–648. [Google Scholar] [CrossRef]
- Khari, M.; Garg, A.K.; Gandomi, A.H.; Gupta, R.; Patan, R.; Balusamy, B. Securing Data in the Internet of Things (IoT) Using Cryptography and Steganography Techniques. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 73–80. [Google Scholar] [CrossRef]
- Hamza, R.; Yan, Z.; Muhammad, K.; Bellavista, P.; Titouna, F. A privacy-preserving cryptosystem for IOT E-healthcare. Inf. Sci. 2020, 527, 493–510. [Google Scholar] [CrossRef]
- Hamza, R.; Hassan, A.; Patil, A.S. A Lightweight Secure IoT Surveillance Framework Based on DCT-DFRT Algorithms. In Machine Learning for Cyber Security, ML4CS 2019; Chen, X., Huang, X., Zhang, J., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2019; Volume 11806. [Google Scholar] [CrossRef]
- Xuan, G.; Zhu, J.; Chen, J.; Shi, Y.Q.; Ni, Z.; Su, W. Distortion less data hiding based on integer wavelet transform. IEE Electron. Lett. 2002, 38, 1646–1648. [Google Scholar] [CrossRef]
- Celik, M.U.; Sharman, G.; Tekalp, A.M.; Saber, E. Reversible data hiding. In Proceedings of the International Conference on Image Processing, Rochester, NY, USA, 22–25 September 2002; Volume 2, pp. 157–160. [Google Scholar]
- Tian, J. Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. 2003, 13, 890–896. [Google Scholar]
- Al-Qershi, O.M.; Khoo, B.E. High capacity data hiding schemes for medical images based on difference expansion. J. Syst. Softw. 2011, 84, 105–112. [Google Scholar] [CrossRef]
- Tseng, H.W.; Chang, C.C. An extended difference expansion algorithm for reversible watermarking. Image Vis. Comput. 2008, 26, 1148–1153. [Google Scholar] [CrossRef]
- Li, X.; Zhang, W.; Gui, X.; Yang, B. A novel reversible data hiding scheme based on two-dimensional difference-histogram modification. IEEE Trans. Inform. Forensics Secur. 2013, 8, 1091–1100. [Google Scholar]
- Pan, J.S.; Yang, C.N.; Lin, C.C.; Wang, Z.H.; Chang, C.C.; Li, M.L. Multi-dimensional and Multi-level Histogram-Shifting-Imitated Reversible Data Hiding Scheme. Adv. Intell. Syst. Appl. 2013, 2, 149–158. [Google Scholar]
- Tai, W.; Yeh, C.; Chang, C. Reversible data hiding based on histogram modification of pixel differences. IEEE Trans. Circuits Syst. Video Technol. 2009, 19, 906–910. [Google Scholar]
- Vleeschouwer, C.D.; Delaigle, J.F.; Macq, B. Circular interpretation of histogram for reversible watermarking. In Proceedings of the 2001 IEEE Fourth Workshop on Multimedia Signal Processing, Cannes, France, 3–5 October 2001; pp. 345–350. [Google Scholar]
- Ni, Z.; Shi, Y.; Ansari, N.; Su, W. Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 2006, 16, 354–362. [Google Scholar]
- Tsai, P.; Hu, Y.C.; Yeh, H.L. Reversible image hiding scheme using predictive coding and histogram shifting. Signal Process. 2009, 89, 1129–1143. [Google Scholar] [CrossRef]
- Jung, K.; Yoo, K. Data hiding method using image interpolation. Comput. Stand. Interfaces 2009, 31, 465–470. [Google Scholar] [CrossRef]
- Luo, L.; Chen, Z.; Chen, M.; Zeng, X.; Xiong, Z. Reversible image watermarking using interpolation technique. IEEE Trans. Inf. Forensics Secur. 2010, 5, 187–193. [Google Scholar]
- Abadi, M.A.M.; Danyali, H.; Helfroush, M.S. Reversible watermarking based on interpolation error histogram shifting. In Proceedings of the 5th International Symposium on Telecommunications (IST), Kish Island, Iran, 4–6 December 2010; pp. 840–845. [Google Scholar]
- Naheed, T.; Usman, I.; Dar, A. Lossless data hiding using optimized interpolation error expansion. In Proceedings of the 2011 Frontiers of Information Technology, Islamabad, Pakistan, 19–21 December 2011; pp. 281–286. [Google Scholar]
- Lee, C.F.; Huang, Y.L. An efficient image interpolation increasing payload in reversible data hiding. Expert Syst. Appl. 2012, 39, 6712–6719. [Google Scholar] [CrossRef]
- Jie, H.; Tianrui, L. Reversible steganography using extended image interpolation technique. Comput. Electr. Eng. 2015. [Google Scholar] [CrossRef]
- Tang, M.; Jie, H.; Wen, S. A high capacity image steganography using multilayer embedding. Optik 2014, 125, 3972–3976. [Google Scholar] [CrossRef]
- Arsalan, M.; Sana, A.M.; Asifullah, K. Intelli-gent reversible watermarking in integer wavelet domain for medical images. J. Syst. Softw. 2012, 85, 883–894. [Google Scholar] [CrossRef]
- Naheed, T.; Imran, U.; Tariq, M.K.; Amir, H.D.; Muhammad, F.S. Intelligent reversible watermarking technique in medical images using GA and PSO. Optik 2014. [Google Scholar] [CrossRef]
- Wang, X.T.; Chang, C.C.; Nguyen, T.S.; Li, M.C. Reversible data hiding for high-quality images exploiting interpolation and direction order mechanism. Digit Signal Process. 2013, 23, 569–577. [Google Scholar] [CrossRef]
- Wahed, M.A.; Nyeem, H.; Elahi, M.F. An Improved Interpolation based Reversible Data Hiding for Medical Images. In Proceedings of the 2019 International Conference on Electrical, Computer and Communication Engineering (ECCE), Cox’sBazar, Bangladesh, 7–9 February 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Wahed, M.A.; Nyeem, H. Efficient Data Embedding for Interpolation based Reversible Data Hiding Scheme. In Proceedings of the 2017 2nd International Conference on Electrical & Electronic Engineering (ICEEE), Rajshahi, Bangladesh, 27–29 December 2017; pp. 1–4. [Google Scholar] [CrossRef]
- Chang, C.; Nguyen, T.; Liu, Y. A reversible data hiding scheme for image interpolation based on reference matrix. In Proceedings of the 2017 5th International Workshop on Biometrics and Forensics (IWBF), Coventry, UK, 4–5 April 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Mathew, T.; Johnpaul, C.I. Reversible data hiding in encrypted images using interpolation-based distributed space reservation. In Proceedings of the 2017 4th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 6–7 January 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Nazari, M.; Mehrabian, M. A novel chaotic IWT-LSB blind watermarking approach with flexible capacity for secure transmission of authenticated medical images. Multimed. Tools Appl. 2020. [Google Scholar] [CrossRef]
- Hemdan, E.E.D. An efficient and robust watermarking approach based on single value decompression, multi-level DWT, and wavelet fusion with scrambled medical images. Multimed. Tools Appl. 2020. [Google Scholar] [CrossRef]
- Garcia-Guerrero, I.E.E.; Inzunza-Gonzalez, E.; Lopez-Bonilla, O.R.; Cardenas-Valdez, J.R.; Tlelo-Cuautle, E. Randomness improvement of chaotic maps for image encryption in a wireless communication scheme using PIC-microcontroller via zigbee channels. Chaos Solitons Fractals 2020, 133, 109646l. [Google Scholar] [CrossRef]
- Malik, M.G.A.; Bashir, Z.; Iqbal, N.; Imtiaz, M.A. Color Image Encryption Algorithm Based on Hyper-Chaos and DNA Computing. IEEE Access 2020, 8, 88093–88107. [Google Scholar] [CrossRef]
- Ergün, S. Security analysis of a chaos-based image encryption scheme. In Proceedings of the 2018 19th IEEE Mediterranean Electrotechnical Conference (MELECON), Marrakech, Morocco, 2–7 May 2018; pp. 58–61. [Google Scholar] [CrossRef]
- Suneja, K.; Dua, S.; Dua, M. A Review of Chaos-based Image Encryption. In Proceedings of the 2019 3rd International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 27–29 March 2019; pp. 693–698. [Google Scholar] [CrossRef]
- Li, A.R.; Liu, Q.; Liu, L. Novel image encryption algorithm based on improved logistic map. IET Image Process. 2019, 13, 125–134. [Google Scholar] [CrossRef]
- Wang, H.; Xiao, D.; Chen, X.; Huang, H. Cryptanalysis and enhancements of image encryption using combination of the 1D chaotic map. Signal Process. 2018, 144, 444–452. [Google Scholar] [CrossRef]
- Chen, J.; Chen, L.; Zhang, L.Y.; Zhu, Z.L. Medical image cipher using hierarchical diffusion and non-sequential encryption. Nonlinear Dyn. 2019, 96, 301–322. [Google Scholar] [CrossRef]
- Hanis, S.; Amutha, R. A fast double-keyed authenticated image encryption scheme using an improved chaotic map and a butter y-like structure. Nonlinear Dyn. 2019, 95, 421–432. [Google Scholar] [CrossRef]
- Zhu, H.; Zhao, Y.; Song, Y. 2D Logistic-modulated-sine-coupling-Logistic chaotic map for image encryption. IEEE Access 2019, 7, 14081–14098. [Google Scholar] [CrossRef]
- Ping, P.; Wu, J.; Mao, Y.; Xu, F.; Fan, J. Design of image cipher using life-like cellular automata and chaotic map. Signal Process. 2018, 150, 233–247. [Google Scholar] [CrossRef]
- Luo, Y.; Zhou, R.; Liu, J.; Qiu, S.; Cao, Y. An efficient and self-adapting colour-image encryption algorithm based on chaos and interactions among multiple layers. Multimed. Tools Appl. 2018, 77, 26191–26217. [Google Scholar] [CrossRef]
- Wang, X.; Zhu, X.; Zhang, Y. An image encryption algorithm based on Josephus traversing and mixed chaotic map. IEEE Access 2018, 6, 23733–23746. [Google Scholar] [CrossRef]
- Wu, J.; Liao, X.; Yang, B. Cryptanalysis and enhancements of image encryption based on three-dimensional bit matrix permutation. Signal Process. 2018, 142, 292–300. [Google Scholar] [CrossRef]
- Jia, H.; Ren, H.; Bai, C.; Li, J. Hyper-chaos encryption application in intelligent home system. In Proceedings of the International Conference On Smart Technologies for Smart Nation (Smart Tech Con), Bangalore, India, 17–19 August 2017; pp. 1004–1009. [Google Scholar] [CrossRef]
- Zhan, K.; Wei, D.; Shi, J.; Yu, J. Cross-utilizing hyperchaotic and DNA sequences for image encryption. J. Electron. Imaging 2017, 26, 013021. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, L.; Wang, Y.; Niu, Y.; Li, Y. An Image Encryption Algorithm Based on Hyperchaotic System and Variable-Step Josephus Problem. Int. J. Opt. 2020. [Google Scholar] [CrossRef]
- Tong, X.; Liu, Y.; Zhang, M.; Xu, H.; Wang, Z. An Image Encryption Scheme Based on Hyperchaotic Rabinovich and Exponential Chaos Maps. Entropy 2015, 17, 181–196. [Google Scholar] [CrossRef]







| MI | PSNR1 (dB) | SSIM1 |
|---|---|---|
| MI-A | 37.4057 | 0.9683 |
| MI-B | 45.2522 | 0.9913 |
| MI-C | 42.3601 | 0.9890 |
| MI-D | 41.4221 | 0.9831 |
| MI-E | 22.2075 | 0.8986 |
| MI-F | 26.5480 | 0.9114 |
| MI-G | 21.7612 | 0.8765 |
| MI-H | 25.0632 | 0.9560 |
| MI-I | 21.6530 | 0.8302 |
| MI-K | 32.9281 | 0.9479 |
| MI-L | 30.4135 | 0.8690 |
| MI-M | 24.4164 | 0.6996 |
| MI-N | 29.2605 | 0.9162 |
| MI-J | 27.5035 | 0.9371 |
| Images | NM1 [36] | INP [40] | Proposed |
|---|---|---|---|
| MI A | 0.0781 | 0.0625 | 0.0625 |
| MI B | 0.0625 | 0.0781 | 0.0625 |
| MI C | 0.625 | 0.0938 | 0.0625 |
| MI D | 0.0781 | 0.0983 | 0.0625 |
| MI E | 0.0938 | 0.0625 | 0.0625 |
| MI F | 0.0938 | 0.0625 | 0.0625 |
| MI G | 0.0781 | 0.0625 | 0.0625 |
| MI H | 0.0938 | 0.0625 | 0.0625 |
| MI I | 0.0938 | 0.0625 | 0.0625 |
| MI J | 0.0781 | 0.0625 | 0.0625 |
| MI-K | 0.0781 | 0.0625 | 0.0625 |
| MI-M | 0.0938 | 0.0625 | 0.0625 |
| MI-L | 0.0781 | 0.0625 | 0.0625 |
| MI-N | 0.0781 | 0.0938 | 0.0781 |
| Images | PSNR2 (dB) | SSIM2 |
|---|---|---|
| MI A | 52.4042 | 0.9953 |
| MI B | 52.3788 | 0.9948 |
| MI C | 52.3882 | 0.9953 |
| MI D | 52.3928 | 0.9967 |
| MI E | 52.3911 | 0.9836 |
| MI F | 52.1761 | 0.9002 |
| MI G | 52.3696 | 0.9844 |
| MI H | 52.3920 | 0.9827 |
| MI I | 52.3967 | 0.9858 |
| MI J | 52.3902 | 0.9833 |
| MI-K | 52.4063 | 0.9967 |
| MI-M | 52.3835 | 0.9964 |
| MI-L | 52.4021 | 0.9980 |
| MI-N | 52.3875 | 0.9964 |
| Average | 52.3756 | 0.9849 |
| Effect of Salt and Pepper Noise on the Extracted Watermark for Authentication | Effect of Gaussian Noise (0.001) on the Extracted Watermark for Authentication | |||||
|---|---|---|---|---|---|---|
| Attacked Image |  |  |  |  |  |  |
| Extracted Logo |  |  |  |  |  |  |
| Attacked Image |  |  |  |  |  |  |
| Extracted Logo |  |  |  |  |  |  |
| Effect of Median Filtering on the extracted Watermark for Authentication | Effect of jpeg 50 compression on the extracted Watermark for Authentication | |||||
| Attacked Image |  |  |  |  |  |  |
| Extracted Logo |  |  |  |  |  |  |
| Attacked Image |  |  |  |  |  |  |
| Extracted Logo |  |  |  |  |  |  |
| Stego-Images | Salt and Peppers (0.01) | Gaussian Noise (0.0001) | MF | JPEG 50 |
|---|---|---|---|---|
| MI-A | 0.9939 | 0.5022 | 0.6018 | 0.4970 |
| MI-B | 0.9952 | 0.4975 | 0.5911 | 0.4995 |
| MI-C | 0.9943 | 0.5052 | 0.5870 | 0.5005 |
| MI-D | 0.9952 | 0.5032 | 0.6221 | 0.5024 |
| MI-K | 0.9960 | 0.5094 | 0.5957 | 0.5059 |
| MI-M | 0.9952 | 0.4930 | 0.5980 | 0.5092 |
| Image | Methods | EC (bits) | PSNR (dB) | BPP | SSIM |
|---|---|---|---|---|---|
| MI-A | [25] | 14,614 | 48.1437 | 0.1282 | 0.9980 |
| [27] | 12,217 | 41.1985 | 0.1082 | 0.9905 | |
| [37] | 36,060 | 48.9464 | 0.3194 | 0.9985 | |
| [39] | 38,700 | 49.0119 | 0.3427 | 0.9985 | |
| [40] | 10,882 | 48.4208 | 0.0963 | 0.9988 | |
| [44] | 38,390 | 49.0047 | 0.3400 | 0.9985 | |
| Proposed | 196,608 | 52.3866 | 0.75 | 0.9951 | |
| MI-B | [25] | 14,614 | 48.1437 | 0.1282 | 0.9980 |
| [27] | 12,217 | 41.1985 | 0.1082 | 0.9905 | |
| [37] | 36,060 | 48.9464 | 0.3194 | 0.9985 | |
| [39] | 38,700 | 49.0119 | 0.3427 | 0.9985 | |
| [40] | 10,882 | 48.4208 | 0.0963 | 0.9988 | |
| [44] | 38,390 | 49.0047 | 0.3400 | 0.9985 | |
| Proposed | 196,608 | 52.3859 | 0.75 | 0.9949 | |
| MI-C | [25] | 14,614 | 48.1437 | 0.1282 | 0.9980 |
| [27] | 12,217 | 41.1985 | 0.1082 | 0.990596 | |
| [37] | 36,060 | 48.9464 | 0.3194 | 0.9985 | |
| [40] | 10,882 | 48.4208 | 0.0963 | 0.9988 | |
| [39] | 38,700 | 49.0119 | 0.3427 | 0.9985 | |
| [44] | 38,390 | 49.0047 | 0.3400 | 0.9985 | |
| Proposed | 196,608 | 52.3865 | 0.75 | 0.9953 | |
| MI-D | [25] | 14,614 | 48.1437 | 0.1282 | 0.9980 |
| [27] | 12,217 | 41.1985 | 0.1082 | 0.9905 | |
| [37] | 36,060 | 48.9464 | 0.3194 | 0.9985 | |
| [39] | 38,700 | 49.0119 | 0.3427 | 0.9985 | |
| [40] | 10,882 | 48.4208 | 0.0963 | 0.9988 | |
| [44] | 38,390 | 49.0047 | 0.3400 | 0.9985 | |
| Proposed | 196,608 | 52.3857 | 0.75 | 0.9968 |
| Technique | MI-K | MI-M | ||
|---|---|---|---|---|
| EC (bits) | PSNR (dB) | EC (bits) | PSNR (dB) | |
| [24] | 24,108 | 39.0 | 2905 | 39.0 |
| [25] | 85,507 | 36.60 | 14,916 | 32.80 |
| [26] | 74,600 | 38.00 | 15,176 | 38.00 |
| [28] | <287,160 | 35.3729 | <139,490 | 38.9982 |
| [33] | 1024 | 30.0 | 1024 | 29.0 |
| [34] | 5460 | 48.20 | 5421 | 48.20 |
| [36] | 200,868 | 41.20 | 425,199 | 35.46 |
| [37] | 71,609 | 48.842 | 22,709 | 48.505 |
| [39] | 73,231 | 48.858 | 23,598 | 48.553 |
| [44] | 73,206 | 48.868 | 23,374 | 48.551 |
| [45] | <71,200 | 48.6747 | <24,965 | 48.9441 |
| Proposed | 196,608 | 52.3941 | 196,608 | 52.4021 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aljuaid, H.; Parah, S.A. Secure Patient Data Transfer Using Information Embedding and Hyperchaos. Sensors 2021, 21, 282. https://doi.org/10.3390/s21010282
Aljuaid H, Parah SA. Secure Patient Data Transfer Using Information Embedding and Hyperchaos. Sensors. 2021; 21(1):282. https://doi.org/10.3390/s21010282
Chicago/Turabian StyleAljuaid, Hanan, and Shabir A. Parah. 2021. "Secure Patient Data Transfer Using Information Embedding and Hyperchaos" Sensors 21, no. 1: 282. https://doi.org/10.3390/s21010282
APA StyleAljuaid, H., & Parah, S. A. (2021). Secure Patient Data Transfer Using Information Embedding and Hyperchaos. Sensors, 21(1), 282. https://doi.org/10.3390/s21010282




