Cross Deep Learning Method for Effectively Detecting the Propagation of IoT Botnet
Abstract
:1. Introduction
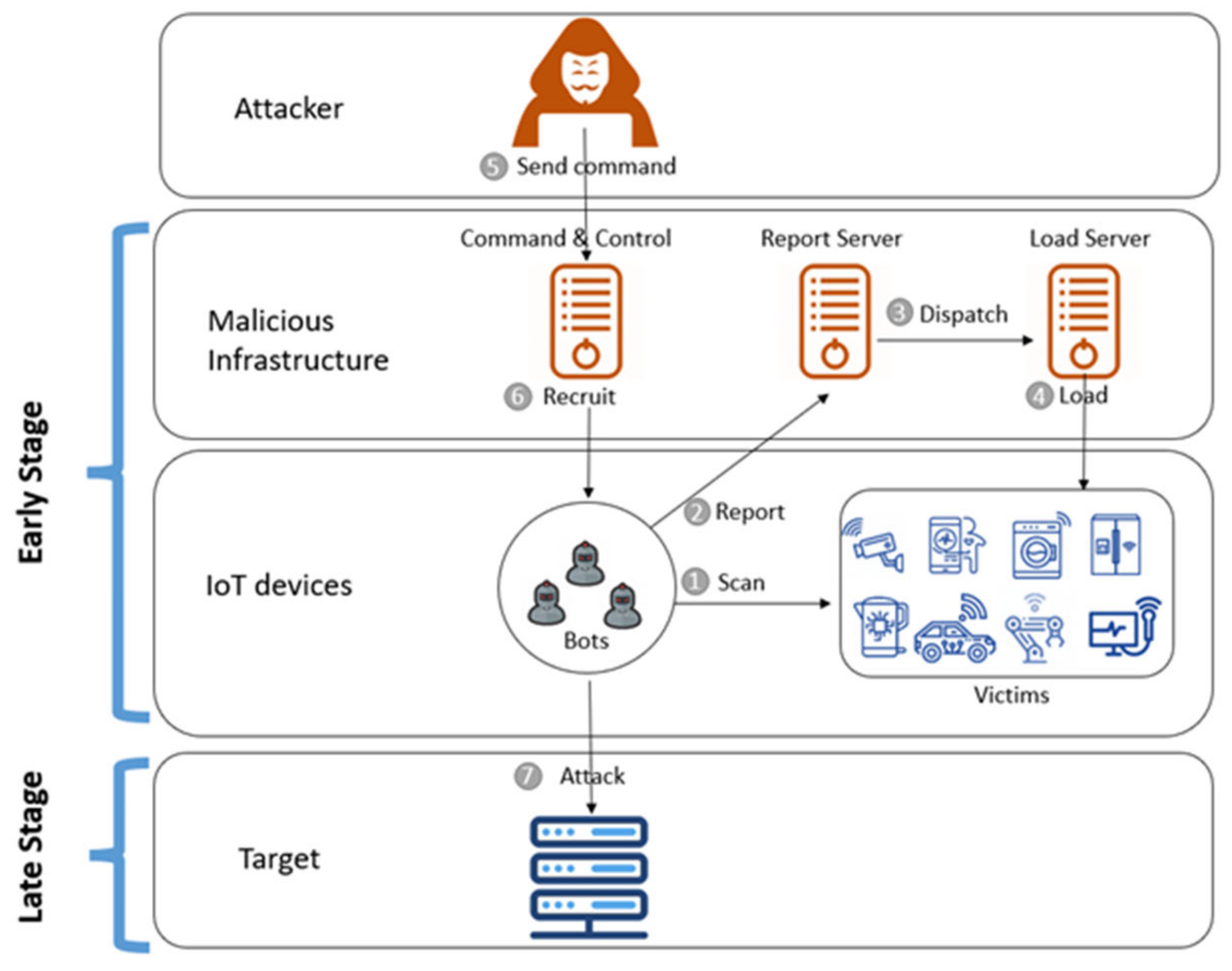
- Early stage: In this stage, the attacker aims to weaponise IoT by scanning for new vulnerable IoT devices, such as devices with weak credentials or known vulnerabilities, which then download the bot, thereby exploiting these devices. Furthermore, the bot makes the necessary communication with the botmaster waiting for the attack command. At the same time, the bot scans for new vulnerable devices to be exploited with the aim to expand the botnet as much as possible.
- Late stage: In this stage, the attacker triggers a command to launch the attack by using the IoT botnet.
1.1. The Need to Detect IoT Botnet in Early Stage
1.2. Research Questions
1.3. Contribution
- A technical experiment was conducted to investigate how IoT malware behaves and how it forms the IoT botnet.
- The Cross CNN_LSTM model was used to detect the IoT botnet in the early stage.
- A comparison of the evaluation of traditional ML classifiers with the proposed method was conducted.
- IoT botnet detection employing binary and multi-decision classes was implemented.
- The proposed methodology’s evaluation was compared with that of previous DL models and other baseline research.
- The proposed model significantly improved the IoT botnet detection ability.
- The proposed kill chain model focuses on detecting IoT botnets in the early stage.
2. Literature Review
3. Materials and Methods
3.1. A Prototype for Analysis of IoT Botnet Propagation
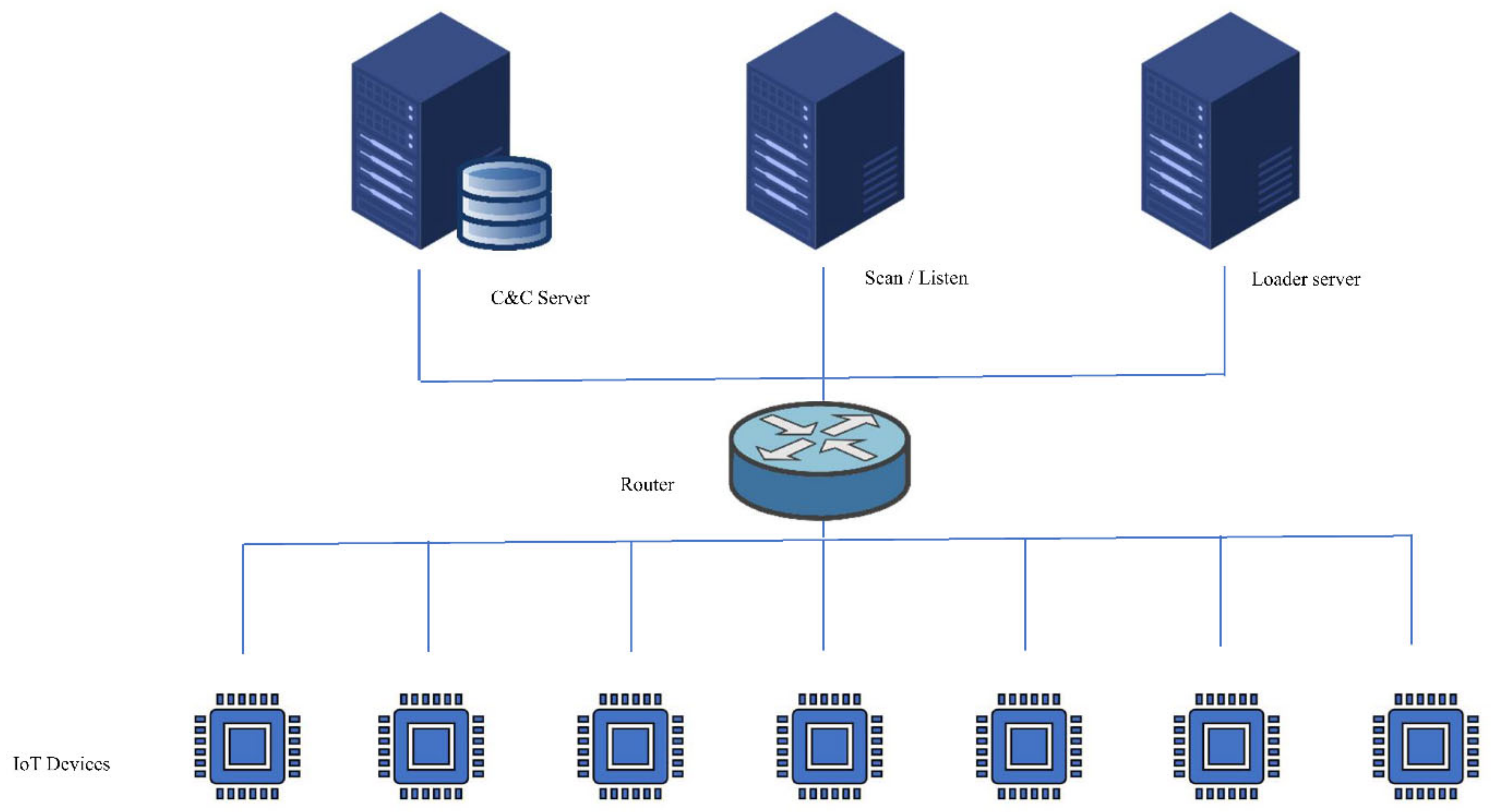
3.1.1. Testbed Environment
3.1.2. Testbed Components
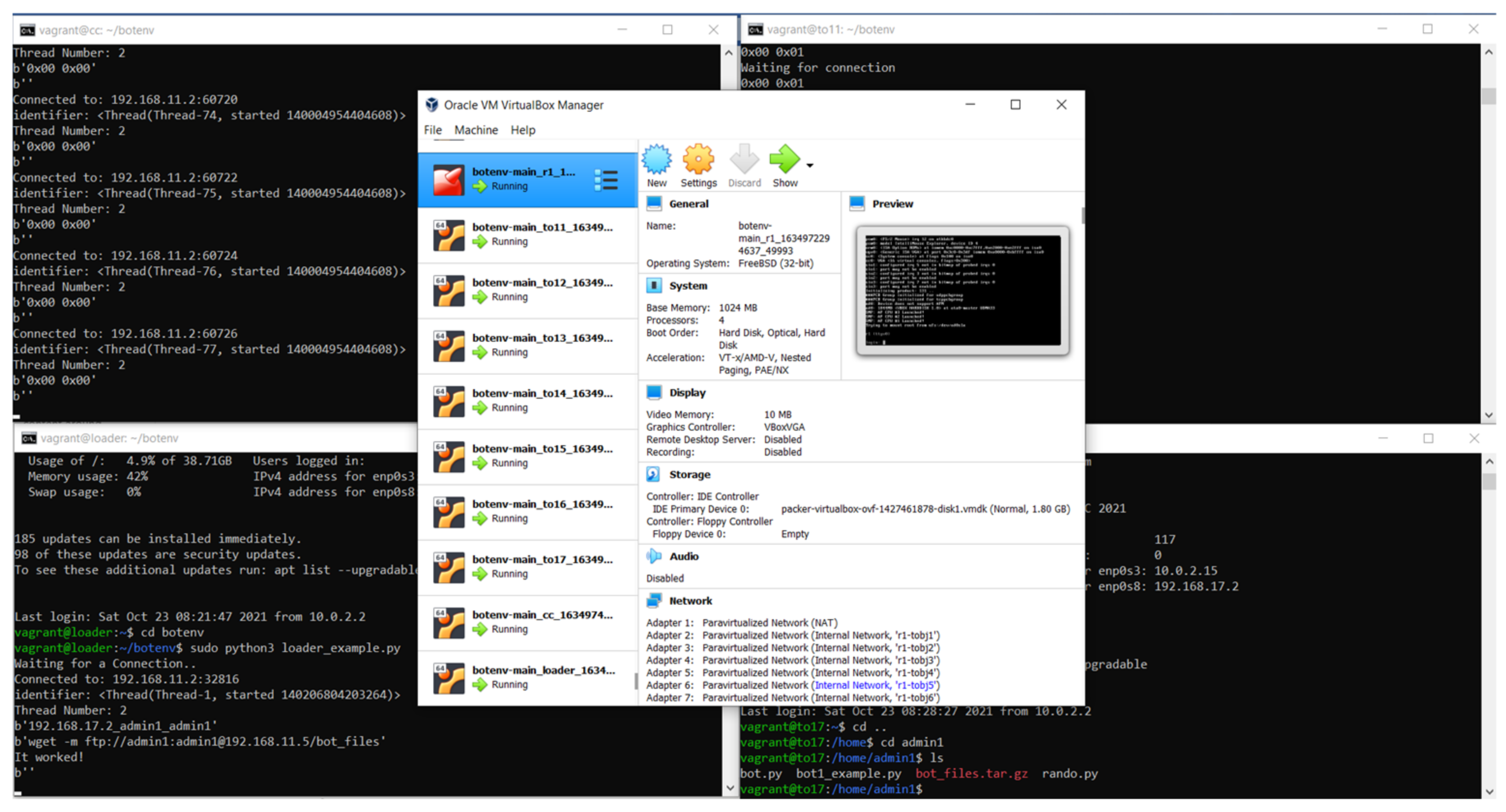
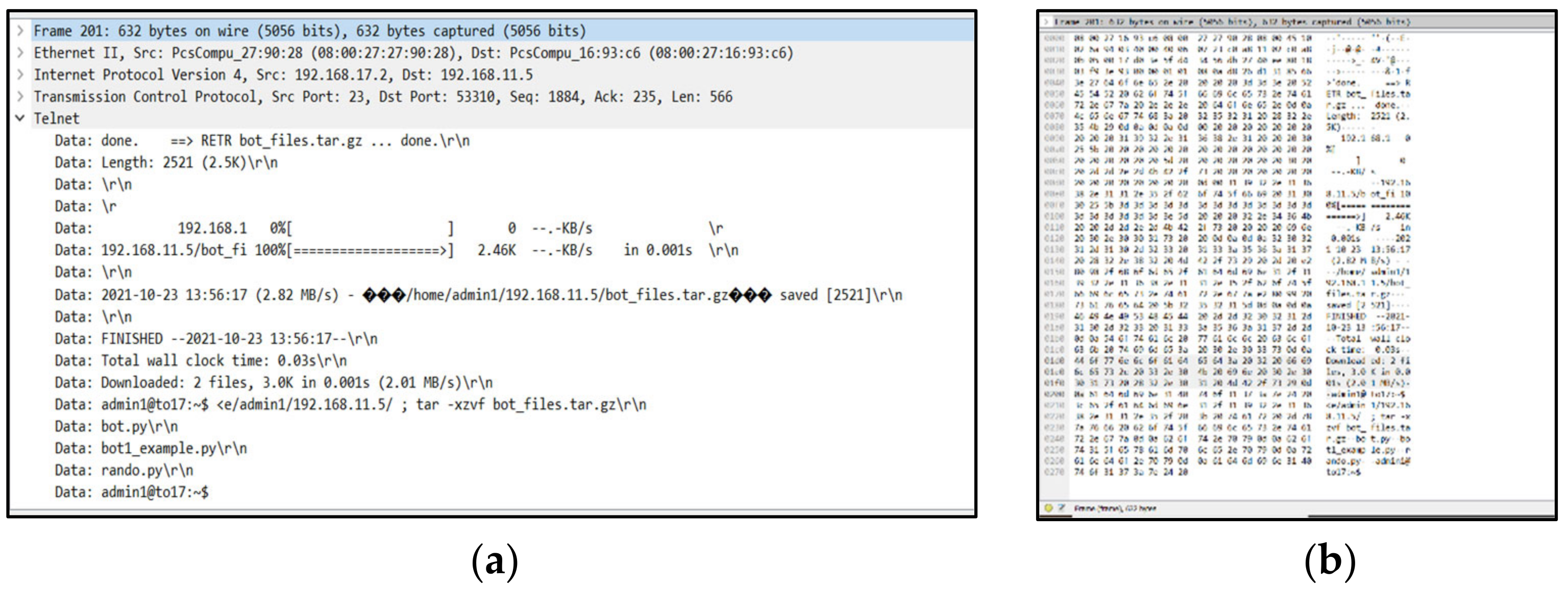
3.1.3. The Experiment
3.2. The Proposed Model
3.2.1. Dataset Selection
- The dataset should be generated using different types of IoT devices.
- More than one IoT malware should be used.
- A real IoT botnet binary code should be used to formulate the botnet.
- The dataset should focus on the early stages of deploying the IoT botnet, as explained in this section.
3.2.2. Feature Extraction
3.2.3. Dataset Sampling
3.2.4. Dataset Preprocessing
3.2.5. Implementation of Baseline Machine Learning Models
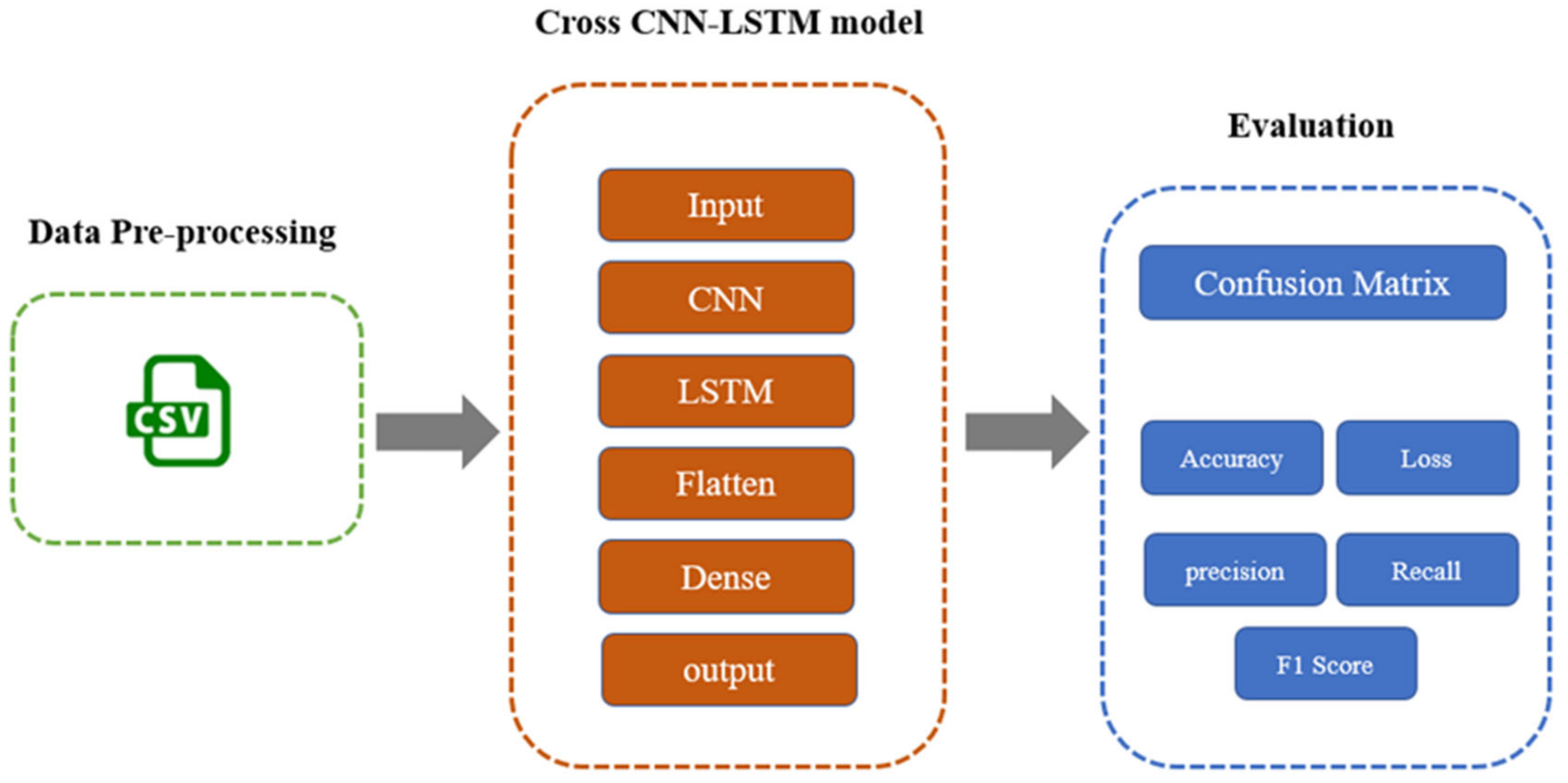
3.2.6. Architecture Design of the Proposed Model
| Algorithm 1 Algorithm for the proposed model |
| Input: Preprocessed data |
| Output: Accuracy, loss, precision, recall, F1-score |
| 1: Standardise (Preprocessed_data) |
| 2: Shuffle (Preprocessed_data)) |
| 3: Split (Preprocessed_data) based on 70:10:20 (training_data, validating_data, test_data) |
| 4: Apply CNN layer |
| 5: Apply LSTM layer |
| 6: Flatten |
| 7: Apply Dense |
| 8: Use Adam optimiser |
| 9: Use a categorical cross-entropy as loss function |
| 10: for (epoch = 1; epoch < 50; epoch++) do |
| 11: evaluate loss, validation loss |
| 12: evaluate accuracy, validation accuracy |
| 13: end for |
| 14: Use testing data to calculate precision, recall, F1-score |
| 15: Calculate loss, accuracy |
3.2.7. Experimental Setup
4. Results and Discussion
4.1. Experimental Results
- True Positive (TP): where the proposed model correctly predicts the positive class;
- True Negative (TN): where the proposed model correctly predicts the negative class;
- False Positive (FP): where the proposed model incorrectly predicts the positive class;
- False Negative (FN): where the proposed model incorrectly predicts the negative class.
- Precision: the proportion of the true positive to all positive:
- Recall: the proportion of the true positive to all relevant elements:
- F1-Score: a combination of precision and recall:
F1 = TP/TP + 1/2 (FP + FN)
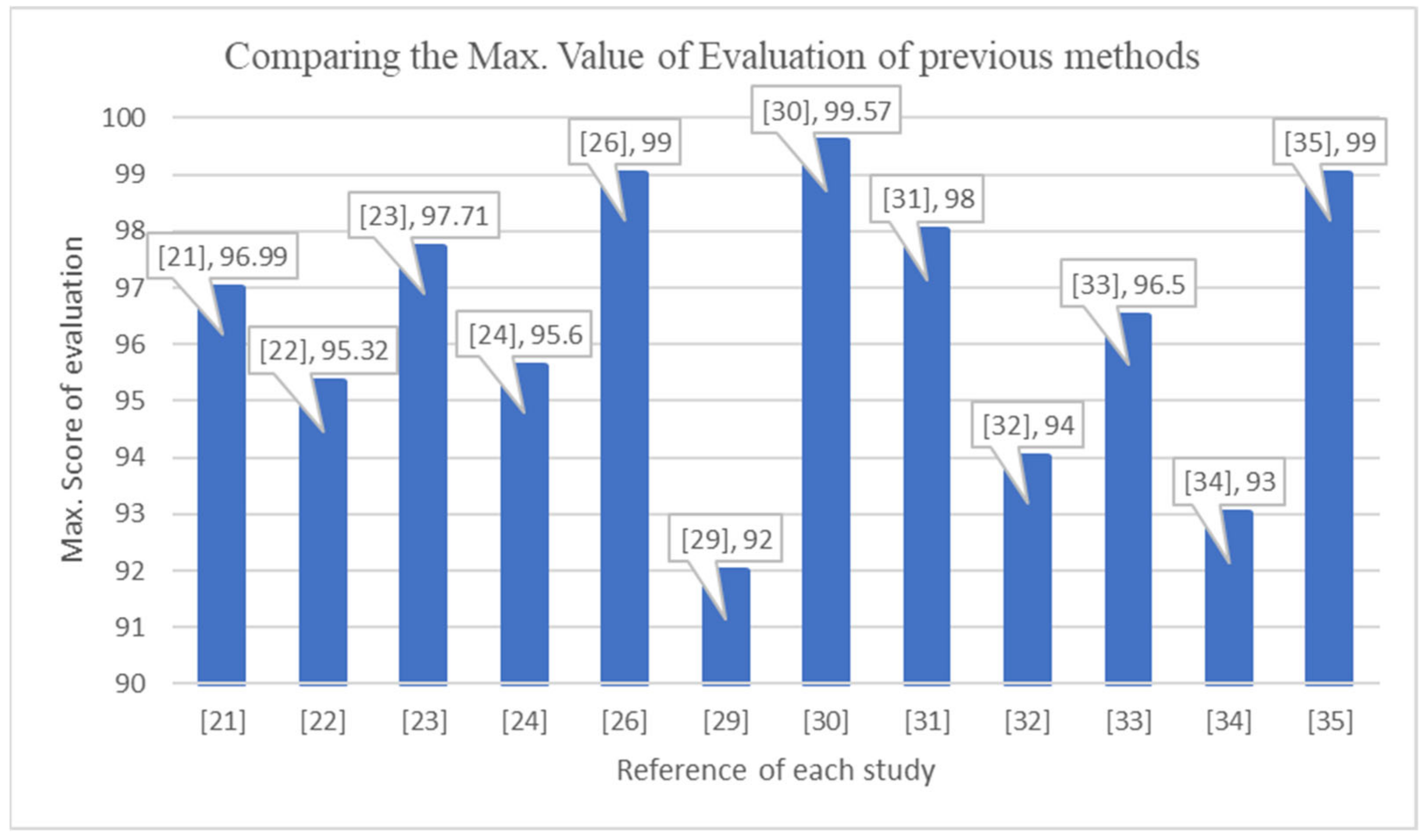
4.2. Comparison against State-of-the-Art
4.3. Discussion
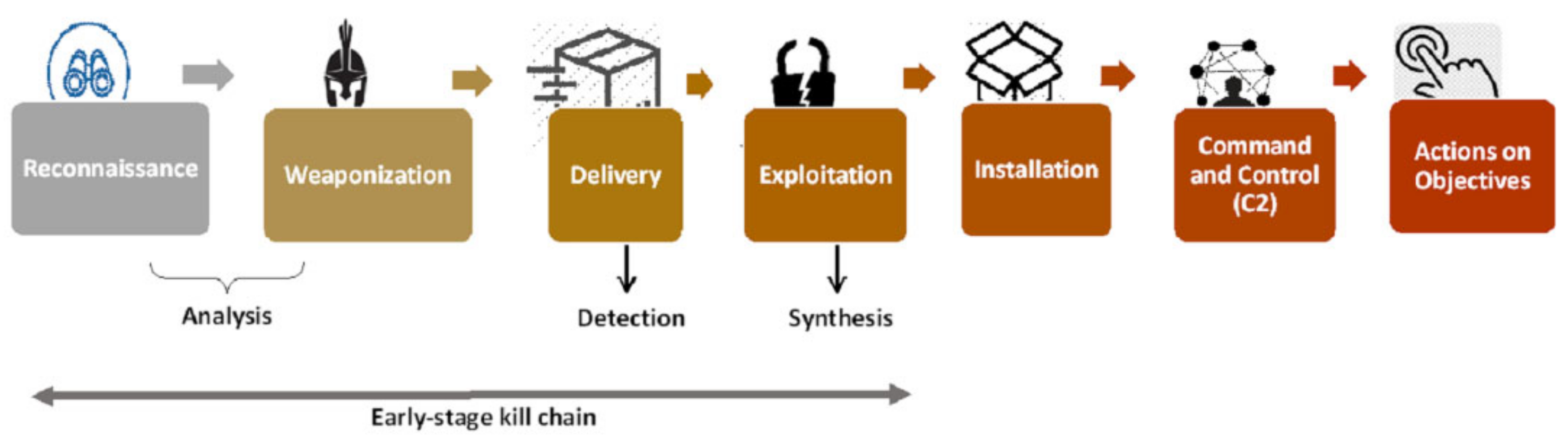
5. IoT Botnet Kill Chain Model
- Reconnaissance;
- Weaponisation;
- Delivery;
- Exploitation;
- Installation;
- Command and Control (C&C);
- Actions on Objectives.
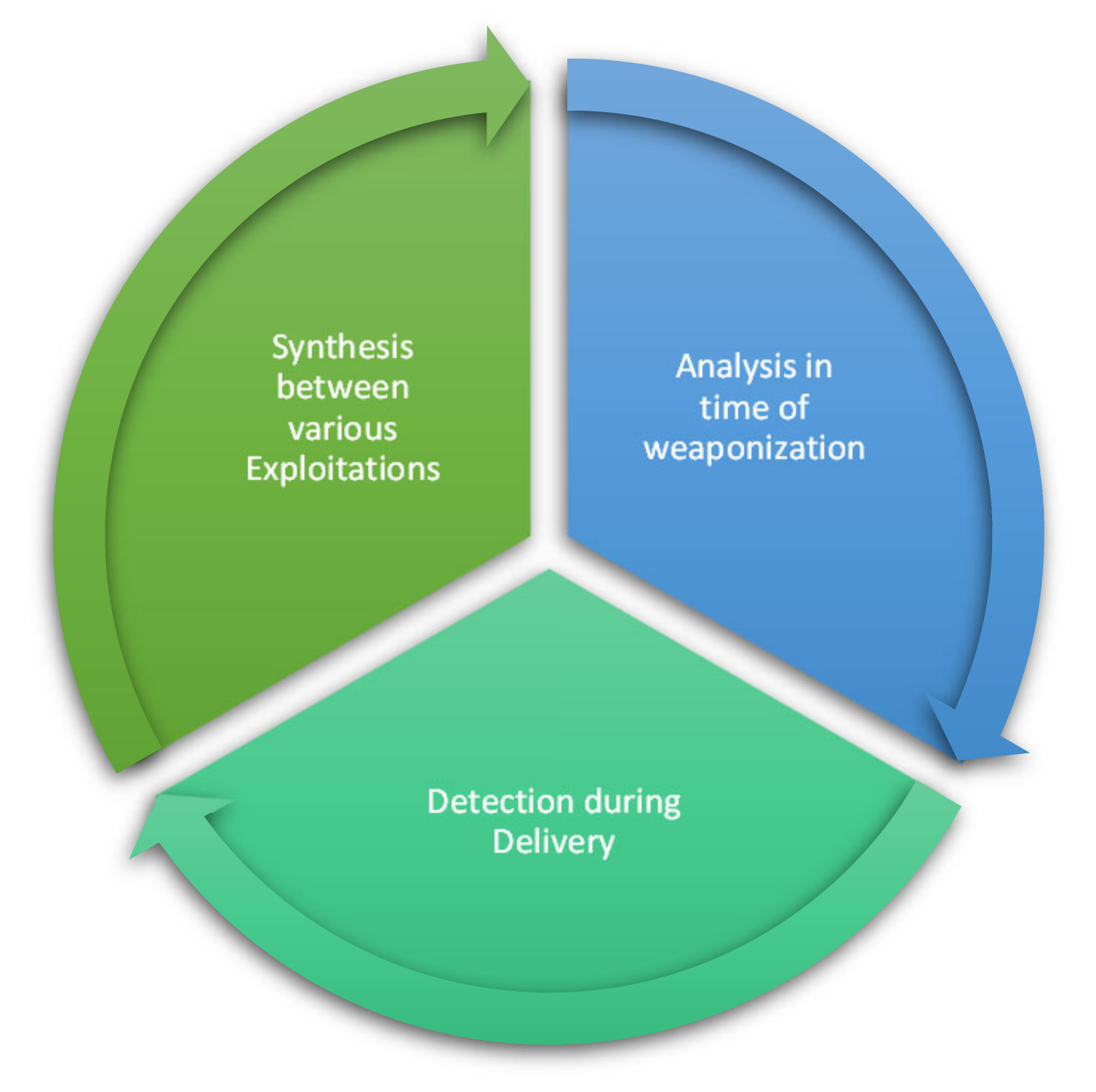
- Analysis at time of weaponisation;
- Detection during delivery;
- Synthesis between various exploitations.
- Analysis at time of weaponisation: This countermeasure can be covered by different techniques. The traffic should be analysed, and the investigation should be conducted to find any scanning activities. Scans can be performed manually or automatically to detect any activities of gathering host information and communications to send to C&C or any brute-forcing, remote access, system restarts, loss of credentials, or other failures.
- Detection during delivery: This countermeasure can be implemented by investigating the existence of any malicious binaries that can be downloaded on IoT devices and removing them periodically.
- Synthesis between various exploitations: All unsuccessful attempts to brute force credentials and any downloaded file attempts should be taken into consideration because the attacker may repeat these attempts through the network and execute successful attempts.
6. Limitations of the Study
- In the developed prototype, we could not use physical IoT devices, so we implemented a virtual environment, and we repeated the experiment many times with different changes for a better understanding of the IoT botnet behaviour. This is because the cost would have been too high if we used real physical IoT devices since repeating the experiment may require replacing the affected device with a new one every time that we repeat the experiment.
- Deep learning does not have a technique to randomly subsample the output and decrease the capacity or diminish the network during the training phase, so the model does not have an implanted technique to prevent overfitting that may occur when training the model.
7. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Hampshire. IoT Connections to Reach 83 Billion by 2024, Driven by Maturing Industrial Use Cases. 2022. Available online: https://www.juniperresearch.com/press/iot-connections-to-reach-83-bn-by-2024 (accessed on 7 April 2022).
- Beltrán-García, P.; Aguirre-Anaya, E.; Escamilla-Ambrosio, P.J.; Acosta-Bermejo, R. IoT botnets. In Communications in Computer and Information Science; Springer Science and Business Media LLC.: Berlin, Germany, 2019; pp. 247–257. [Google Scholar]
- Alzahrani, H.; Abulkhair, M.; Alkayal, E. A multi-class neural network model for rapid detection of IoT botnet attacks. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 688–696. [Google Scholar] [CrossRef]
- Bertino, E.; Islam, N. Botnets and internet of things security. Computer 2017, 50, 76–79. [Google Scholar] [CrossRef]
- TrendMicro. Into the Battlefield: A Security Guide to IoT Botnets. 2019. Available online: https://www.trendmicro.com/vinfo/us/security/news/internet-of-things/into-the-battlefield-a-security-guide-to-iot-botnets (accessed on 5 March 2021).
- Costin, A.; Zaddach, J. Iot malware: Comprehensive survey, analysis framework and case studies. In Proceedings of the BlackHat, Las Vegas, NV, USA, 3–6 December 2018. [Google Scholar]
- Holmes, D.; Shattuck, J. Reaper: The Professional Bot Herder’s Thingbot. 2017. Available online: https://www.f5.com/labs/articles/threat-intelligence/reaper-the-professional-bot-herders-thingbo (accessed on 7 April 2022).
- Vishwakarma, R.; Jain, A.K. A survey of DDoS attacking techniques and defence mechanisms in the IoT network. Telecommun. Syst. 2020, 73, 3–25. [Google Scholar] [CrossRef]
- CSDE. International Botnet and Iot Security Guide 2020. 2019. Available online: https://securingdigitaleconomy.org/wp-content/uploads/2019/11/CSDE_Botnet-Report_2020_FINAL.pdf (accessed on 7 April 2022).
- Wazzan, M.; Algazzawi, D.; Bamasaq, O.; Albeshri, A.; Cheng, L. Internet of Things botnet detection approaches: Analysis and recommendations for future research. Appl. Sci. 2021, 11, 5713. [Google Scholar] [CrossRef]
- Sarker, I.H. Deep cybersecurity: A comprehensive overview from neural network and deep learning perspective. SN Comput. Sci. 2021, 2, 154. [Google Scholar] [CrossRef]
- Li, Y.; Xu, Y.; Liu, Z.; Hou, H.; Zheng, Y.; Xin, Y.; Zhao, Y.; Cui, L. Robust detection for network intrusion of industrial IoT based on multi-CNN fusion. Measurement 2019, 154, 107450. [Google Scholar] [CrossRef]
- Rezende, E.; Ruppert, G.; Carvalho, T.; Ramos, F.; de Geus, P. Malicious software classification using transfer learning of resnet-50 deep neural network. In Proceedings of the 2017 16th IEEE International Conference on Machine Learning and Applications (ICMLA), Cancun, Mexico, 18–21 December 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1011–1014. [Google Scholar]
- Parra, G.D.L.T.; Rad, P.; Choo, K.-K.R.; Beebe, N. Detecting Internet of Things attacks using distributed deep learning. J. Netw. Comput. Appl. 2020, 163, 102662. [Google Scholar] [CrossRef]
- Karbab, E.B.; Debbabi, M.; Derhab, A.; Mouheb, D. MalDozer: Automatic framework for android malware detection using deep learning. Digit. Investig. 2018, 24, S48–S59. [Google Scholar] [CrossRef]
- Sarker, I.H.; Abushark, Y.B.; Alsolami, F.; Khan, A.I. Intrudtree: A machine learning based cyber security intrusion detection model. Symmetry 2020, 12, 754. [Google Scholar] [CrossRef]
- Abuhamad, M.; Abuhmed, T.; Mohaisen, D.; Nyang, D.H. AUToSen: Deep-learning-based implicit continuous authentication using smartphone sensors. IEEE Internet Things J. 2020, 7, 5008–5020. [Google Scholar] [CrossRef]
- Vu, S.N.T.; Stege, M.; El-Habr, P.I.; Bang, J.; Dragoni, N. A survey on botnets: Incentives, evolution, detection and current trends. Future Internet 2021, 13, 198. [Google Scholar]
- Stephens, B.; Shaghaghi, A.; Doss, R.; Kanhere, S.S. Detecting Internet of Things Bots: A Comparative Study. IEEE Access 2021, 9, 160391–160401. [Google Scholar] [CrossRef]
- Alghazzawi, D.; Bamasag, O.; Ullah, H.; Asghar, M.Z. Efficient detection of DDoS attacks using a hybrid deep learning model with improved feature selection. Appl. Sci. 2021, 11, 11634. [Google Scholar] [CrossRef]
- Raju, P.M.; Gupta, G.P. Intrusion Detection Framework Using an Improved Deep Reinforcement Learning Technique for IoT Network. In Soft Computing for Security Applications; Springer: Singapore, 2022; pp. 765–779. [Google Scholar]
- Guerra-Manzanares, A.; Medina-Galindo, J.; Bahsi, H.; Nõmm, S. MedBIoT: Generation of an IoT Botnet Dataset in a Medium-sized IoT Network. In ICISSP; ResearchGate: Berlin, Germany, 2020; pp. 207–218. [Google Scholar]
- Aprianti, W.; Deris Stiawan, M.T. Implementasi Principal Component Analysis (PCA) Dan Algoritma Naïve Bayes Classifier Pada Klasifikasi Botnet di Jaringan Internet of Things (IoT). Ph.D. Dissertation, Sriwijaya University, Palembang, Indonesia, 2021. [Google Scholar]
- Gandhi, R.; Li, Y. Comparing Machine Learning and Deep Learning for IoT Botnet Detection. In Proceedings of the 2021 IEEE International Conference on Smart Computing (SMARTCOMP), Irvine, CA, USA, 23–27 August 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 234–239. [Google Scholar]
- Giaretta, L.; Lekssays, A.; Carminati, B.; Ferrari, E.; Girdzijauskas, Š. LiMNet: Early-Stage Detection of IoT Botnets with Lightweight Memory Networks. In European Symposium on Research in Computer Security; Springer: Cham, Switzerland, 2021; pp. 605–625. [Google Scholar]
- McDermott, C.D.; Majdani, F.; Petrovski, A.V. Botnet detection in the internet of things using deep learning approaches. In Proceedings of the 2018 International Joint Conference on Neural Networks (IJCNN), Rio de Janeiro, Brazil, 8–13 July 2018; pp. 1–8. [Google Scholar]
- Kim, J.; Shim, M.; Hong, S.; Shin, Y.; Choi, E. Intelligent detection of IoT botnets using machine learning and deep learning. Appl. Sci. 2020, 10, 7009. [Google Scholar] [CrossRef]
- Vishwakarma, R.; Jain, A.K. A Honeypot with machine learning based detection framework for defending IoT based botnet DDoS attacks. In Proceedings of the 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 23–25 April 2019; pp. 1019–1024. [Google Scholar]
- Nguyen, H.-T.; Ngo, Q.-D.; Le, V.-H. IoT Botnet Detection Approach Based on PSI graph and DGCNN classifier. In Proceedings of the 2018 IEEE International Conference on Information Communication and Signal Processing (ICICSP), Singapore, 28–30 September 2018; pp. 118–122. [Google Scholar]
- Liu, J.; Liu, S.; Zhang, S. Detection of IoT botnet based on deep learning. In Proceedings of the 2019 Chinese Control Conference (CCC), Guangzhou, China, 27–30 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 8381–8385. [Google Scholar]
- Bahsi, H.; Nomm, S.; La Torre, F.B. Dimensionality reduction for machine learning based iot botnet detection. In Proceedings of the 2018 15th International Conference on Control, Automation, Robotics and Vision (ICARCV), Singapore, 18–21 November 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1857–1862. [Google Scholar]
- Yin, L.; Luo, X.; Zhu, C.; Wang, L.; Xu, Z.; Lu, H. ConnSpoiler: Disrupting C&C communication of IoT-based botnet through fast detection of anomalous domain queries. IEEE Trans. Ind. Inform. 2019, 16, 1373–1384. [Google Scholar]
- Jung, W.; Zhao, H.; Sun, M.; Zhou, G. IoT botnet detection via power consumption modeling. Smart Health 2020, 15, 100103. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Slay, J. Towards developing network forensic mechanism for botnet activities in the IoT based on machine learning techniques. In Proceedings of the International Conference on Mobile Networks and Management, Melbourne, Australia, 13–15 December 2017; Springer: Cham, Switzerland, 2017; pp. 30–44. [Google Scholar]
- Al Shorman, A.; Faris, H.; Aljarah, I. Unsupervised intelligent system based on one class support vector machine and Grey Wolf optimization for IoT botnet detection. J. Ambient Intell. Humaniz. Comput. 2020, 11, 2809–2825. [Google Scholar] [CrossRef]
- Virtualbox. Welcome to VirtualBox.org! 2022. Available online: https://www.virtualbox.org/ (accessed on 7 April 2022).
- Vagrant. Development Environments Made Easy. 2021. Available online: https://www.vagrantup.com/ (accessed on 7 April 2022).
- Jgamblin. Mirai-Source-Code. 2017. Available online: https://github.com/jgamblin/Mirai-Source-Code (accessed on 7 April 2022).
- Lestertang. Mirai-Botnet-Source-Code. 2017. Available online: https://github.com/lestertang/mirai-botnet-source-code (accessed on 7 April 2022).
- Kulukami. Build-a-Mirai-Botnet. 2019. Available online: https://github.com/kulukami/Build-a-Mirai-botnet (accessed on 7 April 2022).
- Virtualbox. VBoxManage. 2022. Available online: https://www.virtualbox.org/manual/ch08.html (accessed on 7 April 2022).
- Wireshark. Download. 2022. Available online: https://www.wireshark.org/ (accessed on 7 April 2022).
- UNSW. The UNSW-NB15 Dataset. 2021. Available online: https://research.unsw.edu.au/projects/unsw-nb15-dataset (accessed on 7 April 2022).
- UNSW. The Bot-IoT Dataset. 2021. Available online: https://research.unsw.edu.au/projects/bot-iot-dataset (accessed on 7 April 2022).
- Splunk. Turn Data into Doing. 2022. Available online: https://www.splunk.com/ (accessed on 7 April 2022).
- Scikit Learn. Sklearn.Model_Selection.Train_Test_Split. 2022. Available online: https://scikit-learn.org/stable/modules/generated/sklearn.model_selection.train_test_split.html (accessed on 7 April 2022).
- Cunningham, P.; Delany, S.J. k-Nearest neighbour classifiers—A Tutorial. ACM Comput. Surv. (CSUR) 2022, 54, 1–25. [Google Scholar] [CrossRef]
- Patel, H.H.; Prajapati, P. Study and analysis of decision tree based classification algorithms. Int. J. Comput. Sci. Eng. 2018, 6, 74–78. [Google Scholar] [CrossRef]
- Resende, P.A.A.; Drummond, A.C. A survey of random forest based methods for intrusion detection systems. ACM Comput. Surv. (CSUR) 2019, 51, 1–36. [Google Scholar] [CrossRef]
- Rao, A. Top 10 Python Libraries. 2022. Available online: https://www.edureka.co/blog/python-libraries/ (accessed on 7 April 2022).
- Cass, S. The 2018 Top Programming Languages. 2018. Available online: https://spectrum.ieee.org/the-2018-top-programming-languages (accessed on 7 April 2022).
- Anaconda. Data Science Technology for a Better World. 2022. Available online: https://www.anaconda.com/ (accessed on 7 April 2022).
- TensorFlow. TensorFlow 2 Quick Start for Beginners. 2022. Available online: https://www.tensorflow.org/ (accessed on 7 April 2022).
- Fchollet, F. Introduction to Keras for Researchers. 2020. Available online: https://keras.io/getting_started/intro_to_keras_for_researchers/ (accessed on 7 April 2022).
- Raschka, S. An overview of general performance metrics of binary classifier systems. arXiv 2014, preprint. arXiv:1410.5330. [Google Scholar]
- MITRE Corporation. ATT&CK Matrix for Enterprise. 2015. Available online: https://attack.mitre.org/ (accessed on 7 April 2022).
- Lockheed Martin Corporation. Seven Ways to Apply the Cyber Kill Chain with a Threat Intelligence Platform. 2015. Available online: https://www.lockheedmartin.com/content/dam/lockheedmartin/rms/documents/cyber/Seven_Ways_to_Apply_the_Cyber_Kill_Chain_with_a_Threat_Intelligence_Platform.pdf (accessed on 7 April 2022).





| Research Question | Motivation |
|---|---|
| RQ1. How does IoT malware behave in the IoT network to form a botnet? | Investigate how IoT malware such as Mirai starts to form a botnet in the IoT network with a concentration on the early stages in formulating the botnet. |
| RQ2. How can the Cross CNN_LSTM Deep Learning model identify IoT botnet detection based on a benchmark dataset? | Examine the proposed cross deep neural network model CNN_LSTM and employ it to detect botnets using a benchmark dataset. |
| RQ3. How can we compare the proposed Cross CNN_LSTM Deep Learning model to traditional ML techniques? | Investigate conventional machine learning approaches such as random forests (RF), k-nearest neighbour algorithm (k-NN), and support vector machine (SVM), along with a variety of evaluation metrics such as accuracy, precision, recall, and F1-score. |
| RQ4. How do we compare the proposed technique’s accuracy in detecting IoT botnets employing a benchmark dataset to baseline and other deep learning approaches? | Investigate state-of-the-art approaches that use deep learning with a variety of evaluation metrics, such as accuracy, precision, recall, and F1-score. |
| Authors | Year of Publication | Stage | Method | Maximum Score of Evaluation | Reference |
|---|---|---|---|---|---|
| Gupta, Govind P. | 2022 | Late | DRL, LR, NB | 96.99%. | [21] |
| Aprianti et al. | 2021 | Late | PCA+Naive | 97.71% | [23] |
| McDermott et al. | 2018 | Late | LSTM-RNN BLSTM-RNN | 99% | [26] |
| Liu et al. | 2019 | Late | CNN | 99.57% | [30] |
| Bahşi et al. | 2018 | Late | DT, k-NN | 98% | [31] |
| Yin et al. | 2019 | Late | TRW | 94% | [32] |
| Jung et al. | 2020 | Late | CNN | 96.5% | [33] |
| Koroniotis et al. | 2017 | Late | C4.5 DT | 93% | [34] |
| Al Shorman et al. | 2020 | Late | OCSVM, GWO | 99% | [35] |
| Guerra-Manzanares et al. | 2020 | Early | k-NN, DT, RF | 95% | [22] |
| Gandhi et al. | 2021 | Early | RF, MLPN, LSTM | 95% | [24] |
| Nguyen et al. | 2018 | Early | DG-CNN | 92% | [29] |
| Our proposed model | - | Early | CNN+LSTM | - | - |
| Traffic Type | Number of Devices | Number of Packets |
|---|---|---|
| BashLite | 40 | 4,143,276 |
| Mirai | 25 | 842,674 |
| Torii | 12 | 319,139 |
| Benign | 83 | 12,540,478 |
| Sum | 160 | 17,845,567 |
| Types | Features | Number of Features | |
|---|---|---|---|
| 1 | Host MAC and IP | Packet count, mean, and variance | 3 |
| 2 | Channel | Packet count, mean, variance, magnitude, radius, covariance, and correlation | 7 |
| 3 | Network Jitter | Packet count, mean, and variance of packet jitter in channel | 3 |
| 4 | Socket | Packet count, mean, variance, magnitude, radius, covariance, and correlation | 7 |
| Malware | Type of Class | Class | Number of Instances |
|---|---|---|---|
| Mirai | Legitimate | mirai_leg | 167,000 |
| Communication | mirai_mal_CC | 100,000 | |
| Spread | mirai_mal_spread | 100,000 | |
| Bashlite | Legitimate | bashlite_leg | 167,000 |
| Communication | bashlite_mal_CC | 100,000 | |
| Spread | bashlite_mal_spread | 100,000 | |
| Torii | Legitimate | torii_leg | 167,000 |
| Spread and communication | torii_mal_all | 100,000 |
| Model | Accuracy | Recall | F1-Score | Precision |
|---|---|---|---|---|
| KNN | 90.0 | 91.8 | 92.1 | 92.0 |
| DT | 91.0 | 93.5 | 93.625 | 93.5 |
| RF | 94.0 | 95.125 | 95.375 | 95.5 |
| Hyperparameter | Value |
|---|---|
| CNN units | 128, 64 |
| LSTM units | 64, 32 |
| Epochs | 50 |
| Early stopping | 10 |
| Starting learning rate | 0.001 |
| Activation | ReLU |
| Loss | Categorical cross-entropy, binary categorical cross-entropy |
| Optimiser | Adam |
| Predicted Class | ||
|---|---|---|
| Actual Class | Positive | Negative |
| Positive | TP | FN |
| Negative | FP | TN |
| Model | Classes | Accuracy | Recall | F1-Score | Precision |
|---|---|---|---|---|---|
| Binary classification | Legitimate | 99.23 | 99.17 | 99.23 | 99.30 |
| Malicious | 99.23 | 99.30 | 99.23 | 99.17 |
| Model | Classes | Accuracy | Recall | F1-Score | Precision |
|---|---|---|---|---|---|
| Multiclassification | Legitimate | 99.44 | 99.49 | 99.46 | 99.43 |
| Spread | 99.44 | 99.50 | 99.52 | 99.53 | |
| CC | 99.44 | 99.28 | 99.32 | 99.35 |
| Model | Classes | Accuracy | Recall | F1-Score | Precision |
|---|---|---|---|---|---|
| Multiclassification | Legitimate | 99.66 | 99.70 | 99.70 | 99.70 |
| Mirai | 99.66 | 99.15 | 99.19 | 99.23 | |
| Bashlite | 99.66 | 99.92 | 99.92 | 99.92 | |
| Torii | 99.66 | 99.95 | 99.88 | 99.81 |
| Type of Model | Dataset | Ref. | Model | Accuracy | Recall | F1-Score | Precision |
|---|---|---|---|---|---|---|---|
| Machine Learning Models | MedBIoT dataset | Our ML Models | KNN | 90.0 | 91.8 | 92.1 | 92.0 |
| DT | 91.0 | 93.5 | 93.625 | 93.5 | |||
| RF | 94.0 | 95.125 | 95.375 | 95.5 | |||
| [22] | KNN | 87.06 | 87.06 | 85.05 | 88.49 | ||
| DT | 95.16 | 95.84 | 95.16 | 94.99 | |||
| RF | 97.66 | 98.24 | 97.66 | 96.57 | |||
| Deep Learning Models | Other | [29] | DG-CNN | 92 | N/A | 94 | N/A |
| [33] | CNN | 96.5 | N/A | N/A | N/A | ||
| Our Cross CNN_LSTM | CNN + LSTM | 99.66 | 99.68 | 99.67 | 99.67 | ||
| Tactics | Reconnaissance | Initial Access | Credential Access | Lateral Movement | Defence Evasion | Execution | Persistence | Discovery |
|---|---|---|---|---|---|---|---|---|
| Related Techniques | Active Scanning | External Remote Services | Brute Force: Password Guessing | Exploitation of Remote Services | Indicator Removal on Host: File Deletion | Command and Scripting Interpreter | Pre-OS Boot: System Firmware | Process Discovery |
| Vulnerability Scanning | Environment Keying |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wazzan, M.; Algazzawi, D.; Albeshri, A.; Hasan, S.; Rabie, O.; Asghar, M.Z. Cross Deep Learning Method for Effectively Detecting the Propagation of IoT Botnet. Sensors 2022, 22, 3895. https://doi.org/10.3390/s22103895
Wazzan M, Algazzawi D, Albeshri A, Hasan S, Rabie O, Asghar MZ. Cross Deep Learning Method for Effectively Detecting the Propagation of IoT Botnet. Sensors. 2022; 22(10):3895. https://doi.org/10.3390/s22103895
Chicago/Turabian StyleWazzan, Majda, Daniyal Algazzawi, Aiiad Albeshri, Syed Hasan, Osama Rabie, and Muhammad Zubair Asghar. 2022. "Cross Deep Learning Method for Effectively Detecting the Propagation of IoT Botnet" Sensors 22, no. 10: 3895. https://doi.org/10.3390/s22103895
APA StyleWazzan, M., Algazzawi, D., Albeshri, A., Hasan, S., Rabie, O., & Asghar, M. Z. (2022). Cross Deep Learning Method for Effectively Detecting the Propagation of IoT Botnet. Sensors, 22(10), 3895. https://doi.org/10.3390/s22103895








